Network Topology Report: Chicago Consulting Network Design Analysis
VerifiedAdded on 2023/01/12
|9
|1018
|90
Report
AI Summary
This report provides a detailed analysis of network topology, focusing on the requirements of Chicago Consulting. The report begins with an overview of five basic control principles crucial for securing a network, particularly in the context of a bank's system. It then outlines the network design for Chicago Consulting, detailing the connection of LAN segments to a core switch, the inclusion of wireless access points, and internet connectivity via a firewall. The design incorporates a network diagram and a breakdown of component costs, including hardware like computers, servers, switches, and printers. The report emphasizes the importance of maintaining proper security throughout the network, covering aspects like data center security, database records, and server efficiency. It also discusses network upgrades and the allocation for VoIP systems. The report references several academic sources for further insights into network security and performance.

Running head: NETWORK TOPOLOGY
Network Topology
Name of the Student:
Name of the University:
Author Note
Network Topology
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK TOPOLOGY
A. Five basic control principles
The basic control principles that are important for securing a networking for the
MinnEast bank system includes
Keeping proper patches and updated system
Using strong password for maintain proper security
Securing the networks VPN
Managing the user access privileges actively
Cleaning up inactive accounts.
B. Chicago consulting
Introduction
The report consists of the details of the network requirements for the Chicago consulting
organization. The organization currently is looking to develop a network that would be
connecting the departments of the organization to a core switch. The network should also have
wireless access and the features enabled for the conference room. In addition to this, the
organization should also be able to have internet connection and LAN facilities within the
network.
The report has been used here for the detailed explanation of the network topology to be
used for the organization along with the cost associated with it for the implementation of the
network.
NETWORK TOPOLOGY
A. Five basic control principles
The basic control principles that are important for securing a networking for the
MinnEast bank system includes
Keeping proper patches and updated system
Using strong password for maintain proper security
Securing the networks VPN
Managing the user access privileges actively
Cleaning up inactive accounts.
B. Chicago consulting
Introduction
The report consists of the details of the network requirements for the Chicago consulting
organization. The organization currently is looking to develop a network that would be
connecting the departments of the organization to a core switch. The network should also have
wireless access and the features enabled for the conference room. In addition to this, the
organization should also be able to have internet connection and LAN facilities within the
network.
The report has been used here for the detailed explanation of the network topology to be
used for the organization along with the cost associated with it for the implementation of the
network.
2
NETWORK TOPOLOGY
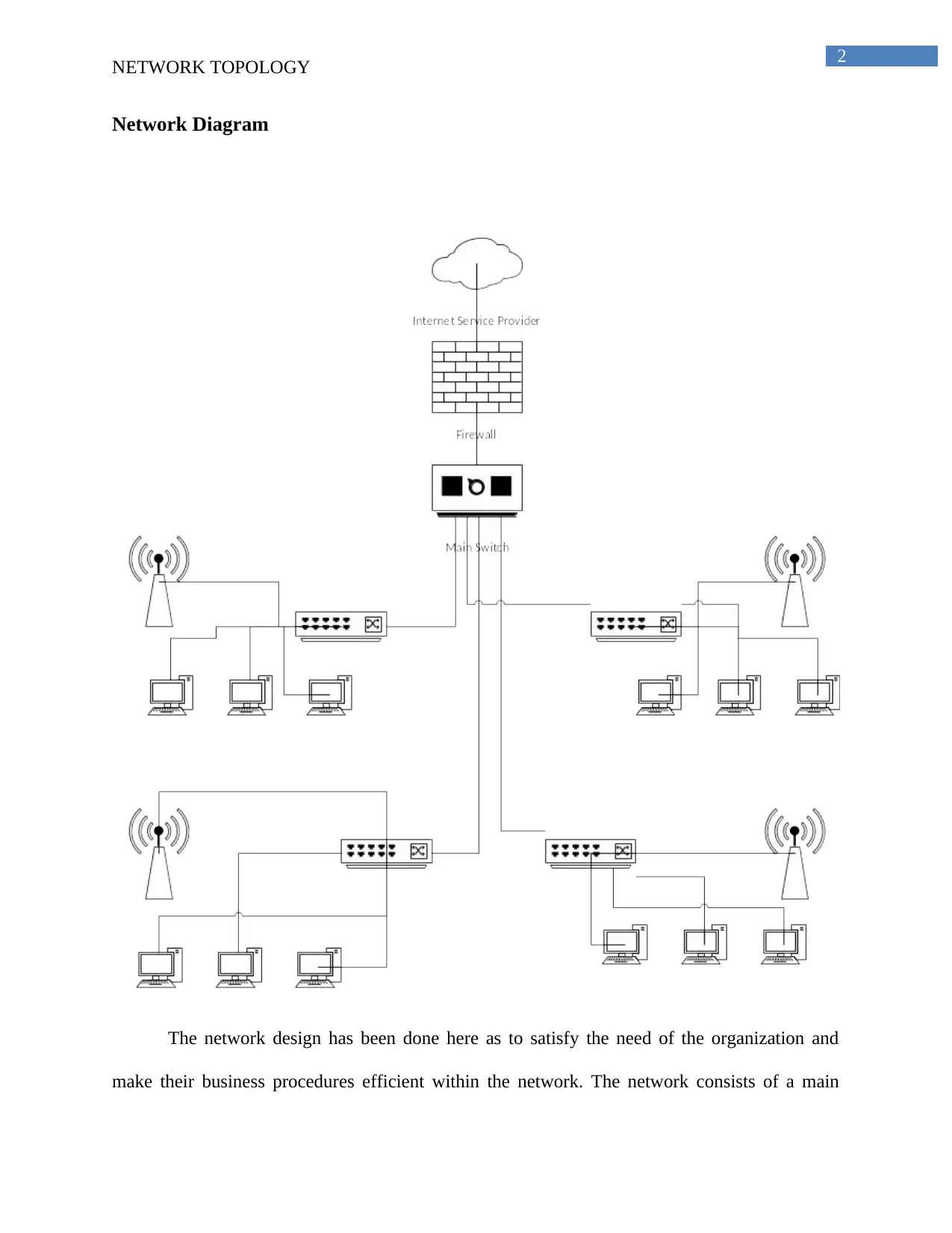
Network Diagram
The network design has been done here as to satisfy the need of the organization and
make their business procedures efficient within the network. The network consists of a main
NETWORK TOPOLOGY
Network Diagram
The network design has been done here as to satisfy the need of the organization and
make their business procedures efficient within the network. The network consists of a main
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK TOPOLOGY
switch which would be connecting the four other switches for the four other departments in the
network. The wireless access points have been installed in the network to provide wireless access
to the users in the network. The main switch is connected to the internet, however the connection
passes through the firewall which protects the network from the outside interference. In addition
to this, the network would be having access controls for the wireless access points installed in the
network. This would take care of the security constraints in the network and prohibit
unauthorized access to the network.
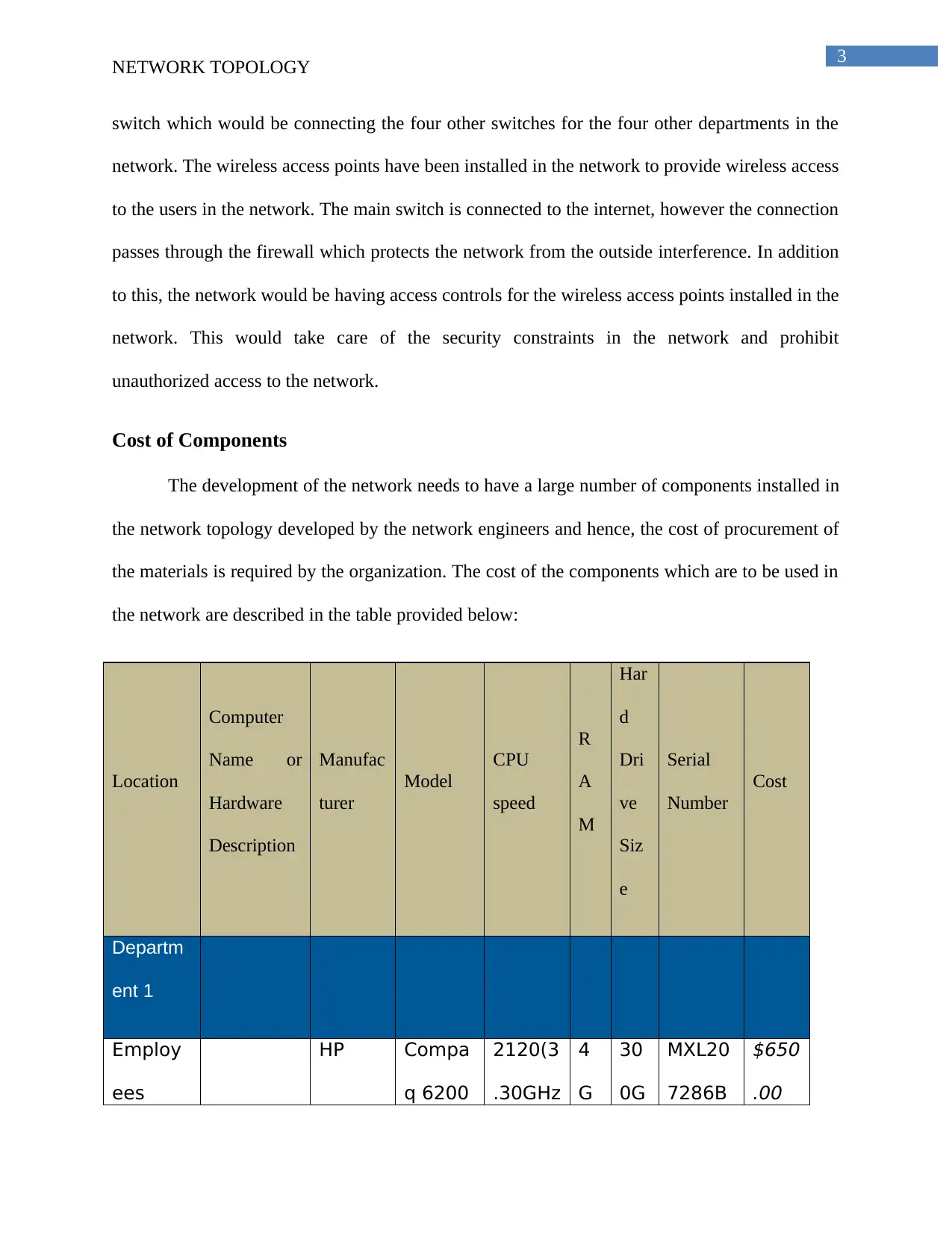
Cost of Components
The development of the network needs to have a large number of components installed in
the network topology developed by the network engineers and hence, the cost of procurement of
the materials is required by the organization. The cost of the components which are to be used in
the network are described in the table provided below:
Location
Computer
Name or
Hardware
Description
Manufac
turer
Model
CPU
speed
R
A
M
Har
d
Dri
ve
Siz
e
Serial
Number
Cost
Departm
ent 1
Employ
ees
HP Compa
q 6200
2120(3
.30GHz
4
G
30
0G
MXL20
7286B
$650
.00
NETWORK TOPOLOGY
switch which would be connecting the four other switches for the four other departments in the
network. The wireless access points have been installed in the network to provide wireless access
to the users in the network. The main switch is connected to the internet, however the connection
passes through the firewall which protects the network from the outside interference. In addition
to this, the network would be having access controls for the wireless access points installed in the
network. This would take care of the security constraints in the network and prohibit
unauthorized access to the network.
Cost of Components
The development of the network needs to have a large number of components installed in
the network topology developed by the network engineers and hence, the cost of procurement of
the materials is required by the organization. The cost of the components which are to be used in
the network are described in the table provided below:
Location
Computer
Name or
Hardware
Description
Manufac
turer
Model
CPU
speed
R
A
M
Har
d
Dri
ve
Siz
e
Serial
Number
Cost
Departm
ent 1
Employ
ees
HP Compa
q 6200
2120(3
.30GHz
4
G
30
0G
MXL20
7286B
$650
.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK TOPOLOGY
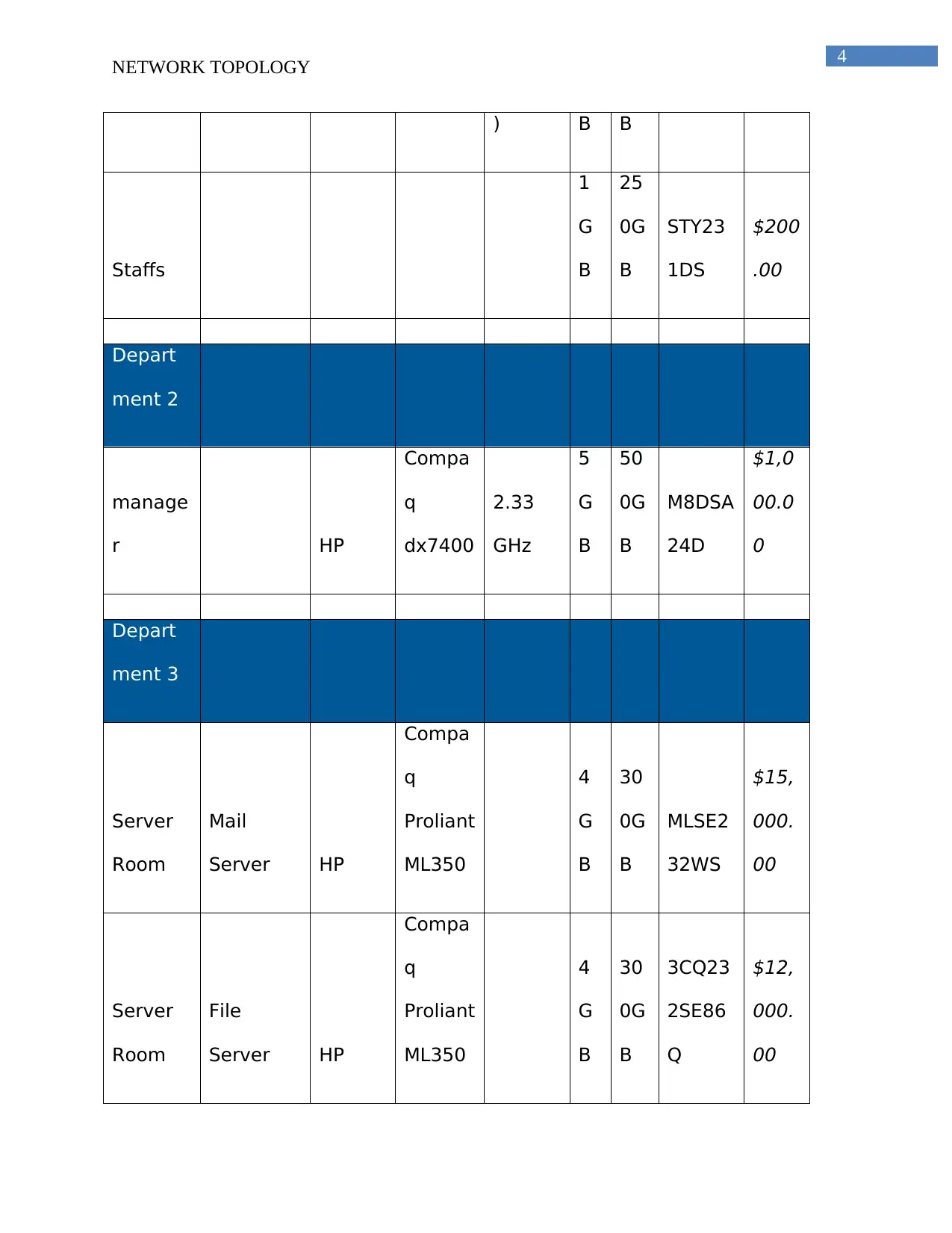
) B B
Staffs
1
G
B
25
0G
B
STY23
1DS
$200
.00
Depart
ment 2
manage
r HP
Compa
q
dx7400
2.33
GHz
5
G
B
50
0G
B
M8DSA
24D
$1,0
00.0
0
Depart
ment 3
Server
Room
Mail
Server HP
Compa
q
Proliant
ML350
4
G
B
30
0G
B
MLSE2
32WS
$15,
000.
00
Server
Room
File
Server HP
Compa
q
Proliant
ML350
4
G
B
30
0G
B
3CQ23
2SE86
Q
$12,
000.
00
NETWORK TOPOLOGY
) B B
Staffs
1
G
B
25
0G
B
STY23
1DS
$200
.00
Depart
ment 2
manage
r HP
Compa
q
dx7400
2.33
GHz
5
G
B
50
0G
B
M8DSA
24D
$1,0
00.0
0
Depart
ment 3
Server
Room
Server HP
Compa
q
Proliant
ML350
4
G
B
30
0G
B
MLSE2
32WS
$15,
000.
00
Server
Room
File
Server HP
Compa
q
Proliant
ML350
4
G
B
30
0G
B
3CQ23
2SE86
Q
$12,
000.
00
5
NETWORK TOPOLOGY
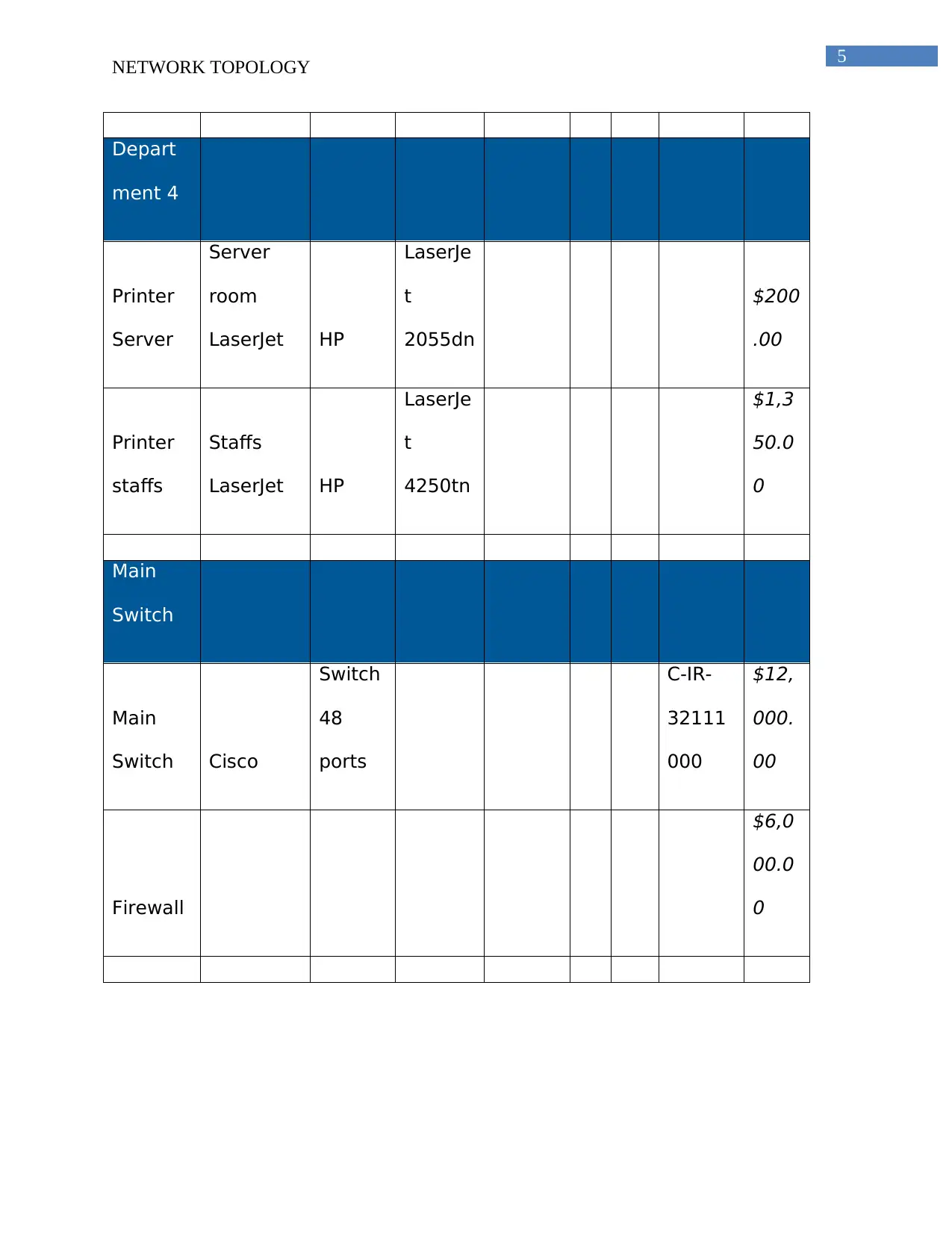
Depart
ment 4
Printer
Server
Server
room
LaserJet HP
LaserJe
t
2055dn
$200
.00
Printer
staffs
Staffs
LaserJet HP
LaserJe
t
4250tn
$1,3
50.0
0
Main
Switch
Main
Switch Cisco
Switch
48
ports
C-IR-
32111
000
$12,
000.
00
Firewall
$6,0
00.0
0
NETWORK TOPOLOGY
Depart
ment 4
Printer
Server
Server
room
LaserJet HP
LaserJe
t
2055dn
$200
.00
Printer
staffs
Staffs
LaserJet HP
LaserJe
t
4250tn
$1,3
50.0
0
Main
Switch
Main
Switch Cisco
Switch
48
ports
C-IR-
32111
000
$12,
000.
00
Firewall
$6,0
00.0
0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK TOPOLOGY
Hardw
are
Total
$48,
400.
00
F. Data center
The main reason behind providing money towards the services providers is to ensure that
proper security is maintained throughout the network and other applications. This will help in
keeping better details regarding the network.
The reasons behind providing money towards the servers, database and host are as
follows:
This ensures better security towards the network.
Maintain proper database records.
Ensures better efficiency from the servers
Network can be easily determined by the organization
Proper control can be kept on the activities performed by the network.
NETWORK TOPOLOGY
Hardw
are
Total
$48,
400.
00
F. Data center
The main reason behind providing money towards the services providers is to ensure that
proper security is maintained throughout the network and other applications. This will help in
keeping better details regarding the network.
The reasons behind providing money towards the servers, database and host are as
follows:
This ensures better security towards the network.
Maintain proper database records.
Ensures better efficiency from the servers
Network can be easily determined by the organization
Proper control can be kept on the activities performed by the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK TOPOLOGY
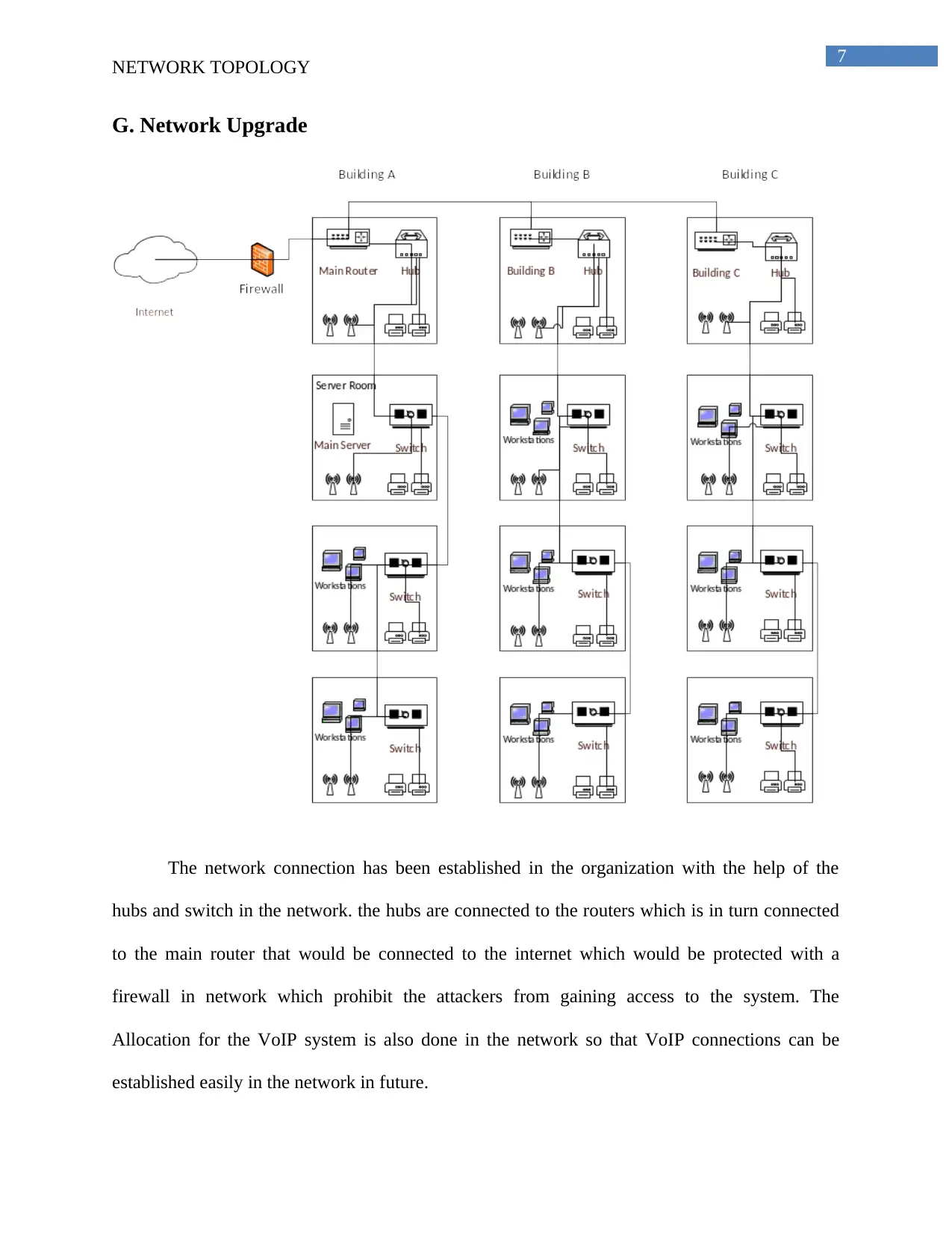
G. Network Upgrade
The network connection has been established in the organization with the help of the
hubs and switch in the network. the hubs are connected to the routers which is in turn connected
to the main router that would be connected to the internet which would be protected with a
firewall in network which prohibit the attackers from gaining access to the system. The
Allocation for the VoIP system is also done in the network so that VoIP connections can be
established easily in the network in future.
NETWORK TOPOLOGY
G. Network Upgrade
The network connection has been established in the organization with the help of the
hubs and switch in the network. the hubs are connected to the routers which is in turn connected
to the main router that would be connected to the internet which would be protected with a
firewall in network which prohibit the attackers from gaining access to the system. The
Allocation for the VoIP system is also done in the network so that VoIP connections can be
established easily in the network in future.

8
NETWORK TOPOLOGY
Bibliography
Wurm, J., Hoang, K., Arias, O., Sadeghi, A. R., & Jin, Y. (2016, January). Security analysis on
consumer and industrial IoT devices. In 2016 21st Asia and South Pacific Design
Automation Conference (ASP-DAC) (pp. 519-524). IEEE.
Ventura, D., Gómez-Goiri, A., Catania, V., López-de-Ipiña, D., Naranjo, J. A. M., & Casado, L.
G. (2015). Security analysis and resource requirements of group-oriented user access
control for hardware-constrained wireless network services.
Ferraiuolo, A., Xu, R., Zhang, D., Myers, A. C., & Suh, G. E. (2017, April). Verification of a
practical hardware security architecture through static information flow analysis. In ACM
SIGARCH Computer Architecture News (Vol. 45, No. 1, pp. 555-568). ACM.
Brown, K. A., Domke, J., & Matsuoka, S. (2015, December). Hardware-centric analysis of
network performance for MPI applications. In 2015 IEEE 21st International Conference
on Parallel and Distributed Systems (ICPADS) (pp. 692-699). IEEE.
NETWORK TOPOLOGY
Bibliography
Wurm, J., Hoang, K., Arias, O., Sadeghi, A. R., & Jin, Y. (2016, January). Security analysis on
consumer and industrial IoT devices. In 2016 21st Asia and South Pacific Design
Automation Conference (ASP-DAC) (pp. 519-524). IEEE.
Ventura, D., Gómez-Goiri, A., Catania, V., López-de-Ipiña, D., Naranjo, J. A. M., & Casado, L.
G. (2015). Security analysis and resource requirements of group-oriented user access
control for hardware-constrained wireless network services.
Ferraiuolo, A., Xu, R., Zhang, D., Myers, A. C., & Suh, G. E. (2017, April). Verification of a
practical hardware security architecture through static information flow analysis. In ACM
SIGARCH Computer Architecture News (Vol. 45, No. 1, pp. 555-568). ACM.
Brown, K. A., Domke, J., & Matsuoka, S. (2015, December). Hardware-centric analysis of
network performance for MPI applications. In 2015 IEEE 21st International Conference
on Parallel and Distributed Systems (ICPADS) (pp. 692-699). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



