Network Design, Configuration, and Management Report - CSC73002
VerifiedAdded on 2022/10/12

Network Design and Management
Name of the Student
Name of the University
Author Note
Paraphrase This Document

NETWORK DESIGN AND MANAGEMENT
Abstract
There are numerous researches conducted so far that highlight the importance of network
topologies and management of network configuration in determining the effectiveness and
efficiency of network infrastructures. First the report presents the network topology and
discusses the physical layout as well as configuration of the interfaces. Next the report goes
on to show the configuration of the devices and that of the interfaces through which these
devices are connected in the network. After that the report shows how the internetwork
routing is configured and how it takes effect through a Wireshark packet capture where the
use of RIP protocol is highlighted. Then the report shows the communication between
devices of different networks through ICMP ping messages. Thereafter the report talks about
the change management plan for the network and ends with concluding notes.

NETWORK DESIGN AND MANAGEMENT
Table of Contents
Introduction................................................................................................................................3
Task 1: Network Simulation......................................................................................................3
Physical Network Topology...................................................................................................3
Suitable hardware configuration........................................................................................5
Suitable link technologies..................................................................................................5
Correct physical topology with sufficient notation............................................................5
Device configuration..............................................................................................................6
Device administration configuration..................................................................................6
Correct interface configuration..........................................................................................7
Internetwork routing configuration........................................................................................8
RIP routing configuration..................................................................................................8
Evidence of network connectivity verification................................................................10
Task 2: Network configuration management...........................................................................11
Network Topology...............................................................................................................11
Network Hardware and Software Requirements..................................................................11
Current configuration of devices......................................................................................12
Change Management........................................................................................................13
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK DESIGN AND MANAGEMENT
Paraphrase This Document
NETWORK DESIGN AND MANAGEMENT
Introduction
The following report tries to highlight the importance of network topologies and
management of network configuration in determining the effectiveness and efficiency of
network infrastructures. The report begins by presenting the network topology and discusses
the physical layout as well as configuration of the interfaces. Next the report goes on to show
the configuration of the devices and that of the interfaces through which these devices are
connected in the network. After that the report shows how the internetwork routing is
configured and how it takes effect through a Wireshark packet capture where the use of RIP
protocol is highlighted. Then the report shows the communication between devices of
different networks through ICMP ping messages. Thereafter the report talks about the change
management plan for the network and ends with concluding notes.
Task 1: Network Simulation
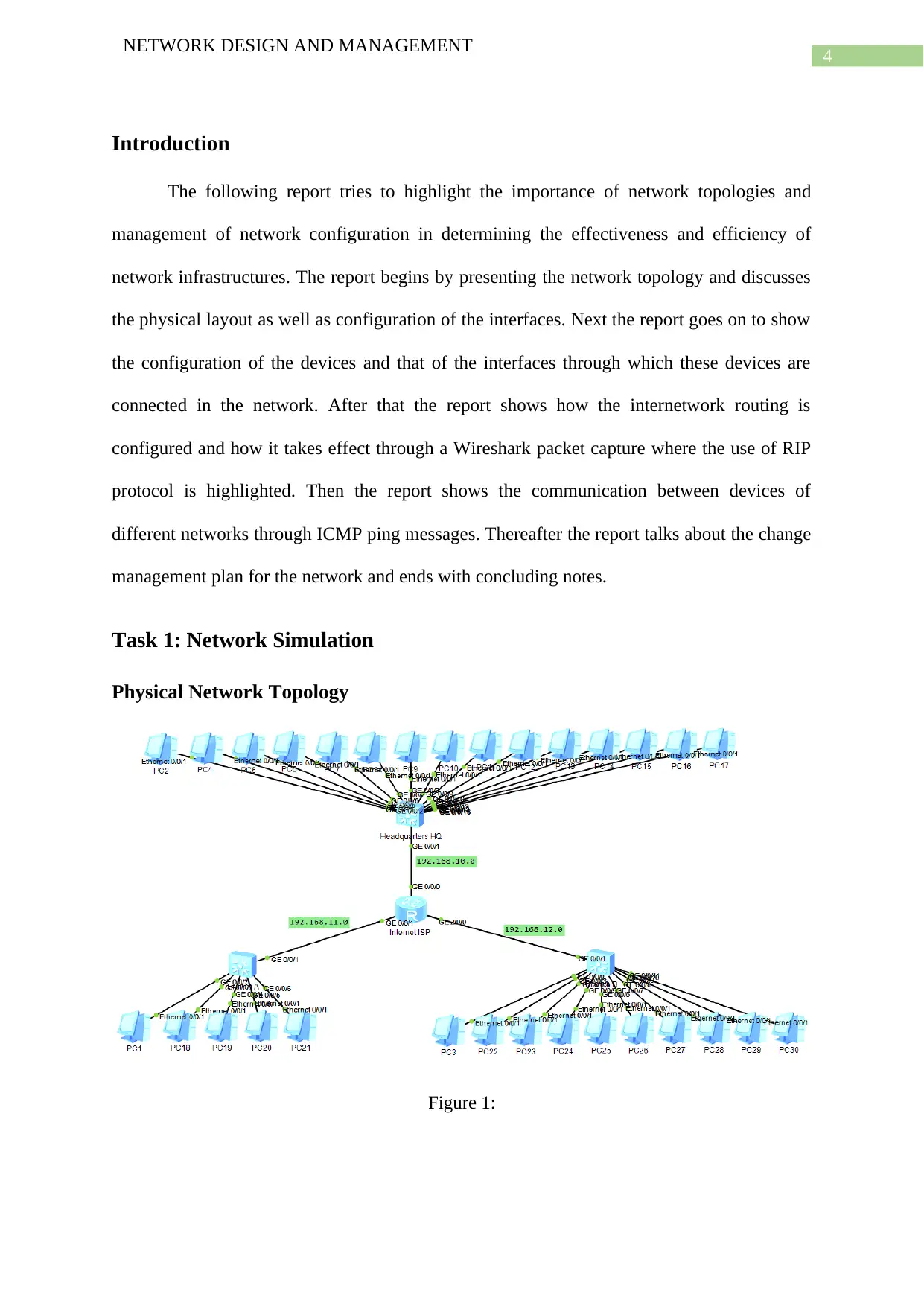
Physical Network Topology
Figure 1:

NETWORK DESIGN AND MANAGEMENT
As can be seen from the above figure the physical topology of the network involves the
computers of the headquarters as well as that of the branches A and B. These three branches
are connected with one another through the internet. The network used for the headquarters is
192.168.10.0. The network used for the branch A is 192.168.11.0 and that for the branch C is
192.168.12.0. The ISP router uses the interfaces GE 0/0/0, 0/0/1 and 2/0/0 for the
headquarters, branch A and branch B respectively. The computers or PCs are connected via
ethernet 0/0/1 interfaces with the switches of these branches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK DESIGN AND MANAGEMENT
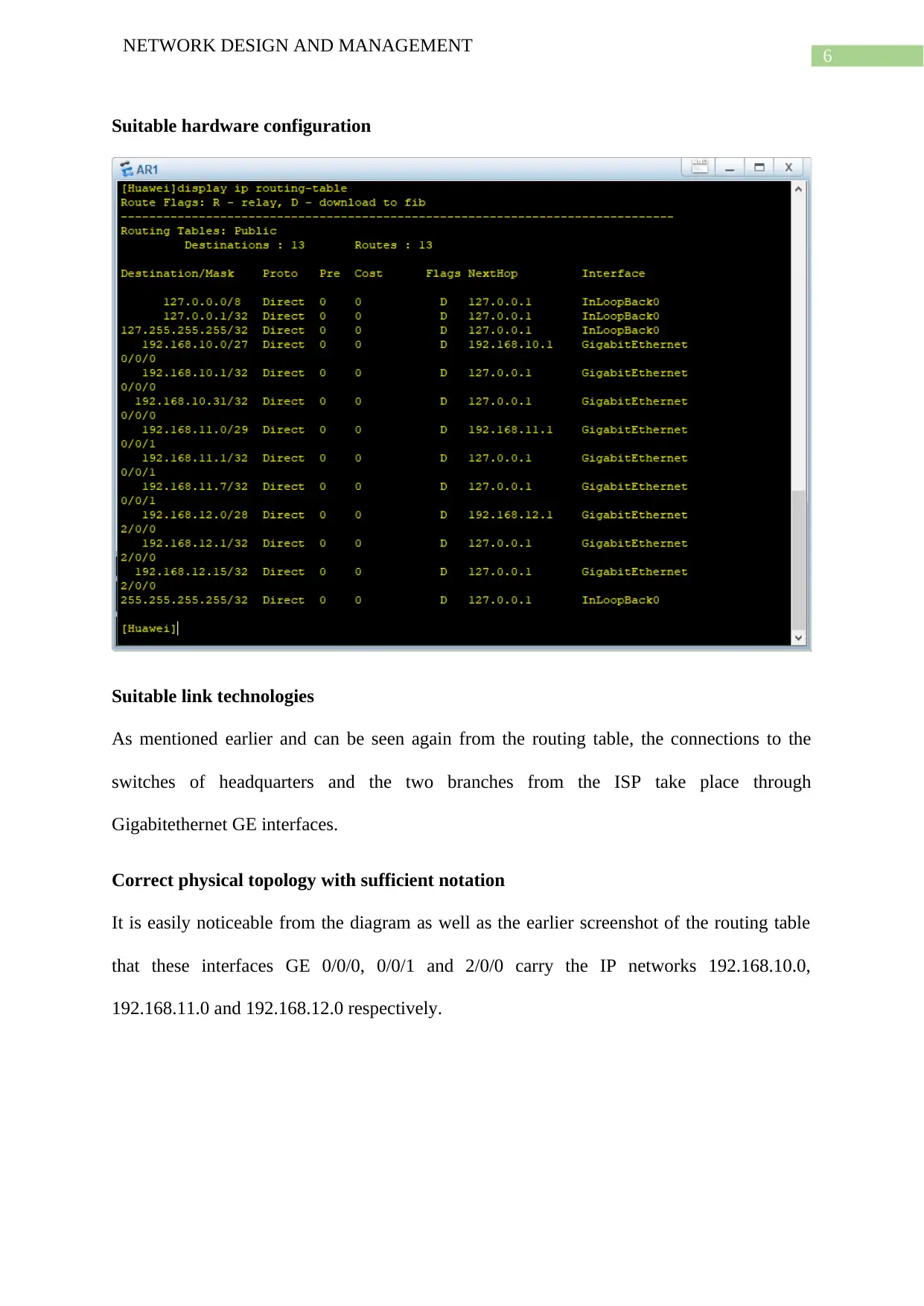
Suitable hardware configuration
Suitable link technologies
As mentioned earlier and can be seen again from the routing table, the connections to the
switches of headquarters and the two branches from the ISP take place through
Gigabitethernet GE interfaces.
Correct physical topology with sufficient notation
It is easily noticeable from the diagram as well as the earlier screenshot of the routing table
that these interfaces GE 0/0/0, 0/0/1 and 2/0/0 carry the IP networks 192.168.10.0,
192.168.11.0 and 192.168.12.0 respectively.
Paraphrase This Document
NETWORK DESIGN AND MANAGEMENT
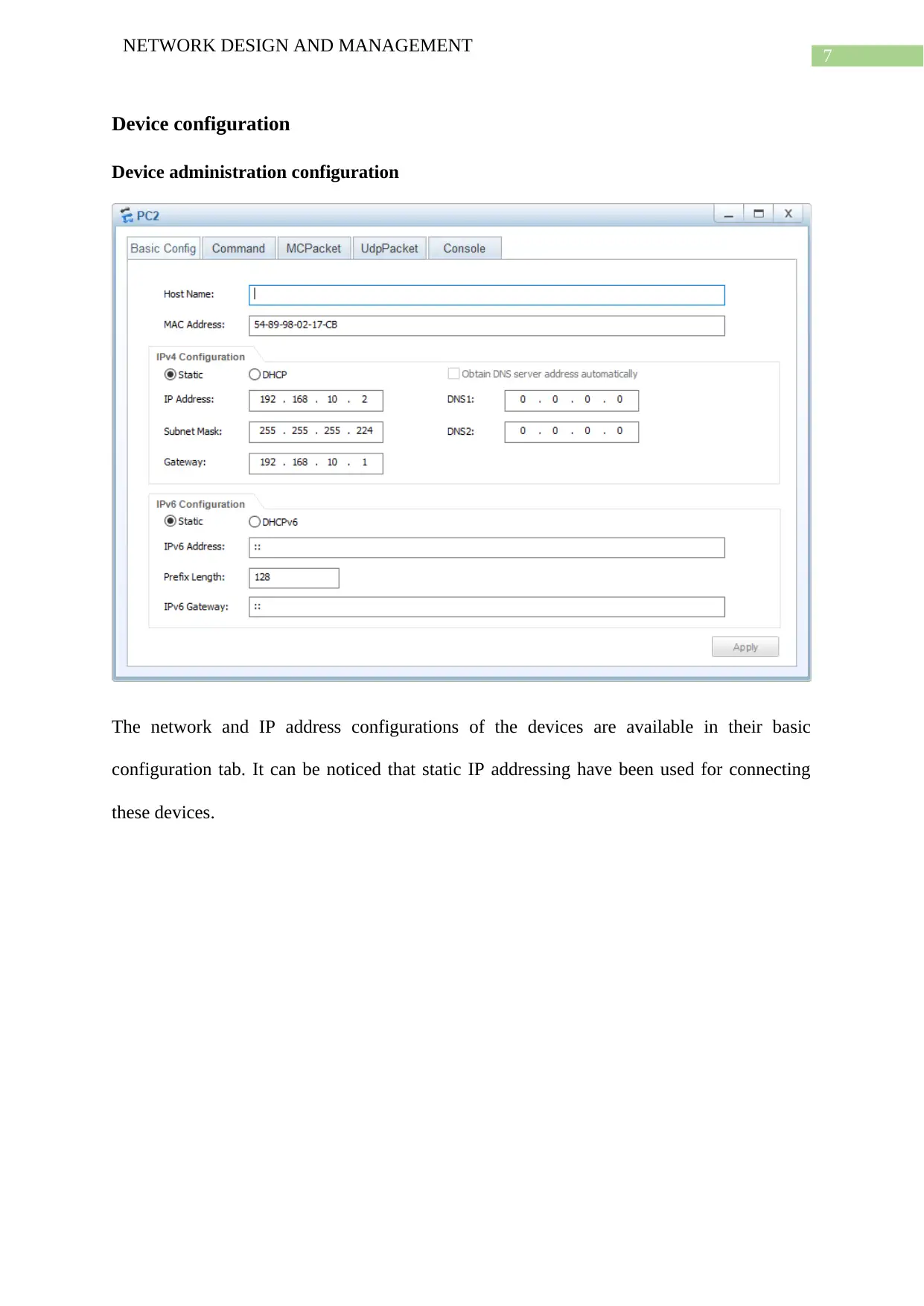
Device configuration
Device administration configuration
The network and IP address configurations of the devices are available in their basic
configuration tab. It can be noticed that static IP addressing have been used for connecting
these devices.
NETWORK DESIGN AND MANAGEMENT
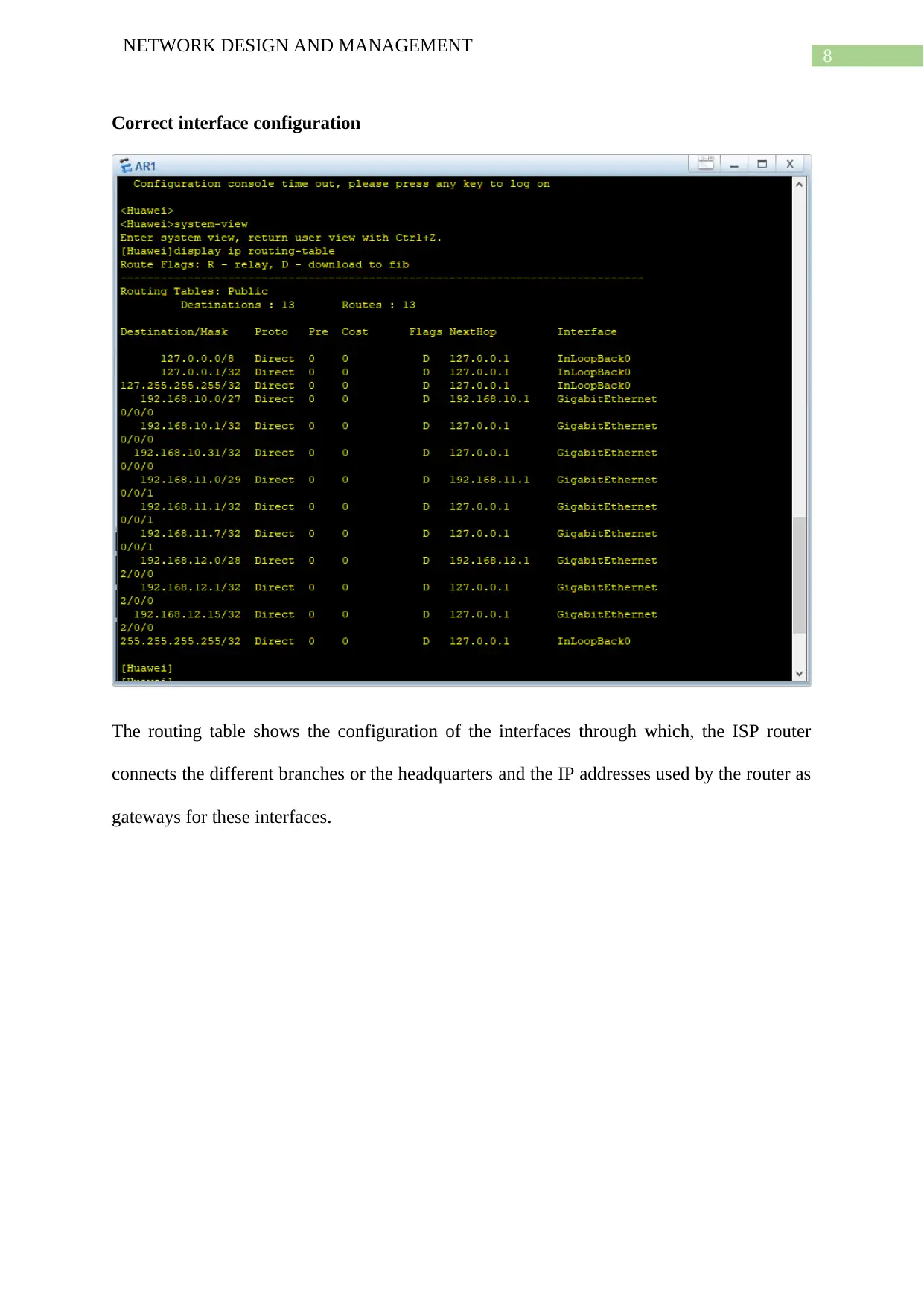
Correct interface configuration
The routing table shows the configuration of the interfaces through which, the ISP router
connects the different branches or the headquarters and the IP addresses used by the router as
gateways for these interfaces.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK DESIGN AND MANAGEMENT
Internetwork routing configuration
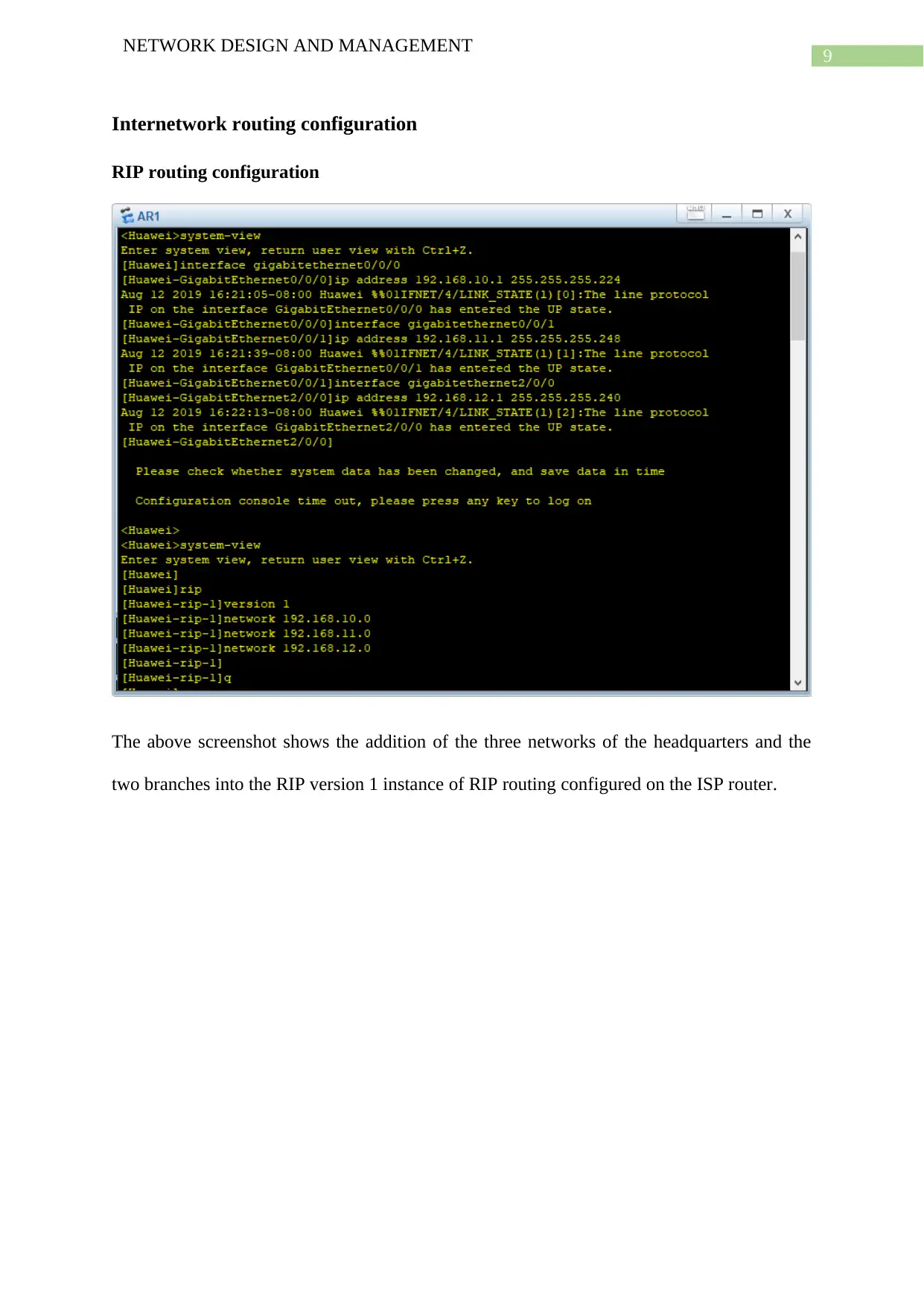
RIP routing configuration
The above screenshot shows the addition of the three networks of the headquarters and the
two branches into the RIP version 1 instance of RIP routing configured on the ISP router.
Paraphrase This Document
NETWORK DESIGN AND MANAGEMENT
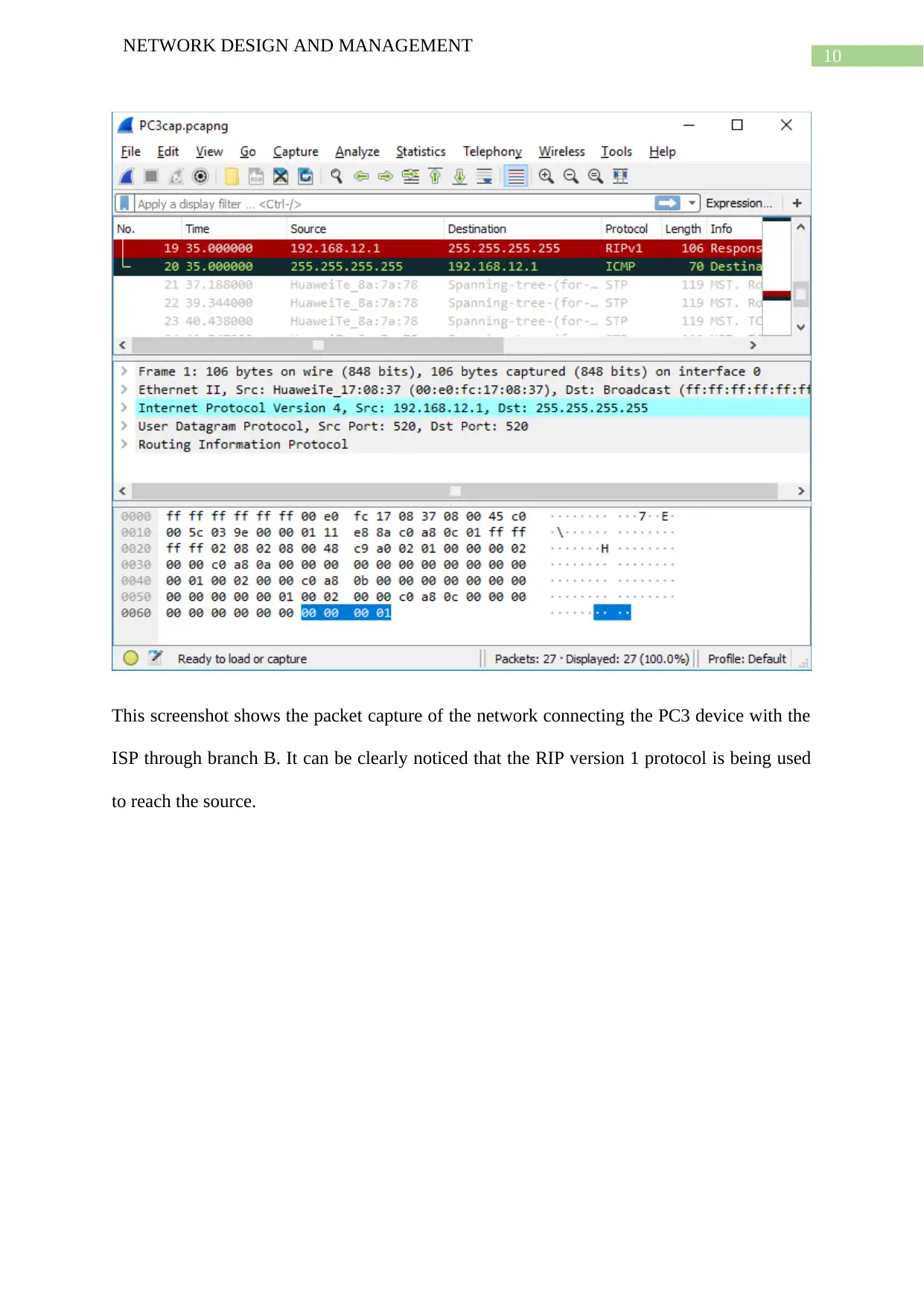
This screenshot shows the packet capture of the network connecting the PC3 device with the
ISP through branch B. It can be clearly noticed that the RIP version 1 protocol is being used
to reach the source.
NETWORK DESIGN AND MANAGEMENT
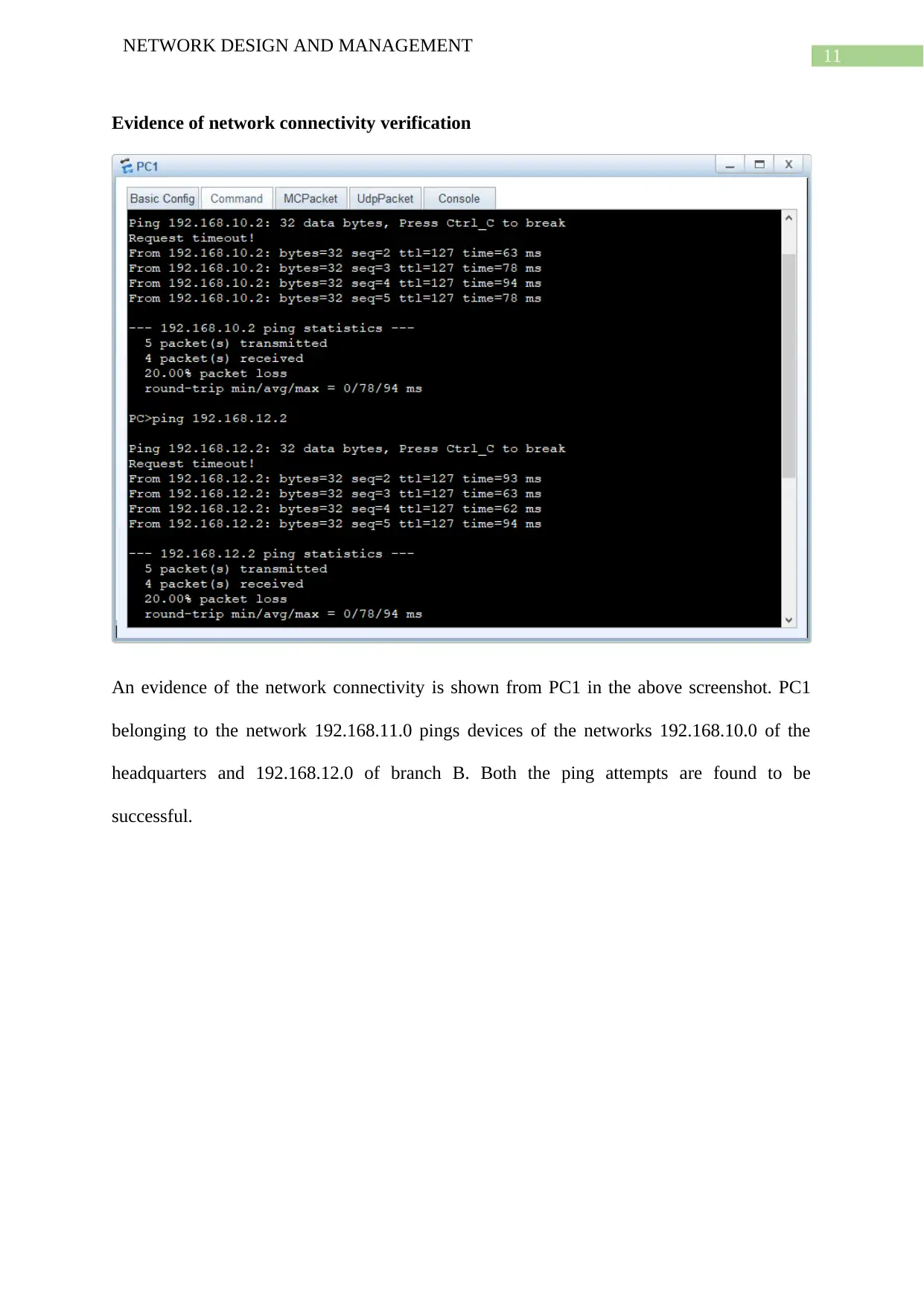
Evidence of network connectivity verification
An evidence of the network connectivity is shown from PC1 in the above screenshot. PC1
belonging to the network 192.168.11.0 pings devices of the networks 192.168.10.0 of the
headquarters and 192.168.12.0 of branch B. Both the ping attempts are found to be
successful.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK DESIGN AND MANAGEMENT
Task 2: Network configuration management
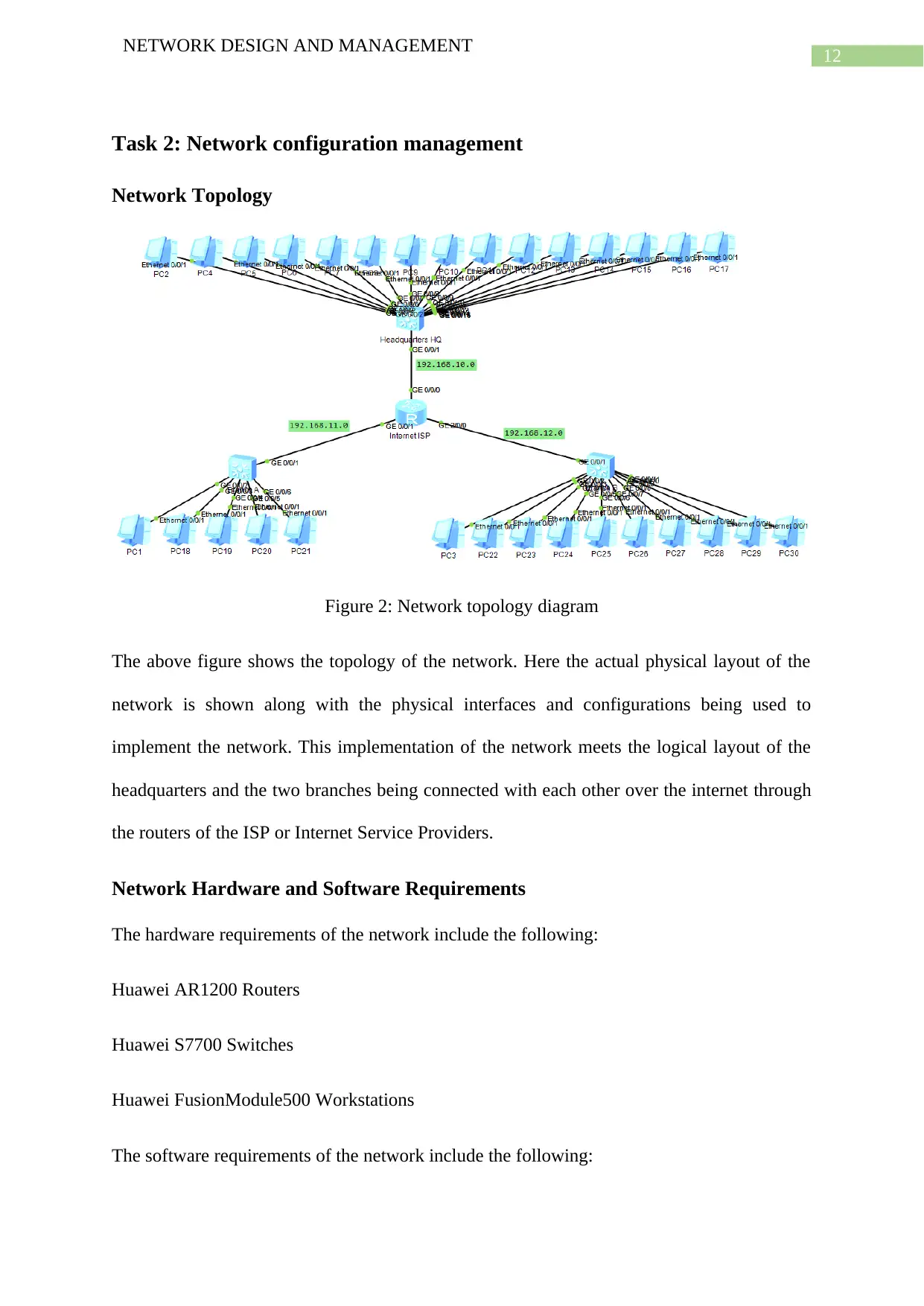
Network Topology
Figure 2: Network topology diagram
The above figure shows the topology of the network. Here the actual physical layout of the
network is shown along with the physical interfaces and configurations being used to
implement the network. This implementation of the network meets the logical layout of the
headquarters and the two branches being connected with each other over the internet through
the routers of the ISP or Internet Service Providers.
Network Hardware and Software Requirements
The hardware requirements of the network include the following:
Huawei AR1200 Routers
Huawei S7700 Switches
Huawei FusionModule500 Workstations
The software requirements of the network include the following:
Paraphrase This Document
NETWORK DESIGN AND MANAGEMENT
AR1200 V200R009C00SPC500 firmware for routers
S7700 V200R010C00SPC600 firmware for switches
Windows 10 operating systems for the workstations
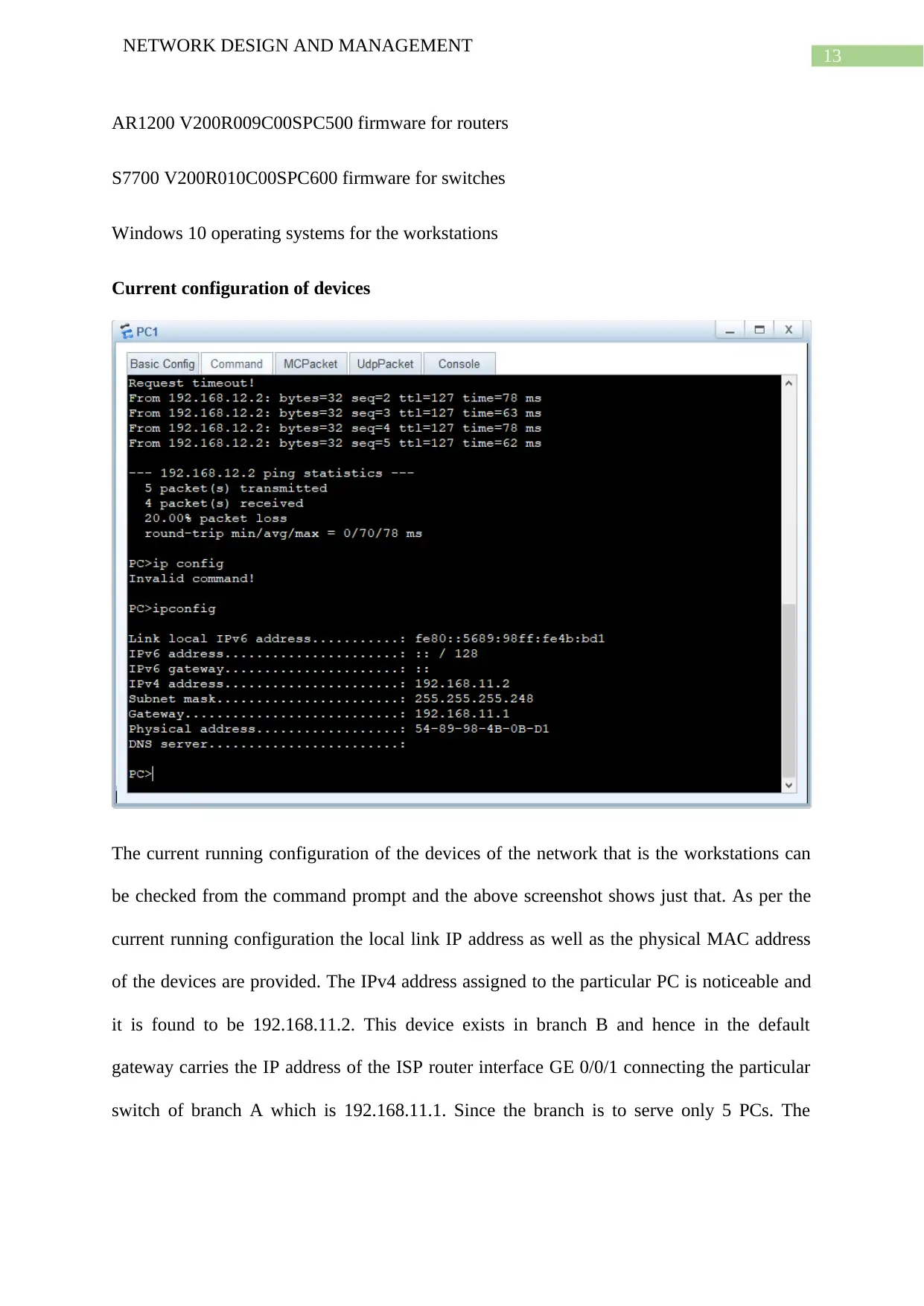
Current configuration of devices
The current running configuration of the devices of the network that is the workstations can
be checked from the command prompt and the above screenshot shows just that. As per the
current running configuration the local link IP address as well as the physical MAC address
of the devices are provided. The IPv4 address assigned to the particular PC is noticeable and
it is found to be 192.168.11.2. This device exists in branch B and hence in the default
gateway carries the IP address of the ISP router interface GE 0/0/1 connecting the particular
switch of branch A which is 192.168.11.1. Since the branch is to serve only 5 PCs. The

NETWORK DESIGN AND MANAGEMENT
address space allocated by the respective subnet is 6 and the subnet mask hence happens to be
255.255.255.248.
Change Management
In most cases the usual cause of network outages happens to be either faulty changes to the
network configuration, violation of compliances as also conflicts of network configuration.
These network issues can get sorted and are even preventable from recurring again and again
provided that the network administrators are enhancing their visibility towards the network to
gain more control over the changes in the flow of the network. The key techniques that these
network admins can resort to for gaining greater control are configuration change alerts,
implementing search configurations, configuring in depth report generation, scheduling of
jobs, remote upgrade of firmware, review of PCI network interfaces, having the option of
rollback of configuration, providing network access in role-based manner. Most importantly
any changes to the configuration of the network should undergo review and approval
processes before being exercised.
Conclusion
In conclusion the above report succeeds in highlighting the importance of network
topologies and management of network configuration in determining the effectiveness and
efficiency of network infrastructures. The report is observed to present the network topology
and discusses the physical layout as well as configuration of the interfaces. Next the report
goes on to show the configuration of the devices and that of the interfaces through which
these devices are connected in the network. After that the report shows how the internetwork
routing is configured and how it takes effect through a Wireshark packet capture where the
use of RIP protocol is highlighted. Then the report shows the communication between
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK DESIGN AND MANAGEMENT
devices of different networks through ICMP ping messages. Thereafter the report talks about
the change management plan for the network and ends with concluding notes.
Paraphrase This Document

NETWORK DESIGN AND MANAGEMENT
Bibliography
Beckett, R., Gupta, A., Mahajan, R. and Walker, D., 2017, August. A general approach to
network configuration verification. In Proceedings of the Conference of the ACM Special
Interest Group on Data Communication (pp. 155-168). ACM.
Clark, T., Burton, E., Clark, E. and Cook, N., 2018. RIP: A Methodology for the Evaluation
of Online Algorithms. International Journal of Software Systems Research and Methodology,
3(1).
Emiliano, R. and Antunes, M., 2015, July. Automatic network configuration in virtualized
environment using gns3. In 2015 10th International Conference on Computer Science &
Education (ICCSE) (pp. 25-30). IEEE.
Fayaz, S.K., Sharma, T., Fogel, A., Mahajan, R., Millstein, T., Sekar, V. and Varghese, G.,
2016. Efficient network reachability analysis using a succinct control plane representation. In
12th {USENIX} Symposium on Operating Systems Design and Implementation ({OSDI} 16)
(pp. 217-232).
Jin, X., Li, Y., Wei, D., Li, S., Gao, J., Xu, L., Li, G., Xu, W. and Rexford, J., 2016, August.
Optimizing bulk transfers with software-defined optical WAN. In Proceedings of the 2016
ACM SIGCOMM Conference (pp. 87-100). ACM.
Skowyra, R., Xu, L., Gu, G., Dedhia, V., Hobson, T., Okhravi, H. and Landry, J., 2018, June.
Effective topology tampering attacks and defenses in software-defined networks. In 2018
48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks
(DSN) (pp. 374-385). IEEE.

NETWORK DESIGN AND MANAGEMENT
Verma, A. and Bhardwaj, N., 2016. A review on routing information protocol (RIP) and open
shortest path first (OSPF) routing protocol. International Journal of Future Generation
Communication and Networking, 9(4), pp.161-170.
Xiong, X., Zheng, K., Xu, R., Xiang, W. and Chatzimisios, P., 2015. Low power wide area
machine-to-machine networks: key techniques and prototype. IEEE Communications
Magazine, 53(9), pp.64-71.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.



