CSCI862 System Security Assignment 2: Analysis of Security Threats
VerifiedAdded on 2022/10/13
|6
|728
|9
Homework Assignment
AI Summary
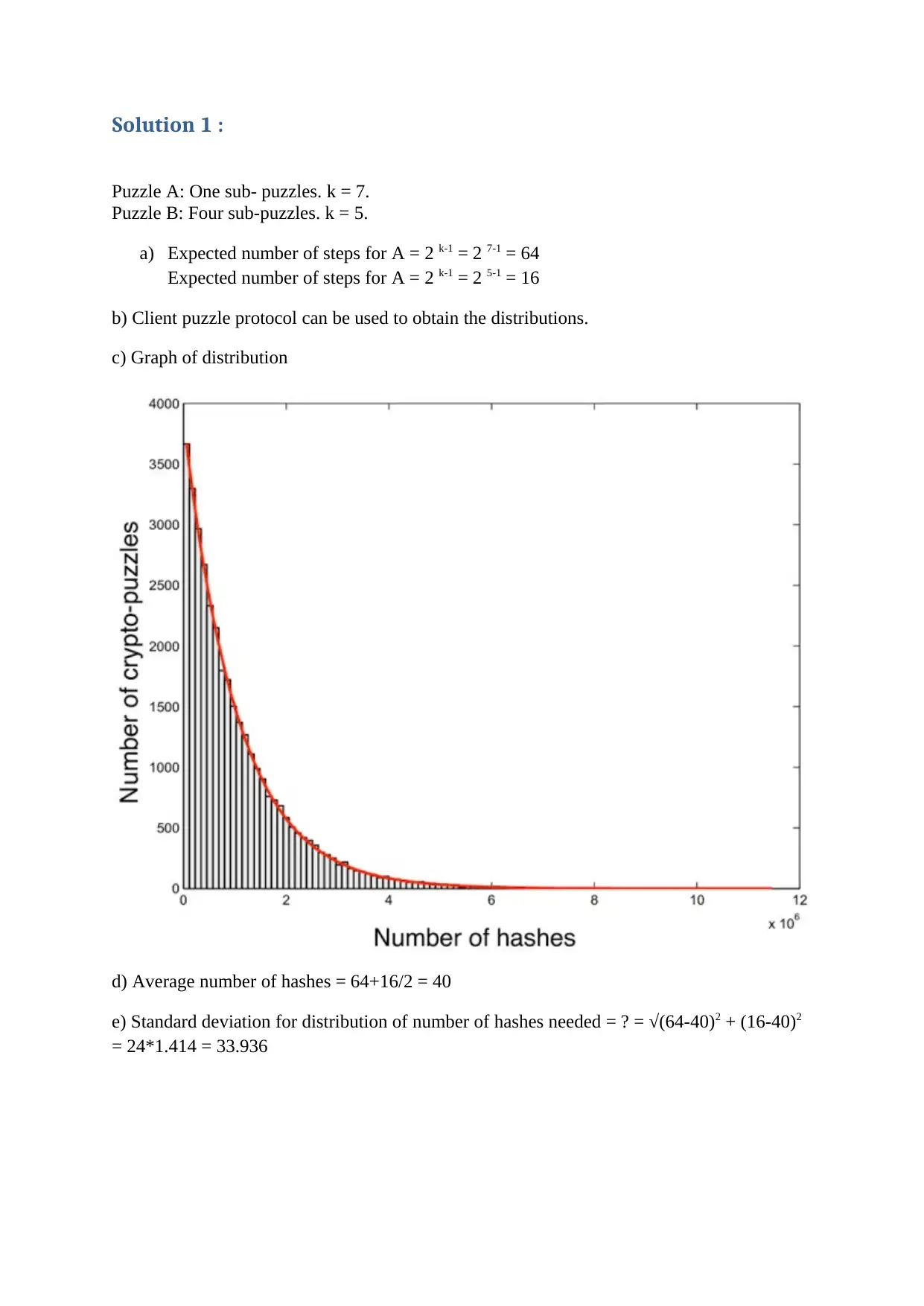
This document presents solutions to a System Security assignment (CSCI862) from Spring 2019, addressing various aspects of network and system security. The solutions encompass puzzle analysis, exploring the distribution, average, and standard deviation of hashes required for different puzzle configurations. It also analyzes a TCP SYN spoofing attack, calculating the bandwidth and rate of the attacker. Furthermore, the assignment delves into the application of Baye's Theorem for assessing malware incidence in email messages. The solutions also discuss insider threats, providing an example and recommending security measures. Additionally, the document covers topics such as the limitations of private access specifiers in C++, and the nature of various security threats including WannaCry, BlueSmack, Emotet, XML Bomb, Cinderella attack, and password manglers. The assignment concludes with SQL queries designed to extract specific information from a database, demonstrating practical application of security principles.
1 out of 6





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)