Cyber Security Solutions: Scams, Malware Prevention and Hacking Tools
VerifiedAdded on 2023/06/11
|12
|2762
|352
Homework Assignment
AI Summary
This assignment delves into various aspects of cyber security, starting with an overview of prevalent internet scams such as bank loan scams, lottery scams, hitman scams, and 'make money fast' scams, highlighting their deceptive tactics. It then discusses the features and security settings of Google Chrome, emphasizing incognito mode, task manager, dynamic tabs, and safe browsing options. The assignment further explores different types of malware, including ransomware, rootkits, Trojan horses, and viruses, detailing methods for their prevention through anti-malware software, regular updates, and cautious downloading practices. Denial of Service attacks, including buffer overflow and DDoS attacks, are explained, followed by a proposed network design for malware protection. The study also examines hacking tools like Wireshark, Yersinia, and Eraser, and concludes with an overview of symmetric cryptography methods for securing networks. Desklib offers a wealth of similar solved assignments and past papers for students.

Running head: CYBER SECURITY
CYBER SECURITY
[Name of the Student]
[Name of the University]
[Author note]
CYBER SECURITY
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 1:
A. Some of the popular Internet scams have been listed below:
Bank loan or credit card scam: This type of scam is very much common and in this
type of scam the users are guaranteed that they would be getting a huge amount of
money which has already been pre-approved by the bank. Though it may seem
unlikely for people to get trapped by this scam, there’s still a big number of people
who lost money by paying the “mandatory” processing fees required by the
scammers.
Lottery scam: This can be considered as another classic internet scam which is a very
old technique of scam. This type of scam also come from the emails where the user is
sent an email saying that they have won a huge amount of money in lottery and for
claiming that price there is a need of paying some small fees.
Hitman scam: this is considered as one of the frequent internet scam which is
associated with sending of threatening email for the purpose of extorting money from
the user. This type of scam generally occurs in various forms which might include the
threatening someone by saying that someone of the family member would be
kidnaped or killed if certain amount of money is not provided.
Make money fast scam: Cyber criminals are associated with making the users accept
the fact that they ca earn money at a faster rate by making use of the internet. In this
type of scam the criminals would be associated with promising the users about jobs
which do not exists and also include plans and methods by which the user can get
rich. This is very much effective approach taken by the criminals as this would be
associated with addressing the basic needs of money and this happens especially in
situations when the users are facing some difficult financial situations.
A. Some of the popular Internet scams have been listed below:
Bank loan or credit card scam: This type of scam is very much common and in this
type of scam the users are guaranteed that they would be getting a huge amount of
money which has already been pre-approved by the bank. Though it may seem
unlikely for people to get trapped by this scam, there’s still a big number of people
who lost money by paying the “mandatory” processing fees required by the
scammers.
Lottery scam: This can be considered as another classic internet scam which is a very
old technique of scam. This type of scam also come from the emails where the user is
sent an email saying that they have won a huge amount of money in lottery and for
claiming that price there is a need of paying some small fees.
Hitman scam: this is considered as one of the frequent internet scam which is
associated with sending of threatening email for the purpose of extorting money from
the user. This type of scam generally occurs in various forms which might include the
threatening someone by saying that someone of the family member would be
kidnaped or killed if certain amount of money is not provided.
Make money fast scam: Cyber criminals are associated with making the users accept
the fact that they ca earn money at a faster rate by making use of the internet. In this
type of scam the criminals would be associated with promising the users about jobs
which do not exists and also include plans and methods by which the user can get
rich. This is very much effective approach taken by the criminals as this would be
associated with addressing the basic needs of money and this happens especially in
situations when the users are facing some difficult financial situations.

B. Features and Security Settings of Google Chrome
It is a web browser designed for a Windows operating system. This browser works on windows
XP, Windows Vista, MAC OS and Linux.
The following are the features and security settings of Google chrome web browser
From the setting menu select the Incognito window a new window appears. Pages
you view from this window won’t appear in your web browser history or search
history.They won’t leave any traces like cookies after you close the incognito window
any files you download or bookmarks will be preserved.
Chrome there is a new feature that has an own Task Manager that shows you how
much memory and CPU usage each tab and plug-in is using. You can open it by
clicking Shift-Esc from within Chrome or place the cursor on a window and right
click and select the Task Manager. You can get more details by clicking the “Stats for
nerds” link, which is on the Task Manager, and it will open a page with full details of
memory and CPU usage for each process within the browser. It is used to close a bad
process in one tab and won’t kill your whole browser session.
One of the features of chrome is dynamic tabs. Here you can drag tabs out of the
browser to create new windows, gather multiple tabs into one window or arrange your
tabs. However, you wish and it becomes quick and easy to login into the desired sites
i.e. reopen the closed sites.
The safe browsing feature in the Google Chrome displays a warning if the web
address listed in the certificate doesn't match the address of the website .The
following are the steps for safe browsing setting in Google Chrome.
It is a web browser designed for a Windows operating system. This browser works on windows
XP, Windows Vista, MAC OS and Linux.
The following are the features and security settings of Google chrome web browser
From the setting menu select the Incognito window a new window appears. Pages
you view from this window won’t appear in your web browser history or search
history.They won’t leave any traces like cookies after you close the incognito window
any files you download or bookmarks will be preserved.
Chrome there is a new feature that has an own Task Manager that shows you how
much memory and CPU usage each tab and plug-in is using. You can open it by
clicking Shift-Esc from within Chrome or place the cursor on a window and right
click and select the Task Manager. You can get more details by clicking the “Stats for
nerds” link, which is on the Task Manager, and it will open a page with full details of
memory and CPU usage for each process within the browser. It is used to close a bad
process in one tab and won’t kill your whole browser session.
One of the features of chrome is dynamic tabs. Here you can drag tabs out of the
browser to create new windows, gather multiple tabs into one window or arrange your
tabs. However, you wish and it becomes quick and easy to login into the desired sites
i.e. reopen the closed sites.
The safe browsing feature in the Google Chrome displays a warning if the web
address listed in the certificate doesn't match the address of the website .The
following are the steps for safe browsing setting in Google Chrome.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

From the settings tab select the options and select under the hood under privacy
enable the option show suggestions for navigation error.
Enable the option use a suggestion service to help complete searches and URLS typed
in the address bar.
Enable DNS pre-fetching to improve page load performance.
Enable the phishing and malware protection.
Under minor tweaks enable the never save passwords.
Under computer wide SSL settings enable the option use SSL 2.0.
From the page menu select the create application shortcuts, this is used if you want
some websites to be viewed regularly, and you may want to create application
shortcuts for the desired websites that can be placed on your desktop, Start menu or
quick launch menu so you can choose any one of these options .After creating, if you
double-click on the shortcut icon on the desktop or start menu, the websites open in a
special window that don’t display tabs, buttons, address bar or menus.
Many of the browser functions are available instead in the drop-down menu that
appears when you click the page logo in the upper-right corner of the window. If you
click a link that takes you to a different website, the link opens in a standard Google
Chrome window so you won't lose track of your website.
Question 2:
A. A. The different kind of virus, malware and spyware mainly includes the following along
with the ways how they can be prevented:
enable the option show suggestions for navigation error.
Enable the option use a suggestion service to help complete searches and URLS typed
in the address bar.
Enable DNS pre-fetching to improve page load performance.
Enable the phishing and malware protection.
Under minor tweaks enable the never save passwords.
Under computer wide SSL settings enable the option use SSL 2.0.
From the page menu select the create application shortcuts, this is used if you want
some websites to be viewed regularly, and you may want to create application
shortcuts for the desired websites that can be placed on your desktop, Start menu or
quick launch menu so you can choose any one of these options .After creating, if you
double-click on the shortcut icon on the desktop or start menu, the websites open in a
special window that don’t display tabs, buttons, address bar or menus.
Many of the browser functions are available instead in the drop-down menu that
appears when you click the page logo in the upper-right corner of the window. If you
click a link that takes you to a different website, the link opens in a standard Google
Chrome window so you won't lose track of your website.
Question 2:
A. A. The different kind of virus, malware and spyware mainly includes the following along
with the ways how they can be prevented:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ransomware: This is a form of malware which is associated with hold the computer
systems captive along with demanding some ransom. This type of malware is associated
with restricting the user from getting access to the computer and this done by either
encrypting the file present in the hard drive or by locking don the system and display a
message which is is generally intended to force the user to pay for the malware creator in
order to remove all the restrictions and the regain access to the computer by the user.
Rootkit: this is a type of malicious software which is generally designed in order to get
remote access or control a computer. This would be totally done without being detected
by the authentic user or by the security program. After installation of the rootkit it makes
the malicious party behind the rootkit to execute the files along with stealing or accessing
of the information and many more.
Trojan horse: this is also known as the Trojan which can be considered as a malware in
disguise to make itself present as a normal file or program. This is then associated with
tricking the user to download and install the malware. This type of malware provides
remote access of the computer which has been affected to the malicious attacker.
Virus: this is generally considered as a form of malware that is associated with copying
itself and spread all throughout the computer. This are often spread to the computer by
getting themselves attached to various programs and the execution codes whenever a user
launches the infected file.
There exists various ways of preventing the malware. Some best practices need be
adopted by the organization as well as by individual users for the purpose of preventing the
infections. Many malwares exists which requires a special prevention along with treatment
method. Some of the methods or prevention has been listed below:
systems captive along with demanding some ransom. This type of malware is associated
with restricting the user from getting access to the computer and this done by either
encrypting the file present in the hard drive or by locking don the system and display a
message which is is generally intended to force the user to pay for the malware creator in
order to remove all the restrictions and the regain access to the computer by the user.
Rootkit: this is a type of malicious software which is generally designed in order to get
remote access or control a computer. This would be totally done without being detected
by the authentic user or by the security program. After installation of the rootkit it makes
the malicious party behind the rootkit to execute the files along with stealing or accessing
of the information and many more.
Trojan horse: this is also known as the Trojan which can be considered as a malware in
disguise to make itself present as a normal file or program. This is then associated with
tricking the user to download and install the malware. This type of malware provides
remote access of the computer which has been affected to the malicious attacker.
Virus: this is generally considered as a form of malware that is associated with copying
itself and spread all throughout the computer. This are often spread to the computer by
getting themselves attached to various programs and the execution codes whenever a user
launches the infected file.
There exists various ways of preventing the malware. Some best practices need be
adopted by the organization as well as by individual users for the purpose of preventing the
infections. Many malwares exists which requires a special prevention along with treatment
method. Some of the methods or prevention has been listed below:

Installing and running of anti-malware and firewall software. Whenever a software is
being chosen it must be seen that program which has been chosen along with the software
is associated with offering tools in order to detect along with quarantining and removing
the various type of malware. The minimum requirement is that the anti-malware software
should be associated with protecting the users from any kind of threats coming from the
viruses, spyware, adware, Trojans and other kind of malwares. By making use of the
firewall along with the anti-malware would be helping a lot in ensuring the fact that the
incoming as well as the outgoing data are getting scanned for the malware. This would be
done for the purpose of removing the threats once they are detected.
Keeping the software and the operating system updated with the new vulnerability
patches would also be very much helpful. This patches are often released for the purpose
of patching the bugs or the other security flaws which are likely to effect the system of
the users.
The users should be vigilant while downloading various files and programs and many
more. The downloads which seem to be strange must be stopped immediately as they
might contain malware.
Question 3:
A. various type of Denial of Service includes the following:
A buffer overflow attack is a catchall description most commonly applied to DoS attacks
that send more traffic to a network resource than was ever anticipated by the developers
who designed the resource. One example of such an attack sent, as email attachments,
files that have 256-character file names to recipients using Netscape or Microsoft email
clients; the longer-than-anticipated file names were sufficient to crash those applications.
being chosen it must be seen that program which has been chosen along with the software
is associated with offering tools in order to detect along with quarantining and removing
the various type of malware. The minimum requirement is that the anti-malware software
should be associated with protecting the users from any kind of threats coming from the
viruses, spyware, adware, Trojans and other kind of malwares. By making use of the
firewall along with the anti-malware would be helping a lot in ensuring the fact that the
incoming as well as the outgoing data are getting scanned for the malware. This would be
done for the purpose of removing the threats once they are detected.
Keeping the software and the operating system updated with the new vulnerability
patches would also be very much helpful. This patches are often released for the purpose
of patching the bugs or the other security flaws which are likely to effect the system of
the users.
The users should be vigilant while downloading various files and programs and many
more. The downloads which seem to be strange must be stopped immediately as they
might contain malware.
Question 3:
A. various type of Denial of Service includes the following:
A buffer overflow attack is a catchall description most commonly applied to DoS attacks
that send more traffic to a network resource than was ever anticipated by the developers
who designed the resource. One example of such an attack sent, as email attachments,
files that have 256-character file names to recipients using Netscape or Microsoft email
clients; the longer-than-anticipated file names were sufficient to crash those applications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
In a DDoS attack, the attacker may use computers or other network-connected devices
that have been infected by malware and made part of a botnet. Distributed denial-of-
service attacks, especially those using botnets, use command-and-control (C&C) servers
to direct the actions of the botnet members. The C&C servers dictate what kind of attack
to launch, what types of data to transmit and what systems or network resources are to be
targeted in the attack.
The ping-of-death attack abuses the Packet Inter-Network Groper (ping) protocol by
sending request messages with oversized payloads, causing targeted systems to become
overwhelmed, stop responding to legitimate requests for service and possibly crashing the
victim systems.
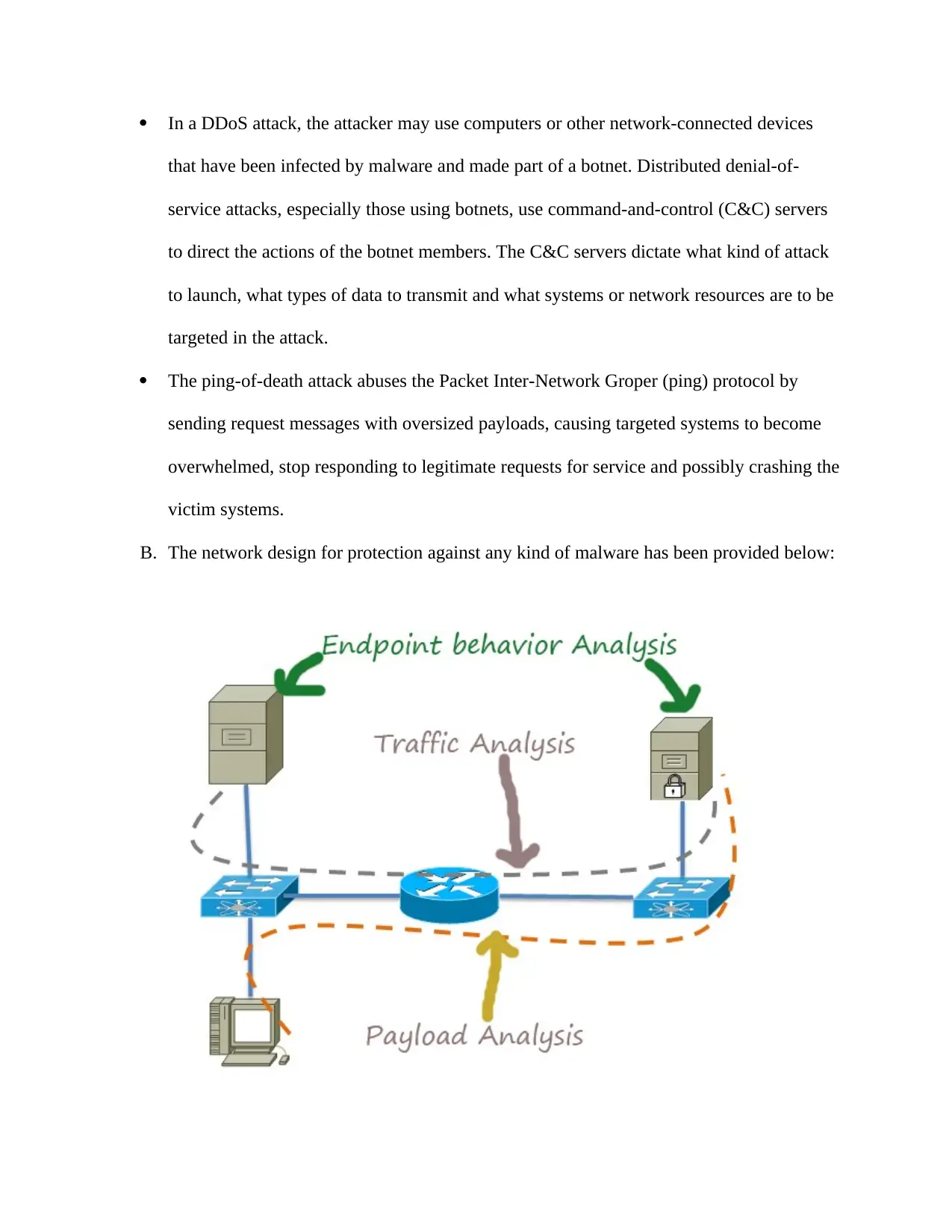
B. The network design for protection against any kind of malware has been provided below:
that have been infected by malware and made part of a botnet. Distributed denial-of-
service attacks, especially those using botnets, use command-and-control (C&C) servers
to direct the actions of the botnet members. The C&C servers dictate what kind of attack
to launch, what types of data to transmit and what systems or network resources are to be
targeted in the attack.
The ping-of-death attack abuses the Packet Inter-Network Groper (ping) protocol by
sending request messages with oversized payloads, causing targeted systems to become
overwhelmed, stop responding to legitimate requests for service and possibly crashing the
victim systems.
B. The network design for protection against any kind of malware has been provided below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 4:
A. Various kind of Hacking tools mainly includes the following:
Wireshark: Wireshark can be considered to a GTK+- based network protocol analyzer or
a sniffer tool which is associated providing the facility of capturing and interactively
browsing the various contents present in the network frame. The main goal of the project
mainly includes the creation of a commercial-quality analyzer which is mainly for the
UNIX and is also associated with providing of the Wireshark features which are
generally missing from the source sniffers which are close to it..
Yersinia: This can be considered as a network tool which has been designed for the
purpose of taking advantage of some weakness that is present in the different Layer 2
protocols. This is generally associated with pretending as a solid framework in order to
analyze and the network and the system which has been deployed. The network protocols
which are implemented generally includes the following: Spanning Tree Protocol (STP),
Cisco Discovery Protocol (CDP), Dynamic Trunking Protocol (DTP), Dynamic Host
Configuration Protocol (DHCP), Hot Standby Router Protocol (HSRP), IEEE 802.1q,
Inter-Switch Link Protocol (ISL), VLAN Trunking Protocol (VTP
Eraser: This can be considered as an advanced security tool which is generally for the
windows and are associated with allowing the users to remove the sensitive data from the
user’s hard drive completed. This is generally done by overwriting it several times with
patterns which has been selected carefully. This tool generally works with Windows 95,
98, ME, NT, 2000, XP and DOS. Eraser is absolutely free of cost software which is
having its source code released under GNU General Public License. This can be
A. Various kind of Hacking tools mainly includes the following:
Wireshark: Wireshark can be considered to a GTK+- based network protocol analyzer or
a sniffer tool which is associated providing the facility of capturing and interactively
browsing the various contents present in the network frame. The main goal of the project
mainly includes the creation of a commercial-quality analyzer which is mainly for the
UNIX and is also associated with providing of the Wireshark features which are
generally missing from the source sniffers which are close to it..
Yersinia: This can be considered as a network tool which has been designed for the
purpose of taking advantage of some weakness that is present in the different Layer 2
protocols. This is generally associated with pretending as a solid framework in order to
analyze and the network and the system which has been deployed. The network protocols
which are implemented generally includes the following: Spanning Tree Protocol (STP),
Cisco Discovery Protocol (CDP), Dynamic Trunking Protocol (DTP), Dynamic Host
Configuration Protocol (DHCP), Hot Standby Router Protocol (HSRP), IEEE 802.1q,
Inter-Switch Link Protocol (ISL), VLAN Trunking Protocol (VTP
Eraser: This can be considered as an advanced security tool which is generally for the
windows and are associated with allowing the users to remove the sensitive data from the
user’s hard drive completed. This is generally done by overwriting it several times with
patterns which has been selected carefully. This tool generally works with Windows 95,
98, ME, NT, 2000, XP and DOS. Eraser is absolutely free of cost software which is
having its source code released under GNU General Public License. This can be

considered as an excellent tool which is associated with keeping the user data really safe,
in cases when the user have deleted it.
B. There exists three types of cryptography methods for the purpose of securing the
network and this mainly includes the following:
Symmetric Cryptography: In this type of method the same key is used for the purpose
of encryption as well as for decryption. In this type of method the sender as well as
the receipt must have shared the key which is known to both of them. The distribution
of the keys can be considered to be a tricky problem and was the major reason
responsible for the creation of asymmetric cryptography method. This type of method
is generally fast and ideal for encryption of data which are large in amount.
Asymmetric Cryptography: In this type of method two different kind of used for the
encryption and for the decryption. The users associated with this method consists of
two keys one private key and the other public key. The private keys are kept secret
whereas the public keys are distributed freely. In this type of method the data which
has been encrypted by making use of the public key can only be decrypted by making
use of the private key which is present corresponding to the public key. This type of
method is generally slow and are capable of encrypting a limited amount of data
which are having a small key size.
C. The best cryptographic method that is suggested for the purpose of securing the computer
is the Asymmetric cryptography. The main reason lying behind this is because of the fact
the asymmetric cryptography method is used for the purpose of encrypting the symmetric
keys which are in turn used for the purpose of encrypting the larger blocks of data.
in cases when the user have deleted it.
B. There exists three types of cryptography methods for the purpose of securing the
network and this mainly includes the following:
Symmetric Cryptography: In this type of method the same key is used for the purpose
of encryption as well as for decryption. In this type of method the sender as well as
the receipt must have shared the key which is known to both of them. The distribution
of the keys can be considered to be a tricky problem and was the major reason
responsible for the creation of asymmetric cryptography method. This type of method
is generally fast and ideal for encryption of data which are large in amount.
Asymmetric Cryptography: In this type of method two different kind of used for the
encryption and for the decryption. The users associated with this method consists of
two keys one private key and the other public key. The private keys are kept secret
whereas the public keys are distributed freely. In this type of method the data which
has been encrypted by making use of the public key can only be decrypted by making
use of the private key which is present corresponding to the public key. This type of
method is generally slow and are capable of encrypting a limited amount of data
which are having a small key size.
C. The best cryptographic method that is suggested for the purpose of securing the computer
is the Asymmetric cryptography. The main reason lying behind this is because of the fact
the asymmetric cryptography method is used for the purpose of encrypting the symmetric
keys which are in turn used for the purpose of encrypting the larger blocks of data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bibliography:
Ciampa, M. (2012). Security+ guide to network security fundamentals. Cengage Learning.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Knapp, E. D., & Langill, J. T. (2014). Industrial Network Security: Securing critical
infrastructure networks for smart grid, SCADA, and other Industrial Control Systems.
Syngress.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets
network security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Morrow, B. (2012). BYOD security challenges: control and protect your most sensitive data.
Network Security, 2012(12), 5-8.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
Shin, S., & Gu, G. (2012, October). CloudWatcher: Network security monitoring using
OpenFlow in dynamic cloud networks (or: How to provide security monitoring as a
service in clouds?). In Network Protocols (ICNP), 2012 20th IEEE International
Conference on (pp. 1-6). IEEE.
Shiravi, H., Shiravi, A., & Ghorbani, A. A. (2012). A survey of visualization systems for
network security. IEEE Transactions on visualization and computer graphics, 18(8),
1313-1329.
Stallings, W., Brown, L., Bauer, M. D., & Bhattacharjee, A. K. (2012). Computer security:
principles and practice (pp. 978-0). Pearson Education.
Tankard, C. (2012). Big data security. Network security, 2012(7), 5-8.
Tokuyoshi, B. (2013). The security implications of BYOD. Network Security, 2013(4), 12-13.
Ciampa, M. (2012). Security+ guide to network security fundamentals. Cengage Learning.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Knapp, E. D., & Langill, J. T. (2014). Industrial Network Security: Securing critical
infrastructure networks for smart grid, SCADA, and other Industrial Control Systems.
Syngress.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets
network security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Morrow, B. (2012). BYOD security challenges: control and protect your most sensitive data.
Network Security, 2012(12), 5-8.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
Shin, S., & Gu, G. (2012, October). CloudWatcher: Network security monitoring using
OpenFlow in dynamic cloud networks (or: How to provide security monitoring as a
service in clouds?). In Network Protocols (ICNP), 2012 20th IEEE International
Conference on (pp. 1-6). IEEE.
Shiravi, H., Shiravi, A., & Ghorbani, A. A. (2012). A survey of visualization systems for
network security. IEEE Transactions on visualization and computer graphics, 18(8),
1313-1329.
Stallings, W., Brown, L., Bauer, M. D., & Bhattacharjee, A. K. (2012). Computer security:
principles and practice (pp. 978-0). Pearson Education.
Tankard, C. (2012). Big data security. Network security, 2012(7), 5-8.
Tokuyoshi, B. (2013). The security implications of BYOD. Network Security, 2013(4), 12-13.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


Threats
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



