COIT20264 Network Design: A Presentation on Network Design Solution
VerifiedAdded on 2023/06/12
|19
|1171
|181
Presentation
AI Summary
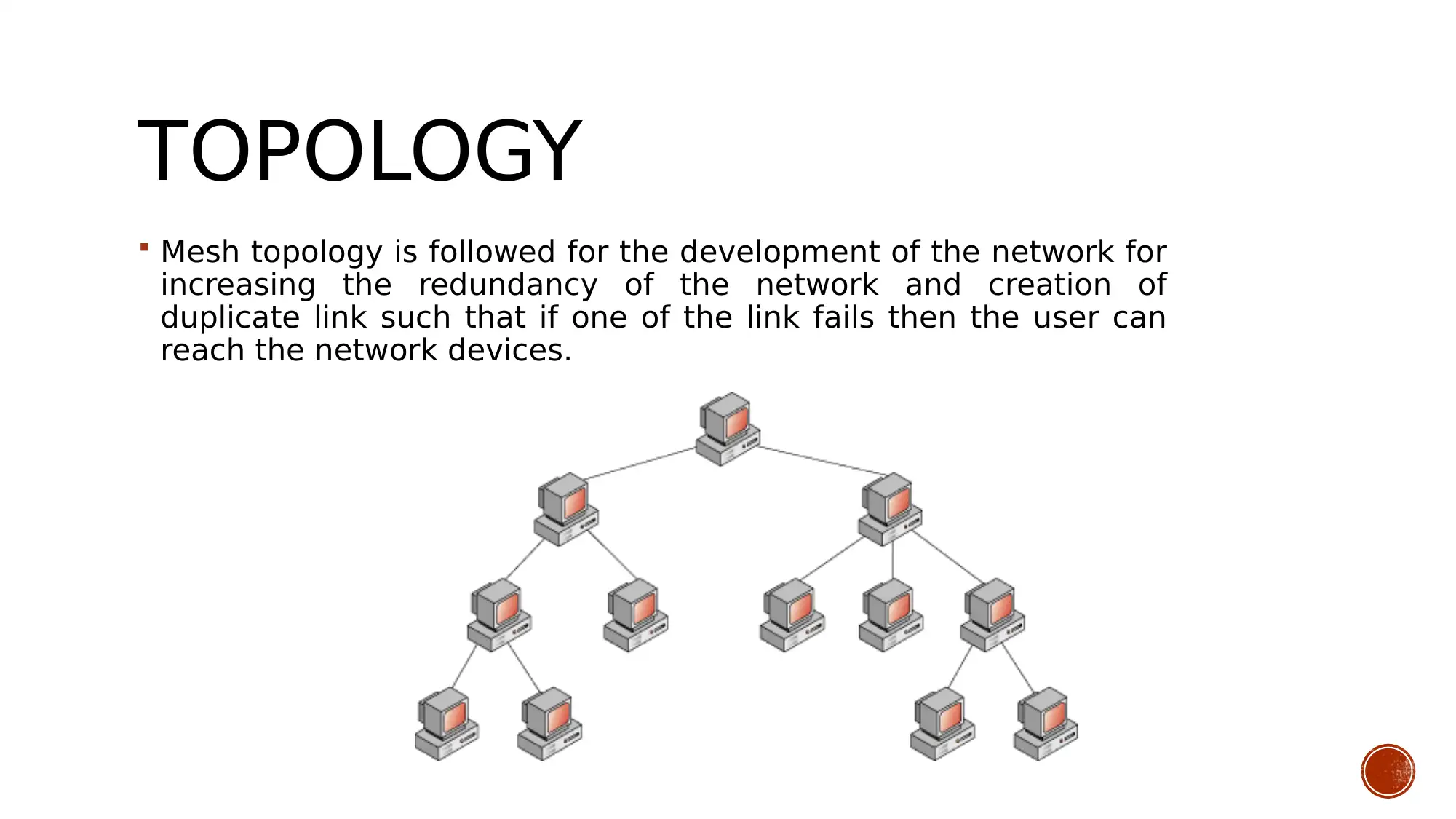
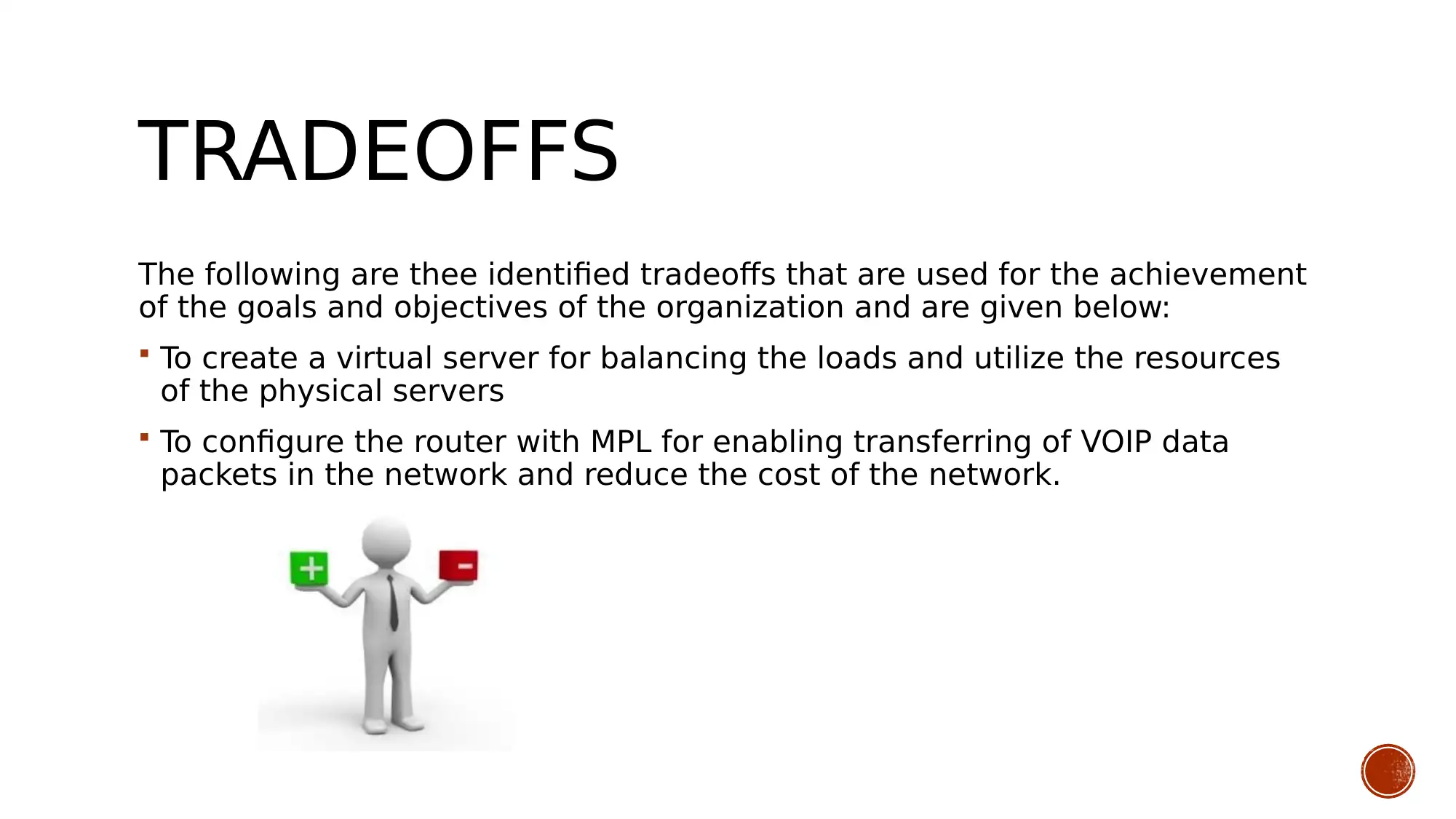
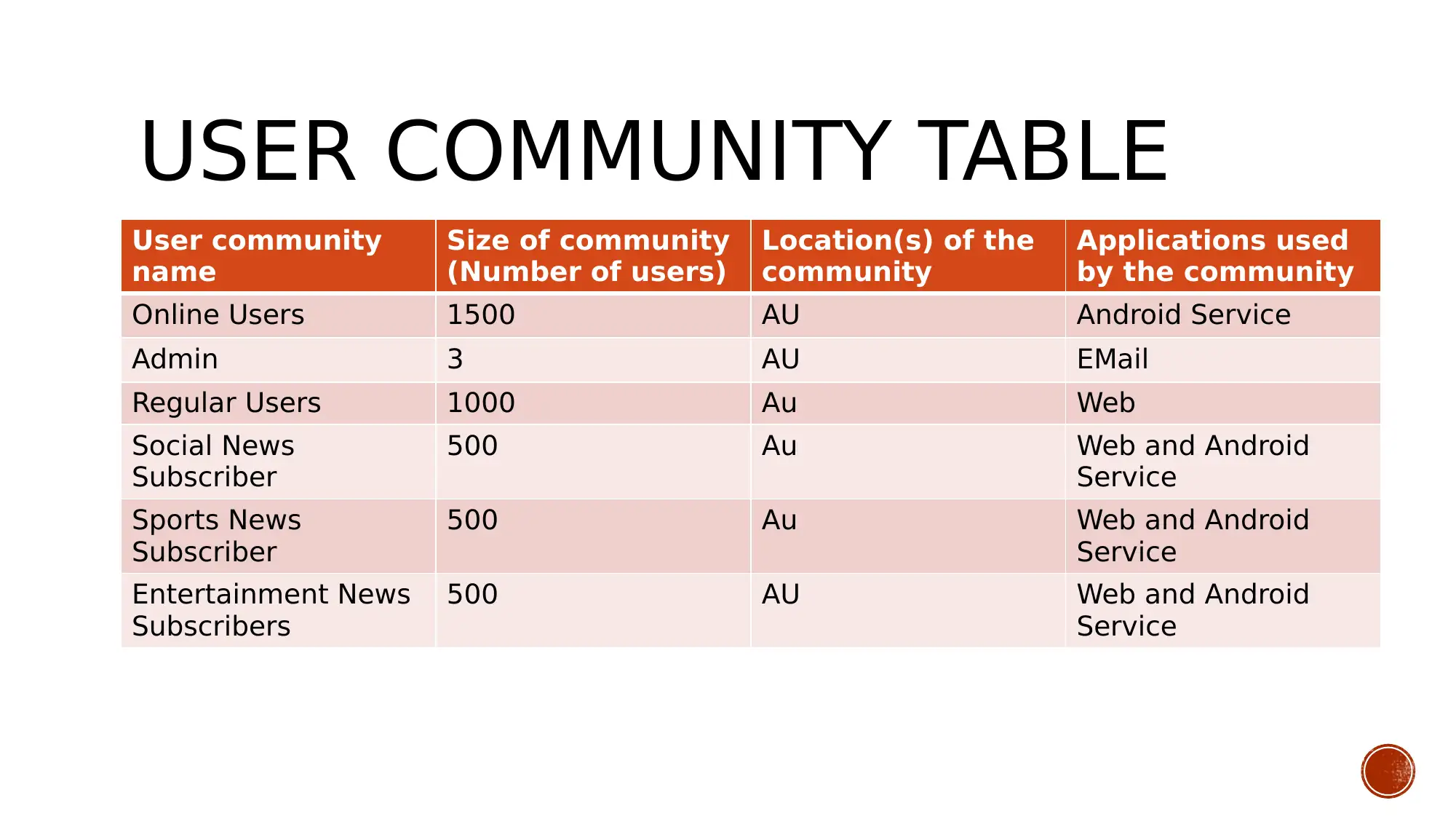
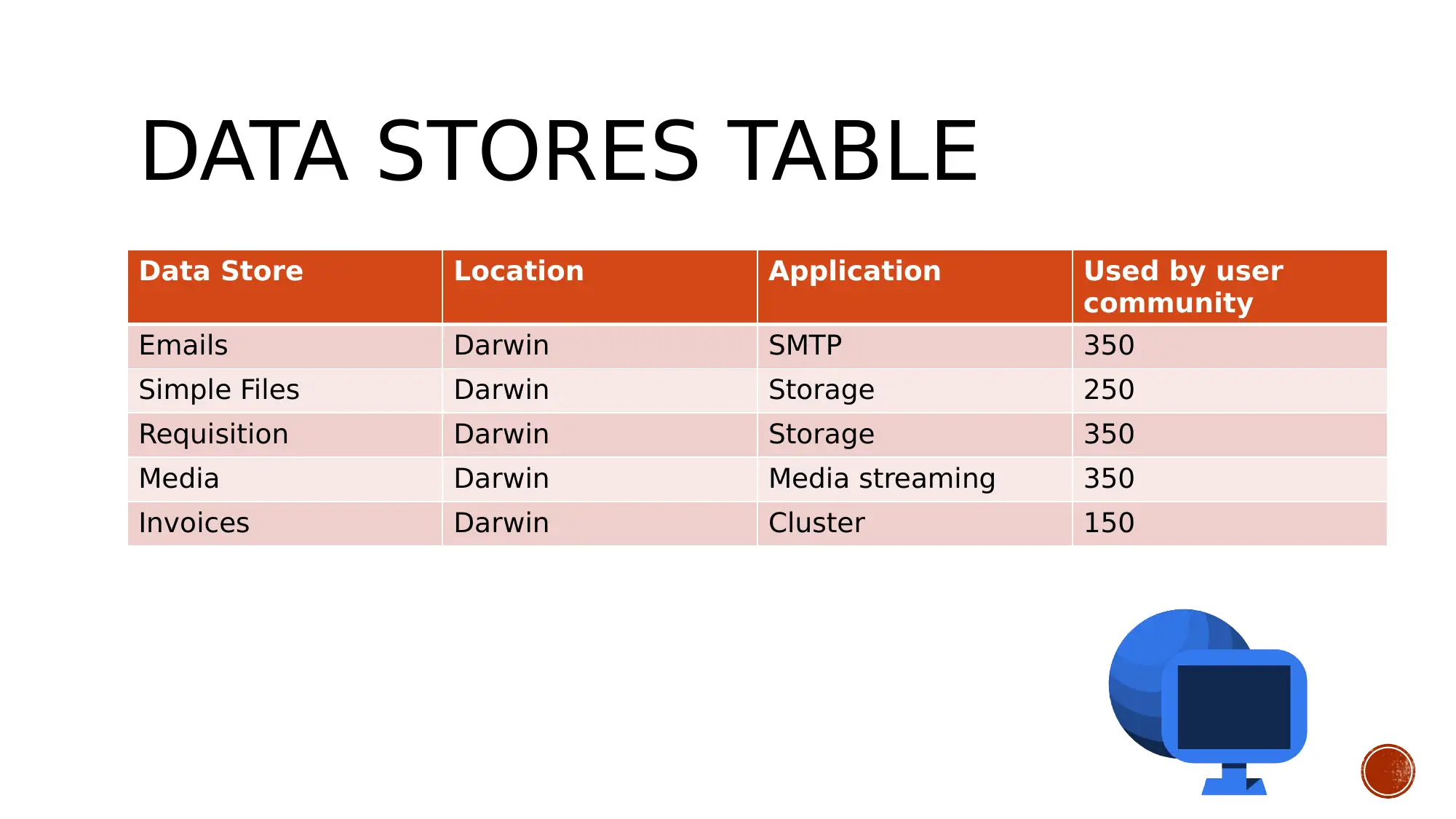
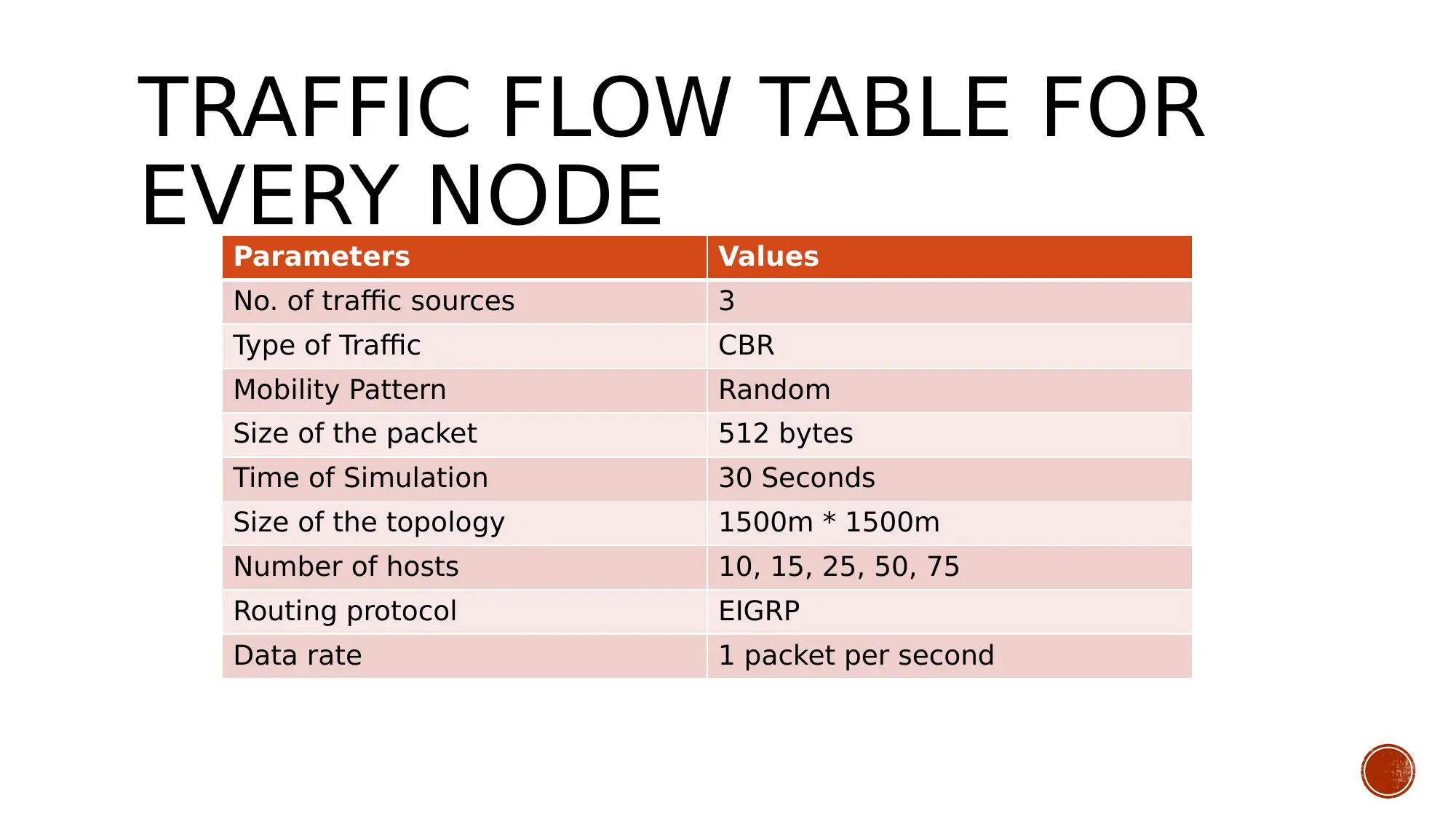
This presentation details a network solution designed for Cosmos Online newspapers, focusing on establishing secure remote connections for freelance reporters to upload files and information to the organization's data center. The solution outlines aims and objectives, including enabling remote file access, analyzing data flow, and connecting network devices using appropriate IP addressing and cabling. Business goals emphasize efficient resource utilization and real-time database updating, while technical goals involve configuring routers and switches with appropriate networking protocols and developing a user interface with secure authentication. Constraints include understanding user requirements and the technical skills of the network developers. The design employs a mesh topology for redundancy, and tradeoffs include virtual server creation for load balancing and MPLS configuration for VoIP data transfer. The presentation also includes tables detailing user communities, data stores, traffic flow, and network application characteristics, as well as logical network design and physical security measures. The conclusion emphasizes the importance of security and resource availability, with various precautions applied to protect the network and organizational data. Desklib offers additional resources, including past papers and solved assignments, to aid students in their studies.
1 out of 19







![[object Object]](/_next/static/media/star-bottom.7253800d.svg)