Improving Network Security: Multiple Gateways for Intrusion Detection
VerifiedAdded on 2020/04/21
|9
|1509
|85
Report
AI Summary
This report delves into the application of multiple gateways to enhance Network Intrusion Detection Systems (NIDS), specifically within corporate environments. The introduction highlights the increasing need for sophisticated defense mechanisms against distributed Denial of Service (DDoS) attacks and the limitations of traditional security measures. The project description outlines the shift in attack focus from host bodies to operating systems and the importance of network auditing. The report then identifies key problems associated with NIDS, such as its incompatibility with Intrusion Prevention Systems (IPS), failure to catch all intruders, and the need for proper integration with existing knowledge. The evaluation section details the criteria for assessing NIDS, including feasibility, cost-effectiveness, and unbiasedness, along with a step-by-step process for evaluating the system. The project management section outlines the steps necessary for managing the project. The objective emphasizes the NIDS's role in detecting attacks, providing information-level security, ensuring secured monitoring, and delivering perimeter network and DMZ protection. The report concludes by emphasizing the need for a mechanism that allows network security officers to customize events and gather only relevant network-level data, with references to key research papers supporting the concepts discussed.

Running head: NETWORK INTRUSION DETECTION SYSTEM
Exploring the Usage of Multiple Gateways for Network Intrusion Detection System (NIDS)
Name of the student:
Name of the university:
Exploring the Usage of Multiple Gateways for Network Intrusion Detection System (NIDS)
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK INTRUSION DETECTION SYSTEM
Introduction
In order to improve the multiple gateways for improving the defense system against
distributed Denial of services attacks in a corporate network intrusion detection system or
approach is required to be adopted by the system developers. Each break-in cannot be detected
manually or eventually including the holes and new attacks as well (Joshi and Pimprale 2013).
Due to lack of defense power the current network systems used in the business organizations are
getting affected each day (Beigi Mohammadi et al. 2014). Thus, in order to mitigate these issues
with multiple layers different design philosophies and active intrusion detection system is needed
to be developed by the network analysts.
Description of a project
Nowadays, network based intrusion detection system has become one of the common and
sophisticated attacks. Due to this reason the network based intrusion detection system has
changes their domain of attack to the operating system from the host body. With the help of
network auditing wide range of information could be produced and due to this reason the system
is currently facing severe challenges those are required to be detected and diminished as well
(Bul'ajoul, James and Pannu 2015). By using the state transition diagram and state transition
analysis technique the state as well as transition could be characterized appropriately. Through a
hyper graph model the target network model can be protected accordingly. In order to carry out
the information transition particularly in the TCP/IP networks are the most important channel of
transition (Faisal et al. 2015). However, the growing rates of security threats have shifted the
focus of network analysts from internet to the operating system.
Introduction
In order to improve the multiple gateways for improving the defense system against
distributed Denial of services attacks in a corporate network intrusion detection system or
approach is required to be adopted by the system developers. Each break-in cannot be detected
manually or eventually including the holes and new attacks as well (Joshi and Pimprale 2013).
Due to lack of defense power the current network systems used in the business organizations are
getting affected each day (Beigi Mohammadi et al. 2014). Thus, in order to mitigate these issues
with multiple layers different design philosophies and active intrusion detection system is needed
to be developed by the network analysts.
Description of a project
Nowadays, network based intrusion detection system has become one of the common and
sophisticated attacks. Due to this reason the network based intrusion detection system has
changes their domain of attack to the operating system from the host body. With the help of
network auditing wide range of information could be produced and due to this reason the system
is currently facing severe challenges those are required to be detected and diminished as well
(Bul'ajoul, James and Pannu 2015). By using the state transition diagram and state transition
analysis technique the state as well as transition could be characterized appropriately. Through a
hyper graph model the target network model can be protected accordingly. In order to carry out
the information transition particularly in the TCP/IP networks are the most important channel of
transition (Faisal et al. 2015). However, the growing rates of security threats have shifted the
focus of network analysts from internet to the operating system.

2NETWORK INTRUSION DETECTION SYSTEM
Intrusion detection is referred to as an approach towards security which is eventually
moving towards the networked environment. In order to detect the masqueraders and misfeasors
within a standalone system the network owners have started using the intrusion detection
approach (Modi et al. 2013). However, in the current days the focus of the intrusion detection
has been shifted towards the networks.
Explanation of problems
Network intrusion detection system is very much important to be adopted for any
business organization however many problems are also associated to it those are needed to be
mitigated for successful implementation of the processes. The problems associated to the system
are as follows:
NIDS is not applicable for IPS: The system has the ability to drop different packets
which defines the known incorrect traffic again it can allow the good also. The activities of the
IDS are almost similar to the firewall it means that, the IDS detects the anomalies, traffic
violation, malicious traffic etc those are not at all helpful from the IPS perspectives (Lin, Ke and
Tsai 2015). This act as an enforcement tools instead of visibility tool which is a major identified
issue.
Does not focus on IDS catches: The IDS fail to catch the intruders those are another
major problems associated to it. It is defined that, the company would be failing to gain
information from the system. On the other hand lacks of security, well defined management
interface are the other problems associated to this.
Intrusion detection is referred to as an approach towards security which is eventually
moving towards the networked environment. In order to detect the masqueraders and misfeasors
within a standalone system the network owners have started using the intrusion detection
approach (Modi et al. 2013). However, in the current days the focus of the intrusion detection
has been shifted towards the networks.
Explanation of problems
Network intrusion detection system is very much important to be adopted for any
business organization however many problems are also associated to it those are needed to be
mitigated for successful implementation of the processes. The problems associated to the system
are as follows:
NIDS is not applicable for IPS: The system has the ability to drop different packets
which defines the known incorrect traffic again it can allow the good also. The activities of the
IDS are almost similar to the firewall it means that, the IDS detects the anomalies, traffic
violation, malicious traffic etc those are not at all helpful from the IPS perspectives (Lin, Ke and
Tsai 2015). This act as an enforcement tools instead of visibility tool which is a major identified
issue.
Does not focus on IDS catches: The IDS fail to catch the intruders those are another
major problems associated to it. It is defined that, the company would be failing to gain
information from the system. On the other hand lacks of security, well defined management
interface are the other problems associated to this.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3NETWORK INTRUSION DETECTION SYSTEM
None IDS could work out of box: The IDS must have the ability to develop proper
linkage with the existing knowledge. However, issues are associated to operating system and
critical organizational management. Due to lack of these approaches the IDS alerts are not
prioritized which is another problem.
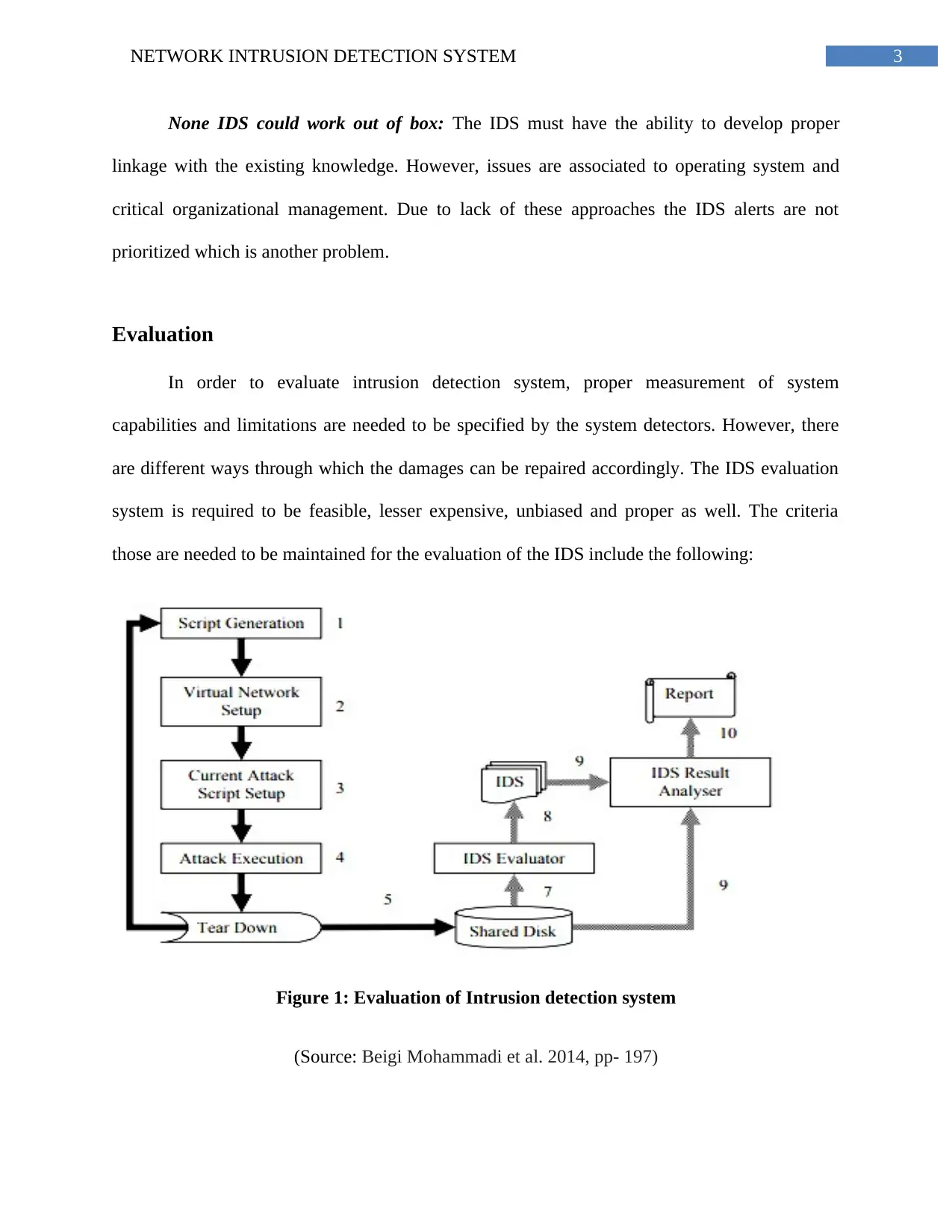
Evaluation
In order to evaluate intrusion detection system, proper measurement of system
capabilities and limitations are needed to be specified by the system detectors. However, there
are different ways through which the damages can be repaired accordingly. The IDS evaluation
system is required to be feasible, lesser expensive, unbiased and proper as well. The criteria
those are needed to be maintained for the evaluation of the IDS include the following:
Figure 1: Evaluation of Intrusion detection system
(Source: Beigi Mohammadi et al. 2014, pp- 197)
None IDS could work out of box: The IDS must have the ability to develop proper
linkage with the existing knowledge. However, issues are associated to operating system and
critical organizational management. Due to lack of these approaches the IDS alerts are not
prioritized which is another problem.
Evaluation
In order to evaluate intrusion detection system, proper measurement of system
capabilities and limitations are needed to be specified by the system detectors. However, there
are different ways through which the damages can be repaired accordingly. The IDS evaluation
system is required to be feasible, lesser expensive, unbiased and proper as well. The criteria
those are needed to be maintained for the evaluation of the IDS include the following:
Figure 1: Evaluation of Intrusion detection system
(Source: Beigi Mohammadi et al. 2014, pp- 197)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK INTRUSION DETECTION SYSTEM
The process of evaluation starts from generating scripts, after visualizing the network
setup, each current attack setup are also required to setup (Singh, Kumar Singla 2015). After
developing the current attack setup it is necessary for the network system developers to attack
the execution approach. After these with the help of the shared disk, IDS evaluators, and tear
down IDS proper IDS result analyzers and reports are also evaluated.
Management of the project
For managing the project the steps those must be followed accordingly include the
following:
The process must choose accurate malware for attacking the target system
including a set of configuration relevant to the target system
Over the virtual attacker the set of evaluation system should be configured
Within the shared disk the recorded information must be saved accordingly
The evaluation system must have the ability to generate the report (Bul'ajoul,
James and Pannu 2015)
To the tested IDS, the evaluators must put the traffic accurately
Objective
The main goal of the Network Intrusion Detection System (NIDS) is based upon certain
requirements such as the following:
The objective of NIDS is to detect the attacks properly
To provide information level attacks that has accurate success throughout
To provide secured monitoring, reporting, corrective measures
The process of evaluation starts from generating scripts, after visualizing the network
setup, each current attack setup are also required to setup (Singh, Kumar Singla 2015). After
developing the current attack setup it is necessary for the network system developers to attack
the execution approach. After these with the help of the shared disk, IDS evaluators, and tear
down IDS proper IDS result analyzers and reports are also evaluated.
Management of the project
For managing the project the steps those must be followed accordingly include the
following:
The process must choose accurate malware for attacking the target system
including a set of configuration relevant to the target system
Over the virtual attacker the set of evaluation system should be configured
Within the shared disk the recorded information must be saved accordingly
The evaluation system must have the ability to generate the report (Bul'ajoul,
James and Pannu 2015)
To the tested IDS, the evaluators must put the traffic accurately
Objective
The main goal of the Network Intrusion Detection System (NIDS) is based upon certain
requirements such as the following:
The objective of NIDS is to detect the attacks properly
To provide information level attacks that has accurate success throughout
To provide secured monitoring, reporting, corrective measures
5NETWORK INTRUSION DETECTION SYSTEM
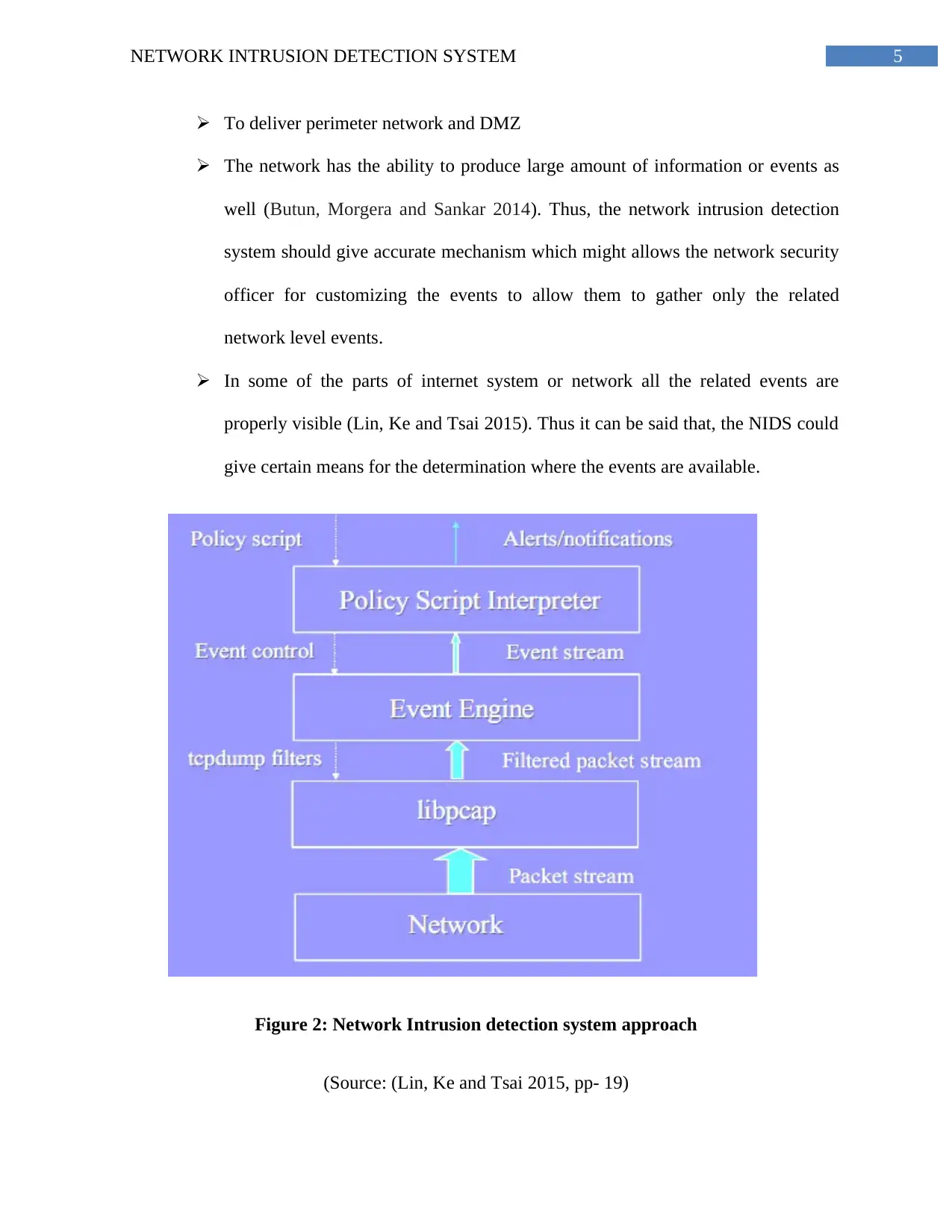
To deliver perimeter network and DMZ
The network has the ability to produce large amount of information or events as
well (Butun, Morgera and Sankar 2014). Thus, the network intrusion detection
system should give accurate mechanism which might allows the network security
officer for customizing the events to allow them to gather only the related
network level events.
In some of the parts of internet system or network all the related events are
properly visible (Lin, Ke and Tsai 2015). Thus it can be said that, the NIDS could
give certain means for the determination where the events are available.
Figure 2: Network Intrusion detection system approach
(Source: (Lin, Ke and Tsai 2015, pp- 19)
To deliver perimeter network and DMZ
The network has the ability to produce large amount of information or events as
well (Butun, Morgera and Sankar 2014). Thus, the network intrusion detection
system should give accurate mechanism which might allows the network security
officer for customizing the events to allow them to gather only the related
network level events.
In some of the parts of internet system or network all the related events are
properly visible (Lin, Ke and Tsai 2015). Thus it can be said that, the NIDS could
give certain means for the determination where the events are available.
Figure 2: Network Intrusion detection system approach
(Source: (Lin, Ke and Tsai 2015, pp- 19)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK INTRUSION DETECTION SYSTEM
A minimum amount of events are needed to be generated by the NIDS. It is expected that
if IDS solution could sometimes take advantages of a TAP or SPAN, for analyzing the inline
traffic, then the objectives or purpose of NIDS will be able to serve as per the requirement of the
project.
A minimum amount of events are needed to be generated by the NIDS. It is expected that
if IDS solution could sometimes take advantages of a TAP or SPAN, for analyzing the inline
traffic, then the objectives or purpose of NIDS will be able to serve as per the requirement of the
project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK INTRUSION DETECTION SYSTEM
References
Beigi Mohammadi, N., Mišić, J., Mišić, V.B. and Khazaei, H., 2014. A framework for intrusion
detection system in advanced metering infrastructure. Security and Communication
Networks, 7(1), pp.195-205.
Bul'ajoul, W., James, A. and Pannu, M., 2015. Improving network intrusion detection system
performance through quality of service configuration and parallel technology. Journal of
Computer and System Sciences, 81(6), pp.981-999.
Butun, I., Morgera, S.D. and Sankar, R., 2014. A survey of intrusion detection systems in
wireless sensor networks. IEEE communications surveys & tutorials, 16(1), pp.266-282.
Faisal, M.A., Aung, Z., Williams, J.R. and Sanchez, A., 2015. Data-stream-based intrusion
detection system for advanced metering infrastructure in smart grid: A feasibility study. IEEE
Systems journal, 9(1), pp.31-44.
Joshi, S.A. and Pimprale, V.S., 2013. Network intrusion detection system (nids) based on data
mining. International Journal of Engineering Science and Innovative Technology (IJESIT), 2(1),
pp.95-98.
Lin, W.C., Ke, S.W. and Tsai, C.F., 2015. CANN: An intrusion detection system based on
combining cluster centers and nearest neighbors. Knowledge-based systems, 78, pp.13-21.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A. and Rajarajan, M., 2013. A survey of
intrusion detection techniques in cloud. Journal of Network and Computer Applications, 36(1),
pp.42-57.
References
Beigi Mohammadi, N., Mišić, J., Mišić, V.B. and Khazaei, H., 2014. A framework for intrusion
detection system in advanced metering infrastructure. Security and Communication
Networks, 7(1), pp.195-205.
Bul'ajoul, W., James, A. and Pannu, M., 2015. Improving network intrusion detection system
performance through quality of service configuration and parallel technology. Journal of
Computer and System Sciences, 81(6), pp.981-999.
Butun, I., Morgera, S.D. and Sankar, R., 2014. A survey of intrusion detection systems in
wireless sensor networks. IEEE communications surveys & tutorials, 16(1), pp.266-282.
Faisal, M.A., Aung, Z., Williams, J.R. and Sanchez, A., 2015. Data-stream-based intrusion
detection system for advanced metering infrastructure in smart grid: A feasibility study. IEEE
Systems journal, 9(1), pp.31-44.
Joshi, S.A. and Pimprale, V.S., 2013. Network intrusion detection system (nids) based on data
mining. International Journal of Engineering Science and Innovative Technology (IJESIT), 2(1),
pp.95-98.
Lin, W.C., Ke, S.W. and Tsai, C.F., 2015. CANN: An intrusion detection system based on
combining cluster centers and nearest neighbors. Knowledge-based systems, 78, pp.13-21.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A. and Rajarajan, M., 2013. A survey of
intrusion detection techniques in cloud. Journal of Network and Computer Applications, 36(1),
pp.42-57.
8NETWORK INTRUSION DETECTION SYSTEM
Singh, R., Kumar, H. and Singla, R.K., 2015. An intrusion detection system using network traffic
profiling and online sequential extreme learning machine. Expert Systems with
Applications, 42(22), pp.8609-8624.
Singh, R., Kumar, H. and Singla, R.K., 2015. An intrusion detection system using network traffic
profiling and online sequential extreme learning machine. Expert Systems with
Applications, 42(22), pp.8609-8624.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





