Installation of Network Operating System
VerifiedAdded on 2023/01/18
|45
|7965
|84
AI Summary
This document provides a step-by-step guide on how to install a network operating system and configure client and server operating systems. It includes hardware requirements and installation procedures for both client and server systems. The document also discusses the importance of vendor specifications and hardware compatibility in network operating systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NETWORK OPERATING
SYSTEM
1
SYSTEM
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................5
LO1 Be able to evaluate the installation of a network operating system........................................5
1.1 Analyse a network operating system in terms of vendor’s specification and hardware
compatibility................................................................................................................................5
1.2 Install and configure a client operating system and a server operating system.........................7
1.3 Perform the installation of a network operating system......................................................15
LO2 Be able to produce a disaster recovery plan, following a catastrophic failure......................28
2.1 Produce a cost analysis, details of specialized devices and an outline of roles of key
personnel, as part of a disaster recovery plan (Network Alliance, 2019)..................................28
2.2 Analyse backup and data storage requirements following a catastrophic failure................30
LO3 Be able to evaluate the performance of a network operating system....................................34
3.1 Analyse the tools available for the performance monitoring of a network operating system
...................................................................................................................................................34
3.2 Evaluate network performance and reliability under load conditions.................................39
LO4 Be able to evaluate the maintenance of a network operating system....................................40
4.1 Analyse the monitoring of event logs and programs...........................................................40
4.2 Evaluate the tools available for the monitoring and optimizing of network operating
system performance...................................................................................................................40
Conclusion.....................................................................................................................................43
References......................................................................................................................................45
2
INTRODUCTION...........................................................................................................................5
LO1 Be able to evaluate the installation of a network operating system........................................5
1.1 Analyse a network operating system in terms of vendor’s specification and hardware
compatibility................................................................................................................................5
1.2 Install and configure a client operating system and a server operating system.........................7
1.3 Perform the installation of a network operating system......................................................15
LO2 Be able to produce a disaster recovery plan, following a catastrophic failure......................28
2.1 Produce a cost analysis, details of specialized devices and an outline of roles of key
personnel, as part of a disaster recovery plan (Network Alliance, 2019)..................................28
2.2 Analyse backup and data storage requirements following a catastrophic failure................30
LO3 Be able to evaluate the performance of a network operating system....................................34
3.1 Analyse the tools available for the performance monitoring of a network operating system
...................................................................................................................................................34
3.2 Evaluate network performance and reliability under load conditions.................................39
LO4 Be able to evaluate the maintenance of a network operating system....................................40
4.1 Analyse the monitoring of event logs and programs...........................................................40
4.2 Evaluate the tools available for the monitoring and optimizing of network operating
system performance...................................................................................................................40
Conclusion.....................................................................................................................................43
References......................................................................................................................................45
2

LIST OF FIGURES
Figure 1 Select Language................................................................................................................8
Figure 2 Installation.........................................................................................................................9
Figure 3 Installation in progress....................................................................................................10
Figure 4 Select Language..............................................................................................................11
Figure 5 Installation.......................................................................................................................12
Figure 6 Select Operating System.................................................................................................12
Figure 7 Accept License terms......................................................................................................13
Figure 8 Type of Installation.........................................................................................................13
Figure 9 Installation in progress....................................................................................................14
Figure 10 Installation Complete....................................................................................................15
Figure 11 Add roles.......................................................................................................................19
Figure 12 select role page..............................................................................................................20
Figure 13 TS licensing...................................................................................................................21
Figure 14 network level authentication.........................................................................................22
Figure 15 Licensing mode page.....................................................................................................22
Figure 16 Discovery scope page....................................................................................................23
Figure 17 installation results..........................................................................................................23
Figure 18 Figure 8: Windows Performance Monitor....................................................................32
Figure 19 Microsoft Performance Manager..................................................................................33
Figure 20 Typeperf........................................................................................................................34
Figure 21 Selecting the Server Roles.............................................................................................39
Figure 22 Configuration of the user experience............................................................................40
Figure 23 Adding users to the remote desktop user’s group.........................................................41
3
Figure 1 Select Language................................................................................................................8
Figure 2 Installation.........................................................................................................................9
Figure 3 Installation in progress....................................................................................................10
Figure 4 Select Language..............................................................................................................11
Figure 5 Installation.......................................................................................................................12
Figure 6 Select Operating System.................................................................................................12
Figure 7 Accept License terms......................................................................................................13
Figure 8 Type of Installation.........................................................................................................13
Figure 9 Installation in progress....................................................................................................14
Figure 10 Installation Complete....................................................................................................15
Figure 11 Add roles.......................................................................................................................19
Figure 12 select role page..............................................................................................................20
Figure 13 TS licensing...................................................................................................................21
Figure 14 network level authentication.........................................................................................22
Figure 15 Licensing mode page.....................................................................................................22
Figure 16 Discovery scope page....................................................................................................23
Figure 17 installation results..........................................................................................................23
Figure 18 Figure 8: Windows Performance Monitor....................................................................32
Figure 19 Microsoft Performance Manager..................................................................................33
Figure 20 Typeperf........................................................................................................................34
Figure 21 Selecting the Server Roles.............................................................................................39
Figure 22 Configuration of the user experience............................................................................40
Figure 23 Adding users to the remote desktop user’s group.........................................................41
3

LIST OF TABLES
Table 1 Hardware requirements 5
Table 2: Cost Analysis 14
4
Table 1 Hardware requirements 5
Table 2: Cost Analysis 14
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTRODUCTION
Network Operating System can be defined a structure that ensures the dependable sharing of
procedures, files, elements that are associated to networking process, network protocol, and
different elements that are associated with the process of networking, for the production of a
machine which is dependable and secured from all the external attacks, and which works along
with the desired specifications. In the lack of an OS, the computer is nothing but a box that
contains various circuits. In case of NOS, the networks are not much more than a group of
system gadgets that are cabled altogether. NOS improve the flow of data and communicating
process across various networks. During the comparison of the NOS with workstation operating
systems, the network operating system is mainly created in order to provide its service to remote
client. One of the major differences is that NOS is created in order to be compatible with the
simultaneous multiuser platform which signifies that with the NOS we may have many users that
are all simultaneously using the sources on the server. In the course of this document, the dos
and don’ts of the network operating systems are discussed. After going through this whole report
the learner would be having the basic knowledge regarding the NOS.
LO1 Be able to evaluate the installation of a network operating system
1.1 Analyse a network operating system in terms of vendor’s specification and hardware
compatibility
There are many of the actions of network-based operating systems that are considered to be
same as those of a basic operating system for single systems, like managing the storage and
command over the hardware. However, the network-based operating systems are also having
proper expertise in various tasks. For instance, whenever the network-based gadgets are taken in
use, like printer and disk drive etc., the network-based operating systems make sure that these
sources are having their appropriate usage and efficiency. The expertise tasks involve the
security of the network as well as their administration. Various clients require gaining the
accessibility to the networks simultaneously and this is the procedure that is much requires to be
handled with much care (Zandbergen, 2019).
On the other hand, there are some of the operating systems that are having their usage for
the single systems that are having built-in networking based tasks, but the OS that is particularly
created for these kinds of tasks are in the trend in the present times. Networking based operating
5
Network Operating System can be defined a structure that ensures the dependable sharing of
procedures, files, elements that are associated to networking process, network protocol, and
different elements that are associated with the process of networking, for the production of a
machine which is dependable and secured from all the external attacks, and which works along
with the desired specifications. In the lack of an OS, the computer is nothing but a box that
contains various circuits. In case of NOS, the networks are not much more than a group of
system gadgets that are cabled altogether. NOS improve the flow of data and communicating
process across various networks. During the comparison of the NOS with workstation operating
systems, the network operating system is mainly created in order to provide its service to remote
client. One of the major differences is that NOS is created in order to be compatible with the
simultaneous multiuser platform which signifies that with the NOS we may have many users that
are all simultaneously using the sources on the server. In the course of this document, the dos
and don’ts of the network operating systems are discussed. After going through this whole report
the learner would be having the basic knowledge regarding the NOS.
LO1 Be able to evaluate the installation of a network operating system
1.1 Analyse a network operating system in terms of vendor’s specification and hardware
compatibility
There are many of the actions of network-based operating systems that are considered to be
same as those of a basic operating system for single systems, like managing the storage and
command over the hardware. However, the network-based operating systems are also having
proper expertise in various tasks. For instance, whenever the network-based gadgets are taken in
use, like printer and disk drive etc., the network-based operating systems make sure that these
sources are having their appropriate usage and efficiency. The expertise tasks involve the
security of the network as well as their administration. Various clients require gaining the
accessibility to the networks simultaneously and this is the procedure that is much requires to be
handled with much care (Zandbergen, 2019).
On the other hand, there are some of the operating systems that are having their usage for
the single systems that are having built-in networking based tasks, but the OS that is particularly
created for these kinds of tasks are in the trend in the present times. Networking based operating
5
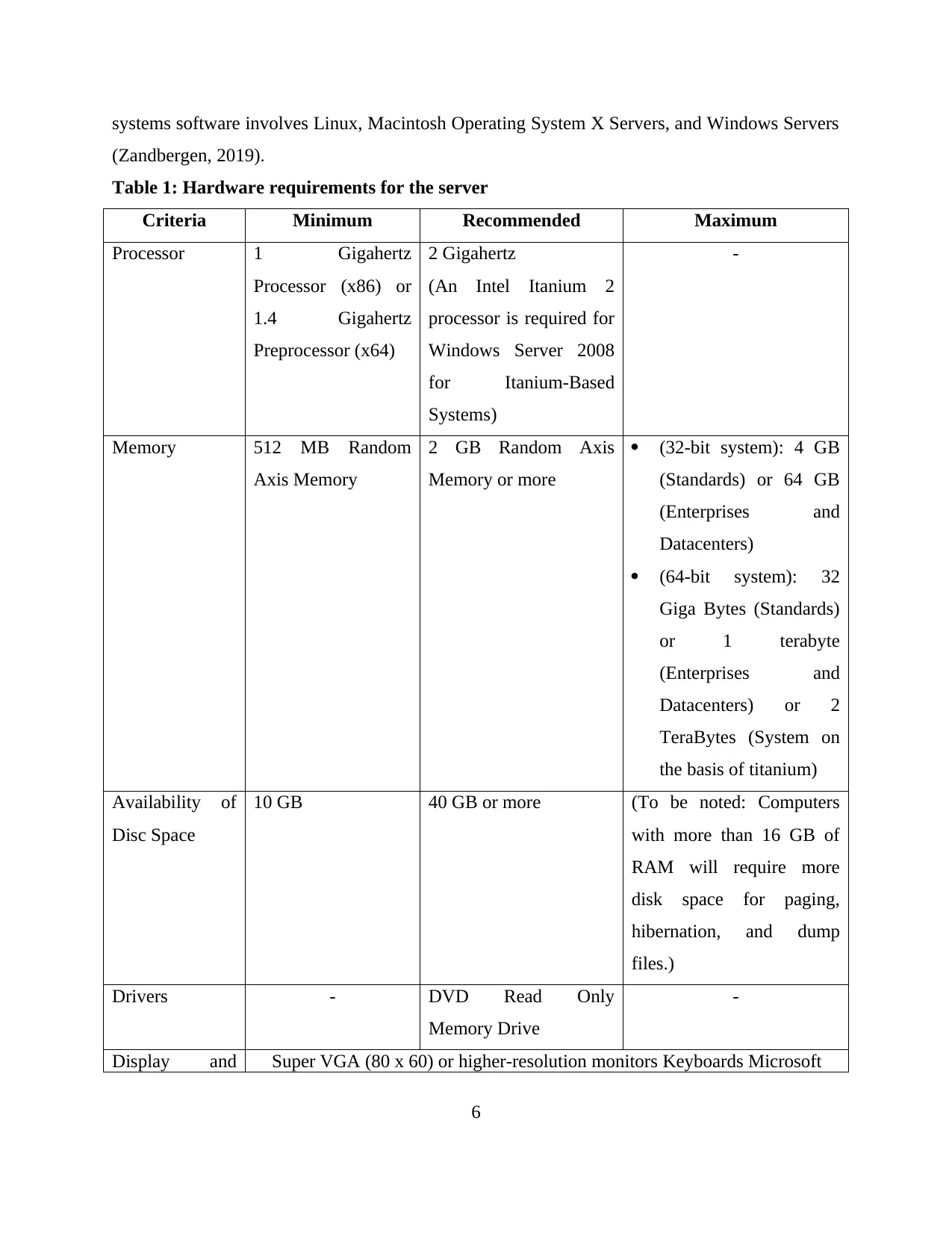
systems software involves Linux, Macintosh Operating System X Servers, and Windows Servers
(Zandbergen, 2019).
Table 1: Hardware requirements for the server
Criteria Minimum Recommended Maximum
Processor 1 Gigahertz
Processor (x86) or
1.4 Gigahertz
Preprocessor (x64)
2 Gigahertz
(An Intel Itanium 2
processor is required for
Windows Server 2008
for Itanium-Based
Systems)
-
Memory 512 MB Random
Axis Memory
2 GB Random Axis
Memory or more
(32-bit system): 4 GB
(Standards) or 64 GB
(Enterprises and
Datacenters)
(64-bit system): 32
Giga Bytes (Standards)
or 1 terabyte
(Enterprises and
Datacenters) or 2
TeraBytes (System on
the basis of titanium)
Availability of
Disc Space
10 GB 40 GB or more (To be noted: Computers
with more than 16 GB of
RAM will require more
disk space for paging,
hibernation, and dump
files.)
Drivers - DVD Read Only
Memory Drive
-
Display and Super VGA (80 x 60) or higher-resolution monitors Keyboards Microsoft
6
(Zandbergen, 2019).
Table 1: Hardware requirements for the server
Criteria Minimum Recommended Maximum
Processor 1 Gigahertz
Processor (x86) or
1.4 Gigahertz
Preprocessor (x64)
2 Gigahertz
(An Intel Itanium 2
processor is required for
Windows Server 2008
for Itanium-Based
Systems)
-
Memory 512 MB Random
Axis Memory
2 GB Random Axis
Memory or more
(32-bit system): 4 GB
(Standards) or 64 GB
(Enterprises and
Datacenters)
(64-bit system): 32
Giga Bytes (Standards)
or 1 terabyte
(Enterprises and
Datacenters) or 2
TeraBytes (System on
the basis of titanium)
Availability of
Disc Space
10 GB 40 GB or more (To be noted: Computers
with more than 16 GB of
RAM will require more
disk space for paging,
hibernation, and dump
files.)
Drivers - DVD Read Only
Memory Drive
-
Display and Super VGA (80 x 60) or higher-resolution monitors Keyboards Microsoft
6
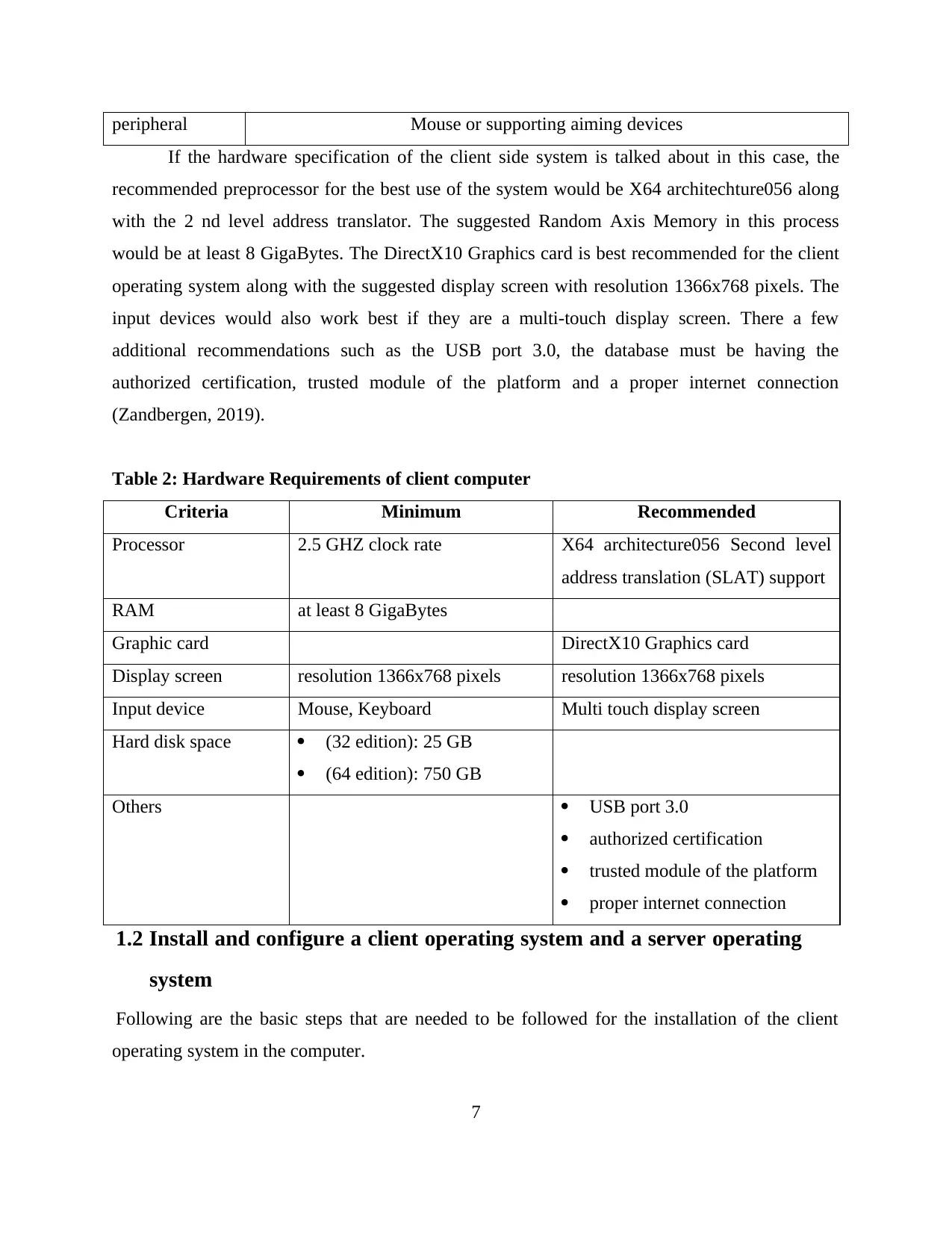
peripheral Mouse or supporting aiming devices
If the hardware specification of the client side system is talked about in this case, the
recommended preprocessor for the best use of the system would be X64 architechture056 along
with the 2 nd level address translator. The suggested Random Axis Memory in this process
would be at least 8 GigaBytes. The DirectX10 Graphics card is best recommended for the client
operating system along with the suggested display screen with resolution 1366x768 pixels. The
input devices would also work best if they are a multi-touch display screen. There a few
additional recommendations such as the USB port 3.0, the database must be having the
authorized certification, trusted module of the platform and a proper internet connection
(Zandbergen, 2019).
Table 2: Hardware Requirements of client computer
Criteria Minimum Recommended
Processor 2.5 GHZ clock rate X64 architecture056 Second level
address translation (SLAT) support
RAM at least 8 GigaBytes
Graphic card DirectX10 Graphics card
Display screen resolution 1366x768 pixels resolution 1366x768 pixels
Input device Mouse, Keyboard Multi touch display screen
Hard disk space (32 edition): 25 GB
(64 edition): 750 GB
Others USB port 3.0
authorized certification
trusted module of the platform
proper internet connection
1.2 Install and configure a client operating system and a server operating
system
Following are the basic steps that are needed to be followed for the installation of the client
operating system in the computer.
7
If the hardware specification of the client side system is talked about in this case, the
recommended preprocessor for the best use of the system would be X64 architechture056 along
with the 2 nd level address translator. The suggested Random Axis Memory in this process
would be at least 8 GigaBytes. The DirectX10 Graphics card is best recommended for the client
operating system along with the suggested display screen with resolution 1366x768 pixels. The
input devices would also work best if they are a multi-touch display screen. There a few
additional recommendations such as the USB port 3.0, the database must be having the
authorized certification, trusted module of the platform and a proper internet connection
(Zandbergen, 2019).
Table 2: Hardware Requirements of client computer
Criteria Minimum Recommended
Processor 2.5 GHZ clock rate X64 architecture056 Second level
address translation (SLAT) support
RAM at least 8 GigaBytes
Graphic card DirectX10 Graphics card
Display screen resolution 1366x768 pixels resolution 1366x768 pixels
Input device Mouse, Keyboard Multi touch display screen
Hard disk space (32 edition): 25 GB
(64 edition): 750 GB
Others USB port 3.0
authorized certification
trusted module of the platform
proper internet connection
1.2 Install and configure a client operating system and a server operating
system
Following are the basic steps that are needed to be followed for the installation of the client
operating system in the computer.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
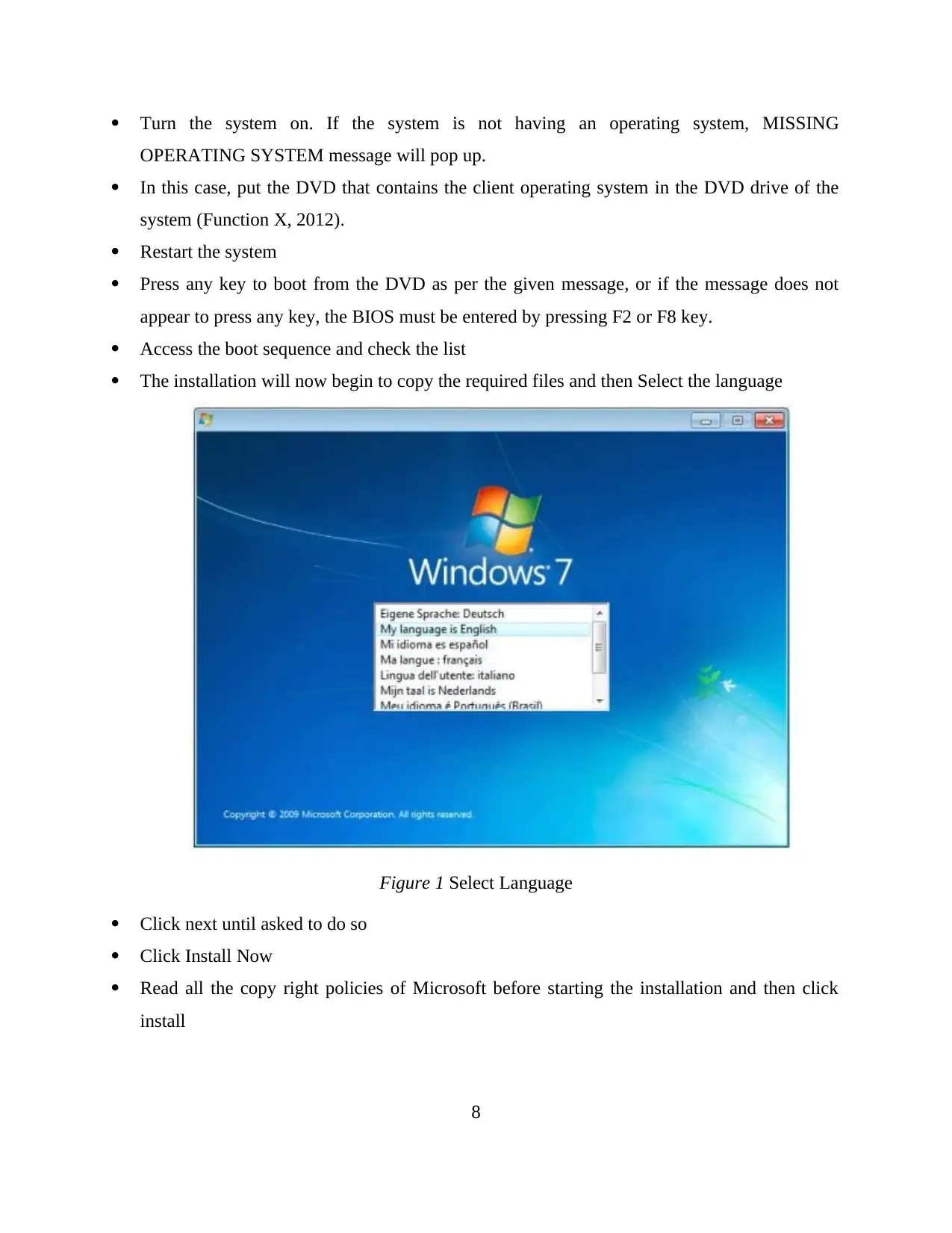
Turn the system on. If the system is not having an operating system, MISSING
OPERATING SYSTEM message will pop up.
In this case, put the DVD that contains the client operating system in the DVD drive of the
system (Function X, 2012).
Restart the system
Press any key to boot from the DVD as per the given message, or if the message does not
appear to press any key, the BIOS must be entered by pressing F2 or F8 key.
Access the boot sequence and check the list
The installation will now begin to copy the required files and then Select the language
Figure 1 Select Language
Click next until asked to do so
Click Install Now
Read all the copy right policies of Microsoft before starting the installation and then click
install
8
OPERATING SYSTEM message will pop up.
In this case, put the DVD that contains the client operating system in the DVD drive of the
system (Function X, 2012).
Restart the system
Press any key to boot from the DVD as per the given message, or if the message does not
appear to press any key, the BIOS must be entered by pressing F2 or F8 key.
Access the boot sequence and check the list
The installation will now begin to copy the required files and then Select the language
Figure 1 Select Language
Click next until asked to do so
Click Install Now
Read all the copy right policies of Microsoft before starting the installation and then click
install
8

Figure 2 Installation
(Source: Function X, 2012)
Select the version as per the requirement of the system Click next
After selecting the Operating system to be installed, accpetance box of license terms is to be
checked. Then afgain click next
After checking the licence box, select the type of installation user wants. Most of the times
custom (advance) is selected
After that disk partition in which OS is to be installed is selected. Then click next
The next screen enables the user to provide the details regarding the disk partition
9
(Source: Function X, 2012)
Select the version as per the requirement of the system Click next
After selecting the Operating system to be installed, accpetance box of license terms is to be
checked. Then afgain click next
After checking the licence box, select the type of installation user wants. Most of the times
custom (advance) is selected
After that disk partition in which OS is to be installed is selected. Then click next
The next screen enables the user to provide the details regarding the disk partition
9

Figure 3 Installation in progress
(Source: Function X, 2012)
Complete rest of the formalities such as setting up the time zone, protect the system etc.
The Client Operating System is now installed. After this configuration of the windows is
done.
Configuration stats with choice of appropriate colours for the system. After this most of the
times express setting is chosen for tracking of internet explorer.
After configuration of express setting, Microsoft account is created and if the users already
have a Microsoft account then users is asked to sign in to the Microsoft account.
Next DHCP setting is done so that client computer can directly obtain IP from DHCP
function.
Window’s server 2008
The steps for installing the server operating system is also similar to the steps that are
required to be followed in order to install the client-side operating system, though the operating
system that is required to be installed in this type of operating system that is Windows Server
2008.
There are various steps that are required to be followed in order to start the installation
process such as:
Insert Window’s server 2008 CD into DVD drive.
Restart the system
10
(Source: Function X, 2012)
Complete rest of the formalities such as setting up the time zone, protect the system etc.
The Client Operating System is now installed. After this configuration of the windows is
done.
Configuration stats with choice of appropriate colours for the system. After this most of the
times express setting is chosen for tracking of internet explorer.
After configuration of express setting, Microsoft account is created and if the users already
have a Microsoft account then users is asked to sign in to the Microsoft account.
Next DHCP setting is done so that client computer can directly obtain IP from DHCP
function.
Window’s server 2008
The steps for installing the server operating system is also similar to the steps that are
required to be followed in order to install the client-side operating system, though the operating
system that is required to be installed in this type of operating system that is Windows Server
2008.
There are various steps that are required to be followed in order to start the installation
process such as:
Insert Window’s server 2008 CD into DVD drive.
Restart the system
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Press any key to boot from the DVD as per the given message, or if the message does not
appear to press any key, the BIOS must be entered by pressing F2 or F8 key.
Access the boot sequence and check the list
Then select the language in which installation is to be done and after selection of language
click next option.
Figure 4 Select Language
(Source: Function X, 2012)
Read all the copy right policies of Microsoft before starting the installation and then click
install.
11
appear to press any key, the BIOS must be entered by pressing F2 or F8 key.
Access the boot sequence and check the list
Then select the language in which installation is to be done and after selection of language
click next option.
Figure 4 Select Language
(Source: Function X, 2012)
Read all the copy right policies of Microsoft before starting the installation and then click
install.
11
Figure 5 Installation
(Source: Function X, 2012)
Figure 6 Select Operating System
12
(Source: Function X, 2012)
Figure 6 Select Operating System
12
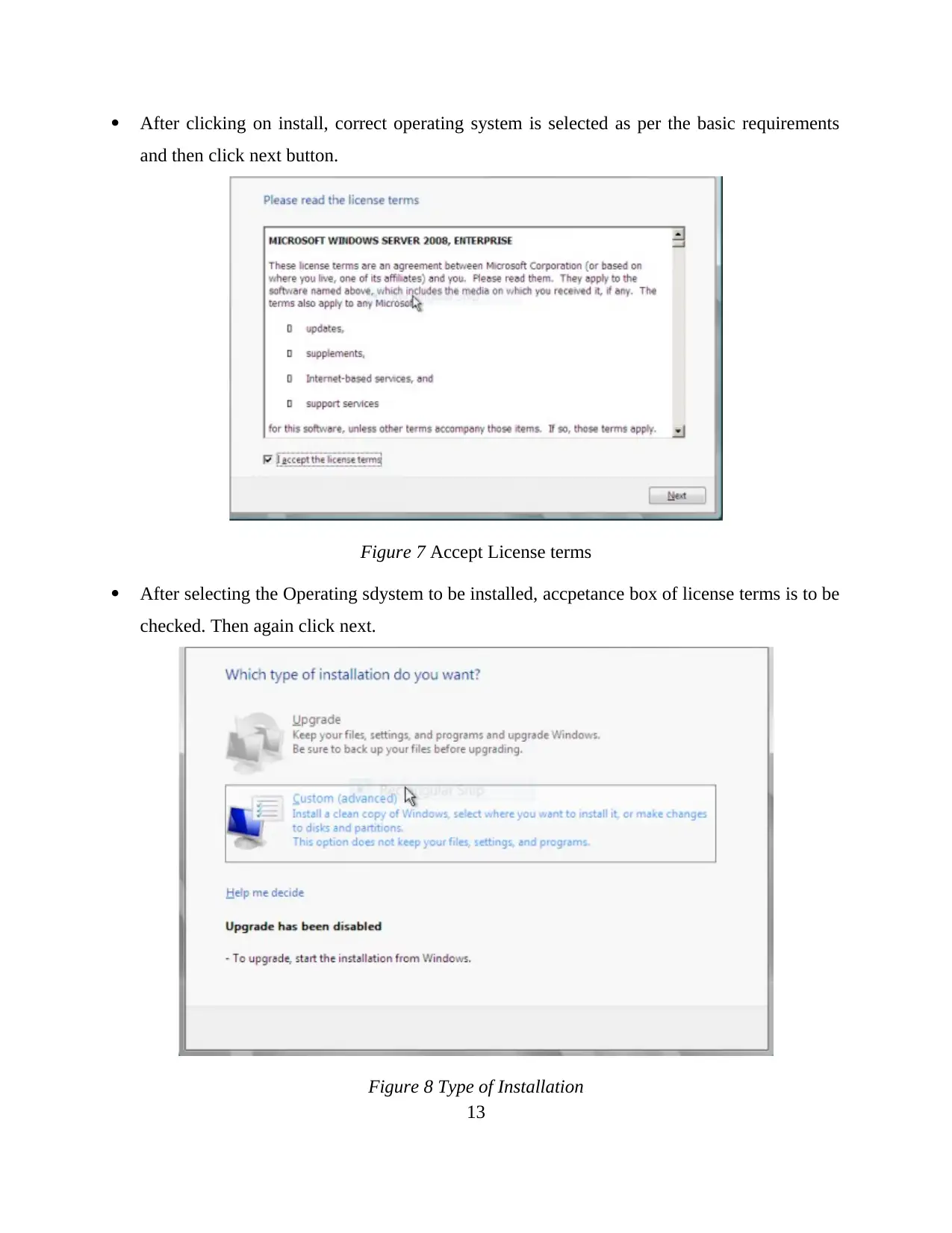
After clicking on install, correct operating system is selected as per the basic requirements
and then click next button.
Figure 7 Accept License terms
After selecting the Operating sdystem to be installed, accpetance box of license terms is to be
checked. Then again click next.
Figure 8 Type of Installation
13
and then click next button.
Figure 7 Accept License terms
After selecting the Operating sdystem to be installed, accpetance box of license terms is to be
checked. Then again click next.
Figure 8 Type of Installation
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
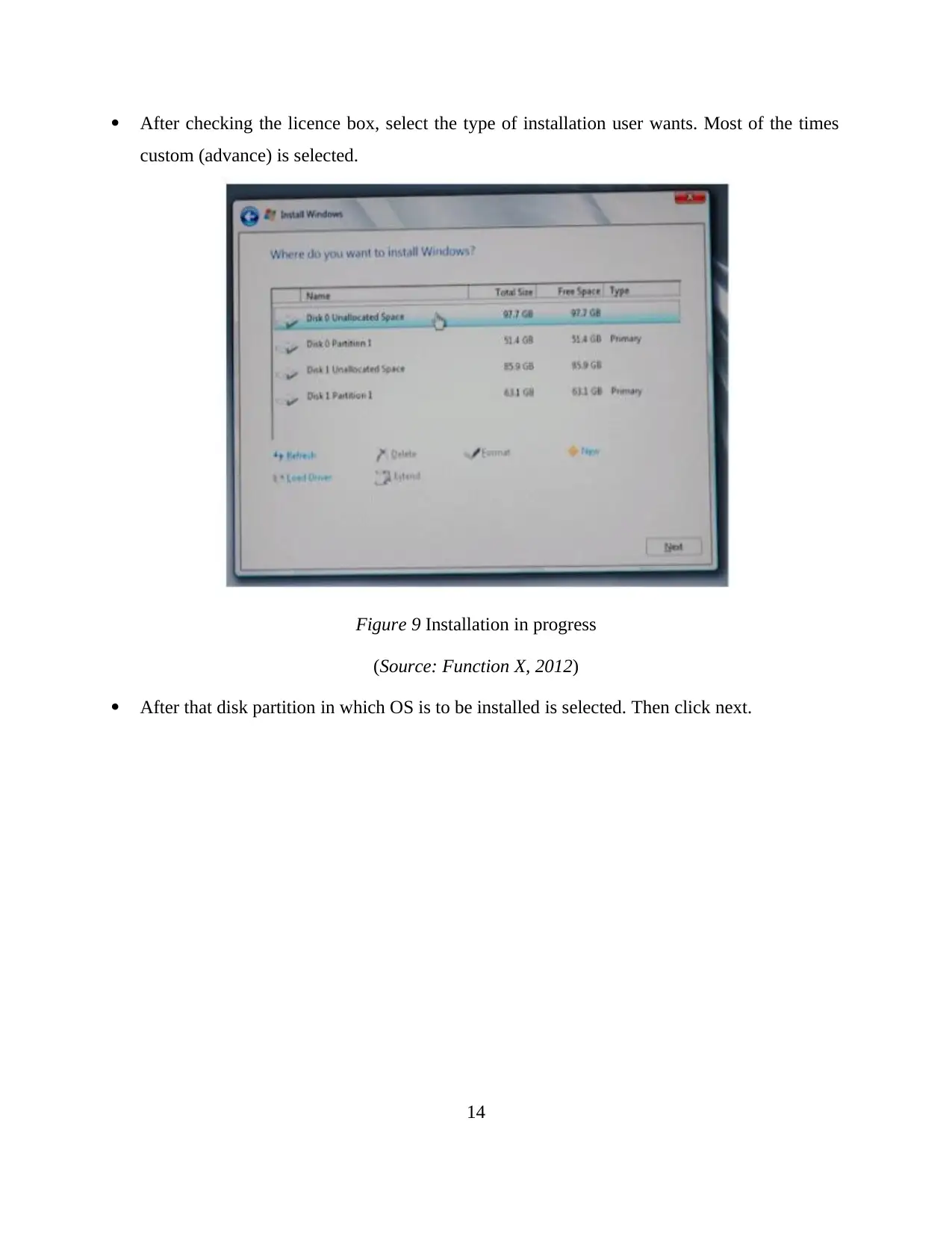
After checking the licence box, select the type of installation user wants. Most of the times
custom (advance) is selected.
Figure 9 Installation in progress
(Source: Function X, 2012)
After that disk partition in which OS is to be installed is selected. Then click next.
14
custom (advance) is selected.
Figure 9 Installation in progress
(Source: Function X, 2012)
After that disk partition in which OS is to be installed is selected. Then click next.
14
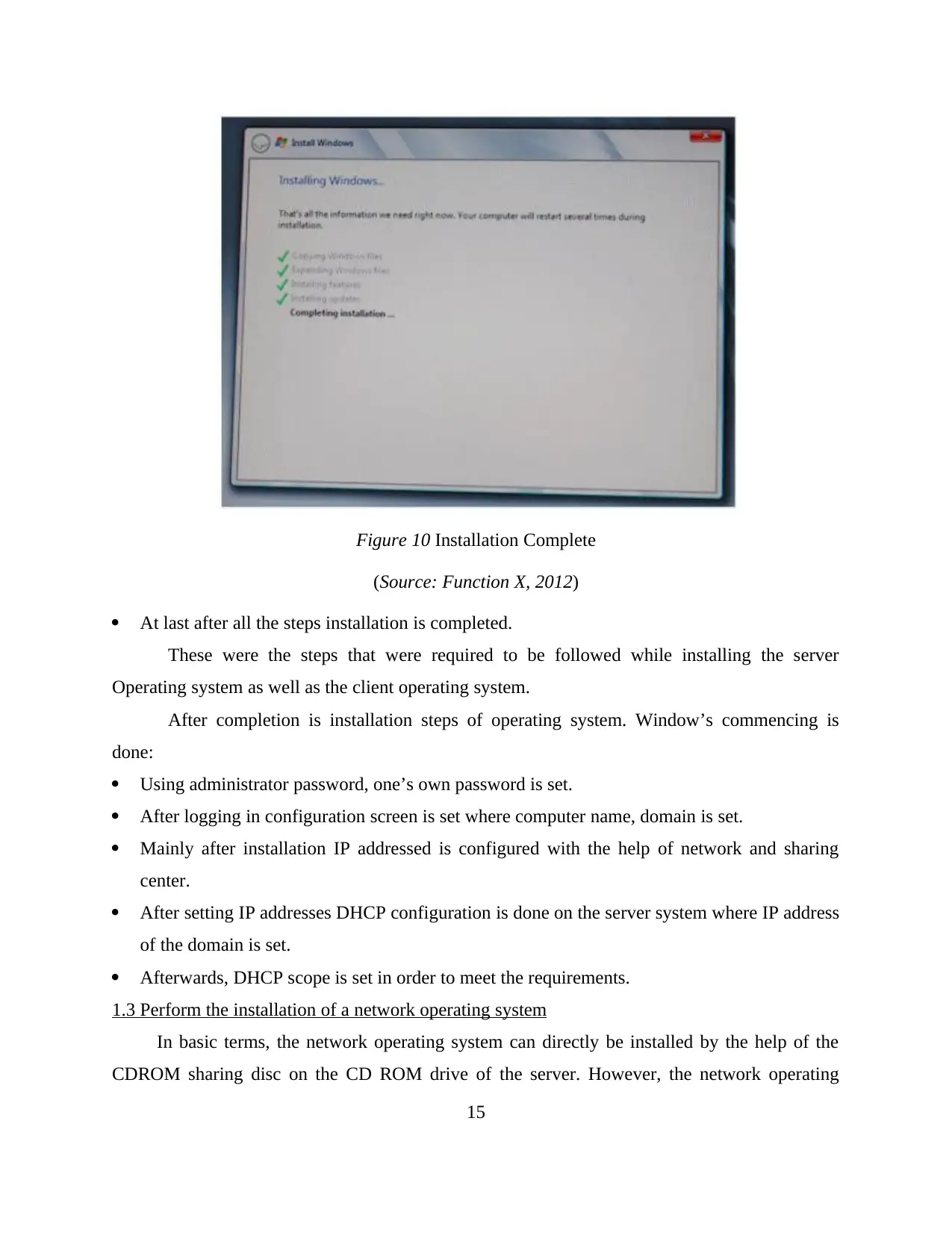
Figure 10 Installation Complete
(Source: Function X, 2012)
At last after all the steps installation is completed.
These were the steps that were required to be followed while installing the server
Operating system as well as the client operating system.
After completion is installation steps of operating system. Window’s commencing is
done:
Using administrator password, one’s own password is set.
After logging in configuration screen is set where computer name, domain is set.
Mainly after installation IP addressed is configured with the help of network and sharing
center.
After setting IP addresses DHCP configuration is done on the server system where IP address
of the domain is set.
Afterwards, DHCP scope is set in order to meet the requirements.
1.3 Perform the installation of a network operating system
In basic terms, the network operating system can directly be installed by the help of the
CDROM sharing disc on the CD ROM drive of the server. However, the network operating
15
(Source: Function X, 2012)
At last after all the steps installation is completed.
These were the steps that were required to be followed while installing the server
Operating system as well as the client operating system.
After completion is installation steps of operating system. Window’s commencing is
done:
Using administrator password, one’s own password is set.
After logging in configuration screen is set where computer name, domain is set.
Mainly after installation IP addressed is configured with the help of network and sharing
center.
After setting IP addresses DHCP configuration is done on the server system where IP address
of the domain is set.
Afterwards, DHCP scope is set in order to meet the requirements.
1.3 Perform the installation of a network operating system
In basic terms, the network operating system can directly be installed by the help of the
CDROM sharing disc on the CD ROM drive of the server. However, the network operating
15

system can also be installed by the help of a distributed drive that is found on any other system
required that the server system is already having the accessibility to the networking elements
(Dummies, 2019). A distributed CD-ROM drive can be used in this case or the entire content of
the sharing CD-ROM drive can also be copied on the distributed hard disc. It is very obvious that
the server system should be having the accessibility to the network for this method to be applied
properly. If the servers are already having the operating system installed in them, then, in that
case, severs might already be having the accessibility to the network. If they’re not, that system
can be booted by the help of a floppy disc that has as basic compatibility with the network. This
administrative UI includes a legit enlistment that enables the administration department to do the
methods like formatting the hard discs and configuring the safety measures for both the systems
and the particular customer or the consumer of the network operating system (Dummies, 2019).
The user may also have the ability to set up the safety and information backup requirement for
the systems or the whole big network. However, the network-based operating systems is also
having proper expertise in various tasks. For instance, whenever the network-based gadgets are
taken in use, like printer and disk drive etc., the network-based operating systems make sure that
these sources are having their appropriate usage and efficiency. The expertise tasks involve the
security of the network as well as their administration (Dummies, 2019). This includes the
hardware and the software components that are required in order to configure and set up the
network operating system, the cost of purchasing these components along with software
licensing etc. All the further steps have been explained above with the installation of operating
system.
Printer service and its configuration
There are various steps that are required to be followed to install printer service
configuration: - In order to configure Window’s printer server following steps are required to be
followed.
Click on start button and open server manager, click on dashboard and select Add roles and
features.
After this click on before you begin page and then click next and then select Role based or
feature base installation and again click next.
Click on sever selection page, select server name user is logged in into and again click next.\
In server role page, print and document service in server role and click next.
16
required that the server system is already having the accessibility to the networking elements
(Dummies, 2019). A distributed CD-ROM drive can be used in this case or the entire content of
the sharing CD-ROM drive can also be copied on the distributed hard disc. It is very obvious that
the server system should be having the accessibility to the network for this method to be applied
properly. If the servers are already having the operating system installed in them, then, in that
case, severs might already be having the accessibility to the network. If they’re not, that system
can be booted by the help of a floppy disc that has as basic compatibility with the network. This
administrative UI includes a legit enlistment that enables the administration department to do the
methods like formatting the hard discs and configuring the safety measures for both the systems
and the particular customer or the consumer of the network operating system (Dummies, 2019).
The user may also have the ability to set up the safety and information backup requirement for
the systems or the whole big network. However, the network-based operating systems is also
having proper expertise in various tasks. For instance, whenever the network-based gadgets are
taken in use, like printer and disk drive etc., the network-based operating systems make sure that
these sources are having their appropriate usage and efficiency. The expertise tasks involve the
security of the network as well as their administration (Dummies, 2019). This includes the
hardware and the software components that are required in order to configure and set up the
network operating system, the cost of purchasing these components along with software
licensing etc. All the further steps have been explained above with the installation of operating
system.
Printer service and its configuration
There are various steps that are required to be followed to install printer service
configuration: - In order to configure Window’s printer server following steps are required to be
followed.
Click on start button and open server manager, click on dashboard and select Add roles and
features.
After this click on before you begin page and then click next and then select Role based or
feature base installation and again click next.
Click on sever selection page, select server name user is logged in into and again click next.\
In server role page, print and document service in server role and click next.
16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
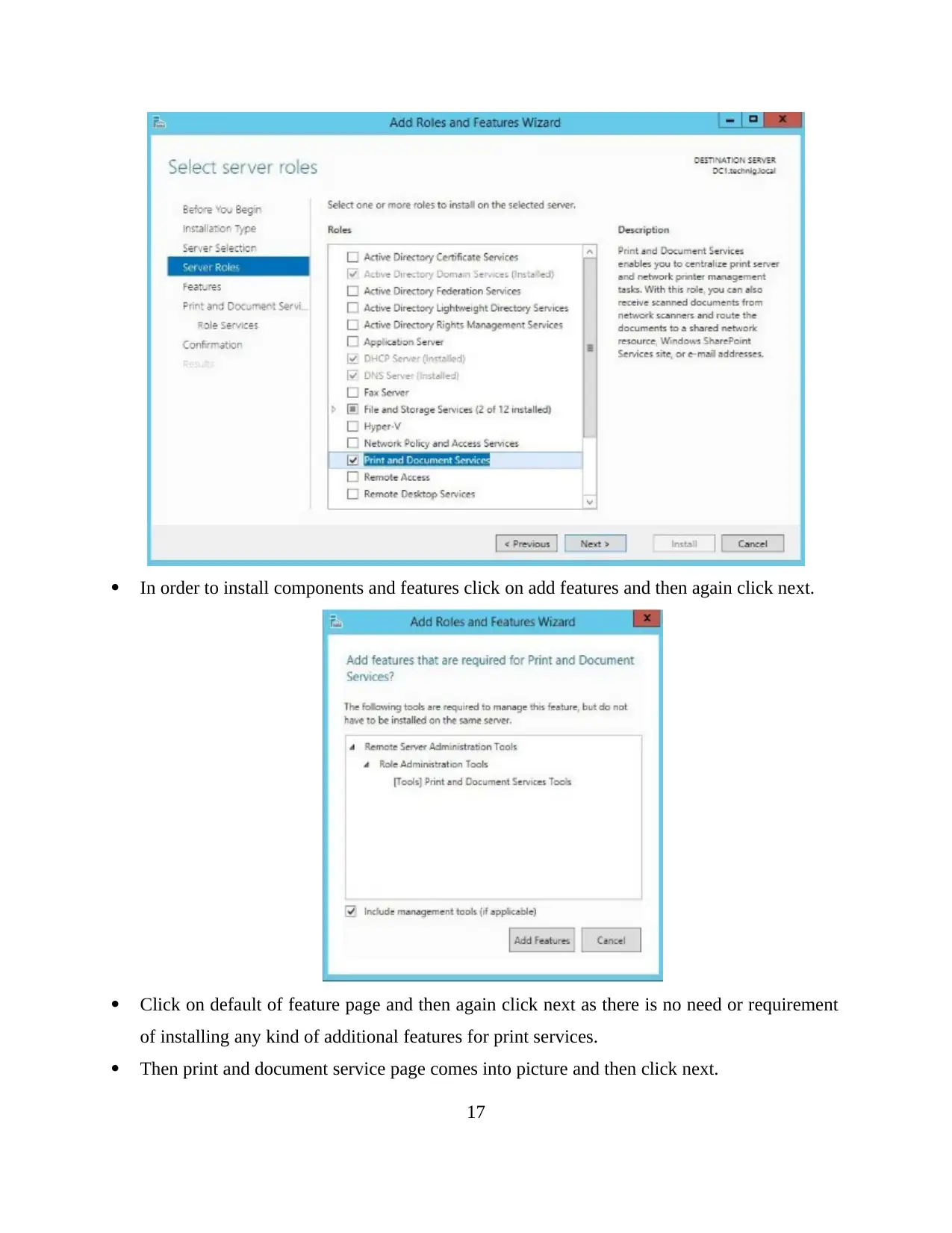
In order to install components and features click on add features and then again click next.
Click on default of feature page and then again click next as there is no need or requirement
of installing any kind of additional features for print services.
Then print and document service page comes into picture and then click next.
17
Click on default of feature page and then again click next as there is no need or requirement
of installing any kind of additional features for print services.
Then print and document service page comes into picture and then click next.
17
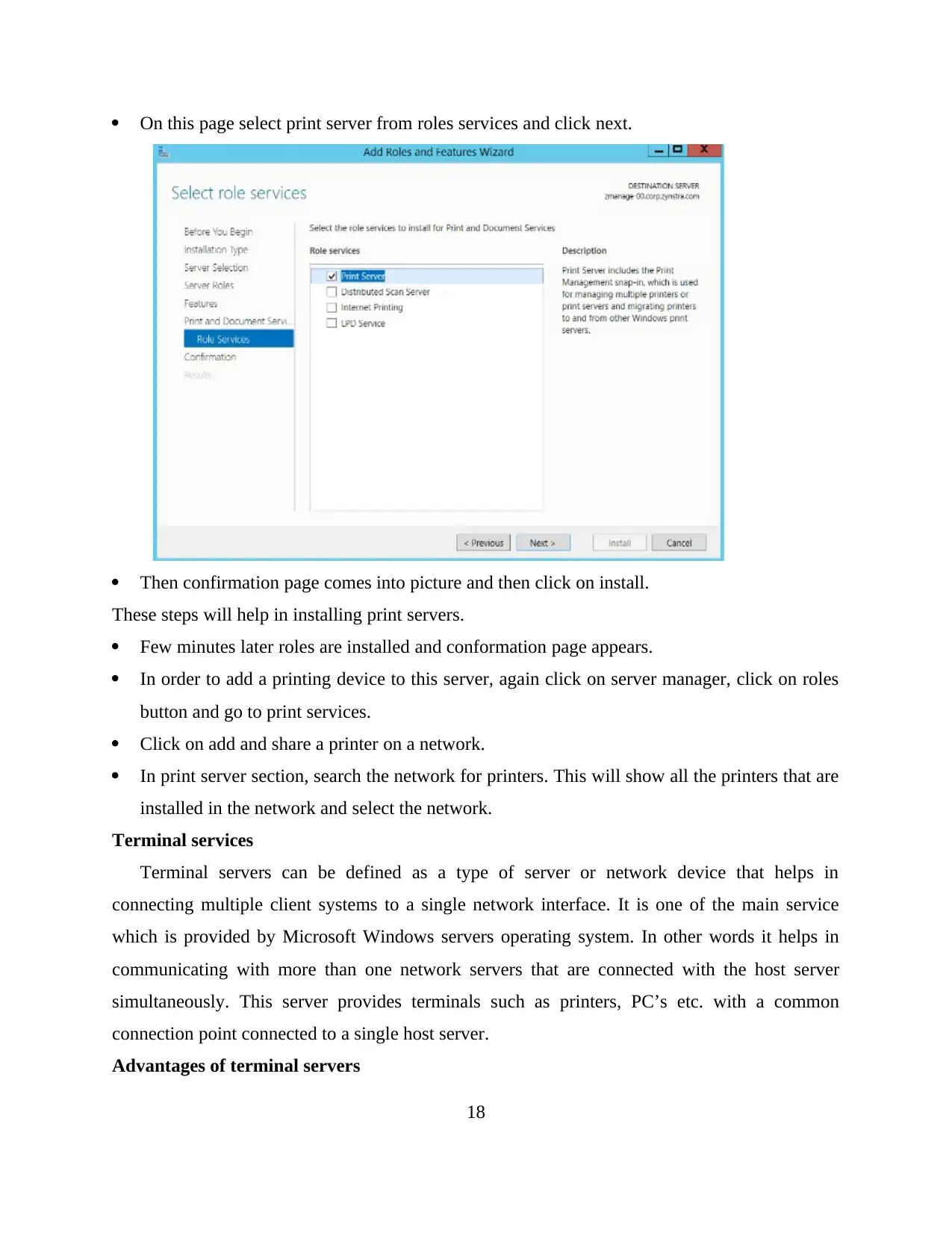
On this page select print server from roles services and click next.
Then confirmation page comes into picture and then click on install.
These steps will help in installing print servers.
Few minutes later roles are installed and conformation page appears.
In order to add a printing device to this server, again click on server manager, click on roles
button and go to print services.
Click on add and share a printer on a network.
In print server section, search the network for printers. This will show all the printers that are
installed in the network and select the network.
Terminal services
Terminal servers can be defined as a type of server or network device that helps in
connecting multiple client systems to a single network interface. It is one of the main service
which is provided by Microsoft Windows servers operating system. In other words it helps in
communicating with more than one network servers that are connected with the host server
simultaneously. This server provides terminals such as printers, PC’s etc. with a common
connection point connected to a single host server.
Advantages of terminal servers
18
Then confirmation page comes into picture and then click on install.
These steps will help in installing print servers.
Few minutes later roles are installed and conformation page appears.
In order to add a printing device to this server, again click on server manager, click on roles
button and go to print services.
Click on add and share a printer on a network.
In print server section, search the network for printers. This will show all the printers that are
installed in the network and select the network.
Terminal services
Terminal servers can be defined as a type of server or network device that helps in
connecting multiple client systems to a single network interface. It is one of the main service
which is provided by Microsoft Windows servers operating system. In other words it helps in
communicating with more than one network servers that are connected with the host server
simultaneously. This server provides terminals such as printers, PC’s etc. with a common
connection point connected to a single host server.
Advantages of terminal servers
18
There are various advantages of terminal servers but main advantages of terminal servers are
such as:
It provides access to a system at any time and from anywhere.
Because of single point of maintenance, application updates become much easier as there is
only one copy of each application.
All the application in this server are installed only once but can be used by everyone at the
same time
It also helps in reducing per users’ monthly cosy
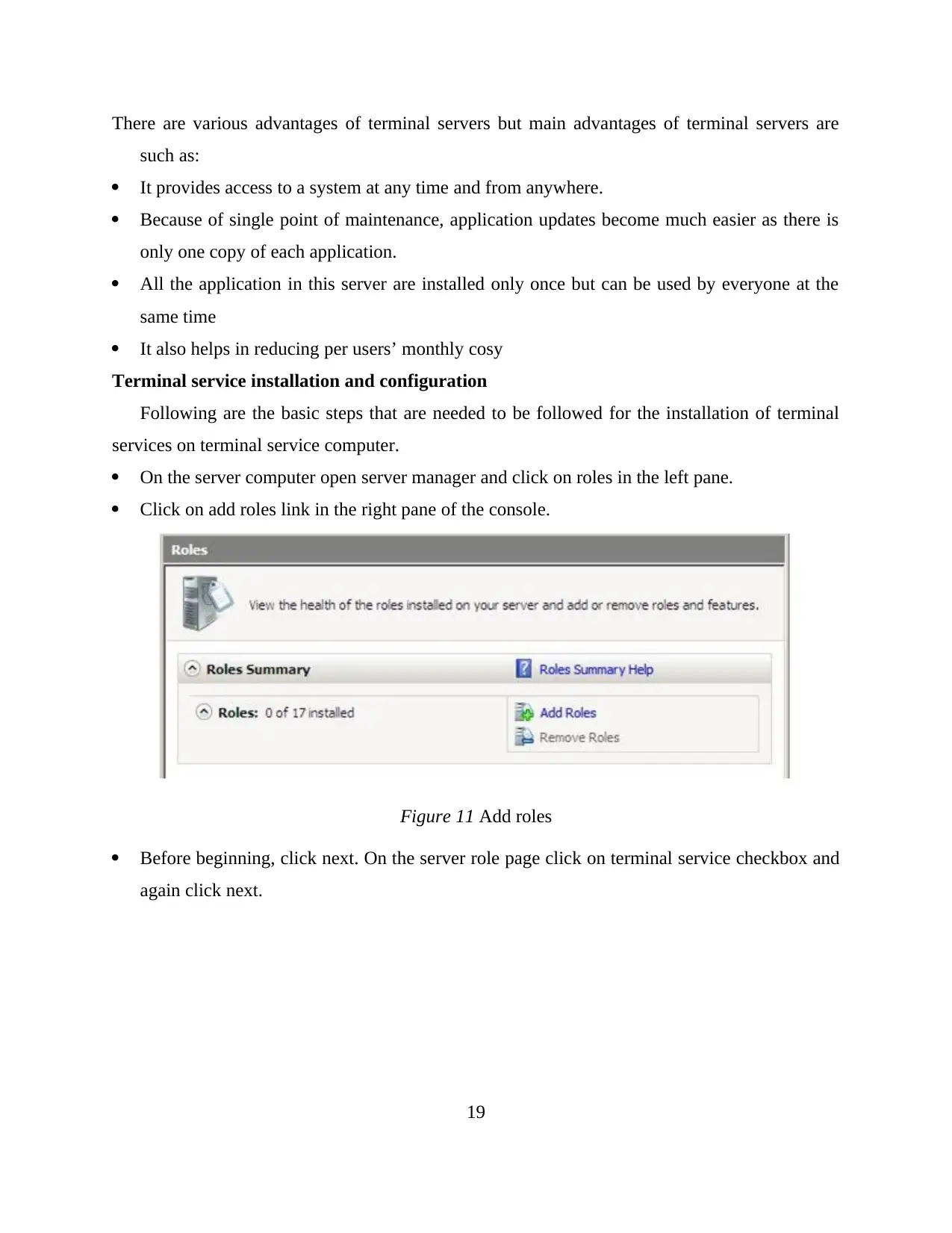
Terminal service installation and configuration
Following are the basic steps that are needed to be followed for the installation of terminal
services on terminal service computer.
On the server computer open server manager and click on roles in the left pane.
Click on add roles link in the right pane of the console.
Figure 11 Add roles
Before beginning, click next. On the server role page click on terminal service checkbox and
again click next.
19
such as:
It provides access to a system at any time and from anywhere.
Because of single point of maintenance, application updates become much easier as there is
only one copy of each application.
All the application in this server are installed only once but can be used by everyone at the
same time
It also helps in reducing per users’ monthly cosy
Terminal service installation and configuration
Following are the basic steps that are needed to be followed for the installation of terminal
services on terminal service computer.
On the server computer open server manager and click on roles in the left pane.
Click on add roles link in the right pane of the console.
Figure 11 Add roles
Before beginning, click next. On the server role page click on terminal service checkbox and
again click next.
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
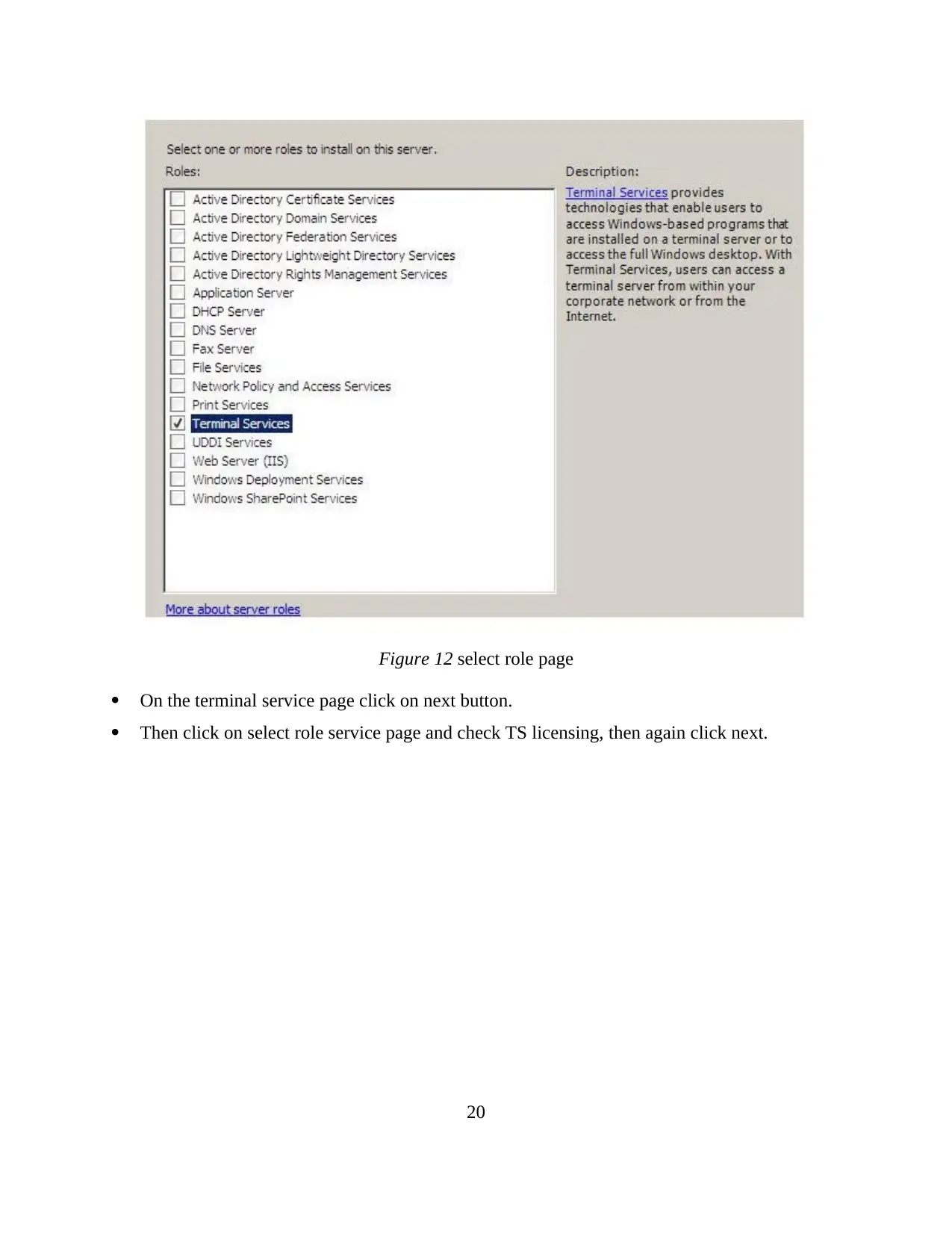
Figure 12 select role page
On the terminal service page click on next button.
Then click on select role service page and check TS licensing, then again click next.
20
On the terminal service page click on next button.
Then click on select role service page and check TS licensing, then again click next.
20
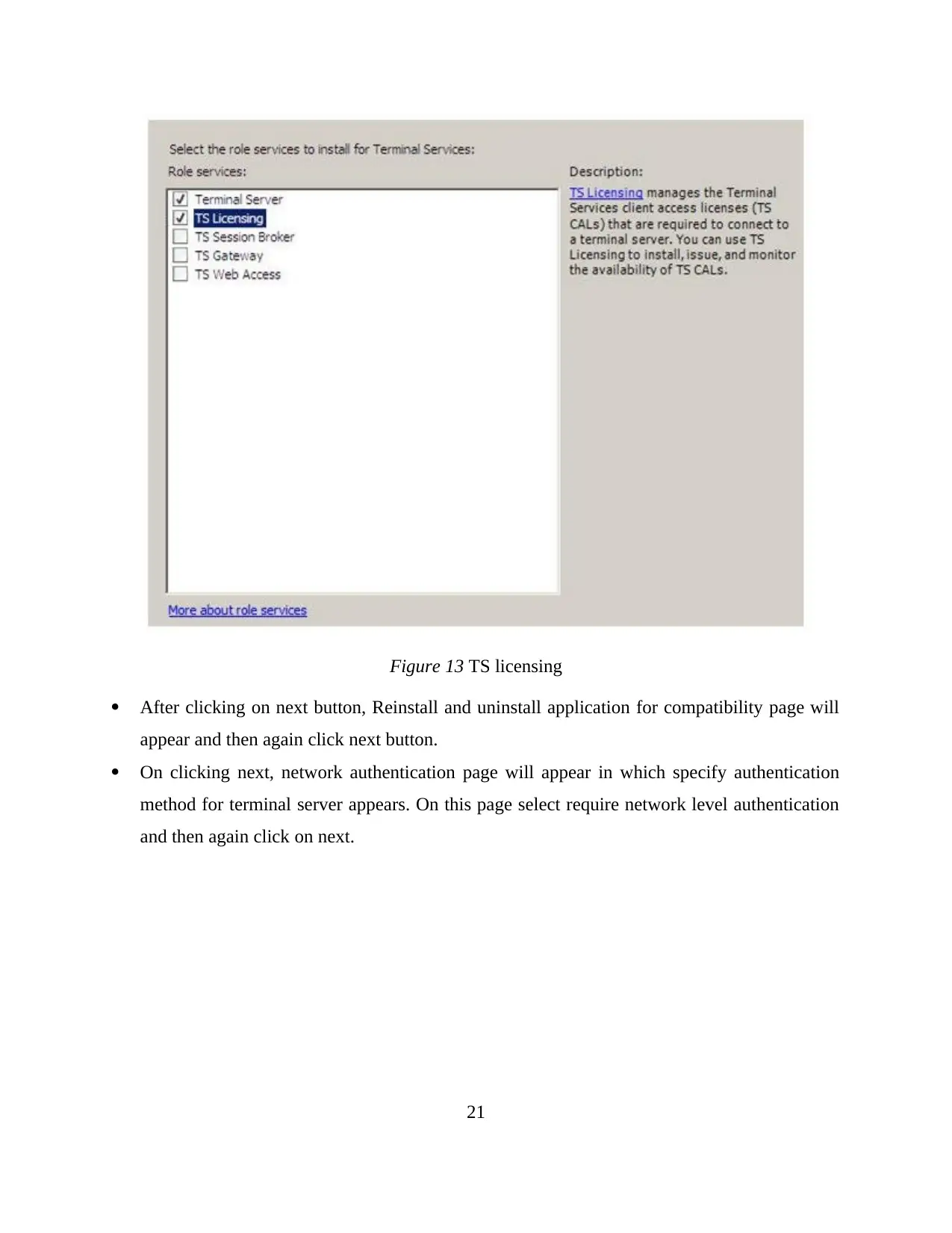
Figure 13 TS licensing
After clicking on next button, Reinstall and uninstall application for compatibility page will
appear and then again click next button.
On clicking next, network authentication page will appear in which specify authentication
method for terminal server appears. On this page select require network level authentication
and then again click on next.
21
After clicking on next button, Reinstall and uninstall application for compatibility page will
appear and then again click next button.
On clicking next, network authentication page will appear in which specify authentication
method for terminal server appears. On this page select require network level authentication
and then again click on next.
21
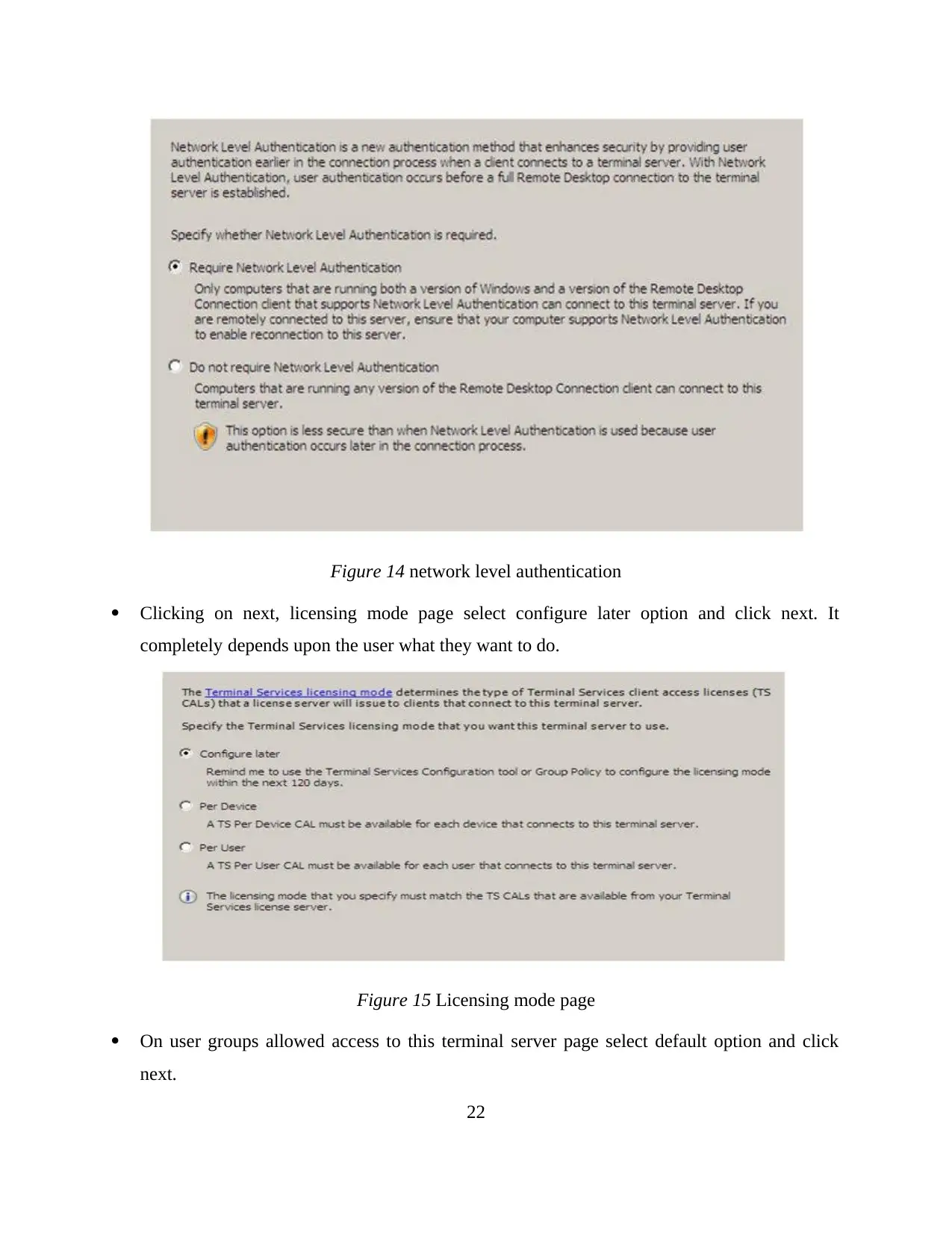
Figure 14 network level authentication
Clicking on next, licensing mode page select configure later option and click next. It
completely depends upon the user what they want to do.
Figure 15 Licensing mode page
On user groups allowed access to this terminal server page select default option and click
next.
22
Clicking on next, licensing mode page select configure later option and click next. It
completely depends upon the user what they want to do.
Figure 15 Licensing mode page
On user groups allowed access to this terminal server page select default option and click
next.
22
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
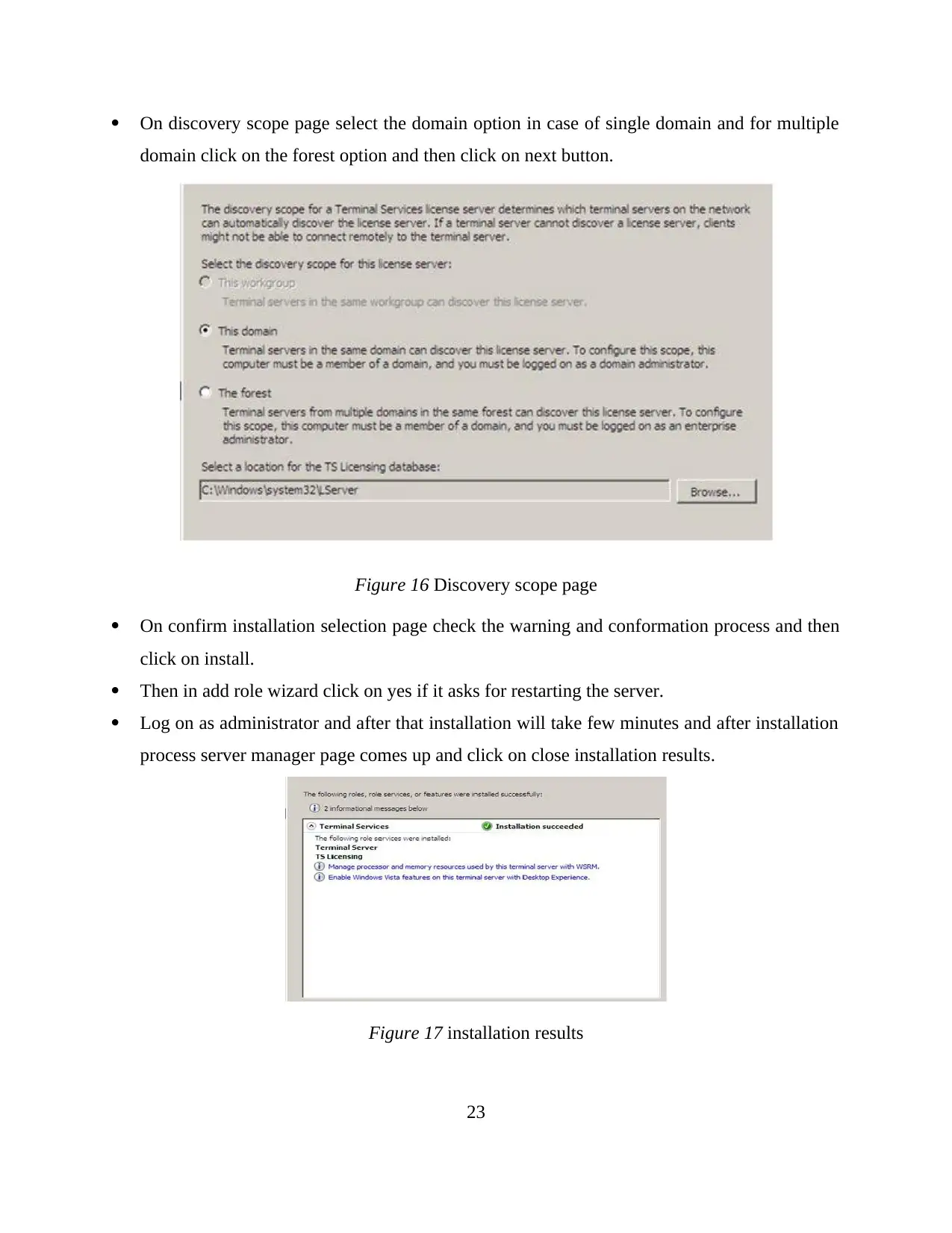
On discovery scope page select the domain option in case of single domain and for multiple
domain click on the forest option and then click on next button.
Figure 16 Discovery scope page
On confirm installation selection page check the warning and conformation process and then
click on install.
Then in add role wizard click on yes if it asks for restarting the server.
Log on as administrator and after that installation will take few minutes and after installation
process server manager page comes up and click on close installation results.
Figure 17 installation results
23
domain click on the forest option and then click on next button.
Figure 16 Discovery scope page
On confirm installation selection page check the warning and conformation process and then
click on install.
Then in add role wizard click on yes if it asks for restarting the server.
Log on as administrator and after that installation will take few minutes and after installation
process server manager page comes up and click on close installation results.
Figure 17 installation results
23
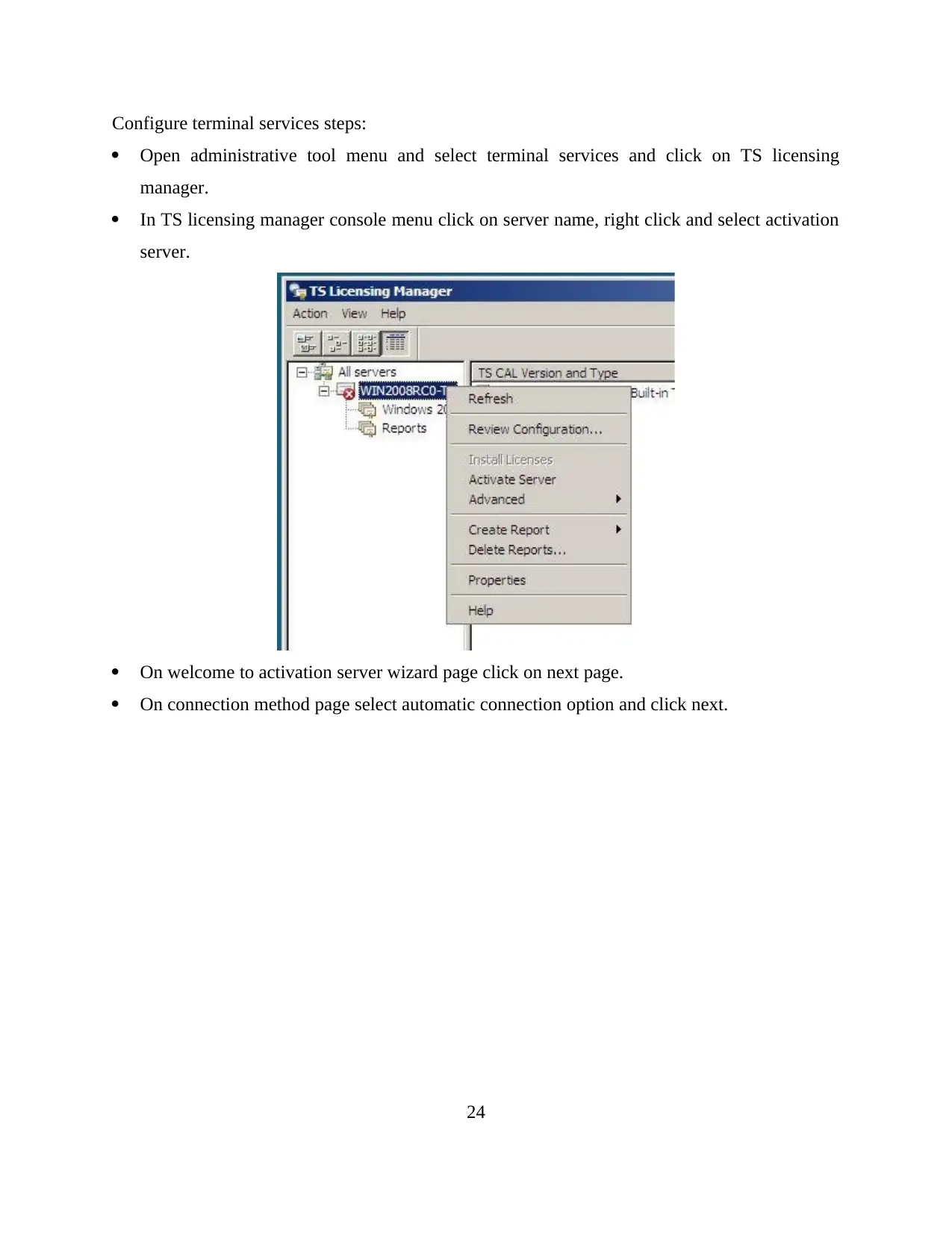
Configure terminal services steps:
Open administrative tool menu and select terminal services and click on TS licensing
manager.
In TS licensing manager console menu click on server name, right click and select activation
server.
On welcome to activation server wizard page click on next page.
On connection method page select automatic connection option and click next.
24
Open administrative tool menu and select terminal services and click on TS licensing
manager.
In TS licensing manager console menu click on server name, right click and select activation
server.
On welcome to activation server wizard page click on next page.
On connection method page select automatic connection option and click next.
24
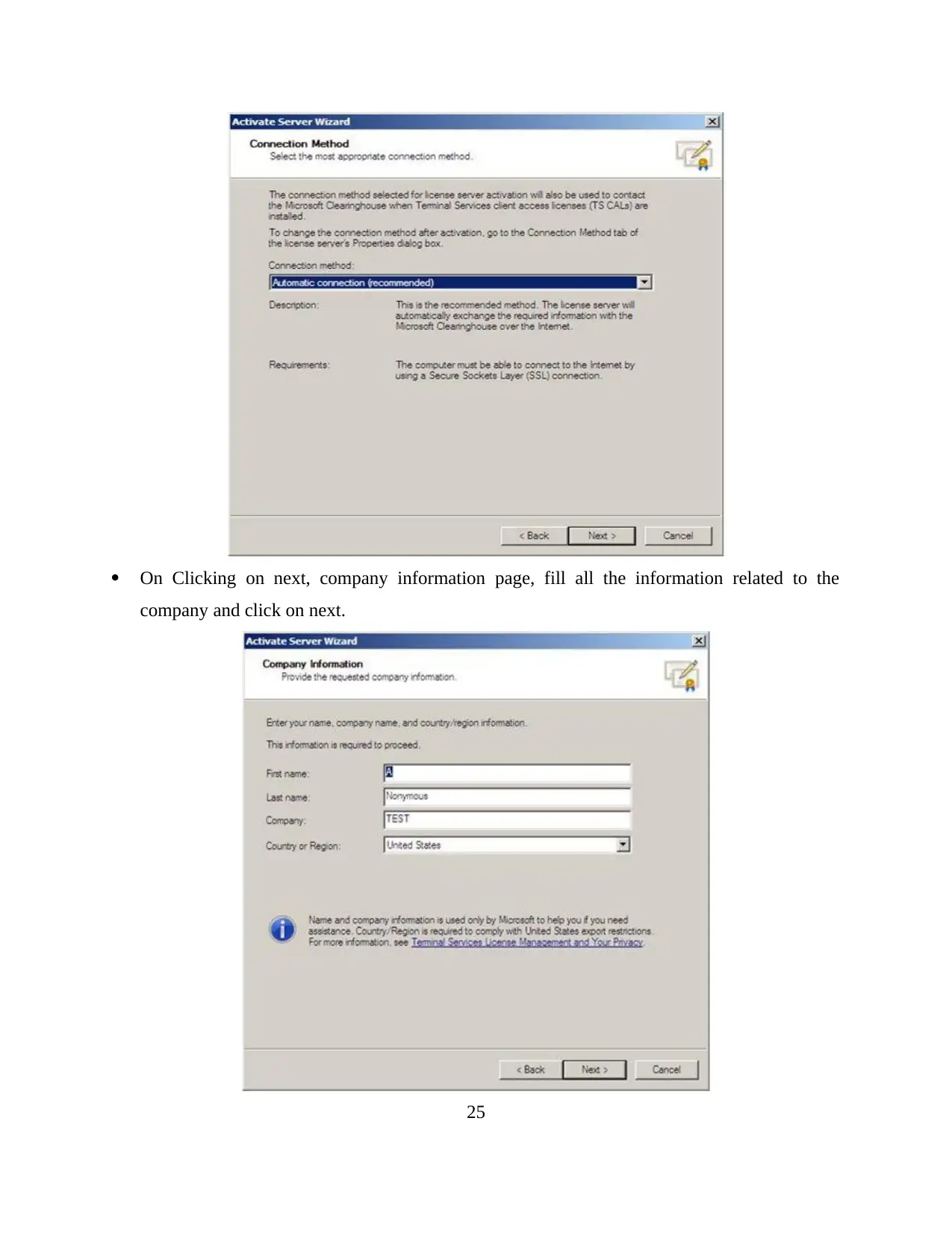
On Clicking on next, company information page, fill all the information related to the
company and click on next.
25
company and click on next.
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
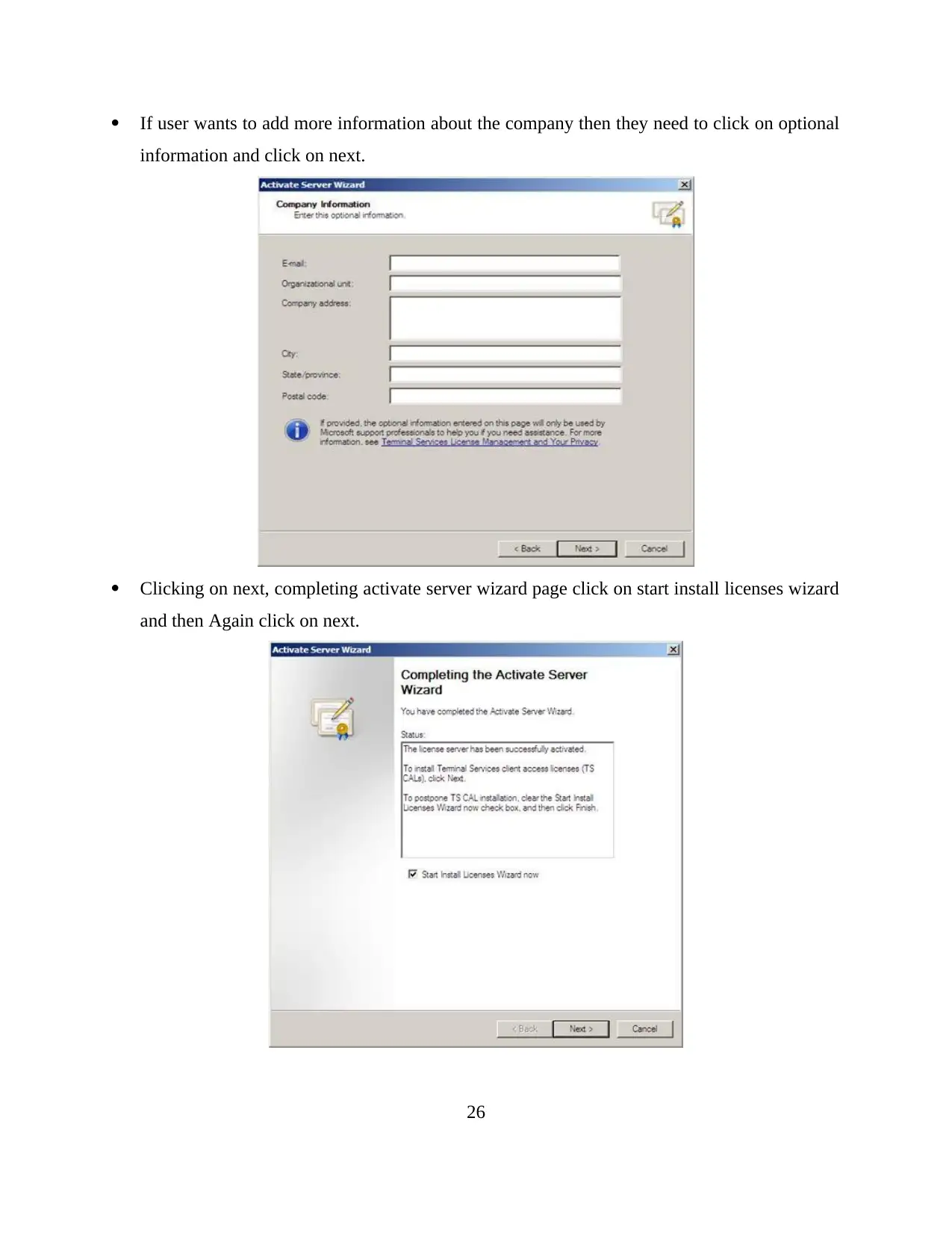
If user wants to add more information about the company then they need to click on optional
information and click on next.
Clicking on next, completing activate server wizard page click on start install licenses wizard
and then Again click on next.
26
information and click on next.
Clicking on next, completing activate server wizard page click on start install licenses wizard
and then Again click on next.
26
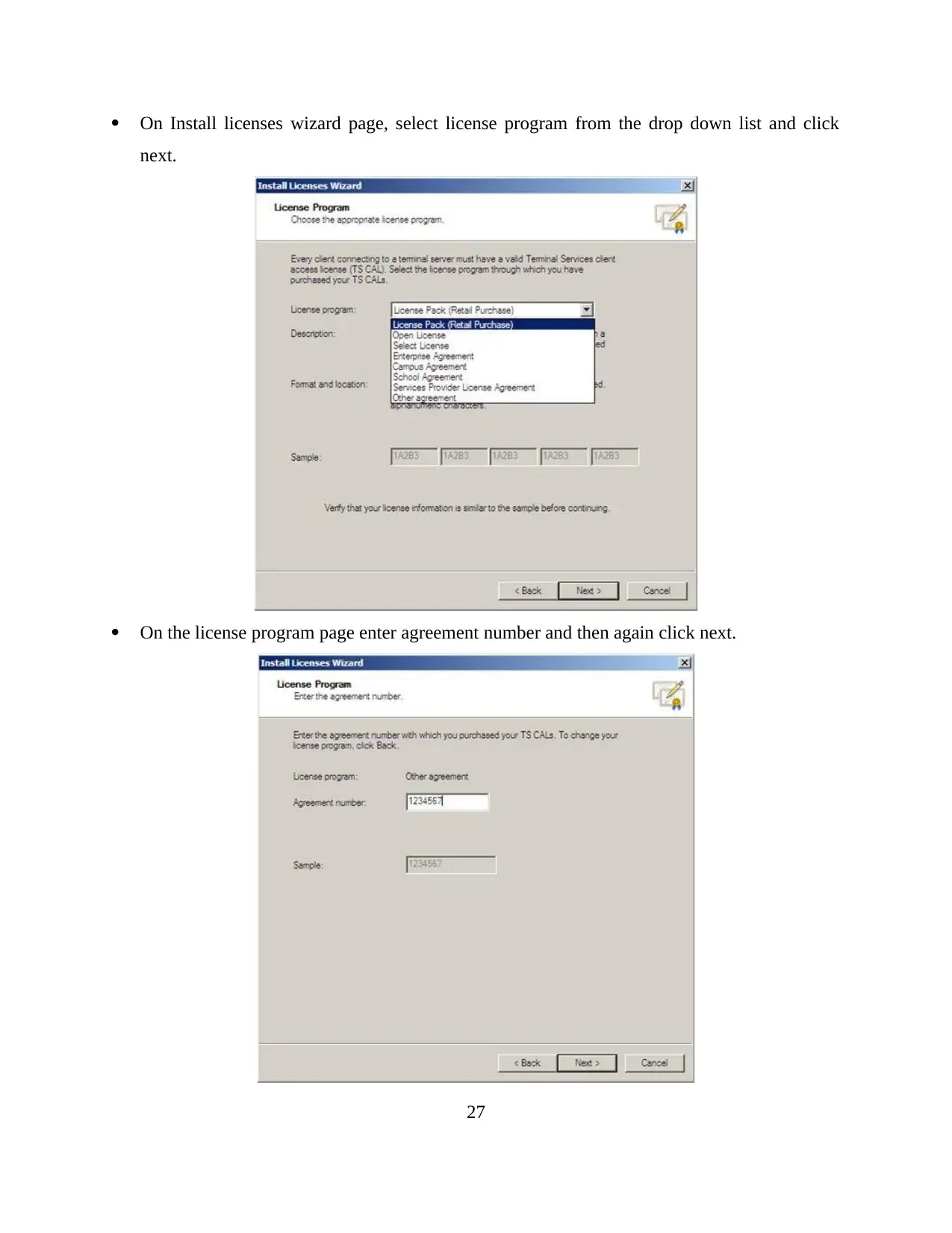
On Install licenses wizard page, select license program from the drop down list and click
next.
On the license program page enter agreement number and then again click next.
27
next.
On the license program page enter agreement number and then again click next.
27
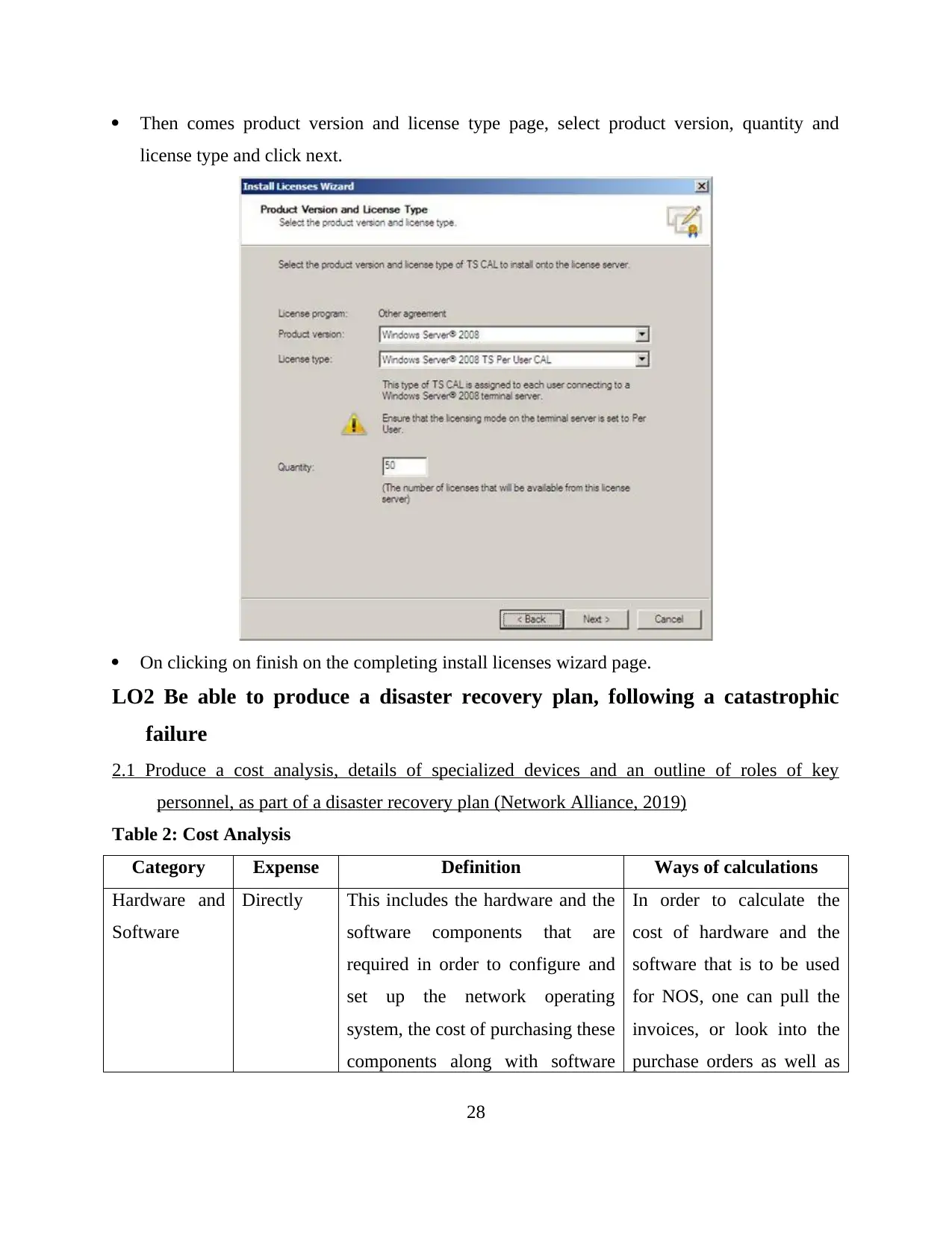
Then comes product version and license type page, select product version, quantity and
license type and click next.
On clicking on finish on the completing install licenses wizard page.
LO2 Be able to produce a disaster recovery plan, following a catastrophic
failure
2.1 Produce a cost analysis, details of specialized devices and an outline of roles of key
personnel, as part of a disaster recovery plan (Network Alliance, 2019)
Table 2: Cost Analysis
Category Expense Definition Ways of calculations
Hardware and
Software
Directly This includes the hardware and the
software components that are
required in order to configure and
set up the network operating
system, the cost of purchasing these
components along with software
In order to calculate the
cost of hardware and the
software that is to be used
for NOS, one can pull the
invoices, or look into the
purchase orders as well as
28
license type and click next.
On clicking on finish on the completing install licenses wizard page.
LO2 Be able to produce a disaster recovery plan, following a catastrophic
failure
2.1 Produce a cost analysis, details of specialized devices and an outline of roles of key
personnel, as part of a disaster recovery plan (Network Alliance, 2019)
Table 2: Cost Analysis
Category Expense Definition Ways of calculations
Hardware and
Software
Directly This includes the hardware and the
software components that are
required in order to configure and
set up the network operating
system, the cost of purchasing these
components along with software
In order to calculate the
cost of hardware and the
software that is to be used
for NOS, one can pull the
invoices, or look into the
purchase orders as well as
28
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
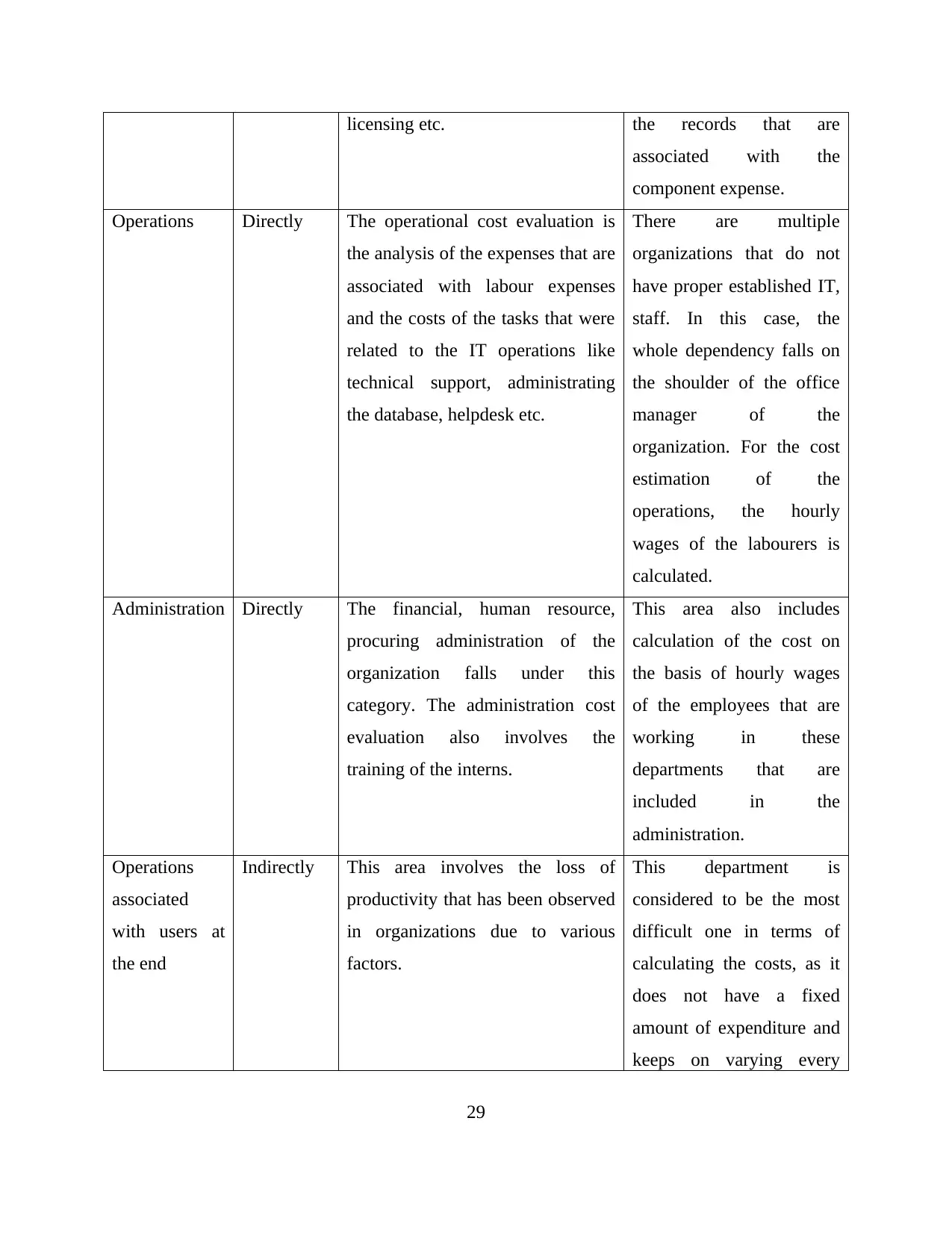
licensing etc. the records that are
associated with the
component expense.
Operations Directly The operational cost evaluation is
the analysis of the expenses that are
associated with labour expenses
and the costs of the tasks that were
related to the IT operations like
technical support, administrating
the database, helpdesk etc.
There are multiple
organizations that do not
have proper established IT,
staff. In this case, the
whole dependency falls on
the shoulder of the office
manager of the
organization. For the cost
estimation of the
operations, the hourly
wages of the labourers is
calculated.
Administration Directly The financial, human resource,
procuring administration of the
organization falls under this
category. The administration cost
evaluation also involves the
training of the interns.
This area also includes
calculation of the cost on
the basis of hourly wages
of the employees that are
working in these
departments that are
included in the
administration.
Operations
associated
with users at
the end
Indirectly This area involves the loss of
productivity that has been observed
in organizations due to various
factors.
This department is
considered to be the most
difficult one in terms of
calculating the costs, as it
does not have a fixed
amount of expenditure and
keeps on varying every
29
associated with the
component expense.
Operations Directly The operational cost evaluation is
the analysis of the expenses that are
associated with labour expenses
and the costs of the tasks that were
related to the IT operations like
technical support, administrating
the database, helpdesk etc.
There are multiple
organizations that do not
have proper established IT,
staff. In this case, the
whole dependency falls on
the shoulder of the office
manager of the
organization. For the cost
estimation of the
operations, the hourly
wages of the labourers is
calculated.
Administration Directly The financial, human resource,
procuring administration of the
organization falls under this
category. The administration cost
evaluation also involves the
training of the interns.
This area also includes
calculation of the cost on
the basis of hourly wages
of the employees that are
working in these
departments that are
included in the
administration.
Operations
associated
with users at
the end
Indirectly This area involves the loss of
productivity that has been observed
in organizations due to various
factors.
This department is
considered to be the most
difficult one in terms of
calculating the costs, as it
does not have a fixed
amount of expenditure and
keeps on varying every
29
time. Yet this department
produces highest TCO
among all the departments.
Down Period Indirectly This phase consists of the
productivity reduction and
expenses due to the failure of the
machines, system or issues in the
internet connectivity.
In order to evaluate the
cost that has been
expended due to the failure
of a system, the hours for
which the system or the
connectivity was down is
calculated along with the
maintenance cost of the
whole configuration of the
different system of the
organizations.
2.2 Analyse backup and data storage requirements following a catastrophic failure
Among the major characteristics of the NOS has to be the administrative interface it has that
enables the network administration department to have a keen eye and also perform the
maintenance tasks over the systems. This administrative UI includes a legit enlistment that
enables the administration department to do the methods like formatting the hard discs and
configuring the safety measures for both the systems and the particular customer or the consumer
of the network operating system. The user may also have the ability to set up the safety and
information backup requirement for the systems or the whole big network. However, the network
-based operating systems is also having proper expertise in various tasks. For instance, whenever
the network-based gadgets are taken in use, like printer and disk drive etc., the network-based
operating systems make sure that these sources are having their appropriate usage and efficiency.
The expertise tasks involve security of the network as well as their administration. This includes
the hardware and the software components that are required in order to configure and set up the
network operating system, the cost of purchasing these components along with software
licensing etc. However, the basic aim of the backup creation over the network operating systems
30
produces highest TCO
among all the departments.
Down Period Indirectly This phase consists of the
productivity reduction and
expenses due to the failure of the
machines, system or issues in the
internet connectivity.
In order to evaluate the
cost that has been
expended due to the failure
of a system, the hours for
which the system or the
connectivity was down is
calculated along with the
maintenance cost of the
whole configuration of the
different system of the
organizations.
2.2 Analyse backup and data storage requirements following a catastrophic failure
Among the major characteristics of the NOS has to be the administrative interface it has that
enables the network administration department to have a keen eye and also perform the
maintenance tasks over the systems. This administrative UI includes a legit enlistment that
enables the administration department to do the methods like formatting the hard discs and
configuring the safety measures for both the systems and the particular customer or the consumer
of the network operating system. The user may also have the ability to set up the safety and
information backup requirement for the systems or the whole big network. However, the network
-based operating systems is also having proper expertise in various tasks. For instance, whenever
the network-based gadgets are taken in use, like printer and disk drive etc., the network-based
operating systems make sure that these sources are having their appropriate usage and efficiency.
The expertise tasks involve security of the network as well as their administration. This includes
the hardware and the software components that are required in order to configure and set up the
network operating system, the cost of purchasing these components along with software
licensing etc. However, the basic aim of the backup creation over the network operating systems
30

in the various organizations is to prevent the NOS from the loss of data in case of system failure
or in the case of any kind of catastrophic failure, buy storing an extra copy of data at a safe
location which would not be affected by any virus attack or the system failure and hence the data
would be failed, the execution of the backup creation does not require to be completely in
relevance with the surrounding of chaos and emergencies, but instead must be observed as a
component of the operational platforms of the company that prevents the information from being
lost, and as it is very clear that information can be considered to be one of the most valuable
resources for any organization.
RAID Implementation
RAID is also known as redundant array of independent disks. It is a data storage
virtualization technology that helps in combining various kinds of physical disk drivers into one
of more than one logical unit for improvement in performance, data redundancy so many times
both. Here are following requirements that are required to be considered in case of catastrophic
failures like system attack, electrical power non-performance, malware attacks etc. These
requirements fulfilment works as a disaster recovery plan.
Backup servers: It is one of the most prominent requirements that can be used for files, data
or programs backup. It can help in retaining all the required data in case of server or event
malfunctioning or in any other kind of circumstances that are beyond the control of an
individual. It helps in creating sufficient space for storage for storing or backing up system
network and all the other programs. It also helps in updating drives with time in order to
reduce security risks.
Uninterrupted power supply (UPS): in order to avoid instability in the power within the
network UPS is required in order to improve reliability of the network. It is most of the times
used as secondary power source when there is a power shut down or whenever administrator
needs some time to close down many important or vital task. Whenever there is a
requirement to fix power source or network issues, it can be used to supply power to the
network and can be used for many hours together.
Multiple servers: Another requirement which is required to be focused on in case of
catastrophic failure is multiple servers. These multiple number of servers are required so that
more than one server can be used to supply services in case one of the main server breaks
down or in case of server failures. In such case other servers can be given option of carrying
31
or in the case of any kind of catastrophic failure, buy storing an extra copy of data at a safe
location which would not be affected by any virus attack or the system failure and hence the data
would be failed, the execution of the backup creation does not require to be completely in
relevance with the surrounding of chaos and emergencies, but instead must be observed as a
component of the operational platforms of the company that prevents the information from being
lost, and as it is very clear that information can be considered to be one of the most valuable
resources for any organization.
RAID Implementation
RAID is also known as redundant array of independent disks. It is a data storage
virtualization technology that helps in combining various kinds of physical disk drivers into one
of more than one logical unit for improvement in performance, data redundancy so many times
both. Here are following requirements that are required to be considered in case of catastrophic
failures like system attack, electrical power non-performance, malware attacks etc. These
requirements fulfilment works as a disaster recovery plan.
Backup servers: It is one of the most prominent requirements that can be used for files, data
or programs backup. It can help in retaining all the required data in case of server or event
malfunctioning or in any other kind of circumstances that are beyond the control of an
individual. It helps in creating sufficient space for storage for storing or backing up system
network and all the other programs. It also helps in updating drives with time in order to
reduce security risks.
Uninterrupted power supply (UPS): in order to avoid instability in the power within the
network UPS is required in order to improve reliability of the network. It is most of the times
used as secondary power source when there is a power shut down or whenever administrator
needs some time to close down many important or vital task. Whenever there is a
requirement to fix power source or network issues, it can be used to supply power to the
network and can be used for many hours together.
Multiple servers: Another requirement which is required to be focused on in case of
catastrophic failure is multiple servers. These multiple number of servers are required so that
more than one server can be used to supply services in case one of the main server breaks
down or in case of server failures. In such case other servers can be given option of carrying
31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

servers such that there is no disturbance in the network or any other kind of issue is not
created.
Server clustering: it can also be used as a service for applications and servers. For this
various network from different sites can be used providing cluster services. In case of any
disaster or failure, work which is most of the time done by the failed server can be transferred
to another server which is present in the server cluster so that all the other network related
services can be continued without any other issue or disturbance.
RAID Tools: it is another one of the requirements which is required to be focused on in case of
catastrophic failure. Various kinds of reductant disks (Trifonov, 2015). RAID tool can help in
protecting failure of physical disk and in case of catastrophic failure, it exceeds the recovery
captivity and stores backup at off site so that it is not affected due to a failure. Majorly it helps in
protecting data loss without any issues or problems. There are various level of RAID that can be
used to store reliable data. These levels help in protecting data from any kind of failure. Most
commonly used levels are RAID level 0,1, 5 and six.
RAID 0: in this data is evenly Striped across two or more than two disks without any
kind of fault tolerance, redundancy etc. and because of this in case of any kind of failure
entire array can get failed.
RAID 1: it holds exact copy of data present in two or more than two disks. Data is
mirrored across all the disks belonging to the array.
RAID 2: it is rarely used in practise but it strips the data at bit level and uses hamming
codes for error detection (Lu and Zhou, 2016).
RAID 3: It is also rarely used in practise and consist of byte level of stripping with
dedicated parity disk but it has a problem i.e. it cannot serve multiple service request
simultaneously.
RAID 4: it consists of block level stripping with a dedicated parity disk.
RAID 5: it also consists of block level stripping with a dedicated parity disk but in this
parity, information is distributed among the drivers. This RAID level requires minimum
of three levels.
RAID 6: in this RAID 5 is extended and another parity block is added. This level of
RAID uses block level of stripping where two parity blocks are distributed across all the
disks members. It is most commonly used in IT firms of increasing security of data.
32
created.
Server clustering: it can also be used as a service for applications and servers. For this
various network from different sites can be used providing cluster services. In case of any
disaster or failure, work which is most of the time done by the failed server can be transferred
to another server which is present in the server cluster so that all the other network related
services can be continued without any other issue or disturbance.
RAID Tools: it is another one of the requirements which is required to be focused on in case of
catastrophic failure. Various kinds of reductant disks (Trifonov, 2015). RAID tool can help in
protecting failure of physical disk and in case of catastrophic failure, it exceeds the recovery
captivity and stores backup at off site so that it is not affected due to a failure. Majorly it helps in
protecting data loss without any issues or problems. There are various level of RAID that can be
used to store reliable data. These levels help in protecting data from any kind of failure. Most
commonly used levels are RAID level 0,1, 5 and six.
RAID 0: in this data is evenly Striped across two or more than two disks without any
kind of fault tolerance, redundancy etc. and because of this in case of any kind of failure
entire array can get failed.
RAID 1: it holds exact copy of data present in two or more than two disks. Data is
mirrored across all the disks belonging to the array.
RAID 2: it is rarely used in practise but it strips the data at bit level and uses hamming
codes for error detection (Lu and Zhou, 2016).
RAID 3: It is also rarely used in practise and consist of byte level of stripping with
dedicated parity disk but it has a problem i.e. it cannot serve multiple service request
simultaneously.
RAID 4: it consists of block level stripping with a dedicated parity disk.
RAID 5: it also consists of block level stripping with a dedicated parity disk but in this
parity, information is distributed among the drivers. This RAID level requires minimum
of three levels.
RAID 6: in this RAID 5 is extended and another parity block is added. This level of
RAID uses block level of stripping where two parity blocks are distributed across all the
disks members. It is most commonly used in IT firms of increasing security of data.
32

LO3 Be able to evaluate the performance of a network operating system
3.1 Analyse the tools available for the performance monitoring of a network operating system
Following are the tools that are used to monitor the performance of the network operating
system.
Windows Performance Monitor: Windows Performance Monitor is one of the obvious
options which are present in this enlistment for monitoring the performance of the network
operating system. This tool is having its usage for observing the performance of the system
overall the platforms such as application levels and over the hardware levels. There is a big
variety of metrics form which the department that can be chosen. The limits which trigger the
alerts, as well as the automatic actions, can also be defined by the help of the windows
performance monitor (Bacula Systems, 2019).
Figure 18 Figure 8: Windows Performance Monitor
(Source: Marcho, 2019)
Microsoft Operations Manager: This is the type of the tool that is used for monitoring the
complete fleets of the servers, the application of the server and the networks by the help of
33
3.1 Analyse the tools available for the performance monitoring of a network operating system
Following are the tools that are used to monitor the performance of the network operating
system.
Windows Performance Monitor: Windows Performance Monitor is one of the obvious
options which are present in this enlistment for monitoring the performance of the network
operating system. This tool is having its usage for observing the performance of the system
overall the platforms such as application levels and over the hardware levels. There is a big
variety of metrics form which the department that can be chosen. The limits which trigger the
alerts, as well as the automatic actions, can also be defined by the help of the windows
performance monitor (Bacula Systems, 2019).
Figure 18 Figure 8: Windows Performance Monitor
(Source: Marcho, 2019)
Microsoft Operations Manager: This is the type of the tool that is used for monitoring the
complete fleets of the servers, the application of the server and the networks by the help of
33

the centralized UI. It is also one of the many tools that are introduced in the Microsoft
System Management tools. The main task of the Microsoft operations manager is to look
after the whole system of the network of computers. It is also having the ability to look after
the server, router, switch, firewall, AWS system and Azure server and at some instances even
the Linux servers (Bacula Systems, 2019).
Figure 19 Microsoft Performance Manager
((Source: Trent, 2015))
Typeperf: The Typeperf is a command line tool that has its usage for showing the various
counters of the performance of the networking systems. It basically shows the list of the
counters that are present at the moment along with their respected magnitudes. The output of
the typeperf can be seen over the command line or it can also be written on the log files. The
typeperf also provides the user, the accessibility to the characteristics of the windows
performance monitor by the help of the command line. The main focus of the Typeperf is on
the querying of the counter and it generally avoids the command over creating the logs
(Bacula Systems, 2019).
34
System Management tools. The main task of the Microsoft operations manager is to look
after the whole system of the network of computers. It is also having the ability to look after
the server, router, switch, firewall, AWS system and Azure server and at some instances even
the Linux servers (Bacula Systems, 2019).
Figure 19 Microsoft Performance Manager
((Source: Trent, 2015))
Typeperf: The Typeperf is a command line tool that has its usage for showing the various
counters of the performance of the networking systems. It basically shows the list of the
counters that are present at the moment along with their respected magnitudes. The output of
the typeperf can be seen over the command line or it can also be written on the log files. The
typeperf also provides the user, the accessibility to the characteristics of the windows
performance monitor by the help of the command line. The main focus of the Typeperf is on
the querying of the counter and it generally avoids the command over creating the logs
(Bacula Systems, 2019).
34
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
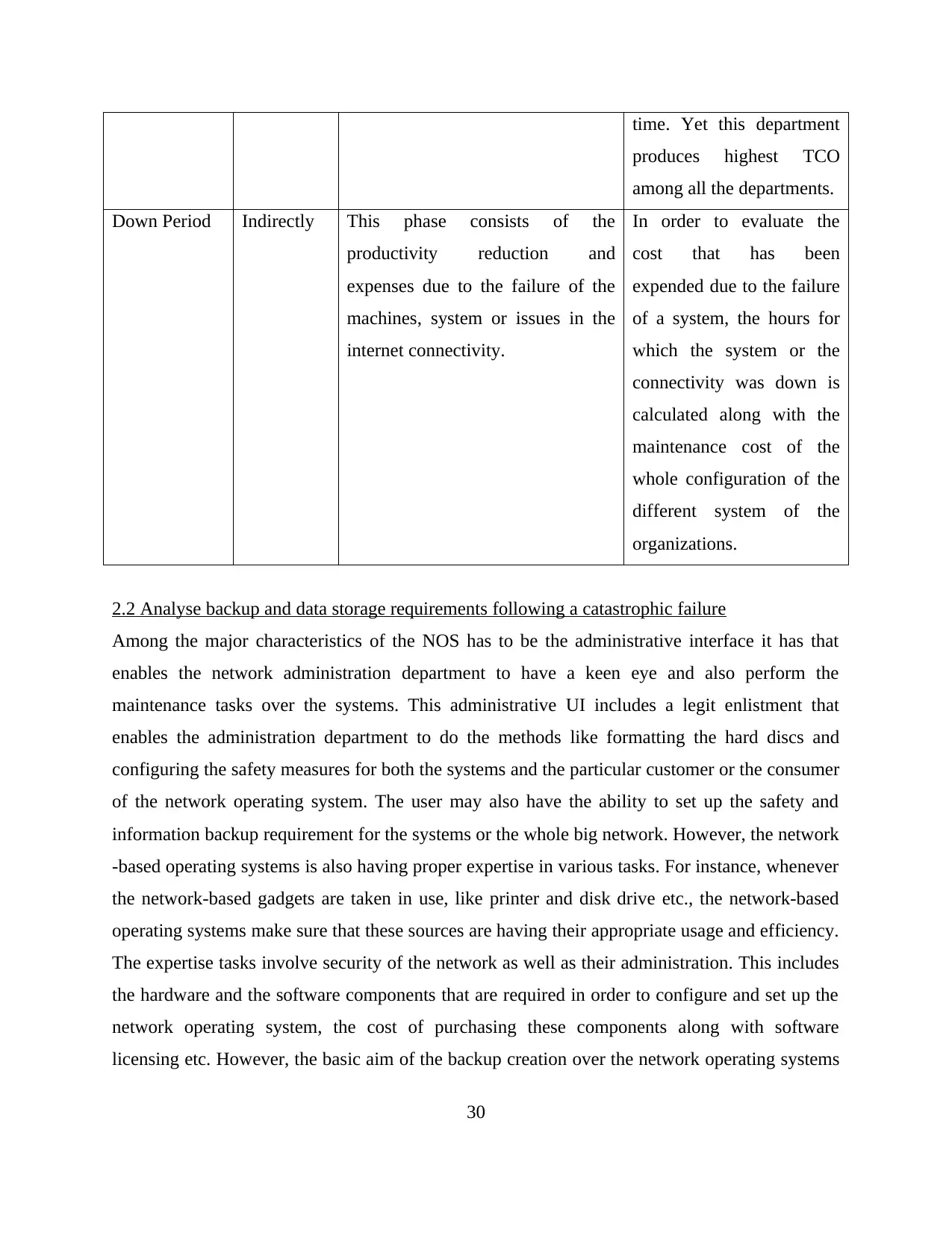
Figure 20 Typeperf
((Source: Genie, 2012))
Monitoring of event log
Windows event viewer helps in displaying event logs (Sciencedirect, 2019). This helps in
navigating or viewing logs, search, export logs for analysis etc. In order to access event viewer in
window’s 7 follow following steps:
Click on start, Open control panel. Click on system and security and again click on
administrative tool and select event viewer.
Select the type of log user wants to viewer review, for example: Windows logs.
35
((Source: Genie, 2012))
Monitoring of event log
Windows event viewer helps in displaying event logs (Sciencedirect, 2019). This helps in
navigating or viewing logs, search, export logs for analysis etc. In order to access event viewer in
window’s 7 follow following steps:
Click on start, Open control panel. Click on system and security and again click on
administrative tool and select event viewer.
Select the type of log user wants to viewer review, for example: Windows logs.
35

In order to export these log files, select the log user wants to export. Right click on that event
log and click on save all events as. Save the log file where ever user wants to save it and then
click on save option.
If users wants that no information should be displayed to the host computer then on display
information ‘no display information should be selected. ’
Programs in windows server
There are various kinds of services and programs present in the windows server:
Active directory domain: this service focuses on designing network domain. It provides a
quality service in order to Carry out design network (Sciencedirect, 2019).
DNS: main role of DNS is to connect all the networks together. It also supplies services to all
database records with respect to the IP addresses of the host systems.
DHCP: it helps in permitting IP addresses to host means of setting up host within the DHCP
server.
Terminal services: Helps the users to communicate required application across the network in
the distance.
File services: main task of this service is to handle all the files that are distributed to the
network for a particular task.
36
log and click on save all events as. Save the log file where ever user wants to save it and then
click on save option.
If users wants that no information should be displayed to the host computer then on display
information ‘no display information should be selected. ’
Programs in windows server
There are various kinds of services and programs present in the windows server:
Active directory domain: this service focuses on designing network domain. It provides a
quality service in order to Carry out design network (Sciencedirect, 2019).
DNS: main role of DNS is to connect all the networks together. It also supplies services to all
database records with respect to the IP addresses of the host systems.
DHCP: it helps in permitting IP addresses to host means of setting up host within the DHCP
server.
Terminal services: Helps the users to communicate required application across the network in
the distance.
File services: main task of this service is to handle all the files that are distributed to the
network for a particular task.
36
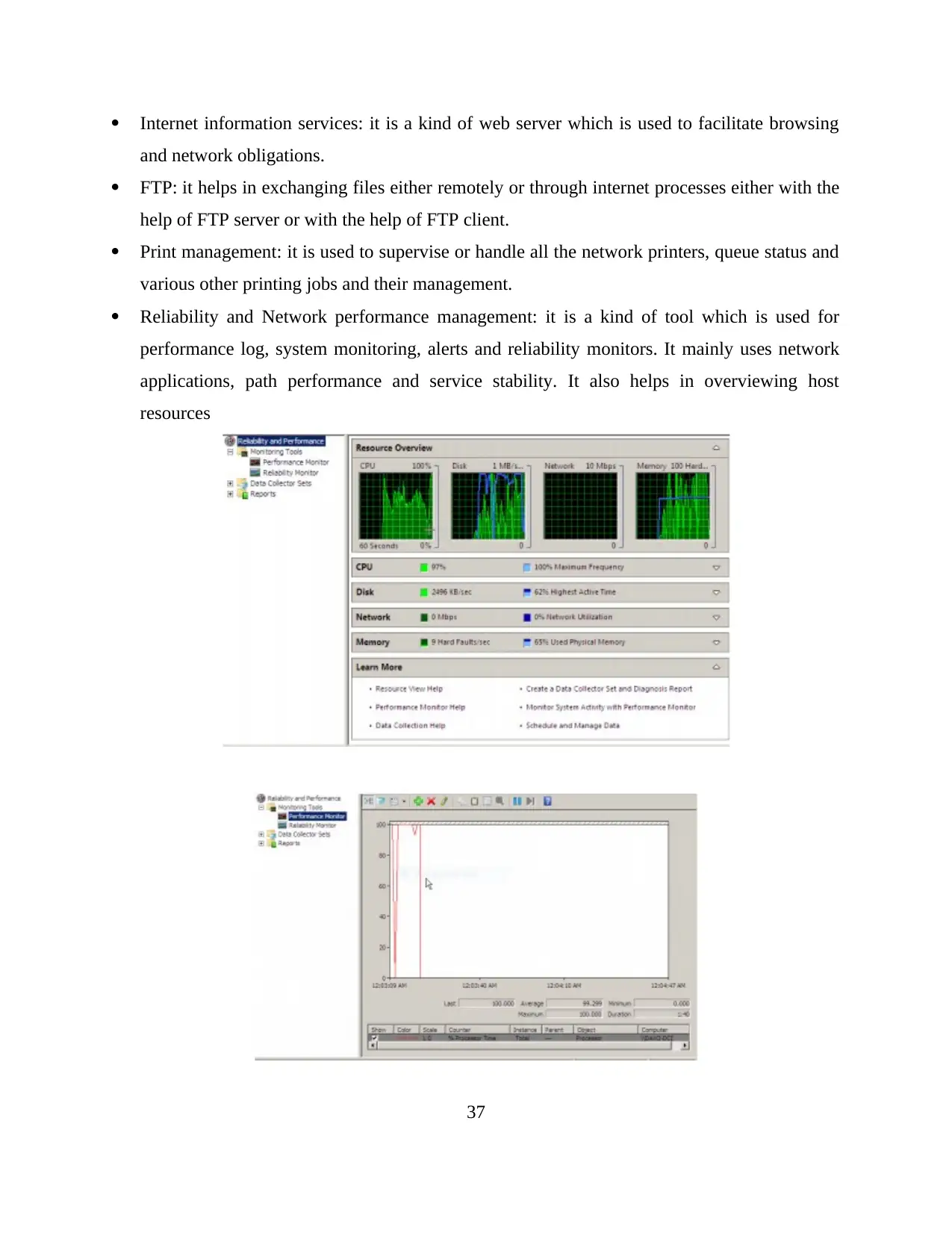
Internet information services: it is a kind of web server which is used to facilitate browsing
and network obligations.
FTP: it helps in exchanging files either remotely or through internet processes either with the
help of FTP server or with the help of FTP client.
Print management: it is used to supervise or handle all the network printers, queue status and
various other printing jobs and their management.
Reliability and Network performance management: it is a kind of tool which is used for
performance log, system monitoring, alerts and reliability monitors. It mainly uses network
applications, path performance and service stability. It also helps in overviewing host
resources
37
and network obligations.
FTP: it helps in exchanging files either remotely or through internet processes either with the
help of FTP server or with the help of FTP client.
Print management: it is used to supervise or handle all the network printers, queue status and
various other printing jobs and their management.
Reliability and Network performance management: it is a kind of tool which is used for
performance log, system monitoring, alerts and reliability monitors. It mainly uses network
applications, path performance and service stability. It also helps in overviewing host
resources
37
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Reliability and performance consist of monitoring tool where graphs and process of the
system can be monitored under performance monitor.
In order to check the stability of the network user can check reliability monitor as well.
3.2 Evaluate network performance and reliability under load conditions
The expertise tasks involve security of the network as well as their administration. This
includes the hardware and the software components that are required in order to configure and
set up the network operating system, the cost of purchasing these components along with
software licensing etc. (Ranjan, et. al., 2014). However, the basic aim of the backup creation
over the network operating systems in the various organizations is to prevent the NOS from the
loss of data in case of system failure or in the case of any kind of catastrophic failure, buy storing
an extra copy of data at a safe location which would not be affected by any virus attack or the
system failure and hence the data would be failed, the execution of the backup creation does not
required to be completely in relevance with the surrounding of chaos and emergencies, but
instead must be observed as a component of the operational platforms of the company that
prevents the information from being lost, and as it is very clear that information can be
considered to be one of the most valuable resources for any organization (Ranjan, et. al., 2014).
There are performance monitors such as windows performance monitor that is used for
evaluating the performance of the network operating system. This is the type of the tool that is
used for monitoring the complete fleets of the servers, the application of the server and the
networks by the help of the centralized UI (Ranjan, et. al., 2014). It is also one of the many tools
38
system can be monitored under performance monitor.
In order to check the stability of the network user can check reliability monitor as well.
3.2 Evaluate network performance and reliability under load conditions
The expertise tasks involve security of the network as well as their administration. This
includes the hardware and the software components that are required in order to configure and
set up the network operating system, the cost of purchasing these components along with
software licensing etc. (Ranjan, et. al., 2014). However, the basic aim of the backup creation
over the network operating systems in the various organizations is to prevent the NOS from the
loss of data in case of system failure or in the case of any kind of catastrophic failure, buy storing
an extra copy of data at a safe location which would not be affected by any virus attack or the
system failure and hence the data would be failed, the execution of the backup creation does not
required to be completely in relevance with the surrounding of chaos and emergencies, but
instead must be observed as a component of the operational platforms of the company that
prevents the information from being lost, and as it is very clear that information can be
considered to be one of the most valuable resources for any organization (Ranjan, et. al., 2014).
There are performance monitors such as windows performance monitor that is used for
evaluating the performance of the network operating system. This is the type of the tool that is
used for monitoring the complete fleets of the servers, the application of the server and the
networks by the help of the centralized UI (Ranjan, et. al., 2014). It is also one of the many tools
38

that are introduced in the Microsoft System Management tools. The main task of the Microsoft
operations manager is to look after the whole system of the network of computers. There are
multiple organizations that do not have proper established IT, staff. In this case, the whole
dependency falls on the shoulder of the office manager of the organization. For the cost
estimation of the operations, the hourly wages of the labourers is calculated. Hence the network
operating systems are considered to be getting better with every update (Ranjan, et. al., 2014).
LO4 Be able to evaluate the maintenance of a network operating system
4.1 Analyse the monitoring of event logs and programs
The Event logs and the programs allow the user to have access just the specific event that
is having some particular kind of features. In case the user is consistently using a particular type
of program or a set of programs in order to do the management of the event log, they must rather
produce a customized display. All the filters are applied just to a unit event log. The user would
also be having the ability to produce the programs on the basis of the logs on the below
mentioned characteristics (Sciencedirect, 2019):
The property Logged is having the responsibility to allow the user to particularly mention the
periodic scope of the program.
The property of event levels is having the responsibility of allowing the user to particularly
mention levels of the event. The user would be having the ability to choose the various
options to choose from such as critical warnings, verbose, errors and data.
The property known as the Event Sources is having the responsibility for the user to opt the
sources that are to be used in the event log and the program.
There is also a property of event IDs that is having the responsibility of for the user to allow
the filtration process on the basis of the primary key of the event log or the program
(Sciencedirect, 2019).
4.2 Evaluate the tools available for the monitoring and optimizing of network operating system
performance
TS Remote App Manager: By the help of the Windows Server 2008 TS RemoteApp, some
of the applications are specifically made accessible to the remote users and at the time of the
execution of the application, the provided significant network rate, it seems to the client that the
server is on the system that is being used by the user. TS RemoteApp is having the ability to
39
operations manager is to look after the whole system of the network of computers. There are
multiple organizations that do not have proper established IT, staff. In this case, the whole
dependency falls on the shoulder of the office manager of the organization. For the cost
estimation of the operations, the hourly wages of the labourers is calculated. Hence the network
operating systems are considered to be getting better with every update (Ranjan, et. al., 2014).
LO4 Be able to evaluate the maintenance of a network operating system
4.1 Analyse the monitoring of event logs and programs
The Event logs and the programs allow the user to have access just the specific event that
is having some particular kind of features. In case the user is consistently using a particular type
of program or a set of programs in order to do the management of the event log, they must rather
produce a customized display. All the filters are applied just to a unit event log. The user would
also be having the ability to produce the programs on the basis of the logs on the below
mentioned characteristics (Sciencedirect, 2019):
The property Logged is having the responsibility to allow the user to particularly mention the
periodic scope of the program.
The property of event levels is having the responsibility of allowing the user to particularly
mention levels of the event. The user would be having the ability to choose the various
options to choose from such as critical warnings, verbose, errors and data.
The property known as the Event Sources is having the responsibility for the user to opt the
sources that are to be used in the event log and the program.
There is also a property of event IDs that is having the responsibility of for the user to allow
the filtration process on the basis of the primary key of the event log or the program
(Sciencedirect, 2019).
4.2 Evaluate the tools available for the monitoring and optimizing of network operating system
performance
TS Remote App Manager: By the help of the Windows Server 2008 TS RemoteApp, some
of the applications are specifically made accessible to the remote users and at the time of the
execution of the application, the provided significant network rate, it seems to the client that the
server is on the system that is being used by the user. TS RemoteApp is having the ability to
39

provide all the mediums in order to select the software and specifically the one that can be used
by the remote users of the application and the medium to pack and provide the delivery of the
application to the client and also to the the primitive manner of maintaining remote users as well
their availability to the terminal servers. Following are the steps to manage the TS Remote App
Manager (SourceDaddy, 2019).
Click Start Menu for accessing the TS Remote App Manager then click on the option of
Administrative Tools, the option that is to be selected is of the Terminal Services and there
the option of TS RemoteApp Manager must be selected.
Another way of doing this is by opening the Role and Terminal Service and selecting the TS
RemoteApp Manager in the Server Manager.
Select the option of Add RemoteApp Programs In the Actions button that is present on the
right side of the window. This will open the RemoteApp Wizard.
Choose the desired applications that the user wants from the remote user to be executed. For
every application that is present select the option of Properties. The user is also free to make
any changes that they want to be made to the point of name, the place where the startup file is
located, the aliases, if it can be accessed by the help of TS Web Access, and if the client is
having the ability for using the command-line arguments.
Figure 21 Selecting the Server Roles
40
by the remote users of the application and the medium to pack and provide the delivery of the
application to the client and also to the the primitive manner of maintaining remote users as well
their availability to the terminal servers. Following are the steps to manage the TS Remote App
Manager (SourceDaddy, 2019).
Click Start Menu for accessing the TS Remote App Manager then click on the option of
Administrative Tools, the option that is to be selected is of the Terminal Services and there
the option of TS RemoteApp Manager must be selected.
Another way of doing this is by opening the Role and Terminal Service and selecting the TS
RemoteApp Manager in the Server Manager.
Select the option of Add RemoteApp Programs In the Actions button that is present on the
right side of the window. This will open the RemoteApp Wizard.
Choose the desired applications that the user wants from the remote user to be executed. For
every application that is present select the option of Properties. The user is also free to make
any changes that they want to be made to the point of name, the place where the startup file is
located, the aliases, if it can be accessed by the help of TS Web Access, and if the client is
having the ability for using the command-line arguments.
Figure 21 Selecting the Server Roles
40
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
(Source: Searchit, 2019)
Figure 22 Configuration of the user experience
(Source: Searchit, 2019)
41
Figure 22 Configuration of the user experience
(Source: Searchit, 2019)
41

Figure 23 Adding users to the remote desktop user’s group
(Source: Searchit, 2019)
Conclusion
In the course of this document, the dos and don’ts of the network operating systems are
discussed. After going through this whole report the learner would be having the basic
knowledge regarding the NOS. It is clearly mentioned in the report that Network Operating
System can be defined a structure that ensures the dependable sharing of procedures, files,
elements that are associated to networking process, network protocol, and different elements that
are associated with the process of networking, for the production of a machine which is
dependable and secured from all the external attacks, and which works along with the desired
specifications. In the lack of an OS, the computer is nothing but a box that contains various
circuits. In case of NOS, the networks are not much more than a group of system gadgets that are
cabled altogether. NOS improve the flow of data and communicating process across various
networks. During the comparison of the NOS with work station operating systems, the network
operating system is mainly created in order to provide its service to remote client. One of the
major differences is that NOS is created in order to be compatible with the simultaneous
42
(Source: Searchit, 2019)
Conclusion
In the course of this document, the dos and don’ts of the network operating systems are
discussed. After going through this whole report the learner would be having the basic
knowledge regarding the NOS. It is clearly mentioned in the report that Network Operating
System can be defined a structure that ensures the dependable sharing of procedures, files,
elements that are associated to networking process, network protocol, and different elements that
are associated with the process of networking, for the production of a machine which is
dependable and secured from all the external attacks, and which works along with the desired
specifications. In the lack of an OS, the computer is nothing but a box that contains various
circuits. In case of NOS, the networks are not much more than a group of system gadgets that are
cabled altogether. NOS improve the flow of data and communicating process across various
networks. During the comparison of the NOS with work station operating systems, the network
operating system is mainly created in order to provide its service to remote client. One of the
major differences is that NOS is created in order to be compatible with the simultaneous
42

multiuser platform which signifies that with the NOS we may have many users that are all
simultaneously using the sources on the server.
43
simultaneously using the sources on the server.
43
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Books and Journals
Bacula Systems, 2019. Network Backup: Definition and Types. [Online]. Bacula Systems.
Available at: https://www.baculasystems.com/glossary/network-backup/. [Accessed on
29 th June 2019]
Dummies, 2019. Network Server Setup: Network Operating System Installation. [Online].
Dummies. Available at: https://www.dummies.com/programming/networking/network-
serversetup-network-operating-system-installation/. [Accessed on 28 th June 2019]
FunctionX, 2012. Introduction to Client/ Server Network Setup. [Online]. FunctionX. Available
at: https://www.functionx.com/networking/Lesson06.htm. [Accessed on 28 th June 2019]
Genie, M., 2012. Typeperf –Windows Command Line Monitoring Tools. [Online] Mickgenie.
Available at: http://www.mickgenie.com/typeperf-windows-command-line-monitoring-
tools/. [Accessed on 8 th July 2019]
Lu, Z.W. and Zhou, G., 2016, August. Design and implementation of hybrid shingled recording
RAID system. In 2016 IEEE 14th Intl Conf on Dependable, Autonomic and Secure
Computing, 14th Intl Conf on Pervasive Intelligence and Computing, 2nd Intl Conf on
Big Data Intelligence and Computing and Cyber Science and Technology Congress
(DASC/PiCom/DataCom/CyberSciTech) (pp. 937-942). IEEE.
Marcho, C., 2019. Windows Perfomrance Monitor Overview. [Online]. Techcommunity.
Available at:
https://techcommunity.microsoft.com/t5/Ask-The-Performance-Team/WindowsPerforma
nce-Monitor-Overview/ba-p/375481. [Accessed on 8 th July 2019]
Network Alliance, 2019. Understanding Technology Costs. [Online]. Network Alliance.
Available at: https://networkalliance.com/understanding-technology-costs/. [Accessed on
28 th June 2019]
Ranjan, R., Buyya, R., Leitner, P., Haller, A. and Tai, S., 2014. A note on software tools and
techniques for monitoring and prediction of cloud services. SOFTWARE: PRACTICE
AND EXPERIENCE. 2014(77). Pp. 771-775.
44
Books and Journals
Bacula Systems, 2019. Network Backup: Definition and Types. [Online]. Bacula Systems.
Available at: https://www.baculasystems.com/glossary/network-backup/. [Accessed on
29 th June 2019]
Dummies, 2019. Network Server Setup: Network Operating System Installation. [Online].
Dummies. Available at: https://www.dummies.com/programming/networking/network-
serversetup-network-operating-system-installation/. [Accessed on 28 th June 2019]
FunctionX, 2012. Introduction to Client/ Server Network Setup. [Online]. FunctionX. Available
at: https://www.functionx.com/networking/Lesson06.htm. [Accessed on 28 th June 2019]
Genie, M., 2012. Typeperf –Windows Command Line Monitoring Tools. [Online] Mickgenie.
Available at: http://www.mickgenie.com/typeperf-windows-command-line-monitoring-
tools/. [Accessed on 8 th July 2019]
Lu, Z.W. and Zhou, G., 2016, August. Design and implementation of hybrid shingled recording
RAID system. In 2016 IEEE 14th Intl Conf on Dependable, Autonomic and Secure
Computing, 14th Intl Conf on Pervasive Intelligence and Computing, 2nd Intl Conf on
Big Data Intelligence and Computing and Cyber Science and Technology Congress
(DASC/PiCom/DataCom/CyberSciTech) (pp. 937-942). IEEE.
Marcho, C., 2019. Windows Perfomrance Monitor Overview. [Online]. Techcommunity.
Available at:
https://techcommunity.microsoft.com/t5/Ask-The-Performance-Team/WindowsPerforma
nce-Monitor-Overview/ba-p/375481. [Accessed on 8 th July 2019]
Network Alliance, 2019. Understanding Technology Costs. [Online]. Network Alliance.
Available at: https://networkalliance.com/understanding-technology-costs/. [Accessed on
28 th June 2019]
Ranjan, R., Buyya, R., Leitner, P., Haller, A. and Tai, S., 2014. A note on software tools and
techniques for monitoring and prediction of cloud services. SOFTWARE: PRACTICE
AND EXPERIENCE. 2014(77). Pp. 771-775.
44

Sciencedirect, 2019. Log Record Event. [Online]. Sciencedirect. Available at:
https://www.sciencedirect.com/topics/computer-science/log-record-event. [Accessed on 1
st July 2019]
Searchit Channel, 2019. Adding Remote Desktop Services and RemoteApp programs. [Online].
Searchitchannel. Available at: https://searchitchannel.techtarget.com/feature/Adding-
RemoteDesktop-Services-and-RemoteApp-programs. [Accessed at 8 th Jut 2019]
SourceDaddy, 2019. Manage TS RemoteApp. [Online]. SourceDaddy. Available at:
https://sourcedaddy.com/windows-7/manage-ts-remoteapp.html. [Accessed on 8 th July
2019]
Trent, R., 2015. Connecting System Center Operations Manager to Microsoft Operations
Manage ment Suite. [Online]. ITPro Today. Available at:
https://www.itprotoday.com/computeengines/connecting-system-center-operations-
manager-microsoft-operations-management-suite. [Accessed on 8 th July, 2019]
Trifonov, P., 2015. Low-complexity implementation of RAID based on Reed-Solomon codes.
ACM Transactions on Storage (TOS). 11(1). p.1.
Zandbergen, P., 2019. Network Operating Systems. [Online]. Study. Available at:
https://study.com/academy/lesson/network-operating-systems-nos-windows-novell-
netware.html. [Accessed on 28 th June 2019]
45
https://www.sciencedirect.com/topics/computer-science/log-record-event. [Accessed on 1
st July 2019]
Searchit Channel, 2019. Adding Remote Desktop Services and RemoteApp programs. [Online].
Searchitchannel. Available at: https://searchitchannel.techtarget.com/feature/Adding-
RemoteDesktop-Services-and-RemoteApp-programs. [Accessed at 8 th Jut 2019]
SourceDaddy, 2019. Manage TS RemoteApp. [Online]. SourceDaddy. Available at:
https://sourcedaddy.com/windows-7/manage-ts-remoteapp.html. [Accessed on 8 th July
2019]
Trent, R., 2015. Connecting System Center Operations Manager to Microsoft Operations
Manage ment Suite. [Online]. ITPro Today. Available at:
https://www.itprotoday.com/computeengines/connecting-system-center-operations-
manager-microsoft-operations-management-suite. [Accessed on 8 th July, 2019]
Trifonov, P., 2015. Low-complexity implementation of RAID based on Reed-Solomon codes.
ACM Transactions on Storage (TOS). 11(1). p.1.
Zandbergen, P., 2019. Network Operating Systems. [Online]. Study. Available at:
https://study.com/academy/lesson/network-operating-systems-nos-windows-novell-
netware.html. [Accessed on 28 th June 2019]
45
1 out of 45
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





