Network Design and Troubleshooting Report for ABC Organization
VerifiedAdded on 2023/01/11
|13
|3460
|89
Report
AI Summary
This report provides a comprehensive analysis of network design and troubleshooting for the ABC organization. It begins by illustrating the network topology, detailing the arrangement of nodes, switches, and routers, and the connections between them, including diagrams. The report then describes the various devices utilized, such as switches, routers, and firewalls, highlighting their functions and importance in the network. It also discusses the technologies employed to meet the organization's requirements, including the OSI model and network layering. Security configurations, including the use of DMZ and spanning tree protocol are detailed, as well as configurations for routers and switches, and the use of VLANs. The report covers security measures like access control lists, firewalls, and encryption. Finally, the report concludes with a summary of the key findings and recommendations for optimizing the network's performance, security, and reliability. The appendix includes configurations for the router and switch.

Network Design and
Troubleshooting
Troubleshooting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................1
Illustrate topology utilised......................................................................................................1
Depict devices utilised............................................................................................................3
Describe technologies for accomplishment of requirements..................................................4
Demilitarised zone and spanning tree.....................................................................................5
Configuration of routers and switches....................................................................................5
Security configuration............................................................................................................5
VLAN.....................................................................................................................................6
Testing servers........................................................................................................................7
Test connectivity....................................................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
Appendix........................................................................................................................................10
Configure Router..................................................................................................................10
Configure Switch..................................................................................................................10
Introduction......................................................................................................................................1
Illustrate topology utilised......................................................................................................1
Depict devices utilised............................................................................................................3
Describe technologies for accomplishment of requirements..................................................4
Demilitarised zone and spanning tree.....................................................................................5
Configuration of routers and switches....................................................................................5
Security configuration............................................................................................................5
VLAN.....................................................................................................................................6
Testing servers........................................................................................................................7
Test connectivity....................................................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
Appendix........................................................................................................................................10
Configure Router..................................................................................................................10
Configure Switch..................................................................................................................10

Introduction
The process of planning execution of computer networking infrastructure is defined as
network design. Basically, they are systems designs which are liable for dealing with transport
mechanism of data (Airi and Anderson, 2017). This involves analysis stage (requirements are
generated) and execution is preceded by making use of relevant system components. Network
troubleshooting implies collective measure as well as processes that are being utilised for
identification, diagnosis and resolving problems along with issues in computer network. It aims
at resolving problems through which network operations can be conducted normally. This report
is based on ABC organisation and their network has to be evaluated. This report involves
network design, devices utilised, and technologies used, security aspects and various other
aspects related with designing and troubleshooting.
Illustrate topology utilised
The way in which network is being arranged that comprises of logical or physical
description of ways in which links as well as nodes are set that are associated with one other is
referred to as network topology (Blair, Key and Wilson, 2019). Basically, it is arrangement of
nodes normally routers, switches or software features along with connections in network. With
respect to ABC firm, the network simulation is specified below:
Illustration 1: Network diagram
1
The process of planning execution of computer networking infrastructure is defined as
network design. Basically, they are systems designs which are liable for dealing with transport
mechanism of data (Airi and Anderson, 2017). This involves analysis stage (requirements are
generated) and execution is preceded by making use of relevant system components. Network
troubleshooting implies collective measure as well as processes that are being utilised for
identification, diagnosis and resolving problems along with issues in computer network. It aims
at resolving problems through which network operations can be conducted normally. This report
is based on ABC organisation and their network has to be evaluated. This report involves
network design, devices utilised, and technologies used, security aspects and various other
aspects related with designing and troubleshooting.
Illustrate topology utilised
The way in which network is being arranged that comprises of logical or physical
description of ways in which links as well as nodes are set that are associated with one other is
referred to as network topology (Blair, Key and Wilson, 2019). Basically, it is arrangement of
nodes normally routers, switches or software features along with connections in network. With
respect to ABC firm, the network simulation is specified below:
Illustration 1: Network diagram
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
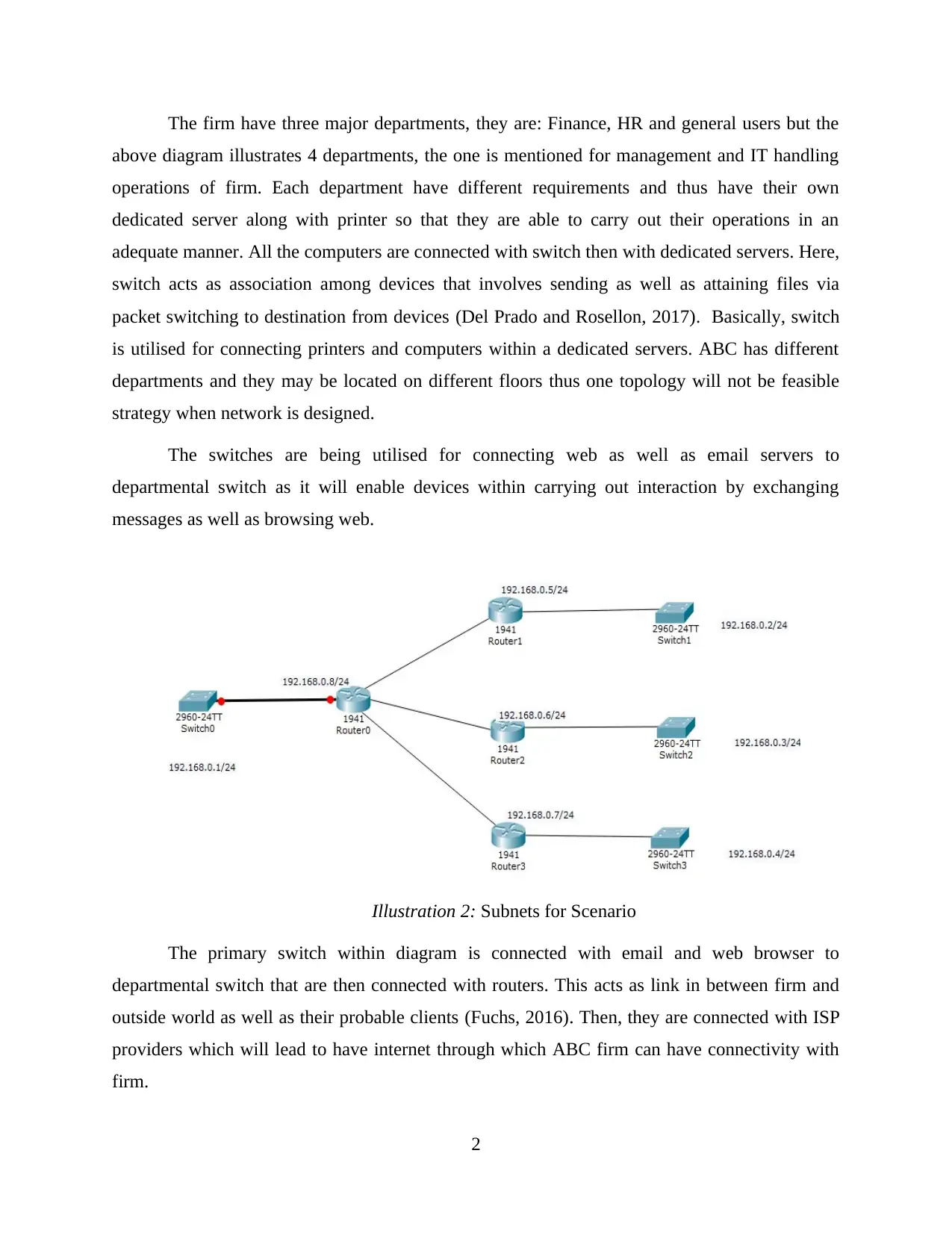
The firm have three major departments, they are: Finance, HR and general users but the
above diagram illustrates 4 departments, the one is mentioned for management and IT handling
operations of firm. Each department have different requirements and thus have their own
dedicated server along with printer so that they are able to carry out their operations in an
adequate manner. All the computers are connected with switch then with dedicated servers. Here,
switch acts as association among devices that involves sending as well as attaining files via
packet switching to destination from devices (Del Prado and Rosellon, 2017). Basically, switch
is utilised for connecting printers and computers within a dedicated servers. ABC has different
departments and they may be located on different floors thus one topology will not be feasible
strategy when network is designed.
The switches are being utilised for connecting web as well as email servers to
departmental switch as it will enable devices within carrying out interaction by exchanging
messages as well as browsing web.
Illustration 2: Subnets for Scenario
The primary switch within diagram is connected with email and web browser to
departmental switch that are then connected with routers. This acts as link in between firm and
outside world as well as their probable clients (Fuchs, 2016). Then, they are connected with ISP
providers which will lead to have internet through which ABC firm can have connectivity with
firm.
2
above diagram illustrates 4 departments, the one is mentioned for management and IT handling
operations of firm. Each department have different requirements and thus have their own
dedicated server along with printer so that they are able to carry out their operations in an
adequate manner. All the computers are connected with switch then with dedicated servers. Here,
switch acts as association among devices that involves sending as well as attaining files via
packet switching to destination from devices (Del Prado and Rosellon, 2017). Basically, switch
is utilised for connecting printers and computers within a dedicated servers. ABC has different
departments and they may be located on different floors thus one topology will not be feasible
strategy when network is designed.
The switches are being utilised for connecting web as well as email servers to
departmental switch as it will enable devices within carrying out interaction by exchanging
messages as well as browsing web.
Illustration 2: Subnets for Scenario
The primary switch within diagram is connected with email and web browser to
departmental switch that are then connected with routers. This acts as link in between firm and
outside world as well as their probable clients (Fuchs, 2016). Then, they are connected with ISP
providers which will lead to have internet through which ABC firm can have connectivity with
firm.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Depict devices utilised
The firm who render services have a network that comprises of different components.
The basic element is they, they are fax machines, laptops, computers, IP phones, printers and
many other peripheral devices on which firm had made investments (Govindan, Fattahi and
Keyvanshokooh, 2017). These devices are liable for identification of links which will be utilised
for enhancing interaction. Networking devices which are being utilised in this scenario are
switches, routers, firewall and servers. The crucial device is server as they comprises of all
software and files so that they can be shared among different departments as per their
requirements. The access must be from single point. Firm have dedicated servers to enhance
security along with their performance. The devices used are specified below:
Switches: They are apt to connect nodes with main sever as well as router. In addition to
this hub also perform same function. But switch is preferred more as it provides advanced
functionalities through which complex functionalities related with sending messages to
devices can be conducted easily. The other feature is speed that is being provided by
switch. As ABC needs to have dedicated email server as well as print server file in which
sharing and synchronisation of data will take place among users and devices so that data
can be retrieved (Jabbarzadeh, Haughton and Khosrojerdi, 2018). Density is liable for
identification of number of devices which are connected with switch. It is relevant that 16
port switch is used as it will furnish relevant power to devices as they connect with VoIP
or printer. With reference to future, stackable switch is apt option as it renders high
capabilities for management of cable failures.
Routers: These devices are best for having network interaction among computers as well
as other devices on the network. The switch can also be used irrespective of routers but it
is restricted to LAN (local area network) but routers have many capabilities as they can
cover MAN (metropolitan area network) and WAN (wide area network). They also store
more IP addresses within routing table which can be utilised for future references. It is
crucial when request have to be made to internet (Jain, Edgeworth and Furr, 2018). As
ABC firm have both public and private IP addresses, this will be crucial way by which
upcoming requests that comes from different addresses can be handled in an adequate
manner. The switch will be used to handle local IP requests and router for public
3
The firm who render services have a network that comprises of different components.
The basic element is they, they are fax machines, laptops, computers, IP phones, printers and
many other peripheral devices on which firm had made investments (Govindan, Fattahi and
Keyvanshokooh, 2017). These devices are liable for identification of links which will be utilised
for enhancing interaction. Networking devices which are being utilised in this scenario are
switches, routers, firewall and servers. The crucial device is server as they comprises of all
software and files so that they can be shared among different departments as per their
requirements. The access must be from single point. Firm have dedicated servers to enhance
security along with their performance. The devices used are specified below:
Switches: They are apt to connect nodes with main sever as well as router. In addition to
this hub also perform same function. But switch is preferred more as it provides advanced
functionalities through which complex functionalities related with sending messages to
devices can be conducted easily. The other feature is speed that is being provided by
switch. As ABC needs to have dedicated email server as well as print server file in which
sharing and synchronisation of data will take place among users and devices so that data
can be retrieved (Jabbarzadeh, Haughton and Khosrojerdi, 2018). Density is liable for
identification of number of devices which are connected with switch. It is relevant that 16
port switch is used as it will furnish relevant power to devices as they connect with VoIP
or printer. With reference to future, stackable switch is apt option as it renders high
capabilities for management of cable failures.
Routers: These devices are best for having network interaction among computers as well
as other devices on the network. The switch can also be used irrespective of routers but it
is restricted to LAN (local area network) but routers have many capabilities as they can
cover MAN (metropolitan area network) and WAN (wide area network). They also store
more IP addresses within routing table which can be utilised for future references. It is
crucial when request have to be made to internet (Jain, Edgeworth and Furr, 2018). As
ABC firm have both public and private IP addresses, this will be crucial way by which
upcoming requests that comes from different addresses can be handled in an adequate
manner. The switch will be used to handle local IP requests and router for public
3

networks. The major requirement of router comprises of dual band which enables speed
of data exchange among offices. Single link router will not be apt as it can be slower with
respect to dual link router. In addition to this, protection must also be enabled within this.
It comprises of encrypting data by which hackers cannot have access to information from
within the network. In addition to this routers have to track devices for making sure that
any kind of abnormal, unwanted or unauthenticated activities are not detected. Other
crucial deliberation for router comprises of capabilities which allow virtual local area
network to be configured (Keyvanshokooh, Ryan and Kabir, 2016). Furthermore, VLAN
is an essential element for firm to ensure that information can share as well as network
can be protected.
Firewall: It is being used for furnish to network as it will act like a defence from
preventing hackers to enter within their system. It will enable IT employees of firm to
monitor the incoming as well as outgoing traffic. This enables it to ensure that any
unauthenticated activities are not carried out by them and it will keep them safe from any
kind of harmful or malicious attacks like hacking, spywares, Trojan horses and many
more (Liang, 2020).
Describe technologies for accomplishment of requirements
The OSI model is being followed by network layering with respect to network protocol
designs. The third and second layers i.e. networking as well as data link layers respectively. This
involves that layer 2 is liable for transferring data packets across local area network. In this layer
Ethernet cables and switches are being used. But the major problem that occurs within this is that
congestion can take place in case traffic gets larger which lead to drop performance of activities
that are being carried out within ABC firm. Therefore, it is not adequate for usage as its own.
Networking layer is used for having interaction by transmission and attaining files. With
reference to this, data is being logically addressed that implies that it has IP addressing which are
then routed so that destination can be reached and precisely (Rajabiyazdi, 2016). This implies
that these layers have capability for connecting LANs with WANs. Furthermore, routers are
being used within layer 3 as it provides an ease to scale up without any congestion even when
traffic is in bulk. This aids administrator within sub-dividing network into small manageable
parts.
4
of data exchange among offices. Single link router will not be apt as it can be slower with
respect to dual link router. In addition to this, protection must also be enabled within this.
It comprises of encrypting data by which hackers cannot have access to information from
within the network. In addition to this routers have to track devices for making sure that
any kind of abnormal, unwanted or unauthenticated activities are not detected. Other
crucial deliberation for router comprises of capabilities which allow virtual local area
network to be configured (Keyvanshokooh, Ryan and Kabir, 2016). Furthermore, VLAN
is an essential element for firm to ensure that information can share as well as network
can be protected.
Firewall: It is being used for furnish to network as it will act like a defence from
preventing hackers to enter within their system. It will enable IT employees of firm to
monitor the incoming as well as outgoing traffic. This enables it to ensure that any
unauthenticated activities are not carried out by them and it will keep them safe from any
kind of harmful or malicious attacks like hacking, spywares, Trojan horses and many
more (Liang, 2020).
Describe technologies for accomplishment of requirements
The OSI model is being followed by network layering with respect to network protocol
designs. The third and second layers i.e. networking as well as data link layers respectively. This
involves that layer 2 is liable for transferring data packets across local area network. In this layer
Ethernet cables and switches are being used. But the major problem that occurs within this is that
congestion can take place in case traffic gets larger which lead to drop performance of activities
that are being carried out within ABC firm. Therefore, it is not adequate for usage as its own.
Networking layer is used for having interaction by transmission and attaining files. With
reference to this, data is being logically addressed that implies that it has IP addressing which are
then routed so that destination can be reached and precisely (Rajabiyazdi, 2016). This implies
that these layers have capability for connecting LANs with WANs. Furthermore, routers are
being used within layer 3 as it provides an ease to scale up without any congestion even when
traffic is in bulk. This aids administrator within sub-dividing network into small manageable
parts.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Demilitarised zone and spanning tree
The network either logical or physical that is being utilised for connecting hosts which
renders interface for untrusted external networks (normally internet) by making sure that private,
internal or corporate network are isolated as well as separated from external network is referred
to as DMZ (demilitarized) zone. The systems are prone to attacks when services are being
provided to outside users i.e. they are not from specified LAN like domain name system (DNS)
servers, email and Web (Spithoven, Vlegels and Ysebaert, 2019). These are quarantined within
DMZ which restricts access towards private network of organisation. Hosts can carry out
interaction with both external and internal networks but certain restrictions are executed.
Spanning tree protocol refers to network protocol that is liable for building up loop-free logical
topology for Ethernet networks. It is liable for preventing bridge loops along with broadcast
radiation that are resulted from this. It aids network design that comprises of backup links that
furnishes fault tolerance in case if any of the links fail.
Configuration of routers and switches
The scheduling of each functional unit as per their number, nature along with chief
characteristics is referred to as configuration. It is necessary to configure routers, switches or any
other device which is used within network to ensure that effective communication takes place
among these components thereby leads to attainment of overall objective i.e. to make sure that
information is shared among different systems within the network in an enhanced manner (Yi
and et. al, 2016). With respect to ABC configuration of switch and router is illustrated in
appendix.
Security configuration
Routers firewall and switches are being utilised for enhancement of security within the
network. Switch is liable for allowing only local area network for communication in the network.
This implies that nodes or systems which are connected with network can interact with those
outside of LAN. It implies the security aspects can be maintained by making use of switches.
Routers are liable for creating an access barrier to nodes which have requested for outside
networks. They will have their requirements accomplished. But this does not imply that
interaction is being channelized for other nodes also (Airi and Anderson, 2017). The node that
has made request will only have access to outside services. But certain security measures,
restrictions and control measures are being utilised.
5
The network either logical or physical that is being utilised for connecting hosts which
renders interface for untrusted external networks (normally internet) by making sure that private,
internal or corporate network are isolated as well as separated from external network is referred
to as DMZ (demilitarized) zone. The systems are prone to attacks when services are being
provided to outside users i.e. they are not from specified LAN like domain name system (DNS)
servers, email and Web (Spithoven, Vlegels and Ysebaert, 2019). These are quarantined within
DMZ which restricts access towards private network of organisation. Hosts can carry out
interaction with both external and internal networks but certain restrictions are executed.
Spanning tree protocol refers to network protocol that is liable for building up loop-free logical
topology for Ethernet networks. It is liable for preventing bridge loops along with broadcast
radiation that are resulted from this. It aids network design that comprises of backup links that
furnishes fault tolerance in case if any of the links fail.
Configuration of routers and switches
The scheduling of each functional unit as per their number, nature along with chief
characteristics is referred to as configuration. It is necessary to configure routers, switches or any
other device which is used within network to ensure that effective communication takes place
among these components thereby leads to attainment of overall objective i.e. to make sure that
information is shared among different systems within the network in an enhanced manner (Yi
and et. al, 2016). With respect to ABC configuration of switch and router is illustrated in
appendix.
Security configuration
Routers firewall and switches are being utilised for enhancement of security within the
network. Switch is liable for allowing only local area network for communication in the network.
This implies that nodes or systems which are connected with network can interact with those
outside of LAN. It implies the security aspects can be maintained by making use of switches.
Routers are liable for creating an access barrier to nodes which have requested for outside
networks. They will have their requirements accomplished. But this does not imply that
interaction is being channelized for other nodes also (Airi and Anderson, 2017). The node that
has made request will only have access to outside services. But certain security measures,
restrictions and control measures are being utilised.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In addition to this, access control measures are accountable for restricting devices so that
communication with other devices is not allowed. To understand this, example can be taken into
consideration, like HR department must not be given access to systems of finance as this will
lead to higher probability of internal attacks and there is possibility that data is altered which
may lead firm to lose their financial assets (Blair, Key and Wilson, 2019). Similarly employees
must be provided with an access to information related with operation they have to carry out
instead of entire network as probability of negative impact enhances in such kind of cases. The
access control lists must be regarded as top priority to have amplified results so that adequate
security measures can be derived. Access control will lead to mitigate risks by making use of
advanced filters as per destination of port number, destination of packet, protocol and various
other aspects. Along with this, it will be for DMZ which will further applied to firewall. It will
be restrictive and firewall will act like a shield for securing system or entire network. This will
also defend or protect internal network from certain threats.
In addition to this, firewall will block they the incoming and outgoing network.
Furthermore, encryption can be used while data is being transmitted by a network to make sure
that even in case if third person gets access to system then also they do not have access to system
(Del Prado and Rosellon, 2017). For this, it is necessary to make use of strong passwords so that
they cannot be decrypted easily and when multiple attempts will be made to decrypt it then
network administrator will come to know that some malicious activity is being carried on the
network. ABC firm need to make sure that there system and software are updated and for this
they can turn on auto update so that when any patch will be released it will be updated
automatically, The reason behind this is that new features that are brought in have better
functionalities or may be a solution to problems or attacks which occur in them. If it is not done
so then due to vulnerabilities within the system the risk of malicious activities amplifies.
VLAN
Virtual local area network implies logical group of devices that are being utilised within
identical broadcast domain. They are normally configured on switches by making use some kind
of interface within broadcast domain. The structured connection is being utilised within
designing for implementation of given scenario or network (Fuchs, 2016). This is practical as it
makes it probable for scaling up the network by making sure that time as well as money is being
saved. The different topologies are being utilised while formulating this, they are point to point,
6
communication with other devices is not allowed. To understand this, example can be taken into
consideration, like HR department must not be given access to systems of finance as this will
lead to higher probability of internal attacks and there is possibility that data is altered which
may lead firm to lose their financial assets (Blair, Key and Wilson, 2019). Similarly employees
must be provided with an access to information related with operation they have to carry out
instead of entire network as probability of negative impact enhances in such kind of cases. The
access control lists must be regarded as top priority to have amplified results so that adequate
security measures can be derived. Access control will lead to mitigate risks by making use of
advanced filters as per destination of port number, destination of packet, protocol and various
other aspects. Along with this, it will be for DMZ which will further applied to firewall. It will
be restrictive and firewall will act like a shield for securing system or entire network. This will
also defend or protect internal network from certain threats.
In addition to this, firewall will block they the incoming and outgoing network.
Furthermore, encryption can be used while data is being transmitted by a network to make sure
that even in case if third person gets access to system then also they do not have access to system
(Del Prado and Rosellon, 2017). For this, it is necessary to make use of strong passwords so that
they cannot be decrypted easily and when multiple attempts will be made to decrypt it then
network administrator will come to know that some malicious activity is being carried on the
network. ABC firm need to make sure that there system and software are updated and for this
they can turn on auto update so that when any patch will be released it will be updated
automatically, The reason behind this is that new features that are brought in have better
functionalities or may be a solution to problems or attacks which occur in them. If it is not done
so then due to vulnerabilities within the system the risk of malicious activities amplifies.
VLAN
Virtual local area network implies logical group of devices that are being utilised within
identical broadcast domain. They are normally configured on switches by making use some kind
of interface within broadcast domain. The structured connection is being utilised within
designing for implementation of given scenario or network (Fuchs, 2016). This is practical as it
makes it probable for scaling up the network by making sure that time as well as money is being
saved. The different topologies are being utilised while formulating this, they are point to point,
6
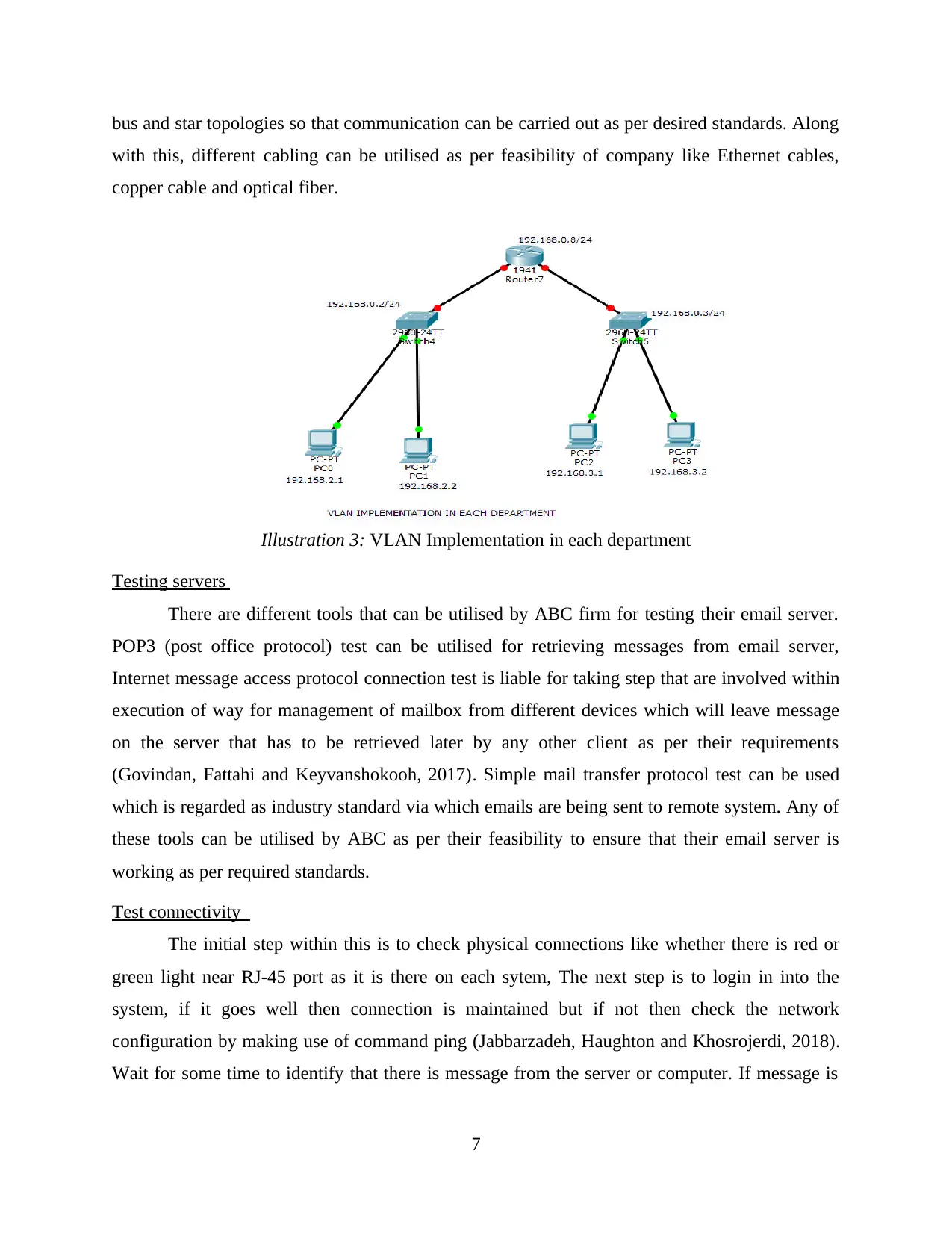
bus and star topologies so that communication can be carried out as per desired standards. Along
with this, different cabling can be utilised as per feasibility of company like Ethernet cables,
copper cable and optical fiber.
Illustration 3: VLAN Implementation in each department
Testing servers
There are different tools that can be utilised by ABC firm for testing their email server.
POP3 (post office protocol) test can be utilised for retrieving messages from email server,
Internet message access protocol connection test is liable for taking step that are involved within
execution of way for management of mailbox from different devices which will leave message
on the server that has to be retrieved later by any other client as per their requirements
(Govindan, Fattahi and Keyvanshokooh, 2017). Simple mail transfer protocol test can be used
which is regarded as industry standard via which emails are being sent to remote system. Any of
these tools can be utilised by ABC as per their feasibility to ensure that their email server is
working as per required standards.
Test connectivity
The initial step within this is to check physical connections like whether there is red or
green light near RJ-45 port as it is there on each sytem, The next step is to login in into the
system, if it goes well then connection is maintained but if not then check the network
configuration by making use of command ping (Jabbarzadeh, Haughton and Khosrojerdi, 2018).
Wait for some time to identify that there is message from the server or computer. If message is
7
with this, different cabling can be utilised as per feasibility of company like Ethernet cables,
copper cable and optical fiber.
Illustration 3: VLAN Implementation in each department
Testing servers
There are different tools that can be utilised by ABC firm for testing their email server.
POP3 (post office protocol) test can be utilised for retrieving messages from email server,
Internet message access protocol connection test is liable for taking step that are involved within
execution of way for management of mailbox from different devices which will leave message
on the server that has to be retrieved later by any other client as per their requirements
(Govindan, Fattahi and Keyvanshokooh, 2017). Simple mail transfer protocol test can be used
which is regarded as industry standard via which emails are being sent to remote system. Any of
these tools can be utilised by ABC as per their feasibility to ensure that their email server is
working as per required standards.
Test connectivity
The initial step within this is to check physical connections like whether there is red or
green light near RJ-45 port as it is there on each sytem, The next step is to login in into the
system, if it goes well then connection is maintained but if not then check the network
configuration by making use of command ping (Jabbarzadeh, Haughton and Khosrojerdi, 2018).
Wait for some time to identify that there is message from the server or computer. If message is
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

received then it implies that connection is proper and further activities can eb carried out as per
requirements.
Conclusion
From above, it can be concluded that, network design is an essential aspect for organisation
as it will lead to connect their systems and devices with one another through which transmission
of information will become easy. In addition to this, troubleshooting has to be ensured so that the
entire network can be protected from certain kind of attacks which will have enhanced impact on
ways in which functions are being conducted by them. This is essential the adequate strategies,
policies or procedures are being executed by them to attain higher levels of security.
8
requirements.
Conclusion
From above, it can be concluded that, network design is an essential aspect for organisation
as it will lead to connect their systems and devices with one another through which transmission
of information will become easy. In addition to this, troubleshooting has to be ensured so that the
entire network can be protected from certain kind of attacks which will have enhanced impact on
ways in which functions are being conducted by them. This is essential the adequate strategies,
policies or procedures are being executed by them to attain higher levels of security.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Books & Journals
Airi, P. and Anderson, P.K., 2017. Cisco Packet Tracer as a teaching and learning tool for
computer networks in DWU. Contemporary PNG Studies, 26, p.88.
Blair, A., Key, T.M. and Wilson, M., 2019. Crowdsourcing to manage service gaps in service
networks. Journal of Business & Industrial Marketing.
Del Prado, F.L. and Rosellon, M.A.D., 2017. Technology and knowledge transfers in production
networks: Case study on Philippine food manufacturing firms (No. 2017-08). PIDS
Discussion Paper Series.
Fuchs, B., 2016. Global field service network design: a simulation-based decision support
system for industrial SME's (Doctoral dissertation, ETH Zurich).
Govindan, K., Fattahi, M. and Keyvanshokooh, E., 2017. Supply chain network design under
uncertainty: A comprehensive review and future research directions. European Journal of
Operational Research, 263(1), pp.108-141.
Jabbarzadeh, A., Haughton, M. and Khosrojerdi, A., 2018. Closed-loop supply chain network
design under disruption risks: A robust approach with real world application. Computers
& Industrial Engineering, 116, pp.178-191.
Jain, V., Edgeworth, B. and Furr, R., 2018. Troubleshooting Cisco Nexus Switches and Nx-os.
Cisco Press.
Keyvanshokooh, E., Ryan, S.M. and Kabir, E., 2016. Hybrid robust and stochastic optimization
for closed-loop supply chain network design using accelerated Benders
decomposition. European Journal of Operational Research, 249(1), pp.76-92.
Liang, J.S., 2020. A process-based automotive troubleshooting service and knowledge
management system in collaborative environment. Robotics and Computer-Integrated
Manufacturing, 61, p.101836.
Rajabiyazdi, F., 2016. Design Concepts Towards Creating a Troubleshooting Knowledge
Management SystemDesignkoncept för att skapa problemlösande system för
kunskapsförvaltning.
Spithoven, A., Vlegels, J. and Ysebaert, W., 2019. Commercializing academic research: a social
network approach exploring the role of regions and distance. The Journal of Technology
Transfer, pp.1-36.
Yi, P. And et. al, 2016. A retailer oriented closed-loop supply chain network design for end of
life construction machinery remanufacturing. Journal of Cleaner Production, 124,
pp.191-203.
9
Books & Journals
Airi, P. and Anderson, P.K., 2017. Cisco Packet Tracer as a teaching and learning tool for
computer networks in DWU. Contemporary PNG Studies, 26, p.88.
Blair, A., Key, T.M. and Wilson, M., 2019. Crowdsourcing to manage service gaps in service
networks. Journal of Business & Industrial Marketing.
Del Prado, F.L. and Rosellon, M.A.D., 2017. Technology and knowledge transfers in production
networks: Case study on Philippine food manufacturing firms (No. 2017-08). PIDS
Discussion Paper Series.
Fuchs, B., 2016. Global field service network design: a simulation-based decision support
system for industrial SME's (Doctoral dissertation, ETH Zurich).
Govindan, K., Fattahi, M. and Keyvanshokooh, E., 2017. Supply chain network design under
uncertainty: A comprehensive review and future research directions. European Journal of
Operational Research, 263(1), pp.108-141.
Jabbarzadeh, A., Haughton, M. and Khosrojerdi, A., 2018. Closed-loop supply chain network
design under disruption risks: A robust approach with real world application. Computers
& Industrial Engineering, 116, pp.178-191.
Jain, V., Edgeworth, B. and Furr, R., 2018. Troubleshooting Cisco Nexus Switches and Nx-os.
Cisco Press.
Keyvanshokooh, E., Ryan, S.M. and Kabir, E., 2016. Hybrid robust and stochastic optimization
for closed-loop supply chain network design using accelerated Benders
decomposition. European Journal of Operational Research, 249(1), pp.76-92.
Liang, J.S., 2020. A process-based automotive troubleshooting service and knowledge
management system in collaborative environment. Robotics and Computer-Integrated
Manufacturing, 61, p.101836.
Rajabiyazdi, F., 2016. Design Concepts Towards Creating a Troubleshooting Knowledge
Management SystemDesignkoncept för att skapa problemlösande system för
kunskapsförvaltning.
Spithoven, A., Vlegels, J. and Ysebaert, W., 2019. Commercializing academic research: a social
network approach exploring the role of regions and distance. The Journal of Technology
Transfer, pp.1-36.
Yi, P. And et. al, 2016. A retailer oriented closed-loop supply chain network design for end of
life construction machinery remanufacturing. Journal of Cleaner Production, 124,
pp.191-203.
9

Appendix
Configure Router
<Router A> system-view
[Router A] interface loopback 1
[RouterA-LoopBack1] ip address 192.168.168. 11 21
[RouterA-LoopBack1] quit
[Router A] interface pos 0/0
[RouterA-Pos0/0] link-protocol hdlc
[RouterA-Pos0/0] ip address unnumbered interface loopback 1
[RouterA-Pos0/0] quit
Configure Switch
Switch>enable
Switch#
Switch#show running-config
Switch#show startup-config
Switch#show interface vlan1
Switch#show ip interface vlan1
Switch#show interface fastethernet 0/18
Switch#show vlan
Switch#dir flash
Switch#dir flash:c2960-lanbase-mz.122-25.SEE3
Switch#show startup-config
startup-config is not present
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname S1 S1(config)#exit
S1#
Switch#copy running-config startup-config
Destination filename [startup-config]? (enter)
Building configuration...
10
Configure Router
<Router A> system-view
[Router A] interface loopback 1
[RouterA-LoopBack1] ip address 192.168.168. 11 21
[RouterA-LoopBack1] quit
[Router A] interface pos 0/0
[RouterA-Pos0/0] link-protocol hdlc
[RouterA-Pos0/0] ip address unnumbered interface loopback 1
[RouterA-Pos0/0] quit
Configure Switch
Switch>enable
Switch#
Switch#show running-config
Switch#show startup-config
Switch#show interface vlan1
Switch#show ip interface vlan1
Switch#show interface fastethernet 0/18
Switch#show vlan
Switch#dir flash
Switch#dir flash:c2960-lanbase-mz.122-25.SEE3
Switch#show startup-config
startup-config is not present
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname S1 S1(config)#exit
S1#
Switch#copy running-config startup-config
Destination filename [startup-config]? (enter)
Building configuration...
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



