Network Design Case Study of LUCMAT LTD: Implementation and Testing
VerifiedAdded on 2022/11/25

Case Study of LUCMAT LTD
Student Name
Institution Affiliation
Paraphrase This Document

Table of Contents........................................................................................................................................2
List of Figures.............................................................................................................................................3
List of Tables...............................................................................................................................................3
Introduction.................................................................................................................................................4
Networking Principles & Protocols.............................................................................................................5
Topology.................................................................................................................................................5
Bus topology........................................................................................................................................6
Ring Topology.....................................................................................................................................6
Mesh Topology....................................................................................................................................7
Star Topology......................................................................................................................................7
Tree Topology.....................................................................................................................................8
Impact of Network Topology Communication and Bandwidth...............................................................8
Protocols................................................................................................................................................10
Internet Protocol................................................................................................................................10
Transmission Control Protocol (TCP)...............................................................................................10
Wireless Network Protocols..............................................................................................................10
OSI Model.........................................................................................................................................10
Selected Physical Network Topology....................................................................................................11
Networking Devices and Operations.........................................................................................................11
Hub........................................................................................................................................................11
Router....................................................................................................................................................12
Switch....................................................................................................................................................12
Network Interface Card.........................................................................................................................12
Gateway.................................................................................................................................................12
Server....................................................................................................................................................13
Design Efficient Networked Systems........................................................................................................16
Testing and Evaluation..........................................................................................................................18
Ping Test............................................................................................................................................22
Maintenance Schedule...........................................................................................................................23
Implement and diagnose networked systems.............................................................................................25
Implementation of the Network System................................................................................................25
Document and testing of the Second network Design............................................................................27

Critical Reflection.................................................................................................................................30
Conclusions...............................................................................................................................................30
List References..........................................................................................................................................32
List of Figures
Figure 1 LUCMAT NETWORK DESIGN...................................................................................16
Figure 2 Test for printer 2 HR in HR Department.........................................................................19
Figure 3 Test for PC5 Sales in Sales Department..........................................................................20
Figure 4 Test for Printer 5 Design in Design Department.............................................................20
Figure 5 File Server.......................................................................................................................21
Figure 6 Testing if the Devices communicate via messages.........................................................22
Figure 7 Pinging for PC0 in PC5 in sales department...................................................................23
Figure 8Pinging for File Server in PC11 in Design department....................................................24
List of Tables
Table 1 Maintenance Schedule Plan..............................................................................................25
Table 2 Improved Network Design with Wireless connections and Firewalls.............................27
Table 3 Wireless PC can see the LUCMAT LTD WIRELESS connections................................28
Table 4 Wireless messaging to other devices................................................................................29
Table 5 Pinging IP 192.168.10.5 and 192.168.10.9 on Wireless PC.............................................29
Table 6 Laptop and Tablet test that they communicate with all other devices..............................30
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking is a very broad area in any discussion. In any case, with regards to
networking is good for one to know if one is installing it from scratch or one is upgrading the
existing network. In this case of LUCMAT Ltd, the objective is to design and implement its
network infrastructure as an upgrade due to its requirements such as the increment of employees
and thus existing network need an upgrade to accommodate the additional members. The idea is
to extend the existing network. The company has about three departments namely HR, Design
and the Sales Departments respectively. The computers and printers have been shared as follows:
HR: 8 Printers and printers
Design: 35 Printers and Printers
Sales: 40 PCs and printers.
There are also three servers installed in the network to accommodate storage, domain and
email sending and receiving namely the web, DNS and Email server respectively. The company
has been using the private IP address 192.168.10.0/24 all through. In this case, there is need to do
the design and implement the system according to the new requirements given by the company
network administrator. The work will also ensure that the network has been assessed for any
malfunctions may it being in the routers or the switches to avoid future problems after the
expansion. The system design expected will help one in doing maintenance schedules, network
monitoring such as the use of the firewall and thus ensuring all the internet security software’s
such as anti-virus and VPNs are always updated.
Paraphrase This Document

Networking can be defined as the use of network devices to communicate, transmit and
share resources from one location to the other using the given work stations. Networking usually
consists of one or more than PCs which are connected or linked together to enable the sharing of
resources such as the printers, scanners and Compact disks, exchanging all the files and allowing
the communication to be done electronically such as the Emails among others (Gibson, Hardy
and Buckley, 2014). This PCs on the network are usually connected and linked to each other via
cables, telephone lines, satellites and radio waves among other medium channels depending on
the company ability and objectives.
In this case of LUCMAT Ltd, since all the departments are within one building, the
networking will be based on Local Area Network so that all the resources can be shared
efficiently. LAN is confined to be a network applied in small areas and is generally considered to
be limited for the geographic areas such as school, firm premises, computer lab among others
(Jain and Paul, 2013). The LAN is usually connected to a WAN in cases there is need for
expansion of the existing LAN in wider geographic areas. In the case where WAN is needed,
there will be need to use the dedicated transoceanic cables or the satellite uplinks which are
preferred for the connection with the global networks (Bergano, 2012).
Topology
In understanding this concept of LUCMAT Ltd network design and implementations, it is
wise for one to know the benefits and weaknesses of such topologies. Topology can be defines as
they network devices are set or arranged in the network set-up. The way the devices have been
set up will help one to know if the network can be easily flexible and scalable when need arises.
In this case of LUCMAT Ltd, there is need to understand more on the network scalability as it is

easy expansion in case there are future enhancements needed. There are five major types of
physical network topologies namely the bus, ring, star, mesh and tree topologies respectively.
The topologies have been discussed in details as explained below one by one.
Bus topology
In the bus topology all the nodes are connected in a manner that they form a series as if in
a linear path. They are usually applied in the cable broadband networks which are distributed.
Some of the advantages is that they are good for organization that need small networks. Another
merit is that they are easy to set up, handling and implementation is very much easy (Cavraro,
Arghandeh and Poolla, 2015). They are very cheap when it comes to installation unlike in other
topologies (Drutskoy, 2012). Although it has some merits, there are so many disadvantages that
make this topology not a good a choice.
One of the cons is that, it will not be easy for one to isolate all the faults in the given
network nodes. The cable length that is used for transmission is limited and thus limiting the
number of PCs connected to it. It is dependent on the central bus and this can lead to a serious
failure to the entire network.
Ring Topology
The ring network topology is where the PCs or nodes are usually connected as if in a loop
configuration. In this case, the rings are assumed to be passing in the one direction while the
others which can also transmit in both directions. The including or evacuating of system hubs is
simple and the traffic is unidirectional and the information transmission is rapid. Data is
transmitted between the existing nodes will pass via the central (Wang, 2014). A focal server
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

handling the loads.
Some of the disadvantages of this ring topology are such as the transmission speed drops
with an expansion in terms of hub number. The failure of a central hub in the framework can
make the entire network to break down. Any changes made to the center hub may have
devastating impact to the whole network in terms of presentation. There is overpowering
dependence on the wire interfacing the framework PCs in the ring topology.
Mesh Topology
This is a topology that links all the existing nodes or PCs or any other networking devices
with connections so that there is availability of multiple between two or more points (Vega,
2012). In this topology, the network will be said to be entirely fully meshed if all the nodes or
PCs are connected directly to all other nodes. This topology can be able to handle very heavy
traffic as there exists dedicated paths between the two PCs. Failure of one single PC will not
break the entire network communication as there exists several alternate paths.Some of the
Demerits of using this topology are such as a lot of cabling being needed and therefore, the costs
realized in setup and upkeep are high.
Star Topology
This is a topology where the network usually have a central node that has direct
connection to all the other PCs. This central node can be realised as the managed switch or
Managed hub. This is the type of topology that will be applied in this case study (Pandya, 2013).
This topology has the following merits; as the examination of traffic is basic, the topology
presents lesser security shot. The expansion or clearing framework center points is basic, and
should be conceivable without affecting the entire framework. Because of its concentrated
Paraphrase This Document

contraption in the framework. In a perfect world, because of the brought together nature, it is
definitely not hard to perceive faults in the framework contraptions.
One of the demerits of this topology is that the network activity depends on the central
hub which acts as the managed switch. Consequently, the central hub, usually may fail the whole
system. In setting up such a network physical topology may be very costly.
Tree Topology
This topology is where the network star topologies are connected in the star
configuration. Shortcoming ID is simple. The upsides of centralization that are cultivated in a
star topology are obtained by the individual star pieces in a tree arrange (Xie and Wang, 2014.
The tree topology is significant in circumstances where a star or bus can't be realized
autonomously. It is most-fit in frameworks organization various divisions of a school or
organization, where each unit (star segment) works autonomously, and is in like manner related
with the guideline center point (root center point) (Mets, 2014).One of the disadvantage of using
this topology is that it is attributable to its size and multifaceted nature, upkeep isn't simple and
expenses are high.
Impact of Network Topology Communication and Bandwidth
The network topology will matter as it impacts the different contexts of the network
itself, or there are other factors which are important in implementing in the design of the
network. In this case of LUCMAT Ltd, the selected topology is the star topology as it will
impacts the performance. The company has to consider the following factor before they setup the
design. It impacts execution – both of the projects utilized or got to through the system, either to
the speed of the system itself. The other factor is in deciding the media type used to link the

yet for a low traffic you can utilize a telephone connection (Dong, El-Gorashi and Elmirghani,
2012). It also impacts the expenses of cabling the system and the gadgets required all together
for the system to run appropriately – the expense related with a fast system (fiber-optic links and
related gadgets) are higher than that of a low speed one, who can be cabled for instance without
the utilization of a switch or server; one has also have to consider how it impacts the system
adaptability, for instance, the quantity of system hubs in a transport topology is restricted, while
in a star topology there are no requirements on the versatility, you simply need to change the
arrangement of the focal center point.
In guidance to the network there must exists some different protocols which will help the
network work within the recommended standards and thus improving the communication of the
network entirely (Zhang, 2012). Network Protocol is as a rule that describes the rules and shows
for correspondence between framework devices. Such conventions join segments for devices to
perceive and make relationship with each other, similarly as the organizing decides that chooses
by demonstrating how data is packaged into messages sent and got. There are somewhere in the
range of couple of conventions that similarly support message certification and data pressure
planned for strong just as world class framework correspondence.
Protocols
Internet Protocol
The family of Internet Protocol (IP) contains a gathering of associated (and among the
chief wide utilized) protocols of networking. More elevated protocol such as the TCP, UDP,
HTTP, and FTP all incorporate with the Internet Protocol (IP) itself, to give extra capacities. =
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This is used hand in hand with the internet protocol which are considered to be the two
distinct computer network protocols. They are applied together as TCP/IP as they have the
standard terminology in terms of the protocol suites (Davidson, 2012). TCP/IP in this case
usually applies the network communications in which the TCP transport is utilized to convey
information crosswise over IP systems.
Wireless Network Protocols
These are such protocols used to in the wireless environments and thus they have become
common and much popular in the current era (Petite, 2016). Most of these network protocols
uses the wireless network which indeed supports the mobile devices and solving the problems
such as the data rates of the variables and the security of the network.
OSI Model
This is a seven-layered methodology general worldview for examining or depicting how
PCs communicate with one another over a system (Bora, Singh and Arsalan, 2014). This way to
deal with information transmission isolates the different activities up into a particular
arrangement of activities on each layer. The OSI model was initially framed as a standard plan
for structure arrange frameworks thus, a few across the board organize advancements today
reflect the layered style of OSI.
Selected Physical Network Topology.
In this case of LUCMAT Ltd, the best topology that will meet all the required
specifications and needs is the star topology. However, the cost is very high, there is use of the
scalable high capacity managed switch. Another reason for its selection is that, it can handle
traffic loads at high speeds and also there is less security vulnerabilities and risks (Zhang, 2013).
Paraphrase This Document

maintenances as the scalability is exceptional.
Networking Devices and Operations
In this case, the idea is to give an explanation of the networking devices that will be
applied in the LUCMAT Ltd network design. There are many networking devices depending on
their functionalities and in this concept they have been applied widely as the network has
majored much on flexibility, security, performance and much more security. In this case, these
means a hierarchical diagram will need to be put in place so that this network design will be
successful. Some of the applied network devices are routers, switches, hub, NIC among others
as explained below with all their respective operations.
Hub
This is a devices that is usually applied for connecting the PCs in a single Local Area
Network. It usually used to send data signals to all the ports except on the one which the signal
has just arrived from so that it does not have to interfere with the signal.
Router
A router is a layer three gadget which sends information parcels starting with one system
portion then onto the next dependent on their destination address. So as to do this, the switch
tracks the way that parcels can utilize when they move over that arrange. Those records are kept
in a database table called a routing table.
Switch
Information signals are designed in edges on layer two, and when a switch gets a casing,
it checks the Frame Checksum Sequence (FCS) field in it, and procedure the casing just on the
legitimate edges are handled and sent to their destination MAC address.
Network Interface Card.
It executes the electronic hardware expected to convey utilizing a particular convention,
for example, for Ethernet or Wi-Fi. One personal computer can be able to communicate with
different workstations, essentially through changing over the information transmission
innovation.
Gateway.
Gateway is utilized to advance the parcels from the neighborhood system to the planned
remote system. The passage gadget has the default entryway address and knows the way of
remote destination address. On the off chance that the bundles don't discover the goal address on
the nearby system, at that point the door will discover the goal address in the remote system.
Server
There exists different type of servers depending on the operation it achieve on the given
network scenario. In this case, some of the servers have been explained with their operations
respectively.
Server Operations
File Usually stores the files and data of the
user in the network
Print Control and manages all the printer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
the printing of the documents
Communication This one handles all types of
communications operation over the network,
it facilitates access in the remote areas,
firewalls email and the internet services.
Application This is used for sharing the network-
based version of the used software and thus it
helps to eliminate the need for to install the
software on computer connected in the
network.
Database oversees the arrangement of the
databases, taking care of the information
stockpiling, the database management and
Specific query with regards to specific
information
Domain This verifies and approves singular
workstations (or clients) to get to explicit
assets inside the system
Programming, applications or notwithstanding working frameworks, for our situation
organizing conventions and designs, are centered around supporting equipment highlights,
organizing gadgets. That is the reason the kinds of assignments that most conventions do are
Paraphrase This Document

other, along these lines the significance of interdependency between the terminal equipment and
the applicable softwares.In structuring a system, aside from the gadgets themselves, a significant
job descends on the links interfacing those gadgets. In view of the vital transfer speed,
association velocities and why not, spending plan, we could utilize coaxial, copper links
(UTP/STP) or fiber optic. Obviously, the decision of link will influence also the decision of the
systems administration gadget, some of them way more costly than the others, that is the reason a
decent system configuration will represent future adaptability in physical framework, just as
spending concerns.
In this case of LUCMAT ltd it will use about 4 servers which are the web, DNS and
Email server with an additions of a file server to help for general storage. The web Server will be
facilitating all the communication using HTTP over and across the internet. The Email server
will be acting as virtual post office where it can just stores all the incoming mail so that they can
be distributed to their destinations who are the local users. The DNS will be used to implement
the Domain Name System Protocol and offering provisions of domain name of resolution
services to the web hosts and the clients on an Internet Protocol-based network. The file server is
used as a storage for data which can be accessed by any local user everywhere as far as you are
connected on the local network or even in cases when one is connected from outside the
government
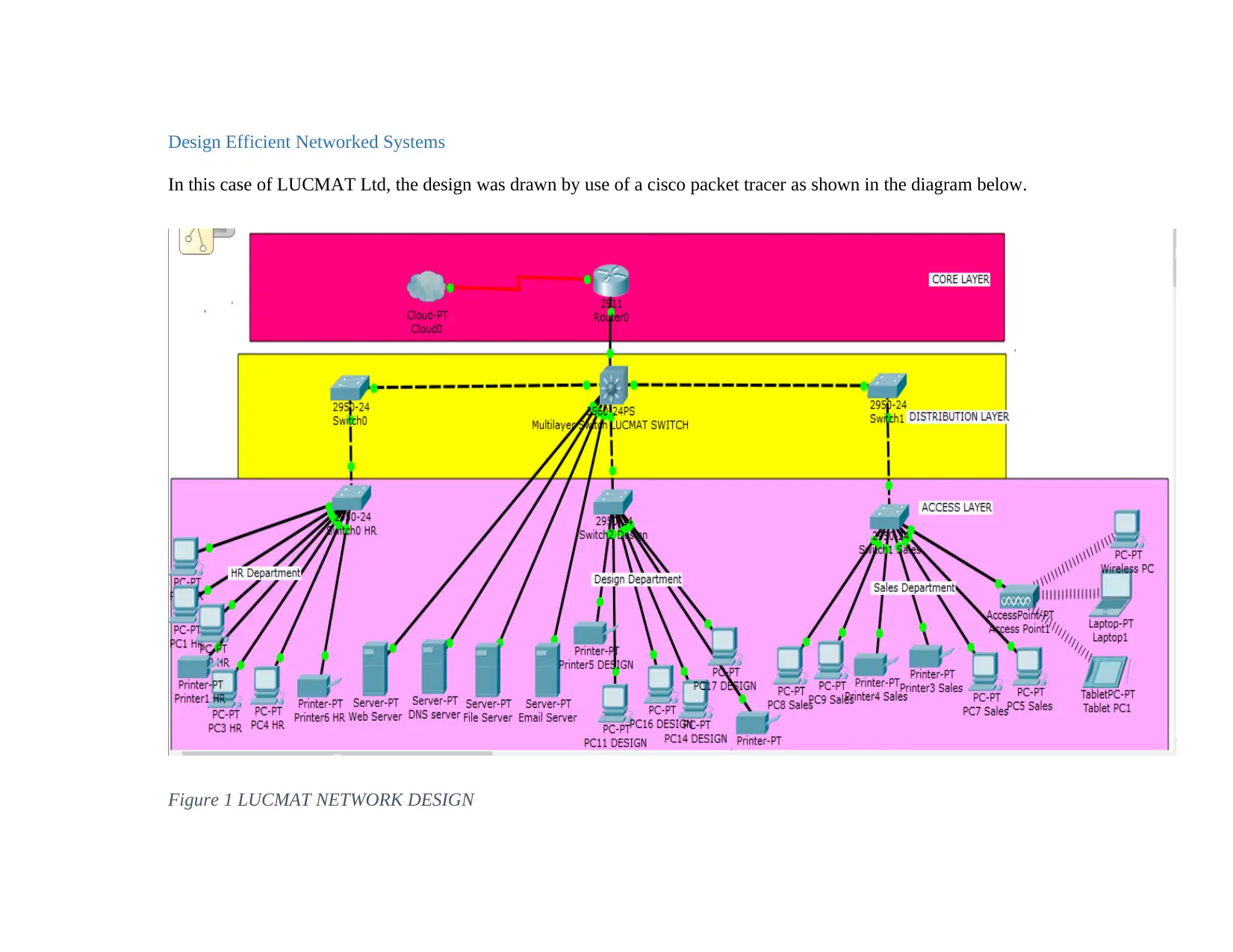
In this case of LUCMAT Ltd, the design was drawn by use of a cisco packet tracer as shown in the diagram below.
Figure 1 LUCMAT NETWORK DESIGN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

which is managed by a hub at center. In this case, this is just a prototype of the expected design
of the network. On the diagram, it is clear that all the devices cannot communicate effectively as
the circle signals blinking are indicating green.
This color green is clearly showing that all the end users devices are transmitting
successfully and thus communicating properly with each other via the connecting cables. The
other concepts is that the servers were also installed where they were manually allocated their IP
addresses statically. In this case, there was need to use a DHCP server which will automatically
assign all the devices connected to the network. In this case the next set up is testing if the
networking is working properly which will be done by checking if the IPs were allocated
appropriately on the network as well as the default and the DNS server Internet Protocols.
Paraphrase This Document
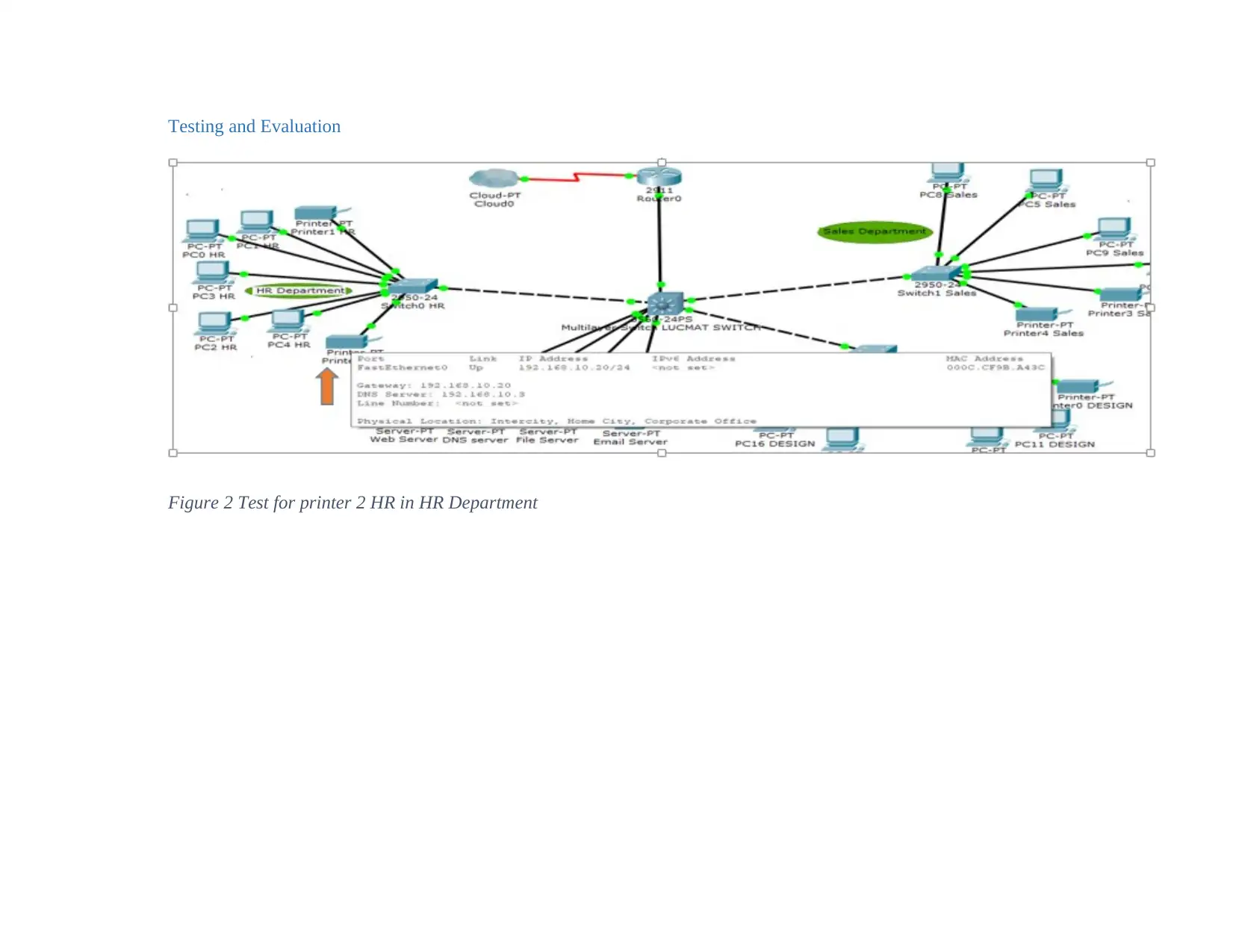
Figure 2 Test for printer 2 HR in HR Department
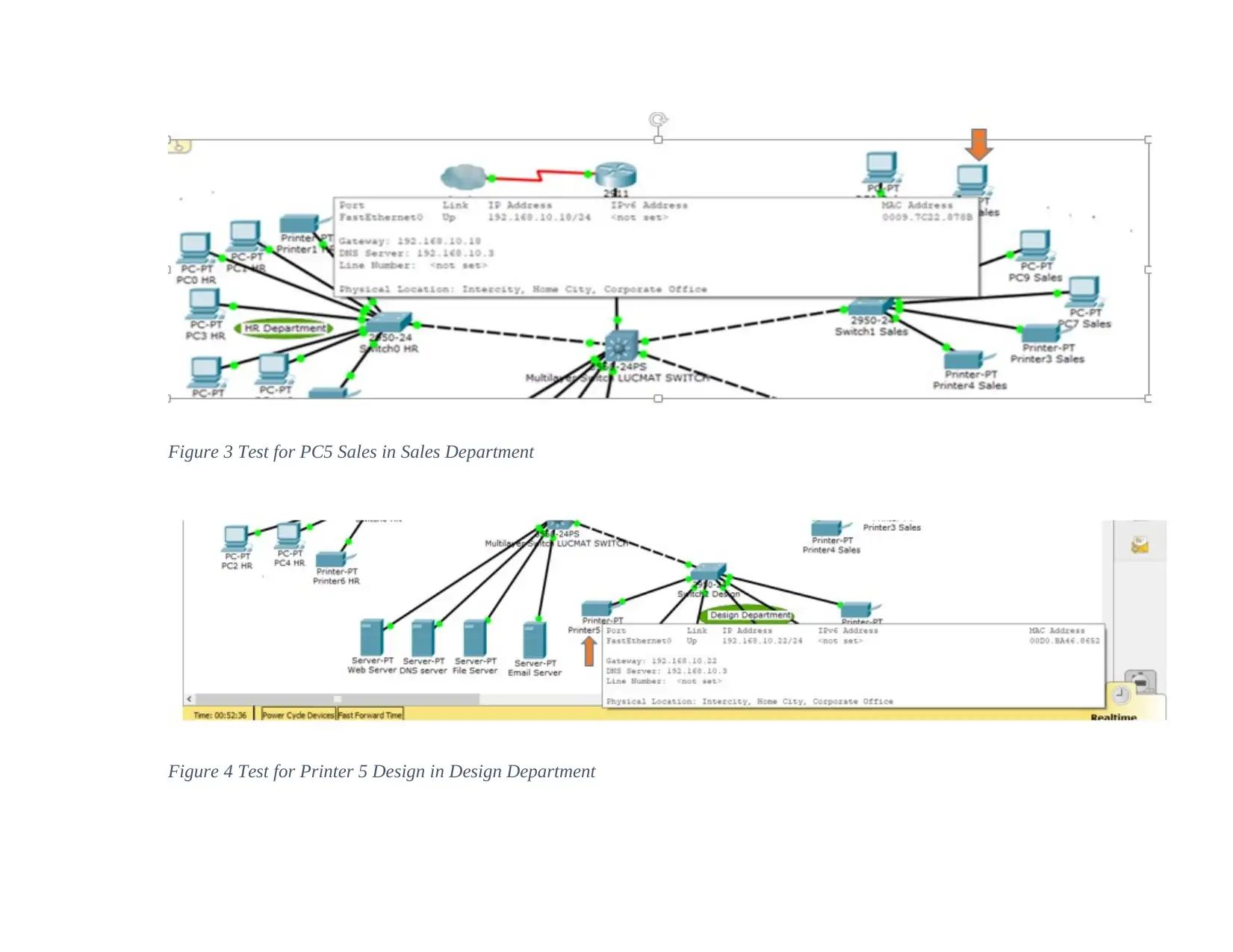
Figure 4 Test for Printer 5 Design in Design Department
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
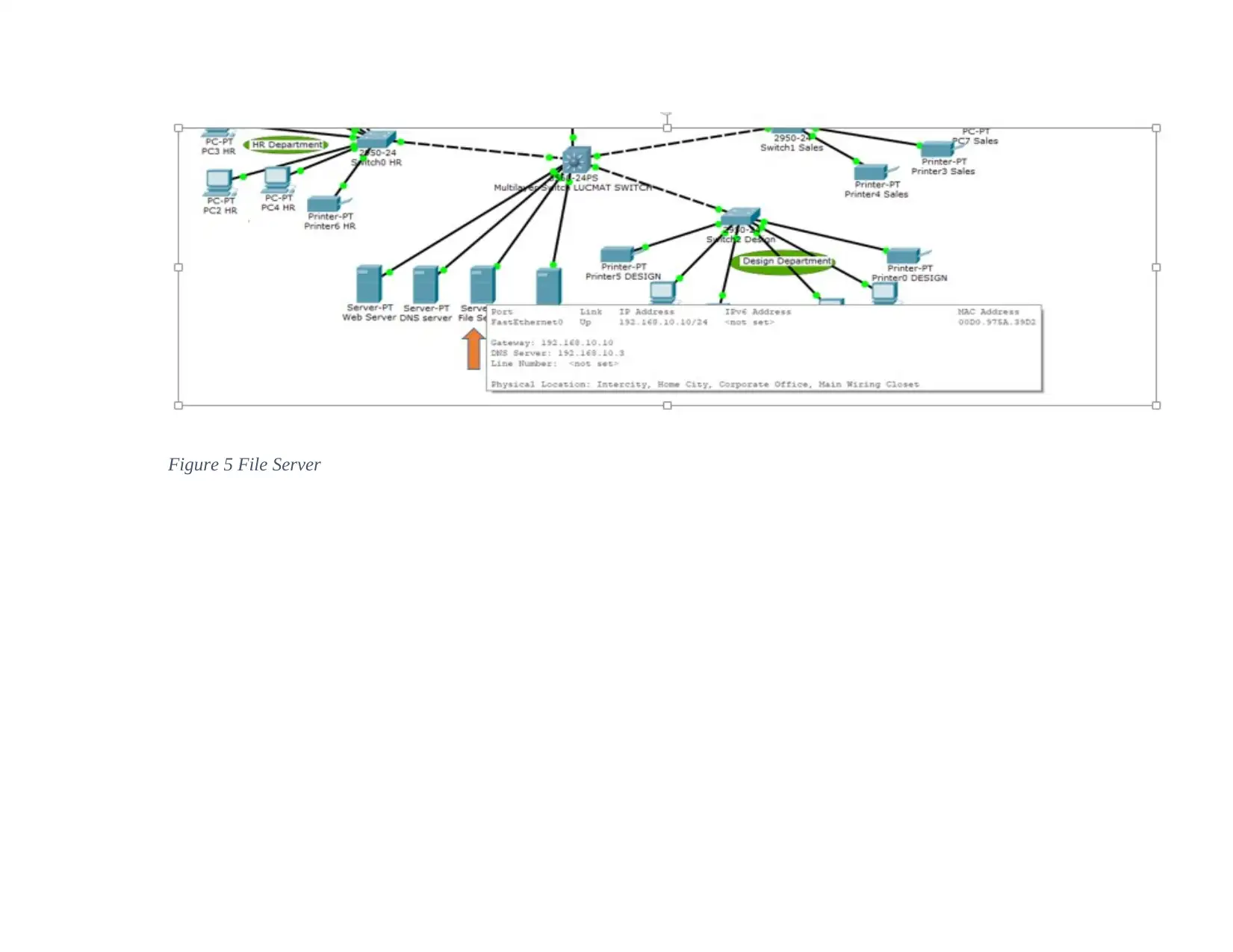
Paraphrase This Document
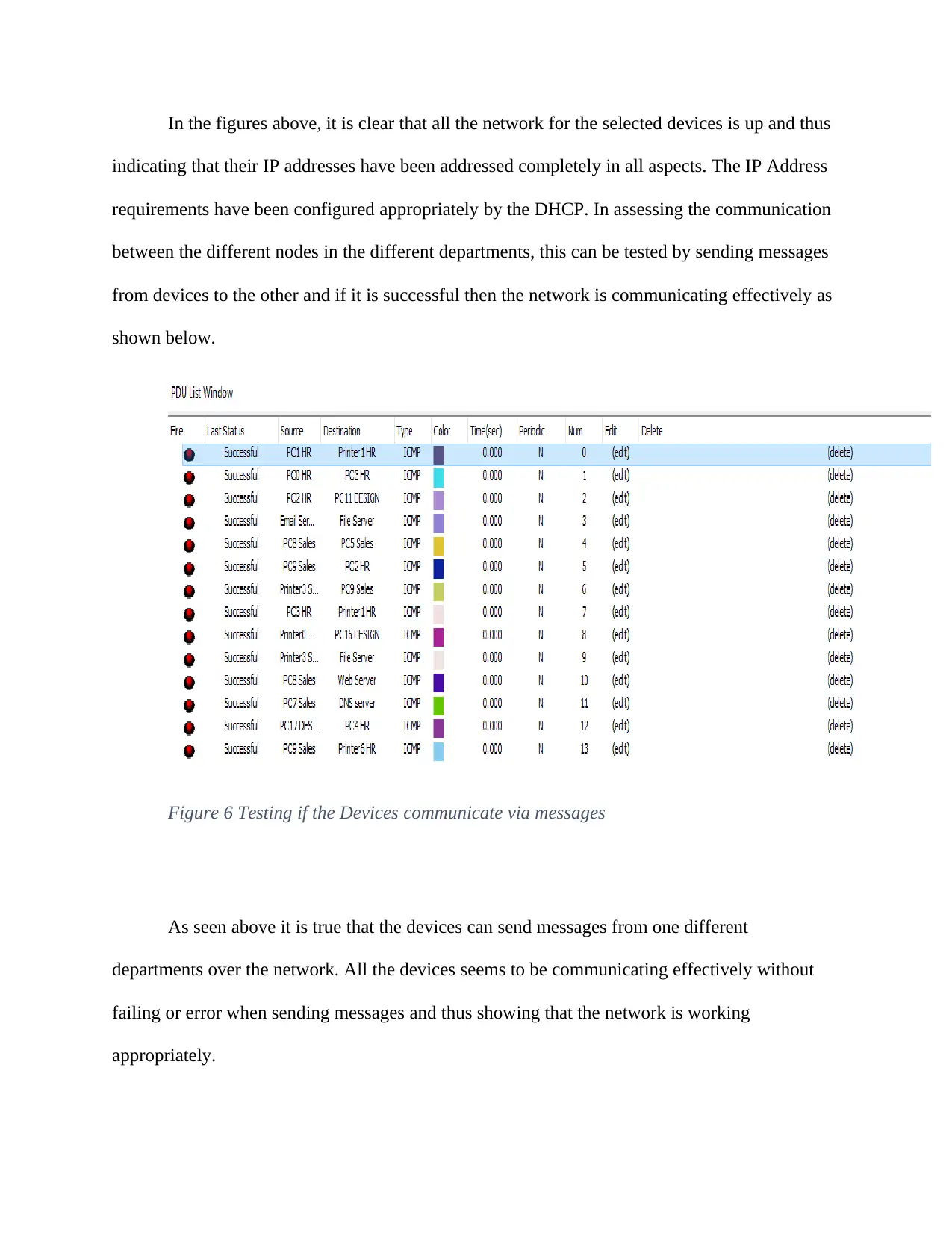
indicating that their IP addresses have been addressed completely in all aspects. The IP Address
requirements have been configured appropriately by the DHCP. In assessing the communication
between the different nodes in the different departments, this can be tested by sending messages
from devices to the other and if it is successful then the network is communicating effectively as
shown below.
Figure 6 Testing if the Devices communicate via messages
As seen above it is true that the devices can send messages from one different
departments over the network. All the devices seems to be communicating effectively without
failing or error when sending messages and thus showing that the network is working
appropriately.
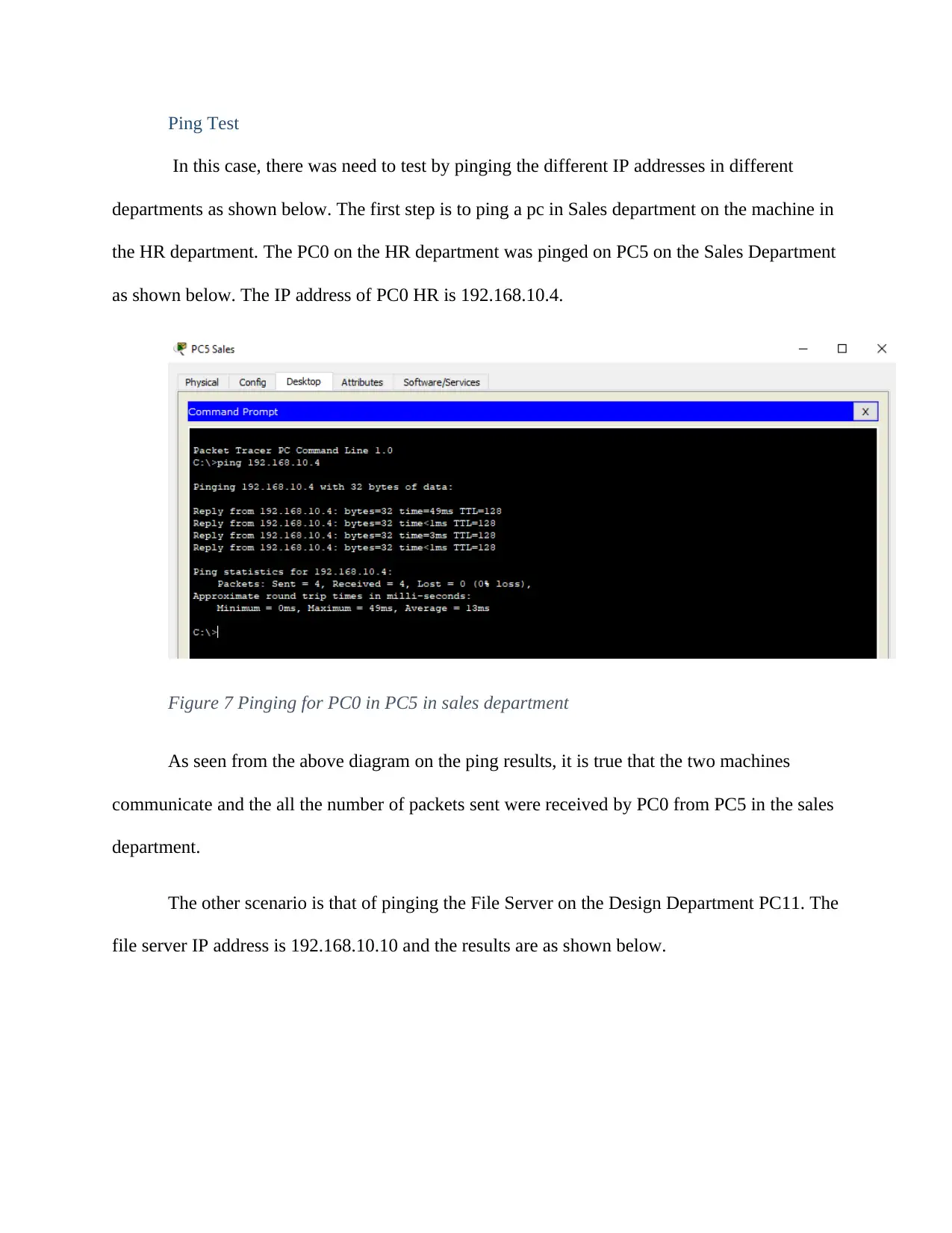
In this case, there was need to test by pinging the different IP addresses in different
departments as shown below. The first step is to ping a pc in Sales department on the machine in
the HR department. The PC0 on the HR department was pinged on PC5 on the Sales Department
as shown below. The IP address of PC0 HR is 192.168.10.4.
Figure 7 Pinging for PC0 in PC5 in sales department
As seen from the above diagram on the ping results, it is true that the two machines
communicate and the all the number of packets sent were received by PC0 from PC5 in the sales
department.
The other scenario is that of pinging the File Server on the Design Department PC11. The
file server IP address is 192.168.10.10 and the results are as shown below.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
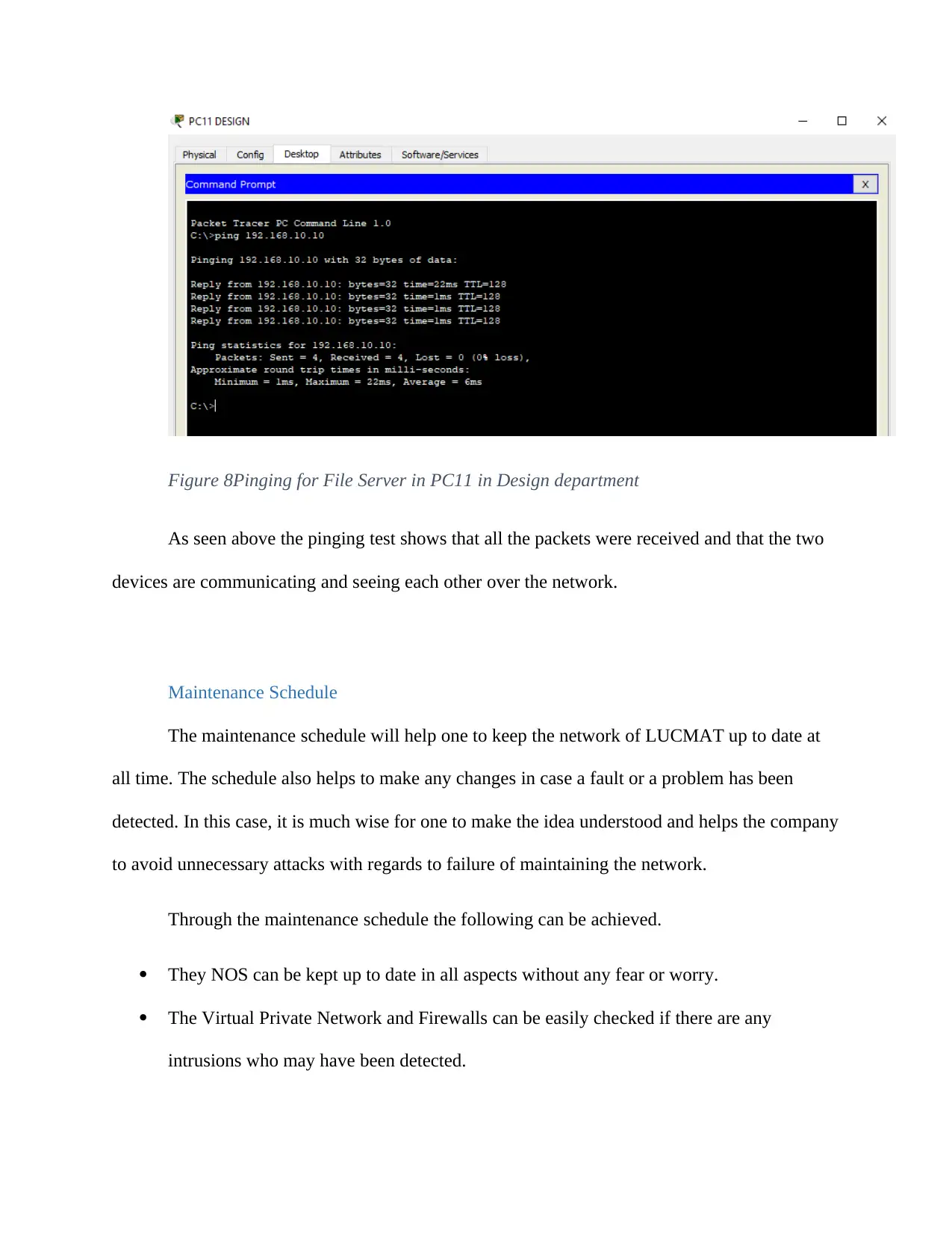
As seen above the pinging test shows that all the packets were received and that the two
devices are communicating and seeing each other over the network.
Maintenance Schedule
The maintenance schedule will help one to keep the network of LUCMAT up to date at
all time. The schedule also helps to make any changes in case a fault or a problem has been
detected. In this case, it is much wise for one to make the idea understood and helps the company
to avoid unnecessary attacks with regards to failure of maintaining the network.
Through the maintenance schedule the following can be achieved.
They NOS can be kept up to date in all aspects without any fear or worry.
The Virtual Private Network and Firewalls can be easily checked if there are any
intrusions who may have been detected.
Paraphrase This Document
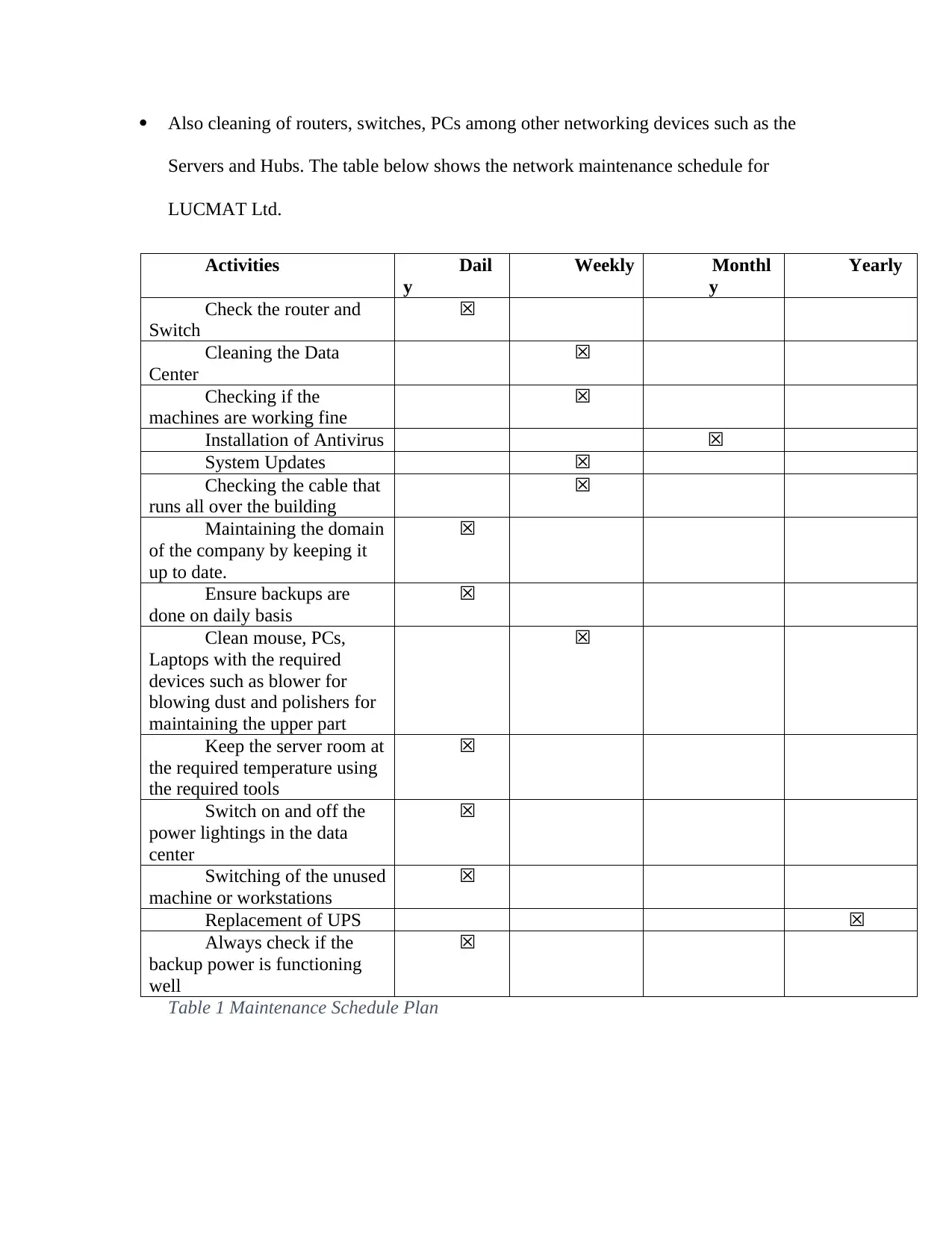
Servers and Hubs. The table below shows the network maintenance schedule for
LUCMAT Ltd.
Activities Dail
y
Weekly Monthl
y
Yearly
Check the router and
Switch
☒
Cleaning the Data
Center
☒
Checking if the
machines are working fine
☒
Installation of Antivirus ☒
System Updates ☒
Checking the cable that
runs all over the building
☒
Maintaining the domain
of the company by keeping it
up to date.
☒
Ensure backups are
done on daily basis
☒
Clean mouse, PCs,
Laptops with the required
devices such as blower for
blowing dust and polishers for
maintaining the upper part
☒
Keep the server room at
the required temperature using
the required tools
☒
Switch on and off the
power lightings in the data
center
☒
Switching of the unused
machine or workstations
☒
Replacement of UPS ☒
Always check if the
backup power is functioning
well
☒
Table 1 Maintenance Schedule Plan

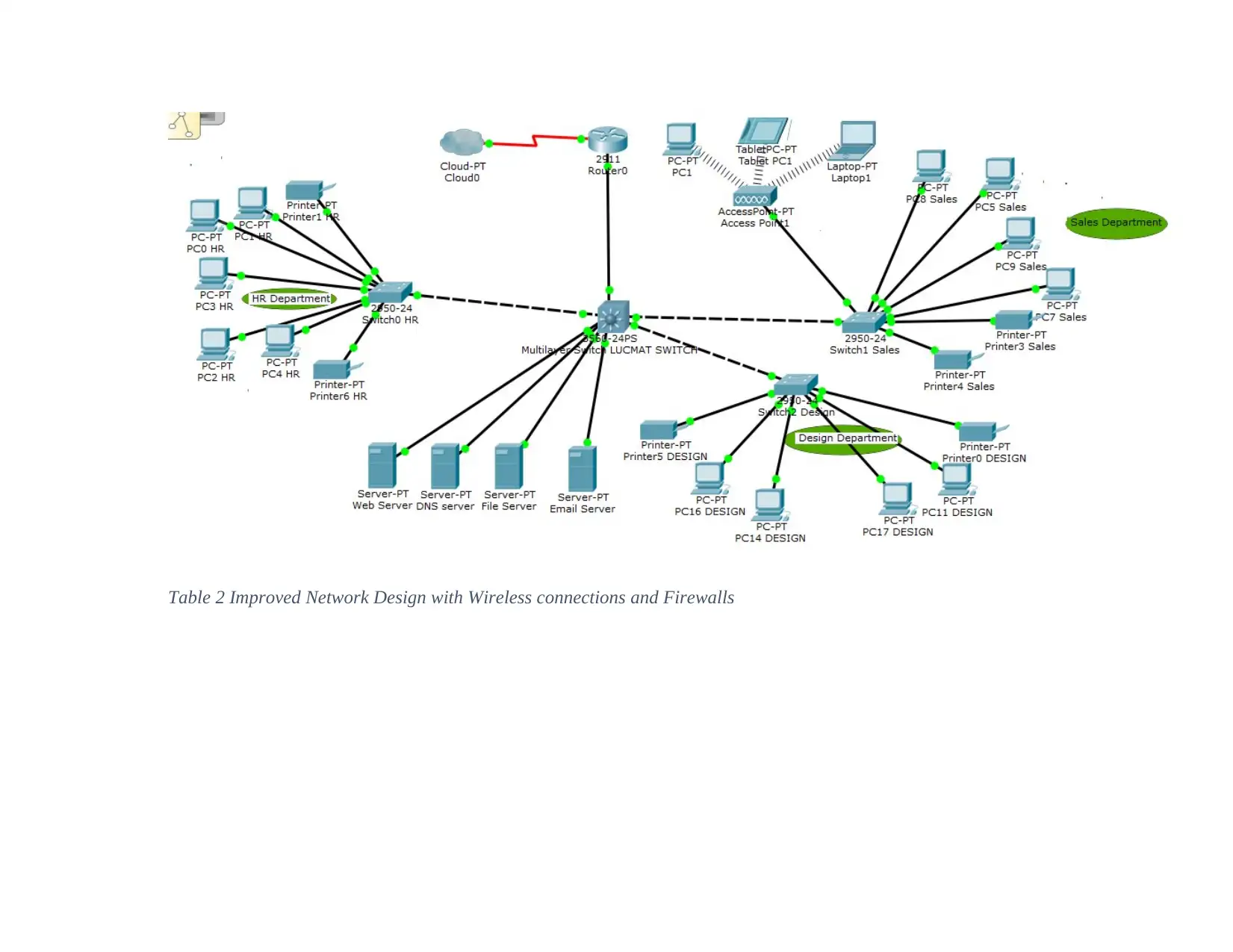
Implementation of the Network System
The two major problems that need to be addressed in the already design are such as
explained below.
There will be need to install a WAP that will provide the end users with wireless
connections on which they can connect to their personal devices such as the smartphones and
Personal Laptops. The second problem is making sure that all the diagram have been installed
with a firewall to ensure that what comes in is filtered before it is executed in the network. In this
case, the company can be able to improve on the security of the network. Also if the company
can afford the use of a Virtual Private Network, such can be installed in the router so that
filtering can be effective in all aspects. The figure below is an implementation change with
regards to the first design eliminating the problems associated.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
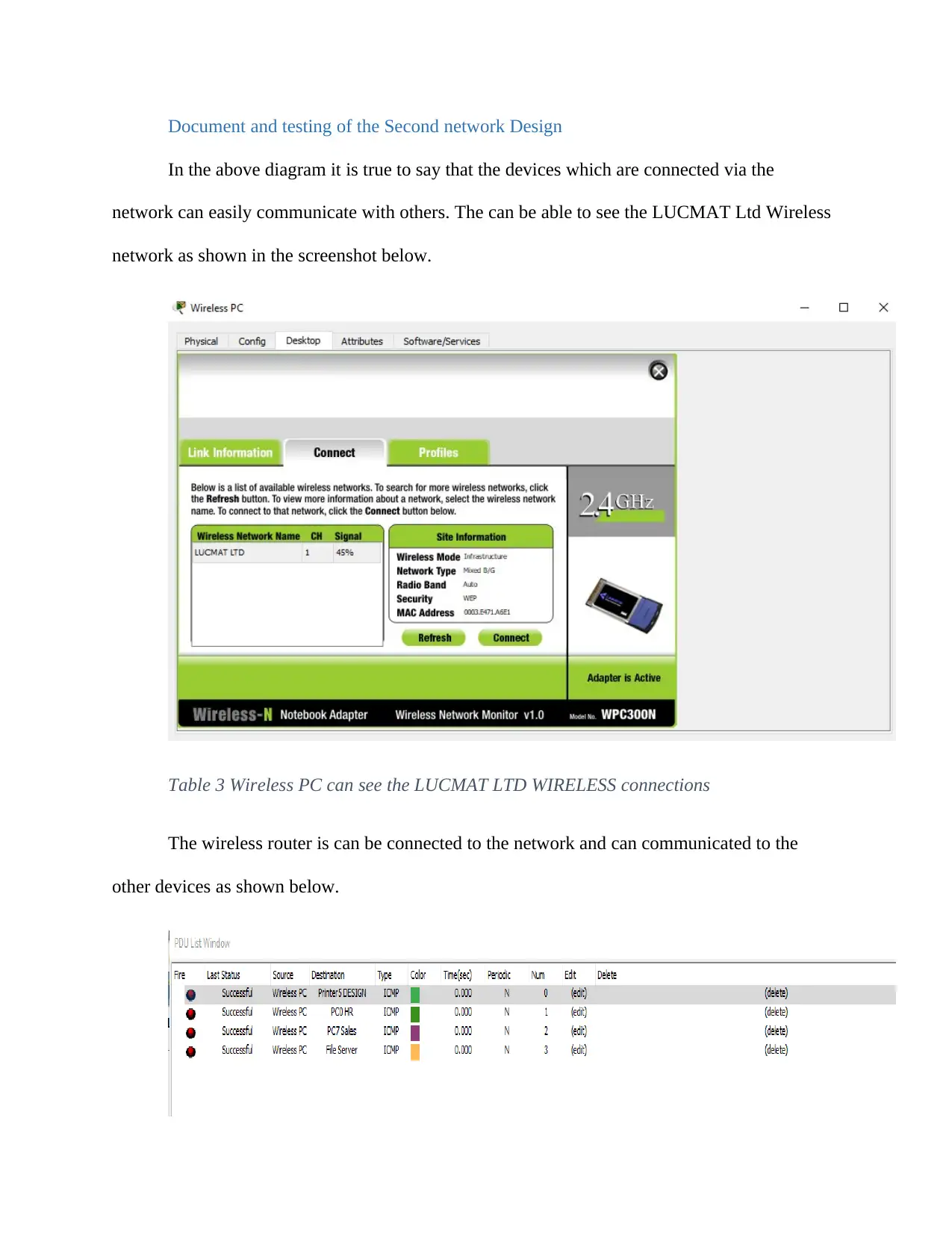
In the above diagram it is true to say that the devices which are connected via the
network can easily communicate with others. The can be able to see the LUCMAT Ltd Wireless
network as shown in the screenshot below.
Table 3 Wireless PC can see the LUCMAT LTD WIRELESS connections
The wireless router is can be connected to the network and can communicated to the
other devices as shown below.
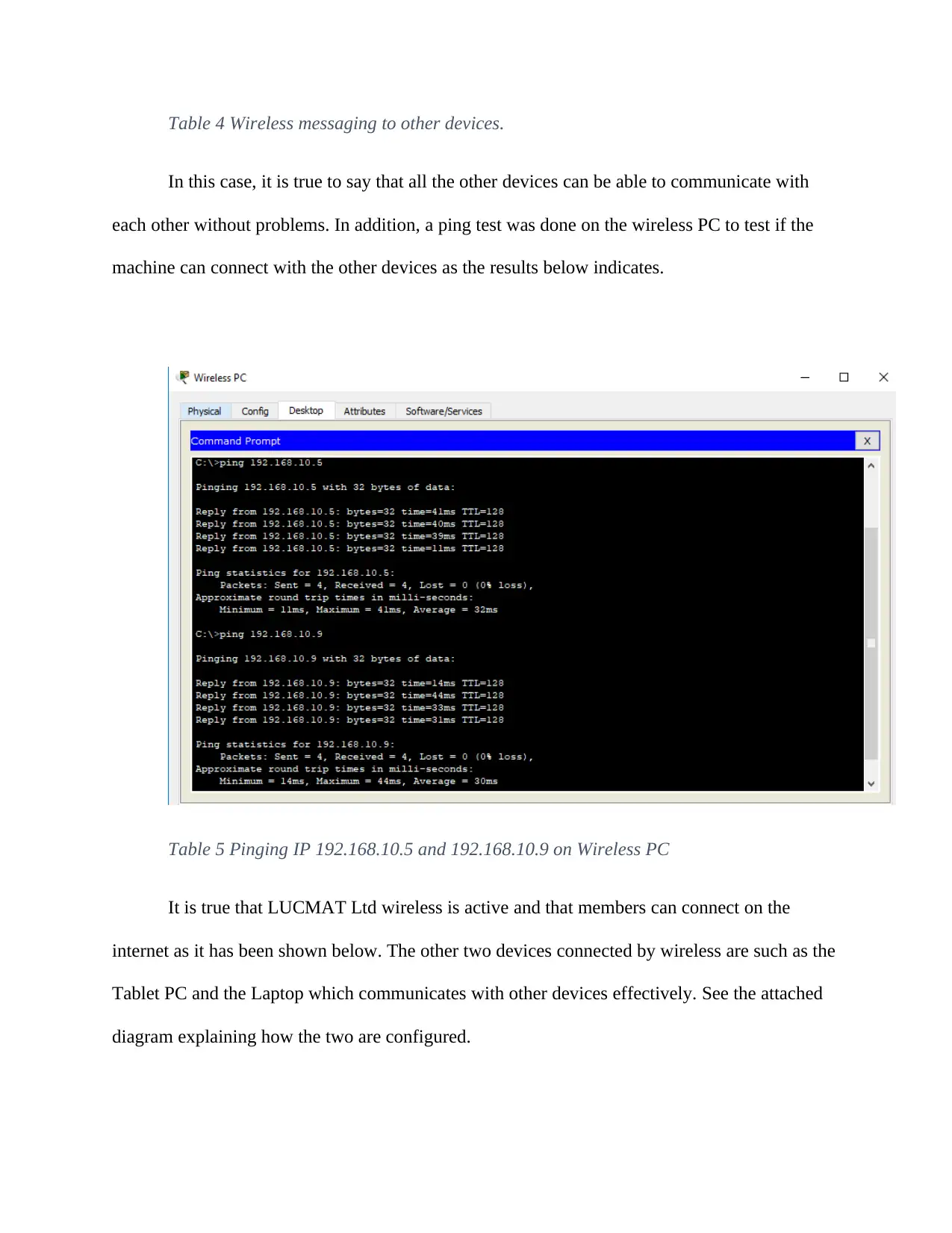
In this case, it is true to say that all the other devices can be able to communicate with
each other without problems. In addition, a ping test was done on the wireless PC to test if the
machine can connect with the other devices as the results below indicates.
Table 5 Pinging IP 192.168.10.5 and 192.168.10.9 on Wireless PC
It is true that LUCMAT Ltd wireless is active and that members can connect on the
internet as it has been shown below. The other two devices connected by wireless are such as the
Tablet PC and the Laptop which communicates with other devices effectively. See the attached
diagram explaining how the two are configured.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
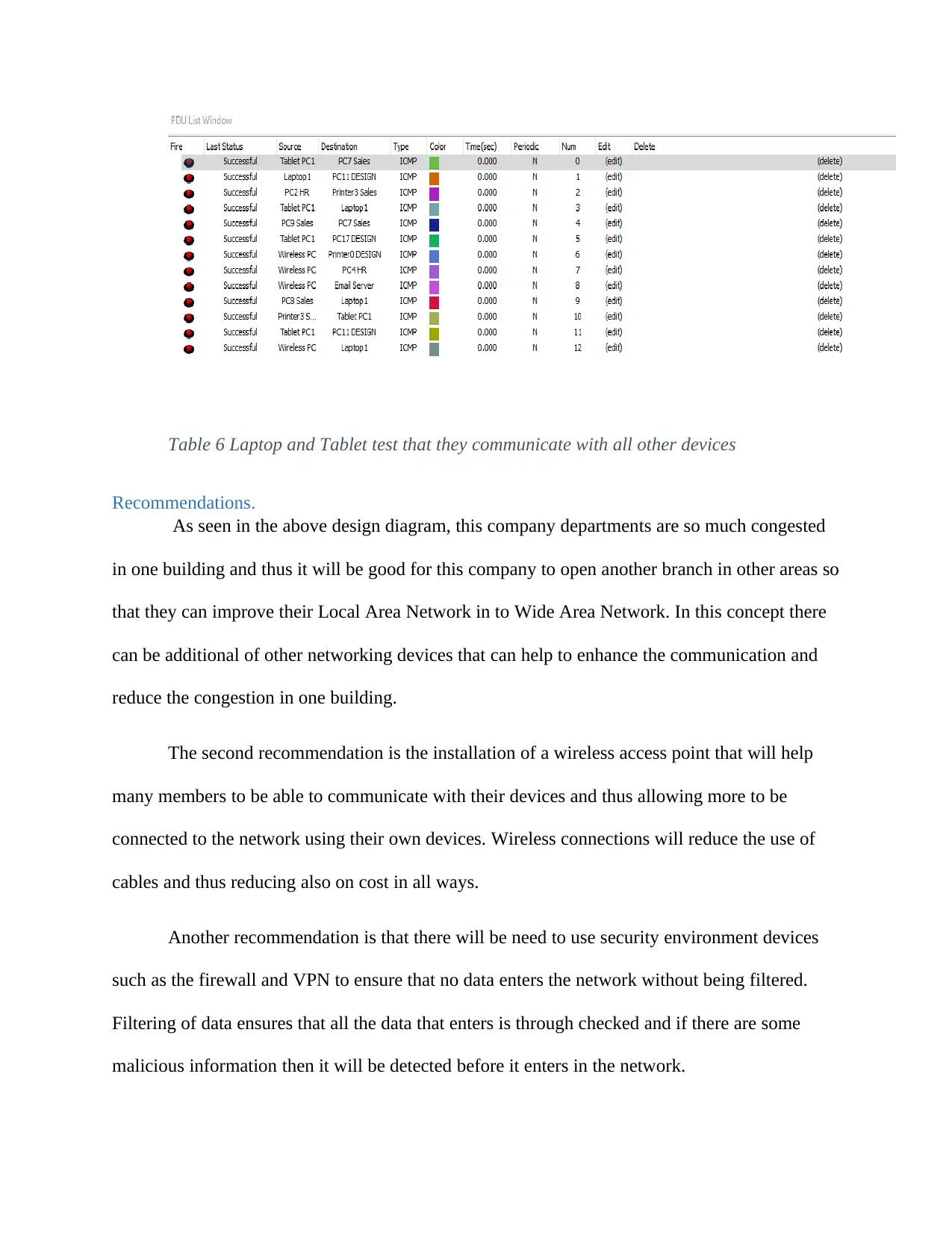
Recommendations.
As seen in the above design diagram, this company departments are so much congested
in one building and thus it will be good for this company to open another branch in other areas so
that they can improve their Local Area Network in to Wide Area Network. In this concept there
can be additional of other networking devices that can help to enhance the communication and
reduce the congestion in one building.
The second recommendation is the installation of a wireless access point that will help
many members to be able to communicate with their devices and thus allowing more to be
connected to the network using their own devices. Wireless connections will reduce the use of
cables and thus reducing also on cost in all ways.
Another recommendation is that there will be need to use security environment devices
such as the firewall and VPN to ensure that no data enters the network without being filtered.
Filtering of data ensures that all the data that enters is through checked and if there are some
malicious information then it will be detected before it enters in the network.
Paraphrase This Document

In my own understanding if all the recommendations mentioned above are put into
considerations then it will be sure that the network will be running smoothly in all ways.
Reflecting the network setup with regards to cost, the cost of the network will be highly at the
beginning, though in future such will change as they will be no need to design another network
model from scratch. I also understand that, through the designing of the hierarchical layered
architecture of the design model, this network design of LUCMAT will not be complex when
there will be need to add more devices in the future.
Setting up the network design at the start will take much time due to design and
implementation, nevertheless, such will change when the design has been setup in future as
additional of other devices will be faster unlike in the flat design model which is not flexible and
scalable.
The quality of the network in the hierarchical layered design model is high as there are
three layers that facilitates the way information moves in and out of the network. The first layer
is the access layer, secondly is the core layer and the third is distribution that allows
dissemination of information from the source to the anticipated destination. I understand that the
use of wireless networks will ensure that cost of buying cables and points of connection has been
reduced in all aspects. This will ensure that the network is affordable and always available to the
end users.
Conclusions
In this case of LUCMAT Ltd, the objective was to design and implement its network
infrastructure as an upgrade due to its requirements such as the increment of employees and thus
existing network needed an upgrade to accommodate the additional members. The idea was to

the Sales Departments respectively. All the three departments needed to be configured within the
company network of 192.168.10.2/24. In this case, a network design was proposed to cater for
their needs.
The report has discussed on all the benefits of the types of protocols in existence and the
associated constraints. In this case, after identifying all the constraints, star topology was chosen
as the best for this case of LUCMAT Ltd. Immediately after understanding the star topology,
there was need to address all the networking devices and their roles so that one will be knowing
what to include in the network design in all concepts. Understanding the network will be
determined by the knowledge of various devices that are needed for this scenario.
The other concept was designing an efficient network system that will meet all the
required specifications of LUCMAT in all aspects of life. To justify if the system network works
fine there was need to do some testing such as pinging and sending messages from one pc to the
other without necessary minding the department. In conclusion, the proposed system was
amended and added some additional features such as the use of Wireless Access Point which
could help the staff to connect to wireless network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bergano, N.S., 2012, July. Undersea fiber-optic cables make the web worldwide. In 2012 17th
Opto-Electronics and Communications Conference (pp. 5-5). IEEE.
Bora, G., Bora, S., Singh, S. and Arsalan, S.M., 2014. OSI reference model: An
overview. International Journal of Computer Trends and Technology (IJCTT), 7(4), pp.214-218.
Cavraro, G., Arghandeh, R., Poolla, K. and Von Meier, A., 2015, July. Data-driven approach for
distribution network topology detection. In 2015 IEEE Power & Energy Society General
Meeting (pp. 1-5). IEEE.
Davidson, J., 2012. An introduction to TCP/IP. Springer Science & Bus
Dong, X., El-Gorashi, T.E. and Elmirghani, J.M., 2012. On the energy efficiency of physical
topology design for IP over WDM networks. Journal of Lightwave Technology, 30(11), pp.1694-
1705.
Drutskoy, D., Keller, E. and Rexford, J., 2012. Scalable network virtualization in software-
defined networks. IEEE Internet Computing, 17(2), pp.20-27.
Gibson, C., H. Hardy III, J. and Ronald Buckley, M., 2014. Understanding the role of
networking in organizations. Career Development International, 19(2), pp.146-161.
Jain, R. and Paul, S., 2013. Network virtualization and software defined networking for cloud
computing: a survey. IEEE Communications Magazine, 51(11), pp.24-31.
Mets, K., Ojea, J.A. and Develder, C., 2014. Combining power and communication network
simulation for cost-effective smart grid analysis. IEEE Communications Surveys &
Tutorials, 16(3), pp.1771-1796.
Paraphrase This Document

in Computer Science and Management Studies, 1(2).
Petite, D., SIPCO LLC, 2016. Wireless network protocol system and methods. U.S. Patent
9,439,126.
Vega, D., Cerda-Alabern, L., Navarro, L. and Meseguer, R., 2012, October. Topology patterns of
a community network: Guifi. net. In 2012 IEEE 8th International Conference on Wireless and
Mobile Computing, Networking and Communications (WiMob) (pp. 612-619). IEEE.
Wang, B. and Wu, S., ZTE Corp, 2014. Topology management method of ether multi-ring
network, and system thereof. U.S. Patent 8,885,521.
Xie, S. and Wang, Y., 2014. Construction of tree network with limited delivery latency in
homogeneous wireless sensor networks. Wireless personal communications, 78(1), pp.231-246.
Zhang, P., Li, W. and Wang, S., 2012. Reliability-oriented distribution network reconfiguration
considering uncertainties of data by interval analysis. International Journal of Electrical Power
& Energy Systems, 34(1), pp.138-144.
Zhang, X. and Papachristodoulou, A., 2013, June. A real-time control framework for smart
power networks with star topology. In 2013 American Control Conference (pp. 5062-5067).
IEEE.
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.





