Exploring Network Security Issues and a Seven-Layer Security Model
VerifiedAdded on 2023/06/12
|11
|1603
|450
Report
AI Summary
This report provides a comprehensive analysis of network security issues, including cyber-attacks, denial-of-service (DoS) attacks, phishing, and cloud attacks, which pose significant threats to organizations. It then proposes a seven-layer network security model comprising Physical, VLAN, ACL, Software, User, Administrative, and IT Department layers to mitigate these risks. Each layer is detailed with its specific functions and contributions to overall network security, emphasizing the importance of physical security, network segmentation, access control, software updates, user training, administrative oversight, and a dedicated IT department. The report concludes by highlighting the critical need for organizations to address network security issues to prevent data breaches and financial losses, advocating for the implementation of robust security measures and continuous monitoring.

Running head: NETWORK SECURITY ISSUES AND SECURITY MODEL
Network security issues and security model
Name of the Student
Name of the University
Author’s Note
Network security issues and security model
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
NETWORK SECURITY ISSUES AND SECURITY MODEL
Table of Contents
Introduction......................................................................................................................................3
Network Security issues..................................................................................................................3
Network Security Model..................................................................................................................7
Conclusion.....................................................................................................................................10
References......................................................................................................................................11
NETWORK SECURITY ISSUES AND SECURITY MODEL
Table of Contents
Introduction......................................................................................................................................3
Network Security issues..................................................................................................................3
Network Security Model..................................................................................................................7
Conclusion.....................................................................................................................................10
References......................................................................................................................................11

3
NETWORK SECURITY ISSUES AND SECURITY MODEL
Introduction
E-commerce and global connectivity have been major advancement in the internet technology
field. Various benefits have been provided by the internet with various vulnerabilities. The
security of data and information over the internet has been major problem for the internet users.
This report deals with various network issues over the internet. These issues have been properly
analyzed in the report. This report outlines the network security model for minimizing the
network issues in the organization.
Network Security issues
There are various network issues can be identified in the organization:
Cyber-attacks
Cyber-attacks have been the most common threats in the network of the company. There are
various cases of cyber-attacks in the organization. Various harmful viruses and malwares can
attack the network server of the company and cause cyber-attacks (Perlman, Kaufman &
Speciner, 2016).
NETWORK SECURITY ISSUES AND SECURITY MODEL
Introduction
E-commerce and global connectivity have been major advancement in the internet technology
field. Various benefits have been provided by the internet with various vulnerabilities. The
security of data and information over the internet has been major problem for the internet users.
This report deals with various network issues over the internet. These issues have been properly
analyzed in the report. This report outlines the network security model for minimizing the
network issues in the organization.
Network Security issues
There are various network issues can be identified in the organization:
Cyber-attacks
Cyber-attacks have been the most common threats in the network of the company. There are
various cases of cyber-attacks in the organization. Various harmful viruses and malwares can
attack the network server of the company and cause cyber-attacks (Perlman, Kaufman &
Speciner, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
NETWORK SECURITY ISSUES AND SECURITY MODEL
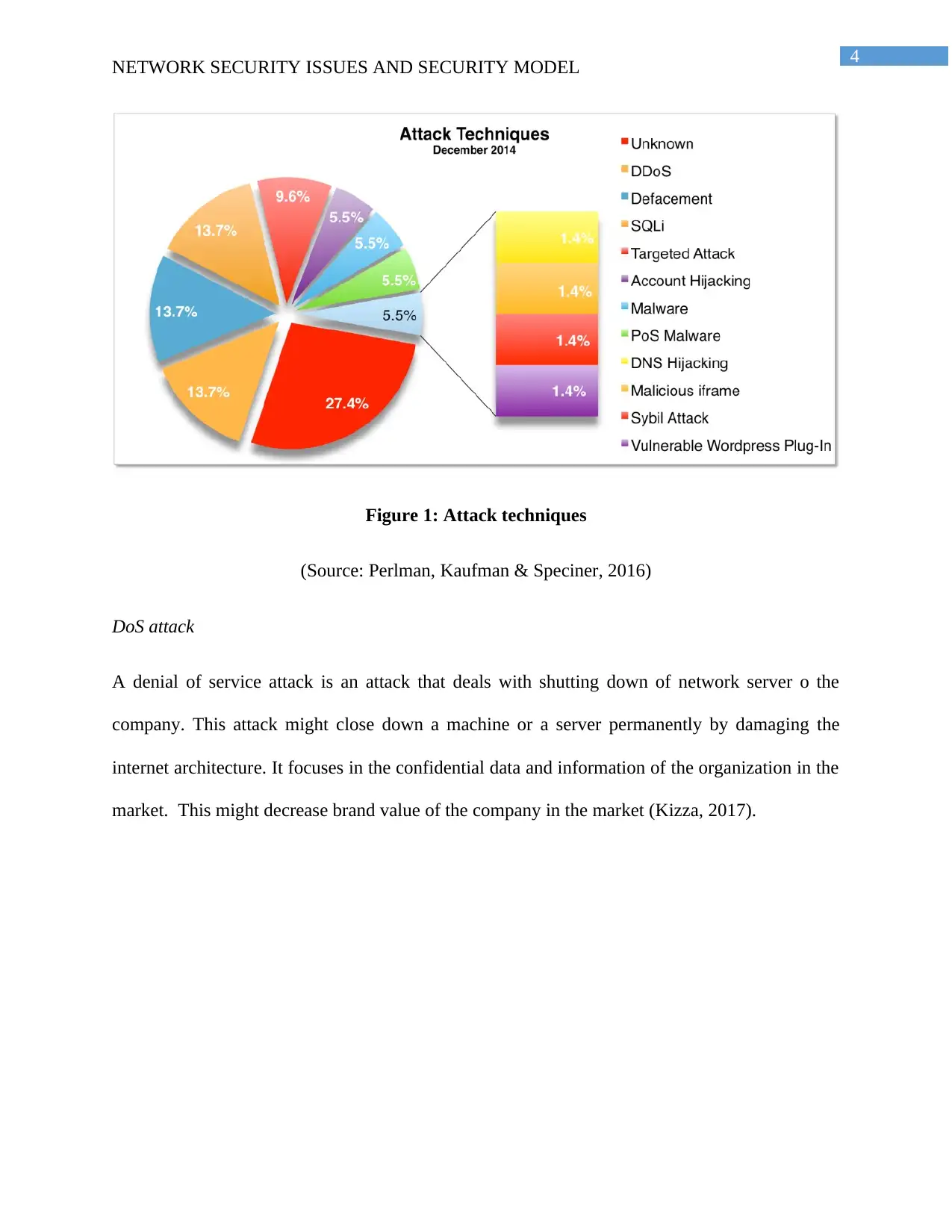
Figure 1: Attack techniques
(Source: Perlman, Kaufman & Speciner, 2016)
DoS attack
A denial of service attack is an attack that deals with shutting down of network server o the
company. This attack might close down a machine or a server permanently by damaging the
internet architecture. It focuses in the confidential data and information of the organization in the
market. This might decrease brand value of the company in the market (Kizza, 2017).
NETWORK SECURITY ISSUES AND SECURITY MODEL
Figure 1: Attack techniques
(Source: Perlman, Kaufman & Speciner, 2016)
DoS attack
A denial of service attack is an attack that deals with shutting down of network server o the
company. This attack might close down a machine or a server permanently by damaging the
internet architecture. It focuses in the confidential data and information of the organization in the
market. This might decrease brand value of the company in the market (Kizza, 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
NETWORK SECURITY ISSUES AND SECURITY MODEL
Figure 2: DoS attack
(Source: Kizza, 2017)
Phishing
This attack targets the personal information o the users including the username, passwords,
banking information and other personal information. This attack is mainly done with the help of
spam emails that are sent to the users. When the users open that spam mail. All the login
credentials are sent to the hackers (Acemoglu, Malekian & Ozdaglar, 2016). This can be a
dangerous or the company, as there are a number of mails are received on their mail id.
NETWORK SECURITY ISSUES AND SECURITY MODEL
Figure 2: DoS attack
(Source: Kizza, 2017)
Phishing
This attack targets the personal information o the users including the username, passwords,
banking information and other personal information. This attack is mainly done with the help of
spam emails that are sent to the users. When the users open that spam mail. All the login
credentials are sent to the hackers (Acemoglu, Malekian & Ozdaglar, 2016). This can be a
dangerous or the company, as there are a number of mails are received on their mail id.
6
NETWORK SECURITY ISSUES AND SECURITY MODEL
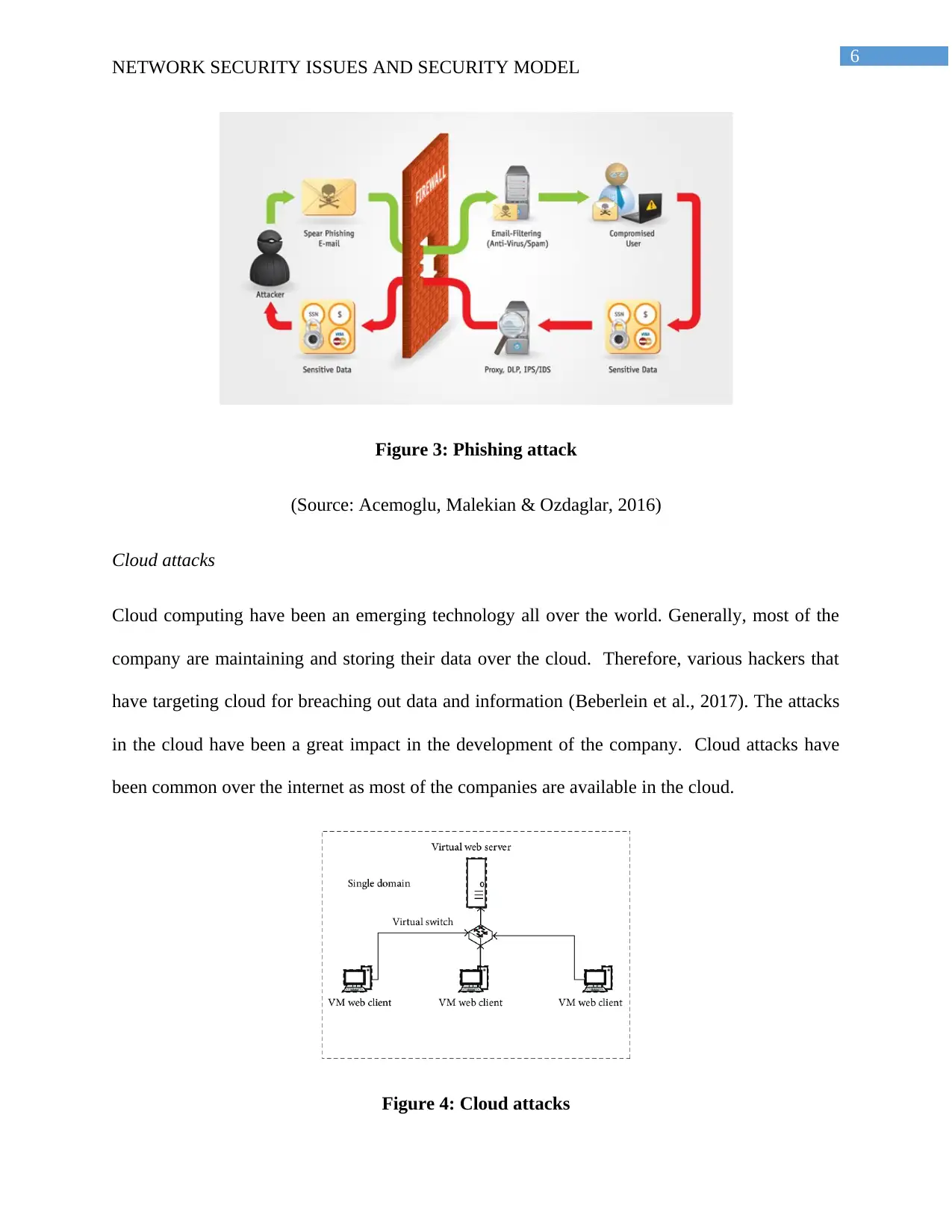
Figure 3: Phishing attack
(Source: Acemoglu, Malekian & Ozdaglar, 2016)
Cloud attacks
Cloud computing have been an emerging technology all over the world. Generally, most of the
company are maintaining and storing their data over the cloud. Therefore, various hackers that
have targeting cloud for breaching out data and information (Beberlein et al., 2017). The attacks
in the cloud have been a great impact in the development of the company. Cloud attacks have
been common over the internet as most of the companies are available in the cloud.
Figure 4: Cloud attacks
NETWORK SECURITY ISSUES AND SECURITY MODEL
Figure 3: Phishing attack
(Source: Acemoglu, Malekian & Ozdaglar, 2016)
Cloud attacks
Cloud computing have been an emerging technology all over the world. Generally, most of the
company are maintaining and storing their data over the cloud. Therefore, various hackers that
have targeting cloud for breaching out data and information (Beberlein et al., 2017). The attacks
in the cloud have been a great impact in the development of the company. Cloud attacks have
been common over the internet as most of the companies are available in the cloud.
Figure 4: Cloud attacks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
NETWORK SECURITY ISSUES AND SECURITY MODEL
(Source: Beberlein et al., 2017)
Network Security Model
The proposed model is of seven layers that helps in dividing task in the network infrastructure.
This model has been a generic model and can be applicable to different security devices. The
seven layers of network security model include Physical, VLAN, ACL, Software, user,
Administrative and IT Department.
Physical layer
The physical layer focuses in the security of the network at physical level. It can be implemented
to the physical security for preventing them from accessing a facility to gain stored on computers
and servers. Users get interacted with the systems through physical layer. However, physical
layer has been the easiest layer in the model (Frigault et al., 2017).
VLAN
The VLAN layer refers to the maintenance and creation of the virtual local area networks. The
VLAN help in maintaining the security of various systems connected together. These connected
computers and other devices get attacked by different viruses and intruders for breaching out
data and information from the network. The VLAN works on the public and private network
(Knapp & Langill, 2014). VLAN helps in creating a protecting over the networks that helps in
protecting them from external intruders in the network.
NETWORK SECURITY ISSUES AND SECURITY MODEL
(Source: Beberlein et al., 2017)
Network Security Model
The proposed model is of seven layers that helps in dividing task in the network infrastructure.
This model has been a generic model and can be applicable to different security devices. The
seven layers of network security model include Physical, VLAN, ACL, Software, user,
Administrative and IT Department.
Physical layer
The physical layer focuses in the security of the network at physical level. It can be implemented
to the physical security for preventing them from accessing a facility to gain stored on computers
and servers. Users get interacted with the systems through physical layer. However, physical
layer has been the easiest layer in the model (Frigault et al., 2017).
VLAN
The VLAN layer refers to the maintenance and creation of the virtual local area networks. The
VLAN help in maintaining the security of various systems connected together. These connected
computers and other devices get attacked by different viruses and intruders for breaching out
data and information from the network. The VLAN works on the public and private network
(Knapp & Langill, 2014). VLAN helps in creating a protecting over the networks that helps in
protecting them from external intruders in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
NETWORK SECURITY ISSUES AND SECURITY MODEL
Figure 5: Network Security Model
(Source: Created by author)
ACL Layer
The Access Control Lists or ACL is security protocol installed in routers and firewalls. This
helps in allowing and denying a particular request on different servers and hosts. User can place
a strong access control lists to restricts some of the websites and servers to be accessed from the
device. This helps in restricting the entry of harmful elements in the networks (Larson et al.,
2016). This layer helps in providing security of the software used in the system. It protects the
domain controller that helps in maintaining the security of the domain names of various server
over the network.
Software layer
Physical layer
VLAN
ACL layer
Software layer
User Layer
Administratuve layer
IT Department layer
NETWORK SECURITY ISSUES AND SECURITY MODEL
Figure 5: Network Security Model
(Source: Created by author)
ACL Layer
The Access Control Lists or ACL is security protocol installed in routers and firewalls. This
helps in allowing and denying a particular request on different servers and hosts. User can place
a strong access control lists to restricts some of the websites and servers to be accessed from the
device. This helps in restricting the entry of harmful elements in the networks (Larson et al.,
2016). This layer helps in providing security of the software used in the system. It protects the
domain controller that helps in maintaining the security of the domain names of various server
over the network.
Software layer
Physical layer
VLAN
ACL layer
Software layer
User Layer
Administratuve layer
IT Department layer

9
NETWORK SECURITY ISSUES AND SECURITY MODEL
The software layer has been focusing on the updating software installed in the device. Upgraded
patches helps in providing security to the new threats over the internet. The use of the software
layer helps in maintaining the advanced version of various software that increases efficiency of
the device used in the network (Kizza, 2017). If a host is properly updated and patched correctly,
a user-layer attack can be restricted in the network.
User Layer
The user layer have focused on training and knowledge of the user over security in network. The
user has to understand the back concept of the network security over the internet. The
knowledge and training over the network security helps in minimizing the threats and risks over
the network. The user needs to know about the vulnerabilities that can be implemented on the
network (Acemoglu, Malekian & Ozdaglar, 2016). A network security professional might help in
providing training and knowledge about network security issues.
Administrative Layer
The administrative layer focuses on training and motivation of the administrative users. This
layer include all the members of management. Therefore, the administrative users need to be
educated with the knowledge of network security and try to identify problem in the network of
the organization.
IT Department layer
The IT department layer contains all network security professionals including technicians,
architects and support specialists. The IT department layer have access to read and write any data
and information from network (Knapp & Langill, 2014). This helps in accessing the security
NETWORK SECURITY ISSUES AND SECURITY MODEL
The software layer has been focusing on the updating software installed in the device. Upgraded
patches helps in providing security to the new threats over the internet. The use of the software
layer helps in maintaining the advanced version of various software that increases efficiency of
the device used in the network (Kizza, 2017). If a host is properly updated and patched correctly,
a user-layer attack can be restricted in the network.
User Layer
The user layer have focused on training and knowledge of the user over security in network. The
user has to understand the back concept of the network security over the internet. The
knowledge and training over the network security helps in minimizing the threats and risks over
the network. The user needs to know about the vulnerabilities that can be implemented on the
network (Acemoglu, Malekian & Ozdaglar, 2016). A network security professional might help in
providing training and knowledge about network security issues.
Administrative Layer
The administrative layer focuses on training and motivation of the administrative users. This
layer include all the members of management. Therefore, the administrative users need to be
educated with the knowledge of network security and try to identify problem in the network of
the organization.
IT Department layer
The IT department layer contains all network security professionals including technicians,
architects and support specialists. The IT department layer have access to read and write any data
and information from network (Knapp & Langill, 2014). This helps in accessing the security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
NETWORK SECURITY ISSUES AND SECURITY MODEL
protocols of the network. The absence of IT department layer cane create risks in the network
related to the financial loss of the company in the market.
Conclusion
It can be concluded that network security issues have been creating problems for the
company. This might results in data and financial loss of the users and organization in the
market. There are numerous phishing attacks are happening over the internet that have been
causing problems for the company. User need to have an alarming system installed in their
system to detect any kind of physical attack in the system.
NETWORK SECURITY ISSUES AND SECURITY MODEL
protocols of the network. The absence of IT department layer cane create risks in the network
related to the financial loss of the company in the market.
Conclusion
It can be concluded that network security issues have been creating problems for the
company. This might results in data and financial loss of the users and organization in the
market. There are numerous phishing attacks are happening over the internet that have been
causing problems for the company. User need to have an alarming system installed in their
system to detect any kind of physical attack in the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
NETWORK SECURITY ISSUES AND SECURITY MODEL
References
Acemoglu, D., Malekian, A., & Ozdaglar, A. (2016). Network security and contagion. Journal
of Economic Theory, 166, 536-585.
Beberlein, L. T., Dias, G., Levitt, K. N., Mukherjee, B., & Wood, J. (2017). Network attacks and
an Ethernet-based network security monitor.
Chen, G., Gong, Y., Xiao, P., & Chambers, J. A. (2015). Physical layer network security in the
full-duplex relay system. IEEE transactions on information forensics and security, 10(3),
574-583.
Frigault, M., Wang, L., Jajodia, S., & Singhal, A. (2017). Measuring the Overall Network
Security by Combining CVSS Scores Based on Attack Graphs and Bayesian Networks.
In Network Security Metrics (pp. 1-23). Springer, Cham.
Kizza, J. M. (2017). Guide to computer network security. Springer.
Knapp, E. D., & Langill, J. T. (2014). Industrial Network Security: Securing critical
infrastructure networks for smart grid, SCADA, and other Industrial Control Systems.
Syngress.
Larson, V., Short III, R. D., Munger, E. C., & Williamson, M. (2016). U.S. Patent No. 9,374,346.
Washington, DC: U.S. Patent and Trademark Office.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
NETWORK SECURITY ISSUES AND SECURITY MODEL
References
Acemoglu, D., Malekian, A., & Ozdaglar, A. (2016). Network security and contagion. Journal
of Economic Theory, 166, 536-585.
Beberlein, L. T., Dias, G., Levitt, K. N., Mukherjee, B., & Wood, J. (2017). Network attacks and
an Ethernet-based network security monitor.
Chen, G., Gong, Y., Xiao, P., & Chambers, J. A. (2015). Physical layer network security in the
full-duplex relay system. IEEE transactions on information forensics and security, 10(3),
574-583.
Frigault, M., Wang, L., Jajodia, S., & Singhal, A. (2017). Measuring the Overall Network
Security by Combining CVSS Scores Based on Attack Graphs and Bayesian Networks.
In Network Security Metrics (pp. 1-23). Springer, Cham.
Kizza, J. M. (2017). Guide to computer network security. Springer.
Knapp, E. D., & Langill, J. T. (2014). Industrial Network Security: Securing critical
infrastructure networks for smart grid, SCADA, and other Industrial Control Systems.
Syngress.
Larson, V., Short III, R. D., Munger, E. C., & Williamson, M. (2016). U.S. Patent No. 9,374,346.
Washington, DC: U.S. Patent and Trademark Office.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




