Client Management Systems: SCCM and Chef Product Comparison
VerifiedAdded on 2023/06/04
|18
|4277
|238
Report
AI Summary
This report provides a comprehensive analysis of Client Management Systems, focusing on two prominent products: System Center Configuration Manager (SCCM) and Chef. The report begins with an introduction to Client Management Systems and their role in enhancing customer relationships. It then delves into the specifics of SCCM, including its general operation, architecture, components, advantages, and disadvantages. The report further explores the Chef product, outlining its architecture, advantages, and disadvantages. A detailed comparison between SCCM and Chef is presented, highlighting their key differences and similarities. The report concludes with a summary of the findings and references. The report covers topics such as the SCCM console, distribution points, SCCM Client agent, Windows Management, CIM class, Virtual Machine Manager, Endpoint Protection, Service Manager, Operations Manager, Data Protection Manager, and App controller.

Running head: NETWORK AND INFRASTRUCTURE 1
Network and Infrastructure
(Client Management Systems)
Student’s Name
Institution Affiliation
Network and Infrastructure
(Client Management Systems)
Student’s Name
Institution Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND INFRASTRUCTURE
Table of Contents
Introduction......................................................................................................................................3
SCCM general operation.................................................................................................................3
Architecture and design features of SCCM.....................................................................................4
Components of SCCM.....................................................................................................................7
Advantages and disadvantages of SCCM........................................................................................9
Architecture and design features of Chef Product.........................................................................11
Advantages and disadvantages of Chef product............................................................................12
Comparison between SCCM and the Chef Client Management System products........................13
Conclusion.....................................................................................................................................15
References......................................................................................................................................16
Table of Contents
Introduction......................................................................................................................................3
SCCM general operation.................................................................................................................3
Architecture and design features of SCCM.....................................................................................4
Components of SCCM.....................................................................................................................7
Advantages and disadvantages of SCCM........................................................................................9
Architecture and design features of Chef Product.........................................................................11
Advantages and disadvantages of Chef product............................................................................12
Comparison between SCCM and the Chef Client Management System products........................13
Conclusion.....................................................................................................................................15
References......................................................................................................................................16

NETWORK AND INFRASTRUCTURE
Introduction
The Client Management System has been used to enhance customer relationship in the
business sectors. According to Chen, & Popovich (2013), Customer Relationship Management
(CRM) refers to the gathering and analysis of data with the aim of decision support to the
business by identifying the needs of existing and potential customers. It includes the payment
processing, account management, credit and adjustment, catalogue and order entry among other
functions. A Client Management System according to the above definition, therefore, refers to
set of software applications that are used in the business to uncover the customer's needs and
preferences by storing, managing, organizing and tracking all the customer's interactions with the
business. The system stores all the relevant information that the business can use to evaluate the
level of relationship to the customers by considering customer retention.
There are various Client Management System products. The most common product is the
System Center Configuration Manager (SCCM) software. The software is provided by
Microsoft, and with this management suite, a large number of Windows-based computers can be
controlled by a single user (Meyler, 2014). The software features include network protection,
operating system deployment, patch management, remote control and other various services. The
users of SCCM can manage computers connected to a network, corporate and the business by
integrating with the Microsoft Intune. Additionally, allows users to manage computers running
an Android operating system, mobile devices running Windows, servers using Linux or Unix and
also macOS.
SCCM general operation
The software contains the console where packages are created. The SCCM console as
well contains the command line and the executable files that support the installation of the
Introduction
The Client Management System has been used to enhance customer relationship in the
business sectors. According to Chen, & Popovich (2013), Customer Relationship Management
(CRM) refers to the gathering and analysis of data with the aim of decision support to the
business by identifying the needs of existing and potential customers. It includes the payment
processing, account management, credit and adjustment, catalogue and order entry among other
functions. A Client Management System according to the above definition, therefore, refers to
set of software applications that are used in the business to uncover the customer's needs and
preferences by storing, managing, organizing and tracking all the customer's interactions with the
business. The system stores all the relevant information that the business can use to evaluate the
level of relationship to the customers by considering customer retention.
There are various Client Management System products. The most common product is the
System Center Configuration Manager (SCCM) software. The software is provided by
Microsoft, and with this management suite, a large number of Windows-based computers can be
controlled by a single user (Meyler, 2014). The software features include network protection,
operating system deployment, patch management, remote control and other various services. The
users of SCCM can manage computers connected to a network, corporate and the business by
integrating with the Microsoft Intune. Additionally, allows users to manage computers running
an Android operating system, mobile devices running Windows, servers using Linux or Unix and
also macOS.
SCCM general operation
The software contains the console where packages are created. The SCCM console as
well contains the command line and the executable files that support the installation of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND INFRASTRUCTURE
application. In the installation system, there are also the distribution points. The distribution
point is where the created packages are stored and replicated (Ashraf, 2017, October). It acts as a
file server, and they are used as storage to store and replicate the content of packages belonging
to a specific region. Therefore, the distribution point can be used for downloading the application
if a bunch of machines are remotely located rather than depending on the SCCM primary server.
To essentially enable all the computers to communicate with the SCCM server, the SCCM Client
agent application is installed on all the machines in an SCCM environment.
Therefore, the SCCM admin creates the deployment where a single target of application
is made on a bunch of machines. The app keeps on checking for the new deployments or policies
with the help of the SCCM client agent that is installed on the end user's computer system. The
policy is evaluated once it reaches the end machine. Downloading of the content is performed
immediately the policy reaches out its respective regional Distribution Point. The executable
files are installed locally once they have been downloaded and the SCCM Server in the database
updated by sending back the status of the same.
Architecture and design features of SCCM
The architecture of the SCCM is based on the client and the Configuration Manager
Server architecture. In Configuration Manager, the components include the applications, services
and threads that run on both the server computer and the client computer (Ashraf, 2015,
November). They provide Configuration Manager functionalities. The critical operation
information is stored in the central location in a dynamic computing environment.
The open architecture in the SCCM helps in customizing and automating Configuration
Manager features such as the Software Distribution by enabling the user to write applications and
application. In the installation system, there are also the distribution points. The distribution
point is where the created packages are stored and replicated (Ashraf, 2017, October). It acts as a
file server, and they are used as storage to store and replicate the content of packages belonging
to a specific region. Therefore, the distribution point can be used for downloading the application
if a bunch of machines are remotely located rather than depending on the SCCM primary server.
To essentially enable all the computers to communicate with the SCCM server, the SCCM Client
agent application is installed on all the machines in an SCCM environment.
Therefore, the SCCM admin creates the deployment where a single target of application
is made on a bunch of machines. The app keeps on checking for the new deployments or policies
with the help of the SCCM client agent that is installed on the end user's computer system. The
policy is evaluated once it reaches the end machine. Downloading of the content is performed
immediately the policy reaches out its respective regional Distribution Point. The executable
files are installed locally once they have been downloaded and the SCCM Server in the database
updated by sending back the status of the same.
Architecture and design features of SCCM
The architecture of the SCCM is based on the client and the Configuration Manager
Server architecture. In Configuration Manager, the components include the applications, services
and threads that run on both the server computer and the client computer (Ashraf, 2015,
November). They provide Configuration Manager functionalities. The critical operation
information is stored in the central location in a dynamic computing environment.
The open architecture in the SCCM helps in customizing and automating Configuration
Manager features such as the Software Distribution by enabling the user to write applications and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND INFRASTRUCTURE
scripts. Customized programs that can start from the Configuration Manager console can also be
created and run. Various sources provide concepts and terms that relate to the Configuration
Manager architecture. According to Chaganti (2014), the managed objects are created from the
terms and conditions originating from the Desktop Management Task Force (DMTF). Other-
initiated terms and concepts are the Web-Based Enterprise (WBE) and the standard COM. The
SCCM manages the objects by the use of WBEM architecture. WBEM is an industry supported
by many network device manufacturers and non-windows computers and is a DMTF adopted
initiative. It manages entity policies by complementing the Active Directory. It also provides an
interactive interface between the management entities and the applications without the user
understanding the protocols used by the entities.
The client computers and the packages stored in the Configuration Manager database are
all objects when it comes to the Configuration Manager. Thus, the WBEM initiative outlines the
architecture used by the DMTF object management standards such as Windows Management.
By use of an extensible, platform-independent interface, the Windows Management provides
access to operations data and the Configuration Manager configuration. The CIM class, on the
other hand, provides the Configuration Manager-managed object. The CIM Object Manager
allows the SCCM to view and manipulate objects as well as storing managed object data by use
of the configuration manager site database (Chandramouli, Schoening, & Nordman, 2015).
However, the Configuration Manager view and manipulate the managed data by use of the SMS
provider and the CIM Object Manager interface. It may not be, however, easy to directly view
and manipulate the SCCM database. Instead, the users have to use the CIM Object managers to
access the underlying database which in turn communicate with the SMS provider.
scripts. Customized programs that can start from the Configuration Manager console can also be
created and run. Various sources provide concepts and terms that relate to the Configuration
Manager architecture. According to Chaganti (2014), the managed objects are created from the
terms and conditions originating from the Desktop Management Task Force (DMTF). Other-
initiated terms and concepts are the Web-Based Enterprise (WBE) and the standard COM. The
SCCM manages the objects by the use of WBEM architecture. WBEM is an industry supported
by many network device manufacturers and non-windows computers and is a DMTF adopted
initiative. It manages entity policies by complementing the Active Directory. It also provides an
interactive interface between the management entities and the applications without the user
understanding the protocols used by the entities.
The client computers and the packages stored in the Configuration Manager database are
all objects when it comes to the Configuration Manager. Thus, the WBEM initiative outlines the
architecture used by the DMTF object management standards such as Windows Management.
By use of an extensible, platform-independent interface, the Windows Management provides
access to operations data and the Configuration Manager configuration. The CIM class, on the
other hand, provides the Configuration Manager-managed object. The CIM Object Manager
allows the SCCM to view and manipulate objects as well as storing managed object data by use
of the configuration manager site database (Chandramouli, Schoening, & Nordman, 2015).
However, the Configuration Manager view and manipulate the managed data by use of the SMS
provider and the CIM Object Manager interface. It may not be, however, easy to directly view
and manipulate the SCCM database. Instead, the users have to use the CIM Object managers to
access the underlying database which in turn communicate with the SMS provider.
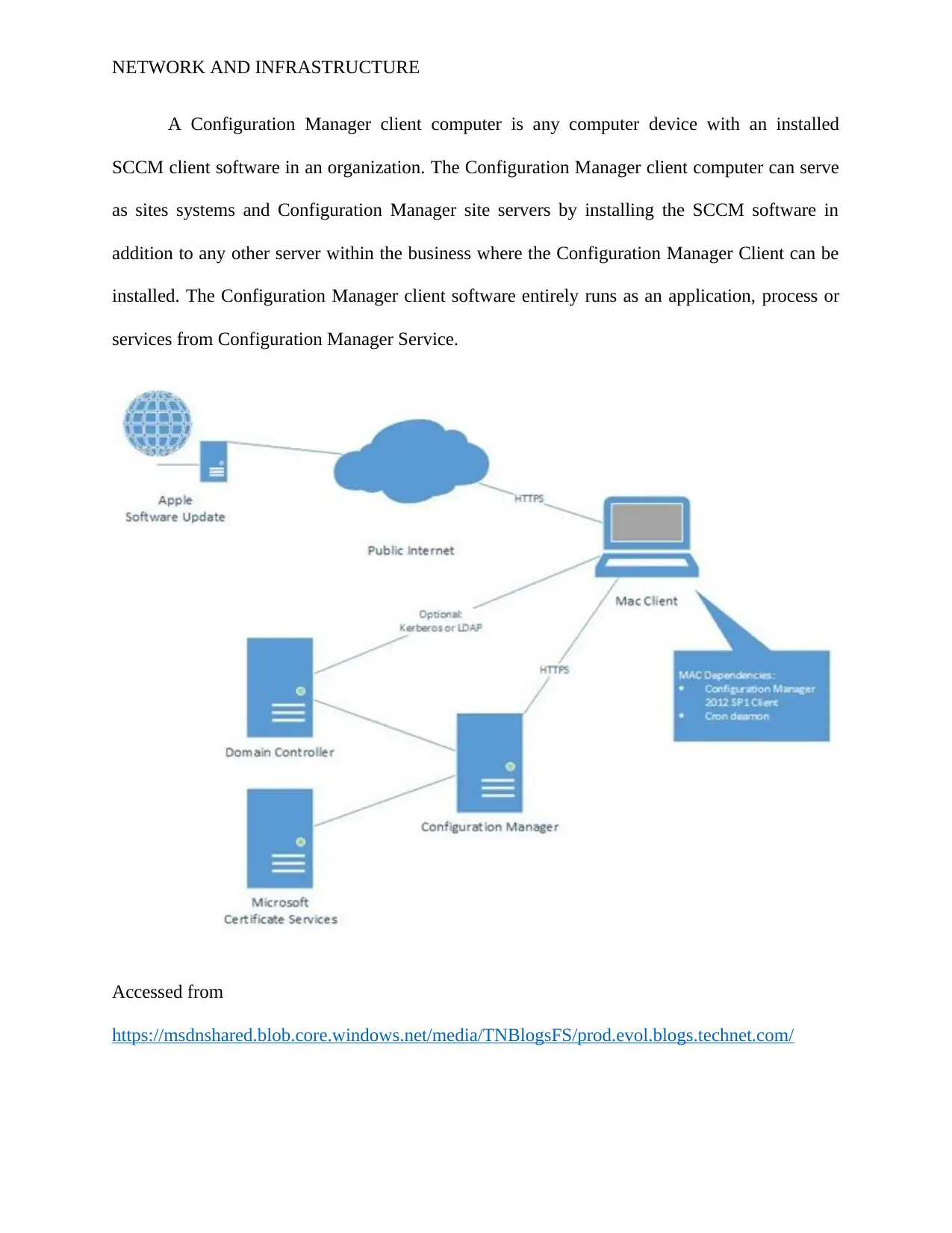
NETWORK AND INFRASTRUCTURE
A Configuration Manager client computer is any computer device with an installed
SCCM client software in an organization. The Configuration Manager client computer can serve
as sites systems and Configuration Manager site servers by installing the SCCM software in
addition to any other server within the business where the Configuration Manager Client can be
installed. The Configuration Manager client software entirely runs as an application, process or
services from Configuration Manager Service.
Accessed from
https://msdnshared.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/
A Configuration Manager client computer is any computer device with an installed
SCCM client software in an organization. The Configuration Manager client computer can serve
as sites systems and Configuration Manager site servers by installing the SCCM software in
addition to any other server within the business where the Configuration Manager Client can be
installed. The Configuration Manager client software entirely runs as an application, process or
services from Configuration Manager Service.
Accessed from
https://msdnshared.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND INFRASTRUCTURE
CommunityServer.Blogs.Components.WeblogFiles/00/00/00/94/29/metablogapi/
0184.052913_1820_SystemCente1.jpg
Components of SCCM
The SCCM software is composed of multiple elements that allows the IT manager and
administrators to manage their IT infrastructure. The components are explained below.
1. Configuration Managers
The components play one of the critical roles in the management of the IT infrastructure.
It allows the IT professionals to install updates, deploy software apps and the operating system
within the working premise (Mori, Masuda, & Nagai, 2017, October). Moreover, it offers
services such as the remote administration of computers, and the maintenance of software and
hardware inventories.
2. Virtual Machine Manager
This component enables the users of the computer systems to create and manage virtual
machines. The Microsoft azure's Hyper-V virtual machines also offer the interface for the
managers. Moreover, the Virtual Machine Manager avails the integration pack for VMware
vSphere add-on system at no additional cost to the admins who wish to interface with the
existing VMware hypervisors (Krsul et al., 2014, November).
3. Endpoint Protection
This is a system antimalware and security client that allows the IT staffs to monitor the
security to the client workstation. It ensures that there is security to the system. It provides
CommunityServer.Blogs.Components.WeblogFiles/00/00/00/94/29/metablogapi/
0184.052913_1820_SystemCente1.jpg
Components of SCCM
The SCCM software is composed of multiple elements that allows the IT manager and
administrators to manage their IT infrastructure. The components are explained below.
1. Configuration Managers
The components play one of the critical roles in the management of the IT infrastructure.
It allows the IT professionals to install updates, deploy software apps and the operating system
within the working premise (Mori, Masuda, & Nagai, 2017, October). Moreover, it offers
services such as the remote administration of computers, and the maintenance of software and
hardware inventories.
2. Virtual Machine Manager
This component enables the users of the computer systems to create and manage virtual
machines. The Microsoft azure's Hyper-V virtual machines also offer the interface for the
managers. Moreover, the Virtual Machine Manager avails the integration pack for VMware
vSphere add-on system at no additional cost to the admins who wish to interface with the
existing VMware hypervisors (Krsul et al., 2014, November).
3. Endpoint Protection
This is a system antimalware and security client that allows the IT staffs to monitor the
security to the client workstation. It ensures that there is security to the system. It provides
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND INFRASTRUCTURE
security to the client workstation by checking on any malware that has been installed into the
system. When the malware is detected, it sent the email alert to the administrator system.
4. Service Manager
This is an IT service management platform (Integrated Center System) that allows the IT
professionals to identify any IT related problem within the system such as tracking incidents and
solving the problem. The Service Manager interfaces with the Configuration Manager and the
Operations Manager.
5. Operations Manager
This is the monitoring software that deploys a monitoring agent to another endpoint and
is included in the System Center pack (Khodakarami, & Chan, 2014). Due to the presence of
adds in the computer, the systems are therefore able to monitor a wide range of services such as
the SQL servers, VMware, Tomcat, and the Apache.
6. Data Protection Manager
Due to the variety of supported process to back up from disk and tape, the backup is
considered to be among the best. It is a centralized console that can manage a large number of
Improved Item Level Recovery (ILR) for files recovery, scope console for troubleshooting, a
new console UI and the Data Protection Managers server (Peltier, 2016).
7. App controller
This is an end user application of the SCCM that enable the user to see Windows Azure
public cloud and Virtual Machine Manager services and the private clouds deployed in them as
security to the client workstation by checking on any malware that has been installed into the
system. When the malware is detected, it sent the email alert to the administrator system.
4. Service Manager
This is an IT service management platform (Integrated Center System) that allows the IT
professionals to identify any IT related problem within the system such as tracking incidents and
solving the problem. The Service Manager interfaces with the Configuration Manager and the
Operations Manager.
5. Operations Manager
This is the monitoring software that deploys a monitoring agent to another endpoint and
is included in the System Center pack (Khodakarami, & Chan, 2014). Due to the presence of
adds in the computer, the systems are therefore able to monitor a wide range of services such as
the SQL servers, VMware, Tomcat, and the Apache.
6. Data Protection Manager
Due to the variety of supported process to back up from disk and tape, the backup is
considered to be among the best. It is a centralized console that can manage a large number of
Improved Item Level Recovery (ILR) for files recovery, scope console for troubleshooting, a
new console UI and the Data Protection Managers server (Peltier, 2016).
7. App controller
This is an end user application of the SCCM that enable the user to see Windows Azure
public cloud and Virtual Machine Manager services and the private clouds deployed in them as

NETWORK AND INFRASTRUCTURE
well as monitoring, scaling in and scaling out on these services (Swoboda et al., 2016). The
unified installer enables the installation of all the components of the application.
Advantages and disadvantages of SCCM.
Although the client management system product is used in many organizations due to
various reason, it has both advantages and disadvantages to the organization. Below are some
examples of the benefits that the organization gains from the product and also disadvantages as a
result of the same product to the organization's operations.
Advantages of SCCM
For the management purpose, the product reduces the overheads in managing services
that run on each computer system, therefore, the product has the manageability of all the
workstations within one console.
The product also allows the user to see a catalogue of applications that are made available
through the feature called Software Centre. By availing the list of application to the users, they
are, therefore, able to install the app themselves. Because the applications have been pre-
packaged, there is no configuration necessary from the user's end as well as no requirement for
the user to be local admin (Meyler et al., 2018). This is a great benefit if applications have to be
availed to few users, therefore, relieving the admin the burden of movement from one system to
another installing the apps.
Another great benefit of SCCM is associated with the deployment of the Operating
System. This allows reinstallation of windows and formatting of computers to be done
automatically (Hammoudi et al., 2016). There are a set of tasks that have been defined to run on
a computer, and the deployment of the operating system has to follow such a task sequence.
well as monitoring, scaling in and scaling out on these services (Swoboda et al., 2016). The
unified installer enables the installation of all the components of the application.
Advantages and disadvantages of SCCM.
Although the client management system product is used in many organizations due to
various reason, it has both advantages and disadvantages to the organization. Below are some
examples of the benefits that the organization gains from the product and also disadvantages as a
result of the same product to the organization's operations.
Advantages of SCCM
For the management purpose, the product reduces the overheads in managing services
that run on each computer system, therefore, the product has the manageability of all the
workstations within one console.
The product also allows the user to see a catalogue of applications that are made available
through the feature called Software Centre. By availing the list of application to the users, they
are, therefore, able to install the app themselves. Because the applications have been pre-
packaged, there is no configuration necessary from the user's end as well as no requirement for
the user to be local admin (Meyler et al., 2018). This is a great benefit if applications have to be
availed to few users, therefore, relieving the admin the burden of movement from one system to
another installing the apps.
Another great benefit of SCCM is associated with the deployment of the Operating
System. This allows reinstallation of windows and formatting of computers to be done
automatically (Hammoudi et al., 2016). There are a set of tasks that have been defined to run on
a computer, and the deployment of the operating system has to follow such a task sequence.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND INFRASTRUCTURE
This can involve installing the system and the applications as well as joining it to the domain
before the user logins. This is a benefit as the deployment of the large scale will work very well
especially by setting up and managing the SOE.
Another benefit is from the User State Migration Tool that can be included while
deploying the Operating System. The tool plays a crucial role in saving the personal data such as
the outlook profile to be copied to the server, local data stored on desktop and also the
background information (Iravani, Akbari, & Zohoori, 2017). This is applied especially in cases
where the new staff members wish to reinstall their own machines through refreshing the
Operating System. The automation of the process reduces any risk of data loss and burden to IT
support. It moreover reduces the IT support overheads, and the user is also able to enjoy the
control of their machines as it gives the option for the user to click install while leaving for the
office and the next day the user finds a newly imaged machine.
When it comes to the asset intelligence, the features allow the SCCM server to monitor
all the workstation installed applications, keep track of a number of instances and also it requires
minimal configuration (Hernantes, Gallardo, & Serrano, 2015). This is vital for license
maintenance in the network to ensure the user only utilizes the number of licenses available.
Disadvantages of SCCM
The application is very complicated. The installation is critical such that it requires
knowledge on how to set up correctly and also its installation is time-consuming. Also, if the
application is well functioning, then that's great, however, when something goes wrong, it
becomes a challenge to solve.
This can involve installing the system and the applications as well as joining it to the domain
before the user logins. This is a benefit as the deployment of the large scale will work very well
especially by setting up and managing the SOE.
Another benefit is from the User State Migration Tool that can be included while
deploying the Operating System. The tool plays a crucial role in saving the personal data such as
the outlook profile to be copied to the server, local data stored on desktop and also the
background information (Iravani, Akbari, & Zohoori, 2017). This is applied especially in cases
where the new staff members wish to reinstall their own machines through refreshing the
Operating System. The automation of the process reduces any risk of data loss and burden to IT
support. It moreover reduces the IT support overheads, and the user is also able to enjoy the
control of their machines as it gives the option for the user to click install while leaving for the
office and the next day the user finds a newly imaged machine.
When it comes to the asset intelligence, the features allow the SCCM server to monitor
all the workstation installed applications, keep track of a number of instances and also it requires
minimal configuration (Hernantes, Gallardo, & Serrano, 2015). This is vital for license
maintenance in the network to ensure the user only utilizes the number of licenses available.
Disadvantages of SCCM
The application is very complicated. The installation is critical such that it requires
knowledge on how to set up correctly and also its installation is time-consuming. Also, if the
application is well functioning, then that's great, however, when something goes wrong, it
becomes a challenge to solve.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND INFRASTRUCTURE
There are more than 120 log files within the SCCM installation location to choose in case
of need for log troubleshooting (Kerzner, & Kerzner, 2017). This becomes tricky to identify the
file log which the problem will be logged in.
In case of any failure during the installation process, the software does not show any
notification until the user gets a pop-up warning upon completing the installation.
All the users are affected if the software installation is flawed or affected by malicious
software as nothing can be installed or updated.
Architecture and design features of Chef Product
In the technology market, there is a high competition among various Client Management
System products. However, in this report, I will analyze on the two competing products; the
SCCM and the Chef. A chef is a powerful automated software to code transformation platform.
According to Masuda et al. (2014, November), the software automates how infrastructure is
managed, deployed and configured across network no matter the network size, or the working
environment such as the cloud, on-premise or hybrid. The architecture of the software consists of
the Chef client, Chef server, nodes, workstation, cookbook and the Chef supermarket.
There are more than 120 log files within the SCCM installation location to choose in case
of need for log troubleshooting (Kerzner, & Kerzner, 2017). This becomes tricky to identify the
file log which the problem will be logged in.
In case of any failure during the installation process, the software does not show any
notification until the user gets a pop-up warning upon completing the installation.
All the users are affected if the software installation is flawed or affected by malicious
software as nothing can be installed or updated.
Architecture and design features of Chef Product
In the technology market, there is a high competition among various Client Management
System products. However, in this report, I will analyze on the two competing products; the
SCCM and the Chef. A chef is a powerful automated software to code transformation platform.
According to Masuda et al. (2014, November), the software automates how infrastructure is
managed, deployed and configured across network no matter the network size, or the working
environment such as the cloud, on-premise or hybrid. The architecture of the software consists of
the Chef client, Chef server, nodes, workstation, cookbook and the Chef supermarket.
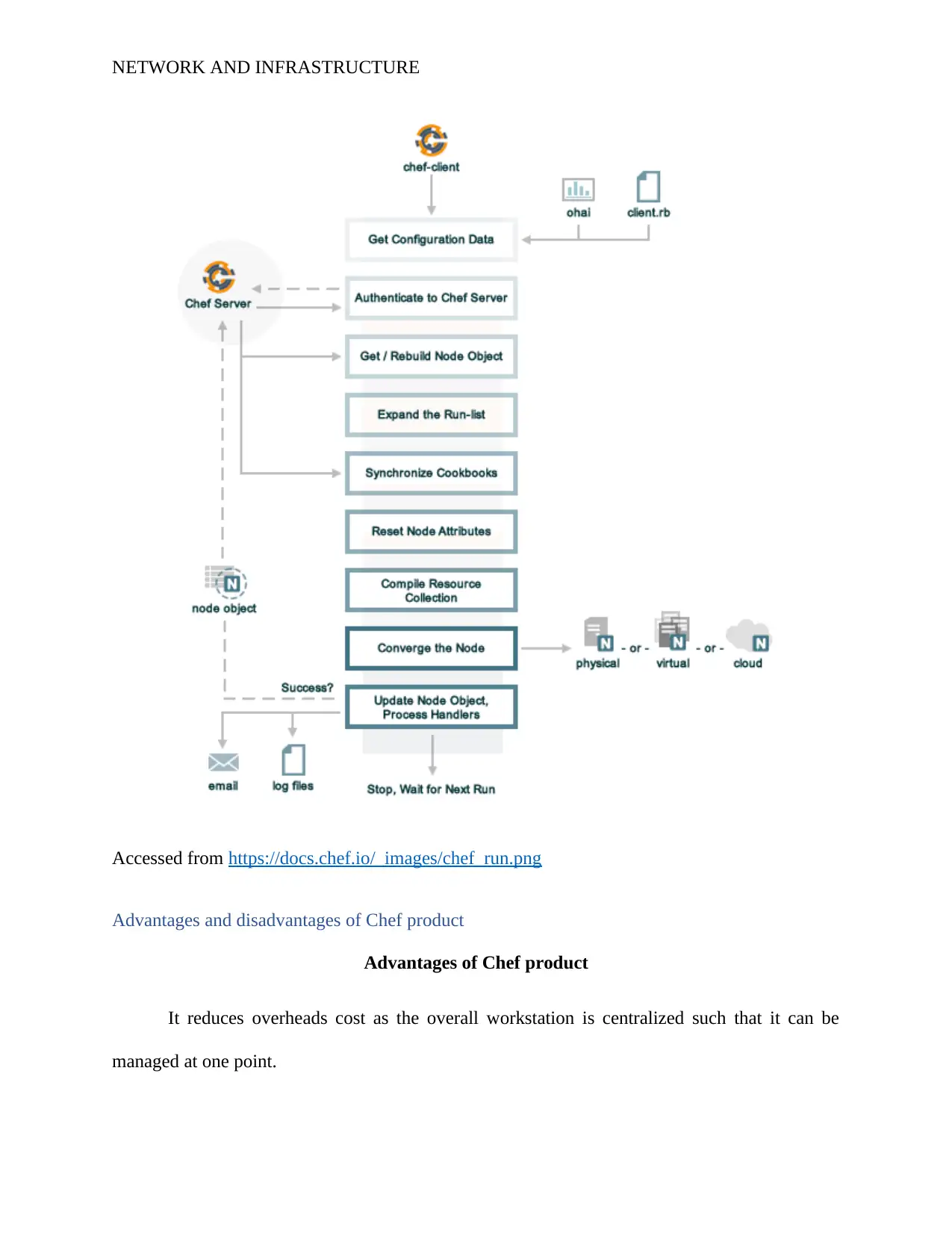
NETWORK AND INFRASTRUCTURE
Accessed from https://docs.chef.io/_images/chef_run.png
Advantages and disadvantages of Chef product
Advantages of Chef product
It reduces overheads cost as the overall workstation is centralized such that it can be
managed at one point.
Accessed from https://docs.chef.io/_images/chef_run.png
Advantages and disadvantages of Chef product
Advantages of Chef product
It reduces overheads cost as the overall workstation is centralized such that it can be
managed at one point.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





