MN502: A Detailed Comparison of Nmap and Nessus for Network Security
VerifiedAdded on 2023/06/13
|11
|1474
|434
Report
AI Summary
This report offers a comprehensive analysis of two prominent network security tools, Nmap and Nessus, highlighting their features, advantages, and disadvantages. Nmap, a network mapper, is discussed in terms of its ability to scan networks, identify open ports, detect operating systems, and discover vulnerabilities. The report also addresses Nmap's limitations, such as proxy support and the complexities of its NSE scripting language. Nessus, a remote security scanner, is examined for its vulnerability analysis, security auditing, and data recovery capabilities. The document also covers the setup administration of Nessus, emphasizing the importance of securing the Nessus server and addressing potential issues like false positives and network overload. The comparison between Nmap and Nessus underscores their respective roles in network security and the necessity of using them appropriately for optimal network protection. Desklib provides more solved assignments and resources for students.

Running Head: OVERVIEW OF NETWORK SECURITY
Overview of network security
[Student Name]
[University Name]
Overview of network security
[Student Name]
[University Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OVERVIEW OF NETWORK SECURITY
Table of Contents
Introduction......................................................................................................................................2
Nmap................................................................................................................................................2
Nessus..............................................................................................................................................5
Advantage and Disadvantages of NESSUS.................................................................................7
Comparison amongst NESSUS and NMAP:...................................................................................8
Table of Contents
Introduction......................................................................................................................................2
Nmap................................................................................................................................................2
Nessus..............................................................................................................................................5
Advantage and Disadvantages of NESSUS.................................................................................7
Comparison amongst NESSUS and NMAP:...................................................................................8

2OVERVIEW OF NETWORK SECURITY
Introduction
Vulnerability scanners are extremely fundamental in the field of Network Security. In
spite of the fact that a great deal of network security scanners has developed as of late, the
opposition amongst NESSUS and NMAP continue enduring occasionally. Albeit them two play
out an incredible activity and offers different highlights, the prevalence rivalry continues flowing
again and again as far back as their development. Subsequently the accompanying exposition
gives a nitty gritty substance of both the huge profoundly secured network instruments NESSUS
and NMAP. Indeed, even the benefits and bad marks related with both of these instruments are
broadly talked about from the accompanying.
Nmap
Nmap is short for network mapper. Namp is a tool that is used to scan the network the
name itself tells us it is a Network Mapper. By using Nmap the information’s about the victim’s
machine can be easily found. It helps in looking at the open ports, Versions and OS you can find
the vulnerabilities in the victims’ machine. It helps in hacking in to the system of the other users.
For hacking a device, the first information that is required is OS the user is working on.
Additional all are the services (like FTP, SSH) and what all ports are open. The basic idea of
penetration is to look for a vulnerable service, exploit that service via open port and get in. all the
process that are being taken into consideration are provided by Nmap.
Introduction
Vulnerability scanners are extremely fundamental in the field of Network Security. In
spite of the fact that a great deal of network security scanners has developed as of late, the
opposition amongst NESSUS and NMAP continue enduring occasionally. Albeit them two play
out an incredible activity and offers different highlights, the prevalence rivalry continues flowing
again and again as far back as their development. Subsequently the accompanying exposition
gives a nitty gritty substance of both the huge profoundly secured network instruments NESSUS
and NMAP. Indeed, even the benefits and bad marks related with both of these instruments are
broadly talked about from the accompanying.
Nmap
Nmap is short for network mapper. Namp is a tool that is used to scan the network the
name itself tells us it is a Network Mapper. By using Nmap the information’s about the victim’s
machine can be easily found. It helps in looking at the open ports, Versions and OS you can find
the vulnerabilities in the victims’ machine. It helps in hacking in to the system of the other users.
For hacking a device, the first information that is required is OS the user is working on.
Additional all are the services (like FTP, SSH) and what all ports are open. The basic idea of
penetration is to look for a vulnerable service, exploit that service via open port and get in. all the
process that are being taken into consideration are provided by Nmap.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
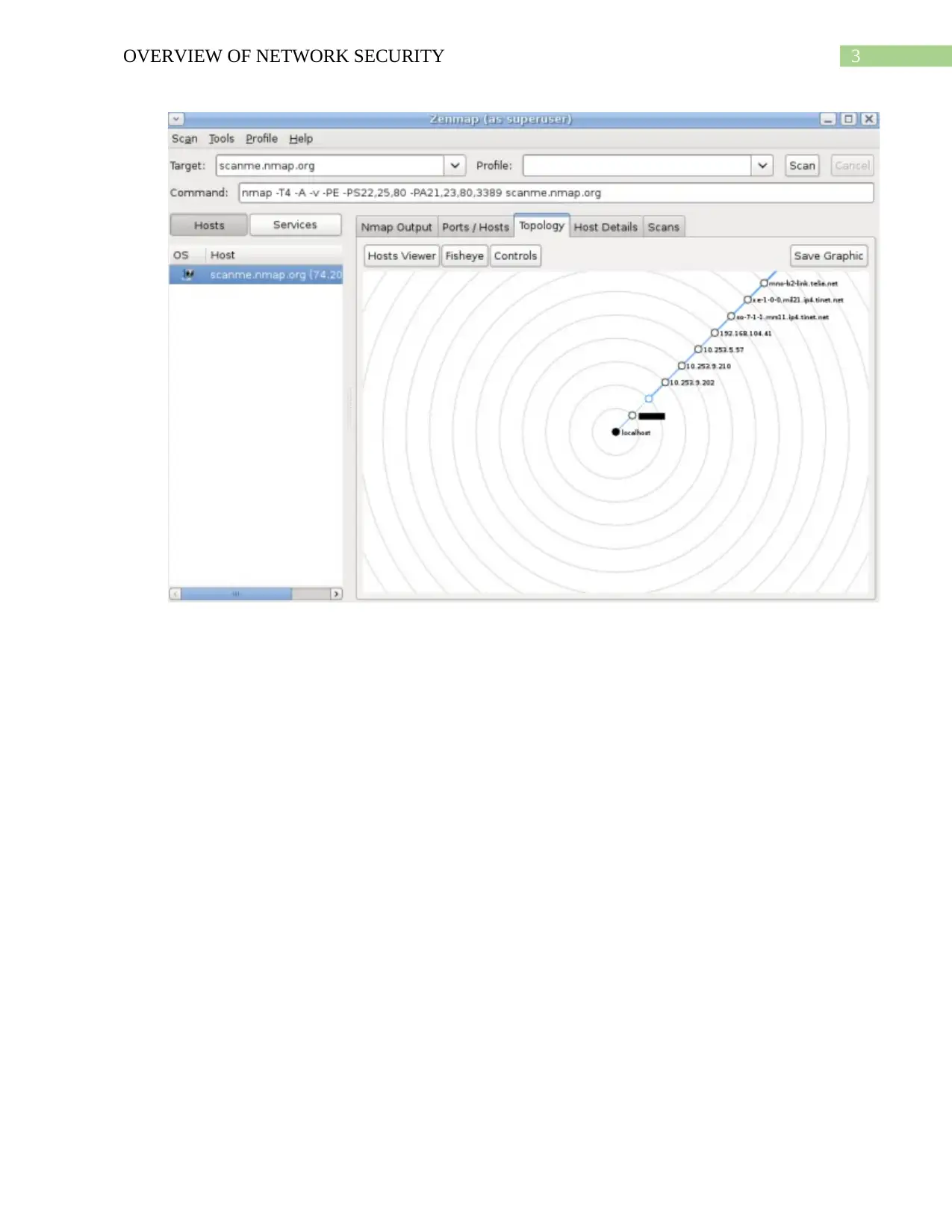
3OVERVIEW OF NETWORK SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
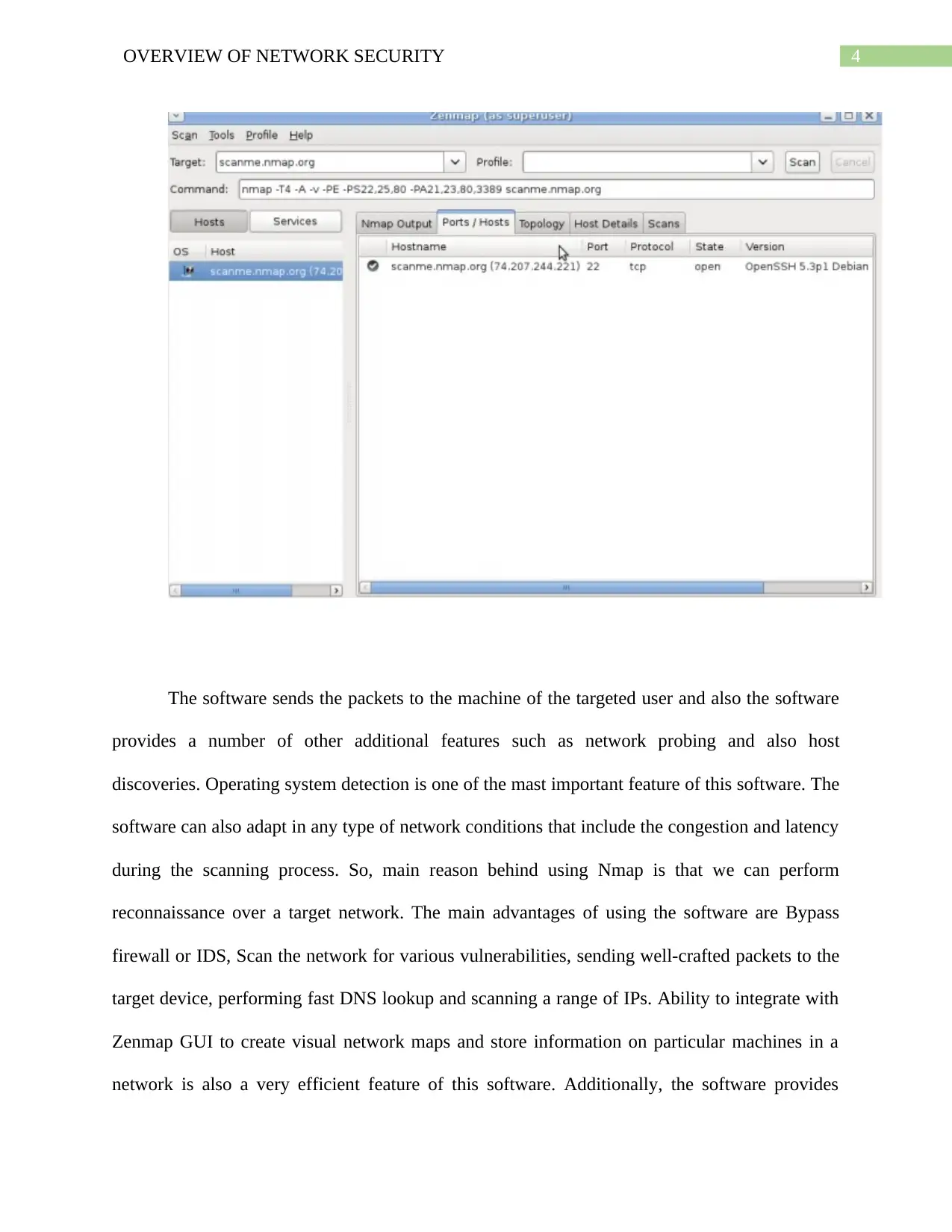
4OVERVIEW OF NETWORK SECURITY
The software sends the packets to the machine of the targeted user and also the software
provides a number of other additional features such as network probing and also host
discoveries. Operating system detection is one of the mast important feature of this software. The
software can also adapt in any type of network conditions that include the congestion and latency
during the scanning process. So, main reason behind using Nmap is that we can perform
reconnaissance over a target network. The main advantages of using the software are Bypass
firewall or IDS, Scan the network for various vulnerabilities, sending well-crafted packets to the
target device, performing fast DNS lookup and scanning a range of IPs. Ability to integrate with
Zenmap GUI to create visual network maps and store information on particular machines in a
network is also a very efficient feature of this software. Additionally, the software provides
The software sends the packets to the machine of the targeted user and also the software
provides a number of other additional features such as network probing and also host
discoveries. Operating system detection is one of the mast important feature of this software. The
software can also adapt in any type of network conditions that include the congestion and latency
during the scanning process. So, main reason behind using Nmap is that we can perform
reconnaissance over a target network. The main advantages of using the software are Bypass
firewall or IDS, Scan the network for various vulnerabilities, sending well-crafted packets to the
target device, performing fast DNS lookup and scanning a range of IPs. Ability to integrate with
Zenmap GUI to create visual network maps and store information on particular machines in a
network is also a very efficient feature of this software. Additionally, the software provides

5OVERVIEW OF NETWORK SECURITY
plethora of NSE scripts for reconnaissance and vulnerability discovery, and even exploitation in
some cases.
However, the software also has a wide range of disadvantages which include, Scanning
through proxies. Sometimes the attacker is needed to masquerade themselves before scanning
and for that purpose scanning through proxies is done but Nmap’s proxy support is kind of
broken. Additionally, NSE scripts are written in lua, rather than a less obscure language like
python or ruby, making extending and customizing Nmap’s capabilities more work than it ought
to be. There are ways to make port scans stealthier included with Nmap, but they always require
generating a whole lot of network traffic, and there is an inverse relationship between stealth and
speed.
Nessus
plethora of NSE scripts for reconnaissance and vulnerability discovery, and even exploitation in
some cases.
However, the software also has a wide range of disadvantages which include, Scanning
through proxies. Sometimes the attacker is needed to masquerade themselves before scanning
and for that purpose scanning through proxies is done but Nmap’s proxy support is kind of
broken. Additionally, NSE scripts are written in lua, rather than a less obscure language like
python or ruby, making extending and customizing Nmap’s capabilities more work than it ought
to be. There are ways to make port scans stealthier included with Nmap, but they always require
generating a whole lot of network traffic, and there is an inverse relationship between stealth and
speed.
Nessus
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
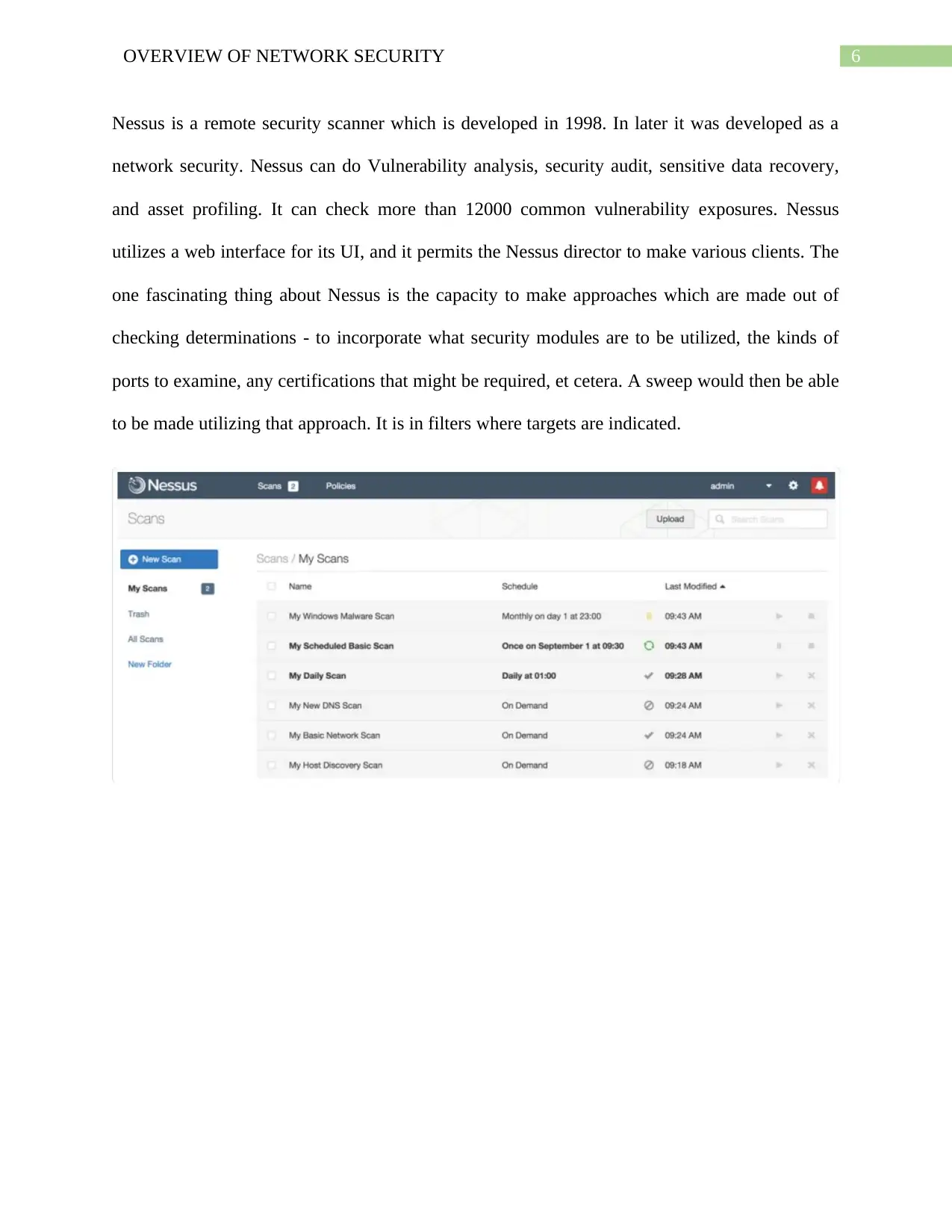
6OVERVIEW OF NETWORK SECURITY
Nessus is a remote security scanner which is developed in 1998. In later it was developed as a
network security. Nessus can do Vulnerability analysis, security audit, sensitive data recovery,
and asset profiling. It can check more than 12000 common vulnerability exposures. Nessus
utilizes a web interface for its UI, and it permits the Nessus director to make various clients. The
one fascinating thing about Nessus is the capacity to make approaches which are made out of
checking determinations - to incorporate what security modules are to be utilized, the kinds of
ports to examine, any certifications that might be required, et cetera. A sweep would then be able
to be made utilizing that approach. It is in filters where targets are indicated.
Nessus is a remote security scanner which is developed in 1998. In later it was developed as a
network security. Nessus can do Vulnerability analysis, security audit, sensitive data recovery,
and asset profiling. It can check more than 12000 common vulnerability exposures. Nessus
utilizes a web interface for its UI, and it permits the Nessus director to make various clients. The
one fascinating thing about Nessus is the capacity to make approaches which are made out of
checking determinations - to incorporate what security modules are to be utilized, the kinds of
ports to examine, any certifications that might be required, et cetera. A sweep would then be able
to be made utilizing that approach. It is in filters where targets are indicated.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
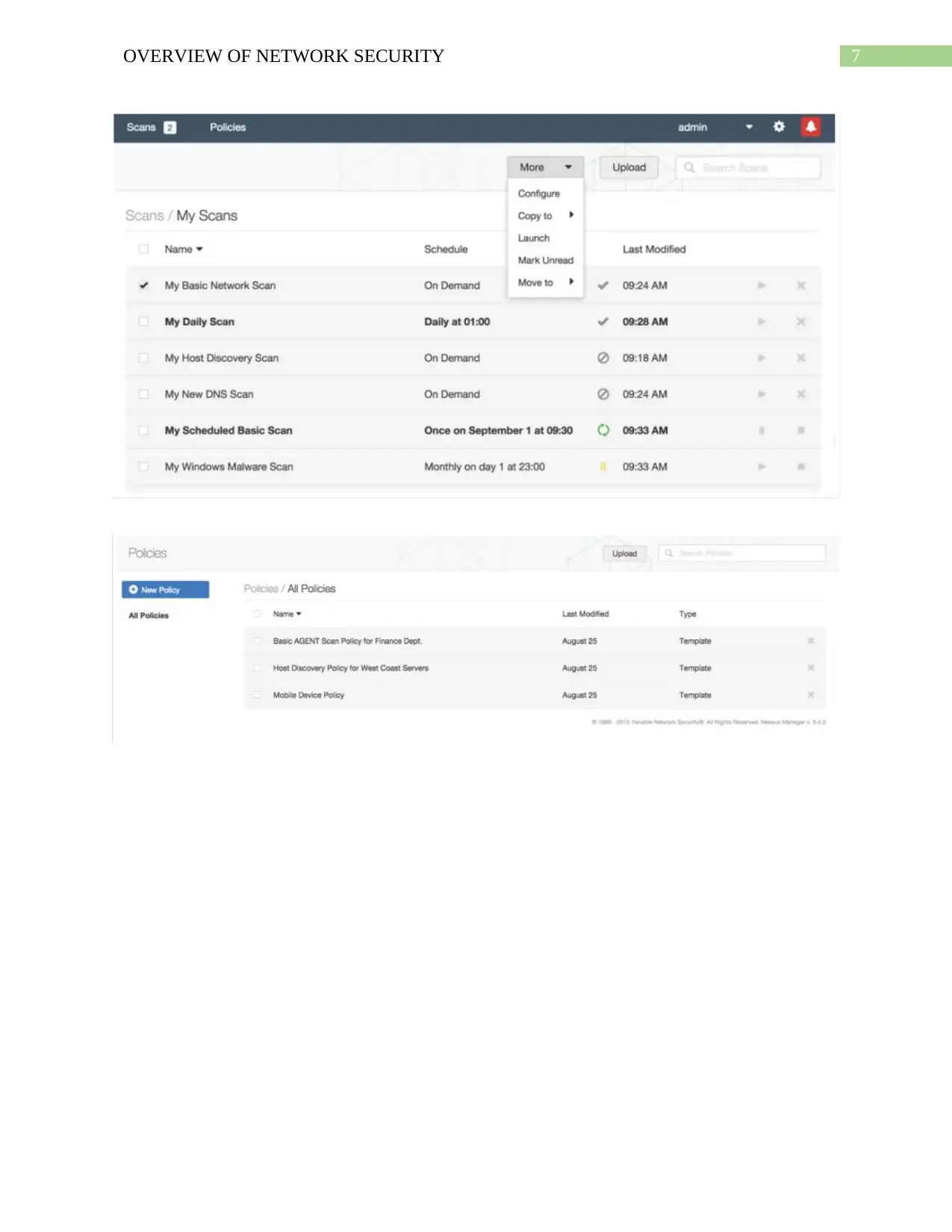
7OVERVIEW OF NETWORK SECURITY

8OVERVIEW OF NETWORK SECURITY
Advantage and Disadvantages of NESSUS
The setup administration of NESSUS benefit is adjusted to the customer – server
engineering. This design document is more entire than the customer adaptation. All design
choices indicated in this record will supersede the alternatives characterized by the client. The
NESSUS server is a daemon. With this arrangement record administration, the head can
concentrate the setup NESSUS. Also, the server has a record to concentrate the scanning rules.
NESSUS will examine the ports of living machines with four interior port scanners, or outer, for
example, NMAP. By realizing that if NESSUS is upgraded utilizing its port scanners home, the
scheduler can be begun. It is along these lines prescribed to utilize NMAP for execution
explanations behind such occurrences.
Advantage and Disadvantages of NESSUS
The setup administration of NESSUS benefit is adjusted to the customer – server
engineering. This design document is more entire than the customer adaptation. All design
choices indicated in this record will supersede the alternatives characterized by the client. The
NESSUS server is a daemon. With this arrangement record administration, the head can
concentrate the setup NESSUS. Also, the server has a record to concentrate the scanning rules.
NESSUS will examine the ports of living machines with four interior port scanners, or outer, for
example, NMAP. By realizing that if NESSUS is upgraded utilizing its port scanners home, the
scheduler can be begun. It is along these lines prescribed to utilize NMAP for execution
explanations behind such occurrences.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OVERVIEW OF NETWORK SECURITY
Since the utilization of NESSUS can be twofold edged, it appears glaringly evident to put
the physical machine in a safe area. At the consistent level, the NESSUS server security is more
intricate. For greatest security, we should put the server in a neighborhood network inaccessible
all things considered. In general, the NESSUS server must characterize a security arrangement to
control get to. For the present, NESSUS does not check the nearby security arrangements for
remote frameworks. To play out its tests, NESSUS dispatches genuine assaults against target
machines. It is subsequently reasonable to keep this assault is by playing out the output on a
schedule vacancy where the objective machine isn't apprehensive about losing information or by
indicating in the arrangement documents that you need to play out a sweep.
The remote output has the impediment of producing false positives. In other words, that
NESSUS can recognize a security rupture for instance, on an out of date benefit when a security
fix is connected on the nearby machine to settle bugs in this rendition. This is the nearby sweep
that amends this issue of false positive. There is a moment downside of this kind of scanning:
network over-burden.
Comparison amongst NESSUS and NMAP:
Both of these devices of network security are imperative for perfect purposes in different
situations and consequently it's our obligation to utilize them properly in the decided timings.
Albeit both these frameworks have advantages and disadvantages under their framework, the
advantages of utilizing them generally overweigh the bad marks. Once recognized the
approaching and active network, it is by and large conceivable to assemble gadgets as per some
general classifications gear. We can, for instance recognize intranet, in other words all the
machine in the network framework of an organization, the extranet is to state all machines the
Since the utilization of NESSUS can be twofold edged, it appears glaringly evident to put
the physical machine in a safe area. At the consistent level, the NESSUS server security is more
intricate. For greatest security, we should put the server in a neighborhood network inaccessible
all things considered. In general, the NESSUS server must characterize a security arrangement to
control get to. For the present, NESSUS does not check the nearby security arrangements for
remote frameworks. To play out its tests, NESSUS dispatches genuine assaults against target
machines. It is subsequently reasonable to keep this assault is by playing out the output on a
schedule vacancy where the objective machine isn't apprehensive about losing information or by
indicating in the arrangement documents that you need to play out a sweep.
The remote output has the impediment of producing false positives. In other words, that
NESSUS can recognize a security rupture for instance, on an out of date benefit when a security
fix is connected on the nearby machine to settle bugs in this rendition. This is the nearby sweep
that amends this issue of false positive. There is a moment downside of this kind of scanning:
network over-burden.
Comparison amongst NESSUS and NMAP:
Both of these devices of network security are imperative for perfect purposes in different
situations and consequently it's our obligation to utilize them properly in the decided timings.
Albeit both these frameworks have advantages and disadvantages under their framework, the
advantages of utilizing them generally overweigh the bad marks. Once recognized the
approaching and active network, it is by and large conceivable to assemble gadgets as per some
general classifications gear. We can, for instance recognize intranet, in other words all the
machine in the network framework of an organization, the extranet is to state all machines the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10OVERVIEW OF NETWORK SECURITY
organization could access from outside to inside data utilizing both these devices in a
commonplace way.
Network insurance is accomplished with wellbeing gear, for example, NESSUS and
NMAP. Their part is to guarantee that exclusive streams recognized in the past advance travel
between various parts of the network. On account of the Internet Company's server that is
accessible from the Internet, both NESSUS and NMAP are thought about once more. It is
pointless, so hurtful, that the stream of conference enters to the core of the intranet. It will be
considerably more secure to position the server between two frameworks that breaking point the
stream between the server and the intranet and the Internet and the server. Two capacities
comparatively as a firewall which constitutes a network that procedures stream at the convention
level, generally TCP/IP gadget. They will thusly have the capacity to ensure the course of
information stream and farthest point the stream to those gave. To secure the hardware against
information streams that could be pernicious, NESSUS and NMAP servers are utilized too with a
specific end goal to improve insurance.
organization could access from outside to inside data utilizing both these devices in a
commonplace way.
Network insurance is accomplished with wellbeing gear, for example, NESSUS and
NMAP. Their part is to guarantee that exclusive streams recognized in the past advance travel
between various parts of the network. On account of the Internet Company's server that is
accessible from the Internet, both NESSUS and NMAP are thought about once more. It is
pointless, so hurtful, that the stream of conference enters to the core of the intranet. It will be
considerably more secure to position the server between two frameworks that breaking point the
stream between the server and the intranet and the Internet and the server. Two capacities
comparatively as a firewall which constitutes a network that procedures stream at the convention
level, generally TCP/IP gadget. They will thusly have the capacity to ensure the course of
information stream and farthest point the stream to those gave. To secure the hardware against
information streams that could be pernicious, NESSUS and NMAP servers are utilized too with a
specific end goal to improve insurance.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





