Comprehensive Analysis: Network Security Protocols and Firewalls
VerifiedAdded on 2023/06/14
|13
|812
|292
Report
AI Summary
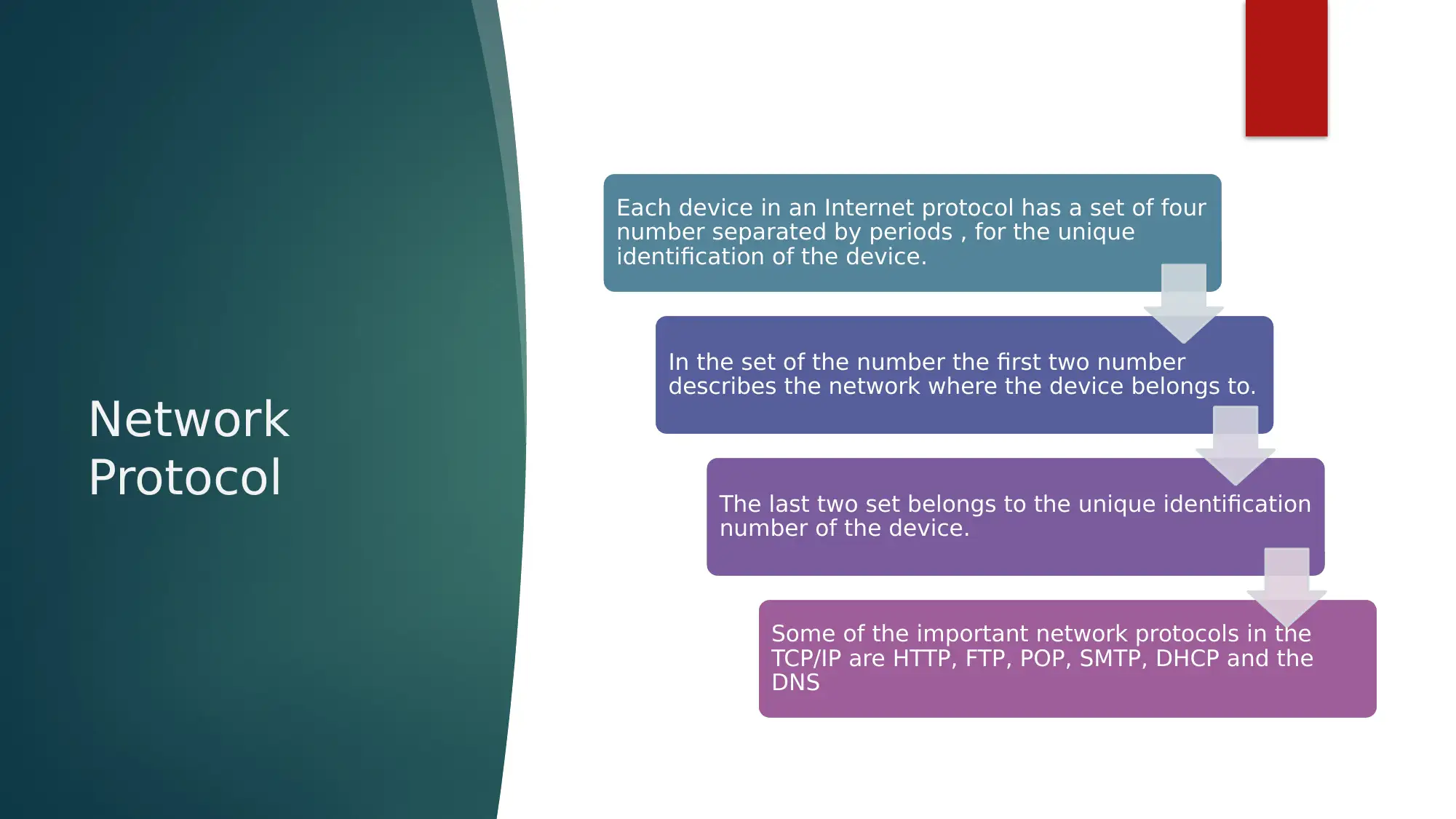
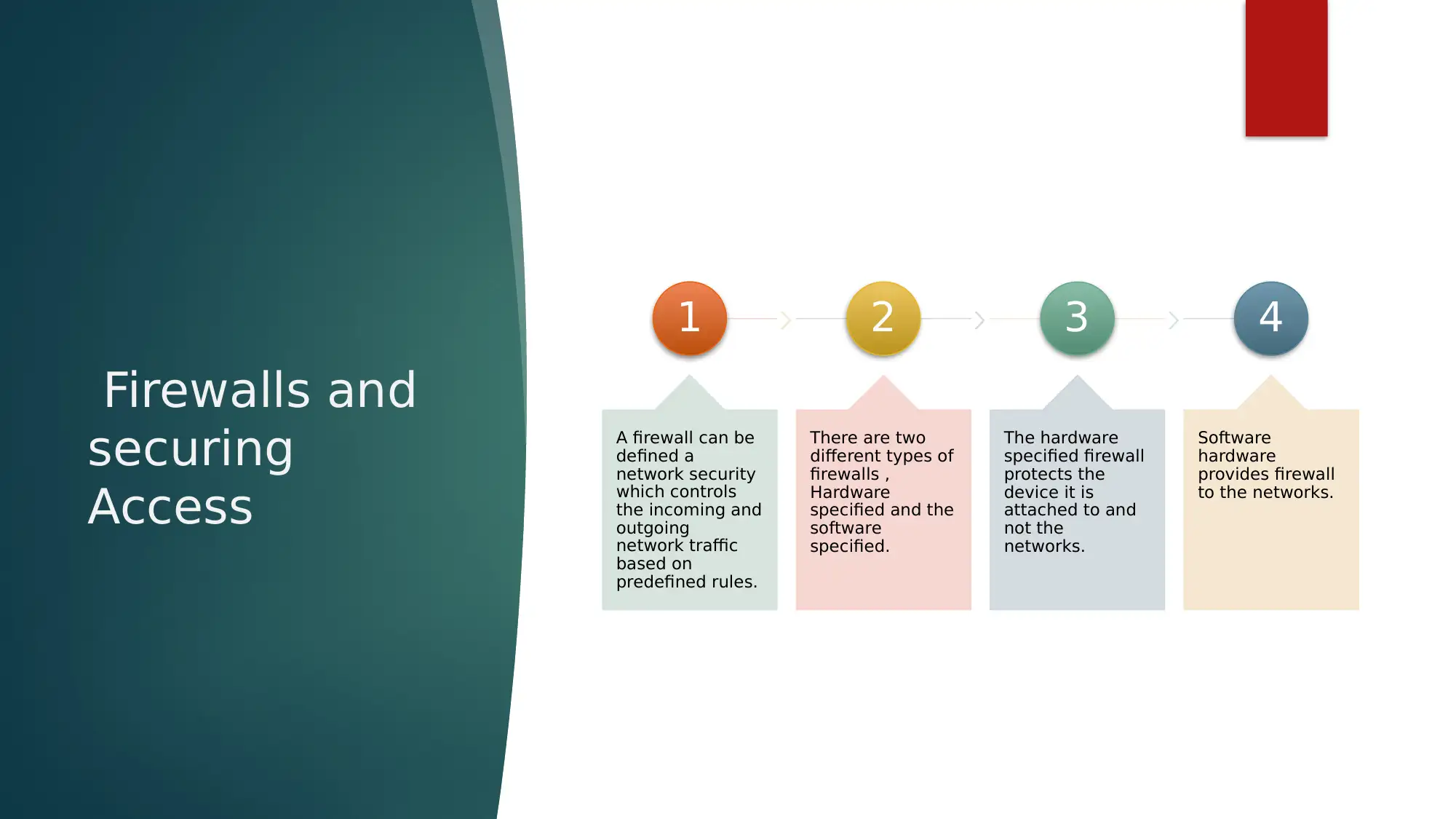
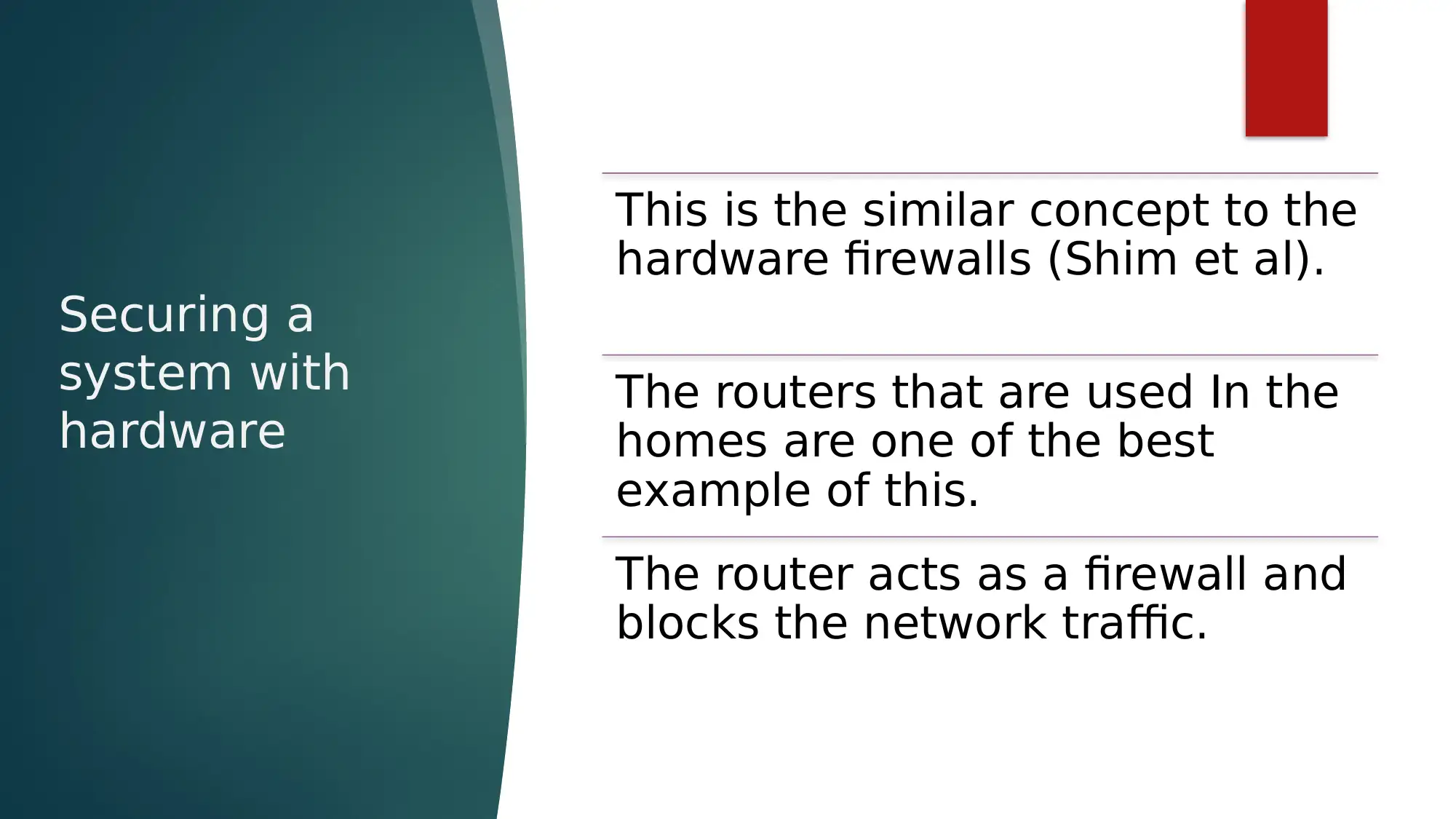
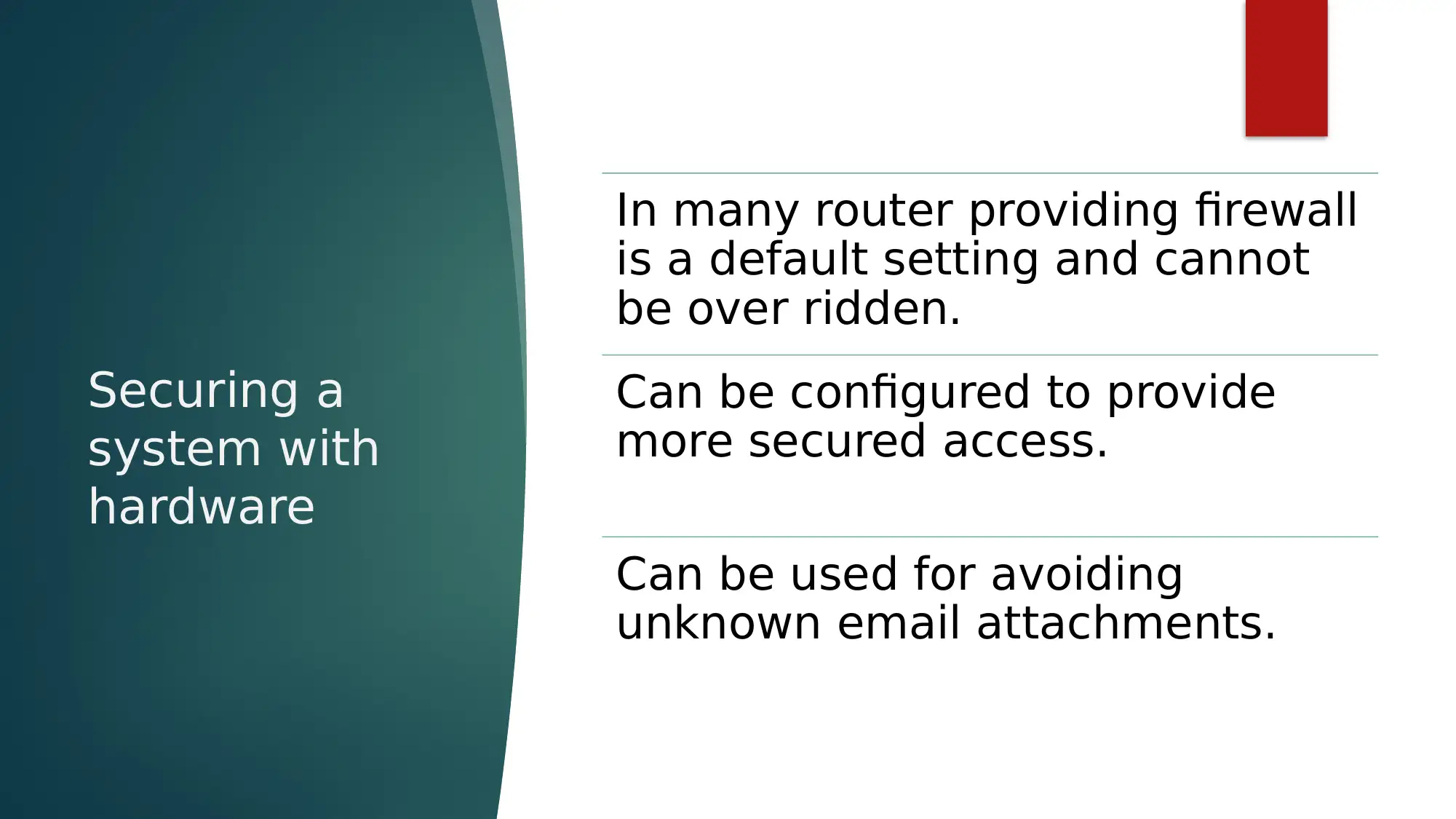
This report provides an overview of network security, emphasizing the crucial role of network protocols, particularly the TCP/IP stack, in ensuring secure data transmission. It details how TCP manages data packet movement and IP handles packet routing using unique device identification. The report further elaborates on firewalls as a key network security measure, discussing hardware and software implementations and their function in controlling network traffic based on predefined rules. Different types of firewalls, including packet filtering, stateful packet inspection, and application layer firewalls, are explained, highlighting their mechanisms for examining data packets and filtering traffic based on IP addresses, protocol types, and domain names. The document also touches upon securing systems with hardware, such as routers acting as firewalls, and references several research papers to support its discussion on programmable firewalls, online examination security, TCP network protocol learning, and the impact of hardware impairments on physical layer security. Desklib offers additional resources and solved assignments for students seeking to deepen their understanding of network security.
1 out of 13















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)