Secure Unified Communication System Design for Fenwick Inc. Project
VerifiedAdded on 2023/04/20
|17
|9823
|402
Report
AI Summary
This report proposes a secure Unified Communication (UC) system design for Fenwick Inc., an international law firm planning to expand in the Newcastle area. The design focuses on unifying communication across three large offices, addressing potential threats through threat modeling, and ensuring secure data exchange. Key considerations include ethical implications, service differentiation, and security measures such as firewalls, intrusion detection systems, and VPNs. The report also explores cloud-based solutions, remote user management, and the importance of network performance for multimedia applications. Vulnerability assessments are performed to identify and mitigate potential impacts and losses due to attacks. The goal is to create a robust, secure, and efficient communication infrastructure that meets the specific needs of Fenwick Inc.

Running head: NETWORK SECURITY
Network security
Name of the Student
Name of the University
Author’s Note
Network security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY
Executive Summary
Unified communication is used for integrating the different real time communication system into a
single platform for saving the cost and increasing the efficiency of communication between the user.
Internet protocol is used for allowing the service and application to communicate with each other.
Since the cost of implementation of unified communication model is higher it is not feasible for small
and medium sized business. The implementation of cloud based solution in the business can help in
development of powerful platform and enables the organization to migrate their files and information
in the cloud servers for sharing it with the users in different location. The selection of the cloud
platform helps in reducing the operational expense and eliminate the need of redundant equipment for
integrating the communication model in an unified platform. The performance issues of the network
and the ability of the network for tolerating delay and jitter is needed to be managed for eliminating the
jitter and guaranteeing quality of service. The organizational network is needed to be created with the
application of different protocols and technologies that enables the network to connect the remote
user for accessing the organizational resources and controlling the flow of data traffic in the network.
The network resources are needed to be partitioned and service level agreement is needed to be
created by defining the service policy and client requirement. Integrated service and availability of end
to end bandwidth is depended for elimination of congestion in the network and reach the remote
location in a minimum time frame.
NETWORK SECURITY
Executive Summary
Unified communication is used for integrating the different real time communication system into a
single platform for saving the cost and increasing the efficiency of communication between the user.
Internet protocol is used for allowing the service and application to communicate with each other.
Since the cost of implementation of unified communication model is higher it is not feasible for small
and medium sized business. The implementation of cloud based solution in the business can help in
development of powerful platform and enables the organization to migrate their files and information
in the cloud servers for sharing it with the users in different location. The selection of the cloud
platform helps in reducing the operational expense and eliminate the need of redundant equipment for
integrating the communication model in an unified platform. The performance issues of the network
and the ability of the network for tolerating delay and jitter is needed to be managed for eliminating the
jitter and guaranteeing quality of service. The organizational network is needed to be created with the
application of different protocols and technologies that enables the network to connect the remote
user for accessing the organizational resources and controlling the flow of data traffic in the network.
The network resources are needed to be partitioned and service level agreement is needed to be
created by defining the service policy and client requirement. Integrated service and availability of end
to end bandwidth is depended for elimination of congestion in the network and reach the remote
location in a minimum time frame.

2
NETWORK SECURITY
Table of Contents
Introduction............................................................................................................................................ 3
UC Threat Modelling.............................................................................................................................. 3
Design Specifications and Ethical Considerations.................................................................................6
Differentiation of services and classes of applications and their requirements..................................6
Security threats:................................................................................................................................. 8
Solution of the security issues:........................................................................................................... 9
Monitoring.......................................................................................................................................... 9
Remote User management.............................................................................................................. 11
Ethical Consideration:...................................................................................................................... 11
Conclusion........................................................................................................................................... 13
Bibliography......................................................................................................................................... 15
NETWORK SECURITY
Table of Contents
Introduction............................................................................................................................................ 3
UC Threat Modelling.............................................................................................................................. 3
Design Specifications and Ethical Considerations.................................................................................6
Differentiation of services and classes of applications and their requirements..................................6
Security threats:................................................................................................................................. 8
Solution of the security issues:........................................................................................................... 9
Monitoring.......................................................................................................................................... 9
Remote User management.............................................................................................................. 11
Ethical Consideration:...................................................................................................................... 11
Conclusion........................................................................................................................................... 13
Bibliography......................................................................................................................................... 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK SECURITY
Introduction
The report is prepared for an international law firm Fenwick Inc for the identification of the
potential of the business opportunity in the greater Newcastle area. In the report a design is proposed
for the implementation of the secure Unified Communication (UC) in the current business process for
meeting the needs of the customer. The development of the unified communication system would
help the organization to eliminate the communication barrier for operating 3 large offices in different
geographical location. For the management of the communication between the three large firms
different services are needed to be provided for the unification of the tools used for communication
and securing the communication between the employees. For interconnecting each of the branches a
distributed network infrastructure should be developed that has the ability to exchange different type
of information. For the development of the network solution an unified threat modelling is created and
the design specification and ethical consideration are evaluated for eliminating the errors and develop
the solution meeting the needs of the organization. There are different approaches that are
implemented for guaranteeing service for the multimedia application and the approaches are divided
into adaptation based schemes, reservation based schemes and network level protocols. The network
level protocols are used for providing QoS support by analysing the network parameters and
interpreting it with the application requirement. It helps in enhancement of the switches connected in
the network and management of the application flow service. The reservation based schemes are
used for reserving the resources of the network following the requirement of the application.
Admission control mechanism are used for matching the request of the application with the availability
of resource. The adaptation based schemes are used for utilizing the adaptive behaviour of the
application that does not have a need of hard service and perform active resource management that
is aware of different application. There are different optimization schemed that are applied for the
development of unified communication network such as integration of the application processing with
the data transport for improvement of the performance of the application and services.
UC Threat Modelling
The unified communication is used for integrating more than one real time communication
system as a single platform and recording the details of the interaction between the user and the
different services provided to the user connected in the network. The model should be developed
such that the user connect with the network from any geographical location. There are different risk
acting on the unified communication network and most of the attacks in the unified communication
network occurs from the internal sources and there is a need to develop a BYOD policy for the
employees for securing the network from malware, data leakage and other types of attacks(Carroll
2014). The poor security practice followed for the development of the network should be identified and
proper security measures should be applied for securing the network from the internal or the external
agents. The following risks are identified and need to be mitigated for the development of unified
communication system such as:
Troll frauds – This risk arise when an attacker forges with the VoIP system by making calls using a
stolen account and automate calls by ringing and generate massive bills for the organization. The
security of the network can be compromised causing different types of attacks such as buffer
overflow, bypass fraud and call transfer.
Eavesdropping – this type of attacks are performed by the attacker for compromising the
network security of the unified communication network with the use of malware and exploiting the
network. The hacker can steal insider information by listening to the board meetings and this type of
attack may not occur at a real time since the hacker can drop in and out of the network for gathering
the data or information captured that are necessary.
Packet Injection – this type of attack occurs for altering the nature of the data traffic in the
network that is intended for a destination address (Inukollu, Arsi and Ravuri 2014). The attacker
injects malformed packets or modifies the RTP packets for intercepting the communication.
Phishing and Vishing – this method is used for attempting and acquiring private or personal
information and is performed by performing fraud attempt for gaining the banking information with the
means of email. The concept of vishing is used as the backbone of phishing and it is done for the
fraud the voice service that takes place using the VoIP and the telephony service of the network.
NETWORK SECURITY
Introduction
The report is prepared for an international law firm Fenwick Inc for the identification of the
potential of the business opportunity in the greater Newcastle area. In the report a design is proposed
for the implementation of the secure Unified Communication (UC) in the current business process for
meeting the needs of the customer. The development of the unified communication system would
help the organization to eliminate the communication barrier for operating 3 large offices in different
geographical location. For the management of the communication between the three large firms
different services are needed to be provided for the unification of the tools used for communication
and securing the communication between the employees. For interconnecting each of the branches a
distributed network infrastructure should be developed that has the ability to exchange different type
of information. For the development of the network solution an unified threat modelling is created and
the design specification and ethical consideration are evaluated for eliminating the errors and develop
the solution meeting the needs of the organization. There are different approaches that are
implemented for guaranteeing service for the multimedia application and the approaches are divided
into adaptation based schemes, reservation based schemes and network level protocols. The network
level protocols are used for providing QoS support by analysing the network parameters and
interpreting it with the application requirement. It helps in enhancement of the switches connected in
the network and management of the application flow service. The reservation based schemes are
used for reserving the resources of the network following the requirement of the application.
Admission control mechanism are used for matching the request of the application with the availability
of resource. The adaptation based schemes are used for utilizing the adaptive behaviour of the
application that does not have a need of hard service and perform active resource management that
is aware of different application. There are different optimization schemed that are applied for the
development of unified communication network such as integration of the application processing with
the data transport for improvement of the performance of the application and services.
UC Threat Modelling
The unified communication is used for integrating more than one real time communication
system as a single platform and recording the details of the interaction between the user and the
different services provided to the user connected in the network. The model should be developed
such that the user connect with the network from any geographical location. There are different risk
acting on the unified communication network and most of the attacks in the unified communication
network occurs from the internal sources and there is a need to develop a BYOD policy for the
employees for securing the network from malware, data leakage and other types of attacks(Carroll
2014). The poor security practice followed for the development of the network should be identified and
proper security measures should be applied for securing the network from the internal or the external
agents. The following risks are identified and need to be mitigated for the development of unified
communication system such as:
Troll frauds – This risk arise when an attacker forges with the VoIP system by making calls using a
stolen account and automate calls by ringing and generate massive bills for the organization. The
security of the network can be compromised causing different types of attacks such as buffer
overflow, bypass fraud and call transfer.
Eavesdropping – this type of attacks are performed by the attacker for compromising the
network security of the unified communication network with the use of malware and exploiting the
network. The hacker can steal insider information by listening to the board meetings and this type of
attack may not occur at a real time since the hacker can drop in and out of the network for gathering
the data or information captured that are necessary.
Packet Injection – this type of attack occurs for altering the nature of the data traffic in the
network that is intended for a destination address (Inukollu, Arsi and Ravuri 2014). The attacker
injects malformed packets or modifies the RTP packets for intercepting the communication.
Phishing and Vishing – this method is used for attempting and acquiring private or personal
information and is performed by performing fraud attempt for gaining the banking information with the
means of email. The concept of vishing is used as the backbone of phishing and it is done for the
fraud the voice service that takes place using the VoIP and the telephony service of the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK SECURITY
Denial of Service – it is used for overloading the system with unwanted requests such that the
service are unavailable for the other users and the productivity of the organization is impacted. For
causing a denial of service for the voice service a war dialler is used that overloads the system by
request for outside connection.
Call hijacking – The devices that are connected as an endpoint should be safe from
tampering and this can be achieved by encrypting the voice packets with the implementation of
cryptographic algorithm.
For the development of the unified communication model and securing the VoIP and unified
communication there are different struggle faced by the IT administrators and the staffs. There are
different types of communication such as video and text, voice and they are performed in different
types of formats such as telephony-type voice traffic, audio conferencing, email and instant
messaging. The interaction between the users with the tools are needed to be managed by collecting
different client interface and combining them to create a single interface (Mahalingam et al. 2014).
There are different threats of unified communication and the voice and video communication should
be integrated to form a unified communication. The main concern for modelling the unified
communication is eavesdropping and unauthorised interception of the VoIP and other network traffic.
The application of the VPN topology for interconnecting the different branches may reduce the threat
and management of the data routes.
For securing the unified communication defence should be applied in all levels of the network
such that the unauthorised access of the resources are restricted and the application and services are
secured from the external agents. Security should be maintenance for the network devices such as
servers, IP phones, routers, switches and the communication channels. The unused services and
switch ports that are not currently used by the users should be blocked and such that it cannot be
used by the external agents for intruding into the network (Thomas 2014). User group policy should
be created and authentication and encryption should be applied at different levels of the connection
for the management of the identity of the users using the network framework. Firewalls should be
installed at the entry and exit point of the network and the routers should be configured with access
control list for the authentication of the access of the network. The switches should be configured with
VLANs and switchport security from preventing the illegal devices to be connected in the network and
protect the IP phone and desktop to access each other.
The application of host and network based intrusion detection system can also help in
monitoring the data traffic flowing from different address in the network. The intrusion detection
system can be combined with the intrusion prevention system for increasing the security of then
network framework and management of the unified communication traffic without adding latency in the
network. The intrusion prevention system or proxy servers are used for looking deep inside the unified
communication network and examination of the data that is sent for sending it in an acceptable
format. The host level security is needed to be measured for the implementation of the firewall,
antispyware and antivirus agents (Asrani, Koul and Khot 2016). The malicious hackers can seek the
path that have the least resistant to access the network and can compromise the security of the
unified communication via the clients or servers installed in the system. There are specific
technologies for example firewalls and SIP proxies that can be used for development of securing
unified communication and mult layer defence should be applied for protecting the network and
increase the security of the enterprise infrastructure.
For the implementation of the cloud service the security and threats should be identified for
mitigation of the threat and securing the network. There are different models that are used for
simulating the concepts and components with the system. The development of the unified
communication model helps in understanding the approach that is used for understanding the
problems in communication and improvement of the real life operation. There are different unified
modelling techniques that can be applied for the identification of each of the steps involved in threat
modelling process. The threat modelling is used for minimizing the vulnerability acting on the network
(Dham and Rao 2014). For the development of the unified communication network the threats acting
on the network is needed to be identified by performing a penetration test on the network. The
network should be developed in individual modules for the identification of the flow of the data packets
in the network and testing each of the modules for management of the exploitation of the network.
The threats can be shrugged off easily such that the security of the network is not compromised and
the awareness is improved for mitigation of the complex problems. After the identification of the
threats acting on the network the vulnerabilities assessment is needed to be performed that helps in
NETWORK SECURITY
Denial of Service – it is used for overloading the system with unwanted requests such that the
service are unavailable for the other users and the productivity of the organization is impacted. For
causing a denial of service for the voice service a war dialler is used that overloads the system by
request for outside connection.
Call hijacking – The devices that are connected as an endpoint should be safe from
tampering and this can be achieved by encrypting the voice packets with the implementation of
cryptographic algorithm.
For the development of the unified communication model and securing the VoIP and unified
communication there are different struggle faced by the IT administrators and the staffs. There are
different types of communication such as video and text, voice and they are performed in different
types of formats such as telephony-type voice traffic, audio conferencing, email and instant
messaging. The interaction between the users with the tools are needed to be managed by collecting
different client interface and combining them to create a single interface (Mahalingam et al. 2014).
There are different threats of unified communication and the voice and video communication should
be integrated to form a unified communication. The main concern for modelling the unified
communication is eavesdropping and unauthorised interception of the VoIP and other network traffic.
The application of the VPN topology for interconnecting the different branches may reduce the threat
and management of the data routes.
For securing the unified communication defence should be applied in all levels of the network
such that the unauthorised access of the resources are restricted and the application and services are
secured from the external agents. Security should be maintenance for the network devices such as
servers, IP phones, routers, switches and the communication channels. The unused services and
switch ports that are not currently used by the users should be blocked and such that it cannot be
used by the external agents for intruding into the network (Thomas 2014). User group policy should
be created and authentication and encryption should be applied at different levels of the connection
for the management of the identity of the users using the network framework. Firewalls should be
installed at the entry and exit point of the network and the routers should be configured with access
control list for the authentication of the access of the network. The switches should be configured with
VLANs and switchport security from preventing the illegal devices to be connected in the network and
protect the IP phone and desktop to access each other.
The application of host and network based intrusion detection system can also help in
monitoring the data traffic flowing from different address in the network. The intrusion detection
system can be combined with the intrusion prevention system for increasing the security of then
network framework and management of the unified communication traffic without adding latency in the
network. The intrusion prevention system or proxy servers are used for looking deep inside the unified
communication network and examination of the data that is sent for sending it in an acceptable
format. The host level security is needed to be measured for the implementation of the firewall,
antispyware and antivirus agents (Asrani, Koul and Khot 2016). The malicious hackers can seek the
path that have the least resistant to access the network and can compromise the security of the
unified communication via the clients or servers installed in the system. There are specific
technologies for example firewalls and SIP proxies that can be used for development of securing
unified communication and mult layer defence should be applied for protecting the network and
increase the security of the enterprise infrastructure.
For the implementation of the cloud service the security and threats should be identified for
mitigation of the threat and securing the network. There are different models that are used for
simulating the concepts and components with the system. The development of the unified
communication model helps in understanding the approach that is used for understanding the
problems in communication and improvement of the real life operation. There are different unified
modelling techniques that can be applied for the identification of each of the steps involved in threat
modelling process. The threat modelling is used for minimizing the vulnerability acting on the network
(Dham and Rao 2014). For the development of the unified communication network the threats acting
on the network is needed to be identified by performing a penetration test on the network. The
network should be developed in individual modules for the identification of the flow of the data packets
in the network and testing each of the modules for management of the exploitation of the network.
The threats can be shrugged off easily such that the security of the network is not compromised and
the awareness is improved for mitigation of the complex problems. After the identification of the
threats acting on the network the vulnerabilities assessment is needed to be performed that helps in

5
NETWORK SECURITY
identification of potential impact and loss due to an attack (Kaplan et al. 2015). The vulnerability can
be categorized into the following four categories such as:
Devastating – The services, assets are lost and cannot be restored and it causes huge loss in
the business and reduces the number of visitors by 75%.
Severe – The network is damaged partially and some of the devices may not be restored and
it needs the network to be inoperable for several weeks for configuration and management of the
assets. It causes reduction of the visitors upto 50%.
Noticeable – It causes the network to be inoperable for limited time frame but it can recover
within 24 hours. In this type a limited number of network devices are affected and can be recovered
from the backup plan.
Minor – There are no significant impact of the vulnerability and the network downtime is less
than 3 hours a no internal network devices are affected.
For the assessment of the vulnerability the potential impact of the loss of the loss due to
different types of attacks are needed to eb measured and network professional with training should be
recruited for performing a penetration testing. The test helps in identification in the flaws in the
network design and configuration of the network devices used for the development of the proposed
unified communication network framework (Puthal et al. 2017). The test can be performed with the
means of automated software tools for exploitation of the network and access the core resources.
Information is gathered from the network and the possible entry points in then network are identified
and the attack is performed for breaking in the network. The findings are reported back for defining
the weakness of the security of the network framework and securing the network. The organization
security policy can also be tested for adhering the compliance requirement and increasing the security
awareness between the employees for responding against the security incidents immediately. The
weakness of the unified network are gathered and identified for making strategic decision and
prioritizing the remediation for mitigation of the threat and vulnerability of the network.
The penetration testing can also be performed on the cloud platform for the prevention of the
distributed attacks and prioritizing the investments for increasing the security. The frequency of
penetration testing needed to be performed on the network depends on the organizational framework.
It should be performed when there is a change in the current framework of the network i.e. new
application is added or an network device is replaced. The upgrades and modification in the network
and connecting new branches should be followed by a penetration testing for meeting the needs of
the network (Wang et al. 2015). The regulation and compliance of the safety standards are needed to
be followed for performing certain tasks and for the cloud platform permission of the cloud vendor is
needed to be taken for performing the pen test. The penetration testing tools are used for scanning
the malicious codes and uncovering the vulnerabilities of the standard application that may result in
breaching of the codes. The encryption techniques that are used for encrypting the channels of
communication can be identified with the hard coded values like password and username. The tools
used for testing are easy to be deployed and configured for scanning the system easily. The
vulnerabilities are categorized based on the severity and automated for verifying the vulnerabilities
and generating reports and logs. Some of the widely used penetration testing tools are Metasploit,
NMAP, Wireshark and John the ripper. The Metasploit is used for uncovering the security issues in a
network and verify the vulnerabilities for its mitigation and managing the security process. The NMAP
is used for scanning the open ports and the vulnerabilities related with the port. The IP address can
be directed with the NMAP and used for monitoring the service uptime and host for mapping the
network surface attacks (Bae et al. 2014). The wireshark can also be used for analysing the network
packets flowing in the network by capturing it and analysing the smaller details of the activities in the
network taking place. The real time traffic of the network is evaluated for the analysis of the threats
related with the unified communication network and scrutinize the traffic details at the different levels.
The john tool is use for cracking password in a package and identifying the password hashes for the
detection of a customizable cracker. The penetration tester uses the tool for launching different types
of attacks and finding the weakness of the database and the systems connected in the network.
For performing the penetration testing the scope is needed to be defined and it should include
the systems, locations, tools and techniques that can be used for penetration testing. For limiting the
scope of penetration testing such that the system have a control on the organization and manage the
NETWORK SECURITY
identification of potential impact and loss due to an attack (Kaplan et al. 2015). The vulnerability can
be categorized into the following four categories such as:
Devastating – The services, assets are lost and cannot be restored and it causes huge loss in
the business and reduces the number of visitors by 75%.
Severe – The network is damaged partially and some of the devices may not be restored and
it needs the network to be inoperable for several weeks for configuration and management of the
assets. It causes reduction of the visitors upto 50%.
Noticeable – It causes the network to be inoperable for limited time frame but it can recover
within 24 hours. In this type a limited number of network devices are affected and can be recovered
from the backup plan.
Minor – There are no significant impact of the vulnerability and the network downtime is less
than 3 hours a no internal network devices are affected.
For the assessment of the vulnerability the potential impact of the loss of the loss due to
different types of attacks are needed to eb measured and network professional with training should be
recruited for performing a penetration testing. The test helps in identification in the flaws in the
network design and configuration of the network devices used for the development of the proposed
unified communication network framework (Puthal et al. 2017). The test can be performed with the
means of automated software tools for exploitation of the network and access the core resources.
Information is gathered from the network and the possible entry points in then network are identified
and the attack is performed for breaking in the network. The findings are reported back for defining
the weakness of the security of the network framework and securing the network. The organization
security policy can also be tested for adhering the compliance requirement and increasing the security
awareness between the employees for responding against the security incidents immediately. The
weakness of the unified network are gathered and identified for making strategic decision and
prioritizing the remediation for mitigation of the threat and vulnerability of the network.
The penetration testing can also be performed on the cloud platform for the prevention of the
distributed attacks and prioritizing the investments for increasing the security. The frequency of
penetration testing needed to be performed on the network depends on the organizational framework.
It should be performed when there is a change in the current framework of the network i.e. new
application is added or an network device is replaced. The upgrades and modification in the network
and connecting new branches should be followed by a penetration testing for meeting the needs of
the network (Wang et al. 2015). The regulation and compliance of the safety standards are needed to
be followed for performing certain tasks and for the cloud platform permission of the cloud vendor is
needed to be taken for performing the pen test. The penetration testing tools are used for scanning
the malicious codes and uncovering the vulnerabilities of the standard application that may result in
breaching of the codes. The encryption techniques that are used for encrypting the channels of
communication can be identified with the hard coded values like password and username. The tools
used for testing are easy to be deployed and configured for scanning the system easily. The
vulnerabilities are categorized based on the severity and automated for verifying the vulnerabilities
and generating reports and logs. Some of the widely used penetration testing tools are Metasploit,
NMAP, Wireshark and John the ripper. The Metasploit is used for uncovering the security issues in a
network and verify the vulnerabilities for its mitigation and managing the security process. The NMAP
is used for scanning the open ports and the vulnerabilities related with the port. The IP address can
be directed with the NMAP and used for monitoring the service uptime and host for mapping the
network surface attacks (Bae et al. 2014). The wireshark can also be used for analysing the network
packets flowing in the network by capturing it and analysing the smaller details of the activities in the
network taking place. The real time traffic of the network is evaluated for the analysis of the threats
related with the unified communication network and scrutinize the traffic details at the different levels.
The john tool is use for cracking password in a package and identifying the password hashes for the
detection of a customizable cracker. The penetration tester uses the tool for launching different types
of attacks and finding the weakness of the database and the systems connected in the network.
For performing the penetration testing the scope is needed to be defined and it should include
the systems, locations, tools and techniques that can be used for penetration testing. For limiting the
scope of penetration testing such that the system have a control on the organization and manage the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK SECURITY
flow of the data packets (Gottimukkala et al. 2013). The penetration tester follows different types of
strategies for performing the test and secure the unified communication network such as:
Targeted testing – It is applied on the targeted devices and the user connected in the network
can visualize the test being carried out.
External testing – the externally visible servers of the company are targeted that includes the
DNS server, firewalls, web server and email server. The main objective of this type of attacks is to find
out that if an outsider can exploit the network if they gain access of this network devices.
Internal testing – It is performed inside the firewall by an authorized user who have the
standard access privileges for estimating the damages causes by an disgruntles employee.
Blind test – It is used for simulating the procedures and action of a real attacker for limiting the
information shared with the team or person performing the test (Liu et al. 2016). The penetration test
needs much amount of time and reconnaissance that can be expensive.
Double blind test – It is used for performing blind test on the network and there are one or two
people involved in the test and it can be used for monitoring the network security and identification of
the incident for development of the response plan.
Black box testing – It is similar with the blind test and no information about the network is
shared with the tester for performing the test and the test is performed by the tester by applying his
own knowledge
White box testing – The targeted user receives all types of information about the targeted
network before starting the test. The information contains the details of the IP address, protocols,
network infrastructure details and the source codes.
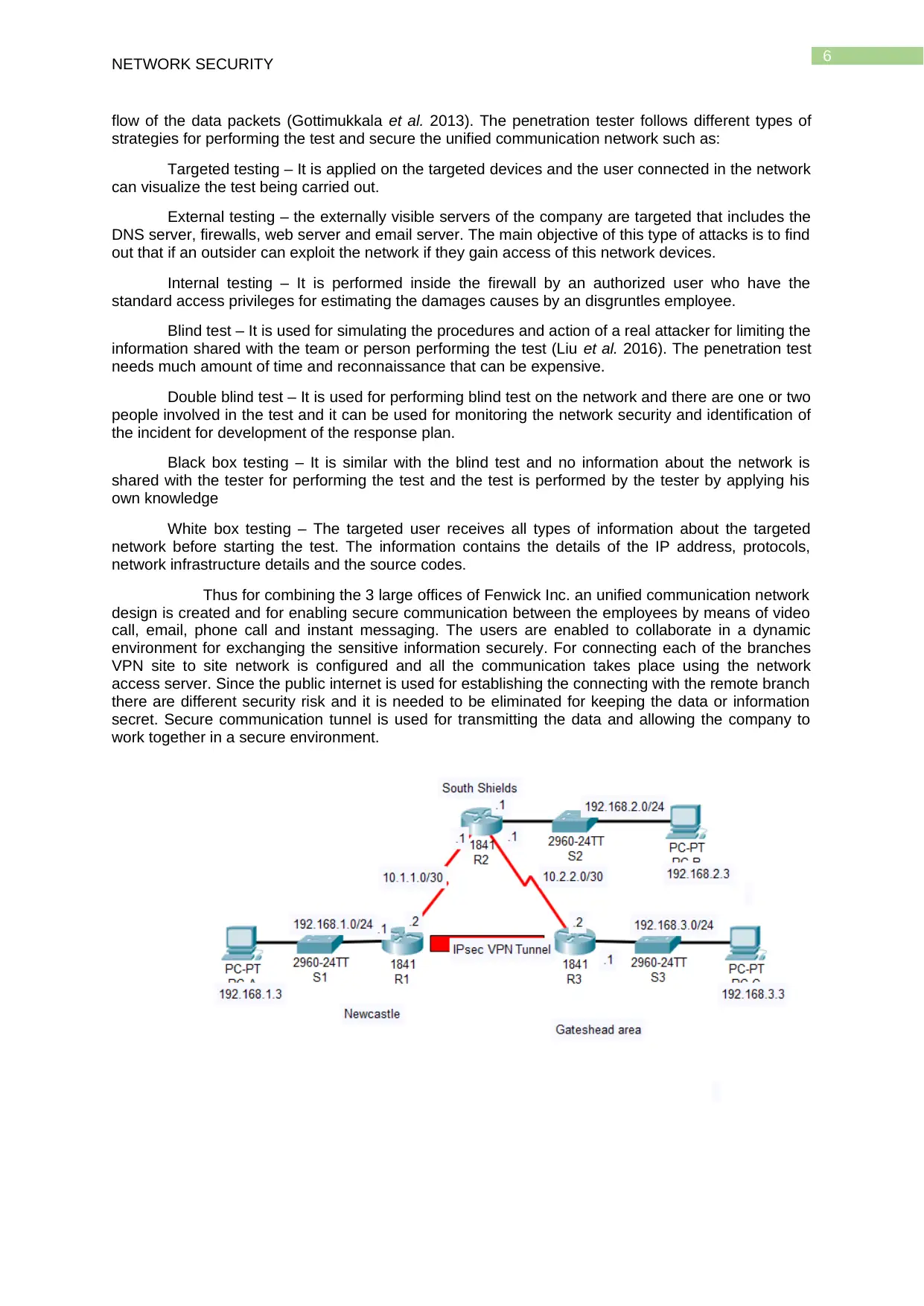
Thus for combining the 3 large offices of Fenwick Inc. an unified communication network
design is created and for enabling secure communication between the employees by means of video
call, email, phone call and instant messaging. The users are enabled to collaborate in a dynamic
environment for exchanging the sensitive information securely. For connecting each of the branches
VPN site to site network is configured and all the communication takes place using the network
access server. Since the public internet is used for establishing the connecting with the remote branch
there are different security risk and it is needed to be eliminated for keeping the data or information
secret. Secure communication tunnel is used for transmitting the data and allowing the company to
work together in a secure environment.
NETWORK SECURITY
flow of the data packets (Gottimukkala et al. 2013). The penetration tester follows different types of
strategies for performing the test and secure the unified communication network such as:
Targeted testing – It is applied on the targeted devices and the user connected in the network
can visualize the test being carried out.
External testing – the externally visible servers of the company are targeted that includes the
DNS server, firewalls, web server and email server. The main objective of this type of attacks is to find
out that if an outsider can exploit the network if they gain access of this network devices.
Internal testing – It is performed inside the firewall by an authorized user who have the
standard access privileges for estimating the damages causes by an disgruntles employee.
Blind test – It is used for simulating the procedures and action of a real attacker for limiting the
information shared with the team or person performing the test (Liu et al. 2016). The penetration test
needs much amount of time and reconnaissance that can be expensive.
Double blind test – It is used for performing blind test on the network and there are one or two
people involved in the test and it can be used for monitoring the network security and identification of
the incident for development of the response plan.
Black box testing – It is similar with the blind test and no information about the network is
shared with the tester for performing the test and the test is performed by the tester by applying his
own knowledge
White box testing – The targeted user receives all types of information about the targeted
network before starting the test. The information contains the details of the IP address, protocols,
network infrastructure details and the source codes.
Thus for combining the 3 large offices of Fenwick Inc. an unified communication network
design is created and for enabling secure communication between the employees by means of video
call, email, phone call and instant messaging. The users are enabled to collaborate in a dynamic
environment for exchanging the sensitive information securely. For connecting each of the branches
VPN site to site network is configured and all the communication takes place using the network
access server. Since the public internet is used for establishing the connecting with the remote branch
there are different security risk and it is needed to be eliminated for keeping the data or information
secret. Secure communication tunnel is used for transmitting the data and allowing the company to
work together in a secure environment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK SECURITY
Design Specifications and Ethical Considerations
Differentiation of services and classes of applications and
their requirements
In order to ensure the quality of the communication among three offices, it is highly
recommended to use VPN. Fenwick wants to enable communication in this offices through video
conferencing and phone call including email. The VOIP communication is changing the way of
communication by route and transfer voice traffic in IP packets. VPN is mainly used to provide secure
communication by encrypting the traffic. Encryption is an effective way to safe keep data from
unwanted sources. The VPN will only allow communication between the IP addresses which are
previously configured to receive data. Such technology is part of unified communication system. UC is
able to integrate email, video, message and VoIP into one flawless application as required for
Fenwick. Unified Communication is also a cost effective model for on-demand delivery of unified
communications services in the cloud.
The integrated service model utilizes absolute parameters for single flows. However, because of
scalability problems and long delays in the data transfers that take place as a result of applying this
approach, a second approach based on the utilization of relative parameters is more widely practice in
global Internet networks. Such an approach is employed in the differentiated services (DiffServ)
model.
The different type of transportation system has different impact on the network in terms of their
availability and effectiveness. The practice has been adopted by numerous infrastructure. Data
networks are becoming more viable day by day in order to provide supporting telephony and the
converged networks are engaging to make themselves apparent. A successful deployment must
consider all of the required element of VoIP coverage. In the deployment of enterprise infrastructure
appropriate guidelines needs to be set for performing an incremental rollout of IP telephony. There are
certain aspects needs to consider for the development of VoIP. It also a complicated process to
maintain the coverage area. Bypassing long distance toll charges for inter-office calls within the
enterprise is one of the main issue. Replacing cost private branch exchanges is also needs to be
considered. Deploying VOIP cannot be achieved through one stop shopping as it is very critical and
maximizing the solution according to the possible scenario and facets make sense. For instance, one
of the things a PBX can do for you is to multiplex ISDN circuits from a trunk group coming in from the
PSTN. These can be used by data devices inside the enterprise network. Phone conversations are
converted to a stream of IP packets and sent over an Ethernet network. The signals are restricted by
the VPN. In terms of IP Telephony selection, the areas to deliberate are the reliability and quality of
the equipment (and whether it maintain the desired applications), the usability of the services (which
speaks to how readily it will be accepted), and how easily the telephony solution can be progressed
(migrate) to your desired future system—these future application needs should be anticipated now.
Finally, the TCO of the system must be computed to the best degree possible. Important TCO factors
are upgrade costs and personnel costs to configure and maintain the converged network. The
converged network architecture gives us flexibility, better response times for users, control over our
telephony systems, back-end and toll-bypass savings.
Every organization and departments needs and maintain a full-fledged Local area network for
interconnecting computers. The IP network can be operated through different media as fiber, wireless
and copper. The advanced IP phones can also be plugged into the computer network while utilizing
RJ-45 jacks. Not only the hardware, the latest software development and their standardization
acceptance ensured that the real time applications such as video and voice can run alongside data on
a computer network. The unified strategy needs to be planned and executed properly. There are also
other critical components of the Services provides by the IP networks that assist the mass adoption
which enables the tighter and newer integration among the voice, data and video applications. Typical
IP telephony server always not support most of the features of the existing EPABX. The server can
also be con figured to enable new feature out of box like CRM, database integration for allow call
recording, meet ne conference, presence information, single number reach, communication
capabilities and IVR enhancement and unified communication capabilities. Likely. Video conferencing
system all over the worlds works effectively if both side of network provide optimal data connection.
Such approach eliminates the requirement of the dedicated ISDN/PRI lines at each location and also
did not have to pay for per minute charge which is applicable for common communication. There are
mainly four components which is necessary for the IP network. The computer network itself required
NETWORK SECURITY
Design Specifications and Ethical Considerations
Differentiation of services and classes of applications and
their requirements
In order to ensure the quality of the communication among three offices, it is highly
recommended to use VPN. Fenwick wants to enable communication in this offices through video
conferencing and phone call including email. The VOIP communication is changing the way of
communication by route and transfer voice traffic in IP packets. VPN is mainly used to provide secure
communication by encrypting the traffic. Encryption is an effective way to safe keep data from
unwanted sources. The VPN will only allow communication between the IP addresses which are
previously configured to receive data. Such technology is part of unified communication system. UC is
able to integrate email, video, message and VoIP into one flawless application as required for
Fenwick. Unified Communication is also a cost effective model for on-demand delivery of unified
communications services in the cloud.
The integrated service model utilizes absolute parameters for single flows. However, because of
scalability problems and long delays in the data transfers that take place as a result of applying this
approach, a second approach based on the utilization of relative parameters is more widely practice in
global Internet networks. Such an approach is employed in the differentiated services (DiffServ)
model.
The different type of transportation system has different impact on the network in terms of their
availability and effectiveness. The practice has been adopted by numerous infrastructure. Data
networks are becoming more viable day by day in order to provide supporting telephony and the
converged networks are engaging to make themselves apparent. A successful deployment must
consider all of the required element of VoIP coverage. In the deployment of enterprise infrastructure
appropriate guidelines needs to be set for performing an incremental rollout of IP telephony. There are
certain aspects needs to consider for the development of VoIP. It also a complicated process to
maintain the coverage area. Bypassing long distance toll charges for inter-office calls within the
enterprise is one of the main issue. Replacing cost private branch exchanges is also needs to be
considered. Deploying VOIP cannot be achieved through one stop shopping as it is very critical and
maximizing the solution according to the possible scenario and facets make sense. For instance, one
of the things a PBX can do for you is to multiplex ISDN circuits from a trunk group coming in from the
PSTN. These can be used by data devices inside the enterprise network. Phone conversations are
converted to a stream of IP packets and sent over an Ethernet network. The signals are restricted by
the VPN. In terms of IP Telephony selection, the areas to deliberate are the reliability and quality of
the equipment (and whether it maintain the desired applications), the usability of the services (which
speaks to how readily it will be accepted), and how easily the telephony solution can be progressed
(migrate) to your desired future system—these future application needs should be anticipated now.
Finally, the TCO of the system must be computed to the best degree possible. Important TCO factors
are upgrade costs and personnel costs to configure and maintain the converged network. The
converged network architecture gives us flexibility, better response times for users, control over our
telephony systems, back-end and toll-bypass savings.
Every organization and departments needs and maintain a full-fledged Local area network for
interconnecting computers. The IP network can be operated through different media as fiber, wireless
and copper. The advanced IP phones can also be plugged into the computer network while utilizing
RJ-45 jacks. Not only the hardware, the latest software development and their standardization
acceptance ensured that the real time applications such as video and voice can run alongside data on
a computer network. The unified strategy needs to be planned and executed properly. There are also
other critical components of the Services provides by the IP networks that assist the mass adoption
which enables the tighter and newer integration among the voice, data and video applications. Typical
IP telephony server always not support most of the features of the existing EPABX. The server can
also be con figured to enable new feature out of box like CRM, database integration for allow call
recording, meet ne conference, presence information, single number reach, communication
capabilities and IVR enhancement and unified communication capabilities. Likely. Video conferencing
system all over the worlds works effectively if both side of network provide optimal data connection.
Such approach eliminates the requirement of the dedicated ISDN/PRI lines at each location and also
did not have to pay for per minute charge which is applicable for common communication. There are
mainly four components which is necessary for the IP network. The computer network itself required

8
NETWORK SECURITY
all the passive and active components to build VoIP and video over IP systems. The different type of
transportation system has different impact on the network in terms of their availability and
effectiveness. The practice has been adopted by numerous infrastructure. Data networks are
becoming more viable day by day in order to provide supporting telephony and the converged
networks are engaging to make themselves apparent. A successful deployment must consider all of
the required element of VoIP coverage. In the deployment of enterprise infrastructure appropriate
guidelines needs to be set for performing an incremental rollout of IP telephony. There are certain
aspects needs to consider for the development of VoIP. It also a complicated process to maintain the
coverage area.
The best of class unified communications platforms provide advanced functionality and features
which could differ slightly from the competitors. The system can be designed to operate as end to end
solution for all of the enterprise communication. The system must be modified according to the
business requirement. Some of the requirements are listed below:
Native integration for your existing apps (Microsoft Office 365, Twitter, Drive, Salesforce)
Integrated directory
Speech-to-text conversions
Unified messaging for emails, calls, texts, voicemails, and chat
Unified messaging for emails, calls, texts, voicemails, and chat
Presence to communicate internal availability to users
Presence to communicate internal availability to users
Interoperability between analogue and VoIP phones to support hybrid implementations
Every department of the company will, be able to communicate with the other department
flawlessly through the unified communication system .The system will enable numerous feature.
Some of the other features are also listed below:
BYOD support
Self-service features for call routing, call management, and other advanced functions
Multisite administration from a single management portal
Multisite administration from a single management portal
Access to monitoring and reporting, especially for organizations with a high call volume or
contact centre
Access to monitoring and reporting, especially for organizations with a high call volume or
contact centre.
Additionally, the utilization of owned session border controller device could ensure higher quality
security between vendors. These pieces of equipment act as a conduct for voice communications,
creating a barrier among the public and private network by offering IP-based signalling translation. IT
professionals are mostly familiar with the five nines when it times to creating technical business needs
for high demand environments. Without access to phones and data, your organization’s ability to
communicate internally and externally is limited, which can result in devastating damage to customer
relationships and loss of revenue. Some Unified Communications platforms only scale to 500 or 2,000
NETWORK SECURITY
all the passive and active components to build VoIP and video over IP systems. The different type of
transportation system has different impact on the network in terms of their availability and
effectiveness. The practice has been adopted by numerous infrastructure. Data networks are
becoming more viable day by day in order to provide supporting telephony and the converged
networks are engaging to make themselves apparent. A successful deployment must consider all of
the required element of VoIP coverage. In the deployment of enterprise infrastructure appropriate
guidelines needs to be set for performing an incremental rollout of IP telephony. There are certain
aspects needs to consider for the development of VoIP. It also a complicated process to maintain the
coverage area.
The best of class unified communications platforms provide advanced functionality and features
which could differ slightly from the competitors. The system can be designed to operate as end to end
solution for all of the enterprise communication. The system must be modified according to the
business requirement. Some of the requirements are listed below:
Native integration for your existing apps (Microsoft Office 365, Twitter, Drive, Salesforce)
Integrated directory
Speech-to-text conversions
Unified messaging for emails, calls, texts, voicemails, and chat
Unified messaging for emails, calls, texts, voicemails, and chat
Presence to communicate internal availability to users
Presence to communicate internal availability to users
Interoperability between analogue and VoIP phones to support hybrid implementations
Every department of the company will, be able to communicate with the other department
flawlessly through the unified communication system .The system will enable numerous feature.
Some of the other features are also listed below:
BYOD support
Self-service features for call routing, call management, and other advanced functions
Multisite administration from a single management portal
Multisite administration from a single management portal
Access to monitoring and reporting, especially for organizations with a high call volume or
contact centre
Access to monitoring and reporting, especially for organizations with a high call volume or
contact centre.
Additionally, the utilization of owned session border controller device could ensure higher quality
security between vendors. These pieces of equipment act as a conduct for voice communications,
creating a barrier among the public and private network by offering IP-based signalling translation. IT
professionals are mostly familiar with the five nines when it times to creating technical business needs
for high demand environments. Without access to phones and data, your organization’s ability to
communicate internally and externally is limited, which can result in devastating damage to customer
relationships and loss of revenue. Some Unified Communications platforms only scale to 500 or 2,000
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK SECURITY
users. If you have a lot of users or aggressive growth goals, ensure that your solution can support
cost-effective scaling to more users and sites.
Security threats:
Unified communication is becoming the modern standards for communication for business
context. However it has several security threats that not only need to be identified but needs to be
mitigated as well.
The common threats related to the unified communication are:
Toll fraud attacks: here the hackers exploit the communication network and get access to the
media access control (MAC) of the PC. It is then considered for registering the soft phones to
the IPBX. Soft phones considers media access control of PC for the registration. Once the
registration is completed it allows to execute international call through the UC network.
Reconnaissance attacks: it refers to call hijacking or eavesdropping on any existing call.
Through this process hackers execute malicious code into the network and then the hacker
controls what the listener would hear. Hence the actual and desired message is not
communicated to the listener
eavesdropping
call hijacks
Solution of the security issues:
typically solution to unified communication threats include IPPBX, voice mail, core network
solution, conference calls, wireless mobile devices, video conferencing solutions and the contact
centre. Hence the solution to the security issues in the UC network cam be broadly classified into two
categories:
UC infrastructure security
UC application security
UC infrastructure security encompasses physical and network security. In order to secure the
UC solution it is required to ensure a secured network and telephony setup and that has to be ensure
at the same time.
Physical security embraces batched and restricted access and that is made mandatory for the
employees. It is also need to be made sure that no third parties or vendors have the access to the
data centre and no one should be allowed to enter inside the data centre. Network security typically
comprises arrangement of security for effectively securing the switching layer, routing layer,
peripherals and wireless networks. Firewalls and an intrusion prevention system are also effective
solutions that is worth considering for peripheral security. In order to secure network security
remotely SSL or IPsec VPN might also be considered for achieving the mobile solution.
Securing the UC application is another important step for securing the UC network and
communication through the network. The basic yet most effective solution is to secure the base OS.
Other important components such as host intrusion prevention system, internal firewalls, network
system need to be secured as well for ensuring secured access to the network. UC application
security is typically achieved through enhancing security for the voice mail application, contact centre
application and meeting places.
Monitoring
The system also needs to be maintained regularly in order to avoid any vulnerability. Intrusion
detection process needs to be adopt which refers to monitoring network and hosts activities. It is used
in computer security as it analyses the network activities and detect intrusion in system. The main
reason of adopting such process is it assist to alert system administration and IT professionals with in
the organization about any potential threat or weakness. The intrusion system also allow to prevent
such threat which act as an active solution.
IDS:
NETWORK SECURITY
users. If you have a lot of users or aggressive growth goals, ensure that your solution can support
cost-effective scaling to more users and sites.
Security threats:
Unified communication is becoming the modern standards for communication for business
context. However it has several security threats that not only need to be identified but needs to be
mitigated as well.
The common threats related to the unified communication are:
Toll fraud attacks: here the hackers exploit the communication network and get access to the
media access control (MAC) of the PC. It is then considered for registering the soft phones to
the IPBX. Soft phones considers media access control of PC for the registration. Once the
registration is completed it allows to execute international call through the UC network.
Reconnaissance attacks: it refers to call hijacking or eavesdropping on any existing call.
Through this process hackers execute malicious code into the network and then the hacker
controls what the listener would hear. Hence the actual and desired message is not
communicated to the listener
eavesdropping
call hijacks
Solution of the security issues:
typically solution to unified communication threats include IPPBX, voice mail, core network
solution, conference calls, wireless mobile devices, video conferencing solutions and the contact
centre. Hence the solution to the security issues in the UC network cam be broadly classified into two
categories:
UC infrastructure security
UC application security
UC infrastructure security encompasses physical and network security. In order to secure the
UC solution it is required to ensure a secured network and telephony setup and that has to be ensure
at the same time.
Physical security embraces batched and restricted access and that is made mandatory for the
employees. It is also need to be made sure that no third parties or vendors have the access to the
data centre and no one should be allowed to enter inside the data centre. Network security typically
comprises arrangement of security for effectively securing the switching layer, routing layer,
peripherals and wireless networks. Firewalls and an intrusion prevention system are also effective
solutions that is worth considering for peripheral security. In order to secure network security
remotely SSL or IPsec VPN might also be considered for achieving the mobile solution.
Securing the UC application is another important step for securing the UC network and
communication through the network. The basic yet most effective solution is to secure the base OS.
Other important components such as host intrusion prevention system, internal firewalls, network
system need to be secured as well for ensuring secured access to the network. UC application
security is typically achieved through enhancing security for the voice mail application, contact centre
application and meeting places.
Monitoring
The system also needs to be maintained regularly in order to avoid any vulnerability. Intrusion
detection process needs to be adopt which refers to monitoring network and hosts activities. It is used
in computer security as it analyses the network activities and detect intrusion in system. The main
reason of adopting such process is it assist to alert system administration and IT professionals with in
the organization about any potential threat or weakness. The intrusion system also allow to prevent
such threat which act as an active solution.
IDS:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK SECURITY
The Intrusion detection system is designed to monitor outbound and inbound network activity
which is useful to detect any suspicious action or threat that could attack the network. For instance, if
some third parties is attempting to access the system in order to compromise the network or any
secure data from the organization. It considered as a passive system as its only monitor the system
and alerts the administrators. It cannot prevent the threat from attack. Generally, IDS analyses the
network data and traffic in order to identify any exploits, attacks and probes or other vulnerabilities. It
can respond in many different ways after detecting any threats. For instance, it can display an alert or
paging or logging the event an administrator. Advanced IDS are able to reconfigure the network in
order to reduce the effects of the exploits.
IDS searches for any unusual activity in the network which might be result of a hack, worm or
virus. Such detection method is achieved by searching for known intrusion signature which stores
information about previous captured exploits, virus and worms. IDS also analyse the traffic activity
and alert the administrator if something unusual activity occurs. The only drawback is it can only
detect known threats which are stored in the intrusion signature.
The IDS solution comes in various form. Network administrator need to configure both
hardware and software at different location of the network. They also needs to look out for any alert
initiated by the IDS and took action accordingly.
However, the organization cannot be totally rely on the IDS as it only assist to detect any
potential theat. Here, IPS comes in action which is considered as next level security technology. IPS
has the capability to provide security at all level of system which makes it superior to others. It also
provides set of rules and guidelines for nnetwork traffic alsong with alerting system. Where IDS
informs of a potential attack, an IPS makes attempts to stop it. Another huge leap over IDS, is that
IPS has the capability of being able to prevent known intrusion signatures, but also some unknown
attacks due to its database of generic attack behaviours. Thought of as a combination of IDS and an
application layer firewall for protection, IPS is generally considered to be the "next generation" of IDS.
Manage VoIP
The success of the VOIP is mostly depends on the end-users. It offers high quality service as
expected by the end-user. Due to the high expectation here is concern about relying on a delay-
tolerant data infrastructure to carry delay-sensitive voice services. It is noticed that before auditioning
voice, data networks becomes complicated because of the new applications, multitude of
technologies and numerous combination of server and systems. It also increase the complexity for
managing the performance. The system must be built for delay-tolerant applications as packet loss in
the time of data applications transportation over a same system. However, IP voice communication
works on real time which can be achieved flawlessly on a dedicated analogue network. However,
when the voice becomes subject to the lows and high of a constant changing data network
environment.
Characteristics Recommendation Definition
Packet loss Dropped packets: Voice
typically uses the RIP protocol
running over UDP which
doesn't retransmit lost packets,
meaning portions of the
conversation can be lost.
Below I% and 13%
jitter Jitter is the variance in delay.
When some voice packets
arrive with little of Standards
and delay followed by
additional voice packets with
greater delay, pans of the
conversation on the receiving
end will become unman.
< 40ms
Delay/latency The time it takes for data to get
from point A to point B on the
network. VolP is sensitive to
delay because human
conversation occurs in real
Below 150ms.
NETWORK SECURITY
The Intrusion detection system is designed to monitor outbound and inbound network activity
which is useful to detect any suspicious action or threat that could attack the network. For instance, if
some third parties is attempting to access the system in order to compromise the network or any
secure data from the organization. It considered as a passive system as its only monitor the system
and alerts the administrators. It cannot prevent the threat from attack. Generally, IDS analyses the
network data and traffic in order to identify any exploits, attacks and probes or other vulnerabilities. It
can respond in many different ways after detecting any threats. For instance, it can display an alert or
paging or logging the event an administrator. Advanced IDS are able to reconfigure the network in
order to reduce the effects of the exploits.
IDS searches for any unusual activity in the network which might be result of a hack, worm or
virus. Such detection method is achieved by searching for known intrusion signature which stores
information about previous captured exploits, virus and worms. IDS also analyse the traffic activity
and alert the administrator if something unusual activity occurs. The only drawback is it can only
detect known threats which are stored in the intrusion signature.
The IDS solution comes in various form. Network administrator need to configure both
hardware and software at different location of the network. They also needs to look out for any alert
initiated by the IDS and took action accordingly.
However, the organization cannot be totally rely on the IDS as it only assist to detect any
potential theat. Here, IPS comes in action which is considered as next level security technology. IPS
has the capability to provide security at all level of system which makes it superior to others. It also
provides set of rules and guidelines for nnetwork traffic alsong with alerting system. Where IDS
informs of a potential attack, an IPS makes attempts to stop it. Another huge leap over IDS, is that
IPS has the capability of being able to prevent known intrusion signatures, but also some unknown
attacks due to its database of generic attack behaviours. Thought of as a combination of IDS and an
application layer firewall for protection, IPS is generally considered to be the "next generation" of IDS.
Manage VoIP
The success of the VOIP is mostly depends on the end-users. It offers high quality service as
expected by the end-user. Due to the high expectation here is concern about relying on a delay-
tolerant data infrastructure to carry delay-sensitive voice services. It is noticed that before auditioning
voice, data networks becomes complicated because of the new applications, multitude of
technologies and numerous combination of server and systems. It also increase the complexity for
managing the performance. The system must be built for delay-tolerant applications as packet loss in
the time of data applications transportation over a same system. However, IP voice communication
works on real time which can be achieved flawlessly on a dedicated analogue network. However,
when the voice becomes subject to the lows and high of a constant changing data network
environment.
Characteristics Recommendation Definition
Packet loss Dropped packets: Voice
typically uses the RIP protocol
running over UDP which
doesn't retransmit lost packets,
meaning portions of the
conversation can be lost.
Below I% and 13%
jitter Jitter is the variance in delay.
When some voice packets
arrive with little of Standards
and delay followed by
additional voice packets with
greater delay, pans of the
conversation on the receiving
end will become unman.
< 40ms
Delay/latency The time it takes for data to get
from point A to point B on the
network. VolP is sensitive to
delay because human
conversation occurs in real
Below 150ms.

11
NETWORK SECURITY
time.
Additionally, managing VOIP required focus on some specific aspects which are listed below:
On-going Management of the converged network to keep performance optimized over the
long-term.
Post-deployment Impact Analysis of both data and voice applications to confirm well-running
network services.
Project planning to ensure network readiness and a well-thought-out process which will stack
the odds in favour of a smooth deployment.
Pre-deployment: Assessment to baseline application performance and network usage, and
discover latent network issues that would be magnified upon voice implementation.
Remote User management
Remote IT infrastructure management services and IP telephony management services are
prerequisites for enabling communication. Remote user management allows remote users to
communicate with the other offices over the internet. The only drawback of the remote connection is
options like call-back is not available. Some security challenges also may occur as the connection
allow each local network to be validated for the network access while enabling virtual connection.
Every organization and departments needs and maintain a full-fledged Local area network for
interconnecting computers. The IP network can be operated through different media as fiber, wireless
and copper. The advanced IP phones can also be plugged into the computer network while utilizing
RJ-45 jacks. Not only the hardware, the latest software development and their standardization
acceptance ensured that the real time applications such as video and voice can run alongside data on
a computer network. The unified strategy needs to be planned and executed properly. There are also
other critical components of the Services provides by the IP networks that assist the mass adoption
which enables the tighter and newer integration among the voice, data and video applications. Typical
IP telephony server always not support most of the features of the existing EPABX. The server can
also be con figured to enable new feature out of box like CRM, database integration for allow call
recording, meet ne conference, presence information, single number reach, communication
capabilities and IVR enhancement and unified communication capabilities.
Ethical Consideration:
A fully secure unified communications requires significant changes in terms of the
organization and IT environment. Some ethical aspects needs to be consider while utilizing such
unified communication system. Establishment of a safe-environment throughout the organization is
necessary for ensuring that the digital workplace stay secure. HR and IT departments must educate
the potential users of such technology abot the guidelines ad workplace policies. Employees
accessing Unified Communications remotely, or from their own devices can pose security risks if they
do not comply with company security policies.
The utilization of system examination to make authoritative and personal changes, moreover
presents risks for the academic field of interpersonal organization research about in light of the fact
that information of the risks of rounding out a system overview will lead association individuals to
stand up to taking action, or to reply in self-serving ways. The responses makes investigate more
troublesome, and the second introduces threats to validity.
The term ethics is characterized as "a set of good standards" or "the standards of direct
overseeing an individual or a group." Since the beginning of civilization, the investigation of ethics and
their effect has entranced civilization. But, what do ethics have to do with data frameworks?
NETWORK SECURITY
time.
Additionally, managing VOIP required focus on some specific aspects which are listed below:
On-going Management of the converged network to keep performance optimized over the
long-term.
Post-deployment Impact Analysis of both data and voice applications to confirm well-running
network services.
Project planning to ensure network readiness and a well-thought-out process which will stack
the odds in favour of a smooth deployment.
Pre-deployment: Assessment to baseline application performance and network usage, and
discover latent network issues that would be magnified upon voice implementation.
Remote User management
Remote IT infrastructure management services and IP telephony management services are
prerequisites for enabling communication. Remote user management allows remote users to
communicate with the other offices over the internet. The only drawback of the remote connection is
options like call-back is not available. Some security challenges also may occur as the connection
allow each local network to be validated for the network access while enabling virtual connection.
Every organization and departments needs and maintain a full-fledged Local area network for
interconnecting computers. The IP network can be operated through different media as fiber, wireless
and copper. The advanced IP phones can also be plugged into the computer network while utilizing
RJ-45 jacks. Not only the hardware, the latest software development and their standardization
acceptance ensured that the real time applications such as video and voice can run alongside data on
a computer network. The unified strategy needs to be planned and executed properly. There are also
other critical components of the Services provides by the IP networks that assist the mass adoption
which enables the tighter and newer integration among the voice, data and video applications. Typical
IP telephony server always not support most of the features of the existing EPABX. The server can
also be con figured to enable new feature out of box like CRM, database integration for allow call
recording, meet ne conference, presence information, single number reach, communication
capabilities and IVR enhancement and unified communication capabilities.
Ethical Consideration:
A fully secure unified communications requires significant changes in terms of the
organization and IT environment. Some ethical aspects needs to be consider while utilizing such
unified communication system. Establishment of a safe-environment throughout the organization is
necessary for ensuring that the digital workplace stay secure. HR and IT departments must educate
the potential users of such technology abot the guidelines ad workplace policies. Employees
accessing Unified Communications remotely, or from their own devices can pose security risks if they
do not comply with company security policies.
The utilization of system examination to make authoritative and personal changes, moreover
presents risks for the academic field of interpersonal organization research about in light of the fact
that information of the risks of rounding out a system overview will lead association individuals to
stand up to taking action, or to reply in self-serving ways. The responses makes investigate more
troublesome, and the second introduces threats to validity.
The term ethics is characterized as "a set of good standards" or "the standards of direct
overseeing an individual or a group." Since the beginning of civilization, the investigation of ethics and
their effect has entranced civilization. But, what do ethics have to do with data frameworks?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





