IY5511 Network Security Exam Paper & Solutions, Royal Holloway 2016
VerifiedAdded on 2023/06/12
|12
|4857
|176
Quiz and Exam
AI Summary
This document provides solutions to a Network Security exam paper (IY5511) from Royal Holloway, University of London, in 2016. The exam covers topics such as network attacks (eavesdropping, modification, fabrication, IP Spoofing), DNS security, TCP handshake, Diffie-Hellman protocol, challenge-response protocols, denial-of-service attacks, SYN cookies, encrypted key exchange (EKE), UDP and TCP, transport layer protocols, IPSec, TLS, private IPv4, NAT, and Internet Key Exchange protocol. The solutions detail cryptographic countermeasures, protocol vulnerabilities, and security mechanisms. Desklib offers this document along with many other resources to aid students in their studies.

Paper 1
Question 1:
(a)
(i) Eavesdropping is one of the potential attacks against network
communications performed by an active attacker.
(ii) An off-path attacker can be able to perform a fabrication attack on a
communication network.
(iii) Modification cannot be performed by a passive attacker as it requires
alteration of data.
(iv) Eavesdropping: The appropriate cryptographic countermeasures for
eavesdropping include the use of authentication mechanisms that do not
allow for the transmission of the password over the network. A Kerberos
protocol may be effective in this. Similarly, users should ensure that
passwords are encrypted if they must be transmitted over the network or an
encryption communication channel such as SSL may be used.
Modification: Cryptographic countermeasures to this attack include use of
data hashing, signing and digital signatures
Fabrication: This attacks can be prevented by authenticating users using the
communication channel.
(b)
(i) DNS plays an important role in address resolution. It enables a host in
learning the IP address for a given domain name.
(ii) Modification is one the attacks that is relevant to DNS. Sometimes
referred to DNS hijacking in which DNS records are modified to point to a
rogue DNS server or domain.
(c) IP spoofing was widespread in 1990’s
(i) IP spoofing refers to attackers inserting an IP address as the source address
of an IP datagram and therefore allowing them to impersonate any host.
The recipient has no guarantee about the true identity of the entity that
sent an IP datagram. Ingress filtering is responsible for identifying and
dropping packets that have been spoofed by inspecting the source address.
This helps identifying and preventing spoof attacks.
(ii) To prevent against IP spoofing, users are provided with a mechanism to
verify the origin of the IP datagram through the linking of the datagram to
an IP address. By encrypting part of the datagram using a key known to
the sender and the receiver can help prevent IP spoofing.
Question 2:
Question 1:
(a)
(i) Eavesdropping is one of the potential attacks against network
communications performed by an active attacker.
(ii) An off-path attacker can be able to perform a fabrication attack on a
communication network.
(iii) Modification cannot be performed by a passive attacker as it requires
alteration of data.
(iv) Eavesdropping: The appropriate cryptographic countermeasures for
eavesdropping include the use of authentication mechanisms that do not
allow for the transmission of the password over the network. A Kerberos
protocol may be effective in this. Similarly, users should ensure that
passwords are encrypted if they must be transmitted over the network or an
encryption communication channel such as SSL may be used.
Modification: Cryptographic countermeasures to this attack include use of
data hashing, signing and digital signatures
Fabrication: This attacks can be prevented by authenticating users using the
communication channel.
(b)
(i) DNS plays an important role in address resolution. It enables a host in
learning the IP address for a given domain name.
(ii) Modification is one the attacks that is relevant to DNS. Sometimes
referred to DNS hijacking in which DNS records are modified to point to a
rogue DNS server or domain.
(c) IP spoofing was widespread in 1990’s
(i) IP spoofing refers to attackers inserting an IP address as the source address
of an IP datagram and therefore allowing them to impersonate any host.
The recipient has no guarantee about the true identity of the entity that
sent an IP datagram. Ingress filtering is responsible for identifying and
dropping packets that have been spoofed by inspecting the source address.
This helps identifying and preventing spoof attacks.
(ii) To prevent against IP spoofing, users are provided with a mechanism to
verify the origin of the IP datagram through the linking of the datagram to
an IP address. By encrypting part of the datagram using a key known to
the sender and the receiver can help prevent IP spoofing.
Question 2:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(a) A TCP handshake is method used by TCP/IP networks in creating connection between
local host/client to a server. It’s meant to create a TCP connection.
(b) Denial-of-service attacks exploit an implementation characteristic of TCP and can be
used to make the server incapable of answering a legitimate client’s application request
for new TCP connections. The services that binds and listens to the TCP socket are
potentially vulnerable to DOS attacks.
(c) SYN cookies are used for the prevention of SYN flood attacks which the TCP handshake
is vulnerable to. They allow the server to avoid dropping connections when the SYN
queue fills up.
(d) The Diffie-Hellman Protocol:
Both the sender and receiver agree on shared parameters
A private value is chosen from the protocol participants and then a public value is
computed using the shared parameters and its private value
Public values are exchanged by the protocol participants over a public network
Each protocol participant uses their private value and the other participant’s
public value to compute a shared secret.
(e) A correct protocol is a protocol that always achieves the desired objective at the end of
the protocol run. A secure protocol is a protocol that will achieve the stated aims of the
protocol when honest parties adhere to the protocol even in the presence of attackers.
Diffie-Hellman protocol is not secure because an active attacker can be able to establish
keys with both participant A and B and thus gain control of the communication channel.
There is no way of confirming the message sent by one of the participants actually came
from the participants.
(f) To make Diffie-Hellman protocol secure needs message origin authentication thereby
requiring either of the participants to share a secret key or both participants should have a
public-private key pair. In the first case, both participants can compute a MAC over each
message and in the second case, the first participant can compute a digital signature over
the first message while the second participant can compute a digital signature over the
second message.
Question 3:
(a) Using the same challenge gives the attacker an opportunity to replay a message from a
previous protocol run by participants A and B. This will allow the attacker to pretend to
be either A or B.
(b)
(i) The hashing function would be inappropriate as the response is a randomized
variable already that is harder for attackers to guess. The variable changes from
time to time.
(ii) There is no need for 64-bit string chosen by claimant as the random value chosen
would be harder to guess
local host/client to a server. It’s meant to create a TCP connection.
(b) Denial-of-service attacks exploit an implementation characteristic of TCP and can be
used to make the server incapable of answering a legitimate client’s application request
for new TCP connections. The services that binds and listens to the TCP socket are
potentially vulnerable to DOS attacks.
(c) SYN cookies are used for the prevention of SYN flood attacks which the TCP handshake
is vulnerable to. They allow the server to avoid dropping connections when the SYN
queue fills up.
(d) The Diffie-Hellman Protocol:
Both the sender and receiver agree on shared parameters
A private value is chosen from the protocol participants and then a public value is
computed using the shared parameters and its private value
Public values are exchanged by the protocol participants over a public network
Each protocol participant uses their private value and the other participant’s
public value to compute a shared secret.
(e) A correct protocol is a protocol that always achieves the desired objective at the end of
the protocol run. A secure protocol is a protocol that will achieve the stated aims of the
protocol when honest parties adhere to the protocol even in the presence of attackers.
Diffie-Hellman protocol is not secure because an active attacker can be able to establish
keys with both participant A and B and thus gain control of the communication channel.
There is no way of confirming the message sent by one of the participants actually came
from the participants.
(f) To make Diffie-Hellman protocol secure needs message origin authentication thereby
requiring either of the participants to share a secret key or both participants should have a
public-private key pair. In the first case, both participants can compute a MAC over each
message and in the second case, the first participant can compute a digital signature over
the first message while the second participant can compute a digital signature over the
second message.
Question 3:
(a) Using the same challenge gives the attacker an opportunity to replay a message from a
previous protocol run by participants A and B. This will allow the attacker to pretend to
be either A or B.
(b)
(i) The hashing function would be inappropriate as the response is a randomized
variable already that is harder for attackers to guess. The variable changes from
time to time.
(ii) There is no need for 64-bit string chosen by claimant as the random value chosen
would be harder to guess

(iii) Using bitwise XOR and a key would waste valuable networking resources since
the random key value for the protocol is enough
(iv) Since authentication would require the respondent to acquire the claimants key,
the 64-bit string chosen would play a minimal role in transmission of the
messages.
(v) This method would be inappropriate because the random value generated would
be hard for attackers to guess.
(c) An offline attack requires work from the attacker only and requires little or no
communication with the server or system under attack. An online attack requires
considerable communication with the system under attack.
An offline brute force attack is more dangerous it easier to perform than an online attack
and stands a better chance of going undetected.
(d) i). The challenge-response protocol requires private key from the participants. The
attacker doesn’t require to engage the server in order to access the messages and keys of
the participants
ii). A dictionary attack is an attempt to gain unauthorized access to a computer system by
the use of a very large set of words in the generation of potential passwords. Offline
dictionary attacks can happen when the attacker selects passwords from the dictionary
and tries to generate responses that matches the recorded one. This process is repeated
over and over until a successful attempt is made.
(e) EKE (encrypted key exchange) ensures that successful password can only be done online
rather than offline. The protocol is designed to use:
(i) Asymmetric cryptography to generate fresh, shared secret k
(ii) The long-term key kcv (password-based) to preserve the confidentiality of k
(iii) k to run a challenge-response protocol.
Question 4
(a)
(i) Both UDP and TCP are used to send bits of data (packets) over the Internet.
(ii) A reliable channel is a channel that has a higher percentage of availability for use
in a specified period of scheduled availability. Reliable channels are necessary in
packet-switched digital networks as they allow for fast network functioning and
scalability.
(iii) The Application layer protocol may sometimes use the UDP as the transport layer
protocol rather than TCP where the requests and responses made are both
lightweight and thus would require the use of a single packet.
(b)
(i) A transport layer protocol that identifies errors introduced by the physical layer
can be constructed by using the concept of ports supporting flow control and
duplicate data suppression.
the random key value for the protocol is enough
(iv) Since authentication would require the respondent to acquire the claimants key,
the 64-bit string chosen would play a minimal role in transmission of the
messages.
(v) This method would be inappropriate because the random value generated would
be hard for attackers to guess.
(c) An offline attack requires work from the attacker only and requires little or no
communication with the server or system under attack. An online attack requires
considerable communication with the system under attack.
An offline brute force attack is more dangerous it easier to perform than an online attack
and stands a better chance of going undetected.
(d) i). The challenge-response protocol requires private key from the participants. The
attacker doesn’t require to engage the server in order to access the messages and keys of
the participants
ii). A dictionary attack is an attempt to gain unauthorized access to a computer system by
the use of a very large set of words in the generation of potential passwords. Offline
dictionary attacks can happen when the attacker selects passwords from the dictionary
and tries to generate responses that matches the recorded one. This process is repeated
over and over until a successful attempt is made.
(e) EKE (encrypted key exchange) ensures that successful password can only be done online
rather than offline. The protocol is designed to use:
(i) Asymmetric cryptography to generate fresh, shared secret k
(ii) The long-term key kcv (password-based) to preserve the confidentiality of k
(iii) k to run a challenge-response protocol.
Question 4
(a)
(i) Both UDP and TCP are used to send bits of data (packets) over the Internet.
(ii) A reliable channel is a channel that has a higher percentage of availability for use
in a specified period of scheduled availability. Reliable channels are necessary in
packet-switched digital networks as they allow for fast network functioning and
scalability.
(iii) The Application layer protocol may sometimes use the UDP as the transport layer
protocol rather than TCP where the requests and responses made are both
lightweight and thus would require the use of a single packet.
(b)
(i) A transport layer protocol that identifies errors introduced by the physical layer
can be constructed by using the concept of ports supporting flow control and
duplicate data suppression.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(ii) A transport layer protocol that is reliable can be constructed by using the concept
of ports supporting reliable data delivery.
(c)
(i) Application layer PDU’s are vulnerable to on-path attacks as they are used for
lightweight single-packets that are less secure. For these reasons, detection of on-
path attacks is difficult.
(ii) The order in which PDU’s are received is loosely attached to the application layer
thereby making it hard for the detection and sequence of on-path attacks.
(d)
(i) IPSec with Authentication Header provides authentication, integrity and anti-
replay for an entire packet thereby making it hard for an on-path attacker to
modify or re-order the application layer PDUs exchanged in a TCP session.
(ii) TLS is the successor protocol of SSL. They are both responsible for securing TCP
sessions and safeguarding sensitive data sent between two systems thereby
reducing the chances on on-path attacker to infiltrate the TCP session.
(iii) TCP authentication protocol ensures specifies stronger authentication codes to
protect against replay attacks for long lived connections like BGP sessions. They
protect against on-path attacks.
Question 5:
(a) Private IPv4 was introduced so that it could help in conservation of address space (public
IPv4 address space was scarce) and ensuring security of the core network. Private IPv4
has led to an expansion of the address space and made core networks more secure.
(b)
(i) Network address and port translation involves a technique where by port numbers
and private internet protocol addresses are mapped to one public IP address from
multiple internal hosts. Network address and port translation extends the
capabilities of NAT (network address translation) by allowing for translation and
mapping of port numbers, in addition to the IP address, when communicating
with an external network.
(ii) IPsec in tunnel mode is the default mode and in this mode, the entire original IP
packet is protected by IPSec. It is commonly used between gateways or at an end-
station to a gateway. The Gateway here acts as a proxy for the hosts behind it.
(c) When IPSec module is enabled, both inbound and outbound traffic passes through the
IPSec module. The Security Policy Database is responsible for controlling how packets
are processed. For an outgoing packet, outbound security policy entries are used to match
the packet fields chosen as the selector. The SP entry that requires security processing,
the search for corresponding Security Association (SA) is created in the Security
Association Database (SAD) whenever there are no matching entries found. The packets
are then processed according to the security specification given by the SA.
of ports supporting reliable data delivery.
(c)
(i) Application layer PDU’s are vulnerable to on-path attacks as they are used for
lightweight single-packets that are less secure. For these reasons, detection of on-
path attacks is difficult.
(ii) The order in which PDU’s are received is loosely attached to the application layer
thereby making it hard for the detection and sequence of on-path attacks.
(d)
(i) IPSec with Authentication Header provides authentication, integrity and anti-
replay for an entire packet thereby making it hard for an on-path attacker to
modify or re-order the application layer PDUs exchanged in a TCP session.
(ii) TLS is the successor protocol of SSL. They are both responsible for securing TCP
sessions and safeguarding sensitive data sent between two systems thereby
reducing the chances on on-path attacker to infiltrate the TCP session.
(iii) TCP authentication protocol ensures specifies stronger authentication codes to
protect against replay attacks for long lived connections like BGP sessions. They
protect against on-path attacks.
Question 5:
(a) Private IPv4 was introduced so that it could help in conservation of address space (public
IPv4 address space was scarce) and ensuring security of the core network. Private IPv4
has led to an expansion of the address space and made core networks more secure.
(b)
(i) Network address and port translation involves a technique where by port numbers
and private internet protocol addresses are mapped to one public IP address from
multiple internal hosts. Network address and port translation extends the
capabilities of NAT (network address translation) by allowing for translation and
mapping of port numbers, in addition to the IP address, when communicating
with an external network.
(ii) IPsec in tunnel mode is the default mode and in this mode, the entire original IP
packet is protected by IPSec. It is commonly used between gateways or at an end-
station to a gateway. The Gateway here acts as a proxy for the hosts behind it.
(c) When IPSec module is enabled, both inbound and outbound traffic passes through the
IPSec module. The Security Policy Database is responsible for controlling how packets
are processed. For an outgoing packet, outbound security policy entries are used to match
the packet fields chosen as the selector. The SP entry that requires security processing,
the search for corresponding Security Association (SA) is created in the Security
Association Database (SAD) whenever there are no matching entries found. The packets
are then processed according to the security specification given by the SA.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
(d) There are three message exchanges in the Internet Key Exchange Protocol: They are
message 1: responsible for proposing policies by sending one or more security
associations proposals; message 2: is a response from the responder to the packet sent
from the initiator; and message 3: is a message that contains Diffie-Hellman Key
exchange payload and nonce payload from initiator.
Paper 2
1 (a) (i) an active on-path attacker-modification, fabrication, sinkhole, Sybil,
spoofing
(ii) A passive on-path attacker-Eavesdropping, traffic analysis
(iii) An active off-path attacker- modification, fabrication, denial of services,
wormhole
(iii) A passive off-path attacker-Eavesdropping, traffic analysis.
1(b) (i) IP and UDP;
Both are transport layer protocols and they allow for application to application delivery
PROTOCOL Similarities Differences
IP and UDP -Both are stateless,
connectionless protocols.
-neither of both IP and UDP
provides a reliable channel
-UDP resides on the transport
layer while IP resides on
internet Layer
TCP and UDP - Both are transport layer
protocols and they allow for
application to application
delivery
-Both TCP and UDP headers
includes source and
destination port numbers
-Both TCP and UDP
encapsulate transport layer
PDUs
-TCP provides a reliable
Service while UDP does not
-TCP has error checking
functionality while UDP
does not have
-TCP is connection oriented
while UDP is connectionless
WEP and WPA -In WEP data integrity is
provided through CRC-32
while WPA it is provided
through message integrity
code
-In WEP encryption is
achieved through Rivest
Cipher 4(RC4) while in WAP
message 1: responsible for proposing policies by sending one or more security
associations proposals; message 2: is a response from the responder to the packet sent
from the initiator; and message 3: is a message that contains Diffie-Hellman Key
exchange payload and nonce payload from initiator.
Paper 2
1 (a) (i) an active on-path attacker-modification, fabrication, sinkhole, Sybil,
spoofing
(ii) A passive on-path attacker-Eavesdropping, traffic analysis
(iii) An active off-path attacker- modification, fabrication, denial of services,
wormhole
(iii) A passive off-path attacker-Eavesdropping, traffic analysis.
1(b) (i) IP and UDP;
Both are transport layer protocols and they allow for application to application delivery
PROTOCOL Similarities Differences
IP and UDP -Both are stateless,
connectionless protocols.
-neither of both IP and UDP
provides a reliable channel
-UDP resides on the transport
layer while IP resides on
internet Layer
TCP and UDP - Both are transport layer
protocols and they allow for
application to application
delivery
-Both TCP and UDP headers
includes source and
destination port numbers
-Both TCP and UDP
encapsulate transport layer
PDUs
-TCP provides a reliable
Service while UDP does not
-TCP has error checking
functionality while UDP
does not have
-TCP is connection oriented
while UDP is connectionless
WEP and WPA -In WEP data integrity is
provided through CRC-32
while WPA it is provided
through message integrity
code
-In WEP encryption is
achieved through Rivest
Cipher 4(RC4) while in WAP
Temporal Key Integrity
Protocol(TKIP) is used for
data privacy(Encryption)
WPA and WPA2 -They both use the 4
handshaking mechanism
which is used for providing
the key management.
-WAP is possible in
deploying to both current and
previous hardware’s while
WAP2 is only possible to be
deployed in newer hardware’s
and those with NIC that is not
older than 2006
-data integrity is provided
through message integrity
code while WAP2 is provided
through Cipher block
Chaining Message
Authentication Code(CBS-
MAC)
TCP Authentication Option
and IPsec Authentication
Header
-They are both derived master
key tuple (MTP).
-TCP-AO uses the TCP
options in providing the
message authentication while
AH is used for providing
integrity services.
IPsec Authentication Header
and IPsec Encapsulating
Security Payload
- Both provides data
origin authentication
and data integrity
services
AH protocol uses sequence
numbers to detect replays
while ESP uses symmetric
encryption and MACs based
on secret keys that are shared
between endpoints.
1 (c) (i) DNS is the Domain Name System that is used for providing a structured way that is
used in naming internet resources, also another purpose is maintaining a map between the
internet protocol addresses and the domain names assigned and Lastly is that the browser
may use DNS in determining the IP address of specific web server for a given Uniform
resource Locator. The sender may use DNS in determining the IP address of the
recipient’s name server from the receiver email address.
(ii) DNS query-response protocol – DNS offer provision of a request response protocol
that enables the hosts in requesting the ip addresses for any known domain name. This
Protocol(TKIP) is used for
data privacy(Encryption)
WPA and WPA2 -They both use the 4
handshaking mechanism
which is used for providing
the key management.
-WAP is possible in
deploying to both current and
previous hardware’s while
WAP2 is only possible to be
deployed in newer hardware’s
and those with NIC that is not
older than 2006
-data integrity is provided
through message integrity
code while WAP2 is provided
through Cipher block
Chaining Message
Authentication Code(CBS-
MAC)
TCP Authentication Option
and IPsec Authentication
Header
-They are both derived master
key tuple (MTP).
-TCP-AO uses the TCP
options in providing the
message authentication while
AH is used for providing
integrity services.
IPsec Authentication Header
and IPsec Encapsulating
Security Payload
- Both provides data
origin authentication
and data integrity
services
AH protocol uses sequence
numbers to detect replays
while ESP uses symmetric
encryption and MACs based
on secret keys that are shared
between endpoints.
1 (c) (i) DNS is the Domain Name System that is used for providing a structured way that is
used in naming internet resources, also another purpose is maintaining a map between the
internet protocol addresses and the domain names assigned and Lastly is that the browser
may use DNS in determining the IP address of specific web server for a given Uniform
resource Locator. The sender may use DNS in determining the IP address of the
recipient’s name server from the receiver email address.
(ii) DNS query-response protocol – DNS offer provision of a request response protocol
that enables the hosts in requesting the ip addresses for any known domain name. This
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
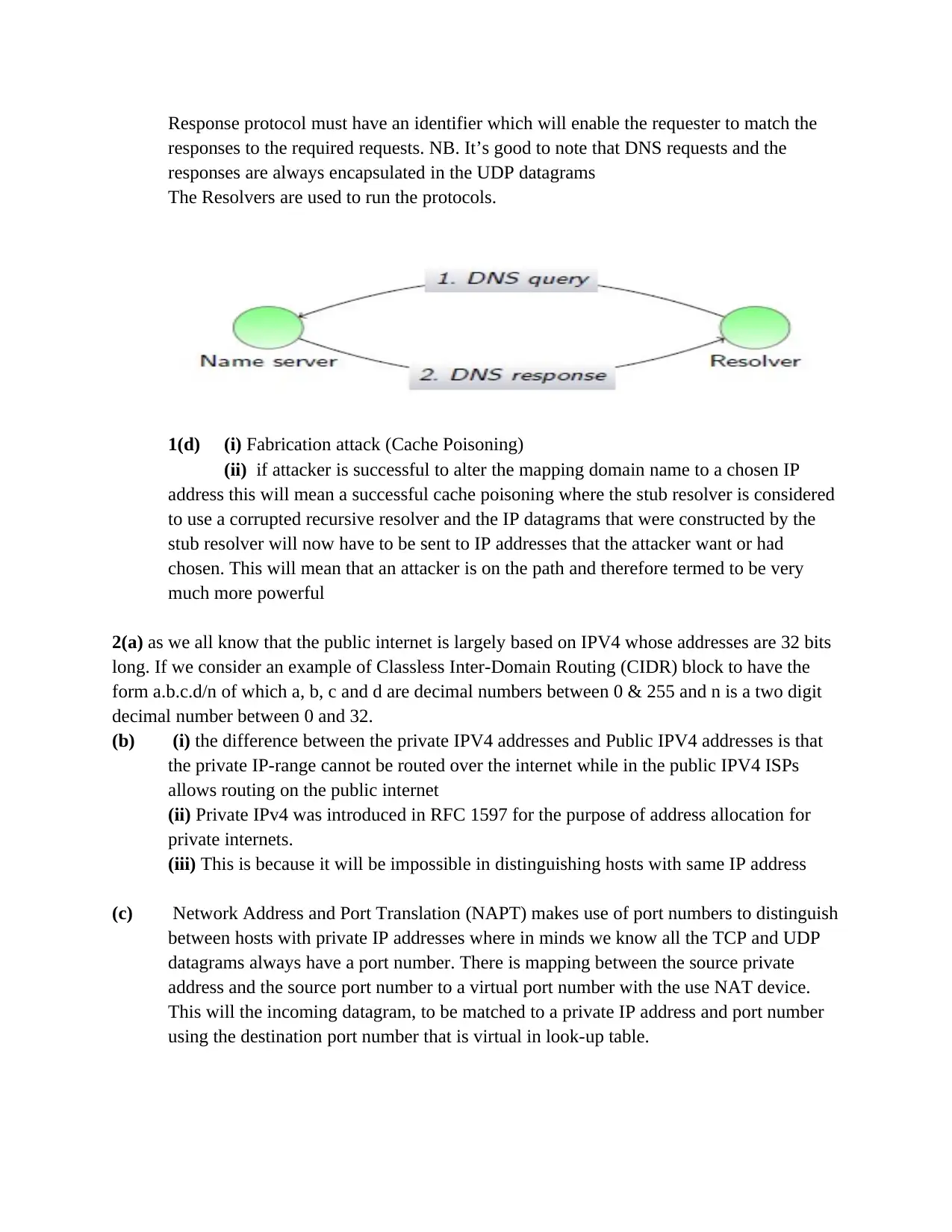
Response protocol must have an identifier which will enable the requester to match the
responses to the required requests. NB. It’s good to note that DNS requests and the
responses are always encapsulated in the UDP datagrams
The Resolvers are used to run the protocols.
1(d) (i) Fabrication attack (Cache Poisoning)
(ii) if attacker is successful to alter the mapping domain name to a chosen IP
address this will mean a successful cache poisoning where the stub resolver is considered
to use a corrupted recursive resolver and the IP datagrams that were constructed by the
stub resolver will now have to be sent to IP addresses that the attacker want or had
chosen. This will mean that an attacker is on the path and therefore termed to be very
much more powerful
2(a) as we all know that the public internet is largely based on IPV4 whose addresses are 32 bits
long. If we consider an example of Classless Inter-Domain Routing (CIDR) block to have the
form a.b.c.d/n of which a, b, c and d are decimal numbers between 0 & 255 and n is a two digit
decimal number between 0 and 32.
(b) (i) the difference between the private IPV4 addresses and Public IPV4 addresses is that
the private IP-range cannot be routed over the internet while in the public IPV4 ISPs
allows routing on the public internet
(ii) Private IPv4 was introduced in RFC 1597 for the purpose of address allocation for
private internets.
(iii) This is because it will be impossible in distinguishing hosts with same IP address
(c) Network Address and Port Translation (NAPT) makes use of port numbers to distinguish
between hosts with private IP addresses where in minds we know all the TCP and UDP
datagrams always have a port number. There is mapping between the source private
address and the source port number to a virtual port number with the use NAT device.
This will the incoming datagram, to be matched to a private IP address and port number
using the destination port number that is virtual in look-up table.
responses to the required requests. NB. It’s good to note that DNS requests and the
responses are always encapsulated in the UDP datagrams
The Resolvers are used to run the protocols.
1(d) (i) Fabrication attack (Cache Poisoning)
(ii) if attacker is successful to alter the mapping domain name to a chosen IP
address this will mean a successful cache poisoning where the stub resolver is considered
to use a corrupted recursive resolver and the IP datagrams that were constructed by the
stub resolver will now have to be sent to IP addresses that the attacker want or had
chosen. This will mean that an attacker is on the path and therefore termed to be very
much more powerful
2(a) as we all know that the public internet is largely based on IPV4 whose addresses are 32 bits
long. If we consider an example of Classless Inter-Domain Routing (CIDR) block to have the
form a.b.c.d/n of which a, b, c and d are decimal numbers between 0 & 255 and n is a two digit
decimal number between 0 and 32.
(b) (i) the difference between the private IPV4 addresses and Public IPV4 addresses is that
the private IP-range cannot be routed over the internet while in the public IPV4 ISPs
allows routing on the public internet
(ii) Private IPv4 was introduced in RFC 1597 for the purpose of address allocation for
private internets.
(iii) This is because it will be impossible in distinguishing hosts with same IP address
(c) Network Address and Port Translation (NAPT) makes use of port numbers to distinguish
between hosts with private IP addresses where in minds we know all the TCP and UDP
datagrams always have a port number. There is mapping between the source private
address and the source port number to a virtual port number with the use NAT device.
This will the incoming datagram, to be matched to a private IP address and port number
using the destination port number that is virtual in look-up table.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The technique is an IP tunneling that modifies IP datagrams as they try to pass through a
gateway. Since IP tunneling works by encapsulating where the gateway at the edge of the
source network encapsulating the IP datagram in an outer datagram. In providing the
confidentiality the gateways must encrypt and decrypt the encapsulated IP packets where
in this manner we can provide the confidentiality service and the integrity of the data
built on a virtual private network. This is often made possible by implementation of IPsec
and IKE by gateways in negotiating security associations and controlling which
datagrams are to be processed using IPsec.
(d) IP spoofing is the underlying cause of a significant proportion of the security problems
associated `with the Internet because all transport and application layer messages are
encapsulated in IP datagrams.
(e) The aim of smurf attack is to exhaust processing resources of any victim by forcing it to
processing the ICMP messages. The following example shows the working of a smurf
attack.
The attack encapsulates echo requests in a spoofed IP datagram. The attacker M sends
ICMP requests to B that appear to come from the victim’s IP address By doing this
repeatedly, M can cause A to be flooded by ICMP echo reply messages causing a denial
of service
(f) Ingress filtering is known as RFC 2827 attempts reducing of IP spoofing by identifying
and dropping packets that have been spoofed by inspecting the source address.
In egress filtering prevention of IP spoofing which is known as RFC 3013 the IP
datagrams sent to a customer should be filtered in that the destination address in the
customer’s range of IP addresses. In this case a datagram should be dropped if that source
address belongs to the customer’s range of IP addresses. Lastly is the Reverse Path
Forwarding which is known as RFC 3704 and is termed to be a more complex form of
ingress filtering? Routes between two Internet hosts are not necessarily symmetrical. This
is particularly true for hosts in multi-homed ASes. In this case, RPF examines each
possible interface on which a datagram could be forwarded The datagram is dropped if
none of these interfaces match the one on which the datagram was received
3 (a) These are techniques that can be used to prevent and detect problems that arise in network
communications.
(b) The procedure below explains how the stop-and-wait protocol in constructing
communications channels that are reliable.
gateway. Since IP tunneling works by encapsulating where the gateway at the edge of the
source network encapsulating the IP datagram in an outer datagram. In providing the
confidentiality the gateways must encrypt and decrypt the encapsulated IP packets where
in this manner we can provide the confidentiality service and the integrity of the data
built on a virtual private network. This is often made possible by implementation of IPsec
and IKE by gateways in negotiating security associations and controlling which
datagrams are to be processed using IPsec.
(d) IP spoofing is the underlying cause of a significant proportion of the security problems
associated `with the Internet because all transport and application layer messages are
encapsulated in IP datagrams.
(e) The aim of smurf attack is to exhaust processing resources of any victim by forcing it to
processing the ICMP messages. The following example shows the working of a smurf
attack.
The attack encapsulates echo requests in a spoofed IP datagram. The attacker M sends
ICMP requests to B that appear to come from the victim’s IP address By doing this
repeatedly, M can cause A to be flooded by ICMP echo reply messages causing a denial
of service
(f) Ingress filtering is known as RFC 2827 attempts reducing of IP spoofing by identifying
and dropping packets that have been spoofed by inspecting the source address.
In egress filtering prevention of IP spoofing which is known as RFC 3013 the IP
datagrams sent to a customer should be filtered in that the destination address in the
customer’s range of IP addresses. In this case a datagram should be dropped if that source
address belongs to the customer’s range of IP addresses. Lastly is the Reverse Path
Forwarding which is known as RFC 3704 and is termed to be a more complex form of
ingress filtering? Routes between two Internet hosts are not necessarily symmetrical. This
is particularly true for hosts in multi-homed ASes. In this case, RPF examines each
possible interface on which a datagram could be forwarded The datagram is dropped if
none of these interfaces match the one on which the datagram was received
3 (a) These are techniques that can be used to prevent and detect problems that arise in network
communications.
(b) The procedure below explains how the stop-and-wait protocol in constructing
communications channels that are reliable.

The stop-and-wait protocol provides a reliable of a one-way channel where the sender transmits
an acknowledgement if the message has arrived and the checksum has been verified. The sender
must wait for an acknowledgement before he or she sends the next package or message. We note
that no acknowledgement will be received if the message is not received. If there is no
acknowledgement is received during the time given then the sender will have to re-transmit the
message again. The stop-and-wait protocol guarantees delivery (and the messages are received in
order because they are sent one at a time).
(c) The sender transmits a synchronization message to the receiver with an initial sequence
number. The receiver returns an acknowledgement which includes the initial sequence number
The acknowledgement has the effect of confirming that both sender and receiver know the initial
sequence number the initial sequence number is an example of shared state once the sender
receives the acknowledgement it will send the first message containing application data using the
next sequence number
(d) The poor design and implementations of important protocols have led to many security
breaches where Lack of origin authentication in IP has led to denial-of-service attacks against
innocent hosts
(e)
The use of SYN cookies means that some information that would normally held in the
half-open connections table is lost. The table would record other parameters used in a
TCP connection, such as window size. Hence there are some (minor) limitations on the
type of TCP connections that can be established using SYN cookies However, SYN
cookies do mean that a server can continue to operate even when there is a SYN flooding
attack. TCP Cookies Transactions is an extension of SYN cookies (RFC 6013).TCPCT
avoids the limitations of SYN cookies but it requires the initiator and responder to
support TCPCT
SYN cookies are used in the IKE handshake to render certain kinds of denial-of-service
attacks ineffective roughly speaking, the first two messages in an IKE handshake are
stateless. The responder only commits resources to an IKE handshake once an
appropriate response to the SYN cookie has been received
4 (a) The entity authentication requires the data origin authentication to confirm the identity
that is provided by the MAC where freshness prevents replays of old authentication messages
(provided by using a different ISN for each run of the protocol. In this context of entity
authentication, the ISN is usually called a nonce (a number used once). This entity authentication
protocols are often known as challenge-response protocols. The verifier sends a nonce to the c12
(b) If an attacker M wants to impersonate A to B, M first runs the protocol with B in order to
obtain the current challenge, n say, from which M deduces the next challenge, n + 1. The
attacker then runs the protocol a second time, this time with A and pretending to be B. During
an acknowledgement if the message has arrived and the checksum has been verified. The sender
must wait for an acknowledgement before he or she sends the next package or message. We note
that no acknowledgement will be received if the message is not received. If there is no
acknowledgement is received during the time given then the sender will have to re-transmit the
message again. The stop-and-wait protocol guarantees delivery (and the messages are received in
order because they are sent one at a time).
(c) The sender transmits a synchronization message to the receiver with an initial sequence
number. The receiver returns an acknowledgement which includes the initial sequence number
The acknowledgement has the effect of confirming that both sender and receiver know the initial
sequence number the initial sequence number is an example of shared state once the sender
receives the acknowledgement it will send the first message containing application data using the
next sequence number
(d) The poor design and implementations of important protocols have led to many security
breaches where Lack of origin authentication in IP has led to denial-of-service attacks against
innocent hosts
(e)
The use of SYN cookies means that some information that would normally held in the
half-open connections table is lost. The table would record other parameters used in a
TCP connection, such as window size. Hence there are some (minor) limitations on the
type of TCP connections that can be established using SYN cookies However, SYN
cookies do mean that a server can continue to operate even when there is a SYN flooding
attack. TCP Cookies Transactions is an extension of SYN cookies (RFC 6013).TCPCT
avoids the limitations of SYN cookies but it requires the initiator and responder to
support TCPCT
SYN cookies are used in the IKE handshake to render certain kinds of denial-of-service
attacks ineffective roughly speaking, the first two messages in an IKE handshake are
stateless. The responder only commits resources to an IKE handshake once an
appropriate response to the SYN cookie has been received
4 (a) The entity authentication requires the data origin authentication to confirm the identity
that is provided by the MAC where freshness prevents replays of old authentication messages
(provided by using a different ISN for each run of the protocol. In this context of entity
authentication, the ISN is usually called a nonce (a number used once). This entity authentication
protocols are often known as challenge-response protocols. The verifier sends a nonce to the c12
(b) If an attacker M wants to impersonate A to B, M first runs the protocol with B in order to
obtain the current challenge, n say, from which M deduces the next challenge, n + 1. The
attacker then runs the protocol a second time, this time with A and pretending to be B. During
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

this protocol run, M chooses n + 1 as his challenge to A. A, an honest protocol participant will
encrypt n + 1 using the key she shares with B. Finally, M runs the protocol a third time, this time
with B and pretending to be A. When B sends the expected challenge, n + 1, M replays the value
received from A in the previous run of the protocol. Hence, M is able to trick B into believing
that he is communicating with A. Note that this attack works whenever B uses a predictable
method of generating n.
The trouble with an 128-bit challenge is that, even if it is chosen at random, it will repeat rather
quickly, thus giving B the opportunity to replay the response to an earlier challenge.
(c) This is because the CRCs and steam ciphers do not mix where RC4 XORs is the keystream
with the plaintext. When there is change in the plaintext means that the ICV field (computed
Using CRC-32) is incorrect. The structure of CRC-32 means that it is possible to predict the
effect on the ICV of a bit changing in the plaintext. The attacker can modify the encrypted ICV
for the modified plaintext, in such a way that the modified ICV is the CRC-32 value
for the modified plaintext. In other words, the attacker can fool the recipient into believing a
modified message is the one that was sent.
(d) Example
1. c → v : Hi
2. v → c : {n ‖‖k}cv (encrypt challenge and key using v’s public key)
3. c → v :‹ n ‖v›cv (compute MAC using k)
In the case of private-public key pairs, it is impractical to use asymmetric cipher systems for bulk
encryption. Thus we often use asymmetric cryptography only to establish a shared secret.
(e) The idea is to ensure that successful password guessing requires the
attacker to be on-line, rather than off-line. The generic design of an EKE protocol uses
asymmetric cryptography to generate a fresh, shared secret k
the long-term (password-based) key kcv to preserve the confidentiality of k
k to run a challenge-response protocol
EKE reveals a plaintext-ciphertext pair to an eavesdropper, but it is encrypted
with k rather than kcv. This is in contrast to other entity authentication protocols
we have seen
(f) Suppose the attacker tries to guess the password (and hence Kir ). Then the decryption of
messages 1 and 2 only reveals DH values and the attacker has no way of knowing whether these
are the DH values chosen by the initiator and responder. Alternatively, the attacker can try to
guess k, but this only works for a particular run of the protocol (and has a very low chance of
success in any case).
Of course, the attacker can try an on-line attack by impersonating I, guessing Kir and selecting x.
If the attacker guesses Kir correctly then he will be able to recover gy and compute k = gxy .
encrypt n + 1 using the key she shares with B. Finally, M runs the protocol a third time, this time
with B and pretending to be A. When B sends the expected challenge, n + 1, M replays the value
received from A in the previous run of the protocol. Hence, M is able to trick B into believing
that he is communicating with A. Note that this attack works whenever B uses a predictable
method of generating n.
The trouble with an 128-bit challenge is that, even if it is chosen at random, it will repeat rather
quickly, thus giving B the opportunity to replay the response to an earlier challenge.
(c) This is because the CRCs and steam ciphers do not mix where RC4 XORs is the keystream
with the plaintext. When there is change in the plaintext means that the ICV field (computed
Using CRC-32) is incorrect. The structure of CRC-32 means that it is possible to predict the
effect on the ICV of a bit changing in the plaintext. The attacker can modify the encrypted ICV
for the modified plaintext, in such a way that the modified ICV is the CRC-32 value
for the modified plaintext. In other words, the attacker can fool the recipient into believing a
modified message is the one that was sent.
(d) Example
1. c → v : Hi
2. v → c : {n ‖‖k}cv (encrypt challenge and key using v’s public key)
3. c → v :‹ n ‖v›cv (compute MAC using k)
In the case of private-public key pairs, it is impractical to use asymmetric cipher systems for bulk
encryption. Thus we often use asymmetric cryptography only to establish a shared secret.
(e) The idea is to ensure that successful password guessing requires the
attacker to be on-line, rather than off-line. The generic design of an EKE protocol uses
asymmetric cryptography to generate a fresh, shared secret k
the long-term (password-based) key kcv to preserve the confidentiality of k
k to run a challenge-response protocol
EKE reveals a plaintext-ciphertext pair to an eavesdropper, but it is encrypted
with k rather than kcv. This is in contrast to other entity authentication protocols
we have seen
(f) Suppose the attacker tries to guess the password (and hence Kir ). Then the decryption of
messages 1 and 2 only reveals DH values and the attacker has no way of knowing whether these
are the DH values chosen by the initiator and responder. Alternatively, the attacker can try to
guess k, but this only works for a particular run of the protocol (and has a very low chance of
success in any case).
Of course, the attacker can try an on-line attack by impersonating I, guessing Kir and selecting x.
If the attacker guesses Kir correctly then he will be able to recover gy and compute k = gxy .
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

However, the attacker has no way of determining whether he has guessed Kir correctly without
completing the protocol run. (If he has guessed correctly, then he will be authenticated as he will
be able to compute the correct response in message 4.) However, if the number of attempts to run
the authentication protocol is limited to a very small number (typically less than five), then the
likelihood of the attacker correctly guessing the password and completing the protocol run
successfully is negligible (even for weak passwords).
5 (a) Generating the TLS (Record) PDU
1. The (SSL) sequence number is appended to the application layer data and the MAC
value is computed. The sequence number is initialized during the TLS handshake
protocol
2. The resulting MAC is appended to the application layer data and encrypted
3. Note that the sequence number is not part of the input to the encryption algorithm and
is not part of the SSL/TSL PDU
(b) Processing the Record PDU
It’s good to note that the SSL/TLS software at the receiver side should receive Record PDUs in
exactly the same order as they were produced because TCP is reliable .This means that the
sender and receiver can maintain independent, synchronized copies of the (TLS) sequence
number used in the MAC computation then Hence, the recipient
1. Decrypts the Record PDU (recovering the application data and the MAC)
2. Reconstructs the input to the MAC algorithm, using its copy of the sequence number and the
application data
3. Recomputes the MAC and compares with the decrypted MAC
The recipient will “tear down” an SSL/TLS connection if MAC verification fails
(c)
If the attacker modifies the application data, then the modification will be detected by
SSL/TLS (because MAC verification will fail).
If the attacker replays a TCP segment, then it will be dropped by TCP as a duplicate
segment.
If the attacker modifies the sequence number without modifying the checksum in the
TCP header, then checksum verification will fail during TCP processing and the segment
will be dropped.
If the attacker modifies the sequence number and the checksum then it may not be
dropped by TCP. However, MAC verification will fail because the segment will be
appear in a different order to the sequence numbers used to compute the MACs.
(d) The idea behind this is that the HTTP and BGP will be used in specifying the application
interaction with network. It does not matter whether sequence numbers are encrypted or not.
Why? Sequence numbers have no intrinsic value, so confidentiality is not required and they
completing the protocol run. (If he has guessed correctly, then he will be authenticated as he will
be able to compute the correct response in message 4.) However, if the number of attempts to run
the authentication protocol is limited to a very small number (typically less than five), then the
likelihood of the attacker correctly guessing the password and completing the protocol run
successfully is negligible (even for weak passwords).
5 (a) Generating the TLS (Record) PDU
1. The (SSL) sequence number is appended to the application layer data and the MAC
value is computed. The sequence number is initialized during the TLS handshake
protocol
2. The resulting MAC is appended to the application layer data and encrypted
3. Note that the sequence number is not part of the input to the encryption algorithm and
is not part of the SSL/TSL PDU
(b) Processing the Record PDU
It’s good to note that the SSL/TLS software at the receiver side should receive Record PDUs in
exactly the same order as they were produced because TCP is reliable .This means that the
sender and receiver can maintain independent, synchronized copies of the (TLS) sequence
number used in the MAC computation then Hence, the recipient
1. Decrypts the Record PDU (recovering the application data and the MAC)
2. Reconstructs the input to the MAC algorithm, using its copy of the sequence number and the
application data
3. Recomputes the MAC and compares with the decrypted MAC
The recipient will “tear down” an SSL/TLS connection if MAC verification fails
(c)
If the attacker modifies the application data, then the modification will be detected by
SSL/TLS (because MAC verification will fail).
If the attacker replays a TCP segment, then it will be dropped by TCP as a duplicate
segment.
If the attacker modifies the sequence number without modifying the checksum in the
TCP header, then checksum verification will fail during TCP processing and the segment
will be dropped.
If the attacker modifies the sequence number and the checksum then it may not be
dropped by TCP. However, MAC verification will fail because the segment will be
appear in a different order to the sequence numbers used to compute the MACs.
(d) The idea behind this is that the HTTP and BGP will be used in specifying the application
interaction with network. It does not matter whether sequence numbers are encrypted or not.
Why? Sequence numbers have no intrinsic value, so confidentiality is not required and they

don’t need to be encrypted. Sequence numbers are only relevant to end devices, not intermediate
devices, so they can be encrypted. Sequence numbers must be integrity protected. Why? If
sequence numbers can be modified, the data chunks may be reassembled in the wrong order.
devices, so they can be encrypted. Sequence numbers must be integrity protected. Why? If
sequence numbers can be modified, the data chunks may be reassembled in the wrong order.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





