Network System Administration: VPN Services and Security Protocols
VerifiedAdded on 2023/04/21
|17
|1806
|192
Report
AI Summary
This report provides an analysis of network operating systems and services, focusing on VPN implementation using Debian Linux. It explores the configuration of VPN services such as IPSec and tunneling to enhance communication security. The report details the experimental work conducted in a virtual environment, including enabling IP forwarding and installing strongSwan. It also covers the configuration of IPSec, VLAN interfaces, and NAT for remote client access. The study emphasizes the importance of VPNs in data encryption and security, highlighting features like data integrity and authentication mechanisms. The conclusion underscores the effectiveness of VPNs in protecting data and ensuring secure online access, making it a valuable resource for understanding network system administration and security protocols.

Running head: NETWORK SYSTEM ADMINISTRATION
Network System Administration
Name of the Student
Name of the University
Author’s Note
Network System Administration
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SYSTEM ADMINISTRATION
Abstract
The report is prepared for analysis of the network operating system and services with the use
of relevant services and protocols. Different mechanism is followed for setting the virtual
private network services and an architectural diagram is created for the management of the
necessary services. The necessary solution that can be implemented for the configuration of
the vpn services is evaluated for meeting the different service requirement. The necessary
mechanism and solution that can be applied for increasing the reliability of the proposed
solution is analysed for development of the system architecture.
NETWORK SYSTEM ADMINISTRATION
Abstract
The report is prepared for analysis of the network operating system and services with the use
of relevant services and protocols. Different mechanism is followed for setting the virtual
private network services and an architectural diagram is created for the management of the
necessary services. The necessary solution that can be implemented for the configuration of
the vpn services is evaluated for meeting the different service requirement. The necessary
mechanism and solution that can be applied for increasing the reliability of the proposed
solution is analysed for development of the system architecture.

2
NETWORK SYSTEM ADMINISTRATION
Table of Contents
Introduction................................................................................................................................3
Background Information............................................................................................................3
Scope and Limitations................................................................................................................3
Literature Review.......................................................................................................................3
Experimental work and analysis................................................................................................5
Conclusion................................................................................................................................14
References:...............................................................................................................................15
NETWORK SYSTEM ADMINISTRATION
Table of Contents
Introduction................................................................................................................................3
Background Information............................................................................................................3
Scope and Limitations................................................................................................................3
Literature Review.......................................................................................................................3
Experimental work and analysis................................................................................................5
Conclusion................................................................................................................................14
References:...............................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK SYSTEM ADMINISTRATION
Introduction
With the advancement of the technology and the influence of internet in various
domain, it has become important to have high speed and secure internet as the organizations
are moving to the cloud and hosting private and sensitive data there (Dongxu et al. 2018).
Due to this it has become important to protect the data as there are increased number of
cyber-attacks such as traffic hijacking and data breach. Now in order to increase the internet
access for better data protection and data security, VPN is an excellent strategy (Jyothi and
Reddy 2018).
Background Information
The main important feature of the open source software is that it does not require the
manufacturing license and free to access (Genç, Lenzini and Ryan 2018). Hence it is very
useful in the software development field and often considered for various activities like
cloning, evaluation and method for thread identification. The Debian Linux is used for the
configuration of VPN service and
Scope and Limitations
The main scope of the project is configure a vpn server and enabling client server
communication for management of the security issues such as handling different types of
attacks. The sever is configured with VPN service such as IPSec, Tunneling for increasing
the security of communication. Since a virtual environment is used for the configuration there
are some limitation faced for testing the configuration. Different types of attacks is needed to
be tested against the configuration.
Literature Review
Literature review is the systematic approach for reviewing and analysing methods
which are relevant with respect to a particular research topic. One area that has particularly
NETWORK SYSTEM ADMINISTRATION
Introduction
With the advancement of the technology and the influence of internet in various
domain, it has become important to have high speed and secure internet as the organizations
are moving to the cloud and hosting private and sensitive data there (Dongxu et al. 2018).
Due to this it has become important to protect the data as there are increased number of
cyber-attacks such as traffic hijacking and data breach. Now in order to increase the internet
access for better data protection and data security, VPN is an excellent strategy (Jyothi and
Reddy 2018).
Background Information
The main important feature of the open source software is that it does not require the
manufacturing license and free to access (Genç, Lenzini and Ryan 2018). Hence it is very
useful in the software development field and often considered for various activities like
cloning, evaluation and method for thread identification. The Debian Linux is used for the
configuration of VPN service and
Scope and Limitations
The main scope of the project is configure a vpn server and enabling client server
communication for management of the security issues such as handling different types of
attacks. The sever is configured with VPN service such as IPSec, Tunneling for increasing
the security of communication. Since a virtual environment is used for the configuration there
are some limitation faced for testing the configuration. Different types of attacks is needed to
be tested against the configuration.
Literature Review
Literature review is the systematic approach for reviewing and analysing methods
which are relevant with respect to a particular research topic. One area that has particularly
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK SYSTEM ADMINISTRATION
attracted major research interest in this context is the application of debian Linux which is
open source software (Diaz et al. 2014).
IPSEC:
IPsec is the protocol suite that helps to secure communication through internet (Lu
2015). It provide encryption for each and every packet that part of the communication and
transmitted through internet protocol (Chen et al. 2017). Various important features offered
by the IPsec are data integrity, anti-replay, confidentiality along with effective authentication.
Anti-replay provides security at the IP-packets level
Data integrity is preferred for reducing chances for data manipulation.
Confidentiality and authentication is ensured through encrypting
Key Exchange and Authentication Mechanism
This is the most important aspect of the authentication of the IPSec-VPNs. Without
this feature it is not possible to ensure authentication of IPsec-VPNs. A digital certificate can
be considered as a form of document provide electronically (Chen and Li 2018). In order to
access the documents it is important to acquire the permission form the owner of the
certificate to access the documents. Hence certification authentication is required to obtain
for the third party. CA or the certification authentication is implemented with RSA signature
which is validated by Certificate Authority which trusts the third parties organizations and
hence it is also an important feature (Genç, Lenzini and Ryan 2018). CA often verifies the
credentials claimed by any peers and need to be approved by the validation associated with
the certificates issues for the third part organizations. According to Wang and Nicol (2014,
September) various components of the digital certificates are as follows:
A digital checksum which is part of the certificates are secured with encryption
through the private key.
NETWORK SYSTEM ADMINISTRATION
attracted major research interest in this context is the application of debian Linux which is
open source software (Diaz et al. 2014).
IPSEC:
IPsec is the protocol suite that helps to secure communication through internet (Lu
2015). It provide encryption for each and every packet that part of the communication and
transmitted through internet protocol (Chen et al. 2017). Various important features offered
by the IPsec are data integrity, anti-replay, confidentiality along with effective authentication.
Anti-replay provides security at the IP-packets level
Data integrity is preferred for reducing chances for data manipulation.
Confidentiality and authentication is ensured through encrypting
Key Exchange and Authentication Mechanism
This is the most important aspect of the authentication of the IPSec-VPNs. Without
this feature it is not possible to ensure authentication of IPsec-VPNs. A digital certificate can
be considered as a form of document provide electronically (Chen and Li 2018). In order to
access the documents it is important to acquire the permission form the owner of the
certificate to access the documents. Hence certification authentication is required to obtain
for the third party. CA or the certification authentication is implemented with RSA signature
which is validated by Certificate Authority which trusts the third parties organizations and
hence it is also an important feature (Genç, Lenzini and Ryan 2018). CA often verifies the
credentials claimed by any peers and need to be approved by the validation associated with
the certificates issues for the third part organizations. According to Wang and Nicol (2014,
September) various components of the digital certificates are as follows:
A digital checksum which is part of the certificates are secured with encryption
through the private key.

5
NETWORK SYSTEM ADMINISTRATION
The public key.
The credentials of a party so that it is possible to certify that the key that is claimed by
the declared holder actually belongs to him or her.
The credentials associated with the public key holder.
The mechanism is very simple and effective, the owner issues a certificate and attach
credentials with the certificate through encrypted key and this key is then issued to the third
party. Now to access the data it is important to provide the key and owner verifies it with the
original key to verify and approve the claim which makes the process efficient and secured.
Experimental work and analysis
For the purposes of this test, the VPN server is allocated with an address of 10.0.5.1
on the VLAN, and connect a second server over the VLAN at 10.0.5.2.
nano /etc/network/interfaces
The terminal return result as
NETWORK SYSTEM ADMINISTRATION
The public key.
The credentials of a party so that it is possible to certify that the key that is claimed by
the declared holder actually belongs to him or her.
The credentials associated with the public key holder.
The mechanism is very simple and effective, the owner issues a certificate and attach
credentials with the certificate through encrypted key and this key is then issued to the third
party. Now to access the data it is important to provide the key and owner verifies it with the
original key to verify and approve the claim which makes the process efficient and secured.
Experimental work and analysis
For the purposes of this test, the VPN server is allocated with an address of 10.0.5.1
on the VLAN, and connect a second server over the VLAN at 10.0.5.2.
nano /etc/network/interfaces
The terminal return result as
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK SYSTEM ADMINISTRATION
Adding lining below the lines
NETWORK SYSTEM ADMINISTRATION
Adding lining below the lines
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK SYSTEM ADMINISTRATION
Next, the IP forwarding is enabled through a text editor after opening sysctl
configuration file
nano /etc/sysctl.conf
The command is used for changing different parameters and the ip forwarding table is
enabled and the ICMP re-direct is disabled.
NETWORK SYSTEM ADMINISTRATION
Next, the IP forwarding is enabled through a text editor after opening sysctl
configuration file
nano /etc/sysctl.conf
The command is used for changing different parameters and the ip forwarding table is
enabled and the ICMP re-direct is disabled.

8
NETWORK SYSTEM ADMINISTRATION
The “sys ctl” command is used for reading the configuration file while utilizing the new
defined parameters.
NETWORK SYSTEM ADMINISTRATION
The “sys ctl” command is used for reading the configuration file while utilizing the new
defined parameters.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK SYSTEM ADMINISTRATION
sysctl -p /etc/sysctl.conf
after that, the strongSwan needs to be installed along with layer 2 tunnelling protocol.
apt-get update
apt-get install strongswan xl2tpd
While installing the strongswan, the system gives option to whether create x.509 certificate.
Which is selected as no as it needs for PSK (preshared key) authentication.
NETWORK SYSTEM ADMINISTRATION
sysctl -p /etc/sysctl.conf
after that, the strongSwan needs to be installed along with layer 2 tunnelling protocol.
apt-get update
apt-get install strongswan xl2tpd
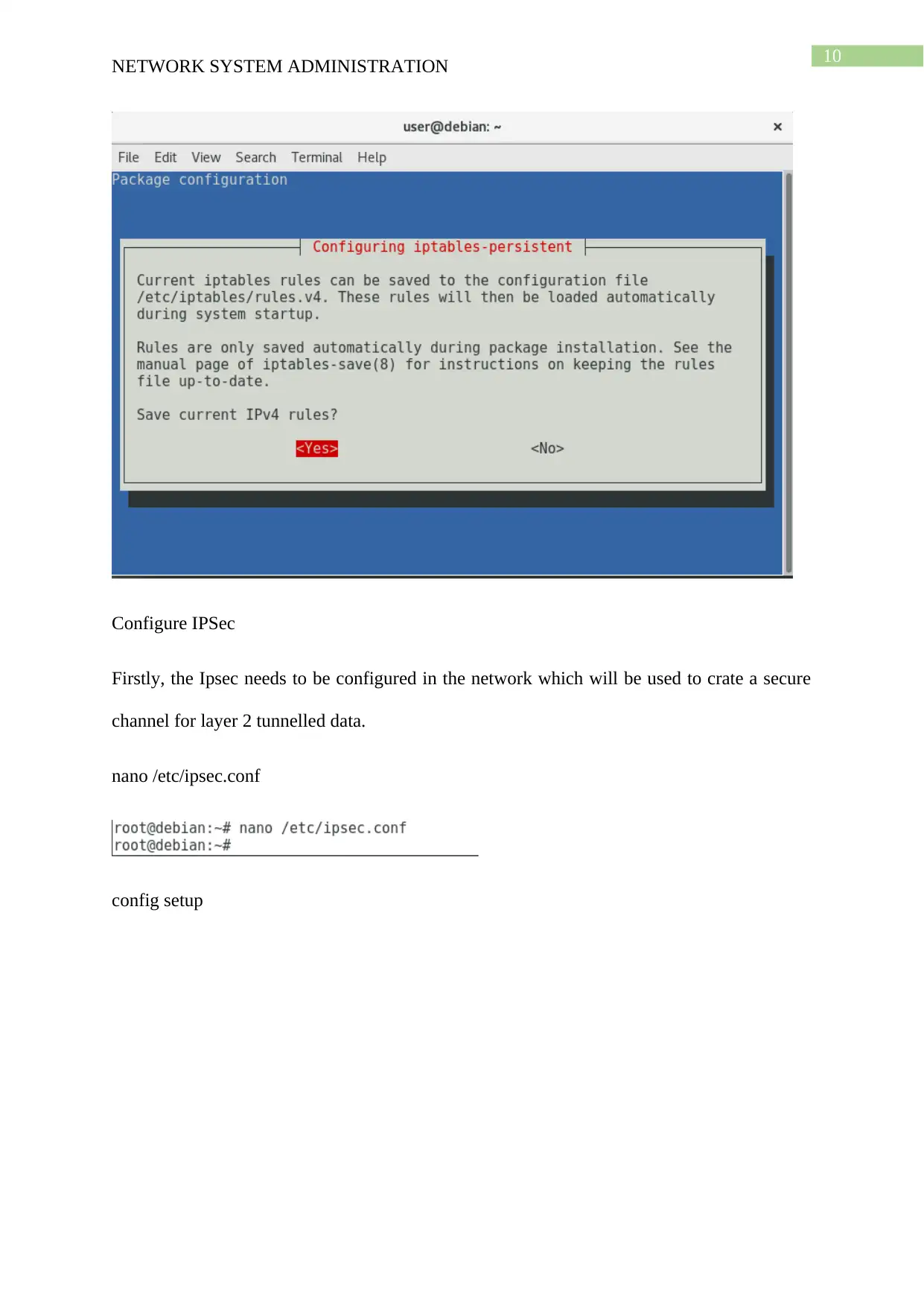
While installing the strongswan, the system gives option to whether create x.509 certificate.
Which is selected as no as it needs for PSK (preshared key) authentication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK SYSTEM ADMINISTRATION
Configure IPSec
Firstly, the Ipsec needs to be configured in the network which will be used to crate a secure
channel for layer 2 tunnelled data.
nano /etc/ipsec.conf
config setup
NETWORK SYSTEM ADMINISTRATION
Configure IPSec
Firstly, the Ipsec needs to be configured in the network which will be used to crate a secure
channel for layer 2 tunnelled data.
nano /etc/ipsec.conf
config setup

11
NETWORK SYSTEM ADMINISTRATION
The IP is given for the VLAN interfaces. The local ip value is given as 10.0.5.1
IP range: the Ip range is given as 10.0.5.50 to 10.0.5.255. it will provide access for 200
remote user.
The codes also specifies refuse pap and refuse chap.
The ppp options needs to be configured as well as
NETWORK SYSTEM ADMINISTRATION
The IP is given for the VLAN interfaces. The local ip value is given as 10.0.5.1
IP range: the Ip range is given as 10.0.5.50 to 10.0.5.255. it will provide access for 200
remote user.
The codes also specifies refuse pap and refuse chap.
The ppp options needs to be configured as well as
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




