Networking Principles and Protocols Report for Complete Systems
VerifiedAdded on 2022/11/30
|13
|3704
|69
Report
AI Summary
This report, prepared for Complete Systems, a high-tech networking solution development organization, provides a comprehensive overview of networking principles and protocols. It begins by defining networks and explores the benefits and constraints of various network types including LAN, MAN, and WAN, along with relevant networking standards. The report then delves into network topology, communication, and bandwidth requirements, comparing different network principles and how protocols enhance network effectiveness. The second section focuses on networking devices, detailing their operating principles and server types, along with the interdependence of workstation hardware and networking software. It also provides recommendations on server selection based on performance and cost. The report concludes with a summary of the network topology and overall findings.

NETWORK PRINCIPLES AND PROTOCOLS 1
Network Principles and Protocols
Name
Course
Institution
Date
Network Principles and Protocols
Name
Course
Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK PRINCIPLES AND PROTOCOLS 2
Table of Contents
Task 1: Networking principles and their protocols..........................................................................3
Introduction......................................................................................................................................3
Benefits and Constraints of Different Network Types and Standards.............................................3
Types of Computer Network.......................................................................................................3
Local Area Network (LAN).....................................................................................................3
Metropolitan Area Network (MAN)........................................................................................5
Wide Area Network (WAN)....................................................................................................5
Networking Standards.................................................................................................................7
Impact of Network Topology, Communication and Bandwidth Requirements..........................7
Network Principles......................................................................................................................8
How Protocols Enable the Effectiveness of Network Systems...................................................8
Task 2 Networking Devices and Operations...................................................................................9
The operating principle of Networking Devices.........................................................................9
Operating Principle of Different Types of Servers....................................................................10
Inter-Dependence of Workstation Hardware with Relevant Networking Software..................10
Types of Servers and Recommendations Based on Performance and Cost..............................11
Task 3 Conclusion.........................................................................................................................11
References......................................................................................................................................13
Table of Contents
Task 1: Networking principles and their protocols..........................................................................3
Introduction......................................................................................................................................3
Benefits and Constraints of Different Network Types and Standards.............................................3
Types of Computer Network.......................................................................................................3
Local Area Network (LAN).....................................................................................................3
Metropolitan Area Network (MAN)........................................................................................5
Wide Area Network (WAN)....................................................................................................5
Networking Standards.................................................................................................................7
Impact of Network Topology, Communication and Bandwidth Requirements..........................7
Network Principles......................................................................................................................8
How Protocols Enable the Effectiveness of Network Systems...................................................8
Task 2 Networking Devices and Operations...................................................................................9
The operating principle of Networking Devices.........................................................................9
Operating Principle of Different Types of Servers....................................................................10
Inter-Dependence of Workstation Hardware with Relevant Networking Software..................10
Types of Servers and Recommendations Based on Performance and Cost..............................11
Task 3 Conclusion.........................................................................................................................11
References......................................................................................................................................13
NETWORK PRINCIPLES AND PROTOCOLS 3
Task 1: Networking principles and their protocols
Introduction
A network has been defined as an interconnection of different computing components such as
servers, workstations, network devices, printers among others for the purposes of sharing data
and communication. For a network to fully operate, the should be physical and logical
connection (Comer, 2015). The former is achieved by use of network protocols such as
Transmission Control Protocol while the latter is established by use of transmission media such
as Ethernet cable (Irving, 2010). This report will seek to described the different networking
principles and their protocols. The first section will discuss the benefits of different types of
networks and standards, the impact of network topology, communication, and bandwidth, and
compare the different network principles and how protocols facilitate effectiveness of
networking systems. The second section will discuss the operating principles of networking
devices and server types, the inter-dependence of workstation hardware with relevant networking
software, and investigate the different types of servers giving recommendations on performance
and cost for a selection of various network situation. The third part will describe the network
topology in the case study and provide a conclusion of the entire paper.
Benefits and Constraints of Different Network Types and Standards
Types of Computer Network
The basic function of a network is to transfer data from one node to another and share resources
such as printers, databases, and servers. A network can be differentiated depending on the range
of computer network and the size. The most common types of computer networks include: Wide
Area Network (WAN), Metropolitan Area Network (MAN), and Local Area Network (LAN).
The subsection will discuss these types in details.
Local Area Network (LAN)
A local area network (LAN) is a type of a network that is used to connect computer systems in
one building, office, or a group of buildings that are nearby. The most commonly used standard
Task 1: Networking principles and their protocols
Introduction
A network has been defined as an interconnection of different computing components such as
servers, workstations, network devices, printers among others for the purposes of sharing data
and communication. For a network to fully operate, the should be physical and logical
connection (Comer, 2015). The former is achieved by use of network protocols such as
Transmission Control Protocol while the latter is established by use of transmission media such
as Ethernet cable (Irving, 2010). This report will seek to described the different networking
principles and their protocols. The first section will discuss the benefits of different types of
networks and standards, the impact of network topology, communication, and bandwidth, and
compare the different network principles and how protocols facilitate effectiveness of
networking systems. The second section will discuss the operating principles of networking
devices and server types, the inter-dependence of workstation hardware with relevant networking
software, and investigate the different types of servers giving recommendations on performance
and cost for a selection of various network situation. The third part will describe the network
topology in the case study and provide a conclusion of the entire paper.
Benefits and Constraints of Different Network Types and Standards
Types of Computer Network
The basic function of a network is to transfer data from one node to another and share resources
such as printers, databases, and servers. A network can be differentiated depending on the range
of computer network and the size. The most common types of computer networks include: Wide
Area Network (WAN), Metropolitan Area Network (MAN), and Local Area Network (LAN).
The subsection will discuss these types in details.
Local Area Network (LAN)
A local area network (LAN) is a type of a network that is used to connect computer systems in
one building, office, or a group of buildings that are nearby. The most commonly used standard
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK PRINCIPLES AND PROTOCOLS 4
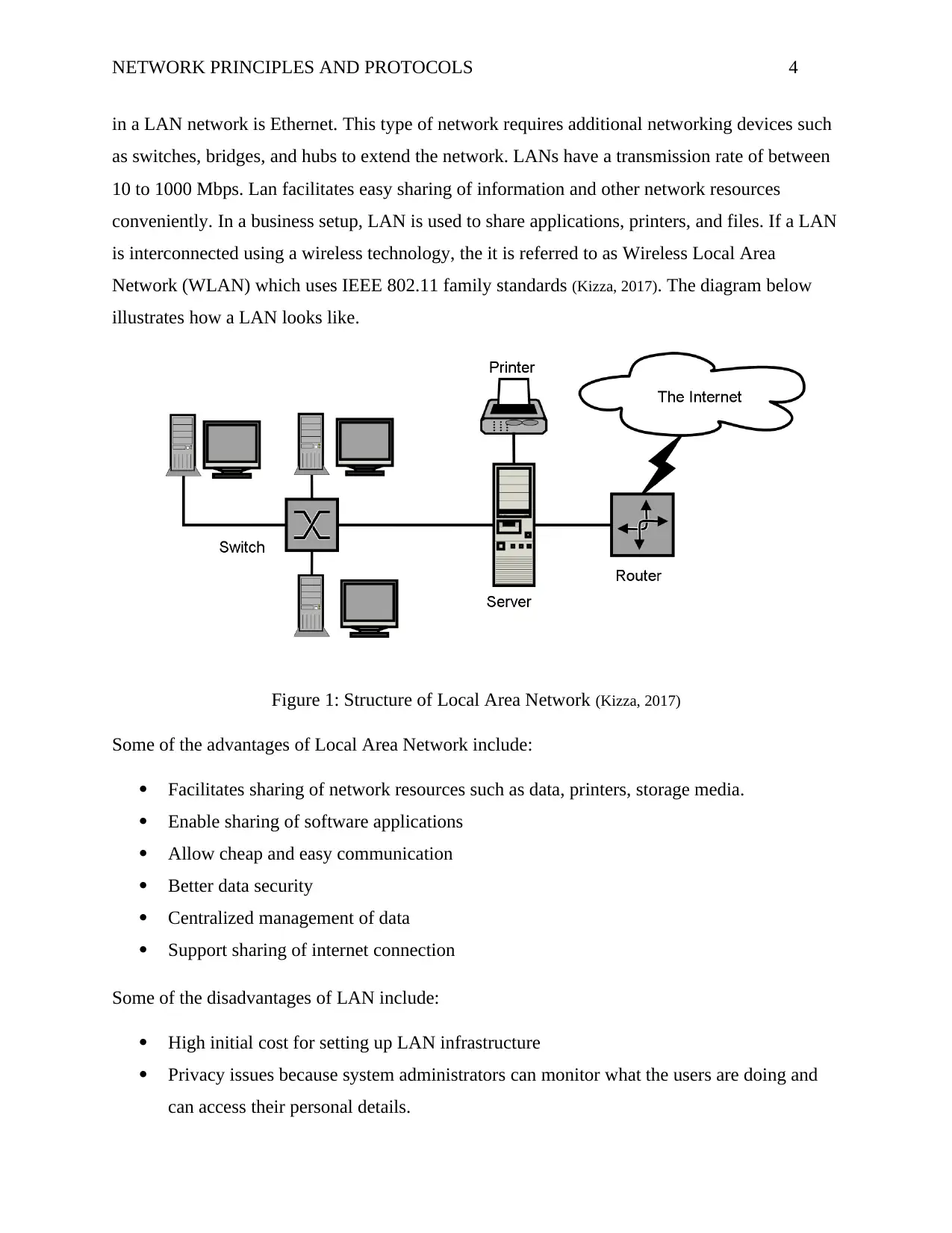
in a LAN network is Ethernet. This type of network requires additional networking devices such
as switches, bridges, and hubs to extend the network. LANs have a transmission rate of between
10 to 1000 Mbps. Lan facilitates easy sharing of information and other network resources
conveniently. In a business setup, LAN is used to share applications, printers, and files. If a LAN
is interconnected using a wireless technology, the it is referred to as Wireless Local Area
Network (WLAN) which uses IEEE 802.11 family standards (Kizza, 2017). The diagram below
illustrates how a LAN looks like.
Figure 1: Structure of Local Area Network (Kizza, 2017)
Some of the advantages of Local Area Network include:
Facilitates sharing of network resources such as data, printers, storage media.
Enable sharing of software applications
Allow cheap and easy communication
Better data security
Centralized management of data
Support sharing of internet connection
Some of the disadvantages of LAN include:
High initial cost for setting up LAN infrastructure
Privacy issues because system administrators can monitor what the users are doing and
can access their personal details.
in a LAN network is Ethernet. This type of network requires additional networking devices such
as switches, bridges, and hubs to extend the network. LANs have a transmission rate of between
10 to 1000 Mbps. Lan facilitates easy sharing of information and other network resources
conveniently. In a business setup, LAN is used to share applications, printers, and files. If a LAN
is interconnected using a wireless technology, the it is referred to as Wireless Local Area
Network (WLAN) which uses IEEE 802.11 family standards (Kizza, 2017). The diagram below
illustrates how a LAN looks like.
Figure 1: Structure of Local Area Network (Kizza, 2017)
Some of the advantages of Local Area Network include:
Facilitates sharing of network resources such as data, printers, storage media.
Enable sharing of software applications
Allow cheap and easy communication
Better data security
Centralized management of data
Support sharing of internet connection
Some of the disadvantages of LAN include:
High initial cost for setting up LAN infrastructure
Privacy issues because system administrators can monitor what the users are doing and
can access their personal details.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK PRINCIPLES AND PROTOCOLS 5
Centralized data management increased the threats and makes the data vulnerable
Covers only a limited area, a building or an office
Metropolitan Area Network (MAN)
A Metropolitan Area Network is a type of computer network that interconnects different LANs
within close proximity mostly in a metropolitan area such as a town or a city. High performance
fiber-based and high-performance routers are used to interconnect the LAN allowing high data
transfer rates than the internet. MAN networks mostly use IEEE 802.16 family standards
(Peterson, 2011).
Some of the advantages of metropolitan area network include:
It is less expensive that wide area network
One can send emails for free
As compared to wide area network, it has higher speeds.
Allow sharing of internet
Higher level of security compared to wide area network
It is easy to convert LAN to MAN
Some of the disadvantages include:
It is difficult to manage
Varying internet speeds
Prone to hacker attacks
Expensive because it requires more cables and hiring of technical people to set up.
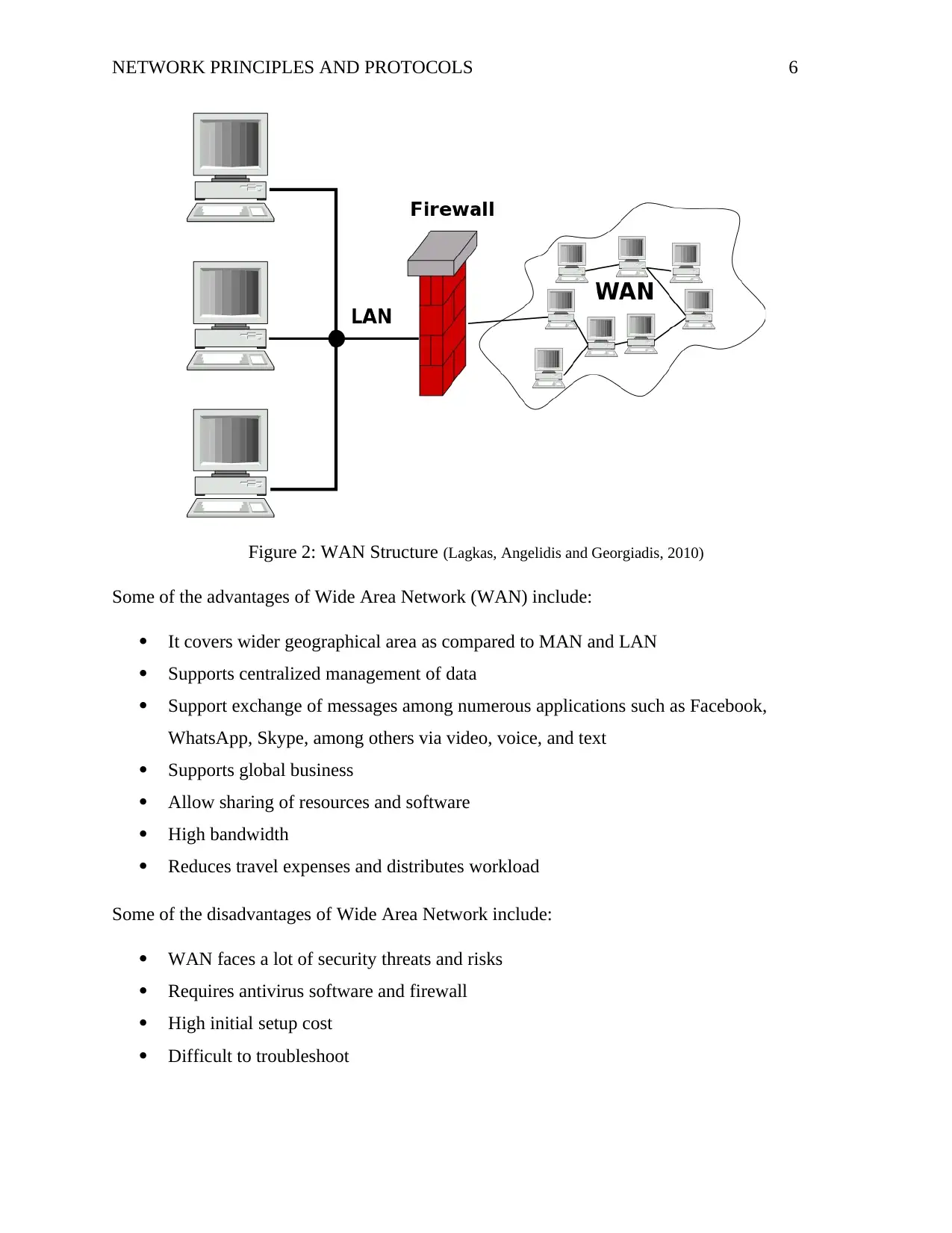
Wide Area Network (WAN)
A Wide Area Network (WAN) is a type of computer network that cover a large geographical
area by connecting the various MANs and LANs. WAN facilitate communication among the
different computer systems and people across the world (Lagkas, Angelidis and Georgiadis, 2010).
WAN can be implemented using a private network od a public transmission system. The diagram
below illustrates the structure of a WAN.
Centralized data management increased the threats and makes the data vulnerable
Covers only a limited area, a building or an office
Metropolitan Area Network (MAN)
A Metropolitan Area Network is a type of computer network that interconnects different LANs
within close proximity mostly in a metropolitan area such as a town or a city. High performance
fiber-based and high-performance routers are used to interconnect the LAN allowing high data
transfer rates than the internet. MAN networks mostly use IEEE 802.16 family standards
(Peterson, 2011).
Some of the advantages of metropolitan area network include:
It is less expensive that wide area network
One can send emails for free
As compared to wide area network, it has higher speeds.
Allow sharing of internet
Higher level of security compared to wide area network
It is easy to convert LAN to MAN
Some of the disadvantages include:
It is difficult to manage
Varying internet speeds
Prone to hacker attacks
Expensive because it requires more cables and hiring of technical people to set up.
Wide Area Network (WAN)
A Wide Area Network (WAN) is a type of computer network that cover a large geographical
area by connecting the various MANs and LANs. WAN facilitate communication among the
different computer systems and people across the world (Lagkas, Angelidis and Georgiadis, 2010).
WAN can be implemented using a private network od a public transmission system. The diagram
below illustrates the structure of a WAN.
NETWORK PRINCIPLES AND PROTOCOLS 6
Figure 2: WAN Structure (Lagkas, Angelidis and Georgiadis, 2010)
Some of the advantages of Wide Area Network (WAN) include:
It covers wider geographical area as compared to MAN and LAN
Supports centralized management of data
Support exchange of messages among numerous applications such as Facebook,
WhatsApp, Skype, among others via video, voice, and text
Supports global business
Allow sharing of resources and software
High bandwidth
Reduces travel expenses and distributes workload
Some of the disadvantages of Wide Area Network include:
WAN faces a lot of security threats and risks
Requires antivirus software and firewall
High initial setup cost
Difficult to troubleshoot
Figure 2: WAN Structure (Lagkas, Angelidis and Georgiadis, 2010)
Some of the advantages of Wide Area Network (WAN) include:
It covers wider geographical area as compared to MAN and LAN
Supports centralized management of data
Support exchange of messages among numerous applications such as Facebook,
WhatsApp, Skype, among others via video, voice, and text
Supports global business
Allow sharing of resources and software
High bandwidth
Reduces travel expenses and distributes workload
Some of the disadvantages of Wide Area Network include:
WAN faces a lot of security threats and risks
Requires antivirus software and firewall
High initial setup cost
Difficult to troubleshoot
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK PRINCIPLES AND PROTOCOLS 7
Networking Standards
There exist different networking standards today. Every network standard has a specific purpose
that is outlines by the standard itself (Begen, Bok and Saltsidis, 2017). The is a different standard that
allows one to communicate through a telephone line and a different one that allows you to
communicate through the internet. Basically, it is the network standards that dictates how we
interact on a daily business through the different networking platforms (Begen, Bok and Saltsidis,
2017). There exist different types of network standards such as de facto standards which are
developed by network vendors like Cisco, the Institute of Electrical and Electronics Engineering,
the American National Standards Institute (ANSI), and those published by the International
Telecommunication Union (Mariotte and Starr, 2018). The most commonly used standards are those
from the IEEE 802 family including IEEE 802.11 designed for Wireless Local area network,
IEEE 802.5 designed for token ring topology networks, IEEE 802.3 designed for Ethernet
Networks, and IEEE802.1 designed for MAN and LAN networks (Begen, Bok and Saltsidis, 2017).
These standards are very important because they have been designed to help us in establishing
communications.
Impact of Network Topology, Communication and Bandwidth Requirements
A network topology can be described as the organization of computer systems on a network. It
outlines how the different nodes on a network are organized and how they are connected to one
another. Basically, it is the physical connection of the nodes and links on a computer network.
There are different network topologies including star topology, ring topology, bus topology,
mesh, and tree topology (Soparia and Bhatt, 2014). These topologies are very essential when
designing a computer network, because as mentioned earlier it determines how the different
nodes on a network communicate. It also determines the performance and the amount of
bandwidth that can be transmitted on the network.
Basically, bandwidth requirements are dictated by the needs of the organization. Typically, a
smaller network requires less bandwidth as compared to a larger network where traffic is heavy.
Bandwidth refers to the amount of data that can be transmitted on a network at a specific time.
Basically, high bandwidth is expensive however, it can transmit data faster the low bandwidth
Networking Standards
There exist different networking standards today. Every network standard has a specific purpose
that is outlines by the standard itself (Begen, Bok and Saltsidis, 2017). The is a different standard that
allows one to communicate through a telephone line and a different one that allows you to
communicate through the internet. Basically, it is the network standards that dictates how we
interact on a daily business through the different networking platforms (Begen, Bok and Saltsidis,
2017). There exist different types of network standards such as de facto standards which are
developed by network vendors like Cisco, the Institute of Electrical and Electronics Engineering,
the American National Standards Institute (ANSI), and those published by the International
Telecommunication Union (Mariotte and Starr, 2018). The most commonly used standards are those
from the IEEE 802 family including IEEE 802.11 designed for Wireless Local area network,
IEEE 802.5 designed for token ring topology networks, IEEE 802.3 designed for Ethernet
Networks, and IEEE802.1 designed for MAN and LAN networks (Begen, Bok and Saltsidis, 2017).
These standards are very important because they have been designed to help us in establishing
communications.
Impact of Network Topology, Communication and Bandwidth Requirements
A network topology can be described as the organization of computer systems on a network. It
outlines how the different nodes on a network are organized and how they are connected to one
another. Basically, it is the physical connection of the nodes and links on a computer network.
There are different network topologies including star topology, ring topology, bus topology,
mesh, and tree topology (Soparia and Bhatt, 2014). These topologies are very essential when
designing a computer network, because as mentioned earlier it determines how the different
nodes on a network communicate. It also determines the performance and the amount of
bandwidth that can be transmitted on the network.
Basically, bandwidth requirements are dictated by the needs of the organization. Typically, a
smaller network requires less bandwidth as compared to a larger network where traffic is heavy.
Bandwidth refers to the amount of data that can be transmitted on a network at a specific time.
Basically, high bandwidth is expensive however, it can transmit data faster the low bandwidth
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK PRINCIPLES AND PROTOCOLS 8
network (Rodrigues, 2012). The amount of bandwidth influenced by the types of modems and
network cards used as well as the kind of cable used.
Network Principles
This section will compare the different network principles and discuss how the various network
protocols enable effectiveness of the different network systems. The different processes running
in different systems can only communicate if there is any link between the two systems. There
are various network principles but this section will only focus on the common principles. They
include the following (Peterson and Davie, 2012):
Switching principles: this principle describes how data is transmitted from one end point to
another through a computer network. There are three type of switching including packet
switching, message switching, and circuit switching.
Message Passing Principle: this principle differs from the switching principle in that, message
passing principle deal with concerns like the type of connection between the receiver and the
sender; whether connectionless or connection-oriented, how massages are addresses, and the
synchronization between the receiving and the sending activities.
Addressing principle: this principle is sued to determine with whom to communicate either by
address, name, content, sources, route, group, or broadcast identifier. Data representation is
another principle that determines how data is represented in the different computer systems
because different computers run on different CPUs. Many at time, data presentation problems
occur because of the size of the pointers, the alignment of data, representation of floating-point
numbers, and the order of bytes in a word.
How Protocols Enable the Effectiveness of Network Systems
Protocols plays a very significant role in enabling the effectiveness of network systems. There
exists different protocol, and just like the network standard each particular protocol plays a
specific role in communication and ensuring effectiveness of the computer systems (Lloret, 2009).
Data link protocol on layer 2 of the OSI layer is responsible for logical and physical connections
to the destination of the packet using the network interface card (NIC) (Lloret, 2009). Transmission
network (Rodrigues, 2012). The amount of bandwidth influenced by the types of modems and
network cards used as well as the kind of cable used.
Network Principles
This section will compare the different network principles and discuss how the various network
protocols enable effectiveness of the different network systems. The different processes running
in different systems can only communicate if there is any link between the two systems. There
are various network principles but this section will only focus on the common principles. They
include the following (Peterson and Davie, 2012):
Switching principles: this principle describes how data is transmitted from one end point to
another through a computer network. There are three type of switching including packet
switching, message switching, and circuit switching.
Message Passing Principle: this principle differs from the switching principle in that, message
passing principle deal with concerns like the type of connection between the receiver and the
sender; whether connectionless or connection-oriented, how massages are addresses, and the
synchronization between the receiving and the sending activities.
Addressing principle: this principle is sued to determine with whom to communicate either by
address, name, content, sources, route, group, or broadcast identifier. Data representation is
another principle that determines how data is represented in the different computer systems
because different computers run on different CPUs. Many at time, data presentation problems
occur because of the size of the pointers, the alignment of data, representation of floating-point
numbers, and the order of bytes in a word.
How Protocols Enable the Effectiveness of Network Systems
Protocols plays a very significant role in enabling the effectiveness of network systems. There
exists different protocol, and just like the network standard each particular protocol plays a
specific role in communication and ensuring effectiveness of the computer systems (Lloret, 2009).
Data link protocol on layer 2 of the OSI layer is responsible for logical and physical connections
to the destination of the packet using the network interface card (NIC) (Lloret, 2009). Transmission

NETWORK PRINCIPLES AND PROTOCOLS 9
control protocol and internet protocol are responsible for routing and directing the packets to the
right destination using the shortest route possible. Additionally, other protocols like UDP are
responsible for establishing connection between two systems on the network through the ports
identified by the IP address and the corresponding port number.
Task 2 Networking Devices and Operations
This section will be responsible for discussing the operating principles of the different
networking devices and server types.
The operating principle of Networking Devices
This section will discuss the operating principle of the different networking devices. We will
focus on the most common networking devices such as a switch, router, hub, gateway, modem,
and network interface card (Sosinsky, 2009).
Network Interface Card (NIC): networking is not possible without this device. It enables the
communication between a device and other networking devices. The function of an NIC card is
to convert the packets between two different technologies of data transmission. Basically, it
converts serial data into parallel data streams and vice versa (Trivedi, 2013).
Bridge: a bridge is a networking device that us used in large network to divide it into small
segments. It connects different types of transmission medium such as a fiber optic with a UTP
cable and connected networks with different architectures such as Token ring with Ethernet
networks.
Switch: this networking device is used to connect several network components in a network just
like a bridge and a hub. However, it has additional functions. The main function of a switch is to
make switching decisions in hardware using application specific integrated circuits (ASICs)
(Trivedi, 2013). It works just like a hub but the difference is that the switch does not broadcast the
data signals, it analyzes the signal identifies the destination address and forwards it only to the
target destination node.
control protocol and internet protocol are responsible for routing and directing the packets to the
right destination using the shortest route possible. Additionally, other protocols like UDP are
responsible for establishing connection between two systems on the network through the ports
identified by the IP address and the corresponding port number.
Task 2 Networking Devices and Operations
This section will be responsible for discussing the operating principles of the different
networking devices and server types.
The operating principle of Networking Devices
This section will discuss the operating principle of the different networking devices. We will
focus on the most common networking devices such as a switch, router, hub, gateway, modem,
and network interface card (Sosinsky, 2009).
Network Interface Card (NIC): networking is not possible without this device. It enables the
communication between a device and other networking devices. The function of an NIC card is
to convert the packets between two different technologies of data transmission. Basically, it
converts serial data into parallel data streams and vice versa (Trivedi, 2013).
Bridge: a bridge is a networking device that us used in large network to divide it into small
segments. It connects different types of transmission medium such as a fiber optic with a UTP
cable and connected networks with different architectures such as Token ring with Ethernet
networks.
Switch: this networking device is used to connect several network components in a network just
like a bridge and a hub. However, it has additional functions. The main function of a switch is to
make switching decisions in hardware using application specific integrated circuits (ASICs)
(Trivedi, 2013). It works just like a hub but the difference is that the switch does not broadcast the
data signals, it analyzes the signal identifies the destination address and forwards it only to the
target destination node.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK PRINCIPLES AND PROTOCOLS 10
Modem: basically, this networking devices is used to connect a network to the internet. It allows
digital data to be transported via telecommunication lines. It allows for communication between
a telecommunication company and the different computer systems on the network.
Router: a router us used to interconnect two different network segments. When a router receives
a packet on its interface, it determines its destination address, and forwards the packet to the
destination address from the interface connected to the destination address. The router maintains
a record of all the connected network sin order to forward a packet. Typically, a router connects
network segments that are different, used to connect different network protocols such as IPX and
IP, connect two different transmission media such as fiber optic and UTP, breaks a large network
in to smaller networks, connects smaller networks in to one big network, enables access to DSL
services, and connects two different network architectures (Trivedi, 2013).
Operating Principle of Different Types of Servers
there exist many types of servers in the computing world. This section will attempt to discuss the
operating principle of three most common servers. A server is a dedicated computer that is
powerful and specialized machine designed to offer dedicated services to other computers
(Bannister, 2012). The following are the different types of servers:
File server: a file server is a type of server that is dedicate to allow users to access file records
from a file server on a network.
Database server: this is a type of server where a client makes SQL requests to a server and the
response is given through the network (Bannister, 2012).
Transaction server: in this type of sever, a client invokes remote procedures that is stored on the
server that contains SQL database engine. The server has procedural statements that are used to
process a batch of SQL statements (transactions) (Bannister, 2012). (Bannister, 2012)
Inter-Dependence of Workstation Hardware with Relevant Networking
Software
Modem: basically, this networking devices is used to connect a network to the internet. It allows
digital data to be transported via telecommunication lines. It allows for communication between
a telecommunication company and the different computer systems on the network.
Router: a router us used to interconnect two different network segments. When a router receives
a packet on its interface, it determines its destination address, and forwards the packet to the
destination address from the interface connected to the destination address. The router maintains
a record of all the connected network sin order to forward a packet. Typically, a router connects
network segments that are different, used to connect different network protocols such as IPX and
IP, connect two different transmission media such as fiber optic and UTP, breaks a large network
in to smaller networks, connects smaller networks in to one big network, enables access to DSL
services, and connects two different network architectures (Trivedi, 2013).
Operating Principle of Different Types of Servers
there exist many types of servers in the computing world. This section will attempt to discuss the
operating principle of three most common servers. A server is a dedicated computer that is
powerful and specialized machine designed to offer dedicated services to other computers
(Bannister, 2012). The following are the different types of servers:
File server: a file server is a type of server that is dedicate to allow users to access file records
from a file server on a network.
Database server: this is a type of server where a client makes SQL requests to a server and the
response is given through the network (Bannister, 2012).
Transaction server: in this type of sever, a client invokes remote procedures that is stored on the
server that contains SQL database engine. The server has procedural statements that are used to
process a batch of SQL statements (transactions) (Bannister, 2012). (Bannister, 2012)
Inter-Dependence of Workstation Hardware with Relevant Networking
Software
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK PRINCIPLES AND PROTOCOLS 11
This section will discuss the inter-dependence of workstation hardware with the relevant
software. A hardware is the physical component that we see on a computer including hard drives,
memory, processor, monitor, peripheral devices among others. Networking software such as
network operating system requires hardware that is compatible with them to operate. As such,
the workstation hardware provides a platform for installing the different types of network
software (Comer, 2015). The hardware is used to maintain the network software, while the software
is used to maintain the network and its resources. In this set up, PRTG monitor will be used to
monitor the network hardware and the overall network infrastructure. For instance, if a network
administrator wants to check on how the different hardware devices such as router, switch,
access points, or servers are working, PRTG software can be used. Also, network operating
system is required to control the network hardware components.
Types of Servers and Recommendations Based on Performance and Cost
The choice of servers depends on the business requirements. Also, the cost of the server is based
on its performance. This section will provide a summary of the different types of servers with
recommendations based on cost and performance.
Proxy server Mail server Web Servers FTP servers Application
server
Cost £900 £1500 £2000 £800 £1099
Performance Number of
CPUs: 2
RAM: at least
8GB
Number of
CPUs: 3
RAM: at least
8GB
Number of
CPUs: 4
RAM: at least
16GB
Number of
CPUs: 2
RAM: at least
8GB
Number of
CPUs: 4
RAM: at
least 32GB
Table 1: Types of Servers (Ezhilchelvan and Mitrani, 2017)
For the above case, a mail server with 3 CPUs and 8GB RAM will be enough to handle the
requirements of the company. It can be noted that this is a small network and will only require
application and mail servers. For the application server, a 32GB RAM and 4CPUs server is
This section will discuss the inter-dependence of workstation hardware with the relevant
software. A hardware is the physical component that we see on a computer including hard drives,
memory, processor, monitor, peripheral devices among others. Networking software such as
network operating system requires hardware that is compatible with them to operate. As such,
the workstation hardware provides a platform for installing the different types of network
software (Comer, 2015). The hardware is used to maintain the network software, while the software
is used to maintain the network and its resources. In this set up, PRTG monitor will be used to
monitor the network hardware and the overall network infrastructure. For instance, if a network
administrator wants to check on how the different hardware devices such as router, switch,
access points, or servers are working, PRTG software can be used. Also, network operating
system is required to control the network hardware components.
Types of Servers and Recommendations Based on Performance and Cost
The choice of servers depends on the business requirements. Also, the cost of the server is based
on its performance. This section will provide a summary of the different types of servers with
recommendations based on cost and performance.
Proxy server Mail server Web Servers FTP servers Application
server
Cost £900 £1500 £2000 £800 £1099
Performance Number of
CPUs: 2
RAM: at least
8GB
Number of
CPUs: 3
RAM: at least
8GB
Number of
CPUs: 4
RAM: at least
16GB
Number of
CPUs: 2
RAM: at least
8GB
Number of
CPUs: 4
RAM: at
least 32GB
Table 1: Types of Servers (Ezhilchelvan and Mitrani, 2017)
For the above case, a mail server with 3 CPUs and 8GB RAM will be enough to handle the
requirements of the company. It can be noted that this is a small network and will only require
application and mail servers. For the application server, a 32GB RAM and 4CPUs server is

NETWORK PRINCIPLES AND PROTOCOLS 12
recommended because regardless of the size of the company, some applications may be ‘heavy’
and may consume a lot of run time capacity.
A proxy server is required to manage request from clients who are trying to access resources
from other servers. The company will also require a web server to allow the clients to access web
pages through hypertext transfer protocol which are then forwarded to the client through a web
browser. FTP server is necessary to allow sharing of files and access to common, up-to-date
records. It is used to mange file transfer between the server and the clients connected on a
network.
Task 3 Conclusion
The type of network topology in the case study bus topology. In this topology, all the network
devices are connected to one backbone cable. The type of cable used varies, but for the above
case cat5 ethernet cable can be used. This topology has several advantages including:
recommended for small networks, easy for connecting devices in a liner manner, and is cheaper
as it requires shorter cables. However, it has a number of setbacks including: it is quite difficult
to troubleshoot the network, difficult to troubleshoot specific issues on individual devices, does
not work well for larger networks, requires terminators on both ends of the backbone cable, if the
backbone cable fails, the entire network is compromised, and is slower. This topology can be
substituted with other topologies such as bus topology or tree topology because they offer better
performance and are more reliable
recommended because regardless of the size of the company, some applications may be ‘heavy’
and may consume a lot of run time capacity.
A proxy server is required to manage request from clients who are trying to access resources
from other servers. The company will also require a web server to allow the clients to access web
pages through hypertext transfer protocol which are then forwarded to the client through a web
browser. FTP server is necessary to allow sharing of files and access to common, up-to-date
records. It is used to mange file transfer between the server and the clients connected on a
network.
Task 3 Conclusion
The type of network topology in the case study bus topology. In this topology, all the network
devices are connected to one backbone cable. The type of cable used varies, but for the above
case cat5 ethernet cable can be used. This topology has several advantages including:
recommended for small networks, easy for connecting devices in a liner manner, and is cheaper
as it requires shorter cables. However, it has a number of setbacks including: it is quite difficult
to troubleshoot the network, difficult to troubleshoot specific issues on individual devices, does
not work well for larger networks, requires terminators on both ends of the backbone cable, if the
backbone cable fails, the entire network is compromised, and is slower. This topology can be
substituted with other topologies such as bus topology or tree topology because they offer better
performance and are more reliable
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




