Network Operating System: Installation and Disaster Recovery Report
VerifiedAdded on 2021/01/02
|16
|4535
|75
Report
AI Summary
This report provides a comprehensive analysis of network operating systems (NOS), covering vendor specifications, hardware compatibility, and the installation and configuration of both client and server operating systems. It delves into cost analysis, outlining specialized devices and the roles of key personnel in a disaster recovery plan. The report details backup and data storage requirements, including the implementation of a RAID system. Furthermore, it analyzes tools available for performance monitoring, network performance under load conditions, event log monitoring, and optimization techniques. The report provides a practical guide for setting up and managing a network operating system, addressing critical aspects such as domain configuration, client-server integration, and PXE network environment installation. It also includes cost analysis and role of key personnel in disaster recovery.

Network Operating
System
System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
1.1 Describe a network operating system in terms of vendor’s specification and hardware
compatibility...............................................................................................................................1
1.2 Installation and configuration of client operating system and a server operating system.....2
1.3 Installation of a network operating system...........................................................................5
TASK 2............................................................................................................................................5
2.1 Cost analysis, details of specialized devices and an outline of roles of key personnel, as
part of a disaster recovery plan...................................................................................................5
2.2 Requirements for back ups and data storage while catastrophic failure...............................6
TASK 3............................................................................................................................................8
3.1 Analyse the tools available for the performance monitoring of a network operating system
.....................................................................................................................................................8
3.2 Network performance and reliability under load conditions.................................................9
4.1 Monitoring event logs and programmes.............................................................................10
4.2 Tools available for monitoring and optimising of network operating system performance
...................................................................................................................................................10
CONCLUSION.............................................................................................................................11
REFERENCES..............................................................................................................................13
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
1.1 Describe a network operating system in terms of vendor’s specification and hardware
compatibility...............................................................................................................................1
1.2 Installation and configuration of client operating system and a server operating system.....2
1.3 Installation of a network operating system...........................................................................5
TASK 2............................................................................................................................................5
2.1 Cost analysis, details of specialized devices and an outline of roles of key personnel, as
part of a disaster recovery plan...................................................................................................5
2.2 Requirements for back ups and data storage while catastrophic failure...............................6
TASK 3............................................................................................................................................8
3.1 Analyse the tools available for the performance monitoring of a network operating system
.....................................................................................................................................................8
3.2 Network performance and reliability under load conditions.................................................9
4.1 Monitoring event logs and programmes.............................................................................10
4.2 Tools available for monitoring and optimising of network operating system performance
...................................................................................................................................................10
CONCLUSION.............................................................................................................................11
REFERENCES..............................................................................................................................13

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Operating system is software which allows user to execute applications. It acts as a
interface between user and hardware. Network operating system is an operating system which
connects devices and computer to local area network (Network Operating System (NOS), 2018).
This report covers requirement of vendor, hardware specifications and installation of client and
server operating system. It also provides joining of computer with server and describing risks
involved in it. Approximate analysis of cost and role of manager is discussed. Backup followed
by storage requirements are covered by implementing RAID system. Performance of monitoring,
event logs and different tools used in it are analyzed.
TASK 1
1.1 Describe a network operating system in terms of vendor’s specification and hardware
compatibility.
Network operating system: For network device like switch, routers, hub or firewall a
specific operating system is required, it is known as network operating system. For providing
printer access and shared file between multiple computers present within network an operating
system is is connected to computer networking(Anderson and Vongpanitlerd, 2013).
Vendor's specification: Toner partner limited is small company looking for expansion of
its organization for which they need to hire 50 employees for which they require client and
server operating system for accumulating 50 client systems.
Hardware compatibility:
Processor: Minimum 2GHz or higher
RAM: 16GB
Hard Drive: 250 GB or more
Monitor: 19'' LCD, desktop only
Operating System: Windows 8 or higher
Backup Device: USB Flash drive or External hard drive
Wireless adapter (Wi-Fi) or Ethernet connection (LAN)
Above are hardware specifications to handle vendors' requirement. All specifications mentioned
above are enough for efficiently expanding organization.
1
Operating system is software which allows user to execute applications. It acts as a
interface between user and hardware. Network operating system is an operating system which
connects devices and computer to local area network (Network Operating System (NOS), 2018).
This report covers requirement of vendor, hardware specifications and installation of client and
server operating system. It also provides joining of computer with server and describing risks
involved in it. Approximate analysis of cost and role of manager is discussed. Backup followed
by storage requirements are covered by implementing RAID system. Performance of monitoring,
event logs and different tools used in it are analyzed.
TASK 1
1.1 Describe a network operating system in terms of vendor’s specification and hardware
compatibility.
Network operating system: For network device like switch, routers, hub or firewall a
specific operating system is required, it is known as network operating system. For providing
printer access and shared file between multiple computers present within network an operating
system is is connected to computer networking(Anderson and Vongpanitlerd, 2013).
Vendor's specification: Toner partner limited is small company looking for expansion of
its organization for which they need to hire 50 employees for which they require client and
server operating system for accumulating 50 client systems.
Hardware compatibility:
Processor: Minimum 2GHz or higher
RAM: 16GB
Hard Drive: 250 GB or more
Monitor: 19'' LCD, desktop only
Operating System: Windows 8 or higher
Backup Device: USB Flash drive or External hard drive
Wireless adapter (Wi-Fi) or Ethernet connection (LAN)
Above are hardware specifications to handle vendors' requirement. All specifications mentioned
above are enough for efficiently expanding organization.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.2 Installation and configuration of client operating system and a server operating system
Installation and configuration of client operating system: To start with installation, a
system is required in which windows 10 will be installed(Botta, Dainotti and Pescapé, 2012).
Following are steps for installation:
1. Start computer and if message appears “missing operating system” then press F1 to boot
and F2 to enter into system utility.
2. Open DVD driver and insert Cd which is having operating system and restart computer
3. A system is started a message pop up “press key to boot from Cd or DVD for installing
operating system.
If message do not appear on screen then restart system and when black screen will appear
press F10 OR F11 to enter into BIOS. Access sequence of boot and check list if DVD do
not appear at top then move it to top if possible. If this do not happen then disable drives
like hard drive so that DVD can come on top. Now save changes made and exit BIOS.
Restart system and follow instructions to install operating system
If message do not pop up then check DVD drive is inserted properly.
4. Installation will be started and files will be copied. Then select language option will
appear on screen as per requirement select one. And it will appear on screen. Then
click on next.
5. Next screen will have option install now, click on it. Select version either 32 or 64
bits and then click next.
6. License agreement will be shown on next screen. Read it and click on “I accept
license agreement” and then click next.
7. Next screen will ask to for specifying partition where OS will be installed. Select a
partition and click next. Copying of files will start and will take time.
8. When it is done then computer will restart. When it will start then it will ask for
username and product key. After typing details click on next.
9. Now give name to computer and password (it's optional). And click next.
10. Now screen will show select time zone, time and date, after doing this click on next.
11. Welcome message will appear which take to desktop.
Installation and configuration of server operating system:
2
Installation and configuration of client operating system: To start with installation, a
system is required in which windows 10 will be installed(Botta, Dainotti and Pescapé, 2012).
Following are steps for installation:
1. Start computer and if message appears “missing operating system” then press F1 to boot
and F2 to enter into system utility.
2. Open DVD driver and insert Cd which is having operating system and restart computer
3. A system is started a message pop up “press key to boot from Cd or DVD for installing
operating system.
If message do not appear on screen then restart system and when black screen will appear
press F10 OR F11 to enter into BIOS. Access sequence of boot and check list if DVD do
not appear at top then move it to top if possible. If this do not happen then disable drives
like hard drive so that DVD can come on top. Now save changes made and exit BIOS.
Restart system and follow instructions to install operating system
If message do not pop up then check DVD drive is inserted properly.
4. Installation will be started and files will be copied. Then select language option will
appear on screen as per requirement select one. And it will appear on screen. Then
click on next.
5. Next screen will have option install now, click on it. Select version either 32 or 64
bits and then click next.
6. License agreement will be shown on next screen. Read it and click on “I accept
license agreement” and then click next.
7. Next screen will ask to for specifying partition where OS will be installed. Select a
partition and click next. Copying of files will start and will take time.
8. When it is done then computer will restart. When it will start then it will ask for
username and product key. After typing details click on next.
9. Now give name to computer and password (it's optional). And click next.
10. Now screen will show select time zone, time and date, after doing this click on next.
11. Welcome message will appear which take to desktop.
Installation and configuration of server operating system:
2

1. Insert DVD with windows server 2016 and reboot system. Message will pop up on screen
press any key to boot.
2. Installation will start and screen will appear in which language will be selected. Then
click on next
3. Click on install now, a window will appear in which version will be asked, select
windows server 2016 Enterprise with service pack1. Click on continue
4. Next screen will present license terms, click on I agree and click next. Select partition in
which server will be installed, click next and files will be copied.
5. Once files are copied system will restart. Some installations will be going after restart.
And then administrator's password will be asked. Enter details and press enter.
DHCP (Dynamic Host Configuration Protocol): IP addresses are assigned to client computers
to reduce configuration activity(Brettel and et. al., 2014) . IP addresses are present on server
machine which are stored in database. Conflict of IP's should not occur so manual IP addresses
are not provided instead of that DHCP server is used.
Configuration of DHCP Server to provide IP address to Client Operating system:
1. Visit website of DHCP server and download “DHCP Server V2.5.2”.
2. Now excerpt content from downloaded file and double click on dhcpwiz.exe file.
3. DHCP configuration wizard will be opened click on next.
4. Window with Network interface card will be shown in which class c (like 192.168.1.1) IP
addresses will be mentioned, select it and click on next.
5. DHCP server supports more protocols select other protocol like http whichever is
required and click on next.
6. Now configure DHCP interface i.e. range of IP addresses and lease time with help of
advanced option select gateway, subnet mask, WINS and DNS. If these are not provided
then DHCP will automatically take values depending upon network interface card. Press
next.
7. Write INI file and pop up will appear INS file is written successfully. Press next.
8. Window of DHCP server will appear in which status is not installed. Click on install
option to continue, status will be changed to stop. Click on next.
9. DHCP server program will start by clicking on start, status will change to running. To
know current status of installation check 127.0.0.1 in browser.
3
press any key to boot.
2. Installation will start and screen will appear in which language will be selected. Then
click on next
3. Click on install now, a window will appear in which version will be asked, select
windows server 2016 Enterprise with service pack1. Click on continue
4. Next screen will present license terms, click on I agree and click next. Select partition in
which server will be installed, click next and files will be copied.
5. Once files are copied system will restart. Some installations will be going after restart.
And then administrator's password will be asked. Enter details and press enter.
DHCP (Dynamic Host Configuration Protocol): IP addresses are assigned to client computers
to reduce configuration activity(Brettel and et. al., 2014) . IP addresses are present on server
machine which are stored in database. Conflict of IP's should not occur so manual IP addresses
are not provided instead of that DHCP server is used.
Configuration of DHCP Server to provide IP address to Client Operating system:
1. Visit website of DHCP server and download “DHCP Server V2.5.2”.
2. Now excerpt content from downloaded file and double click on dhcpwiz.exe file.
3. DHCP configuration wizard will be opened click on next.
4. Window with Network interface card will be shown in which class c (like 192.168.1.1) IP
addresses will be mentioned, select it and click on next.
5. DHCP server supports more protocols select other protocol like http whichever is
required and click on next.
6. Now configure DHCP interface i.e. range of IP addresses and lease time with help of
advanced option select gateway, subnet mask, WINS and DNS. If these are not provided
then DHCP will automatically take values depending upon network interface card. Press
next.
7. Write INI file and pop up will appear INS file is written successfully. Press next.
8. Window of DHCP server will appear in which status is not installed. Click on install
option to continue, status will be changed to stop. Click on next.
9. DHCP server program will start by clicking on start, status will change to running. To
know current status of installation check 127.0.0.1 in browser.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Installation of Active Directory Domain Services role: Go to command prompt and write
following command: dcpromo /unattend:<unattendfile>
Here in place of unattendfile it can be replaced with Dcpromo.exe unattend file.
This command will install active directory domain services role and server will be promoted to
domain controller by settings in unattend file(Castells, 2011).
Installation of Domain Name Server (DNS) role: Installation of DNS server role is shown
below and these commands are typed in command prompt:
1. start /w ocsetup DNS-Server-Core-Role
(/w will allow to stay in command prompt until installation is completed otherwise it will be not
indicated that process of installation is complete.
2. Type dnscmd at command prompt to configure DNS zone or use DNS MMC snap-in.
Setting up Domain Name: Domain name is selected. It can be either toner.com or
innovativetonner.com.
Now check whether domain is selected or not. To check availability of domain search for
domain names with help of domain registrar. If chosen domain name is available then
owning it.
Now find a registrar. Number of options are available from which search can be made
and check who is offering best price for registration. To attract customers, registrars are
giving add on services so on that basis selection can be made.
When registrar is shortlisted, check for domain on website of registrar . If it is
addressable for registration then complete registration process.
When this is done, go for payment to registrar.
In this way Toner Partner limited can have their own domain name by which they can be
searched on internet.
Join Client to server: Ping server from client's system using server's hostname. If it is not done
then it wont be possible to join client and server (Wang and et. al., 2014).
Set server's IP on client computer as DNS entry.
Go to start button and write domain. Then click on join a domain or rename your system.
Go to about page and click on select join a domain given under organization. Write
domain name and click on next.
4
following command: dcpromo /unattend:<unattendfile>
Here in place of unattendfile it can be replaced with Dcpromo.exe unattend file.
This command will install active directory domain services role and server will be promoted to
domain controller by settings in unattend file(Castells, 2011).
Installation of Domain Name Server (DNS) role: Installation of DNS server role is shown
below and these commands are typed in command prompt:
1. start /w ocsetup DNS-Server-Core-Role
(/w will allow to stay in command prompt until installation is completed otherwise it will be not
indicated that process of installation is complete.
2. Type dnscmd at command prompt to configure DNS zone or use DNS MMC snap-in.
Setting up Domain Name: Domain name is selected. It can be either toner.com or
innovativetonner.com.
Now check whether domain is selected or not. To check availability of domain search for
domain names with help of domain registrar. If chosen domain name is available then
owning it.
Now find a registrar. Number of options are available from which search can be made
and check who is offering best price for registration. To attract customers, registrars are
giving add on services so on that basis selection can be made.
When registrar is shortlisted, check for domain on website of registrar . If it is
addressable for registration then complete registration process.
When this is done, go for payment to registrar.
In this way Toner Partner limited can have their own domain name by which they can be
searched on internet.
Join Client to server: Ping server from client's system using server's hostname. If it is not done
then it wont be possible to join client and server (Wang and et. al., 2014).
Set server's IP on client computer as DNS entry.
Go to start button and write domain. Then click on join a domain or rename your system.
Go to about page and click on select join a domain given under organization. Write
domain name and click on next.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Now enter domain credentials and system will be restarted. Now log in into other user
options by doing this logging will be on domain rather than local computer.
Use credentials to log in into system and open active directories and computers on
windows server. Drag new computers into OU where they will be located physically
(Cole, 2011).
In this way windows 10 systems will be joined with window server 2016 within Toner Partner
Limited.
1.3 Installation of a network operating system
Installation steps:
1. PXE network environment should be properly set.
2. Restart server, boot process will begin.
3. Ensure that PXE boot is not disabled.
To enter into BIOS press F10 or F11
Go to advanced options present in menu of BIOS.
BIOS setup utility network stack appears on screen. This will result in resetting BIOS.
4. Press F8 key on BIOS to signify a boot device which is temporary or F12 to PXE.
5. Select PXE boot port on boot device menu and click enter
6. To complete installation, follow prompts shown on screen.
TASK 2
2.1 Cost analysis, details of specialized devices and an outline of roles of key personnel, as part
of a disaster recovery plan
For meeting requirements of Toner Partner limited a cost analysis is presented beneath:
Items Expected Price (£)
Processor 2628.5
RAM 1212.5
Hard Drive 2916
Monitor,keyboard and other peripherals 3905.5
Operating System 3271.5
5
options by doing this logging will be on domain rather than local computer.
Use credentials to log in into system and open active directories and computers on
windows server. Drag new computers into OU where they will be located physically
(Cole, 2011).
In this way windows 10 systems will be joined with window server 2016 within Toner Partner
Limited.
1.3 Installation of a network operating system
Installation steps:
1. PXE network environment should be properly set.
2. Restart server, boot process will begin.
3. Ensure that PXE boot is not disabled.
To enter into BIOS press F10 or F11
Go to advanced options present in menu of BIOS.
BIOS setup utility network stack appears on screen. This will result in resetting BIOS.
4. Press F8 key on BIOS to signify a boot device which is temporary or F12 to PXE.
5. Select PXE boot port on boot device menu and click enter
6. To complete installation, follow prompts shown on screen.
TASK 2
2.1 Cost analysis, details of specialized devices and an outline of roles of key personnel, as part
of a disaster recovery plan
For meeting requirements of Toner Partner limited a cost analysis is presented beneath:
Items Expected Price (£)
Processor 2628.5
RAM 1212.5
Hard Drive 2916
Monitor,keyboard and other peripherals 3905.5
Operating System 3271.5
5
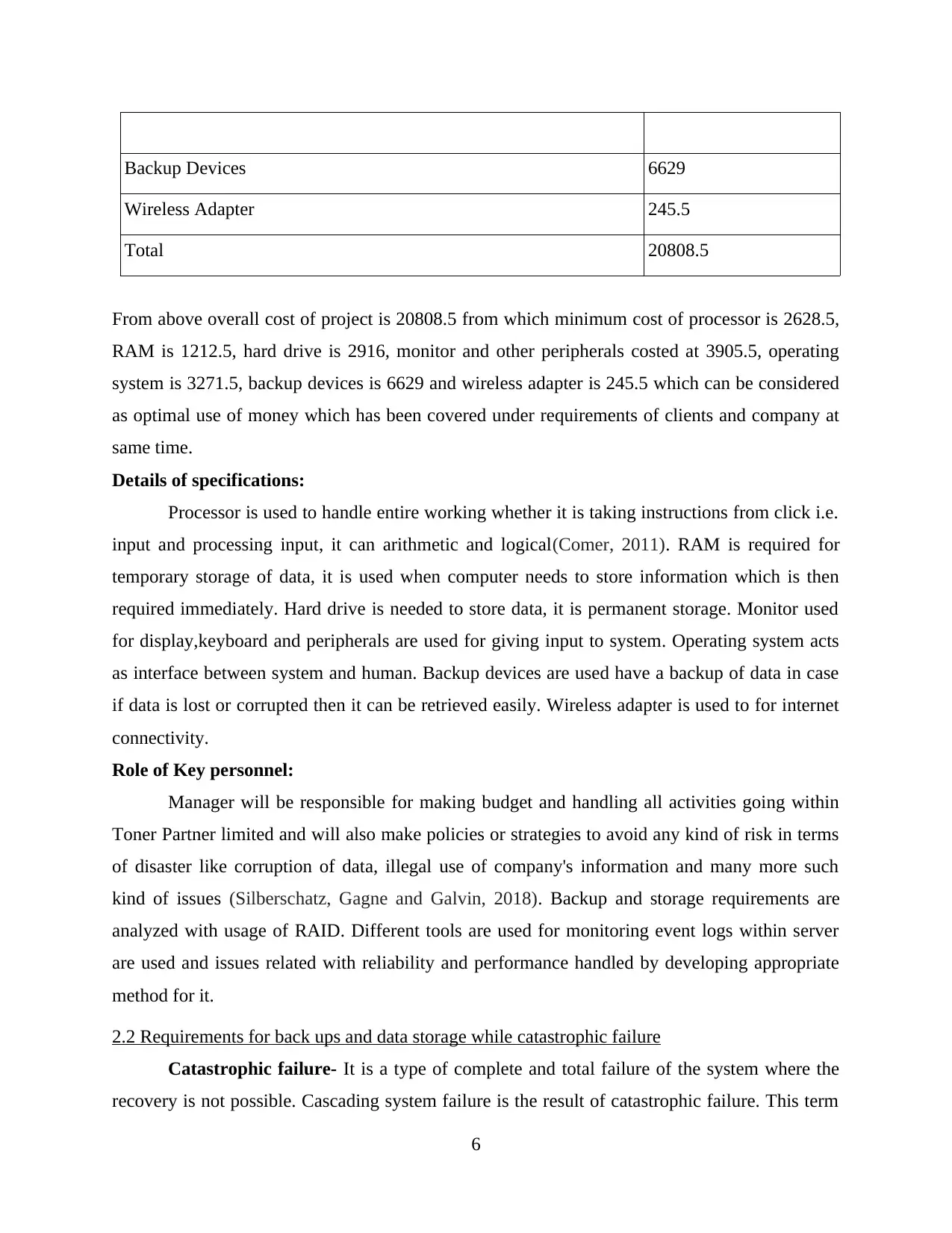
Backup Devices 6629
Wireless Adapter 245.5
Total 20808.5
From above overall cost of project is 20808.5 from which minimum cost of processor is 2628.5,
RAM is 1212.5, hard drive is 2916, monitor and other peripherals costed at 3905.5, operating
system is 3271.5, backup devices is 6629 and wireless adapter is 245.5 which can be considered
as optimal use of money which has been covered under requirements of clients and company at
same time.
Details of specifications:
Processor is used to handle entire working whether it is taking instructions from click i.e.
input and processing input, it can arithmetic and logical(Comer, 2011). RAM is required for
temporary storage of data, it is used when computer needs to store information which is then
required immediately. Hard drive is needed to store data, it is permanent storage. Monitor used
for display,keyboard and peripherals are used for giving input to system. Operating system acts
as interface between system and human. Backup devices are used have a backup of data in case
if data is lost or corrupted then it can be retrieved easily. Wireless adapter is used to for internet
connectivity.
Role of Key personnel:
Manager will be responsible for making budget and handling all activities going within
Toner Partner limited and will also make policies or strategies to avoid any kind of risk in terms
of disaster like corruption of data, illegal use of company's information and many more such
kind of issues (Silberschatz, Gagne and Galvin, 2018). Backup and storage requirements are
analyzed with usage of RAID. Different tools are used for monitoring event logs within server
are used and issues related with reliability and performance handled by developing appropriate
method for it.
2.2 Requirements for back ups and data storage while catastrophic failure
Catastrophic failure- It is a type of complete and total failure of the system where the
recovery is not possible. Cascading system failure is the result of catastrophic failure. This term
6
Wireless Adapter 245.5
Total 20808.5
From above overall cost of project is 20808.5 from which minimum cost of processor is 2628.5,
RAM is 1212.5, hard drive is 2916, monitor and other peripherals costed at 3905.5, operating
system is 3271.5, backup devices is 6629 and wireless adapter is 245.5 which can be considered
as optimal use of money which has been covered under requirements of clients and company at
same time.
Details of specifications:
Processor is used to handle entire working whether it is taking instructions from click i.e.
input and processing input, it can arithmetic and logical(Comer, 2011). RAM is required for
temporary storage of data, it is used when computer needs to store information which is then
required immediately. Hard drive is needed to store data, it is permanent storage. Monitor used
for display,keyboard and peripherals are used for giving input to system. Operating system acts
as interface between system and human. Backup devices are used have a backup of data in case
if data is lost or corrupted then it can be retrieved easily. Wireless adapter is used to for internet
connectivity.
Role of Key personnel:
Manager will be responsible for making budget and handling all activities going within
Toner Partner limited and will also make policies or strategies to avoid any kind of risk in terms
of disaster like corruption of data, illegal use of company's information and many more such
kind of issues (Silberschatz, Gagne and Galvin, 2018). Backup and storage requirements are
analyzed with usage of RAID. Different tools are used for monitoring event logs within server
are used and issues related with reliability and performance handled by developing appropriate
method for it.
2.2 Requirements for back ups and data storage while catastrophic failure
Catastrophic failure- It is a type of complete and total failure of the system where the
recovery is not possible. Cascading system failure is the result of catastrophic failure. This term
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

is generally used for structural failures and other discipline where total and irrecoverable loss
occurs.
To pre-cure this forensic engineering is the techniques can be use by the organization.
This means to “the investigation of the failure”. In this the early causes of the failure are detected
and to handle them plans are implemented.
To backup and restore data in the windows server 2016 there are 2 build in techniques
provided by the Microsoft.
1. System Backup- This is the feature available in the windows server 2016 to backup the
data and restore it. In this the external drive from the hardware can be used to make
backup of files (Dely, Kassler and Bayer, 2011). This can be activated from the control
panel of the system. For Torner Partner Limited it is good option to backup the files
because duplicates the files and restore them as it as they were.
2. System Restoration Protection- It is different from the system backup as it use to store
the Resident programs, their settings and Windows Registry in the form of an image. It
stores the essential files and the documents necessary to restore the required data (Röpke
and Holz, 2016). Torner Partner Limited can use this method also, but this may cause
them loss in data. Using this they can only restores the essential data not the detailed
data.
Torner Partner Limited can install server backup manager on the Linux machine. It help
the organisation to backup data at both windows and linux server. This reduces the cost of
organization if in future they change their server from windows to Linux. For this some system
requirement are:-
Hardware Requirements
Linux Kernel current 64 bit Linux kernel
Physical
Memory 16 GB of RAM minimum plus 1 GB RAM per protected machine
CPU 4 CPU cores minimum, recommended 1 core for each concurrent disk safe task (set in
manager options)
Free Disk
Space Minimum 200 GB for the Server Backup Manager installation
7
occurs.
To pre-cure this forensic engineering is the techniques can be use by the organization.
This means to “the investigation of the failure”. In this the early causes of the failure are detected
and to handle them plans are implemented.
To backup and restore data in the windows server 2016 there are 2 build in techniques
provided by the Microsoft.
1. System Backup- This is the feature available in the windows server 2016 to backup the
data and restore it. In this the external drive from the hardware can be used to make
backup of files (Dely, Kassler and Bayer, 2011). This can be activated from the control
panel of the system. For Torner Partner Limited it is good option to backup the files
because duplicates the files and restore them as it as they were.
2. System Restoration Protection- It is different from the system backup as it use to store
the Resident programs, their settings and Windows Registry in the form of an image. It
stores the essential files and the documents necessary to restore the required data (Röpke
and Holz, 2016). Torner Partner Limited can use this method also, but this may cause
them loss in data. Using this they can only restores the essential data not the detailed
data.
Torner Partner Limited can install server backup manager on the Linux machine. It help
the organisation to backup data at both windows and linux server. This reduces the cost of
organization if in future they change their server from windows to Linux. For this some system
requirement are:-
Hardware Requirements
Linux Kernel current 64 bit Linux kernel
Physical
Memory 16 GB of RAM minimum plus 1 GB RAM per protected machine
CPU 4 CPU cores minimum, recommended 1 core for each concurrent disk safe task (set in
manager options)
Free Disk
Space Minimum 200 GB for the Server Backup Manager installation
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 3
3.1 Analyse the tools available for the performance monitoring of a network operating system
Monitoring the performance of operating systems and procedure is necessary to debug
operations and systems, effectively manage system resources, making system decisions, and
assessing and investigating systems. These tools are basically divided into two main categories:
real time and log-based. Real time monitoring tools are concerned by calculating the current
system state and give up to date information about the system performance. Log-based
monitoring tools record system performance information for post-processing and analysis to
obtain tendency in the system performance(Dong and et. al., 2012). This Report presents a
survey of the most commonly used tools for monitoring network operating system.
Task Manager – This is the most well-known tool for monitoring operation on the
windows operating system. Through this Toner Partner limited can examine all
applications and their state, all actions and some of their most frequently used
performance measures. Two tabs of Task manager describes operating system
performance data to the user. First is the Processes Tab , this tab shows the current
memory and percentage of CPU usage of every process running on the computer as well
as the total CPU and memory usage of the system. Second is the Performance Tab, this
tab provides a top level view of the system state in terms of CPU and memory usage.
Windows Performance Monitor – This is the second most common operating system
performance monitoring tool for windows (Rainie and Wellman, 2012). This acts as both
real time and log-based. This monitors various presentation metrics, presents them in a
real-time graph, shows historic data, and be designed for alerting. However, it doesn’t
give enough details for deeper analysis and troubleshooting. Toner Partner limited
administrator can use this to examine how programs running on their servers/PC and to
check the performance of their computers.
Typeperf – It is a log based monitoring tool used for monitoring their server/PC through
command prompt instead of GUI interface. To get all of the counter that can be listed in
typeperf, Toner partner limited have to enter the following command (c:\> typeperf -q >
c:\counter.txt) and to define a counter live from your PC, they may enter this
command(C:\> typeperf “\processsor(*)\% Processor Time”).
8
3.1 Analyse the tools available for the performance monitoring of a network operating system
Monitoring the performance of operating systems and procedure is necessary to debug
operations and systems, effectively manage system resources, making system decisions, and
assessing and investigating systems. These tools are basically divided into two main categories:
real time and log-based. Real time monitoring tools are concerned by calculating the current
system state and give up to date information about the system performance. Log-based
monitoring tools record system performance information for post-processing and analysis to
obtain tendency in the system performance(Dong and et. al., 2012). This Report presents a
survey of the most commonly used tools for monitoring network operating system.
Task Manager – This is the most well-known tool for monitoring operation on the
windows operating system. Through this Toner Partner limited can examine all
applications and their state, all actions and some of their most frequently used
performance measures. Two tabs of Task manager describes operating system
performance data to the user. First is the Processes Tab , this tab shows the current
memory and percentage of CPU usage of every process running on the computer as well
as the total CPU and memory usage of the system. Second is the Performance Tab, this
tab provides a top level view of the system state in terms of CPU and memory usage.
Windows Performance Monitor – This is the second most common operating system
performance monitoring tool for windows (Rainie and Wellman, 2012). This acts as both
real time and log-based. This monitors various presentation metrics, presents them in a
real-time graph, shows historic data, and be designed for alerting. However, it doesn’t
give enough details for deeper analysis and troubleshooting. Toner Partner limited
administrator can use this to examine how programs running on their servers/PC and to
check the performance of their computers.
Typeperf – It is a log based monitoring tool used for monitoring their server/PC through
command prompt instead of GUI interface. To get all of the counter that can be listed in
typeperf, Toner partner limited have to enter the following command (c:\> typeperf -q >
c:\counter.txt) and to define a counter live from your PC, they may enter this
command(C:\> typeperf “\processsor(*)\% Processor Time”).
8

3.2 Network performance and reliability under load conditions.
To evaluate network performance and reliability under load conditions, firstly company
should know about network performance and reliability.
Network Performance
This is the analysis of joint network statistics, that defines the performance level of given
network. Network monitoring tool examine networks on different performance metrics such as
latency, bandwidth usage, and responsiveness. They also explore network applications and
devices in real time and notify network admins about any variation through voice and text alerts.
(Etzion, Niblett and Luckham, 2011). Toner Partner limited can use the following ways to
improve network performance under load conditions :
1. Use a Network Monitoring Tool : When users complain that the network is slow, it's
rarely the network itself that is the actual problem.
2. Educate your users and establish policies : Sometimes network slow downs are simply a
matter of two many people accessing the network at once and doing things that require a
great deal of bandwidth.
3. Limit the number of network users : Too many drivers on the way can create a
congestion, so it's useful to limit the number of users on your network.
Reliability
Reliability is concerned with the capacity of a network to carry out a desired operation
such as communication. A source node interface with a terminal node for all OD pairs is
Terminal Reliability. It is an aspect of any computer based component that consistently performs
according to its identifications. Network Reliability describes the ability of the network to offer
the same services even during a fault. Toner Partner limited can use these two models to
improve reliability under load conditions :
Deterministic Models : In this class they include
Connectivity
Hop counts Node and link disjoint paths
Probabilistic Models : In this they include
Path reliabilities
Probability of path disconnection
9
To evaluate network performance and reliability under load conditions, firstly company
should know about network performance and reliability.
Network Performance
This is the analysis of joint network statistics, that defines the performance level of given
network. Network monitoring tool examine networks on different performance metrics such as
latency, bandwidth usage, and responsiveness. They also explore network applications and
devices in real time and notify network admins about any variation through voice and text alerts.
(Etzion, Niblett and Luckham, 2011). Toner Partner limited can use the following ways to
improve network performance under load conditions :
1. Use a Network Monitoring Tool : When users complain that the network is slow, it's
rarely the network itself that is the actual problem.
2. Educate your users and establish policies : Sometimes network slow downs are simply a
matter of two many people accessing the network at once and doing things that require a
great deal of bandwidth.
3. Limit the number of network users : Too many drivers on the way can create a
congestion, so it's useful to limit the number of users on your network.
Reliability
Reliability is concerned with the capacity of a network to carry out a desired operation
such as communication. A source node interface with a terminal node for all OD pairs is
Terminal Reliability. It is an aspect of any computer based component that consistently performs
according to its identifications. Network Reliability describes the ability of the network to offer
the same services even during a fault. Toner Partner limited can use these two models to
improve reliability under load conditions :
Deterministic Models : In this class they include
Connectivity
Hop counts Node and link disjoint paths
Probabilistic Models : In this they include
Path reliabilities
Probability of path disconnection
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




