CSI3207/CSI5212 - Network Security: Enhancing Lucent Pharma's Posture
VerifiedAdded on 2023/06/11
|19
|3735
|380
Report
AI Summary
This report delves into the network security fundamentals, specifically focusing on enhancing the security posture of Lucent Pharma. It identifies vulnerabilities such as missing patches, default passwords, misconfigured firewalls, and USB flash drive threats. The report explains the purpose and placement of security devices like firewalls, IDS/IPS, honeypots, and routers within the network. It emphasizes the necessity of network segregation using VLANs for improved security and broadcast control. Furthermore, it outlines firewall rules and policies essential for controlling network traffic and enforcing security strategies. The development of IDS/IPS policies for monitoring and analyzing network activity is also discussed, along with specific security policies tailored for Lucent Pharma's network. Finally, the assignment proposes a secured network design to address the identified vulnerabilities and enhance the overall security infrastructure.

Network Security Fundamentals
Name of the Student
Name of the University
Author’s Note
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Vulnerabilities in the network................................................................................................3
2. Explanation of the security devices........................................................................................4
3. Explanation for the need of placing the security devices.......................................................5
4. Requirement of network segregation.....................................................................................6
5. Firewall rules and policies.....................................................................................................7
6. Developing IDS/IPS policies.................................................................................................9
7. Security policies for Lucent Pharma network......................................................................10
8. Designing proposed secured network design.......................................................................11
Part 2........................................................................................................................................12
Bibliography.............................................................................................................................16
1. Vulnerabilities in the network................................................................................................3
2. Explanation of the security devices........................................................................................4
3. Explanation for the need of placing the security devices.......................................................5
4. Requirement of network segregation.....................................................................................6
5. Firewall rules and policies.....................................................................................................7
6. Developing IDS/IPS policies.................................................................................................9
7. Security policies for Lucent Pharma network......................................................................10
8. Designing proposed secured network design.......................................................................11
Part 2........................................................................................................................................12
Bibliography.............................................................................................................................16

1. Vulnerabilities in the network
The real vulnerabilities exist inside the present system topology of "Lucent Pharma"
are illustrated below:
Missing patches: Missing patches is considered as one of the real vulnerabilities that
is available inside the present system topology of "Lucent Pharma". It is distinguished that
missing patches largely allows a verified indirect access way and summon insight into the
web condition for the rouge insider. Hence, it very important to be very careful while
utilizing patches. It is recognized that it is important to use proper policy procedures for
organizing security by updating the OS.
Default passwords: It is found that passwords are not considered inside the network
vulnerability but it is recognized because huge numbers of the content management
framework and web applications utilizes feeble passwords requires SQL infusion. This issue
can be settled by testing the passwords consistently to ensure that the passwords that are used
are appropriate and secure.
Misconfigured firewall: The misconfigured firewall discharge is one of the real
vulnerabilities that is available inside the system of the organization. It is recognized that
misconfiguration of firewall discharge can be one of the genuine design related shortcoming
that for the most part helps in permitting unapproved web condition. With a specific end goal
to moderate this issue, it is very essential to use suitable security approaches.
USB flash drives: The threat that is related with USB flash drives can make number
of system vulnerabilities and in addition issues. It is distinguished that USB drivers are a
standout amongst the most well-known courses through which the whole system can be
The real vulnerabilities exist inside the present system topology of "Lucent Pharma"
are illustrated below:
Missing patches: Missing patches is considered as one of the real vulnerabilities that
is available inside the present system topology of "Lucent Pharma". It is distinguished that
missing patches largely allows a verified indirect access way and summon insight into the
web condition for the rouge insider. Hence, it very important to be very careful while
utilizing patches. It is recognized that it is important to use proper policy procedures for
organizing security by updating the OS.
Default passwords: It is found that passwords are not considered inside the network
vulnerability but it is recognized because huge numbers of the content management
framework and web applications utilizes feeble passwords requires SQL infusion. This issue
can be settled by testing the passwords consistently to ensure that the passwords that are used
are appropriate and secure.
Misconfigured firewall: The misconfigured firewall discharge is one of the real
vulnerabilities that is available inside the system of the organization. It is recognized that
misconfiguration of firewall discharge can be one of the genuine design related shortcoming
that for the most part helps in permitting unapproved web condition. With a specific end goal
to moderate this issue, it is very essential to use suitable security approaches.
USB flash drives: The threat that is related with USB flash drives can make number
of system vulnerabilities and in addition issues. It is distinguished that USB drivers are a
standout amongst the most well-known courses through which the whole system can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

tainted from or inside the firewall. With a specific end goal to moderate this issue, it is very
vital to use appropriate security related strategies in setting to individual stockpiling gadgets.
2. Explanation of the security devices
. The security devices that are placed within the network of the organization are
illustrated below:
Firewall: Firewall is considered as one of the device of system security that f helps
with checking both active and ingoing movement that causes in choosing that assists in
deciding whether to permit or block the traffic as per the permit security rules. Firewall is
considered as one of the principal line of barrier inside the system security. They for the most
part help with making appropriate impediment between controlled and in addition secured
inside system, which largely can trust and untrusted outside system including the web.
IDS/IPS: Intrusion discovery is considered as one of the methodology that helps with
checking the whole event that happens inside the whole system by deciding the indications of
different sorts of incident violations and assists in setting to different security arrangements.
Nonetheless, IPS is one of the system that aides in playing out the whole interruption
discovery that for the most part helps in blocking the occurrence that is recognized. It is
discovered that this safety efforts that are present as IDS and IPS end up one of the piece of
the system for distinguishing and halting distinctive kinds of potential occurrences.
Honeypot: Honeypot is one of the PC framework that is for the most part set for
going about as one of the imitation keeping in mind the end goal to bait different
cybercriminals and for identifying and diverting different examination endeavours with a
specific end goal to accomplish unapproved access to different data framework. It for the
vital to use appropriate security related strategies in setting to individual stockpiling gadgets.
2. Explanation of the security devices
. The security devices that are placed within the network of the organization are
illustrated below:
Firewall: Firewall is considered as one of the device of system security that f helps
with checking both active and ingoing movement that causes in choosing that assists in
deciding whether to permit or block the traffic as per the permit security rules. Firewall is
considered as one of the principal line of barrier inside the system security. They for the most
part help with making appropriate impediment between controlled and in addition secured
inside system, which largely can trust and untrusted outside system including the web.
IDS/IPS: Intrusion discovery is considered as one of the methodology that helps with
checking the whole event that happens inside the whole system by deciding the indications of
different sorts of incident violations and assists in setting to different security arrangements.
Nonetheless, IPS is one of the system that aides in playing out the whole interruption
discovery that for the most part helps in blocking the occurrence that is recognized. It is
discovered that this safety efforts that are present as IDS and IPS end up one of the piece of
the system for distinguishing and halting distinctive kinds of potential occurrences.
Honeypot: Honeypot is one of the PC framework that is for the most part set for
going about as one of the imitation keeping in mind the end goal to bait different
cybercriminals and for identifying and diverting different examination endeavours with a
specific end goal to accomplish unapproved access to different data framework. It for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

most part traded off different applications, information and PCs that for the most part helps in
recreating conduct of the genuine framework.
Switch/Routers: Router aides in sending different information related packets inside
the system. They are for the most part situated inside the gateways for interfacing different
systems and devices. Switches use headers with a specific end goal to forward tables for
deciding appropriate way to forward the whole packet. In addition to this, switch is
characterized as of the gadget that aides in separating and also sending packets between LAN
sections. It is distinguished that switches for the most part works as the information connect
layer and hence helps with supporting the parcel convention.
3. Explanation for the need of placing the security devices
The devices like Firewall, IDS, Honeypot, and Routers are put inside the chose area
because of the reasons that are illustrated below:
Firewall: The firewall is used inside the system with a specific end goal to keep
unapproved access various private systems. It is recognized that system firewalls largely help
with in preventing unapproved clients of the web from getting access that are private and
associated with intranets. Every messages that enters and the intranet needs to go through the
firewall and the then the firewall inspects every one of the messages appropriately a obstructs
those messages that do not by meet the security related criteria.
IDS/IPS: Network interruption discovery framework is put inside the system with the
goal that they can have the capacity to screen the conduct of the framework and can have the
capacity to give caution on different sorts of conceivably pernicious system activity. It is
discovered that the two IDS and IPS are largely used so the side effects of movement and
recreating conduct of the genuine framework.
Switch/Routers: Router aides in sending different information related packets inside
the system. They are for the most part situated inside the gateways for interfacing different
systems and devices. Switches use headers with a specific end goal to forward tables for
deciding appropriate way to forward the whole packet. In addition to this, switch is
characterized as of the gadget that aides in separating and also sending packets between LAN
sections. It is distinguished that switches for the most part works as the information connect
layer and hence helps with supporting the parcel convention.
3. Explanation for the need of placing the security devices
The devices like Firewall, IDS, Honeypot, and Routers are put inside the chose area
because of the reasons that are illustrated below:
Firewall: The firewall is used inside the system with a specific end goal to keep
unapproved access various private systems. It is recognized that system firewalls largely help
with in preventing unapproved clients of the web from getting access that are private and
associated with intranets. Every messages that enters and the intranet needs to go through the
firewall and the then the firewall inspects every one of the messages appropriately a obstructs
those messages that do not by meet the security related criteria.
IDS/IPS: Network interruption discovery framework is put inside the system with the
goal that they can have the capacity to screen the conduct of the framework and can have the
capacity to give caution on different sorts of conceivably pernicious system activity. It is
discovered that the two IDS and IPS are largely used so the side effects of movement and

additionally interruptions can without much of a stretch be distinguished so the security
related vulnerabilities and difficulties could be settled in the underlying stage. IPS/IDS help
in breaking down malicious code that can make security challenges for the system.
Honeypot: This is considered as one of the vulnerable and disconnected framework
that is kept inside the system to think about the different strategies and procedures of attacks
and for shielding the genuine framework from various kinds of attacks. Honeypots is
considered as a standout amongst the best security of system that for the most part can helps
in copying vulnerabilities, tolerating and in addition reacting to different tests that is set by
different aggressors.
Switches/Routers: Routers or switches used between different type of networks so as
to interface the system with the assistance of web. It helps in checking both the goal and
additionally source IP address that is related with every packet and aides in steering the
packet to another switch. It is discovered that switches help in giving ISP that further aides in
assigning switch IP address, which is one of the general population IP address.
4. Requirement of network segregation
Lucent Pharma requires network segregation into different areas which reflects that
VLANs are needed to be used. VLANs are primarily characterized as one of the system PC
that is chiefly situated inside a similar region. It is discovered that VLANs are for the most
part used inside the system keeping to make the whole system administration framework
significantly less demanding in number of ways. It is recognized that VLAN are ordered into
number communicate spaces and also number of intelligent subsets for making the whole
system administration framework less demanding. One of the best-preferred standpoints of
VLANs is that it helps with setting up particular domain segment for single hardware that is
related vulnerabilities and difficulties could be settled in the underlying stage. IPS/IDS help
in breaking down malicious code that can make security challenges for the system.
Honeypot: This is considered as one of the vulnerable and disconnected framework
that is kept inside the system to think about the different strategies and procedures of attacks
and for shielding the genuine framework from various kinds of attacks. Honeypots is
considered as a standout amongst the best security of system that for the most part can helps
in copying vulnerabilities, tolerating and in addition reacting to different tests that is set by
different aggressors.
Switches/Routers: Routers or switches used between different type of networks so as
to interface the system with the assistance of web. It helps in checking both the goal and
additionally source IP address that is related with every packet and aides in steering the
packet to another switch. It is discovered that switches help in giving ISP that further aides in
assigning switch IP address, which is one of the general population IP address.
4. Requirement of network segregation
Lucent Pharma requires network segregation into different areas which reflects that
VLANs are needed to be used. VLANs are primarily characterized as one of the system PC
that is chiefly situated inside a similar region. It is discovered that VLANs are for the most
part used inside the system keeping to make the whole system administration framework
significantly less demanding in number of ways. It is recognized that VLAN are ordered into
number communicate spaces and also number of intelligent subsets for making the whole
system administration framework less demanding. One of the best-preferred standpoints of
VLANs is that it helps with setting up particular domain segment for single hardware that is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

identified with the switch. It is recognized that VLANs gives number of advantages that are
as follows:
Security: VLANs helps in giving enhanced security of the network. It is found that
VLAN organize condition helps in controlling each port and in addition client. A noxious
client can by and large attachment workstation for exchanging system.
Broadcast control: Broadcast is considered as one of the ordinary capacity of the
system. It is distinguished that there are number of conventions and applications that for the
most part rely upon the correspondence communicate to capacities fittingly. It is
distinguished that usage of VLANs inside the system by and large helps with decreasing the
communicate movement as every one of the communicate are by and large sent to the
significant and additionally particular VLAN as it were.
Physical layer transparency: VLANs are very transparent on the physical topology
and medium over which the whole system is associated.
Cost: It is recognized that portioning huge VLAN helps in making appropriate steered
connect with the switches as switches are for the most part very costlier when contrasted with
the switches.
It is distinguished that VLANs aides in limiting the need switch arrangement on the
system that for the most part have communicated movement. Notwithstanding this the control
of the communicate areas for the most part helps with lessening the activity.
5. Firewall rules and policies
Firewall is considered as one of the device that is mostly intended for controlling the
stream of the web convention with a specific end goal to frame appropriate system or
as follows:
Security: VLANs helps in giving enhanced security of the network. It is found that
VLAN organize condition helps in controlling each port and in addition client. A noxious
client can by and large attachment workstation for exchanging system.
Broadcast control: Broadcast is considered as one of the ordinary capacity of the
system. It is distinguished that there are number of conventions and applications that for the
most part rely upon the correspondence communicate to capacities fittingly. It is
distinguished that usage of VLANs inside the system by and large helps with decreasing the
communicate movement as every one of the communicate are by and large sent to the
significant and additionally particular VLAN as it were.
Physical layer transparency: VLANs are very transparent on the physical topology
and medium over which the whole system is associated.
Cost: It is recognized that portioning huge VLAN helps in making appropriate steered
connect with the switches as switches are for the most part very costlier when contrasted with
the switches.
It is distinguished that VLANs aides in limiting the need switch arrangement on the
system that for the most part have communicated movement. Notwithstanding this the control
of the communicate areas for the most part helps with lessening the activity.
5. Firewall rules and policies
Firewall is considered as one of the device that is mostly intended for controlling the
stream of the web convention with a specific end goal to frame appropriate system or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

electronic gear. The system activity and additionally to enforce strategies that is reliant on
directions contained inside the rule set of the firewall. The arrangement that is predominantly
planned is useful in giving appropriate direction when the firewall is required. The firewall
arrangement that is used is very useful in bringing issues to light on the importance of
legitimately designed firewall. The firewall strategies that must be executed by the system
head are recorded beneath:
Network connection: All the remote association of the association organize must go
through the firewall of the system. Furthermore, all the system associations that for the most
part enters high security organize by and large goes through the system firewall.
Dedicated functionality: The system firewall must be used for securing the system of
the association by running on single reason gadgets. Every firewall arrange must have fitting
arrangement of tenets that must be particular to its motivation according to the IT’S standard
of system firewall.
System firewall change control: It is distinguished that system firewall design tenets
ought not be changed unless appropriate authorization is given by the data security officer
and also organize supervisor. It is discovered that any of the of the progressions to different
administrations and in addition leads should be legitimately archived.
Regular auditing: Proper review on the system firewall must be done appropriately.
These reviews must incorporate the best possible execution vulnerability scanning to the ITS
vulnerability assessment policy.
System firewall physical security: The system firewall of the organization is situated
on the ITS server farm and it must be available by the parts and duties that for the most part
gives access to the system firewall that is characterized inside the whole ITS entrance control
approach. It is distinguished this protected space by and large has appropriate security related
directions contained inside the rule set of the firewall. The arrangement that is predominantly
planned is useful in giving appropriate direction when the firewall is required. The firewall
arrangement that is used is very useful in bringing issues to light on the importance of
legitimately designed firewall. The firewall strategies that must be executed by the system
head are recorded beneath:
Network connection: All the remote association of the association organize must go
through the firewall of the system. Furthermore, all the system associations that for the most
part enters high security organize by and large goes through the system firewall.
Dedicated functionality: The system firewall must be used for securing the system of
the association by running on single reason gadgets. Every firewall arrange must have fitting
arrangement of tenets that must be particular to its motivation according to the IT’S standard
of system firewall.
System firewall change control: It is distinguished that system firewall design tenets
ought not be changed unless appropriate authorization is given by the data security officer
and also organize supervisor. It is discovered that any of the of the progressions to different
administrations and in addition leads should be legitimately archived.
Regular auditing: Proper review on the system firewall must be done appropriately.
These reviews must incorporate the best possible execution vulnerability scanning to the ITS
vulnerability assessment policy.
System firewall physical security: The system firewall of the organization is situated
on the ITS server farm and it must be available by the parts and duties that for the most part
gives access to the system firewall that is characterized inside the whole ITS entrance control
approach. It is distinguished this protected space by and large has appropriate security related

measures introduced and thusly all the physical access that is for the most part secured will be
for the most part consequently logged. It is distinguished that every one of the guests get to
must aides in securing spaces that is for the most part keep the ITA get to control related
arrangement.
6. Developing IDS/IPS policies
Intrusion detection system are found as one of the framework that helps with
observing and also breaking down the system movement because of different exercises that
for the most part coordinates through known examples of pernicious exercises. It is
recognized that to break down and additionally screen the movement, number of approaches
are required to be executed by the system manager with the goal that the arrangements and
principles are very useful in settling the difficulties of cyber security from the system. The
policies that are needed to be executed include:
1) It is distinguished that the perimeter firewall ought to be set between the router
and also the switch
2) It is discovered that both inbound and in addition outbound of system must be
confined and it must be subject to the framework order as appropriately distinguished by the
method of hazard evaluation
3) It is recognized that framework must hold the confined information that must
be outbound and in addition inbound the whole activity that is limited to that is required for
the business for working all other inbound and additionally outbound movement.
4) Firewall arrangement must be effectively updated according to the new sorts
of vulnerabilities that are for the most part recognized
5) IDS and IPS must be suitably checked for confining the whole information
for the most part consequently logged. It is distinguished that every one of the guests get to
must aides in securing spaces that is for the most part keep the ITA get to control related
arrangement.
6. Developing IDS/IPS policies
Intrusion detection system are found as one of the framework that helps with
observing and also breaking down the system movement because of different exercises that
for the most part coordinates through known examples of pernicious exercises. It is
recognized that to break down and additionally screen the movement, number of approaches
are required to be executed by the system manager with the goal that the arrangements and
principles are very useful in settling the difficulties of cyber security from the system. The
policies that are needed to be executed include:
1) It is distinguished that the perimeter firewall ought to be set between the router
and also the switch
2) It is discovered that both inbound and in addition outbound of system must be
confined and it must be subject to the framework order as appropriately distinguished by the
method of hazard evaluation
3) It is recognized that framework must hold the confined information that must
be outbound and in addition inbound the whole activity that is limited to that is required for
the business for working all other inbound and additionally outbound movement.
4) Firewall arrangement must be effectively updated according to the new sorts
of vulnerabilities that are for the most part recognized
5) IDS and IPS must be suitably checked for confining the whole information
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6) Proper hazard investigation requires to be effectively directed for deciding the
inward limited framework and in addition IDS IPS.
7) It is discovered that IDS and also IPS that for helps with confining
information condition must be appropriately designed for ready work force of different
presumed bargains.
8) It is discovered that IPS and IDS, baselines and signatures are required to be
keep up to date.
7. Security policies for Lucent Pharma network
The security strategies that are especially needed for the system of Lucent Pharma are
principally provided below:
Sys administrator: The power of the system relies upon the framework
administrator. The whole part of the framework administrator relies upon the whole
usefulness of the system. It is discovered that security related difficulties occurs then the sys
admin needs to deal with the situation by managing it properly. The system functionality
must considers all the security related arrangements while working with the framework so no
security related difficulties can have the capacity to influence the framework successfully.
Audit: It is distinguished that the audit area assumes an extraordinary part in the field
of networking because of number of variables that are required within the different segments
of functionality is accomplished. It is discovered that the primary approach that relevant
inside the devices must be performed effectively and additionally framework prerequisites.
The audit idea must be done as such that the individual can assume the whole liability. It is
discovered that if any kind of blunder is found inside the system it would largely aides in
inward limited framework and in addition IDS IPS.
7) It is discovered that IDS and also IPS that for helps with confining
information condition must be appropriately designed for ready work force of different
presumed bargains.
8) It is discovered that IPS and IDS, baselines and signatures are required to be
keep up to date.
7. Security policies for Lucent Pharma network
The security strategies that are especially needed for the system of Lucent Pharma are
principally provided below:
Sys administrator: The power of the system relies upon the framework
administrator. The whole part of the framework administrator relies upon the whole
usefulness of the system. It is discovered that security related difficulties occurs then the sys
admin needs to deal with the situation by managing it properly. The system functionality
must considers all the security related arrangements while working with the framework so no
security related difficulties can have the capacity to influence the framework successfully.
Audit: It is distinguished that the audit area assumes an extraordinary part in the field
of networking because of number of variables that are required within the different segments
of functionality is accomplished. It is discovered that the primary approach that relevant
inside the devices must be performed effectively and additionally framework prerequisites.
The audit idea must be done as such that the individual can assume the whole liability. It is
discovered that if any kind of blunder is found inside the system it would largely aides in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

securing the whole framework. Some of the time legitimate arranging must be done in setting
to strategy because of number of sorts of changes inside the framework which would
influence the typical usefulness of the framework.
System: The approach that related with the system can be inside the segment which
reflects that every one of the packets are exchanged inside the system must be legitimately
accessed. It is identified that the primary thought process of the system is to limit the general
time that is essentially connected with the bundles conveyance starting with one section then
onto the next. It is found that the system must be legitimately secured with the goal that no
action can affect the working of the system contrarily. It is recognized that as system involves
different kinds of bundles and hence it must incorporate distinctive sorts of fundamental data
that are particularly basic.
Security: Security is considered as one of the critical perspective of networking.
Number of different kinds of attacks occurs within the system that negatively impact the
system function. Therefore, in order to resolve this type of challenges and issues it very much
important to use proper policies as well as rules within the entire system. It is recognized that
there are number of principles and arrangements that must be incorporated inside the idea of
system with a specific end goal to keep up the system secure.
to strategy because of number of sorts of changes inside the framework which would
influence the typical usefulness of the framework.
System: The approach that related with the system can be inside the segment which
reflects that every one of the packets are exchanged inside the system must be legitimately
accessed. It is identified that the primary thought process of the system is to limit the general
time that is essentially connected with the bundles conveyance starting with one section then
onto the next. It is found that the system must be legitimately secured with the goal that no
action can affect the working of the system contrarily. It is recognized that as system involves
different kinds of bundles and hence it must incorporate distinctive sorts of fundamental data
that are particularly basic.
Security: Security is considered as one of the critical perspective of networking.
Number of different kinds of attacks occurs within the system that negatively impact the
system function. Therefore, in order to resolve this type of challenges and issues it very much
important to use proper policies as well as rules within the entire system. It is recognized that
there are number of principles and arrangements that must be incorporated inside the idea of
system with a specific end goal to keep up the system secure.
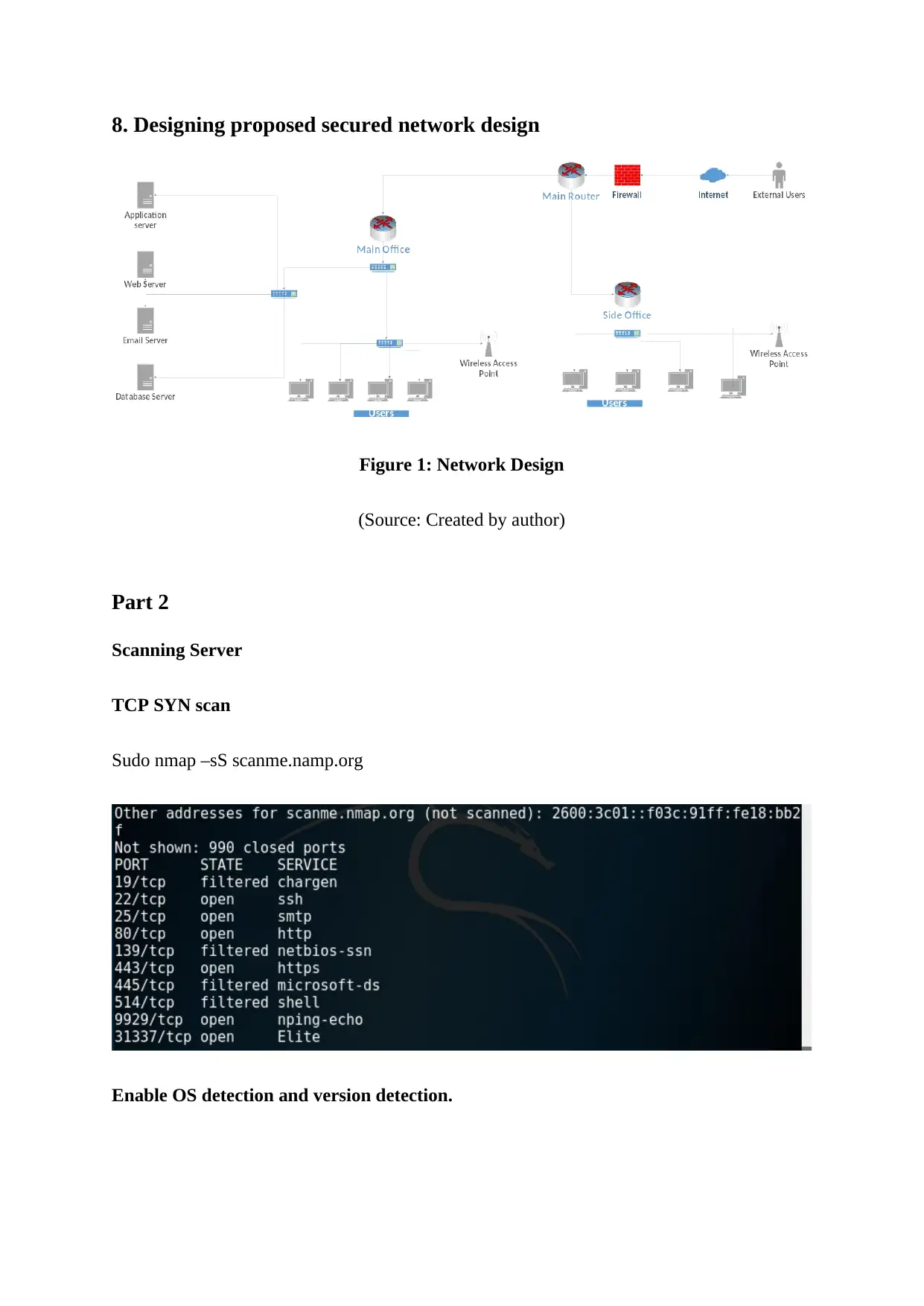
8. Designing proposed secured network design
Figure 1: Network Design
(Source: Created by author)
Part 2
Scanning Server
TCP SYN scan
Sudo nmap –sS scanme.namp.org
Enable OS detection and version detection.
Figure 1: Network Design
(Source: Created by author)
Part 2
Scanning Server
TCP SYN scan
Sudo nmap –sS scanme.namp.org
Enable OS detection and version detection.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


