CSC00240 - Network Design for Advanced Medicos Ltd: A Detailed Report
VerifiedAdded on 2023/04/17
|10
|1794
|294
Report
AI Summary
This report outlines the network design for Advanced Medicos Limited (AML), addressing the requirements of both the existing and future network infrastructure. It details how the proposed network design meets AML's evolving needs, including scalability, enhanced communication, and robust security measures. The report includes an analysis of user requirements, a description of the current setup, and specifications for the proposed network, covering aspects such as wireless access, WAN connectivity, and security protocols using solutions like SOPHOS. The design incorporates a class B IP network and a 1000 MB/s bandwidth to support over 400 network components, ensuring optimal performance and addressing concerns related to the older network. Diagrams illustrating the proposed network layout are also provided.

Running head: NETWORK DESIGN FOR AML
Network Design for AML
Author
Dated
Network Design for AML
Author
Dated
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK DESIGN FOR AML
Executive Summary
The objective of this report is to summarize the requirement specifications for the
network of Advanced Medicos Limited which is expanding and wishes to reshape their
network structure. After summarizing the requirements, the study goes on to explain
why and how the proposed network layout meets all the future requirements of AML by
relating the different requirements with how they are achieved in the future network.
Then the full layout of the network is discussed along with roles of key components of
the network. It is concluded that the proposed network handily meets the future
requirements and successfully addresses all concerns.
Executive Summary
The objective of this report is to summarize the requirement specifications for the
network of Advanced Medicos Limited which is expanding and wishes to reshape their
network structure. After summarizing the requirements, the study goes on to explain
why and how the proposed network layout meets all the future requirements of AML by
relating the different requirements with how they are achieved in the future network.
Then the full layout of the network is discussed along with roles of key components of
the network. It is concluded that the proposed network handily meets the future
requirements and successfully addresses all concerns.

2NETWORK DESIGN FOR AML
Table of Contents
Introduction..............................................................................................................................3
Discussion.................................................................................................................................3
1. Requirements Summary..................................................................................................3
1.1 Requirement Specifications for Existing network...................................................3
1.2 Requirement Specifications for proposed network................................................3
2. Analysis of User Requirements..................................................................................4
2.1 Business goals:............................................................................................................4
2.2 Technical goals:..........................................................................................................4
2.3 How the proposed network meets future requirements........................................4
2.4 Current Network Requirements...............................................................................5
3. Description & Analysis of Current Setup........................................................................5
3.1 Security:.......................................................................................................................6
3.2 Wireless Networks:....................................................................................................6
3.3 Wide Area Network (WAN):......................................................................................6
Conclusion.................................................................................................................................6
References.................................................................................................................................7
Appendix A................................................................................................................................8
Network and System Diagrams...........................................................................................8
Proposed System..............................................................................................................8
Table of Contents
Introduction..............................................................................................................................3
Discussion.................................................................................................................................3
1. Requirements Summary..................................................................................................3
1.1 Requirement Specifications for Existing network...................................................3
1.2 Requirement Specifications for proposed network................................................3
2. Analysis of User Requirements..................................................................................4
2.1 Business goals:............................................................................................................4
2.2 Technical goals:..........................................................................................................4
2.3 How the proposed network meets future requirements........................................4
2.4 Current Network Requirements...............................................................................5
3. Description & Analysis of Current Setup........................................................................5
3.1 Security:.......................................................................................................................6
3.2 Wireless Networks:....................................................................................................6
3.3 Wide Area Network (WAN):......................................................................................6
Conclusion.................................................................................................................................6
References.................................................................................................................................7
Appendix A................................................................................................................................8
Network and System Diagrams...........................................................................................8
Proposed System..............................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3NETWORK DESIGN FOR AML
Introduction
The report summarizes the requirements of both the old and the new networks
for the company AML and explains how the new network design can cope with the
future requirements. The report starts by listing the requirement specifications for both
existing and future network layouts in tabular formats and mentions the differences.
Thereafter the study thoroughly explains how the future network goes about meeting
the future requirements of AML. In doing this the report briefly covers all the aspects of
the network and explains how the proposed network design is implemented and the
role of key components like WAN, wireless access points and security. The report then
ends with concluding notes.
Discussion
1. Requirements Summary
1.1 Requirement Specifications for Existing network
The headquarters of the company Advanced Medicos Limited (AML) is located in
two buildings that are adjacent to each other and three-story tall. There are four
departments within the network. For the existing network requirements of the
organization are as follows:
Branch Servers Workstations Printers Laptop
s
IP
Connections
Number
of floors
Headquarters
A
4 87 18 0 109 3
Headquarters
B
15 3 0 0 18 3
Branch
B – A 2
B – Branch
Total 125
1.2 Requirement Specifications for proposed network
The organization is expanding and there is a desire in the firm to reshape the
culture of the workplace based on future requirements.
Branch Servers Workstations Printers Laptop
s
IP
Connections
Number
of floors
Headquarters 4 155 20 65 244 3
Introduction
The report summarizes the requirements of both the old and the new networks
for the company AML and explains how the new network design can cope with the
future requirements. The report starts by listing the requirement specifications for both
existing and future network layouts in tabular formats and mentions the differences.
Thereafter the study thoroughly explains how the future network goes about meeting
the future requirements of AML. In doing this the report briefly covers all the aspects of
the network and explains how the proposed network design is implemented and the
role of key components like WAN, wireless access points and security. The report then
ends with concluding notes.
Discussion
1. Requirements Summary
1.1 Requirement Specifications for Existing network
The headquarters of the company Advanced Medicos Limited (AML) is located in
two buildings that are adjacent to each other and three-story tall. There are four
departments within the network. For the existing network requirements of the
organization are as follows:
Branch Servers Workstations Printers Laptop
s
IP
Connections
Number
of floors
Headquarters
A
4 87 18 0 109 3
Headquarters
B
15 3 0 0 18 3
Branch
B – A 2
B – Branch
Total 125
1.2 Requirement Specifications for proposed network
The organization is expanding and there is a desire in the firm to reshape the
culture of the workplace based on future requirements.
Branch Servers Workstations Printers Laptop
s
IP
Connections
Number
of floors
Headquarters 4 155 20 65 244 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK DESIGN FOR AML
A
Headquarters
B
15 5 0 0 20 3
Branch 3 31 5 28 67 3
B – A 2
B – Branch 2
Total 335
2. Analysis of User Requirements
2.1 Business goals:
The mode of communication is improved by enabling wireless access and introducing
video conversation and videoconferencing. A tight budget is allocated for the restructuring
the network based on requirements. Part of the requirements is to keep company information
secure. The company is to have more than 400 employees in future and wants to rely on
excellence in technology to accomplish this without heavy spending.
2.2 Technical goals:
The computer rooms must be upgraded for the new network and include facilities for
video conferencing and be accessible from campus to meet employees’ needs. The new
network should be scalable as the company is to double in size. Wireless network access must
be present to help employees remotely access the company’s network. Company resources
should be available to employees from office as well as homes. Performance of the network
must never hamper the work of members of the organization. No loopholes or areas of failure
should be present. Security of the network should be of paramount importance.
2.3 How the proposed network meets future requirements
The future network of AML provides services to over 400 employees These
services include access for additional workstations and printers, network access to the
issued as well as personal laptops for ‘bring your own device’ BYOD service (Song
2014). Therefore, the IP network to sustain the requirements is:
Major Network chosen: 128.160.0.0/22
IP addresses available in the network: 1022
IP addresses required: 335
Total IP addresses available from the different subnets: 414
The BYOD service is operated without sacrificing security by installing an
enterprise grade firewall solution to secure all the components of the network. The
company also wants to support online services. Previously the company conducted
network operations among two closely positioned buildings by means of a web portal
A
Headquarters
B
15 5 0 0 20 3
Branch 3 31 5 28 67 3
B – A 2
B – Branch 2
Total 335
2. Analysis of User Requirements
2.1 Business goals:
The mode of communication is improved by enabling wireless access and introducing
video conversation and videoconferencing. A tight budget is allocated for the restructuring
the network based on requirements. Part of the requirements is to keep company information
secure. The company is to have more than 400 employees in future and wants to rely on
excellence in technology to accomplish this without heavy spending.
2.2 Technical goals:
The computer rooms must be upgraded for the new network and include facilities for
video conferencing and be accessible from campus to meet employees’ needs. The new
network should be scalable as the company is to double in size. Wireless network access must
be present to help employees remotely access the company’s network. Company resources
should be available to employees from office as well as homes. Performance of the network
must never hamper the work of members of the organization. No loopholes or areas of failure
should be present. Security of the network should be of paramount importance.
2.3 How the proposed network meets future requirements
The future network of AML provides services to over 400 employees These
services include access for additional workstations and printers, network access to the
issued as well as personal laptops for ‘bring your own device’ BYOD service (Song
2014). Therefore, the IP network to sustain the requirements is:
Major Network chosen: 128.160.0.0/22
IP addresses available in the network: 1022
IP addresses required: 335
Total IP addresses available from the different subnets: 414
The BYOD service is operated without sacrificing security by installing an
enterprise grade firewall solution to secure all the components of the network. The
company also wants to support online services. Previously the company conducted
network operations among two closely positioned buildings by means of a web portal

5NETWORK DESIGN FOR AML
over the LAN of the headquarters. The new network design involves internally hosting
the company web portal that is accessible directly from internet.
2.4 Current Network Requirements
Communities of users: The three different communities of users for the network in
the order of priority are the administrators responsible for maintaining the network,
executive and managerial level members and the employees in general of different
departments.
Mobility Requirements: For ensuring mobility in work, the BYOD service is
introduced for all the laptops or MacBook Pros being used by the organizational
members.
Security Requirements: The entire network gets protected through enterprise grade
Firewall solutions -SOPHOS security installed in the headquarters of the company.
The firewall ensures security cover for all the network components like routers,
switches and office devices.
Bandwidth Requirements: The network of AML has been allocated class B type IP
address network which typically supports 1022 assignable IPs (Sari et al. 2017). The
maximum total network bandwidth is chosen to be 1000 MB/s.
Application Requirements: The applications that are mandatorily required for
installation are SOPHOS security, Nod32 antivirus, Skype and Cisco WebEx, Remote
Desktop, Microsoft Office 2016, Mozilla Firefox, MS Outlook, Windows 10 64bit OS,
Tally, Adobe Creative Cloud, inhouse applications and the company web portal.
Remote access requirements: Remote access is by means of using the default
Windows application called Remote Desktop to access other devices present in the
network (Billah, Porter and Ramakrishnan 2016). Only the administrator has
privileges to perform such tasks.
Performance Requirements: The network is well expected to meet the performance
criteria for the accumulated load of over 400 network components at any time.
Quality of Service (QoS): The networks for each floor of the offices of the company is
internally segmented and admins continuously exercise the Quality of Service (QoS)
technology to manage the data traffic in the network by setting priorities on the
various types of data.
3. Description & Analysis of Current Setup
The full network layout is drawn in Cisco Packet Tracer (refer to Figure 1). The
network of the headquarters of AML is ensured through two different LAN networks,
one for the offices and the other for the server farm. The web portal that were accessed
internal when both the buildings were connected through a single LAN network is being
hosted through internal web servers and is accessible directly from the internet which
employees and members of AML can use from anywhere and anytime (Leon, Parra and
Bermudez 2018). The wireless access points for the entire headquarters are located in
building A. The branch office building has their own wireless access points. Each of the
buildings A, B as also that of the branch are three-storied with each of the floors
over the LAN of the headquarters. The new network design involves internally hosting
the company web portal that is accessible directly from internet.
2.4 Current Network Requirements
Communities of users: The three different communities of users for the network in
the order of priority are the administrators responsible for maintaining the network,
executive and managerial level members and the employees in general of different
departments.
Mobility Requirements: For ensuring mobility in work, the BYOD service is
introduced for all the laptops or MacBook Pros being used by the organizational
members.
Security Requirements: The entire network gets protected through enterprise grade
Firewall solutions -SOPHOS security installed in the headquarters of the company.
The firewall ensures security cover for all the network components like routers,
switches and office devices.
Bandwidth Requirements: The network of AML has been allocated class B type IP
address network which typically supports 1022 assignable IPs (Sari et al. 2017). The
maximum total network bandwidth is chosen to be 1000 MB/s.
Application Requirements: The applications that are mandatorily required for
installation are SOPHOS security, Nod32 antivirus, Skype and Cisco WebEx, Remote
Desktop, Microsoft Office 2016, Mozilla Firefox, MS Outlook, Windows 10 64bit OS,
Tally, Adobe Creative Cloud, inhouse applications and the company web portal.
Remote access requirements: Remote access is by means of using the default
Windows application called Remote Desktop to access other devices present in the
network (Billah, Porter and Ramakrishnan 2016). Only the administrator has
privileges to perform such tasks.
Performance Requirements: The network is well expected to meet the performance
criteria for the accumulated load of over 400 network components at any time.
Quality of Service (QoS): The networks for each floor of the offices of the company is
internally segmented and admins continuously exercise the Quality of Service (QoS)
technology to manage the data traffic in the network by setting priorities on the
various types of data.
3. Description & Analysis of Current Setup
The full network layout is drawn in Cisco Packet Tracer (refer to Figure 1). The
network of the headquarters of AML is ensured through two different LAN networks,
one for the offices and the other for the server farm. The web portal that were accessed
internal when both the buildings were connected through a single LAN network is being
hosted through internal web servers and is accessible directly from the internet which
employees and members of AML can use from anywhere and anytime (Leon, Parra and
Bermudez 2018). The wireless access points for the entire headquarters are located in
building A. The branch office building has their own wireless access points. Each of the
buildings A, B as also that of the branch are three-storied with each of the floors
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK DESIGN FOR AML
containing at least one server to oversee the operations of the different departments
present. Building B acts as server farm and responsible for storing all the information,
running the websites, portals, facilitating communications through a host of database
servers, email servers, web servers and security servers.
3.1 Security:
The entire network and web services are secured primarily with the help of a
leading industry standard firewall solution from SOPHOS installed in the headquarters
of the company AML (Hils, Young and D'Hoinne 2015). The client nodes of the network
comprising PCs and laptops are further protected by corporate versions of multi-
layered security applications similar to solutions from ESET who excel in preventing
viruses and malware from compromising systems (Schuh 2013).
3.2 Wireless Networks:
The laptops are connected to the network with the help of the wireless access
points which enable mobility of work from inside or outside the office rooms (Schulz-
Zander et al. 2014).
3.3 Wide Area Network (WAN):
The headquarters and the branch office of the company AML is connected to the
same network with the help of a WAN. Wide Area Networks have round-trip delay of
30ms and peak download speed of 20 MB/s. (Schlechtendahl et al. 2017). The branch
office is 100km apart from the company headquarters.
Conclusion
In conclusion, the report clearly summarizes the requirements of both the
existing network as also the future network of Advanced Medicos Limited after which
explanation is given on how the proposed network can serve the future demands of the
organization. This is done by briefly describing every aspect of the proposed network
followed by description on the network layout and explanation on security, and
network components. It is observed that, most importantly the proposed network
design requires a class B major IP network, 1000 MB/s of bandwidth and an industry
standard firewall to meet the future requirements of AML and addresses all concerns
over the older network.
containing at least one server to oversee the operations of the different departments
present. Building B acts as server farm and responsible for storing all the information,
running the websites, portals, facilitating communications through a host of database
servers, email servers, web servers and security servers.
3.1 Security:
The entire network and web services are secured primarily with the help of a
leading industry standard firewall solution from SOPHOS installed in the headquarters
of the company AML (Hils, Young and D'Hoinne 2015). The client nodes of the network
comprising PCs and laptops are further protected by corporate versions of multi-
layered security applications similar to solutions from ESET who excel in preventing
viruses and malware from compromising systems (Schuh 2013).
3.2 Wireless Networks:
The laptops are connected to the network with the help of the wireless access
points which enable mobility of work from inside or outside the office rooms (Schulz-
Zander et al. 2014).
3.3 Wide Area Network (WAN):
The headquarters and the branch office of the company AML is connected to the
same network with the help of a WAN. Wide Area Networks have round-trip delay of
30ms and peak download speed of 20 MB/s. (Schlechtendahl et al. 2017). The branch
office is 100km apart from the company headquarters.
Conclusion
In conclusion, the report clearly summarizes the requirements of both the
existing network as also the future network of Advanced Medicos Limited after which
explanation is given on how the proposed network can serve the future demands of the
organization. This is done by briefly describing every aspect of the proposed network
followed by description on the network layout and explanation on security, and
network components. It is observed that, most importantly the proposed network
design requires a class B major IP network, 1000 MB/s of bandwidth and an industry
standard firewall to meet the future requirements of AML and addresses all concerns
over the older network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN FOR AML
References
Billah, S.M., Porter, D.E. and Ramakrishnan, I.V., 2016, April. Sinter: Low-bandwidth
remote access for the visually-impaired.
In Proceedings of the Eleventh European
Conference on Computer Systems (p. 27). ACM.
Hils, A., Young, G. and D'Hoinne, J., 2015. Magic Quadrant for Enterprise Network
Firewalls.
Gartner Inc, 22, p.30.
Leon, A.F.H., Parra, O.J.S. and Bermudez, G.M.T., 2018. LAN-WAN-LAN end-to-end
Network Simulation with NS2.
International Journal of Applied Engineering Research,
13(17), pp.13136-13140.
Sari, R.D., Supiyandi, A.P.U., Siahaan, M.M. and Ginting, R.B., 2017. A Review of IP and
MAC Address Filtering in Wireless Network Security.
Int. J. Sci. Res. Sci. Technol, 3(6),
pp.470-473.
Schlechtendahl, J., Kretschmer, F., Sang, Z., Lechler, A. and Xu, X., 2017. Extended study
of network capability for cloud based control systems.
Robotics and Computer-
Integrated Manufacturing,
43, pp.89-95.
Schuh, A., 2013. ESET: From a" Living-Room" Firm to a Global Player in the Antivirus
Software Industry.
Global Business, Mason: Southwestern Publishing, pp.582-585.
Schulz-Zander, J., Suresh, L., Sarrar, N., Feldmann, A., HuNhn, T. and Merz, R., 2014.
Programmatic orchestration of wifi networks.
In USENIX Annual Technical
Conference (pp. 347-358). USENIX Association.
Song, Y., 2014. “Bring Your Own Device (BYOD)” for seamless science inquiry in a
primary school.
Computers & Education, 74, pp.50-60.
References
Billah, S.M., Porter, D.E. and Ramakrishnan, I.V., 2016, April. Sinter: Low-bandwidth
remote access for the visually-impaired.
In Proceedings of the Eleventh European
Conference on Computer Systems (p. 27). ACM.
Hils, A., Young, G. and D'Hoinne, J., 2015. Magic Quadrant for Enterprise Network
Firewalls.
Gartner Inc, 22, p.30.
Leon, A.F.H., Parra, O.J.S. and Bermudez, G.M.T., 2018. LAN-WAN-LAN end-to-end
Network Simulation with NS2.
International Journal of Applied Engineering Research,
13(17), pp.13136-13140.
Sari, R.D., Supiyandi, A.P.U., Siahaan, M.M. and Ginting, R.B., 2017. A Review of IP and
MAC Address Filtering in Wireless Network Security.
Int. J. Sci. Res. Sci. Technol, 3(6),
pp.470-473.
Schlechtendahl, J., Kretschmer, F., Sang, Z., Lechler, A. and Xu, X., 2017. Extended study
of network capability for cloud based control systems.
Robotics and Computer-
Integrated Manufacturing,
43, pp.89-95.
Schuh, A., 2013. ESET: From a" Living-Room" Firm to a Global Player in the Antivirus
Software Industry.
Global Business, Mason: Southwestern Publishing, pp.582-585.
Schulz-Zander, J., Suresh, L., Sarrar, N., Feldmann, A., HuNhn, T. and Merz, R., 2014.
Programmatic orchestration of wifi networks.
In USENIX Annual Technical
Conference (pp. 347-358). USENIX Association.
Song, Y., 2014. “Bring Your Own Device (BYOD)” for seamless science inquiry in a
primary school.
Computers & Education, 74, pp.50-60.
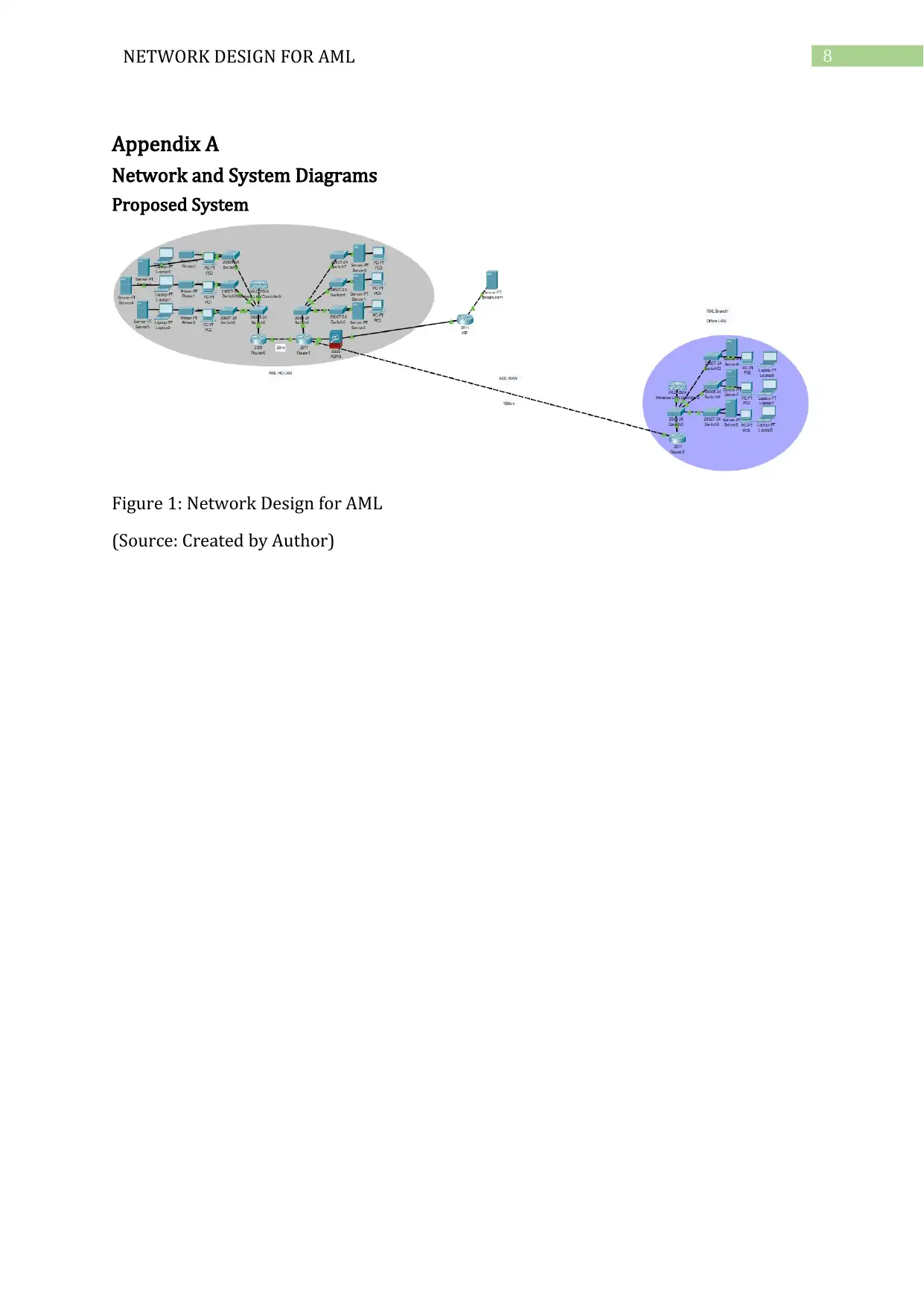
8NETWORK DESIGN FOR AML
Appendix A
Network and System Diagrams
Proposed System
Figure 1: Network Design for AML
(Source: Created by Author)
Appendix A
Network and System Diagrams
Proposed System
Figure 1: Network Design for AML
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK DESIGN FOR AML
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




