BTEC HND: Network Operating Systems Implementation and Management
VerifiedAdded on 2023/06/13
|31
|3811
|242
Report
AI Summary
This report provides a comprehensive overview of network operating systems (NOS), covering principles, implementation, and management. It begins with an examination of different types of operating systems, emphasizing the importance of network security services and recommending Windows as a preferred NOS. The report then discusses disaster recovery and business continuity planning, including backup strategies and RAID configurations. The implementation plan covers IP addressing, server requirements, and security policies, including password and patch management. The report also outlines a step-by-step process for installing Windows Server, enabling security policies, and performing performance testing. Finally, it addresses network monitoring tools and strategies for mitigating patch issues, Windows vulnerabilities, and threats. Desklib offers a wealth of resources, including past papers and solved assignments, to support students in their academic endeavors.

1
Networking
Student Name
Affiliate Institution
Networking
Student Name
Affiliate Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Table of Contents
1 Task-1: Network Operating System Principles........................................................................3
1.1 Summary...........................................................................................................................3
1.2 Types of operating System................................................................................................3
1.2.1 Require network security Services............................................................................3
1.2.2 Recommended network operating system.................................................................4
1.2.3 The differentiation of Operating systems..................................................................4
1.3 Disaster Recovery and Business Continuity.....................................................................5
1.3.1 Planning for Business continuity: Disaster Recovery...............................................5
1.3.2 Back Up strategies in place........................................................................................5
1.3.3 RAID..........................................................................................................................6
2 Task-2: Network Operating System Implementation Plan.......................................................7
2.1.1 Server hardware Requirement:..................................................................................8
2.2 Understand Security Policy...............................................................................................8
2.3 User Feedback justification and Evaluation Plan.............................................................9
3 Task-3: Network Operating System Implementation...............................................................9
3.1 Deployment, installation, and configuration of NOS.......................................................9
3.1.1 Step-By-Step Process of Installing Windows Server................................................9
3.2 Enabling Security Policy and Testing.............................................................................25
3.2.1 Threat and password /folder permission policy.......................................................25
3.2.2 Security, Auditing & Monitoring....................................................................25
3.3 Analyze performance and test.........................................................................................25
4 Task-4: Network Operating System Management.................................................................26
4.1 Tools for Monitoring the Network..................................................................................26
4.2 Network Monitoring against patch issues, Windows Vulnerability and Threats...........26
Table of Contents
1 Task-1: Network Operating System Principles........................................................................3
1.1 Summary...........................................................................................................................3
1.2 Types of operating System................................................................................................3
1.2.1 Require network security Services............................................................................3
1.2.2 Recommended network operating system.................................................................4
1.2.3 The differentiation of Operating systems..................................................................4
1.3 Disaster Recovery and Business Continuity.....................................................................5
1.3.1 Planning for Business continuity: Disaster Recovery...............................................5
1.3.2 Back Up strategies in place........................................................................................5
1.3.3 RAID..........................................................................................................................6
2 Task-2: Network Operating System Implementation Plan.......................................................7
2.1.1 Server hardware Requirement:..................................................................................8
2.2 Understand Security Policy...............................................................................................8
2.3 User Feedback justification and Evaluation Plan.............................................................9
3 Task-3: Network Operating System Implementation...............................................................9
3.1 Deployment, installation, and configuration of NOS.......................................................9
3.1.1 Step-By-Step Process of Installing Windows Server................................................9
3.2 Enabling Security Policy and Testing.............................................................................25
3.2.1 Threat and password /folder permission policy.......................................................25
3.2.2 Security, Auditing & Monitoring....................................................................25
3.3 Analyze performance and test.........................................................................................25
4 Task-4: Network Operating System Management.................................................................26
4.1 Tools for Monitoring the Network..................................................................................26
4.2 Network Monitoring against patch issues, Windows Vulnerability and Threats...........26

3
1 Task-1: Network Operating System Principles
1.1 Summary
Every computer needs an operating system for it to run its process. Meaning every
software needs the operating system to for it to function efficiently in the system. Various
hardware devices such as printers, laptops, and many others (Pillai, 2017) can be controlled by
an operating system therefore it interfaces the application software with the hardware.
1.2 Types of operating System
There exist four main divisions of operating systems which dominate the market and play
important part in today’s technology world. They include:
Real time operating systems (RTOS): RTOS is a kind of operating systems that aids in
scheduling dedicated algorithms to attain a specific output. One characteristic of real time
operating system is that quickly response to any activity in process. In addition, it can execute
several real time applications at the same time. However, it is important to point out that this
particular operating system has little capability when it comes to user interface (Chennaicisco,
2013). There exist two types of RTOS; hard real time and soft real time. The distinguishing
feature of the two types is that hard real time OS execute delegated tasks within stipulated
timeline while soft real time operating system prioritizes tasks according to urgency and index,
that is, the most critical processes are executed first.
Batch operating system: this kind of operating system analyzes all the input data and
categorizes them into batches.
Single task operating system: it allows only one user to carry out a single task at a time.
Examples include Palm OS where a single task is executed by a single user.
Multi task operating system: this type allows the simultaneous execution of several tasks at
the same time by several users.
1.2.1 Require network security Services
It is necessary to come up with a virtualized environment that will support future
requirements of the company in order to support print services, installation of firewalls, remote
desktop connection, data security, end point security antiviruses, patches management,
1 Task-1: Network Operating System Principles
1.1 Summary
Every computer needs an operating system for it to run its process. Meaning every
software needs the operating system to for it to function efficiently in the system. Various
hardware devices such as printers, laptops, and many others (Pillai, 2017) can be controlled by
an operating system therefore it interfaces the application software with the hardware.
1.2 Types of operating System
There exist four main divisions of operating systems which dominate the market and play
important part in today’s technology world. They include:
Real time operating systems (RTOS): RTOS is a kind of operating systems that aids in
scheduling dedicated algorithms to attain a specific output. One characteristic of real time
operating system is that quickly response to any activity in process. In addition, it can execute
several real time applications at the same time. However, it is important to point out that this
particular operating system has little capability when it comes to user interface (Chennaicisco,
2013). There exist two types of RTOS; hard real time and soft real time. The distinguishing
feature of the two types is that hard real time OS execute delegated tasks within stipulated
timeline while soft real time operating system prioritizes tasks according to urgency and index,
that is, the most critical processes are executed first.
Batch operating system: this kind of operating system analyzes all the input data and
categorizes them into batches.
Single task operating system: it allows only one user to carry out a single task at a time.
Examples include Palm OS where a single task is executed by a single user.
Multi task operating system: this type allows the simultaneous execution of several tasks at
the same time by several users.
1.2.1 Require network security Services
It is necessary to come up with a virtualized environment that will support future
requirements of the company in order to support print services, installation of firewalls, remote
desktop connection, data security, end point security antiviruses, patches management,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
deployment, high availability of resources, and many others. These services when combined
build up the basic IT requirements for any company.
1.2.2 Recommended network operating system
Windows: windows operating system has over the years evolved to be the most preferred
OS worldwide because of its performance, security, and user friendliness (Technopedia, 2018).
There are different versions of windows operating systems, they include windows server OS and
client OS.
Linux: It is a free and open source operating system. For a device to be configured,
daemon has to be setup with the aid of Linux kernel that has libraries and other supporting tools.
The Linux operating system can be installed in several platforms such as notebooks, desktops,
mobile, and laptop among others. Ubuntu, OpenUse, Fedora, Debian, and RedHat are examples
of Linux. All the Linux upgrades after Linux 7 have GUI.
Mac OSX: It is a series of Unix-based graphical interface operating systems developed
and marketed by Apple Inc. Only designed to run on Macintosh computers, having been pre-
installed on all Macs since 2002. It delivers the best possible performance with the processor in
your Mac. Since super-responsive trackpad is used in Mac notebooks, Multi-Touch gestures feel
natural to use (Pillai, 2017). The entire system is up to date while it sleeps because OS X works
with your Mac hardware to manage this. Another benefit of this OS is advanced power-saving
technologies help extend battery life. It also designs for the gorgeous Mac displays including
high-resolution Retina displays.
1.2.3 The differentiation of Operating systems
Technical features Windows Linux Mac OsX
Software
Availability
Readily available in
the market but the
licensing policy has
an intricate
understanding. Each
version has its cost.
No monetary cost
hence freeware and
also open source
software.
No monetary cost
hence freeware.
Scalability Should be down time
when upgrading and
patching. In case of
any corrupt file, it
can be at risk.
Therefore it is
Only scalable on
server sides.
Scalability on the
client side is not
possible because it
only supports one
user at a time.
deployment, high availability of resources, and many others. These services when combined
build up the basic IT requirements for any company.
1.2.2 Recommended network operating system
Windows: windows operating system has over the years evolved to be the most preferred
OS worldwide because of its performance, security, and user friendliness (Technopedia, 2018).
There are different versions of windows operating systems, they include windows server OS and
client OS.
Linux: It is a free and open source operating system. For a device to be configured,
daemon has to be setup with the aid of Linux kernel that has libraries and other supporting tools.
The Linux operating system can be installed in several platforms such as notebooks, desktops,
mobile, and laptop among others. Ubuntu, OpenUse, Fedora, Debian, and RedHat are examples
of Linux. All the Linux upgrades after Linux 7 have GUI.
Mac OSX: It is a series of Unix-based graphical interface operating systems developed
and marketed by Apple Inc. Only designed to run on Macintosh computers, having been pre-
installed on all Macs since 2002. It delivers the best possible performance with the processor in
your Mac. Since super-responsive trackpad is used in Mac notebooks, Multi-Touch gestures feel
natural to use (Pillai, 2017). The entire system is up to date while it sleeps because OS X works
with your Mac hardware to manage this. Another benefit of this OS is advanced power-saving
technologies help extend battery life. It also designs for the gorgeous Mac displays including
high-resolution Retina displays.
1.2.3 The differentiation of Operating systems
Technical features Windows Linux Mac OsX
Software
Availability
Readily available in
the market but the
licensing policy has
an intricate
understanding. Each
version has its cost.
No monetary cost
hence freeware and
also open source
software.
No monetary cost
hence freeware.
Scalability Should be down time
when upgrading and
patching. In case of
any corrupt file, it
can be at risk.
Therefore it is
Only scalable on
server sides.
Scalability on the
client side is not
possible because it
only supports one
user at a time.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
available to run
services because it’s
scalable at all level.
System Security Though hackers can
get access even with
presence of patches ,
Windows OS are
keen on them and any
attacks that make the
pc vulnerable
Has less vulnerable
attacks since the
Linux kernel
maintains its security
level
The kernel security
has enough
internal/external
security in place.
Technical Support Support is available
directly with the
assist of the
Microsoft team that
provides solutions to
the client’s problems.
Support is only
available on forum.
Support only
available on forum or
websites.
Maintainability Patches are
important for
maintenance
Easily maintainable Very easy
maintainability
1.3 Disaster Recovery and Business Continuity
1.3.1 Planning for Business continuity: Disaster Recovery
Issues of failures in business could take place because of unpredictable reasons. This is
can be erased by business continuity and disaster recovery. Business continuity entails
accessibility of all business critical data and no dormancy period. Disaster recovery prevents
failure or a standstill of the operations in the business due to unfortunate causes such as power
loss or natural calamities (Blogspot.in, 2015). Therefore it aids technology companies by
devising a backup to save most of critical data, specific application, and service in 3-way
architecture. In the primary site the systems are ensured high availability. If a natural calamity
takes place in the area, the disaster recover sites connects with Primary site and keeps the system
running and business continues.
1.3.2 Back Up strategies in place
In business continuity, data backup in a business is a policy that have been collectively
agreed and defined by the management. It can be in the form of database backup, backing up the
file systems, or data placed in a different folder. Backing up employee’s data is not mandatory
but the critical systems of the company have to be backed up (Networks, 2015). Data in the
organization can be stored either in tape drive, Zip drive or backup media’s. After storage, they
available to run
services because it’s
scalable at all level.
System Security Though hackers can
get access even with
presence of patches ,
Windows OS are
keen on them and any
attacks that make the
pc vulnerable
Has less vulnerable
attacks since the
Linux kernel
maintains its security
level
The kernel security
has enough
internal/external
security in place.
Technical Support Support is available
directly with the
assist of the
Microsoft team that
provides solutions to
the client’s problems.
Support is only
available on forum.
Support only
available on forum or
websites.
Maintainability Patches are
important for
maintenance
Easily maintainable Very easy
maintainability
1.3 Disaster Recovery and Business Continuity
1.3.1 Planning for Business continuity: Disaster Recovery
Issues of failures in business could take place because of unpredictable reasons. This is
can be erased by business continuity and disaster recovery. Business continuity entails
accessibility of all business critical data and no dormancy period. Disaster recovery prevents
failure or a standstill of the operations in the business due to unfortunate causes such as power
loss or natural calamities (Blogspot.in, 2015). Therefore it aids technology companies by
devising a backup to save most of critical data, specific application, and service in 3-way
architecture. In the primary site the systems are ensured high availability. If a natural calamity
takes place in the area, the disaster recover sites connects with Primary site and keeps the system
running and business continues.
1.3.2 Back Up strategies in place
In business continuity, data backup in a business is a policy that have been collectively
agreed and defined by the management. It can be in the form of database backup, backing up the
file systems, or data placed in a different folder. Backing up employee’s data is not mandatory
but the critical systems of the company have to be backed up (Networks, 2015). Data in the
organization can be stored either in tape drive, Zip drive or backup media’s. After storage, they

6
are moved as a physical copy and kept in a classified room or a bank locker depending with the
policy. This is for safety purposes.
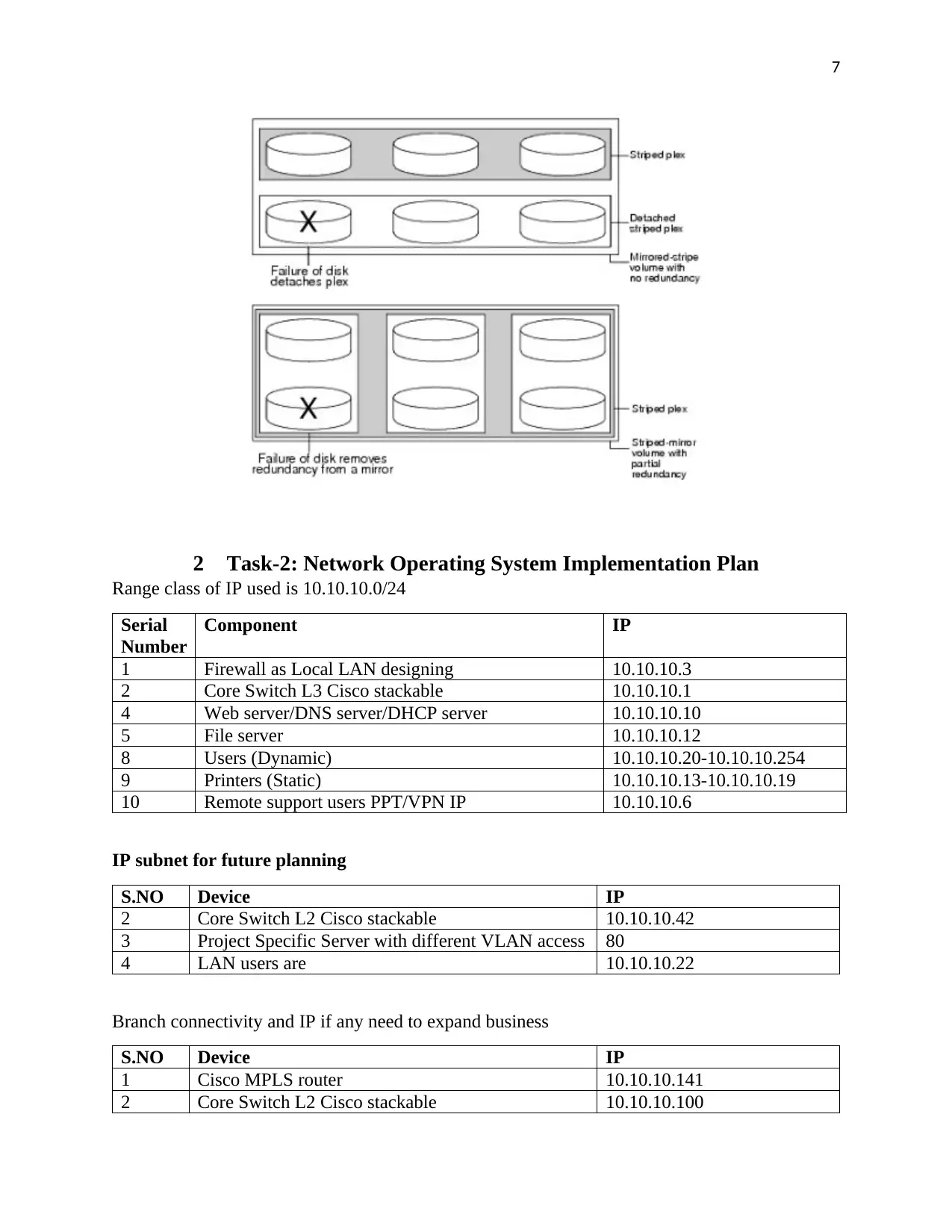
1.3.3 RAID
RAID (redundant array of independent disk) is a system that invent partition to boost
storage performance and reliability and availability (Meena, 2017). The technology expert
achieves this by developing a mechanism to group physical hard disk into a common big size
drive for the purpose of assuring data storage capacity. Server administrator is the sole decision
maker when it comes to creation of levels of RAID. The figure below describe the case further:
In case of disk failures, mirror image may be created in RAID1+0 in order to restore.
are moved as a physical copy and kept in a classified room or a bank locker depending with the
policy. This is for safety purposes.
1.3.3 RAID
RAID (redundant array of independent disk) is a system that invent partition to boost
storage performance and reliability and availability (Meena, 2017). The technology expert
achieves this by developing a mechanism to group physical hard disk into a common big size
drive for the purpose of assuring data storage capacity. Server administrator is the sole decision
maker when it comes to creation of levels of RAID. The figure below describe the case further:
In case of disk failures, mirror image may be created in RAID1+0 in order to restore.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
2 Task-2: Network Operating System Implementation Plan
Range class of IP used is 10.10.10.0/24
Serial
Number
Component IP
1 Firewall as Local LAN designing 10.10.10.3
2 Core Switch L3 Cisco stackable 10.10.10.1
4 Web server/DNS server/DHCP server 10.10.10.10
5 File server 10.10.10.12
8 Users (Dynamic) 10.10.10.20-10.10.10.254
9 Printers (Static) 10.10.10.13-10.10.10.19
10 Remote support users PPT/VPN IP 10.10.10.6
IP subnet for future planning
S.NO Device IP
2 Core Switch L2 Cisco stackable 10.10.10.42
3 Project Specific Server with different VLAN access 80
4 LAN users are 10.10.10.22
Branch connectivity and IP if any need to expand business
S.NO Device IP
1 Cisco MPLS router 10.10.10.141
2 Core Switch L2 Cisco stackable 10.10.10.100
2 Task-2: Network Operating System Implementation Plan
Range class of IP used is 10.10.10.0/24
Serial
Number
Component IP
1 Firewall as Local LAN designing 10.10.10.3
2 Core Switch L3 Cisco stackable 10.10.10.1
4 Web server/DNS server/DHCP server 10.10.10.10
5 File server 10.10.10.12
8 Users (Dynamic) 10.10.10.20-10.10.10.254
9 Printers (Static) 10.10.10.13-10.10.10.19
10 Remote support users PPT/VPN IP 10.10.10.6
IP subnet for future planning
S.NO Device IP
2 Core Switch L2 Cisco stackable 10.10.10.42
3 Project Specific Server with different VLAN access 80
4 LAN users are 10.10.10.22
Branch connectivity and IP if any need to expand business
S.NO Device IP
1 Cisco MPLS router 10.10.10.141
2 Core Switch L2 Cisco stackable 10.10.10.100
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
3 File server 10.10.10.72
4 LAN users are 10.10.10.9
Server basic requirements.
Serial
numbe
r
Specification of the Product Quantit
y
1 Windows server 2016 4 File Sever
Application server
Printer server
DHCP
3 Windows 8.1 client operating system 200 To be installed in client machines to
be used by users
2.1.1 Server hardware Requirement:
One of the vital roles of a server administrator is planning of server hardware. A system’s
performance, productivity, availability of services, continuity and scalability works efficiently if
the server hardware is planned properly (Administrator, 2018). A proposal plan is therefore
needed for the purpose is to create a virtualized farm to leverage current and future requirement.
2.2 Understand Security Policy
Security Policy- it is described as standards in place to ensure that company resources are
safe and secure. Every security policy of an organization lies with all resource whether tangible
or intangible that help the organization to run its business operations and processes, therefore a
company has to prepare and deploy a system that will secure these assets where technology is
majorly needed (De, 2015). Violation of security can happen anyhow. As such every user who
interacts with the system whether directly or indirectly has to keep these policies in mind while
using it.
Password Management- every employee has to have a password that meets the standards
as defined in the policy. The password should be complex enough not to be guessed. It should
have special and alphanumeric characters (Mbaocha, 2012).
Patch Management: - a patch is a set of changes to a computer program or its supporting
data designed to update, fix or improve the system hence it keeps things at specific level to run
which improves performance. When a server administrator realizes that a patch is released, he
3 File server 10.10.10.72
4 LAN users are 10.10.10.9
Server basic requirements.
Serial
numbe
r
Specification of the Product Quantit
y
1 Windows server 2016 4 File Sever
Application server
Printer server
DHCP
3 Windows 8.1 client operating system 200 To be installed in client machines to
be used by users
2.1.1 Server hardware Requirement:
One of the vital roles of a server administrator is planning of server hardware. A system’s
performance, productivity, availability of services, continuity and scalability works efficiently if
the server hardware is planned properly (Administrator, 2018). A proposal plan is therefore
needed for the purpose is to create a virtualized farm to leverage current and future requirement.
2.2 Understand Security Policy
Security Policy- it is described as standards in place to ensure that company resources are
safe and secure. Every security policy of an organization lies with all resource whether tangible
or intangible that help the organization to run its business operations and processes, therefore a
company has to prepare and deploy a system that will secure these assets where technology is
majorly needed (De, 2015). Violation of security can happen anyhow. As such every user who
interacts with the system whether directly or indirectly has to keep these policies in mind while
using it.
Password Management- every employee has to have a password that meets the standards
as defined in the policy. The password should be complex enough not to be guessed. It should
have special and alphanumeric characters (Mbaocha, 2012).
Patch Management: - a patch is a set of changes to a computer program or its supporting
data designed to update, fix or improve the system hence it keeps things at specific level to run
which improves performance. When a server administrator realizes that a patch is released, he

9
carries out troubleshooting and setup on the server to meet specific requirements defied in the
patch (SearchSecurity, 2015).
2.3 User Feedback justification and Evaluation Plan
The requirement and the scope has to mitigate the future requirement as proposed in the
meeting plan (Macken, 2016). For the purpose of supplying all applicable information and allow
users to ingress IT services and document the both remotely and locally without undermining the
company’s security policy
3 Task-3: Network Operating System Implementation
3.1 Deployment, installation, and configuration of NOS
3.1.1 Step-By-Step Process of Installing Windows Server
Minimum Requirements
Processor: 64-bit, speed 1.5 GHz,
RAM: 1GB
ROM: 50 GB
The process of installing the windows server operating system is as follows:
Step 1: Insert the installation media and boot up the computer. You will see the message below,
press Enter.
carries out troubleshooting and setup on the server to meet specific requirements defied in the
patch (SearchSecurity, 2015).
2.3 User Feedback justification and Evaluation Plan
The requirement and the scope has to mitigate the future requirement as proposed in the
meeting plan (Macken, 2016). For the purpose of supplying all applicable information and allow
users to ingress IT services and document the both remotely and locally without undermining the
company’s security policy
3 Task-3: Network Operating System Implementation
3.1 Deployment, installation, and configuration of NOS
3.1.1 Step-By-Step Process of Installing Windows Server
Minimum Requirements
Processor: 64-bit, speed 1.5 GHz,
RAM: 1GB
ROM: 50 GB
The process of installing the windows server operating system is as follows:
Step 1: Insert the installation media and boot up the computer. You will see the message below,
press Enter.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
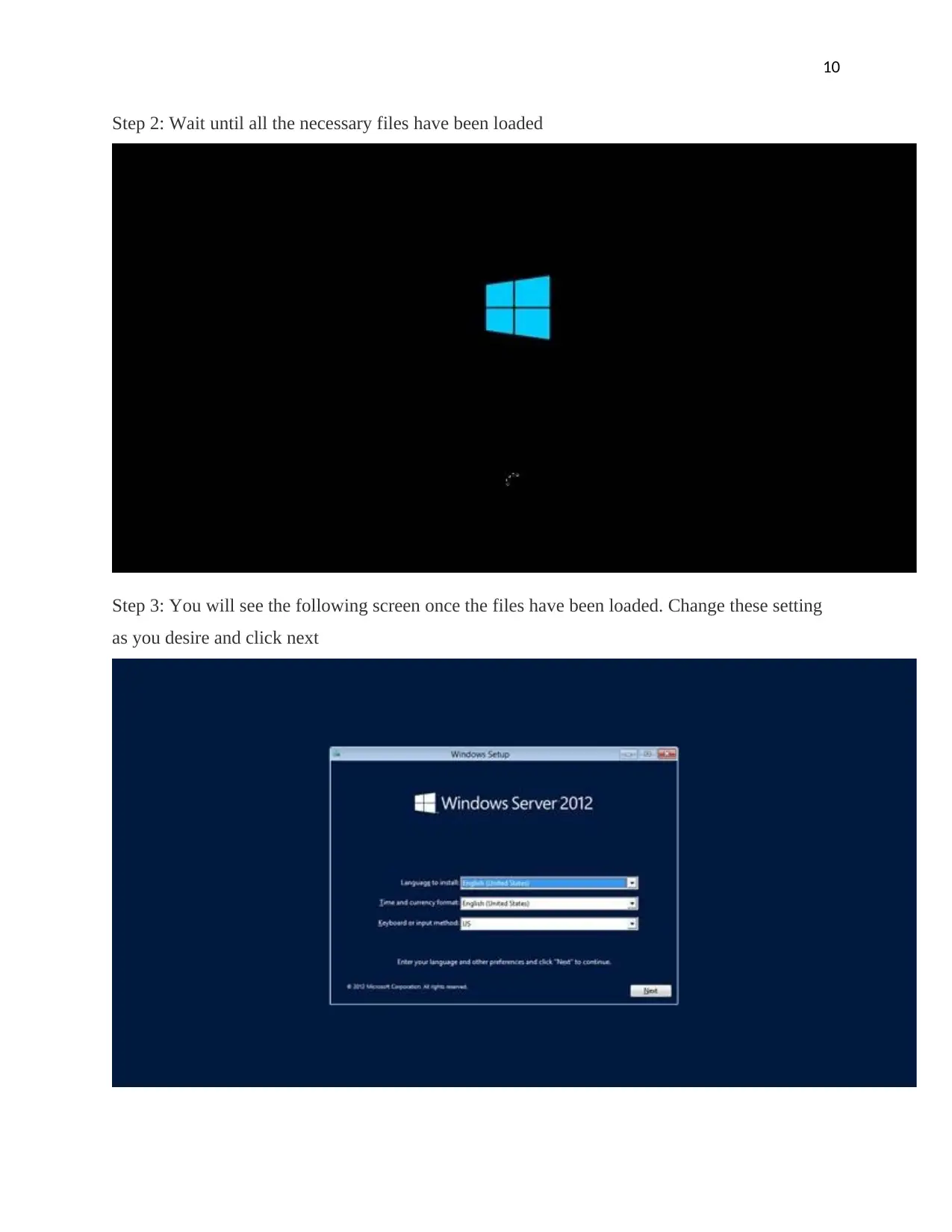
Step 2: Wait until all the necessary files have been loaded
Step 3: You will see the following screen once the files have been loaded. Change these setting
as you desire and click next
Step 2: Wait until all the necessary files have been loaded
Step 3: You will see the following screen once the files have been loaded. Change these setting
as you desire and click next
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
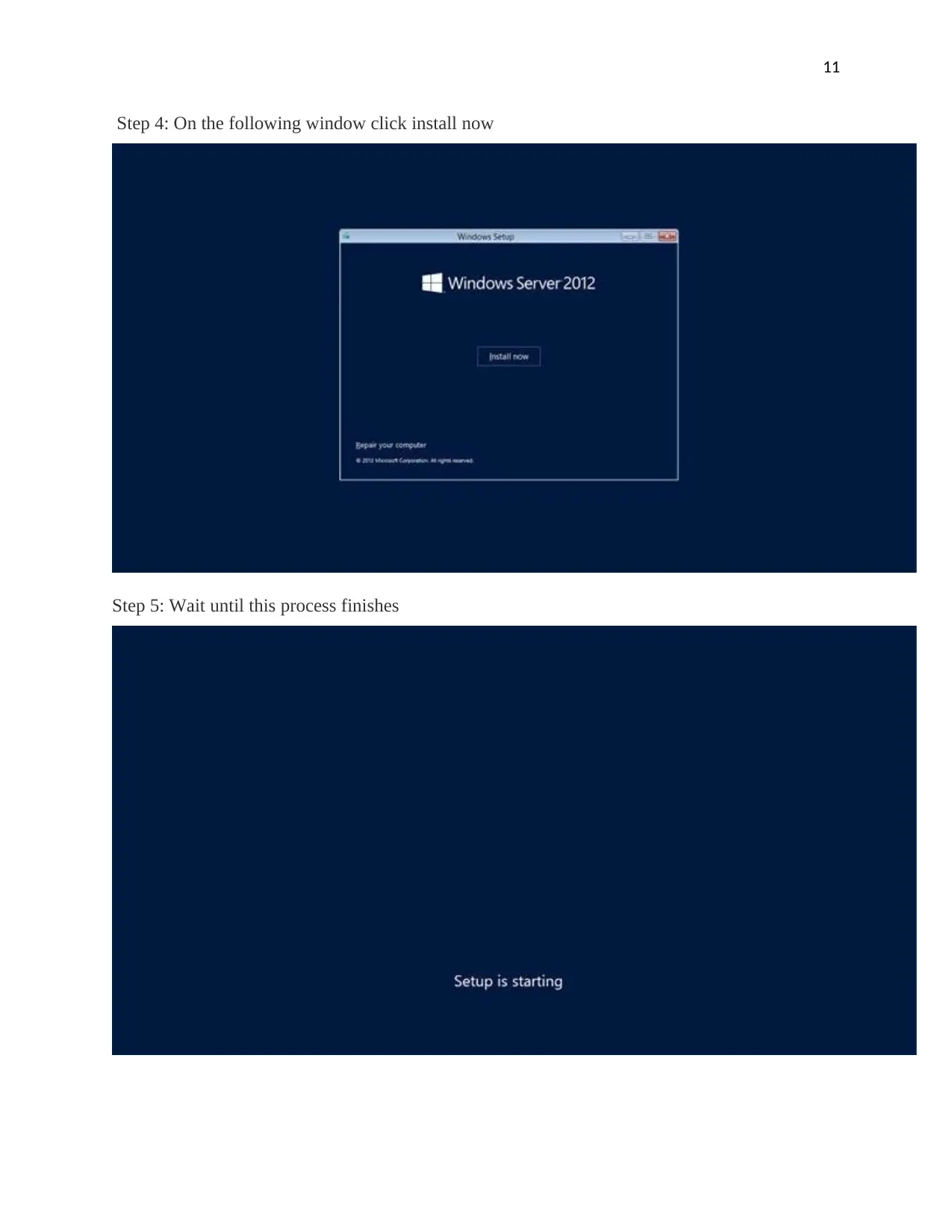
Step 4: On the following window click install now
Step 5: Wait until this process finishes
Step 4: On the following window click install now
Step 5: Wait until this process finishes
12
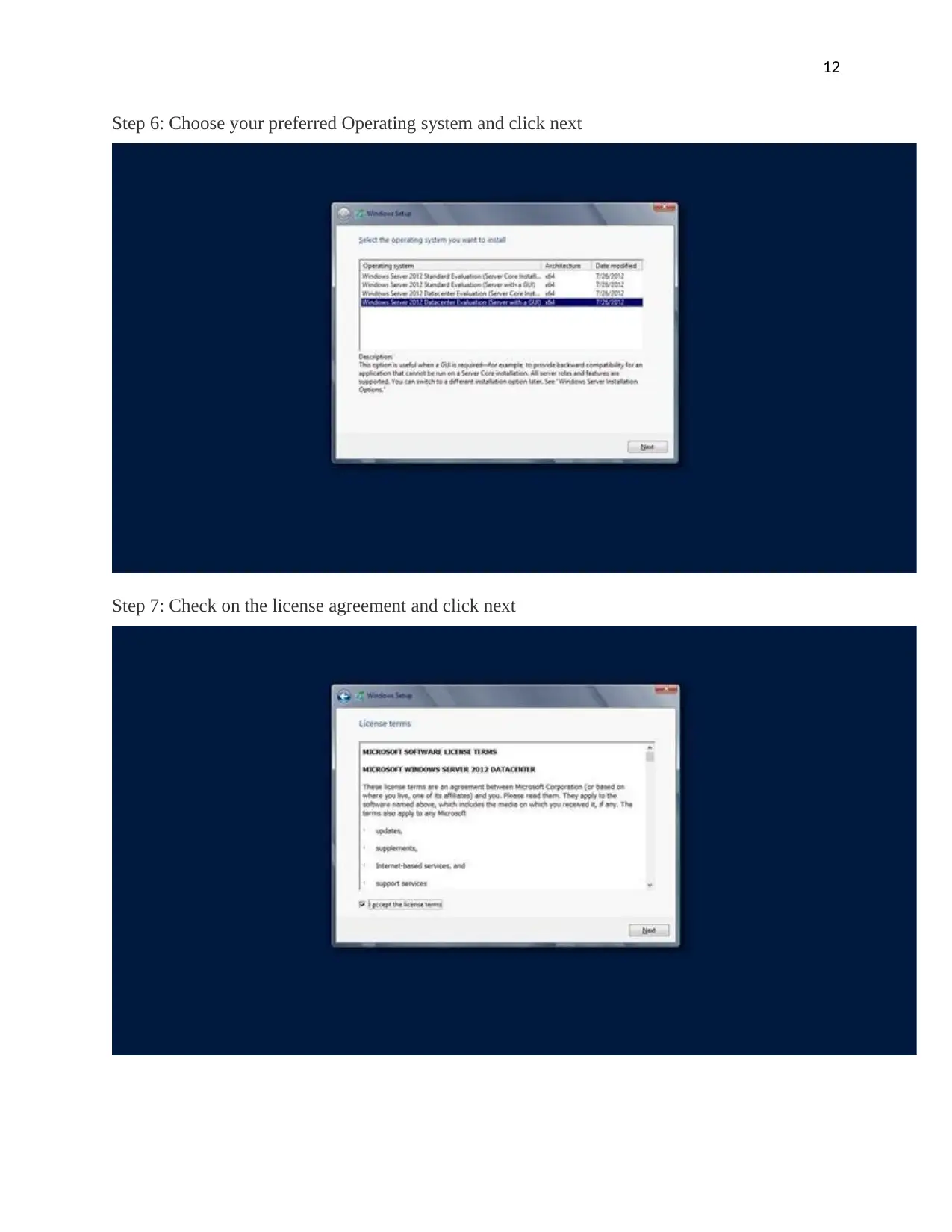
Step 6: Choose your preferred Operating system and click next
Step 7: Check on the license agreement and click next
Step 6: Choose your preferred Operating system and click next
Step 7: Check on the license agreement and click next
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



![Server Installation and Management Project - [Course Name] [Semester]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fkl%2F1a2c109da7e14c78a6b2e8ca6dd132c5.jpg&w=256&q=75)

