Network Performance Evaluation using Riverbed Modeler - COMP1664
VerifiedAdded on 2023/06/03
|13
|1905
|400
Project
AI Summary
This project report details a network design and performance evaluation using Riverbed Modeler. The project begins by designing a network for a medium-sized hospital, including the selection of a tree topology and the use of technologies like client-server, Ethernet, and routers. The second part involves modeling network traffic, configuring applications like FTP, HTTP, and databases, and simulating network behavior. Finally, the project investigates network performance by analyzing throughput and data received under different user loads and access point configurations. The results highlight the impact of user numbers on network delay and data transfer rates. The project also discusses the steps involved in network performance investigation and the factors affecting the network performance.

Network Technology-Riverbed Modeler 1
NETWORK TECHNOLOGY-RIVERBED MODELER
By (Student Name)
(Course)
(Tutor)
(University)
(City)
(Date)
NETWORK TECHNOLOGY-RIVERBED MODELER
By (Student Name)
(Course)
(Tutor)
(University)
(City)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Technology-Riverbed Modeler 2
Introduction
The main aim of this work is to design and use riverbed modeler to investigate the factors
which affect network performance. The paper is dived into three parts which are labeled A, B
and C, and a conclusion. The first part will include designing a network for a medium sized
company and modeling it. Part B will be evaluating the performance of the network. The last part
will be investigating the performance of the network so as to understand its performance and
network configuration.
Part A: Designing and modeling it
Overview of XYZ hospital
XYZ hospital is an organization which specializes in treating cancer patients. The
company has over 100 employees divided into various departments which are the IT department,
Finance department, HR department, and the medical department. Medical department has the
largest number of employees 80 of them. The Finance department has seven staff members, the
HR department has six members, five in the IT department and two secretaries who are always
located in the reception.
Network design needs
XYZ hospital is located in three-floor building where the finance and the two secretaries
are located in the ground floor, medical team department in the second floor, HR department is
located in the third floor. Everyone is required to connect to the organization campus LAN for
internet access and to access the shared resources. Due to an increased number of cancer
Introduction
The main aim of this work is to design and use riverbed modeler to investigate the factors
which affect network performance. The paper is dived into three parts which are labeled A, B
and C, and a conclusion. The first part will include designing a network for a medium sized
company and modeling it. Part B will be evaluating the performance of the network. The last part
will be investigating the performance of the network so as to understand its performance and
network configuration.
Part A: Designing and modeling it
Overview of XYZ hospital
XYZ hospital is an organization which specializes in treating cancer patients. The
company has over 100 employees divided into various departments which are the IT department,
Finance department, HR department, and the medical department. Medical department has the
largest number of employees 80 of them. The Finance department has seven staff members, the
HR department has six members, five in the IT department and two secretaries who are always
located in the reception.
Network design needs
XYZ hospital is located in three-floor building where the finance and the two secretaries
are located in the ground floor, medical team department in the second floor, HR department is
located in the third floor. Everyone is required to connect to the organization campus LAN for
internet access and to access the shared resources. Due to an increased number of cancer
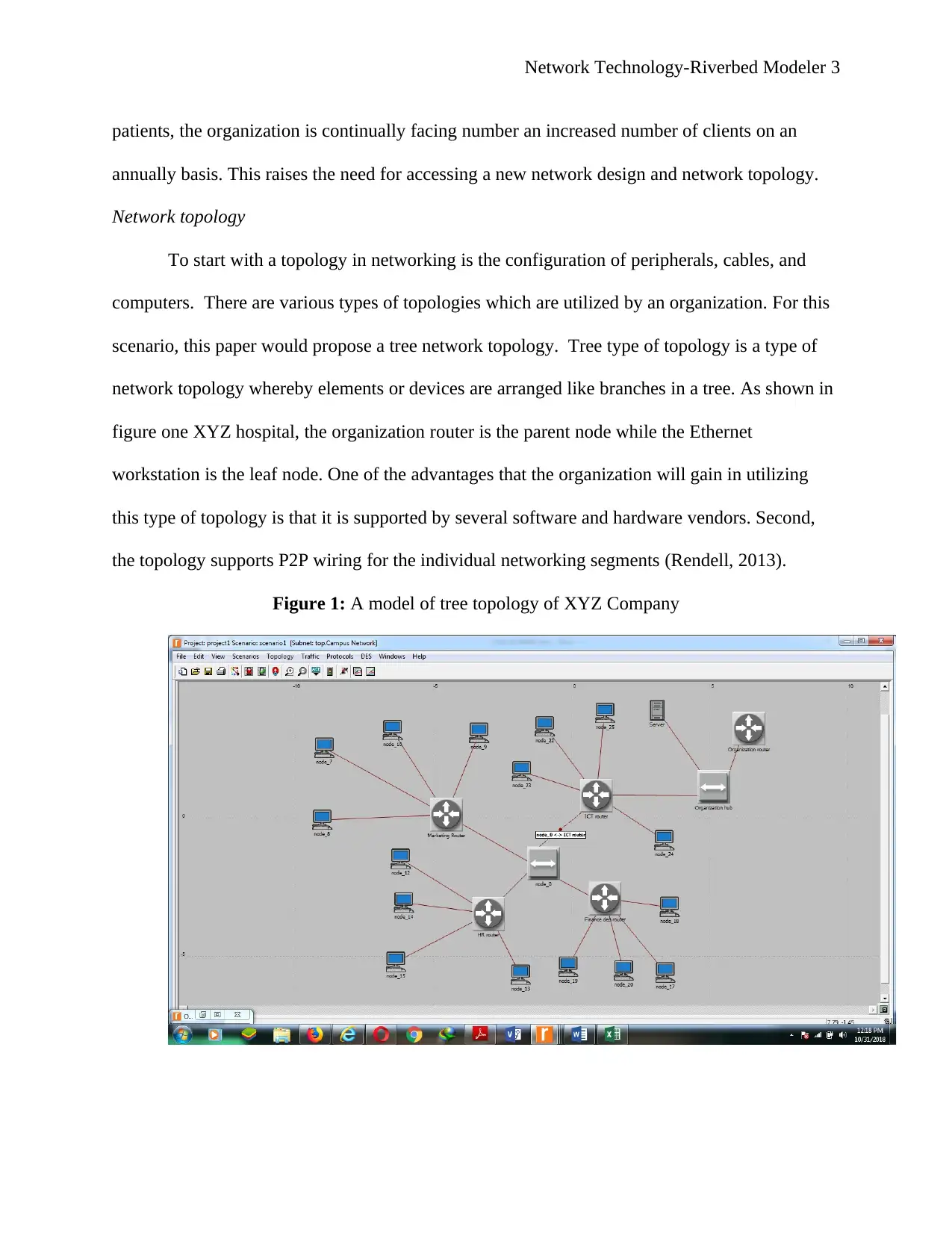
Network Technology-Riverbed Modeler 3
patients, the organization is continually facing number an increased number of clients on an
annually basis. This raises the need for accessing a new network design and network topology.
Network topology
To start with a topology in networking is the configuration of peripherals, cables, and
computers. There are various types of topologies which are utilized by an organization. For this
scenario, this paper would propose a tree network topology. Tree type of topology is a type of
network topology whereby elements or devices are arranged like branches in a tree. As shown in
figure one XYZ hospital, the organization router is the parent node while the Ethernet
workstation is the leaf node. One of the advantages that the organization will gain in utilizing
this type of topology is that it is supported by several software and hardware vendors. Second,
the topology supports P2P wiring for the individual networking segments (Rendell, 2013).
Figure 1: A model of tree topology of XYZ Company
patients, the organization is continually facing number an increased number of clients on an
annually basis. This raises the need for accessing a new network design and network topology.
Network topology
To start with a topology in networking is the configuration of peripherals, cables, and
computers. There are various types of topologies which are utilized by an organization. For this
scenario, this paper would propose a tree network topology. Tree type of topology is a type of
network topology whereby elements or devices are arranged like branches in a tree. As shown in
figure one XYZ hospital, the organization router is the parent node while the Ethernet
workstation is the leaf node. One of the advantages that the organization will gain in utilizing
this type of topology is that it is supported by several software and hardware vendors. Second,
the topology supports P2P wiring for the individual networking segments (Rendell, 2013).
Figure 1: A model of tree topology of XYZ Company
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Technology-Riverbed Modeler 4
Network technologies utilized
To come with this type of topology, the organization need to utilize different types of
network technologies. For this scenario, the technologies which have been utilized are client-
server, Ethernet, Ethernet workstation, routers, and Ethernet-servers. One of the supported link
type, in this case, is duplex- 1000 Base X (Manning, 2013).
The justification for network technologies used
Duplex -1000 Base X is a type of link which represents which supports 1000 Mbps which
connect every network element expect hub to hub. Client-server technology helps in connecting
every user into one single server for sharing of resources. Ethernet workstations technology helps
in connecting every user computer to the wide area network via Ethernet cable. Routers
technology are used in routing of protocols. Ethernet server assists in connecting the organization
client-server into the campus LAN via Ethernet (Krawetz, 2014).
Why XYZ as the organization of choice in this paper
This project opted to investigate XYZ as the company has utilized various networking design
technologies. Also the organization, it provided a chance for the simulator to present and analyze
results using network riverbed modeler.
Part B: Network Traffic Modeling
This part presents the exact network simulation and design of XYZ hospital; no security
scenario is presented in this section i.e. no security which was imposed on the XYZ network. IP
based cloud technology will act as the internet which connects the organization to the wide area
network. Two network routers are used to connect across the network simulation. There are three
different applications utilized in this scenario which are FTP, HTTP, and database applications
Network technologies utilized
To come with this type of topology, the organization need to utilize different types of
network technologies. For this scenario, the technologies which have been utilized are client-
server, Ethernet, Ethernet workstation, routers, and Ethernet-servers. One of the supported link
type, in this case, is duplex- 1000 Base X (Manning, 2013).
The justification for network technologies used
Duplex -1000 Base X is a type of link which represents which supports 1000 Mbps which
connect every network element expect hub to hub. Client-server technology helps in connecting
every user into one single server for sharing of resources. Ethernet workstations technology helps
in connecting every user computer to the wide area network via Ethernet cable. Routers
technology are used in routing of protocols. Ethernet server assists in connecting the organization
client-server into the campus LAN via Ethernet (Krawetz, 2014).
Why XYZ as the organization of choice in this paper
This project opted to investigate XYZ as the company has utilized various networking design
technologies. Also the organization, it provided a chance for the simulator to present and analyze
results using network riverbed modeler.
Part B: Network Traffic Modeling
This part presents the exact network simulation and design of XYZ hospital; no security
scenario is presented in this section i.e. no security which was imposed on the XYZ network. IP
based cloud technology will act as the internet which connects the organization to the wide area
network. Two network routers are used to connect across the network simulation. There are three
different applications utilized in this scenario which are FTP, HTTP, and database applications
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Technology-Riverbed Modeler 5
for each department. The required traffic is generated after both the profile configuration and
application objects.
User profiles and justification
As highlighted in part one there are four departments but here, this section the project
will only utilize three department profiles. The HR department is mandated in managing
employees’ data. The IT department mandated to maintain the organization network. The
medical department mandated to keep patient records.
The HR department keeps records of the hours worked for each employee as they are
paid according to the number of employees. This means that they have to transfer that data to the
Finance department to facilitate payment hence they have to utilize FTP application. The
department members also connect to the wide area network hence the utilize HTTP application.
They also send emails meaning they utilize email application. The IT department, on the other
hand, is used to secure the organization network and files this means that they have to utilize
HTTP type of applications, sending emails thus utilizing email application, and sending of files
thus utilizing FTP application. The medical department is mandated in managing patient data;
the depart host the hospital management software. This is an example of a database application
which is used to enter and retrieve patient information. The department also connects to the wide
area network thus utilizing HTTP application and sending of files to the other sections thus they
utilizes the FTP application.
Configuring the Http application
To configure HTTP application in riverbed one ought to select built-in models and pre-
set configurations; for this scenario, heavy browsing was selected. Also, HTTP specification that
for each department. The required traffic is generated after both the profile configuration and
application objects.
User profiles and justification
As highlighted in part one there are four departments but here, this section the project
will only utilize three department profiles. The HR department is mandated in managing
employees’ data. The IT department mandated to maintain the organization network. The
medical department mandated to keep patient records.
The HR department keeps records of the hours worked for each employee as they are
paid according to the number of employees. This means that they have to transfer that data to the
Finance department to facilitate payment hence they have to utilize FTP application. The
department members also connect to the wide area network hence the utilize HTTP application.
They also send emails meaning they utilize email application. The IT department, on the other
hand, is used to secure the organization network and files this means that they have to utilize
HTTP type of applications, sending emails thus utilizing email application, and sending of files
thus utilizing FTP application. The medical department is mandated in managing patient data;
the depart host the hospital management software. This is an example of a database application
which is used to enter and retrieve patient information. The department also connects to the wide
area network thus utilizing HTTP application and sending of files to the other sections thus they
utilizes the FTP application.
Configuring the Http application
To configure HTTP application in riverbed one ought to select built-in models and pre-
set configurations; for this scenario, heavy browsing was selected. Also, HTTP specification that
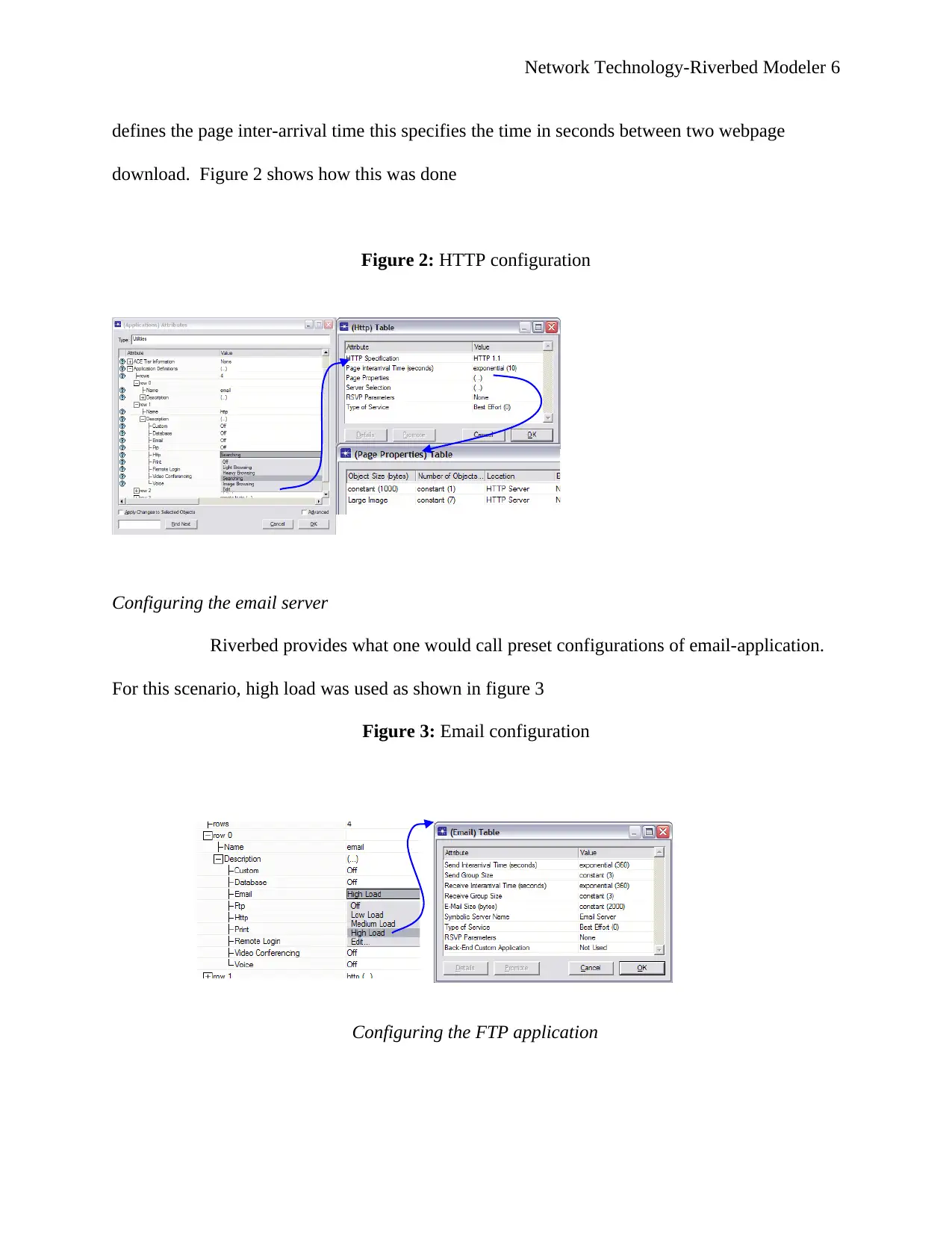
Network Technology-Riverbed Modeler 6
defines the page inter-arrival time this specifies the time in seconds between two webpage
download. Figure 2 shows how this was done
Figure 2: HTTP configuration
Configuring the email server
Riverbed provides what one would call preset configurations of email-application.
For this scenario, high load was used as shown in figure 3
Figure 3: Email configuration
Configuring the FTP application
defines the page inter-arrival time this specifies the time in seconds between two webpage
download. Figure 2 shows how this was done
Figure 2: HTTP configuration
Configuring the email server
Riverbed provides what one would call preset configurations of email-application.
For this scenario, high load was used as shown in figure 3
Figure 3: Email configuration
Configuring the FTP application
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
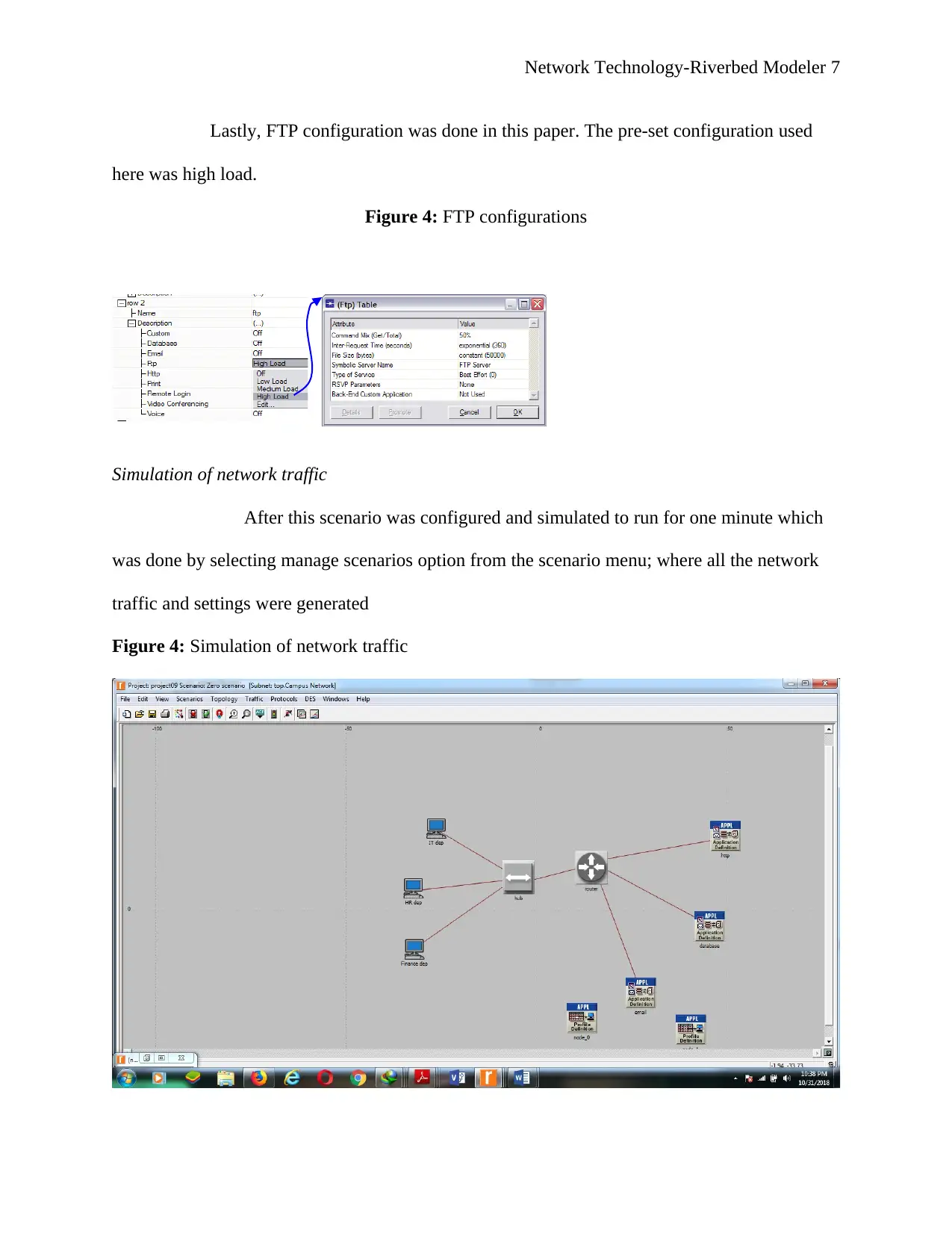
Network Technology-Riverbed Modeler 7
Lastly, FTP configuration was done in this paper. The pre-set configuration used
here was high load.
Figure 4: FTP configurations
Simulation of network traffic
After this scenario was configured and simulated to run for one minute which
was done by selecting manage scenarios option from the scenario menu; where all the network
traffic and settings were generated
Figure 4: Simulation of network traffic
Lastly, FTP configuration was done in this paper. The pre-set configuration used
here was high load.
Figure 4: FTP configurations
Simulation of network traffic
After this scenario was configured and simulated to run for one minute which
was done by selecting manage scenarios option from the scenario menu; where all the network
traffic and settings were generated
Figure 4: Simulation of network traffic
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
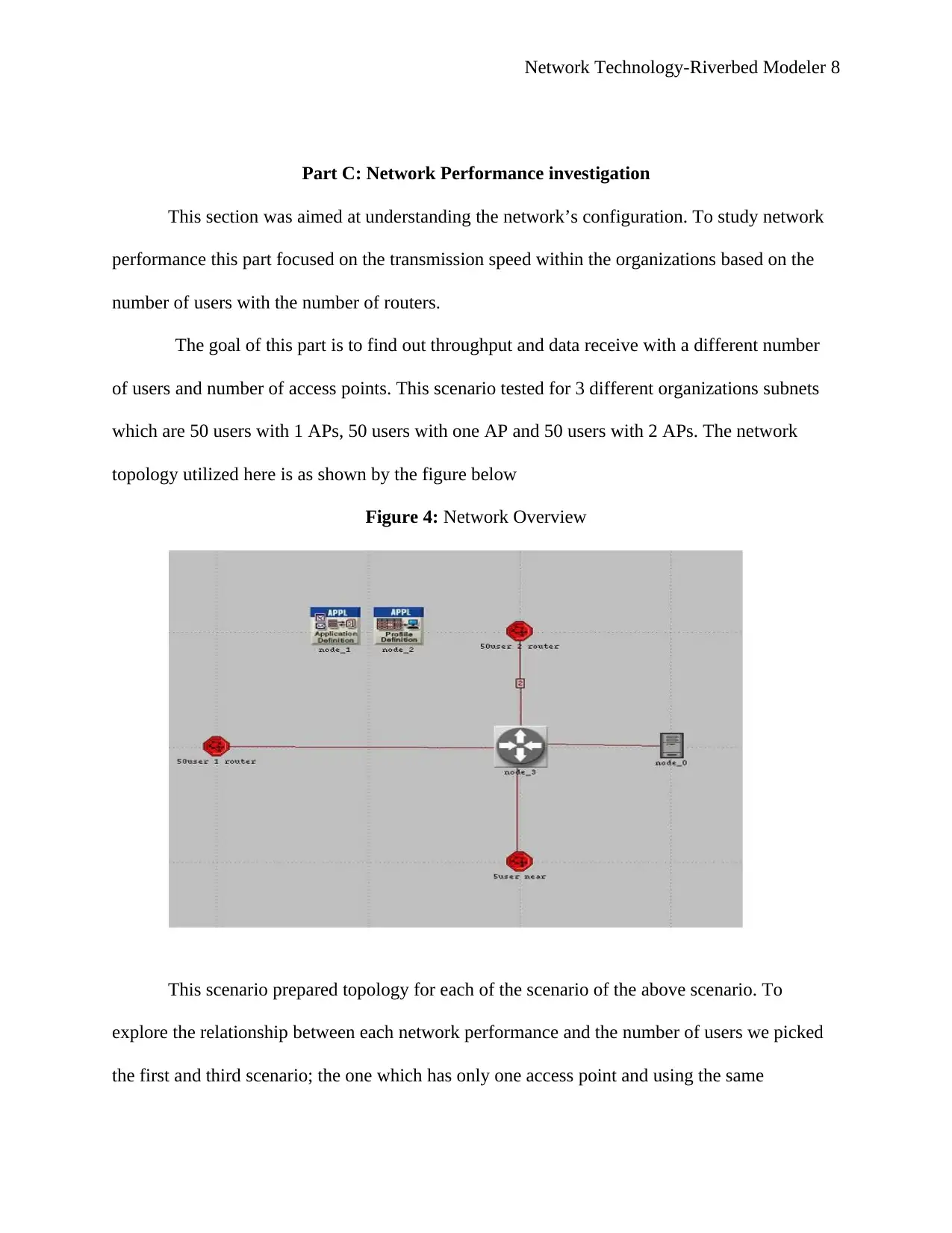
Network Technology-Riverbed Modeler 8
Part C: Network Performance investigation
This section was aimed at understanding the network’s configuration. To study network
performance this part focused on the transmission speed within the organizations based on the
number of users with the number of routers.
The goal of this part is to find out throughput and data receive with a different number
of users and number of access points. This scenario tested for 3 different organizations subnets
which are 50 users with 1 APs, 50 users with one AP and 50 users with 2 APs. The network
topology utilized here is as shown by the figure below
Figure 4: Network Overview
This scenario prepared topology for each of the scenario of the above scenario. To
explore the relationship between each network performance and the number of users we picked
the first and third scenario; the one which has only one access point and using the same
Part C: Network Performance investigation
This section was aimed at understanding the network’s configuration. To study network
performance this part focused on the transmission speed within the organizations based on the
number of users with the number of routers.
The goal of this part is to find out throughput and data receive with a different number
of users and number of access points. This scenario tested for 3 different organizations subnets
which are 50 users with 1 APs, 50 users with one AP and 50 users with 2 APs. The network
topology utilized here is as shown by the figure below
Figure 4: Network Overview
This scenario prepared topology for each of the scenario of the above scenario. To
explore the relationship between each network performance and the number of users we picked
the first and third scenario; the one which has only one access point and using the same
Network Technology-Riverbed Modeler 9
application. The first had 50 users in a subnet using 1 AP and 50 users using 2 APs. The
application utilized in here was video conference which preset to high load. The simulation time
was five minutes and simulating running time was 10 minutes.
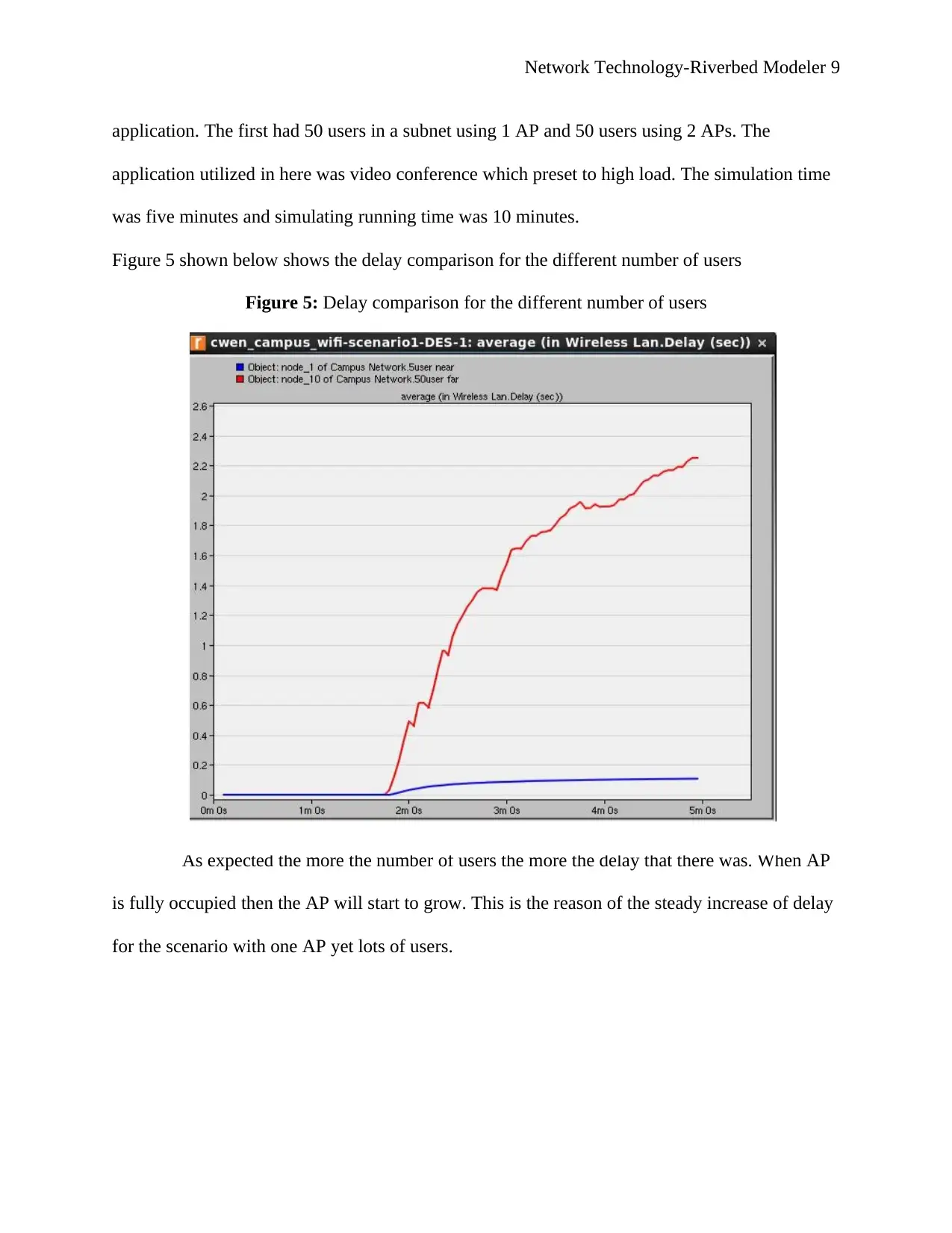
Figure 5 shown below shows the delay comparison for the different number of users
Figure 5: Delay comparison for the different number of users
As expected the more the number of users the more the delay that there was. When AP
is fully occupied then the AP will start to grow. This is the reason of the steady increase of delay
for the scenario with one AP yet lots of users.
application. The first had 50 users in a subnet using 1 AP and 50 users using 2 APs. The
application utilized in here was video conference which preset to high load. The simulation time
was five minutes and simulating running time was 10 minutes.
Figure 5 shown below shows the delay comparison for the different number of users
Figure 5: Delay comparison for the different number of users
As expected the more the number of users the more the delay that there was. When AP
is fully occupied then the AP will start to grow. This is the reason of the steady increase of delay
for the scenario with one AP yet lots of users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Network Technology-Riverbed Modeler 10
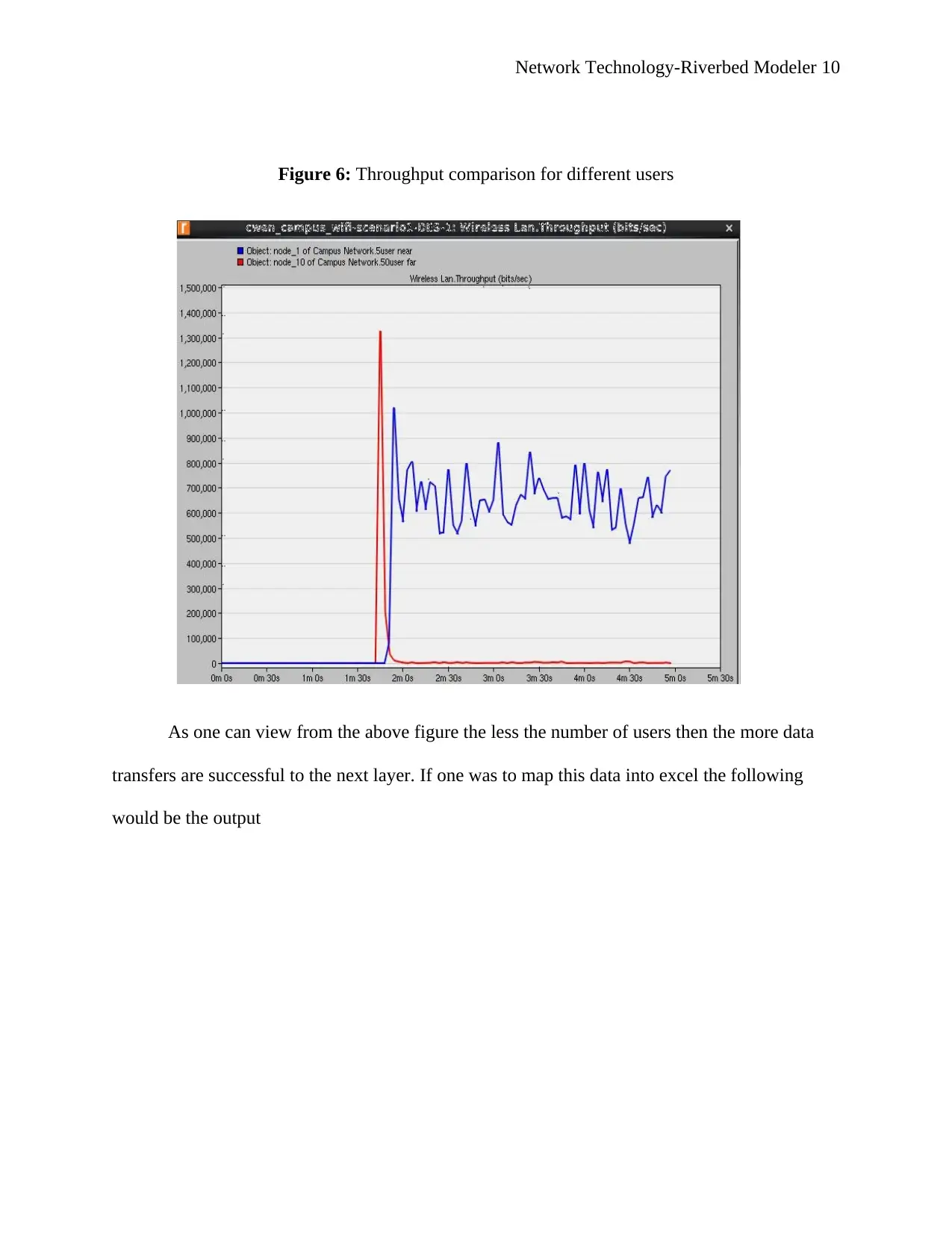
Figure 6: Throughput comparison for different users
As one can view from the above figure the less the number of users then the more data
transfers are successful to the next layer. If one was to map this data into excel the following
would be the output
Figure 6: Throughput comparison for different users
As one can view from the above figure the less the number of users then the more data
transfers are successful to the next layer. If one was to map this data into excel the following
would be the output
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Technology-Riverbed Modeler 11
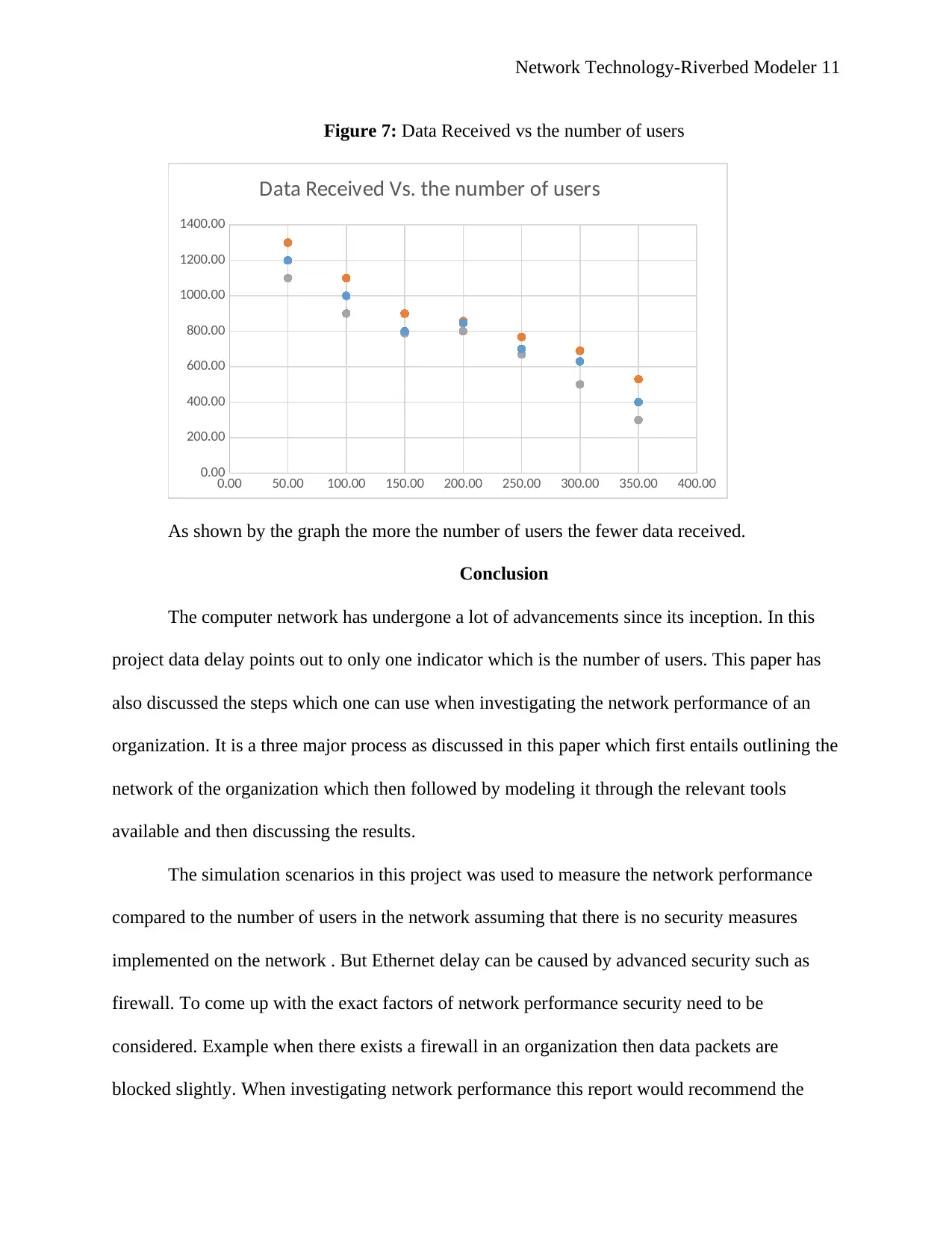
Figure 7: Data Received vs the number of users
0.00 50.00 100.00 150.00 200.00 250.00 300.00 350.00 400.00
0.00
200.00
400.00
600.00
800.00
1000.00
1200.00
1400.00
Data Received Vs. the number of users
As shown by the graph the more the number of users the fewer data received.
Conclusion
The computer network has undergone a lot of advancements since its inception. In this
project data delay points out to only one indicator which is the number of users. This paper has
also discussed the steps which one can use when investigating the network performance of an
organization. It is a three major process as discussed in this paper which first entails outlining the
network of the organization which then followed by modeling it through the relevant tools
available and then discussing the results.
The simulation scenarios in this project was used to measure the network performance
compared to the number of users in the network assuming that there is no security measures
implemented on the network . But Ethernet delay can be caused by advanced security such as
firewall. To come up with the exact factors of network performance security need to be
considered. Example when there exists a firewall in an organization then data packets are
blocked slightly. When investigating network performance this report would recommend the
Figure 7: Data Received vs the number of users
0.00 50.00 100.00 150.00 200.00 250.00 300.00 350.00 400.00
0.00
200.00
400.00
600.00
800.00
1000.00
1200.00
1400.00
Data Received Vs. the number of users
As shown by the graph the more the number of users the fewer data received.
Conclusion
The computer network has undergone a lot of advancements since its inception. In this
project data delay points out to only one indicator which is the number of users. This paper has
also discussed the steps which one can use when investigating the network performance of an
organization. It is a three major process as discussed in this paper which first entails outlining the
network of the organization which then followed by modeling it through the relevant tools
available and then discussing the results.
The simulation scenarios in this project was used to measure the network performance
compared to the number of users in the network assuming that there is no security measures
implemented on the network . But Ethernet delay can be caused by advanced security such as
firewall. To come up with the exact factors of network performance security need to be
considered. Example when there exists a firewall in an organization then data packets are
blocked slightly. When investigating network performance this report would recommend the

Network Technology-Riverbed Modeler 12
fours factors to be always considered which are; the number of users, no security measures on
the network, limited security measures on the network, and advances security measures. The last
three factors need to keep the number of users constant.
References
fours factors to be always considered which are; the number of users, no security measures on
the network, limited security measures on the network, and advances security measures. The last
three factors need to keep the number of users constant.
References
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




