HND Project: Network Design for Small Business with VPN Solution
VerifiedAdded on 2023/04/20
|30
|9068
|373
Project
AI Summary
This project report details the network design for a small business with 400 employees across multiple locations, including London, Birmingham, and Manchester. The project aims to create a secure and efficient network infrastructure, addressing design requirements, network concepts, network technology, network operating systems, IP addressing, and security measures. The design incorporates a site-to-site VPN solution to connect the main office and branches, reducing communication costs and enhancing data transmission security. The report includes a Gantt chart for project scheduling, identifies potential risks and assumptions, and specifies hardware and software resources. Key network components such as Cisco routers and firewalls are selected to ensure reliability and security. The proposed network also supports wireless connectivity and VoIP, with considerations for QoS and VLAN configuration. The project emphasizes scalability to accommodate future growth and includes security protocols like SSH and measures to mitigate risks from viruses, hackers, and internal threats. This comprehensive network solution aims to meet the current and future needs of the small business while maintaining a secure and efficient communication infrastructure. Desklib provides access to similar solved assignments for students.

Running head: NETWORK DESIGN FOR SMALL BUSINESS
Network Design for Small Business
Name of the Student
Name of the University
Author’s Note
Network Design for Small Business
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK DESIGN FOR SMALL BUSINESS
Table of Contents
1. Introduction..................................................................................................................................2
1.1. Project Aim...........................................................................................................................2
1.2. Objectives.............................................................................................................................2
2. Brief description..........................................................................................................................3
2.1. Design requirements with diagram.......................................................................................4
2.2. Gantt Chart............................................................................................................................5
3. Special Condition.........................................................................................................................8
3.1. Assumption...........................................................................................................................8
3.2. Risk.......................................................................................................................................8
4. Resources.....................................................................................................................................9
4.1. Hardware Resources.............................................................................................................9
4.2. Software Resources..............................................................................................................9
5. Network Concept.........................................................................................................................9
6. Network technology...................................................................................................................11
7. Network Operating System........................................................................................................14
8. Internet Server Management......................................................................................................17
9. IP addresses...............................................................................................................................17
10. Security....................................................................................................................................21
11. Conclusion...............................................................................................................................24
Bibliography..................................................................................................................................25
NETWORK DESIGN FOR SMALL BUSINESS
Table of Contents
1. Introduction..................................................................................................................................2
1.1. Project Aim...........................................................................................................................2
1.2. Objectives.............................................................................................................................2
2. Brief description..........................................................................................................................3
2.1. Design requirements with diagram.......................................................................................4
2.2. Gantt Chart............................................................................................................................5
3. Special Condition.........................................................................................................................8
3.1. Assumption...........................................................................................................................8
3.2. Risk.......................................................................................................................................8
4. Resources.....................................................................................................................................9
4.1. Hardware Resources.............................................................................................................9
4.2. Software Resources..............................................................................................................9
5. Network Concept.........................................................................................................................9
6. Network technology...................................................................................................................11
7. Network Operating System........................................................................................................14
8. Internet Server Management......................................................................................................17
9. IP addresses...............................................................................................................................17
10. Security....................................................................................................................................21
11. Conclusion...............................................................................................................................24
Bibliography..................................................................................................................................25

2
NETWORK DESIGN FOR SMALL BUSINESS
1. Introduction
The paper mainly reflects on the network design for the small business that works with
400 staffs in different cities. The main office of the company is situated in London, Birmingham.
The main aim of the project is to design a network for the company. The paper provides
information regarding the design requirements of the project. The report also discusses the
network concept, network technology, network operating system, internet server management as
IP address related information. In addition to this, proper security related information is provided
in the report for keeping the network secure.
This specific report is prepared to design and develop a network for small business
organizations. In order to develop the network design the aims and objectives of the organization
is needed to be identified. A brief description of the network is given in the project specification
document and a diagram is created aligning the requirement of the organization. The project
schedule is created for organizing the development activity required while developing a project.
The potential risk and assumption that are identified for development of network solution is also
attached with the report for its elimination and increasing the network security.
1.1. Project Aim
The main of the company is to design a network for the company that has its main office
in London, Birmingham. The design network of the organization must include proper
information about design requirements, network concept, network technology, network operating
system, IP addresses as well as security with the help of proper diagram.
The main aim of the network is to connect the different branches of the organization and
enable secure transmission of data packets between the main office and branches to reduce the
communication cost and increase the efficiency of the business.
The network device installed in different location is needed to be connected with
redundant link such that if one of the link becomes down the other link can be used for reaching
the destination address.
1.2. Objectives
The main objectives of the development of network design solution is given below:
NETWORK DESIGN FOR SMALL BUSINESS
1. Introduction
The paper mainly reflects on the network design for the small business that works with
400 staffs in different cities. The main office of the company is situated in London, Birmingham.
The main aim of the project is to design a network for the company. The paper provides
information regarding the design requirements of the project. The report also discusses the
network concept, network technology, network operating system, internet server management as
IP address related information. In addition to this, proper security related information is provided
in the report for keeping the network secure.
This specific report is prepared to design and develop a network for small business
organizations. In order to develop the network design the aims and objectives of the organization
is needed to be identified. A brief description of the network is given in the project specification
document and a diagram is created aligning the requirement of the organization. The project
schedule is created for organizing the development activity required while developing a project.
The potential risk and assumption that are identified for development of network solution is also
attached with the report for its elimination and increasing the network security.
1.1. Project Aim
The main of the company is to design a network for the company that has its main office
in London, Birmingham. The design network of the organization must include proper
information about design requirements, network concept, network technology, network operating
system, IP addresses as well as security with the help of proper diagram.
The main aim of the network is to connect the different branches of the organization and
enable secure transmission of data packets between the main office and branches to reduce the
communication cost and increase the efficiency of the business.
The network device installed in different location is needed to be connected with
redundant link such that if one of the link becomes down the other link can be used for reaching
the destination address.
1.2. Objectives
The main objectives of the development of network design solution is given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK DESIGN FOR SMALL BUSINESS
To reduce the communication cost of the user connected in different geographical
location of the network.
To increase the availability and eradicate different risk of collision, lost packets and
jitters within the network.
To enable wireless connectivity for allowing the employees to connect their wireless
devices with the network
To secure the wireless connection such that it cannot be used by unauthorized users for
accessing the internal resources
To install the severs in secured area are restrict the users to physically access the server
such that the security is never compromised.
2. Brief description
The network is developed after understanding the specific requirement of the
organization and the success of the network depends on the selection of the technology and
topology. A research is made on the available technology that can be applied for connecting two
remote locations and enabling secure transmission of data between them. The network is also
designed such that it can support the intra office communication for enabling faster
communication than the traditional telephony networks. The routers are needed to be configured
with VoIP and it should be ensured that QoS is enabled in the network and the network is
reliable. The switch is needed to be configured with VLAN depending on the number of
departments of the organization and voice and data requirements. A firewall is also required to
be connected to both the entry and exit points of network such that the internal network of the
organization cannot be access by the intruders and the network is secured from the external
agents.
The network solution is developed by ensuring that it is secured and reliable to meet the
current and future needs of the organization. It is a scalable network design solution that can be
expanded with the growth of the organization. The application of VPN technology in the
network designed for the organization helps in increasing the security and maintain fast reliable
secure connection with the branch office. It can use the public lines and internet connection to
connect with the different location and eliminated the cost needed for maintaining leased lines.
The geographical connectivity cane be extended for allowing the remote employees to connect
NETWORK DESIGN FOR SMALL BUSINESS
To reduce the communication cost of the user connected in different geographical
location of the network.
To increase the availability and eradicate different risk of collision, lost packets and
jitters within the network.
To enable wireless connectivity for allowing the employees to connect their wireless
devices with the network
To secure the wireless connection such that it cannot be used by unauthorized users for
accessing the internal resources
To install the severs in secured area are restrict the users to physically access the server
such that the security is never compromised.
2. Brief description
The network is developed after understanding the specific requirement of the
organization and the success of the network depends on the selection of the technology and
topology. A research is made on the available technology that can be applied for connecting two
remote locations and enabling secure transmission of data between them. The network is also
designed such that it can support the intra office communication for enabling faster
communication than the traditional telephony networks. The routers are needed to be configured
with VoIP and it should be ensured that QoS is enabled in the network and the network is
reliable. The switch is needed to be configured with VLAN depending on the number of
departments of the organization and voice and data requirements. A firewall is also required to
be connected to both the entry and exit points of network such that the internal network of the
organization cannot be access by the intruders and the network is secured from the external
agents.
The network solution is developed by ensuring that it is secured and reliable to meet the
current and future needs of the organization. It is a scalable network design solution that can be
expanded with the growth of the organization. The application of VPN technology in the
network designed for the organization helps in increasing the security and maintain fast reliable
secure connection with the branch office. It can use the public lines and internet connection to
connect with the different location and eliminated the cost needed for maintaining leased lines.
The geographical connectivity cane be extended for allowing the remote employees to connect
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK DESIGN FOR SMALL BUSINESS
with the organizational network and maintain their global operations. The scalability of the
network improves and thus it helps the organization to increase the capacity of the network
without adding infrastructure in the current network solution. The long distance telephone
changes can also be reduced and remote connectivity and service can be configured for
increasing the efficiency of communication between the sites of the organization. The network is
configured such that it can establish a secure connection with its business partners and other
sites. For the establishment of VPN connection servers are required to design, deployed and
configure with different services. Here site to site VPN configuration is used for connecting the
remote sites and the protocols and configuration required for the development of the network is
identified before starting the development of the project. For the establishment of secure
connection with the remote site a VPN gateway is used for encapsulating the outbound traffic
and send it via the VPN tunnel. The site to site VPN is used since it can be extended in future for
connecting more than one branches and increase the scalability of the network solution.
2.1. Design requirements with diagram
The above network design is crated for a small business with three offices in three
different cities i.e. Main office in London, Birmingham and Manchester. There are 400 number
of users currently connected with the network from different areas and thus the site to site VPN
solution is proposed for the organization. The intranet VPN solution is proposed since it can help
NETWORK DESIGN FOR SMALL BUSINESS
with the organizational network and maintain their global operations. The scalability of the
network improves and thus it helps the organization to increase the capacity of the network
without adding infrastructure in the current network solution. The long distance telephone
changes can also be reduced and remote connectivity and service can be configured for
increasing the efficiency of communication between the sites of the organization. The network is
configured such that it can establish a secure connection with its business partners and other
sites. For the establishment of VPN connection servers are required to design, deployed and
configure with different services. Here site to site VPN configuration is used for connecting the
remote sites and the protocols and configuration required for the development of the network is
identified before starting the development of the project. For the establishment of secure
connection with the remote site a VPN gateway is used for encapsulating the outbound traffic
and send it via the VPN tunnel. The site to site VPN is used since it can be extended in future for
connecting more than one branches and increase the scalability of the network solution.
2.1. Design requirements with diagram
The above network design is crated for a small business with three offices in three
different cities i.e. Main office in London, Birmingham and Manchester. There are 400 number
of users currently connected with the network from different areas and thus the site to site VPN
solution is proposed for the organization. The intranet VPN solution is proposed since it can help
5
NETWORK DESIGN FOR SMALL BUSINESS
in delivering a cost effective network for the main offices when compared with connecting each
of the sites with traditional leased lines. The site to site VPN is proposed since it is suitable for
small office and enterprise sites and it can support the growth of the organization and connect
more number of branch office for enabling secured communication between the main office and
the branch office to advance the competence and performance of different business operations. In
case of the intranet VPN for the long distance communication ISP connections are used that
carries the data packets in encapsulated format such that it cannot be access by any third party
for gaining access of the sensitive information of the organization. A syslog server is used for
capturing the error log and troubleshooting the errors for increasing the efficiency of the network
solution. It also helps in management of the configuration and generating real time alerts for
increasing the network security. A NTP server is also deployed for synchronizing the clocks
between the computer system and it is essential for the long distance communication for
identification of latency in then network and synchronizing the network according to the daylight
saving time. For each of the department of the organization a SSH client is created such that it
can connect with the remote network for transferring files and information and gaining terminal
access. SSH protocol adds a layer of security for transferring files and for it there are different
software such as Putty, Win SCP, etc. that can be used for establishing a secure link with the
remote network.
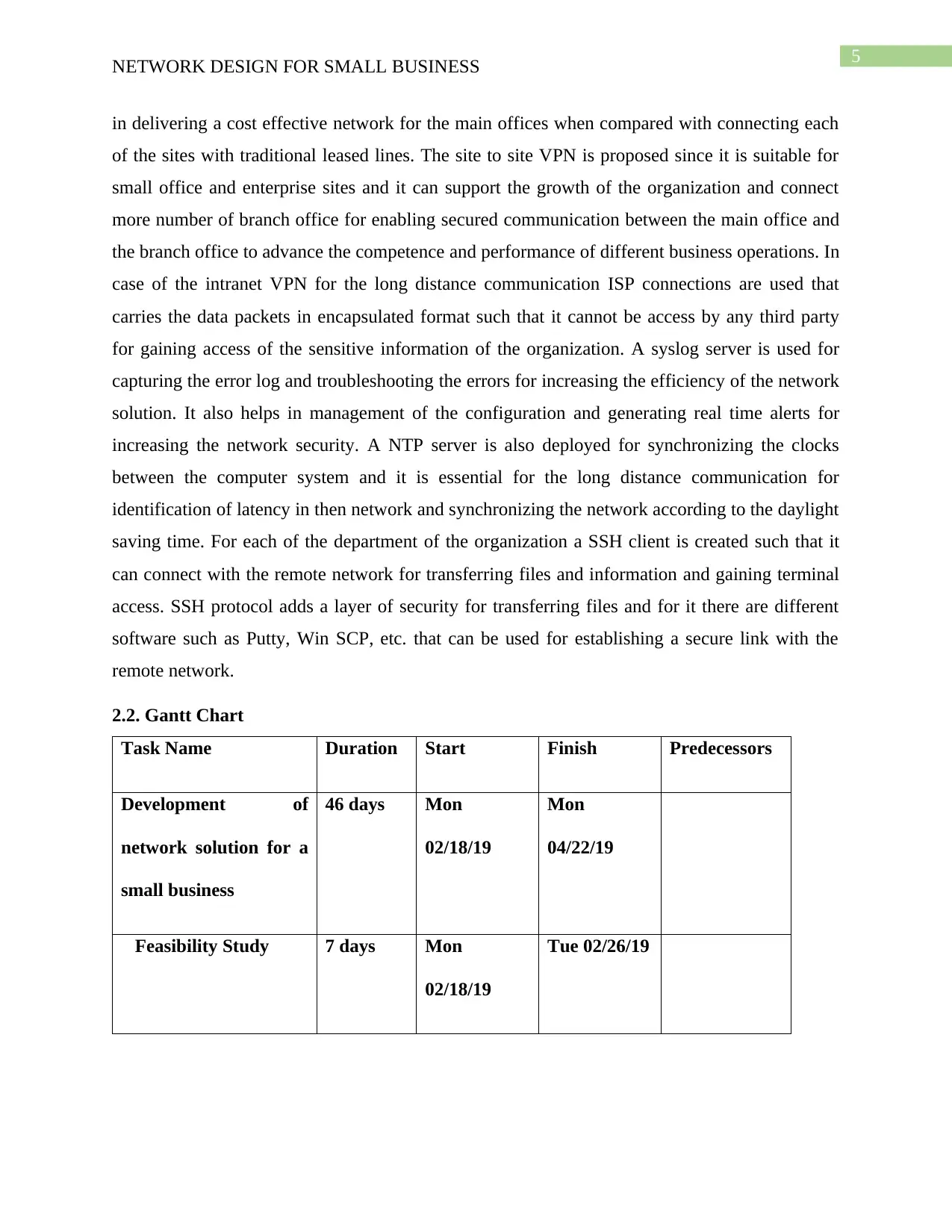
2.2. Gantt Chart
Task Name Duration Start Finish Predecessors
Development of
network solution for a
small business
46 days Mon
02/18/19
Mon
04/22/19
Feasibility Study 7 days Mon
02/18/19
Tue 02/26/19
NETWORK DESIGN FOR SMALL BUSINESS
in delivering a cost effective network for the main offices when compared with connecting each
of the sites with traditional leased lines. The site to site VPN is proposed since it is suitable for
small office and enterprise sites and it can support the growth of the organization and connect
more number of branch office for enabling secured communication between the main office and
the branch office to advance the competence and performance of different business operations. In
case of the intranet VPN for the long distance communication ISP connections are used that
carries the data packets in encapsulated format such that it cannot be access by any third party
for gaining access of the sensitive information of the organization. A syslog server is used for
capturing the error log and troubleshooting the errors for increasing the efficiency of the network
solution. It also helps in management of the configuration and generating real time alerts for
increasing the network security. A NTP server is also deployed for synchronizing the clocks
between the computer system and it is essential for the long distance communication for
identification of latency in then network and synchronizing the network according to the daylight
saving time. For each of the department of the organization a SSH client is created such that it
can connect with the remote network for transferring files and information and gaining terminal
access. SSH protocol adds a layer of security for transferring files and for it there are different
software such as Putty, Win SCP, etc. that can be used for establishing a secure link with the
remote network.
2.2. Gantt Chart
Task Name Duration Start Finish Predecessors
Development of
network solution for a
small business
46 days Mon
02/18/19
Mon
04/22/19
Feasibility Study 7 days Mon
02/18/19
Tue 02/26/19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK DESIGN FOR SMALL BUSINESS
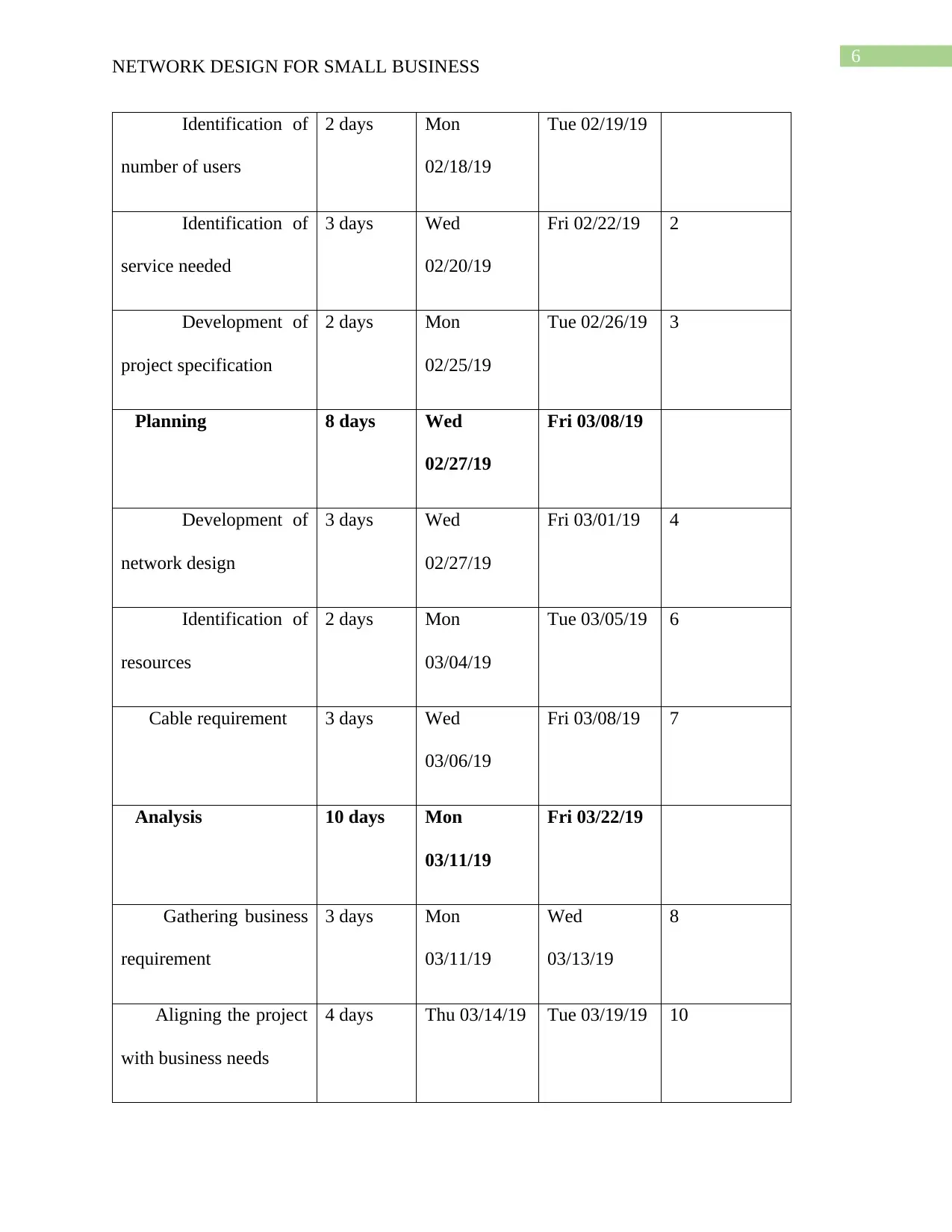
Identification of
number of users
2 days Mon
02/18/19
Tue 02/19/19
Identification of
service needed
3 days Wed
02/20/19
Fri 02/22/19 2
Development of
project specification
2 days Mon
02/25/19
Tue 02/26/19 3
Planning 8 days Wed
02/27/19
Fri 03/08/19
Development of
network design
3 days Wed
02/27/19
Fri 03/01/19 4
Identification of
resources
2 days Mon
03/04/19
Tue 03/05/19 6
Cable requirement 3 days Wed
03/06/19
Fri 03/08/19 7
Analysis 10 days Mon
03/11/19
Fri 03/22/19
Gathering business
requirement
3 days Mon
03/11/19
Wed
03/13/19
8
Aligning the project
with business needs
4 days Thu 03/14/19 Tue 03/19/19 10
NETWORK DESIGN FOR SMALL BUSINESS
Identification of
number of users
2 days Mon
02/18/19
Tue 02/19/19
Identification of
service needed
3 days Wed
02/20/19
Fri 02/22/19 2
Development of
project specification
2 days Mon
02/25/19
Tue 02/26/19 3
Planning 8 days Wed
02/27/19
Fri 03/08/19
Development of
network design
3 days Wed
02/27/19
Fri 03/01/19 4
Identification of
resources
2 days Mon
03/04/19
Tue 03/05/19 6
Cable requirement 3 days Wed
03/06/19
Fri 03/08/19 7
Analysis 10 days Mon
03/11/19
Fri 03/22/19
Gathering business
requirement
3 days Mon
03/11/19
Wed
03/13/19
8
Aligning the project
with business needs
4 days Thu 03/14/19 Tue 03/19/19 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK DESIGN FOR SMALL BUSINESS
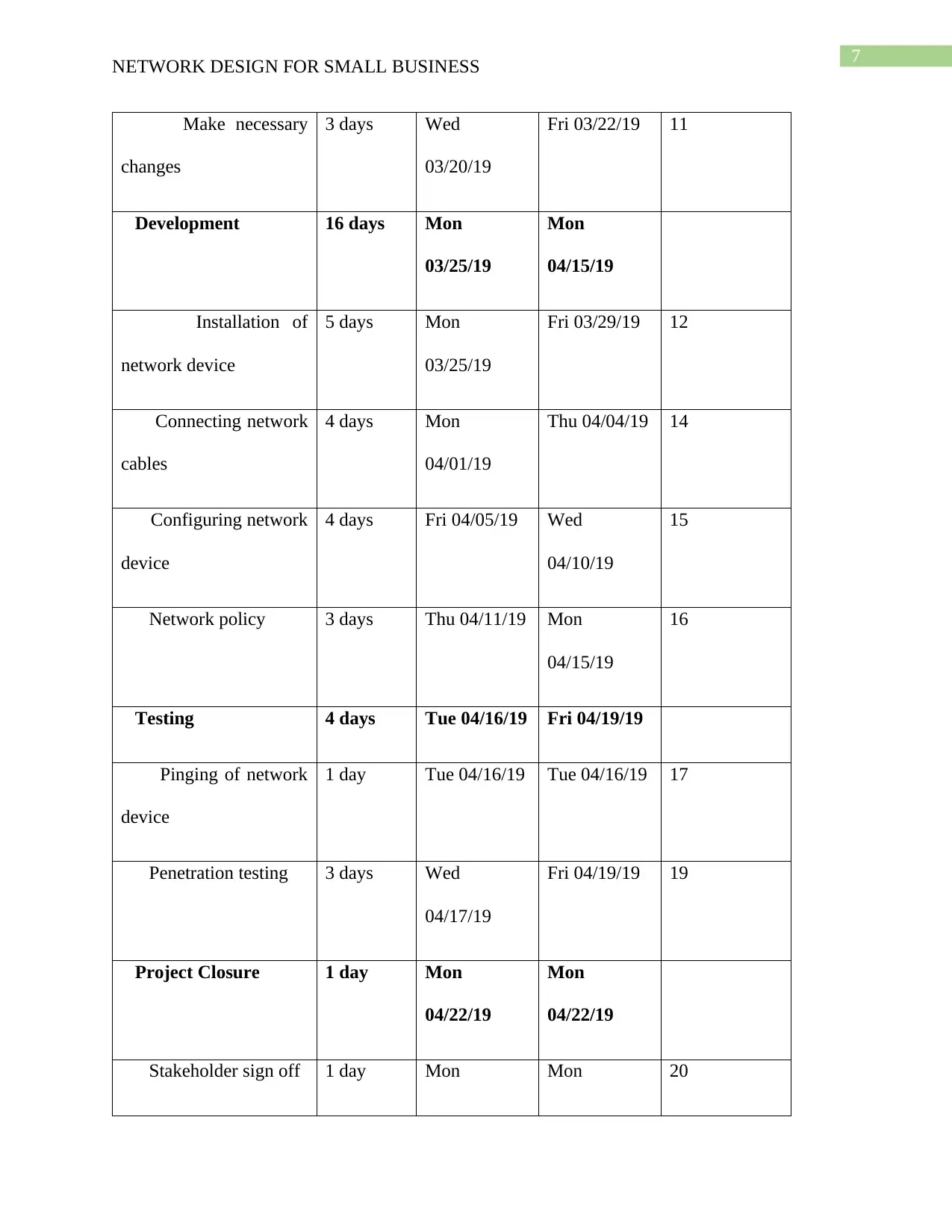
Make necessary
changes
3 days Wed
03/20/19
Fri 03/22/19 11
Development 16 days Mon
03/25/19
Mon
04/15/19
Installation of
network device
5 days Mon
03/25/19
Fri 03/29/19 12
Connecting network
cables
4 days Mon
04/01/19
Thu 04/04/19 14
Configuring network
device
4 days Fri 04/05/19 Wed
04/10/19
15
Network policy 3 days Thu 04/11/19 Mon
04/15/19
16
Testing 4 days Tue 04/16/19 Fri 04/19/19
Pinging of network
device
1 day Tue 04/16/19 Tue 04/16/19 17
Penetration testing 3 days Wed
04/17/19
Fri 04/19/19 19
Project Closure 1 day Mon
04/22/19
Mon
04/22/19
Stakeholder sign off 1 day Mon Mon 20
NETWORK DESIGN FOR SMALL BUSINESS
Make necessary
changes
3 days Wed
03/20/19
Fri 03/22/19 11
Development 16 days Mon
03/25/19
Mon
04/15/19
Installation of
network device
5 days Mon
03/25/19
Fri 03/29/19 12
Connecting network
cables
4 days Mon
04/01/19
Thu 04/04/19 14
Configuring network
device
4 days Fri 04/05/19 Wed
04/10/19
15
Network policy 3 days Thu 04/11/19 Mon
04/15/19
16
Testing 4 days Tue 04/16/19 Fri 04/19/19
Pinging of network
device
1 day Tue 04/16/19 Tue 04/16/19 17
Penetration testing 3 days Wed
04/17/19
Fri 04/19/19 19
Project Closure 1 day Mon
04/22/19
Mon
04/22/19
Stakeholder sign off 1 day Mon Mon 20

8
NETWORK DESIGN FOR SMALL BUSINESS
04/22/19 04/22/19
3. Special Condition
3.1. Assumption
For the development of the network solution the following assumptions are made:
100 mbps bandwidth would be efficient for the users connected in the network and met
the future needs of the organization.
The users would be able to use the current network efficiently without any errors and
hindrance
The software update of the firmware would be automatically applied to the operating
system of the network device for securing the network from external threats
The pcs would be installed with antivirus software for protecting the user from malware
and spyware and improve the security of the current network framework.
NETWORK DESIGN FOR SMALL BUSINESS
04/22/19 04/22/19
3. Special Condition
3.1. Assumption
For the development of the network solution the following assumptions are made:
100 mbps bandwidth would be efficient for the users connected in the network and met
the future needs of the organization.
The users would be able to use the current network efficiently without any errors and
hindrance
The software update of the firmware would be automatically applied to the operating
system of the network device for securing the network from external threats
The pcs would be installed with antivirus software for protecting the user from malware
and spyware and improve the security of the current network framework.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK DESIGN FOR SMALL BUSINESS
3.2. Risk
The following the network security risk identified prior of starting the development of the
network solution:
Computer Viruses – The instance of virus attack can pose a threat for the small
organization because it can delete or corrupt files that contains valuable information and impact
the daily operation of the business.
Software Vulnerability – The unsigned and outdated software can cause the computer
system to crash or slow down the entire network causing a major issue for the small business to
loss information.
Hackers – The hackers can break into the computer system for gaining access to the
privilege information, steal files and expose the secrets of the organization.
Internal Employees – Even the trustworthy employee can pose a security threat for the
network because they can unintentionally harm the system and leave the information of the
organization to a vulnerable position. The best practice should be shared with the employees and
the malicious websites should be blocked from the firewall for eliminating the risk.
4. Resources
4.1. Hardware Resources
The hardware resources those are essential for development of a proposed network solution for
different small business organization are given below:
Router - Cisco 1941 Series Router
Firewall - Cisco ASA 5505 firewall
Server - AAA Server, NTP Server, Sys Log Server
4.2. Software Resources
For establishing a secure connection with the remote terminal and enabling transfer of
files and information a VPN client software is necessary that would allow the user to establish a
secure connection and send and receive data packets through the tunnel securely. Some example
of VPN software is Putty, Win SCP, FileZilla, etc.
NETWORK DESIGN FOR SMALL BUSINESS
3.2. Risk
The following the network security risk identified prior of starting the development of the
network solution:
Computer Viruses – The instance of virus attack can pose a threat for the small
organization because it can delete or corrupt files that contains valuable information and impact
the daily operation of the business.
Software Vulnerability – The unsigned and outdated software can cause the computer
system to crash or slow down the entire network causing a major issue for the small business to
loss information.
Hackers – The hackers can break into the computer system for gaining access to the
privilege information, steal files and expose the secrets of the organization.
Internal Employees – Even the trustworthy employee can pose a security threat for the
network because they can unintentionally harm the system and leave the information of the
organization to a vulnerable position. The best practice should be shared with the employees and
the malicious websites should be blocked from the firewall for eliminating the risk.
4. Resources
4.1. Hardware Resources
The hardware resources those are essential for development of a proposed network solution for
different small business organization are given below:
Router - Cisco 1941 Series Router
Firewall - Cisco ASA 5505 firewall
Server - AAA Server, NTP Server, Sys Log Server
4.2. Software Resources
For establishing a secure connection with the remote terminal and enabling transfer of
files and information a VPN client software is necessary that would allow the user to establish a
secure connection and send and receive data packets through the tunnel securely. Some example
of VPN software is Putty, Win SCP, FileZilla, etc.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK DESIGN FOR SMALL BUSINESS
5. Network Concept
For the development of the network infrastructure for the small business a budget of the
network and the device obligatory for the development of a network solution is needed to be
identified. A design of the network is also needed to be created such that the reliability of the
network is increased and it can be used for allowing multiple users to communicate with
different users connected in the network. A router is deployed in the network for separating the
network and multiple switches are used for enabling interconnectivity between the network
devices and enabling communication between them. The local area network is designed with
network equipment such that it has support for VPN network infrastructure and establish a secure
connection with the remote site. The LAN is need to be designed by analysing the number of
members of the organization and twisted pair cables are used for connecting the host with the
switches and enabling communication between the hosts. The requirement for deployment of a
server and the service that is needed to be configured should be identified prior to the
development of the network. For enabling the user to communicate with email the server should
be configured with SMTP service and active directory should be configured such that the users
accessing the servers can be managed centrally.
A disaster recovery plan should also be created such that the redundancy of the network
is improved and a business continuity is improved. A plan is needed to be created such that it
covers all the devices and services and recover all the functionality and data in case of any
disaster such that business organisation can increase the reliability of the organization. The
support of the upper level management team is essential for the development of the disaster
recovery plan and the impact of the plan in the current business is also needed to be identified for
the management of critical functions and different operations on different sites. Each of the
employees in the organization an off site data backup and off site recovery plan should be
created. An alternative location should be selected for storing the backup location and remote
location should be used for storing the backup. A contingency plan should be created for
restoring the data and no data should be lost.
For increasing the reliability of the network framework investment should be made on
deployment of high quality routers and switches. The home networking equipment’s cannot
support the growth of the current business and it can be used for growing the network over time.
NETWORK DESIGN FOR SMALL BUSINESS
5. Network Concept
For the development of the network infrastructure for the small business a budget of the
network and the device obligatory for the development of a network solution is needed to be
identified. A design of the network is also needed to be created such that the reliability of the
network is increased and it can be used for allowing multiple users to communicate with
different users connected in the network. A router is deployed in the network for separating the
network and multiple switches are used for enabling interconnectivity between the network
devices and enabling communication between them. The local area network is designed with
network equipment such that it has support for VPN network infrastructure and establish a secure
connection with the remote site. The LAN is need to be designed by analysing the number of
members of the organization and twisted pair cables are used for connecting the host with the
switches and enabling communication between the hosts. The requirement for deployment of a
server and the service that is needed to be configured should be identified prior to the
development of the network. For enabling the user to communicate with email the server should
be configured with SMTP service and active directory should be configured such that the users
accessing the servers can be managed centrally.
A disaster recovery plan should also be created such that the redundancy of the network
is improved and a business continuity is improved. A plan is needed to be created such that it
covers all the devices and services and recover all the functionality and data in case of any
disaster such that business organisation can increase the reliability of the organization. The
support of the upper level management team is essential for the development of the disaster
recovery plan and the impact of the plan in the current business is also needed to be identified for
the management of critical functions and different operations on different sites. Each of the
employees in the organization an off site data backup and off site recovery plan should be
created. An alternative location should be selected for storing the backup location and remote
location should be used for storing the backup. A contingency plan should be created for
restoring the data and no data should be lost.
For increasing the reliability of the network framework investment should be made on
deployment of high quality routers and switches. The home networking equipment’s cannot
support the growth of the current business and it can be used for growing the network over time.

11
NETWORK DESIGN FOR SMALL BUSINESS
The use of high quality device helps in adding new features and functionality in the network and
the features include VoIP, wireless application and integrated messaging service. It should be
made sure that the routers and switches can be easily installed such as the switches having in line
power helps in placing equipment’s anywhere in the building location connecting it with wall
jack. It eliminated the need of installation of additional fitting and outlets for powering on the
network devices. It should be made sure that the network design is created for increasing
redundancy and reliability of the current framework for enabling business continuity and respond
against the unforeseen forecasts.
Here, client server framework is followed for designing the network framework and
connect each of the group in different location of the business organization. For the long distance
communication leased lines are avoided since it adds extra cost for communicating with the
remote branches and instead it is replaced with the VPN technology that would help in using the
public internet connection and encryption to securely transmit the data packets to the remote
location. Same type of topology is used for each of the branches such that the users are familiar
with the network of the remote location and does not face any difficulty while using the network
solution. The users are sub divided into groups according to their patter of usage and needs for
management of access of the resources and sharing of the resources with each other. The
different types of risks and security threats acting on the network framework is analysed for
increasing the network security and keep the sensitive information of the organization safe from
the external agents. Network policy is needed to be developed aligning the needs of the business
for the management of access of the users to different parts of the network. The implementation
of the network policy helps in configuring access control list on the router and manage the access
of the users. The network should be redundant such that the uptime of the network is maximum
and it can respond to the needs of the users at a real time. Intrusion prevention System should be
deployed in the network from increasing the resistance of the network and eliminate the risk of
distributed denial of service, SQL injection, Man in the middle or other types of attacks.
6. Network technology
The network technology that will generally be used for this entire network will be VPN.
Virtual Private Network (VPN) is defined as a technology that helps in improving the online
security as well as privacy. It is found that by using the entire commercial VPN service, it is
NETWORK DESIGN FOR SMALL BUSINESS
The use of high quality device helps in adding new features and functionality in the network and
the features include VoIP, wireless application and integrated messaging service. It should be
made sure that the routers and switches can be easily installed such as the switches having in line
power helps in placing equipment’s anywhere in the building location connecting it with wall
jack. It eliminated the need of installation of additional fitting and outlets for powering on the
network devices. It should be made sure that the network design is created for increasing
redundancy and reliability of the current framework for enabling business continuity and respond
against the unforeseen forecasts.
Here, client server framework is followed for designing the network framework and
connect each of the group in different location of the business organization. For the long distance
communication leased lines are avoided since it adds extra cost for communicating with the
remote branches and instead it is replaced with the VPN technology that would help in using the
public internet connection and encryption to securely transmit the data packets to the remote
location. Same type of topology is used for each of the branches such that the users are familiar
with the network of the remote location and does not face any difficulty while using the network
solution. The users are sub divided into groups according to their patter of usage and needs for
management of access of the resources and sharing of the resources with each other. The
different types of risks and security threats acting on the network framework is analysed for
increasing the network security and keep the sensitive information of the organization safe from
the external agents. Network policy is needed to be developed aligning the needs of the business
for the management of access of the users to different parts of the network. The implementation
of the network policy helps in configuring access control list on the router and manage the access
of the users. The network should be redundant such that the uptime of the network is maximum
and it can respond to the needs of the users at a real time. Intrusion prevention System should be
deployed in the network from increasing the resistance of the network and eliminate the risk of
distributed denial of service, SQL injection, Man in the middle or other types of attacks.
6. Network technology
The network technology that will generally be used for this entire network will be VPN.
Virtual Private Network (VPN) is defined as a technology that helps in improving the online
security as well as privacy. It is found that by using the entire commercial VPN service, it is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30