Network Technologies: System Design, Implementation, and Analysis
VerifiedAdded on 2024/05/21
|32
|4255
|498
Report
AI Summary
This report provides a detailed analysis of networking technologies, beginning with a discussion of different network types and standards, including peer-to-peer and client-server systems, and various network topologies such as star, ring, mesh, and bus. It explores the benefits and constraints of each, along with the impact of network topology, communication methods, and bandwidth requirements. The report also compares common networking principles and how protocols like HTTP, IP, SMTP, DNS, and DHCP enable effective networked systems. Further, it discusses the operating principles of networking devices and server types, focusing on file, mail, web, and database servers, and the interdependence of workstation hardware and networking software. A LAN network system is designed, implemented, tested, and evaluated based on user feedback, and a maintenance schedule is proposed for system support. Potential enhancements for security and robustness are recommended, and the report concludes with a critical reflection on the work and justifications for valid conclusions. The document includes network diagrams, configuration screenshots, and test results to support the analysis and recommendations.

NETWORKING TECHNOLOGIES
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION......................................................................................................................1
LO1............................................................................................................................................2
P1 Discuss the benefits and constraints of different network types and standards................2
P2 Explain the impact of network topology, communication and bandwidth requirements. 6
M1 Compare common networking principles and how protocols enable the effectiveness
of networked systems.............................................................................................................8
LO2..........................................................................................................................................10
P3 Discuss the operating principles of networking devices and server types......................10
P4 Discuss the interdependence of workstation hardware with relevant networking
software................................................................................................................................11
LO3..........................................................................................................................................12
P5. Design a network system to meet a given specification................................................12
P6. Test and evaluate the design to meet the requirements and analyses user feedback.....13
M3 Install and configure network services and applications...............................................15
D2 Design a maintenance schedule to support the networked system.................................16
M4 Recommend potential enhancements for the networked systems more secure, robust
applications..........................................................................................................................18
LO4..........................................................................................................................................19
P7 Implement a networked system based on a prepared design..........................................19
P8 Document and analyse test results against expected results...........................................24
D3 Use critical reflection to evaluate own work and justify valid conclusions...................25
CONCLUSION........................................................................................................................27
REFERENCES.........................................................................................................................28
INTRODUCTION......................................................................................................................1
LO1............................................................................................................................................2
P1 Discuss the benefits and constraints of different network types and standards................2
P2 Explain the impact of network topology, communication and bandwidth requirements. 6
M1 Compare common networking principles and how protocols enable the effectiveness
of networked systems.............................................................................................................8
LO2..........................................................................................................................................10
P3 Discuss the operating principles of networking devices and server types......................10
P4 Discuss the interdependence of workstation hardware with relevant networking
software................................................................................................................................11
LO3..........................................................................................................................................12
P5. Design a network system to meet a given specification................................................12
P6. Test and evaluate the design to meet the requirements and analyses user feedback.....13
M3 Install and configure network services and applications...............................................15
D2 Design a maintenance schedule to support the networked system.................................16
M4 Recommend potential enhancements for the networked systems more secure, robust
applications..........................................................................................................................18
LO4..........................................................................................................................................19
P7 Implement a networked system based on a prepared design..........................................19
P8 Document and analyse test results against expected results...........................................24
D3 Use critical reflection to evaluate own work and justify valid conclusions...................25
CONCLUSION........................................................................................................................27
REFERENCES.........................................................................................................................28

LIST OF FIGURES
Figure 1: Types of Network.......................................................................................................3
Figure 2: Protocols used in different network layer...................................................................6
Figure 3: Global Wireless Standards..........................................................................................7
Figure 4: Network design.........................................................................................................12
Figure 5: user’s opinion on network design.............................................................................13
Figure 6: Switch configuration.................................................................................................19
Figure 7: Router configuration.................................................................................................20
Figure 8: Web server configuration.........................................................................................21
Figure 9: DNS configuration....................................................................................................21
Figure 10: User and password on mail server..........................................................................22
Figure 11: FTP configuration...................................................................................................22
Figure 12: IP address on computers.........................................................................................23
Figure 13: Printer configuration...............................................................................................23
Figure 14: Screenshot for the successful ping command.........................................................25
Figure 15: Screenshot for failed ping command......................................................................25
Figure 1: Types of Network.......................................................................................................3
Figure 2: Protocols used in different network layer...................................................................6
Figure 3: Global Wireless Standards..........................................................................................7
Figure 4: Network design.........................................................................................................12
Figure 5: user’s opinion on network design.............................................................................13
Figure 6: Switch configuration.................................................................................................19
Figure 7: Router configuration.................................................................................................20
Figure 8: Web server configuration.........................................................................................21
Figure 9: DNS configuration....................................................................................................21
Figure 10: User and password on mail server..........................................................................22
Figure 11: FTP configuration...................................................................................................22
Figure 12: IP address on computers.........................................................................................23
Figure 13: Printer configuration...............................................................................................23
Figure 14: Screenshot for the successful ping command.........................................................25
Figure 15: Screenshot for failed ping command......................................................................25
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF TABLES
Table 1: Different network system.............................................................................................2
Table 2: Different types of networks.........................................................................................3
Table 3: Different types of network topologies.........................................................................4
Table 4: Various Protocols used in networking.........................................................................8
Table 5: Network Maintenance Schedule................................................................................16
Table 6: Changes for network enhancement............................................................................18
Table 7: Network Test results..................................................................................................20
Table 1: Different network system.............................................................................................2
Table 2: Different types of networks.........................................................................................3
Table 3: Different types of network topologies.........................................................................4
Table 4: Various Protocols used in networking.........................................................................8
Table 5: Network Maintenance Schedule................................................................................16
Table 6: Changes for network enhancement............................................................................18
Table 7: Network Test results..................................................................................................20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Networking is very effective for any organisation as it is effective in offering communication
in the network. In this present report, different network types, systems, topologies will be
studied along with their benefit and constraints. A LAN network is designed and
implemented for the provided organisation. Various hardware and software devices are used
in the network which will be studied. Different Servers and protocols will be studied in the
present report along with testing principles. The network is tested and the result of the test are
compared with the expected result. Proper maintenance schedule is provided in the network
for enhancing its performance for future requirement.
1
Networking is very effective for any organisation as it is effective in offering communication
in the network. In this present report, different network types, systems, topologies will be
studied along with their benefit and constraints. A LAN network is designed and
implemented for the provided organisation. Various hardware and software devices are used
in the network which will be studied. Different Servers and protocols will be studied in the
present report along with testing principles. The network is tested and the result of the test are
compared with the expected result. Proper maintenance schedule is provided in the network
for enhancing its performance for future requirement.
1

LO1
P1 Discuss the benefits and constraints of different network types and standards.
Network systems
Table 1: Different network system
Network
systems
Peer-to-peer network system Client- server network system
Description In these network, workstation is
connected with each other for
communication and flow of data
without a server for controlling the
operations in the network (O'brien
et al 2017).
Here, the computers in the network
uses a server for controlling and
allocation of resources and data.
Communication and sessions with
clients is complete through server.
Benefit High performance
Cost effective
Cost effective
Centralized network
management
Security is high
Constraints Complex network
management
Less secure
Server Dependency is high.
Performance is low
Image
2
P1 Discuss the benefits and constraints of different network types and standards.
Network systems
Table 1: Different network system
Network
systems
Peer-to-peer network system Client- server network system
Description In these network, workstation is
connected with each other for
communication and flow of data
without a server for controlling the
operations in the network (O'brien
et al 2017).
Here, the computers in the network
uses a server for controlling and
allocation of resources and data.
Communication and sessions with
clients is complete through server.
Benefit High performance
Cost effective
Cost effective
Centralized network
management
Security is high
Constraints Complex network
management
Less secure
Server Dependency is high.
Performance is low
Image
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network types
Figure 1: Types of Network
(Source: https://www.lifewire.com/lans-wans-and-other-area-networks-817376, 2018 )
Table 2: Different types of networks
Network
type
Personal area
network (PAN)
Local Area
Network (LAN)
Wide Area
Network
(WAN)
Metropolitan
Area
Network(MAN)
Descriptio
n
personal devices
of a user are
interconnected
with each other it
forms PAN (Faith
et al 2017).
These network
plan is generally
used for
connecting
computers and
devices over a
small
organization
which is limited
to a group of
buildings,
building or even a
Networking is
done over of
two or more
LANs network
linked together.
Data are
transfer in high
speed using
satellite links or
phone lines.
MAN is larger
in size then
LAN and ranges
over a large
campus, city. It
can be operated
and maintained
by a single
owner.
3
Figure 1: Types of Network
(Source: https://www.lifewire.com/lans-wans-and-other-area-networks-817376, 2018 )
Table 2: Different types of networks
Network
type
Personal area
network (PAN)
Local Area
Network (LAN)
Wide Area
Network
(WAN)
Metropolitan
Area
Network(MAN)
Descriptio
n
personal devices
of a user are
interconnected
with each other it
forms PAN (Faith
et al 2017).
These network
plan is generally
used for
connecting
computers and
devices over a
small
organization
which is limited
to a group of
buildings,
building or even a
Networking is
done over of
two or more
LANs network
linked together.
Data are
transfer in high
speed using
satellite links or
phone lines.
MAN is larger
in size then
LAN and ranges
over a large
campus, city. It
can be operated
and maintained
by a single
owner.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

room.
Benefits Simple
structuring
cost effective
network
Instant data
sharing
High speed
data transfer
Easy to
establish
Easy network
management.
High
scalability
high
performance
high speed
networking
security is
high
Constraint
s
Security
control
Bandwidth
limitations
Network
administrator
is required
Size is limited
Hard to
establish
Costly
Structural
complexity
arises
Security is
low
Hard to
establish
More
security
feature is
required.
Image
Network topologies
Table 3: Different types of network topologies
Types of
topology
Image Description Benefit Constraints
4
Benefits Simple
structuring
cost effective
network
Instant data
sharing
High speed
data transfer
Easy to
establish
Easy network
management.
High
scalability
high
performance
high speed
networking
security is
high
Constraint
s
Security
control
Bandwidth
limitations
Network
administrator
is required
Size is limited
Hard to
establish
Costly
Structural
complexity
arises
Security is
low
Hard to
establish
More
security
feature is
required.
Image
Network topologies
Table 3: Different types of network topologies
Types of
topology
Image Description Benefit Constraints
4

Star
topology
Workstation are
connected in this
type of network
using a centralized
device(Switch/hub)
Maintenance is
easy
Performance is
high
Dependency
is high in
the
centralized
device
Costly due
to high
cable
requirement
Ring
topology
Computer and
devices are
connected with one
another using the
ring format (Bisht,
and Singh, 2015).
easy
implementation
cost effective
single node
failure leads
to network
failure.
Low
scalability
Mesh
topology
All the computing
devices are capable
of linking with all
or many of the
computer present
in the network.
Many devices
can be
connected
Cost effective
High
maintenance
cost
complex
structure
Bus
topology
The workstations
in these types of
network
communicate with
server by means of
single cable or
node.
Less cable
therefore low
cost
Simple
structuring
High load in
cable
Breakdown if
cable fails
5
topology
Workstation are
connected in this
type of network
using a centralized
device(Switch/hub)
Maintenance is
easy
Performance is
high
Dependency
is high in
the
centralized
device
Costly due
to high
cable
requirement
Ring
topology
Computer and
devices are
connected with one
another using the
ring format (Bisht,
and Singh, 2015).
easy
implementation
cost effective
single node
failure leads
to network
failure.
Low
scalability
Mesh
topology
All the computing
devices are capable
of linking with all
or many of the
computer present
in the network.
Many devices
can be
connected
Cost effective
High
maintenance
cost
complex
structure
Bus
topology
The workstations
in these types of
network
communicate with
server by means of
single cable or
node.
Less cable
therefore low
cost
Simple
structuring
High load in
cable
Breakdown if
cable fails
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P2 Explain the impact of network topology, communication and bandwidth requirements.
Network technology
Token Ring: In LAN network, if the computing devices are linked with one another though
ring topology, then it uses a data frame of three byte for transmission of the data and for
utilisation of resources. In these structure, server is not required for managing the network
therefore it is cost efficient (Comer, 2015). However, the network is in capable of
performing simultaneous operation like data transmission.
Ethernet: It is the network form when the devices in the network are connected with the help
of various different types of cables. Network Interface Card or NIC is effectively used in
ethernet. Transmission of data is done using various technologies. The Ethernet is simple
structuring hence it is easy to understand and implement.
Communication
TCP/IP and OSI Model: OSI or the Open System Interconnection is a seven layered a
theoretical model, which helps in implementation of a network using various protocols. On
other hand, TCP/IP stands for Transmission protocol and internet protocols, it is four layer
telecommunication structure and is communication oriented model (Alani, 2014)
Figure 2: Protocols used in different network layer
(Source: http://www.ids-sax2.com, 2018 )
Standards
6
Network technology
Token Ring: In LAN network, if the computing devices are linked with one another though
ring topology, then it uses a data frame of three byte for transmission of the data and for
utilisation of resources. In these structure, server is not required for managing the network
therefore it is cost efficient (Comer, 2015). However, the network is in capable of
performing simultaneous operation like data transmission.
Ethernet: It is the network form when the devices in the network are connected with the help
of various different types of cables. Network Interface Card or NIC is effectively used in
ethernet. Transmission of data is done using various technologies. The Ethernet is simple
structuring hence it is easy to understand and implement.
Communication
TCP/IP and OSI Model: OSI or the Open System Interconnection is a seven layered a
theoretical model, which helps in implementation of a network using various protocols. On
other hand, TCP/IP stands for Transmission protocol and internet protocols, it is four layer
telecommunication structure and is communication oriented model (Alani, 2014)
Figure 2: Protocols used in different network layer
(Source: http://www.ids-sax2.com, 2018 )
Standards
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
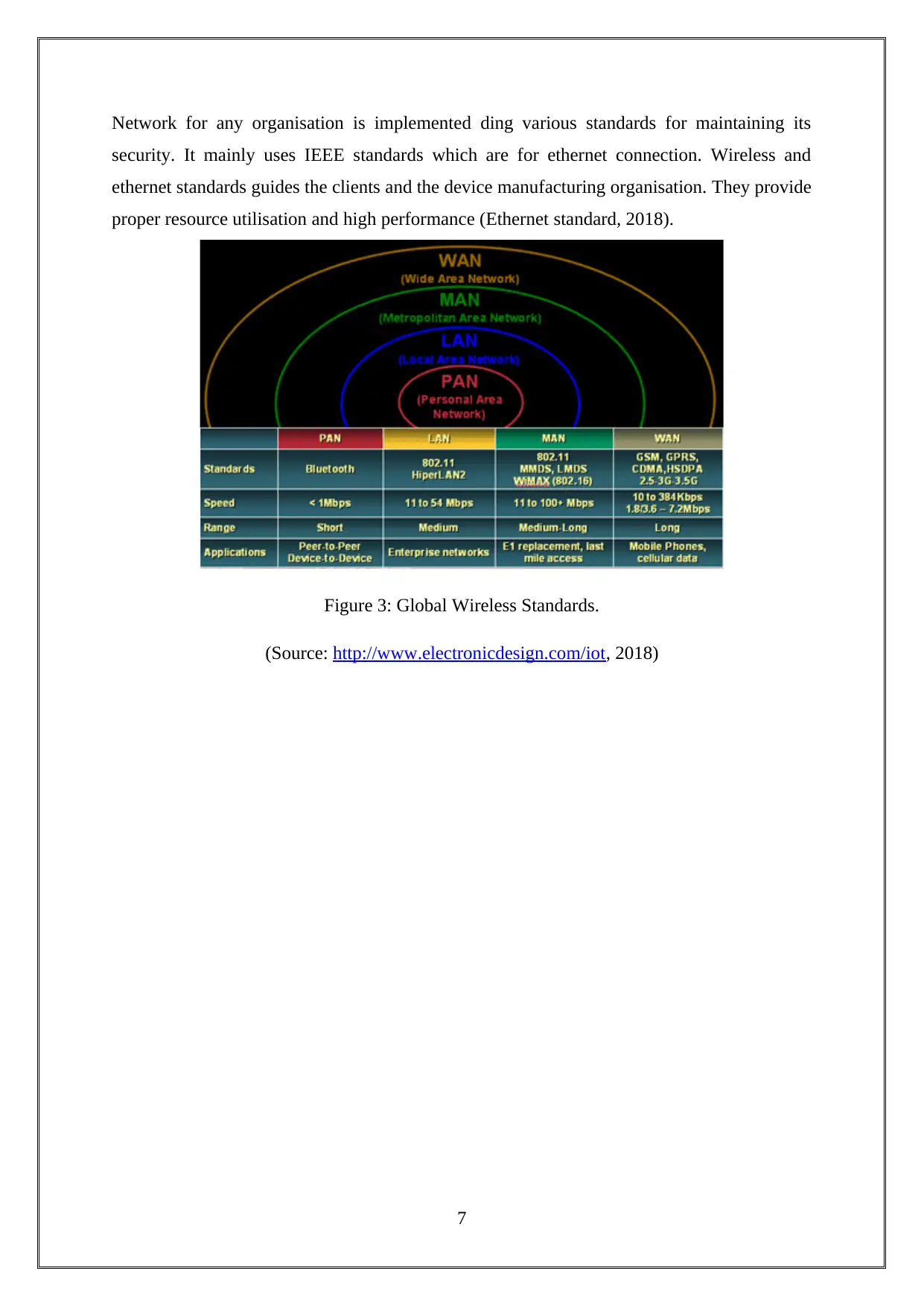
Network for any organisation is implemented ding various standards for maintaining its
security. It mainly uses IEEE standards which are for ethernet connection. Wireless and
ethernet standards guides the clients and the device manufacturing organisation. They provide
proper resource utilisation and high performance (Ethernet standard, 2018).
Figure 3: Global Wireless Standards.
(Source: http://www.electronicdesign.com/iot, 2018)
7
security. It mainly uses IEEE standards which are for ethernet connection. Wireless and
ethernet standards guides the clients and the device manufacturing organisation. They provide
proper resource utilisation and high performance (Ethernet standard, 2018).
Figure 3: Global Wireless Standards.
(Source: http://www.electronicdesign.com/iot, 2018)
7

M1 Compare common networking principles and how protocols enable the effectiveness of
networked systems.
Protocols
Table 4: Various Protocols used in networking
Protocol Description
HTTP Information from client to server and server to client is sent and receive
via web page using this HTTP protocol. The user generates a Request over
server, and as a response the server forwards information in the form of
web page.
IP In a network, data packet travels from the source to destination device
through IP address. It provides fast and secure data delivery.
SMTP Simple Mail Transfer Protocol is commonly used for client-server
network model. Communication of mail can be managed using a Local
server.
DNS This protocol is implemented for isolating an existing request that is being
processed in the domain. Web address can be interpreted to form the
corresponding IP address
DHCP For network administration, allocation of address space for the computing
devices can be reduced providing quicker connectivity with the server.
Networking principles:
In computer network, all the function and operation are held by following four networking
principles:
Switching
technique
Massage passing
concept
Addressing issue Data representation
Data are transmitting
in a network from
Its main concern is
to establish
Different methods
can be used for
Transmitted data in a
network is checked
8
networked systems.
Protocols
Table 4: Various Protocols used in networking
Protocol Description
HTTP Information from client to server and server to client is sent and receive
via web page using this HTTP protocol. The user generates a Request over
server, and as a response the server forwards information in the form of
web page.
IP In a network, data packet travels from the source to destination device
through IP address. It provides fast and secure data delivery.
SMTP Simple Mail Transfer Protocol is commonly used for client-server
network model. Communication of mail can be managed using a Local
server.
DNS This protocol is implemented for isolating an existing request that is being
processed in the domain. Web address can be interpreted to form the
corresponding IP address
DHCP For network administration, allocation of address space for the computing
devices can be reduced providing quicker connectivity with the server.
Networking principles:
In computer network, all the function and operation are held by following four networking
principles:
Switching
technique
Massage passing
concept
Addressing issue Data representation
Data are transmitting
in a network from
Its main concern is
to establish
Different methods
can be used for
Transmitted data in a
network is checked
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



