Network Security 1 Assignment: Threat Identification and Mitigation
VerifiedAdded on 2023/06/04
|9
|1824
|206
Report
AI Summary
This report presents an analysis of network security threats, focusing on the use of Nmap and Metasploit for vulnerability assessment and penetration testing. The assignment begins with an introduction to network security, emphasizing the importance of identifying and mitigating vulnerabilities to prevent cyberattacks. A literature review provides context by discussing the impact of network security breaches and outlining the stages of a cyberattack, including information gathering, which is the primary focus of the practical exercise. The report details the use of Nmap for network scanning, including host discovery, port scanning, service and OS detection, and the identification of open ports. The practical application of Nmap identified an Android phone with an outdated dnsmasq software. The report then describes the use of Metasploit to confirm the findings of Nmap. The report concludes with a discussion of threat mitigation strategies, specifically addressing the vulnerabilities associated with the outdated dnsmasq software, suggesting software patching or updates as solutions. The report highlights the critical role of reconnaissance tools in ensuring maximum network security and provides references to support the findings.

Network Security 1
[Name]
[Institution]
[Name]
[Institution]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Network security is a critical component of any firm, especially with the rising incidences of
cyber espionage. Deploying and maintaining the best security exposure requires that a firm
understands vulnerabilities that can be exploited on its network, and take mitigation measures
to avoid being a victim of a cyber attack. To understand how well a network and computers
on the network are secured, it is important to carry out security scans - at a minimum - or a
full penetration testing.
A number of tools can be used to scan a network for vulnerabilities. Key among them
include; Open VAS,TCPdump, Metasploit, Nmap, PRTG and GFI LanGuard. For this
assignment, the tools of choice are Metasploit and Nmap.
Nmap or Network Mapper is a tool for network scanning; a process that entails discovery of
active hosts on a given network, as well as information about the given hosts [1]. NMAP
scans a network and builds a map of the network, informing on active hosts, operating system
running on the hosts, active ports , applications and services. Nmap maps out a network by
sending out well crafted packets to the host, and depending on the responses, the tool can tell
the active hosts [1]. The tool provides 4 basic scanning facilities; Network Mapping, Port
Scanning, Service and Version Detection and OS Detection. Additionally, the tool can be
extended to perform advanced network scanning such as evading firewalls and perimeter
defences, vulnerability detection, masking the origin of the scan and timed scans which
enable stealthy scans [1].
Information obtained through Nmap, such as open ports is used to launch attacks through the
openings. For the case where Nmap reports on software versions running on a host, the
information can be used to look for specific vulnerabilities for the given software version.
Metasploit is a tool for scanning a network or host for security vulnerabilities [2]. The tool
comes bundled with the ability to scan for vulnerabilities, exploits that can be used to
compromise the vulnerabilities, payloads for the exploits, encoders and auxiliary modules [2].
The exploits are OS and application specific, thus when a scan finds an application with a
known vulnerability, it can easily be exploited using the bundled exploits and payload [2].
Network security is a critical component of any firm, especially with the rising incidences of
cyber espionage. Deploying and maintaining the best security exposure requires that a firm
understands vulnerabilities that can be exploited on its network, and take mitigation measures
to avoid being a victim of a cyber attack. To understand how well a network and computers
on the network are secured, it is important to carry out security scans - at a minimum - or a
full penetration testing.
A number of tools can be used to scan a network for vulnerabilities. Key among them
include; Open VAS,TCPdump, Metasploit, Nmap, PRTG and GFI LanGuard. For this
assignment, the tools of choice are Metasploit and Nmap.
Nmap or Network Mapper is a tool for network scanning; a process that entails discovery of
active hosts on a given network, as well as information about the given hosts [1]. NMAP
scans a network and builds a map of the network, informing on active hosts, operating system
running on the hosts, active ports , applications and services. Nmap maps out a network by
sending out well crafted packets to the host, and depending on the responses, the tool can tell
the active hosts [1]. The tool provides 4 basic scanning facilities; Network Mapping, Port
Scanning, Service and Version Detection and OS Detection. Additionally, the tool can be
extended to perform advanced network scanning such as evading firewalls and perimeter
defences, vulnerability detection, masking the origin of the scan and timed scans which
enable stealthy scans [1].
Information obtained through Nmap, such as open ports is used to launch attacks through the
openings. For the case where Nmap reports on software versions running on a host, the
information can be used to look for specific vulnerabilities for the given software version.
Metasploit is a tool for scanning a network or host for security vulnerabilities [2]. The tool
comes bundled with the ability to scan for vulnerabilities, exploits that can be used to
compromise the vulnerabilities, payloads for the exploits, encoders and auxiliary modules [2].
The exploits are OS and application specific, thus when a scan finds an application with a
known vulnerability, it can easily be exploited using the bundled exploits and payload [2].

Literature Review
Network security attacks can be devastating to an organization, business or even a
government. Recent attacks, such as the hack on Sony Systems, attacks on Equifax - an
American credit company [3], and Ashley Madison just shows how devastating an attack can
be. In all the attacks, the hacking follows four critical steps, as outline in [4] ;
Figure 1.0 Steps in carrying out a cyber attack. [4]
Reconnaissance or Information gathering is the first stage of an attack, and is the subject of
this paper. An attacker gathers information through scanning the target, Enumerating the
services and foot printing the victim [5]. Information gathering helps in identifying network
vulnerabilities can be exploited on the target network or system. The attacker understands the
attack environment by getting information about ports, machines on the network, services
running, operating systems among other.
After gathering sufficient information, and depending on the nature of vulnerability, an
attacker can launch an attack through a number of attack vectors. The most common attack
types as outline in [6] includes; Denial-of-Service Attack, Intrusion, Virus, Worms, Trojans,
Buffer Overflow attacks, Advanced Persistent Threats, Eavesdropping and Traffic analysis
attacks.
With intrusion attacks, a hacker tries to gain unauthorized access to a computing resource, to
access or manipulate information [7]. With DoS attacks, the target is flooded with too many
bogus requests, from other compromised hosts, to take up computing resources, thus starving
genuine requests and rendering the network or computer unusable [7]. Viruses and Worms on
Network security attacks can be devastating to an organization, business or even a
government. Recent attacks, such as the hack on Sony Systems, attacks on Equifax - an
American credit company [3], and Ashley Madison just shows how devastating an attack can
be. In all the attacks, the hacking follows four critical steps, as outline in [4] ;
Figure 1.0 Steps in carrying out a cyber attack. [4]
Reconnaissance or Information gathering is the first stage of an attack, and is the subject of
this paper. An attacker gathers information through scanning the target, Enumerating the
services and foot printing the victim [5]. Information gathering helps in identifying network
vulnerabilities can be exploited on the target network or system. The attacker understands the
attack environment by getting information about ports, machines on the network, services
running, operating systems among other.
After gathering sufficient information, and depending on the nature of vulnerability, an
attacker can launch an attack through a number of attack vectors. The most common attack
types as outline in [6] includes; Denial-of-Service Attack, Intrusion, Virus, Worms, Trojans,
Buffer Overflow attacks, Advanced Persistent Threats, Eavesdropping and Traffic analysis
attacks.
With intrusion attacks, a hacker tries to gain unauthorized access to a computing resource, to
access or manipulate information [7]. With DoS attacks, the target is flooded with too many
bogus requests, from other compromised hosts, to take up computing resources, thus starving
genuine requests and rendering the network or computer unusable [7]. Viruses and Worms on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
the other hand are used to either carry out automated exploits, send information to the
attacker or used to launch attacks such as DoS attacks on other hosts [7].
Network Security Tools
Nmap
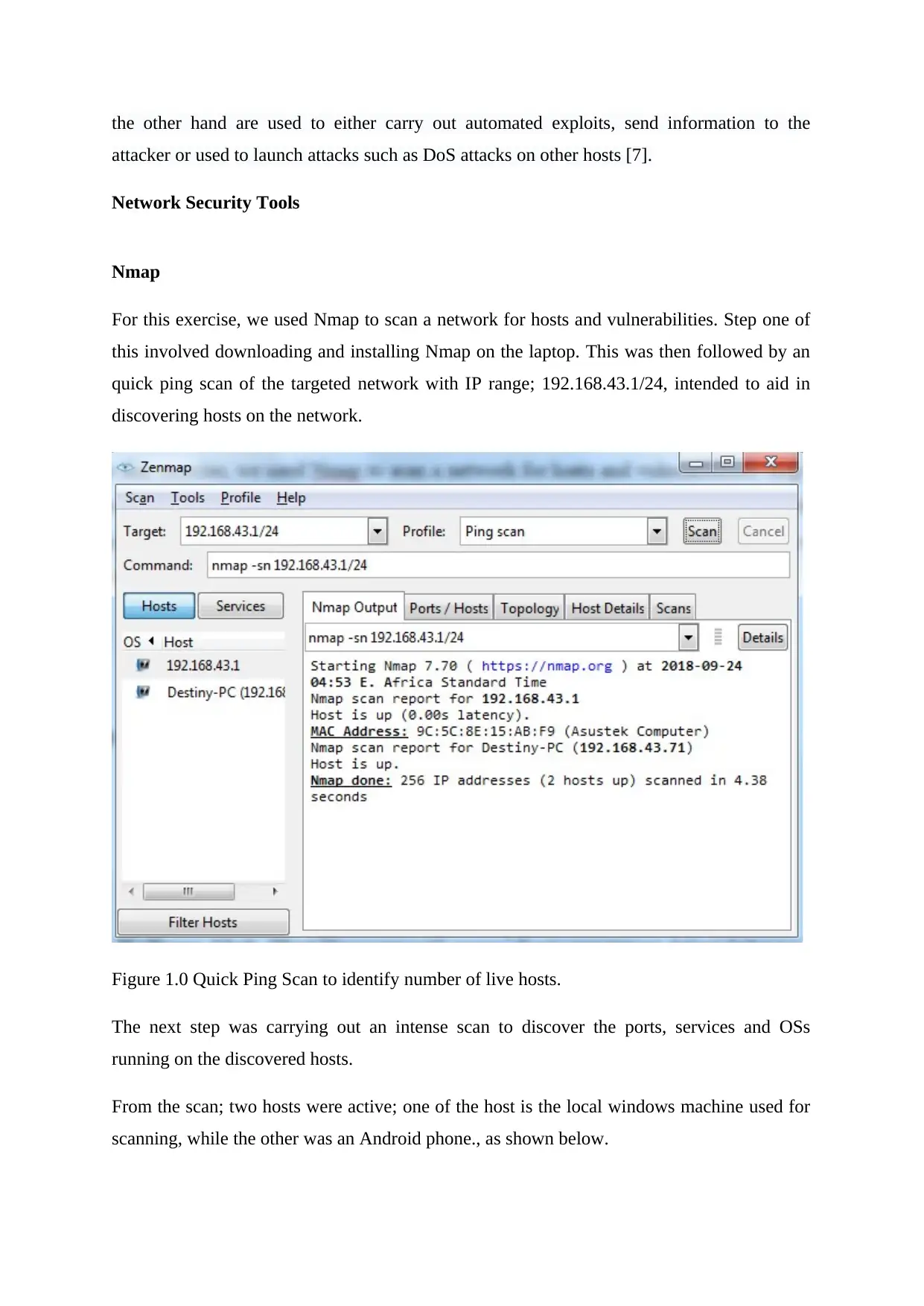
For this exercise, we used Nmap to scan a network for hosts and vulnerabilities. Step one of
this involved downloading and installing Nmap on the laptop. This was then followed by an
quick ping scan of the targeted network with IP range; 192.168.43.1/24, intended to aid in
discovering hosts on the network.
Figure 1.0 Quick Ping Scan to identify number of live hosts.
The next step was carrying out an intense scan to discover the ports, services and OSs
running on the discovered hosts.
From the scan; two hosts were active; one of the host is the local windows machine used for
scanning, while the other was an Android phone., as shown below.
attacker or used to launch attacks such as DoS attacks on other hosts [7].
Network Security Tools
Nmap
For this exercise, we used Nmap to scan a network for hosts and vulnerabilities. Step one of
this involved downloading and installing Nmap on the laptop. This was then followed by an
quick ping scan of the targeted network with IP range; 192.168.43.1/24, intended to aid in
discovering hosts on the network.
Figure 1.0 Quick Ping Scan to identify number of live hosts.
The next step was carrying out an intense scan to discover the ports, services and OSs
running on the discovered hosts.
From the scan; two hosts were active; one of the host is the local windows machine used for
scanning, while the other was an Android phone., as shown below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
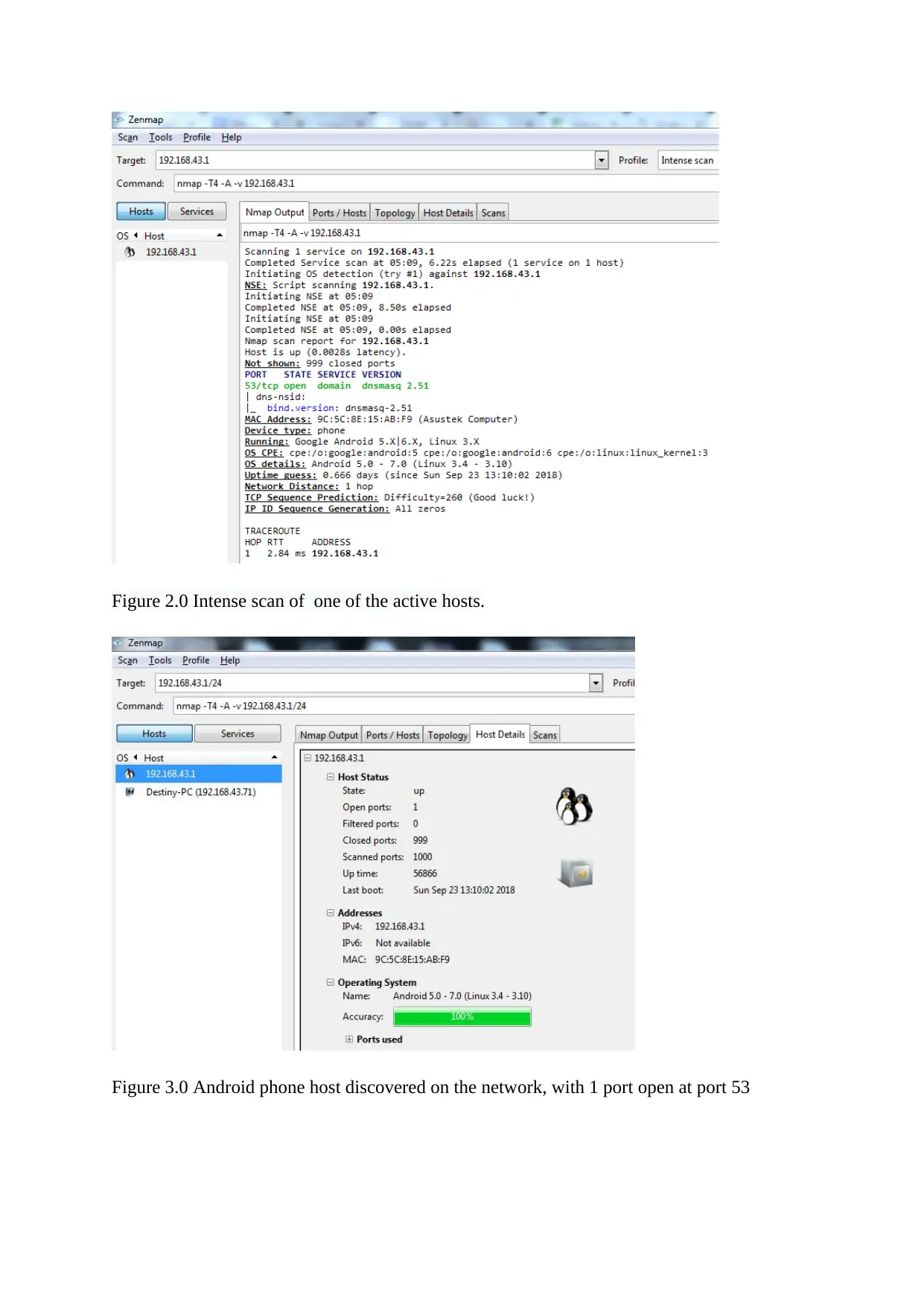
Figure 2.0 Intense scan of one of the active hosts.
Figure 3.0 Android phone host discovered on the network, with 1 port open at port 53
Figure 3.0 Android phone host discovered on the network, with 1 port open at port 53
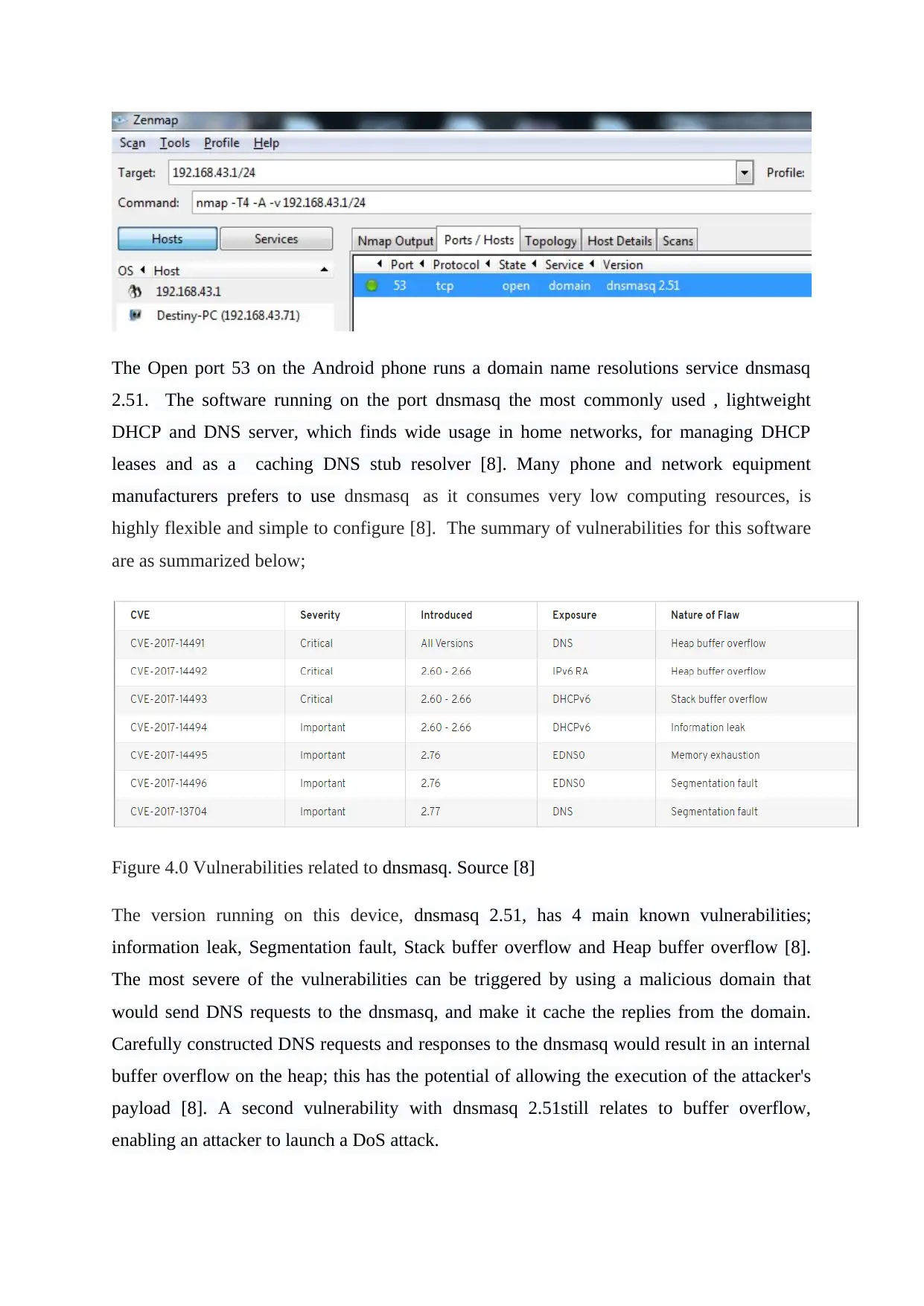
The Open port 53 on the Android phone runs a domain name resolutions service dnsmasq
2.51. The software running on the port dnsmasq the most commonly used , lightweight
DHCP and DNS server, which finds wide usage in home networks, for managing DHCP
leases and as a caching DNS stub resolver [8]. Many phone and network equipment
manufacturers prefers to use dnsmasq as it consumes very low computing resources, is
highly flexible and simple to configure [8]. The summary of vulnerabilities for this software
are as summarized below;
Figure 4.0 Vulnerabilities related to dnsmasq. Source [8]
The version running on this device, dnsmasq 2.51, has 4 main known vulnerabilities;
information leak, Segmentation fault, Stack buffer overflow and Heap buffer overflow [8].
The most severe of the vulnerabilities can be triggered by using a malicious domain that
would send DNS requests to the dnsmasq, and make it cache the replies from the domain.
Carefully constructed DNS requests and responses to the dnsmasq would result in an internal
buffer overflow on the heap; this has the potential of allowing the execution of the attacker's
payload [8]. A second vulnerability with dnsmasq 2.51still relates to buffer overflow,
enabling an attacker to launch a DoS attack.
2.51. The software running on the port dnsmasq the most commonly used , lightweight
DHCP and DNS server, which finds wide usage in home networks, for managing DHCP
leases and as a caching DNS stub resolver [8]. Many phone and network equipment
manufacturers prefers to use dnsmasq as it consumes very low computing resources, is
highly flexible and simple to configure [8]. The summary of vulnerabilities for this software
are as summarized below;
Figure 4.0 Vulnerabilities related to dnsmasq. Source [8]
The version running on this device, dnsmasq 2.51, has 4 main known vulnerabilities;
information leak, Segmentation fault, Stack buffer overflow and Heap buffer overflow [8].
The most severe of the vulnerabilities can be triggered by using a malicious domain that
would send DNS requests to the dnsmasq, and make it cache the replies from the domain.
Carefully constructed DNS requests and responses to the dnsmasq would result in an internal
buffer overflow on the heap; this has the potential of allowing the execution of the attacker's
payload [8]. A second vulnerability with dnsmasq 2.51still relates to buffer overflow,
enabling an attacker to launch a DoS attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
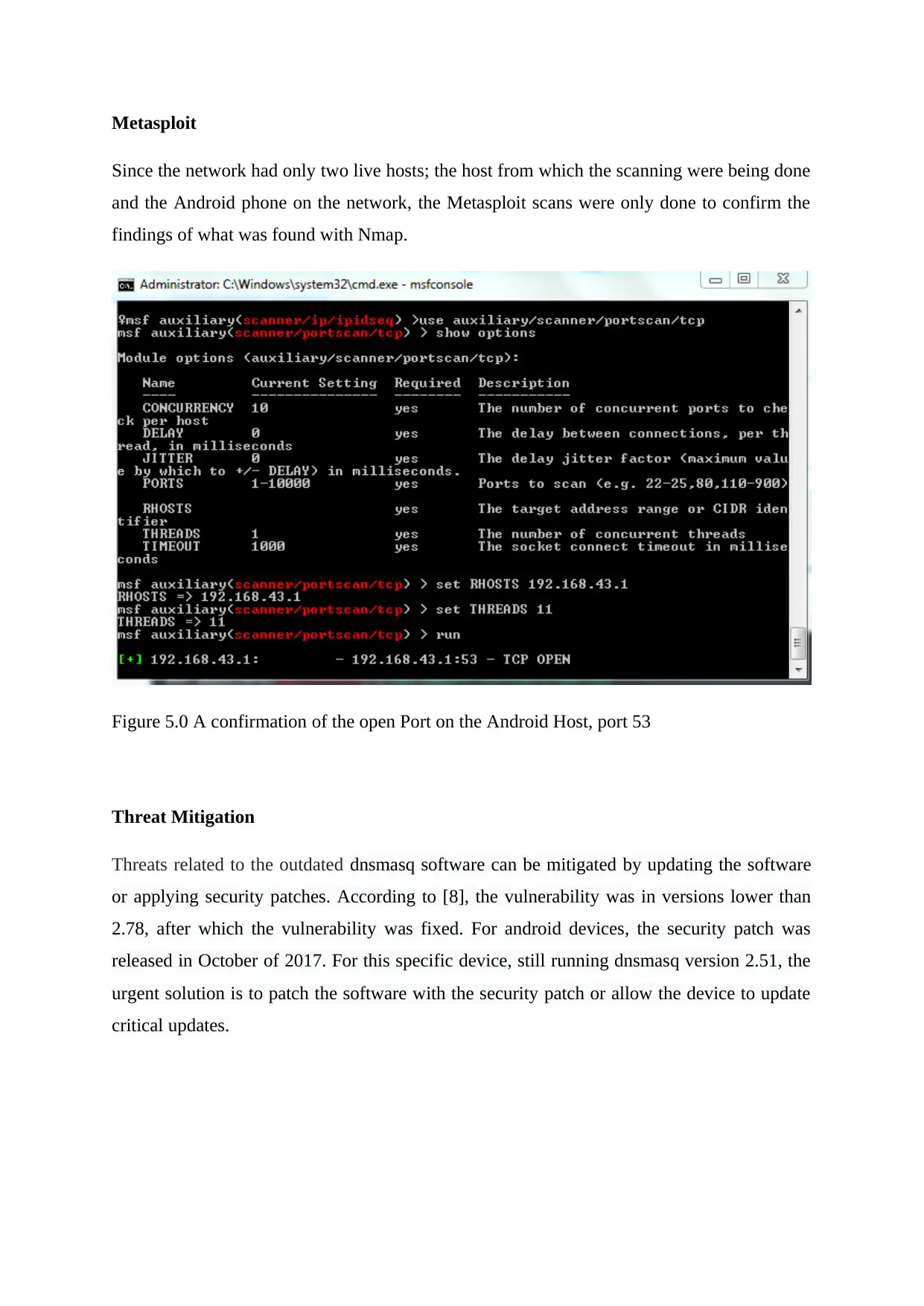
Metasploit
Since the network had only two live hosts; the host from which the scanning were being done
and the Android phone on the network, the Metasploit scans were only done to confirm the
findings of what was found with Nmap.
Figure 5.0 A confirmation of the open Port on the Android Host, port 53
Threat Mitigation
Threats related to the outdated dnsmasq software can be mitigated by updating the software
or applying security patches. According to [8], the vulnerability was in versions lower than
2.78, after which the vulnerability was fixed. For android devices, the security patch was
released in October of 2017. For this specific device, still running dnsmasq version 2.51, the
urgent solution is to patch the software with the security patch or allow the device to update
critical updates.
Since the network had only two live hosts; the host from which the scanning were being done
and the Android phone on the network, the Metasploit scans were only done to confirm the
findings of what was found with Nmap.
Figure 5.0 A confirmation of the open Port on the Android Host, port 53
Threat Mitigation
Threats related to the outdated dnsmasq software can be mitigated by updating the software
or applying security patches. According to [8], the vulnerability was in versions lower than
2.78, after which the vulnerability was fixed. For android devices, the security patch was
released in October of 2017. For this specific device, still running dnsmasq version 2.51, the
urgent solution is to patch the software with the security patch or allow the device to update
critical updates.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
This paper has presented a theoretical analysis and practical information gathering, using
Nmap and Metasploit tools. Being the first step in the hacking process, as well as being a
critical step for IT security specialists, the tools used in reconnaissance are critical in ensuring
maximum network security is achieved. Both Nmap and Metasploit aids in this endeavour by
facilitating network scanning; identifying open ports, services, software applications,
operating systems and vulnerabilities that can be exploited.
Nmap maps out a network by sending out well crafted packets to the host, and depending on
the responses, the tool can tell the active hosts. It scans a network and builds a map of the
network, informing on active hosts, operating system running on the hosts, active ports ,
applications and services. On the other hand, Metasploit scans a network or a host for
vulnerabilities. Besides providing scanning capabilities, the tool comes bundled with the
ability to scan for vulnerabilities, exploits that can be used to compromise the vulnerabilities,
payloads for the exploits, encoders and auxiliary modules.
The practical information-gathering exercise discovered a major vulnerability on an Android
phone that was serving as a Wireless Network hotspot. The outdated dnsmasq has know
vulnerabilities which can be exploited through buffer overflow attacks. The vulnerability can
however be fixed through patching of the application or updating the software.
This paper has presented a theoretical analysis and practical information gathering, using
Nmap and Metasploit tools. Being the first step in the hacking process, as well as being a
critical step for IT security specialists, the tools used in reconnaissance are critical in ensuring
maximum network security is achieved. Both Nmap and Metasploit aids in this endeavour by
facilitating network scanning; identifying open ports, services, software applications,
operating systems and vulnerabilities that can be exploited.
Nmap maps out a network by sending out well crafted packets to the host, and depending on
the responses, the tool can tell the active hosts. It scans a network and builds a map of the
network, informing on active hosts, operating system running on the hosts, active ports ,
applications and services. On the other hand, Metasploit scans a network or a host for
vulnerabilities. Besides providing scanning capabilities, the tool comes bundled with the
ability to scan for vulnerabilities, exploits that can be used to compromise the vulnerabilities,
payloads for the exploits, encoders and auxiliary modules.
The practical information-gathering exercise discovered a major vulnerability on an Android
phone that was serving as a Wireless Network hotspot. The outdated dnsmasq has know
vulnerabilities which can be exploited through buffer overflow attacks. The vulnerability can
however be fixed through patching of the application or updating the software.

References
[1] W. Mark. "Host Discovery with nmap." Exploring nmap's default behavior 1 (2002): 16.
[2] M., C. Joshua. "An analysis of the ids penetration tool: Metasploit." The InfoSec Writers
Text Library, Dec 9 (2010).
[3] A., M. Andriotis, Rapoport, and R. McMillan. "‘We’ve been breached’: Inside the
Equifax hack." Editorial], The Wall Street Journal (2017).
[4] B. Bhuyan, H. Monowar, D Bhattacharyya, and J. K. Kalita. "Surveying port scans and
their detection methodologies." The Computer Journal 54.10 (2011): 1565-1581.
[5] H, Nazrul, et al. "Network attacks: Taxonomy, tools and systems." Journal of Network
and Computer Applications 40 (2014): 307-324.
[6] H, Simon, and R Hunt. "A taxonomy of network and computer attacks." Computers &
Security 24.1 (2005): 31-43.
[7] B. Bhuyan, H. Monowar, D. K. Bhattacharyya, and J. K. Kalita. "Network anomaly
detection: methods, systems and tools." Ieee communications surveys & tutorials16.1
(2014): 303-336.
[8] RedHat, dnsmasq: Multiple Critical and Important vulnerabilities. [Online] Available at
https://access.redhat.com/security/vulnerabilities/3199382
[1] W. Mark. "Host Discovery with nmap." Exploring nmap's default behavior 1 (2002): 16.
[2] M., C. Joshua. "An analysis of the ids penetration tool: Metasploit." The InfoSec Writers
Text Library, Dec 9 (2010).
[3] A., M. Andriotis, Rapoport, and R. McMillan. "‘We’ve been breached’: Inside the
Equifax hack." Editorial], The Wall Street Journal (2017).
[4] B. Bhuyan, H. Monowar, D Bhattacharyya, and J. K. Kalita. "Surveying port scans and
their detection methodologies." The Computer Journal 54.10 (2011): 1565-1581.
[5] H, Nazrul, et al. "Network attacks: Taxonomy, tools and systems." Journal of Network
and Computer Applications 40 (2014): 307-324.
[6] H, Simon, and R Hunt. "A taxonomy of network and computer attacks." Computers &
Security 24.1 (2005): 31-43.
[7] B. Bhuyan, H. Monowar, D. K. Bhattacharyya, and J. K. Kalita. "Network anomaly
detection: methods, systems and tools." Ieee communications surveys & tutorials16.1
(2014): 303-336.
[8] RedHat, dnsmasq: Multiple Critical and Important vulnerabilities. [Online] Available at
https://access.redhat.com/security/vulnerabilities/3199382
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



