Analysis of the Network Security Plan at First National University
VerifiedAdded on 2023/06/11
|15
|679
|496
Report
AI Summary
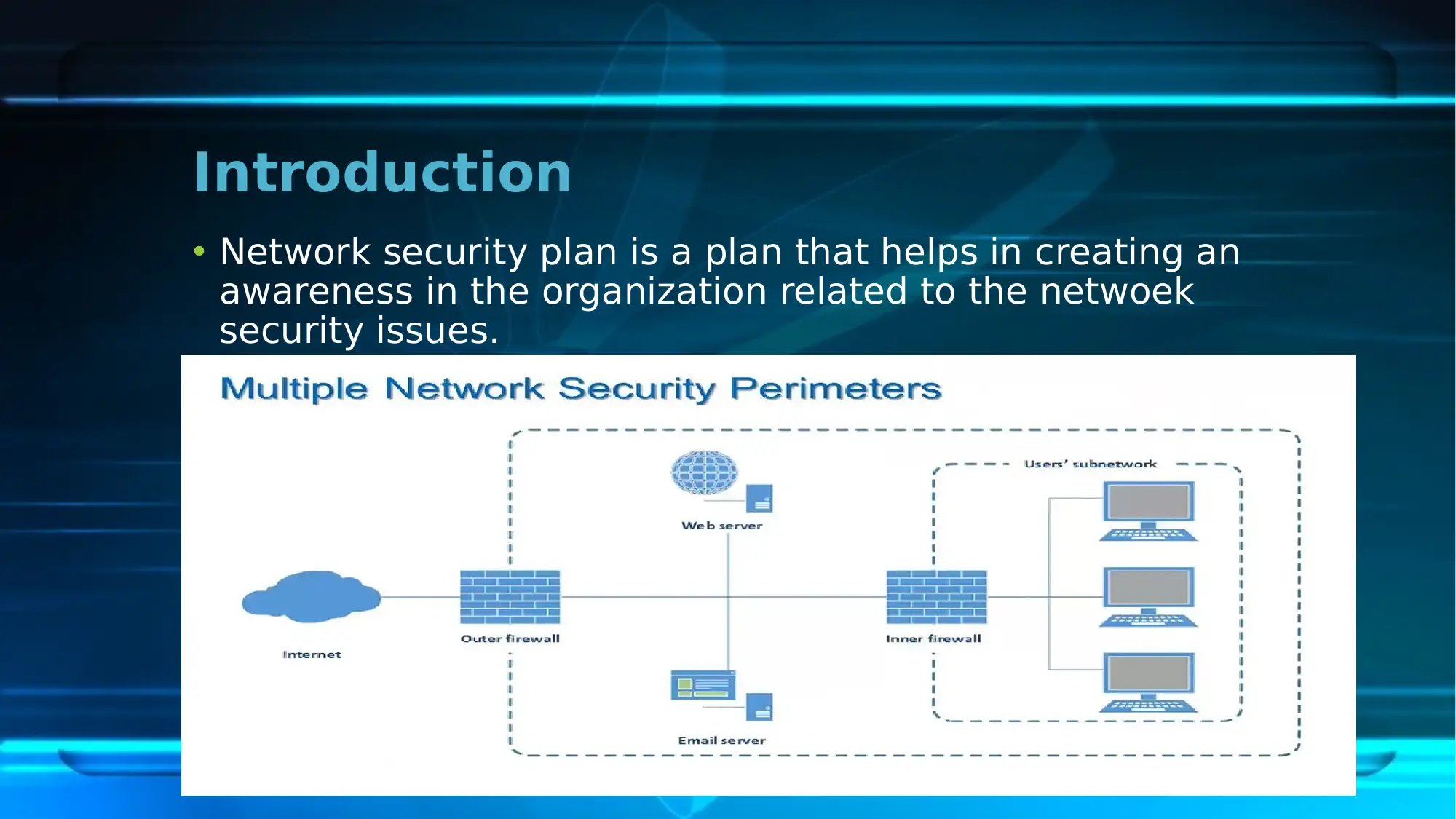
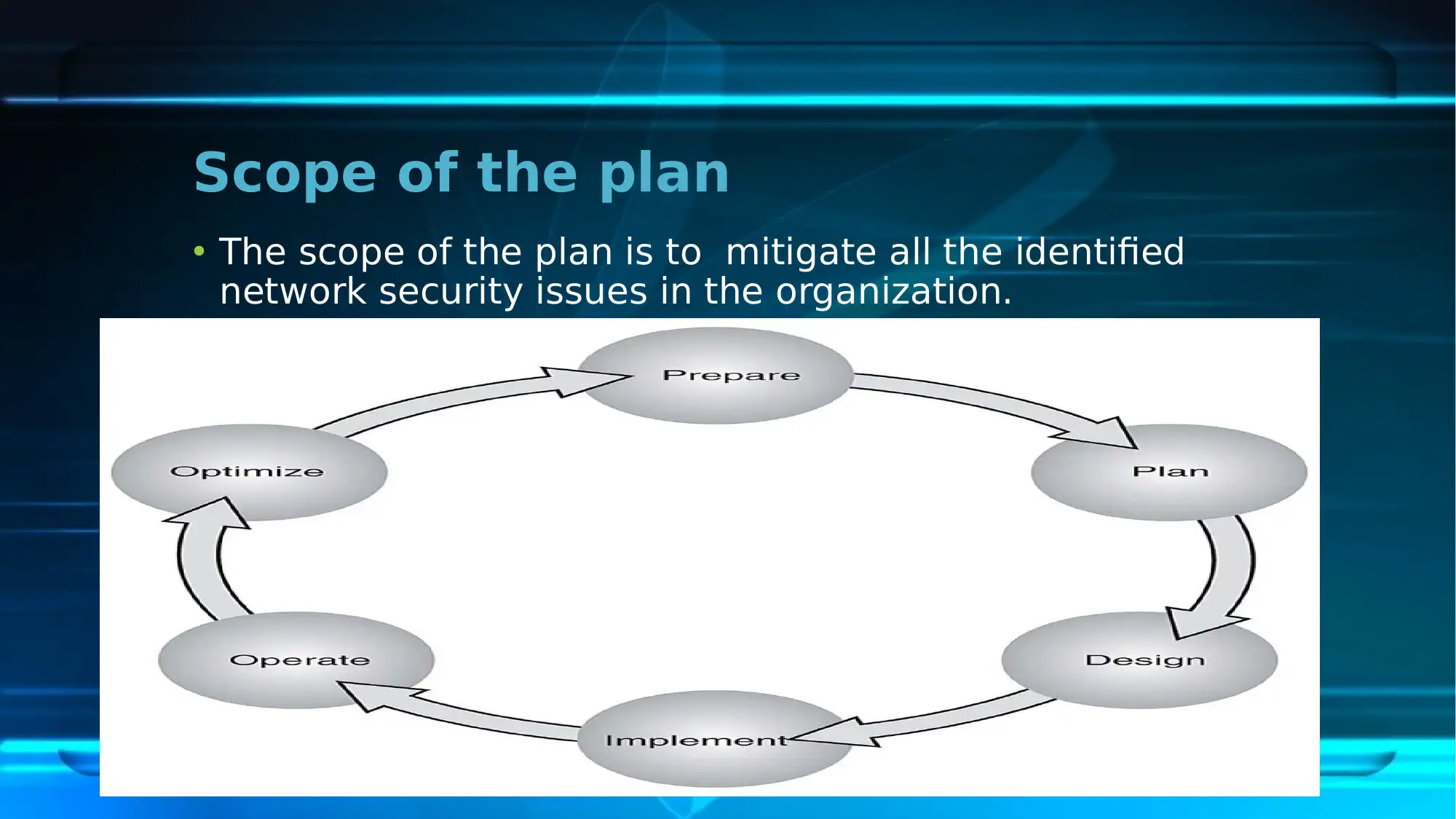
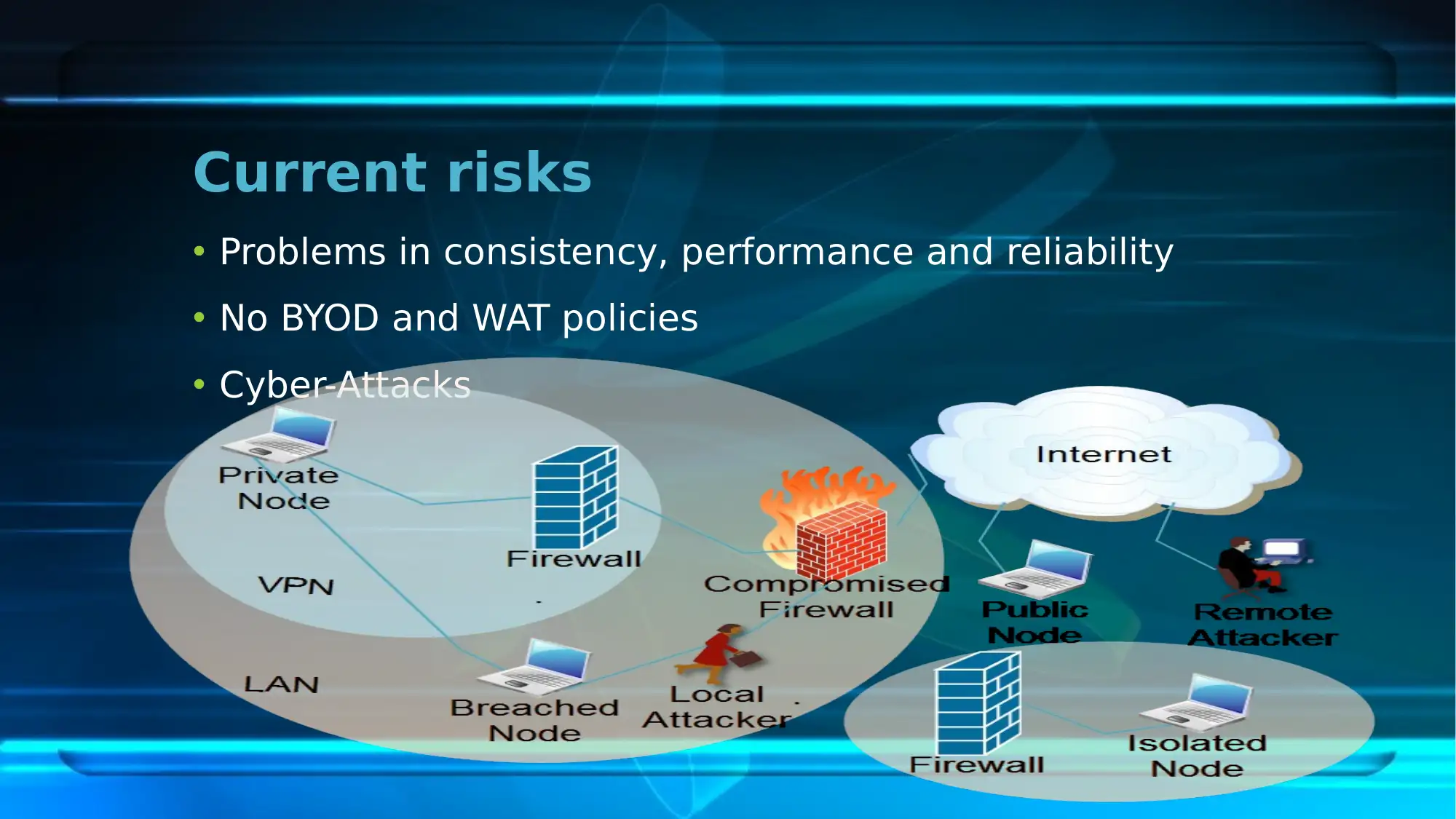
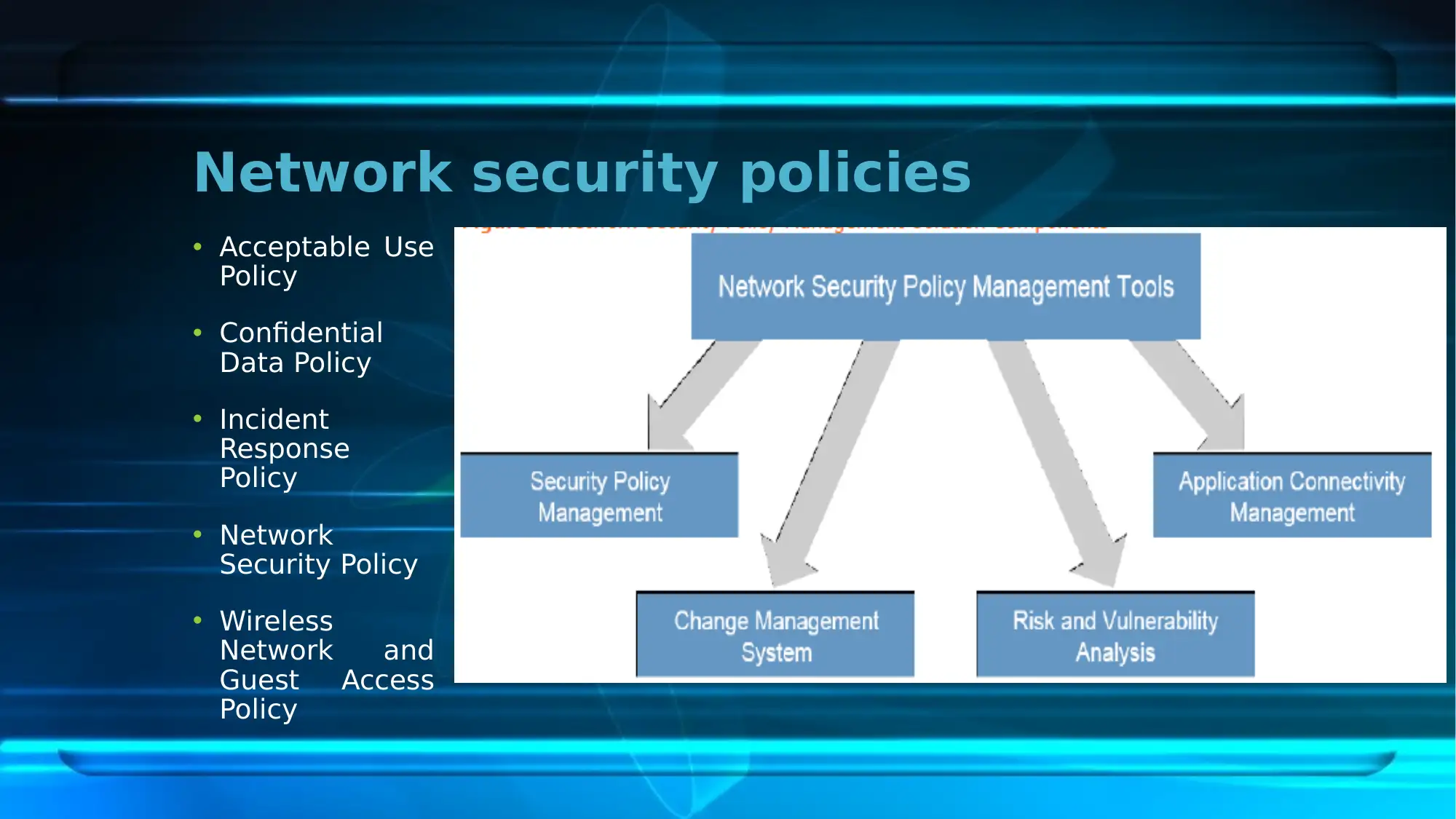
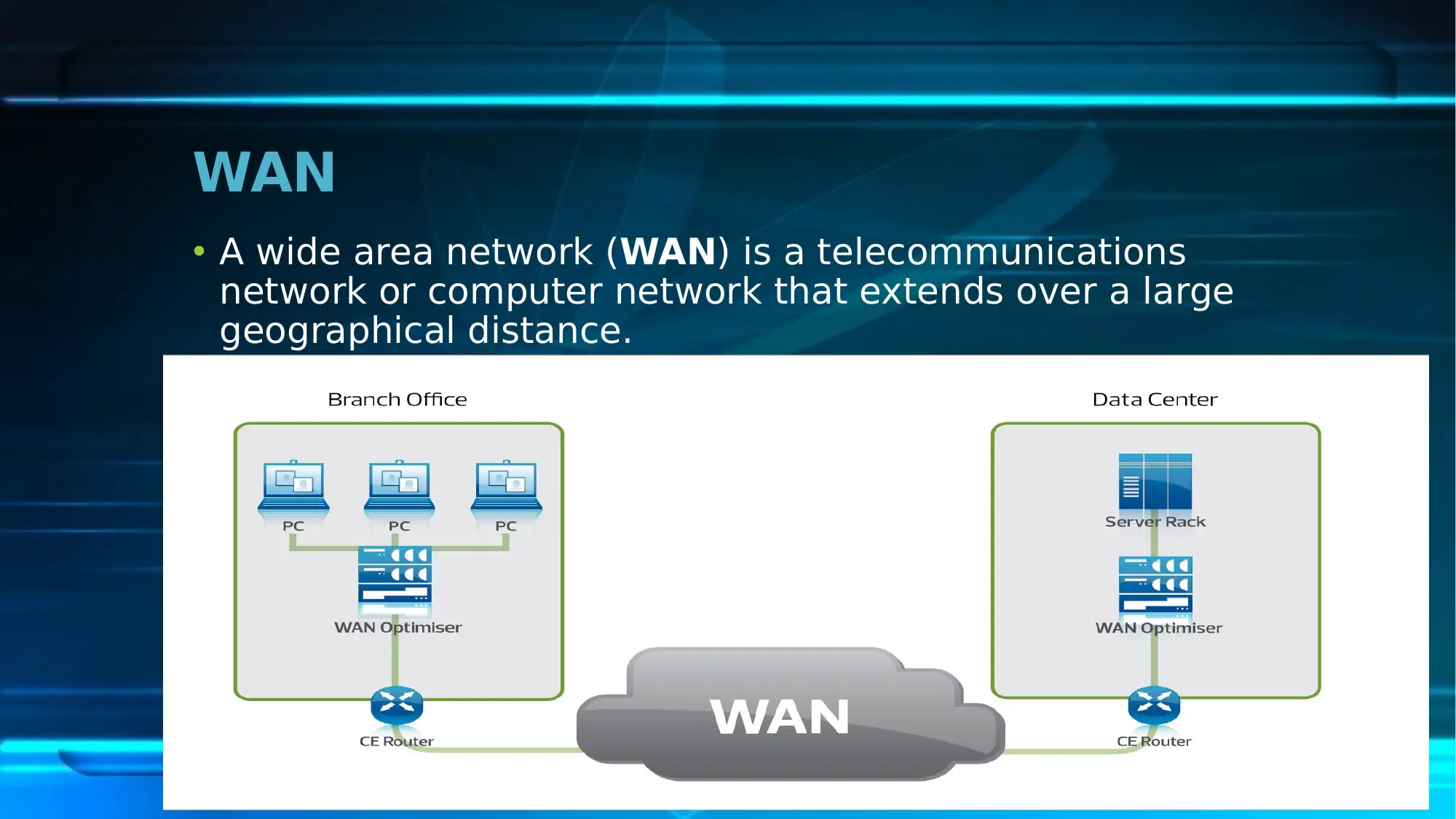
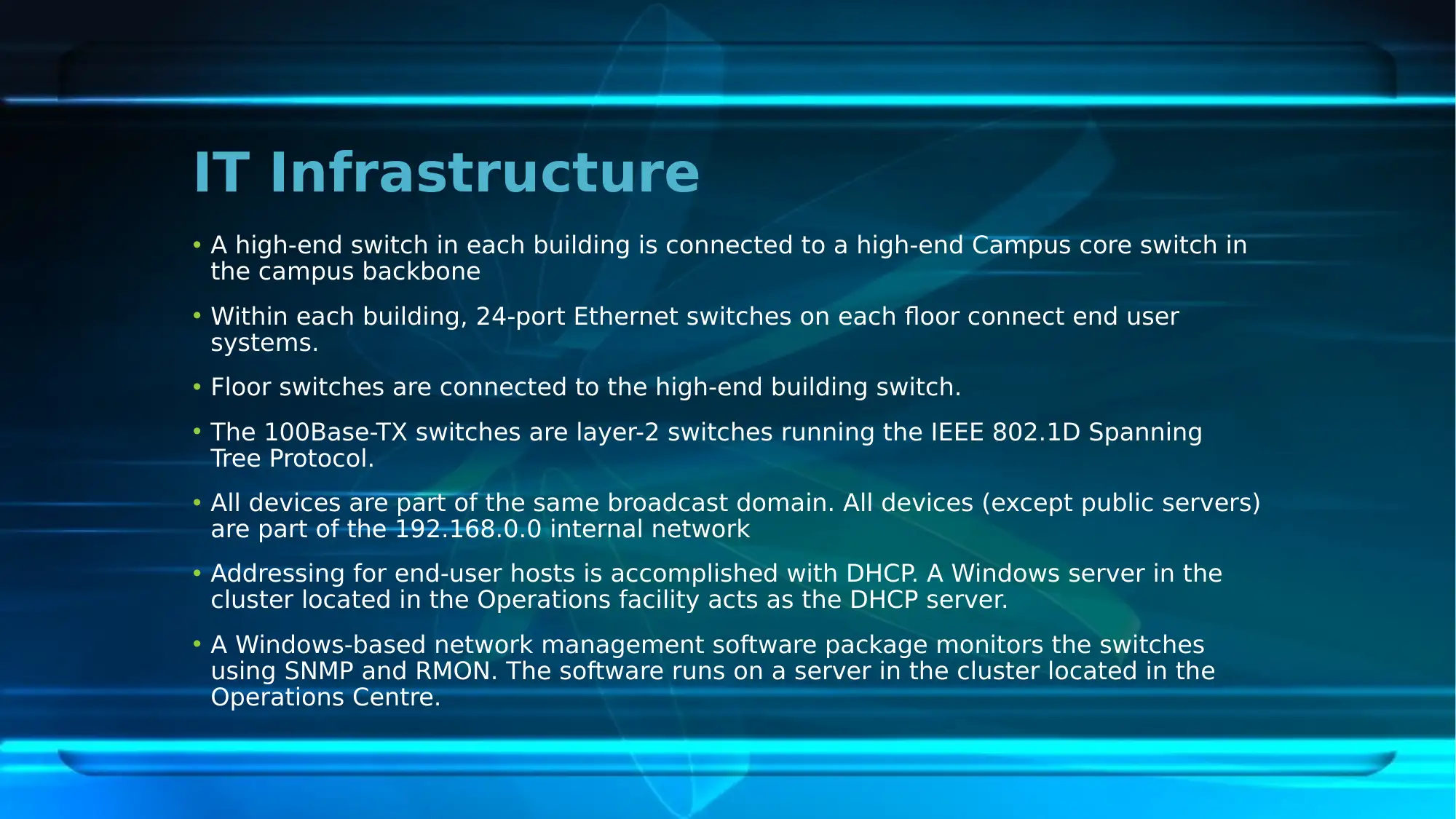
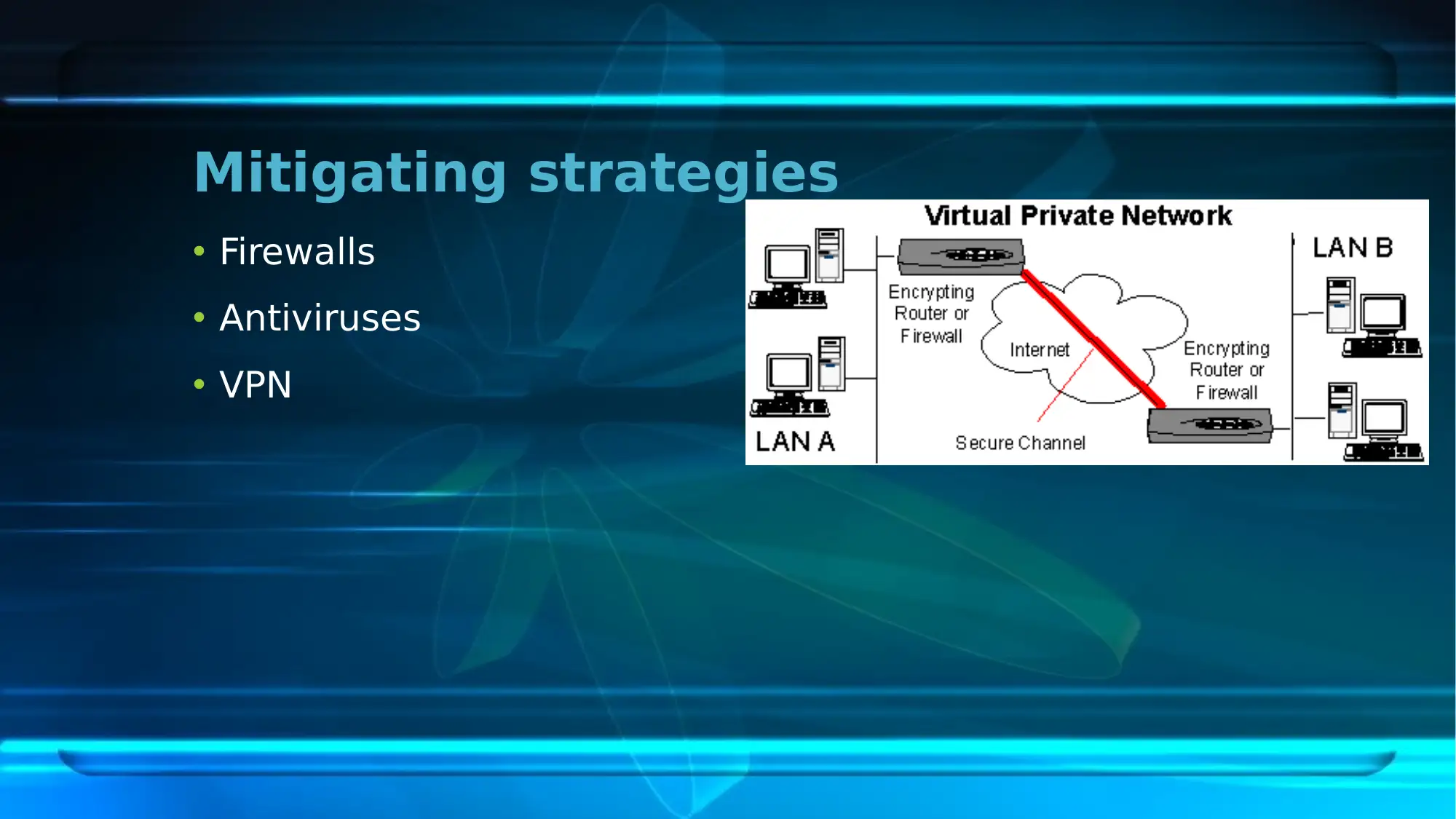
This report provides an overview of the network security plan implemented at the First National University (FNU). It highlights the scope of the plan, focusing on mitigating identified network security issues. The report identifies current risks such as problems in consistency, performance, and reliability, the absence of BYOD and WAT policies, and potential cyber-attacks. Key network security policies including Acceptable Use Policy, Confidential Data Policy, Incident Response Policy, Network Security Policy, and Wireless Network and Guest Access Policy are discussed. The security strategies involve redesigning the current network, overhauling the IP addressing scheme, and ensuring high availability. The existing IT infrastructure, including switches, addressing schemes, and network management software, is detailed along with mitigating strategies such as firewalls and antiviruses. The report also covers security technology implementation, including the use of a Higher Performance Computing Cluster, web services, online teaching programs, and data backup and recovery technologies. Finally, it outlines the security testing process, encompassing security architecture study, threat modeling, test planning, and test case execution, concluding that the network security plan plays a crucial role in mitigating network issues at the university. Desklib provides resources to students, visit for more solved assignments and past papers.
1 out of 15










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)