Examine Networking Principles and Protocols Report
VerifiedAdded on 2020/07/22
|14
|3714
|47
Report
AI Summary
This report delves into the principles and protocols of computer networking, focusing on the implementation within a college technology center. It examines the purposes and benefits of network systems, including improved communication, resource sharing, and collaboration. The report covers various conceptual models, such as the OSI and TCP/IP models, and explores different system types, including peer-to-peer, client-server, and cloud systems. It further analyzes Ethernet, various network topologies (LAN, MAN, WAN, Token Ring, Star, Bus, Mesh, Tree), and IP addressing (IPv4 and IPv6). Additionally, the report discusses networking devices such as servers, hubs, routers, switches, firewalls, and wireless devices. The report aims to provide a comprehensive understanding of network design, implementation, and management, which can be used in educational settings.

Examine networking
principles and their protocols
principles and their protocols
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
P1 and P2................................................................................................................................1
A. Explain the roles:...............................................................................................................2
B. Explain...............................................................................................................................2
C. Examine the system types:.................................................................................................4
D. Explain...............................................................................................................................5
E. Explain...............................................................................................................................6
TASK 2............................................................................................................................................7
A Networking devices............................................................................................................7
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
P1 and P2................................................................................................................................1
A. Explain the roles:...............................................................................................................2
B. Explain...............................................................................................................................2
C. Examine the system types:.................................................................................................4
D. Explain...............................................................................................................................5
E. Explain...............................................................................................................................6
TASK 2............................................................................................................................................7
A Networking devices............................................................................................................7
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8

Illustration Index
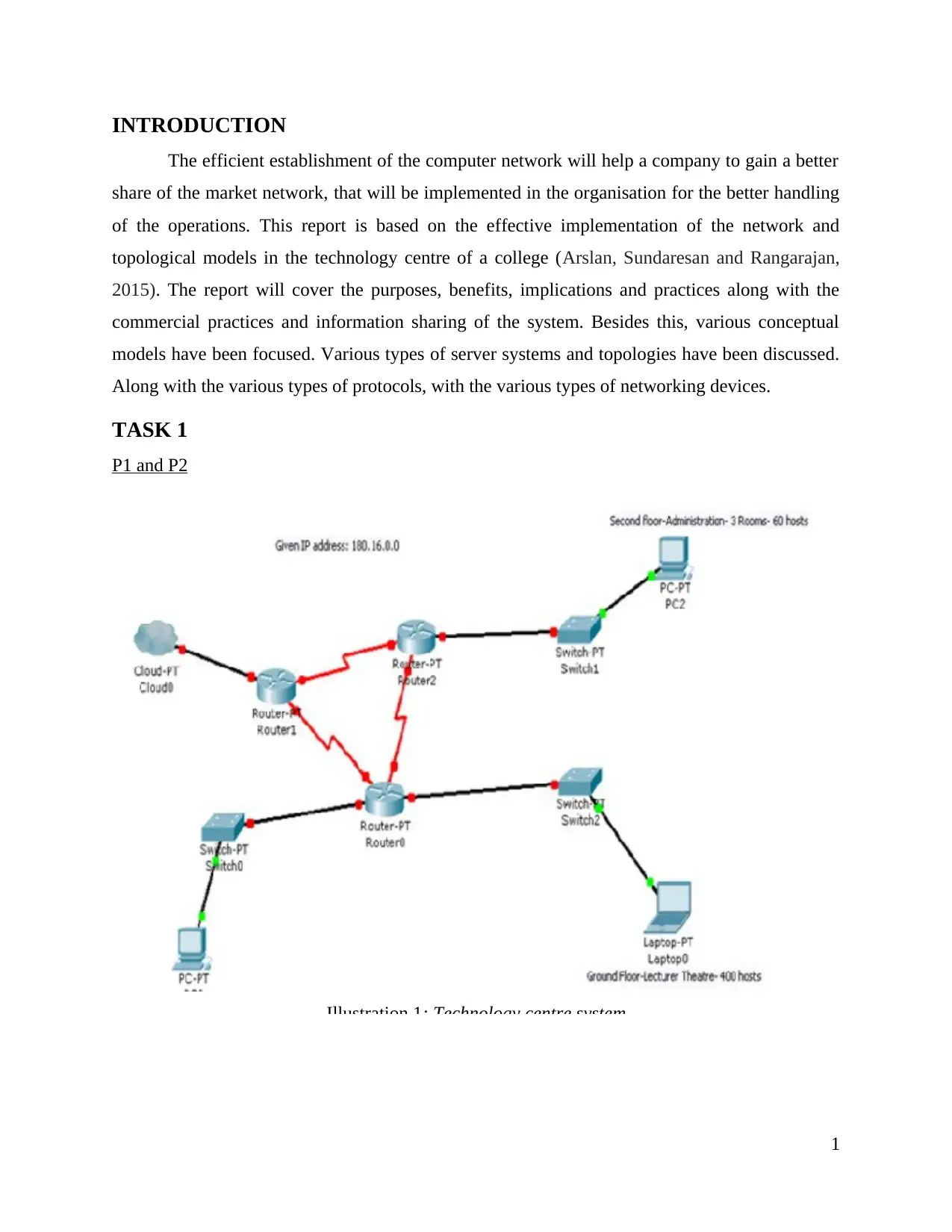
Illustration 1: Technology centre system.........................................................................................1
Illustration 2: OSI model.................................................................................................................3
Illustration 1: Technology centre system.........................................................................................1
Illustration 2: OSI model.................................................................................................................3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTRODUCTION
The efficient establishment of the computer network will help a company to gain a better
share of the market network, that will be implemented in the organisation for the better handling
of the operations. This report is based on the effective implementation of the network and
topological models in the technology centre of a college (Arslan, Sundaresan and Rangarajan,
2015). The report will cover the purposes, benefits, implications and practices along with the
commercial practices and information sharing of the system. Besides this, various conceptual
models have been focused. Various types of server systems and topologies have been discussed.
Along with the various types of protocols, with the various types of networking devices.
TASK 1
P1 and P2
1
Illustration 1: Technology centre system
The efficient establishment of the computer network will help a company to gain a better
share of the market network, that will be implemented in the organisation for the better handling
of the operations. This report is based on the effective implementation of the network and
topological models in the technology centre of a college (Arslan, Sundaresan and Rangarajan,
2015). The report will cover the purposes, benefits, implications and practices along with the
commercial practices and information sharing of the system. Besides this, various conceptual
models have been focused. Various types of server systems and topologies have been discussed.
Along with the various types of protocols, with the various types of networking devices.
TASK 1
P1 and P2
1
Illustration 1: Technology centre system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A. Explain the roles:
Purpose: The major purpose of using this system is to interconnect various components of the
technology centre of a college.
Benefits: The implementation of the above system will help the college to improve operations of
various departments in a very efficient and effective manner (Broll and et.al., 2017).
Some major benefits of using this system are:
Increase in the communication efficiency of the college.
It will help the college to cater the curriculum and other support services.
Resources implications: Various resources will be used in this system and helps the college to
maintain its operations in a better way.
Communication: The effective communication between various system admins will help in the
impelling establishment of the above system in the college (Carofiglio and et.al., 2015).
Working practice: Different types of working practices will help the college to implement the
operations of the above discussed system. This system will improve the work efficiency of
different departments of the college.
Commercial opportunities: The implementation of the above system will increase the work
efficiency of the college management and administration. However, rise in the work efficiency
will help the institution to gain better productivity and profitability.
Information Sharing: The implementation of the proposed system will help to increase the
information sharing process of the college. The interconnection of the various departments and
levels of the college will aid in better information or data sharing at given institution (Hu, 2014).
Collaboration: The proposed system will also help to improve the collaboration with other
organisations and departments of the college. This coordination will help the company to have
better productivity and resource sharing at the given college.
B. Explain
OSI Model: Open System Interconnection (OSI) model is a network framework that helps to
gain a better share of the market. This model is used to implement the network protocol in layers
of the company which are as follows:
2
Purpose: The major purpose of using this system is to interconnect various components of the
technology centre of a college.
Benefits: The implementation of the above system will help the college to improve operations of
various departments in a very efficient and effective manner (Broll and et.al., 2017).
Some major benefits of using this system are:
Increase in the communication efficiency of the college.
It will help the college to cater the curriculum and other support services.
Resources implications: Various resources will be used in this system and helps the college to
maintain its operations in a better way.
Communication: The effective communication between various system admins will help in the
impelling establishment of the above system in the college (Carofiglio and et.al., 2015).
Working practice: Different types of working practices will help the college to implement the
operations of the above discussed system. This system will improve the work efficiency of
different departments of the college.
Commercial opportunities: The implementation of the above system will increase the work
efficiency of the college management and administration. However, rise in the work efficiency
will help the institution to gain better productivity and profitability.
Information Sharing: The implementation of the proposed system will help to increase the
information sharing process of the college. The interconnection of the various departments and
levels of the college will aid in better information or data sharing at given institution (Hu, 2014).
Collaboration: The proposed system will also help to improve the collaboration with other
organisations and departments of the college. This coordination will help the company to have
better productivity and resource sharing at the given college.
B. Explain
OSI Model: Open System Interconnection (OSI) model is a network framework that helps to
gain a better share of the market. This model is used to implement the network protocol in layers
of the company which are as follows:
2
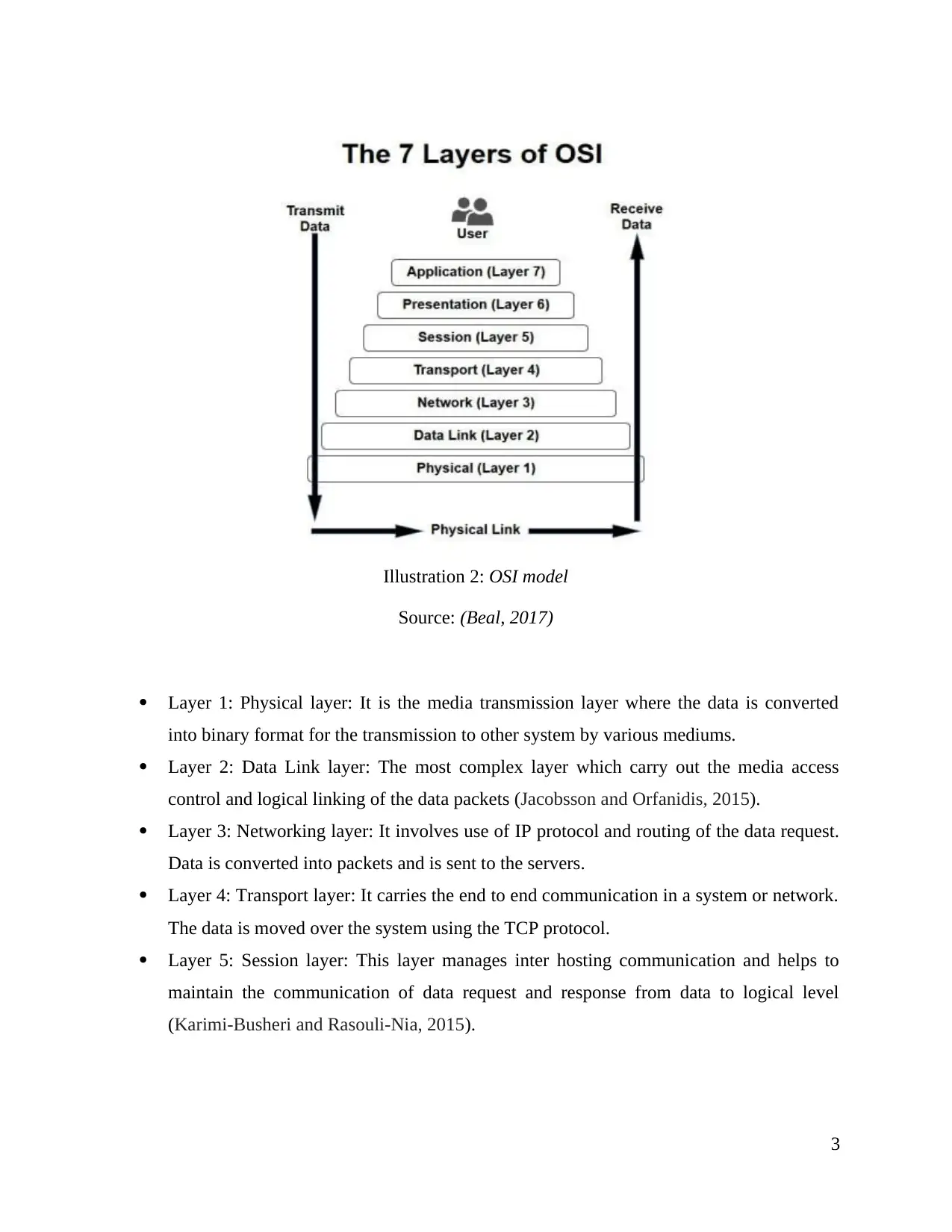
Layer 1: Physical layer: It is the media transmission layer where the data is converted
into binary format for the transmission to other system by various mediums.
Layer 2: Data Link layer: The most complex layer which carry out the media access
control and logical linking of the data packets (Jacobsson and Orfanidis, 2015).
Layer 3: Networking layer: It involves use of IP protocol and routing of the data request.
Data is converted into packets and is sent to the servers.
Layer 4: Transport layer: It carries the end to end communication in a system or network.
The data is moved over the system using the TCP protocol.
Layer 5: Session layer: This layer manages inter hosting communication and helps to
maintain the communication of data request and response from data to logical level
(Karimi-Busheri and Rasouli-Nia, 2015).
3
Illustration 2: OSI model
Source: (Beal, 2017)
into binary format for the transmission to other system by various mediums.
Layer 2: Data Link layer: The most complex layer which carry out the media access
control and logical linking of the data packets (Jacobsson and Orfanidis, 2015).
Layer 3: Networking layer: It involves use of IP protocol and routing of the data request.
Data is converted into packets and is sent to the servers.
Layer 4: Transport layer: It carries the end to end communication in a system or network.
The data is moved over the system using the TCP protocol.
Layer 5: Session layer: This layer manages inter hosting communication and helps to
maintain the communication of data request and response from data to logical level
(Karimi-Busheri and Rasouli-Nia, 2015).
3
Illustration 2: OSI model
Source: (Beal, 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Layer 6: Presentation layer: Also known as the data representation layer, it consists of the
encryption protocols that help in maintaining safety of the data and the system. It
includes various protocols like ASCII, MIDI etc.
Layer 7: Application layer: This is on the side of end user where the user looks at the web
application. This involves the web application, web browsers and SMTP or HTTP
protocols (Khan, Rehmani and Reisslein, 2016).
TCP/IP Model: The TCP/IP model will help to interlink its system to the internet and the local
server. It helps the system to use the computer protocols in a very effective manner, in order to
design a computer network in an organisation. The TCP/IP model has four layers named:
Networking or Access layer, Internet or connection layer, Transportation layer and Application
layer.
IEEE 802.x: The IEEE 802.x is the set of the standards and the protocols that are being taken
into consideration and helps in the effective management of various protocols that are being
implemented at the organisation (Lee and et.al., 2014). They are primarily used for setting up of
Ethernet in the organisation and helps in their effective management. They are suitable for the
network carrying limited amount of data (Li, 2015).
C. Examine the system types:
Peer based system: Also known as the peer to peer system that helps to gain better productivity
by connecting two or more PCs to share file and access the peripheral devices in sharing from
various computers or over the server.
Client server system: The client server system is the network setup which consists of the client
PC or the system. In majority of the cases or the networks, there is a single server PC which is
connected to the multiple client PC and communication is carried out between the client system
and that on the server side (Maj and et.al., 2016).
Cloud System: This is the latest and widely used network or the system type in the present
scenario. In this, the client uses the services of a remotely located cloud service provider to carry
out its operation. The cloud service provider will help to carry out its operations by providing
various types of software, networking and storage facility to the client.
Cluster system: The cluster system is the network of the loosely and tightly connected systems
that are interconnected to each other in a random and complex manner (Truong and Dustdar,
4
encryption protocols that help in maintaining safety of the data and the system. It
includes various protocols like ASCII, MIDI etc.
Layer 7: Application layer: This is on the side of end user where the user looks at the web
application. This involves the web application, web browsers and SMTP or HTTP
protocols (Khan, Rehmani and Reisslein, 2016).
TCP/IP Model: The TCP/IP model will help to interlink its system to the internet and the local
server. It helps the system to use the computer protocols in a very effective manner, in order to
design a computer network in an organisation. The TCP/IP model has four layers named:
Networking or Access layer, Internet or connection layer, Transportation layer and Application
layer.
IEEE 802.x: The IEEE 802.x is the set of the standards and the protocols that are being taken
into consideration and helps in the effective management of various protocols that are being
implemented at the organisation (Lee and et.al., 2014). They are primarily used for setting up of
Ethernet in the organisation and helps in their effective management. They are suitable for the
network carrying limited amount of data (Li, 2015).
C. Examine the system types:
Peer based system: Also known as the peer to peer system that helps to gain better productivity
by connecting two or more PCs to share file and access the peripheral devices in sharing from
various computers or over the server.
Client server system: The client server system is the network setup which consists of the client
PC or the system. In majority of the cases or the networks, there is a single server PC which is
connected to the multiple client PC and communication is carried out between the client system
and that on the server side (Maj and et.al., 2016).
Cloud System: This is the latest and widely used network or the system type in the present
scenario. In this, the client uses the services of a remotely located cloud service provider to carry
out its operation. The cloud service provider will help to carry out its operations by providing
various types of software, networking and storage facility to the client.
Cluster system: The cluster system is the network of the loosely and tightly connected systems
that are interconnected to each other in a random and complex manner (Truong and Dustdar,
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2015). This method of networking is done in order to make a single system. In the cluster
system, every PC or the system that is being connected performs a common task.
Centralised: It is the network system where various PCs or systems are being connected to the
centralised computer system that will look after all the operations to the connected PCs. The
centralised system will have a control over the operations of the peripheral systems. The systems
are either the part of the local system or may be placed remotely, connected through various
connection mediums to the terminal or the main server at the workplace (van Adrichem and
Kuipers, 2015).
D. Explain
Ethernet: It is a type of internet network or connection that is being carried out in the system or
an organisation. This is usually set up in an organisation or a building but can be used on the
wider level. It consists of mainly 3 types of the system such as:
LAN: It stands for Local Area Network. This is the system, in which the network is being
set up on a local level i.e. a building, lab or an office etc. they are less complex and have
moderate computing speed.
MAN: It abbreviates to Metropolitan Area Network. This is usually established on the
city or the area level and is more complex and critical to maintain as compared to the
LAN. It is used by offices with various branches in a city or an area (Vilalta and et.al.,
2015).
WAN: This stands for Wide Area Network. It is on the national or the international level
and is mainly based on the operations of many smaller networks. This is the most
complex system and requires greater effort and computational power to maintain and
handle.
Token Ring topology: A token ring topology will help the organisation to set its network and
the system in a better and efficient manner. It is a LAN system and the systems are being
connected in a loop or a ring set up to avoid any glitches of sending one message to multiple
systems and improve the connectivity (Wang and et.al., 2015). The major drawback is that if one
system disconnects, the loop breaks and the system comes down. Here, the nodes or the PCs
connected are called as Tokens.
Physical
5
system, every PC or the system that is being connected performs a common task.
Centralised: It is the network system where various PCs or systems are being connected to the
centralised computer system that will look after all the operations to the connected PCs. The
centralised system will have a control over the operations of the peripheral systems. The systems
are either the part of the local system or may be placed remotely, connected through various
connection mediums to the terminal or the main server at the workplace (van Adrichem and
Kuipers, 2015).
D. Explain
Ethernet: It is a type of internet network or connection that is being carried out in the system or
an organisation. This is usually set up in an organisation or a building but can be used on the
wider level. It consists of mainly 3 types of the system such as:
LAN: It stands for Local Area Network. This is the system, in which the network is being
set up on a local level i.e. a building, lab or an office etc. they are less complex and have
moderate computing speed.
MAN: It abbreviates to Metropolitan Area Network. This is usually established on the
city or the area level and is more complex and critical to maintain as compared to the
LAN. It is used by offices with various branches in a city or an area (Vilalta and et.al.,
2015).
WAN: This stands for Wide Area Network. It is on the national or the international level
and is mainly based on the operations of many smaller networks. This is the most
complex system and requires greater effort and computational power to maintain and
handle.
Token Ring topology: A token ring topology will help the organisation to set its network and
the system in a better and efficient manner. It is a LAN system and the systems are being
connected in a loop or a ring set up to avoid any glitches of sending one message to multiple
systems and improve the connectivity (Wang and et.al., 2015). The major drawback is that if one
system disconnects, the loop breaks and the system comes down. Here, the nodes or the PCs
connected are called as Tokens.
Physical
5

Star Topology: It is a LAN in which multiple systems are connected to each other through a
centralised connection point. In this, if one systems fails, the complete server never breaks down.
It is quite expensive to establish.
Ring: In this, the system is being connected to each other in a better way by a circular loop to get
the better connection. However, the systems are interconnected to each other without any
connection to an external system.
Bus: It is the most basic and simple topology to set up and maintain in which the systems are
connected to each other in linear manner. The major disadvantage of this system is that if one
system breaks, the whole server stops and comes down (Zhang and et.al., 2014).
Mesh: In this, the systems are interconnected in a very complex and compound manner. It is
very difficult to maintain this system and is used for the security purpose.
Tree: In this, the systems are being set in the sequence connected to the node of the previous
system in the topology.
E. Explain
Ipv4 and Ipv6: It is the part of the IP protocol and helps to manage the internet connection in an
organisation. The Ipv4 help to connect with the systems that are connected to each other
physically over a server. It helps the server to manage 2^32 number of system in one
connection. The Ipv6 provides better security over Ipv4 and can host more number of clients
(Wang and et.al., 2015).
Multi casting: In this, the data is being transmitted to each other system in order to cater
multiple systems simultaneously. It can be one to one, one to many and many to many.
Auto configuration: It is a feature of Ipv6 and helps in better management of the system. This
makes the stateless system network and configures the system without any servers.
FTP: Stands for File Transfer Protocol. It is used to send and receive various types of files on
the internet over the server.
HTTP: Abbreviates as Hyper Text Transfer Protocol. It is used to host the websites and manage
web pages (van Adrichem and Kuipers, 2015).
SMTP: Simple Mail Transfer Protocol. It is used to send and receive the files over the mail.
POP3: This is used to send and receive the e-mails over the server.
SSL: This is known as Security Socket Layer. It is a security protocol that is used to gain a better
control over the browser for communication.
6
centralised connection point. In this, if one systems fails, the complete server never breaks down.
It is quite expensive to establish.
Ring: In this, the system is being connected to each other in a better way by a circular loop to get
the better connection. However, the systems are interconnected to each other without any
connection to an external system.
Bus: It is the most basic and simple topology to set up and maintain in which the systems are
connected to each other in linear manner. The major disadvantage of this system is that if one
system breaks, the whole server stops and comes down (Zhang and et.al., 2014).
Mesh: In this, the systems are interconnected in a very complex and compound manner. It is
very difficult to maintain this system and is used for the security purpose.
Tree: In this, the systems are being set in the sequence connected to the node of the previous
system in the topology.
E. Explain
Ipv4 and Ipv6: It is the part of the IP protocol and helps to manage the internet connection in an
organisation. The Ipv4 help to connect with the systems that are connected to each other
physically over a server. It helps the server to manage 2^32 number of system in one
connection. The Ipv6 provides better security over Ipv4 and can host more number of clients
(Wang and et.al., 2015).
Multi casting: In this, the data is being transmitted to each other system in order to cater
multiple systems simultaneously. It can be one to one, one to many and many to many.
Auto configuration: It is a feature of Ipv6 and helps in better management of the system. This
makes the stateless system network and configures the system without any servers.
FTP: Stands for File Transfer Protocol. It is used to send and receive various types of files on
the internet over the server.
HTTP: Abbreviates as Hyper Text Transfer Protocol. It is used to host the websites and manage
web pages (van Adrichem and Kuipers, 2015).
SMTP: Simple Mail Transfer Protocol. It is used to send and receive the files over the mail.
POP3: This is used to send and receive the e-mails over the server.
SSL: This is known as Security Socket Layer. It is a security protocol that is used to gain a better
control over the browser for communication.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VLSM: It is a sub net masking that helps the system to get a better sharing of data of variable
size over internet.
TASK 2
A Networking devices
Server: Group of multiple systems interconnected to each other.
HUB: It is the multi port repeater that hosts the multiple system in one time.
Routers, switches and repeaters: Repeaters work on the physical level and regenerate the
signals over the system. A switch is a multi port bridge that helps the buffering and boosts
network efficiency. Router is the devices that sends the data packets over the internet based on
the IP address connected to them (Wang and et.al., 2015).
Firewall: This is a mechanism to stop the entry of malware and virus in the system. It consists of
hardware and software.
Wireless devices: They consist of the devices to connect to Wi-Fi or Bluetooth.
Load balancer: It is the device that helps the server to distribute the load on a particular system
and avoid the failing of the system.
VPN Concentrator: It helps to provide the effective creation of the Virtual connection and
delivery of message between the various VPN nodes (Zhang and et.al., 2014).
B Networking software
Client software: This will be used on the client side. It will help in transferring the details of a
hub request to the server and will get the response over the request sent. For example, CSS,
HTML and Javascript of a web service.
Server software: This is been used on server side thus will help in better management of
different operations or requests that are been sent on server by a client. For example, WAMP
server, Apache etc.
Client OS: various operating system can be used for a management of a wide range of
operations that will support a good rise in compatibility of the server and effective management
of requests and traffic on the network. Some major OS that can be used is MS Windows, Linux,
Ubuntu, Sun OS etc.
C Workstation
Hardware
7
size over internet.
TASK 2
A Networking devices
Server: Group of multiple systems interconnected to each other.
HUB: It is the multi port repeater that hosts the multiple system in one time.
Routers, switches and repeaters: Repeaters work on the physical level and regenerate the
signals over the system. A switch is a multi port bridge that helps the buffering and boosts
network efficiency. Router is the devices that sends the data packets over the internet based on
the IP address connected to them (Wang and et.al., 2015).
Firewall: This is a mechanism to stop the entry of malware and virus in the system. It consists of
hardware and software.
Wireless devices: They consist of the devices to connect to Wi-Fi or Bluetooth.
Load balancer: It is the device that helps the server to distribute the load on a particular system
and avoid the failing of the system.
VPN Concentrator: It helps to provide the effective creation of the Virtual connection and
delivery of message between the various VPN nodes (Zhang and et.al., 2014).
B Networking software
Client software: This will be used on the client side. It will help in transferring the details of a
hub request to the server and will get the response over the request sent. For example, CSS,
HTML and Javascript of a web service.
Server software: This is been used on server side thus will help in better management of
different operations or requests that are been sent on server by a client. For example, WAMP
server, Apache etc.
Client OS: various operating system can be used for a management of a wide range of
operations that will support a good rise in compatibility of the server and effective management
of requests and traffic on the network. Some major OS that can be used is MS Windows, Linux,
Ubuntu, Sun OS etc.
C Workstation
Hardware
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network card: its is a digital peripheral component that is used as the portable modem and help
in suitable management of request and responses that will help in suitable rise in operational
capacity.
Cabling: It is the connection in a network consists of utilization of different cables such as LAN
cable, optical fibre, coexcial etc. the data and information is been transmitted through the means
of cables from one system to another.
Permission manager: it is a combination of hardware and software that will help the work
station to grand the permission on a port for accessibility in a better way.
Memory: it is the storage device, volatile and non volatile in nature that stores the date and
information of a networking process in a better way.
Processor: it is the centralised chipset that manage all the operations and request that are been
met by the workstation system. The more advance the processor, higher the functional capacity
of organisation.
I/O Devices: This consists of different input output devices that will help in easy insertion and
getting of data and information respectively.
D Server type
Web: such servers are internet based and work on different website that are processed on the
server. It will include the better management of high quality internet connection to manage the
networking operations.
File: These servers contains file of specific format that will help in suitable rise in operations and
meeting of requirements of the company.
Database: this server types have a good handling of the operations and thus support a good rise
in functionality of operations helping in meeting the processing requirements of the use or the
client.
Combination: It is the complex setup of various server type that are operation in a network to
manage the critical and high amount of network traffic.
Virtualisation: it is the usage of virtual system to increase the functionality and efficiency of a
networking system. This support a better rise operational capability of the system and help in
meeting the requirements of a client in a better way.
8
in suitable management of request and responses that will help in suitable rise in operational
capacity.
Cabling: It is the connection in a network consists of utilization of different cables such as LAN
cable, optical fibre, coexcial etc. the data and information is been transmitted through the means
of cables from one system to another.
Permission manager: it is a combination of hardware and software that will help the work
station to grand the permission on a port for accessibility in a better way.
Memory: it is the storage device, volatile and non volatile in nature that stores the date and
information of a networking process in a better way.
Processor: it is the centralised chipset that manage all the operations and request that are been
met by the workstation system. The more advance the processor, higher the functional capacity
of organisation.
I/O Devices: This consists of different input output devices that will help in easy insertion and
getting of data and information respectively.
D Server type
Web: such servers are internet based and work on different website that are processed on the
server. It will include the better management of high quality internet connection to manage the
networking operations.
File: These servers contains file of specific format that will help in suitable rise in operations and
meeting of requirements of the company.
Database: this server types have a good handling of the operations and thus support a good rise
in functionality of operations helping in meeting the processing requirements of the use or the
client.
Combination: It is the complex setup of various server type that are operation in a network to
manage the critical and high amount of network traffic.
Virtualisation: it is the usage of virtual system to increase the functionality and efficiency of a
networking system. This support a better rise operational capability of the system and help in
meeting the requirements of a client in a better way.
8

E Server Selection
Cost: this factor plays a very vital role in selection of a server as the organisation will adopt the
server that will help in effective management of the operations or requirements of clients in the
minimal investment and setup.
Purpose: this is another important factor that will help in suitable handling of operations that
will help ins suitable rise in operation and thus will help in meeting the requirements of the
operations in a better way. Here it will be used for centralisation of a college system.
Operating system requirements: this will help in suitable handling of the operations that will
help in meeting the operations of the organisations in a better way. A good OS will help in
effective rise in compatibility of organisation.
F Elaboration
On the basis of above discussed system, it can be aid that the college will opt for an economic,
efficient and versatile centralised server system that will help in better management of the
operations by the organisation. A good server will help in improving the efficiency of
educational firm in a better way.
CONCLUSION
Thus, from the report, the importance of the network in an organisation can be concluded.
The report covered the purposes, benefits, implications and practices along with the commercial
practices and information sharing of the system. Besides this, various conceptual models like
OSI model, TCP/IP model are been discussed. Different types of the server system is been
considered. And topologies are been discussed. Along with this, the various types of protocols
with the networking devices are been explained in brief.
9
Cost: this factor plays a very vital role in selection of a server as the organisation will adopt the
server that will help in effective management of the operations or requirements of clients in the
minimal investment and setup.
Purpose: this is another important factor that will help in suitable handling of operations that
will help ins suitable rise in operation and thus will help in meeting the requirements of the
operations in a better way. Here it will be used for centralisation of a college system.
Operating system requirements: this will help in suitable handling of the operations that will
help in meeting the operations of the organisations in a better way. A good OS will help in
effective rise in compatibility of organisation.
F Elaboration
On the basis of above discussed system, it can be aid that the college will opt for an economic,
efficient and versatile centralised server system that will help in better management of the
operations by the organisation. A good server will help in improving the efficiency of
educational firm in a better way.
CONCLUSION
Thus, from the report, the importance of the network in an organisation can be concluded.
The report covered the purposes, benefits, implications and practices along with the commercial
practices and information sharing of the system. Besides this, various conceptual models like
OSI model, TCP/IP model are been discussed. Different types of the server system is been
considered. And topologies are been discussed. Along with this, the various types of protocols
with the networking devices are been explained in brief.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





