CSI6201 Networking Technologies: Subnetting, APIPA and VLANs
VerifiedAdded on 2023/04/11
|8
|1047
|132
Homework Assignment
AI Summary
This assignment solution delves into various networking technologies, starting with an explanation of Automatic Private IP Addressing (APIPA) and its role in LAN configurations. It addresses subnetting for a given network (172.16.100.0 /22) to create specified subnets, including those with 32, 64, 128, and 256 IP addresses. The solution further elucidates the differences between switches and routers, highlighting how they build and use their respective tables (MAC address tables for switches and routing tables for routers). Finally, it discusses the necessity of routers for communication between different VLANs, explaining how routers facilitate inter-VLAN routing due to VLANs having separate broadcast domains and MAC address tables. The reflection exercise summarizes key learnings about MAC addresses, routers, switches, and VLANs, while also acknowledging the challenges in understanding switch configurations and VLAN complexities. Desklib offers this and many other solved assignments to aid students in their studies.

Running head: NETWORKING TECHNOLOGIES
NETWORKING TECHNOLOGIES
Name of the Student:
Name of the University:
Author Note:
NETWORKING TECHNOLOGIES
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKING TECHNOLOGIES
Table of Contents
Question 1........................................................................................................................................2
Question 2........................................................................................................................................2
Question 3........................................................................................................................................4
Question 4........................................................................................................................................5
Reflection Exercise..........................................................................................................................5
References........................................................................................................................................7
Table of Contents
Question 1........................................................................................................................................2
Question 2........................................................................................................................................2
Question 3........................................................................................................................................4
Question 4........................................................................................................................................5
Reflection Exercise..........................................................................................................................5
References........................................................................................................................................7

2NETWORKING TECHNOLOGIES
Question 1
Automatic Private IP Addressing also known as APIPA is a feature of old windows operating
systems (Windows 98, ME, 2000 and XP) which automatically enables a computer to allocate
itself an IP address when the Dynamic Host Configuration Protocol or DHCP is absent or
missing from the device. APIPA acts as the backup in case of missing DHCP function and helps
in configuring and supporting Local Area Networks or LANS.
LAN networks require a specific local IP addresses to work properly. The APIPA by
default can allocate IP addresses between 169.254.0.0 and 169.254.255.255 (Comer, 2018). Each
of these addresses are guaranteed to not conflict with other routable addresses. This enables
APIPA to allot IP addresses to multiple computers connected locally to the same LAN network.
This makes APIPA capable of handling a broadcast of a LAN domain without any help in the
absence of a manual configuration or DHCP.
Question 2
Given IP address: 172.16.100.0/22 Division: Class B CIDR = 22
22 Network bits
10 Host bits.
Maximum number of assignable IP addresses: 2^10= 1024
Total number of networks possible: 2^6= 64
The IP address sub netting is given below:
1. Two networks each having 32 IP addresses
Question 1
Automatic Private IP Addressing also known as APIPA is a feature of old windows operating
systems (Windows 98, ME, 2000 and XP) which automatically enables a computer to allocate
itself an IP address when the Dynamic Host Configuration Protocol or DHCP is absent or
missing from the device. APIPA acts as the backup in case of missing DHCP function and helps
in configuring and supporting Local Area Networks or LANS.
LAN networks require a specific local IP addresses to work properly. The APIPA by
default can allocate IP addresses between 169.254.0.0 and 169.254.255.255 (Comer, 2018). Each
of these addresses are guaranteed to not conflict with other routable addresses. This enables
APIPA to allot IP addresses to multiple computers connected locally to the same LAN network.
This makes APIPA capable of handling a broadcast of a LAN domain without any help in the
absence of a manual configuration or DHCP.
Question 2
Given IP address: 172.16.100.0/22 Division: Class B CIDR = 22
22 Network bits
10 Host bits.
Maximum number of assignable IP addresses: 2^10= 1024
Total number of networks possible: 2^6= 64
The IP address sub netting is given below:
1. Two networks each having 32 IP addresses
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
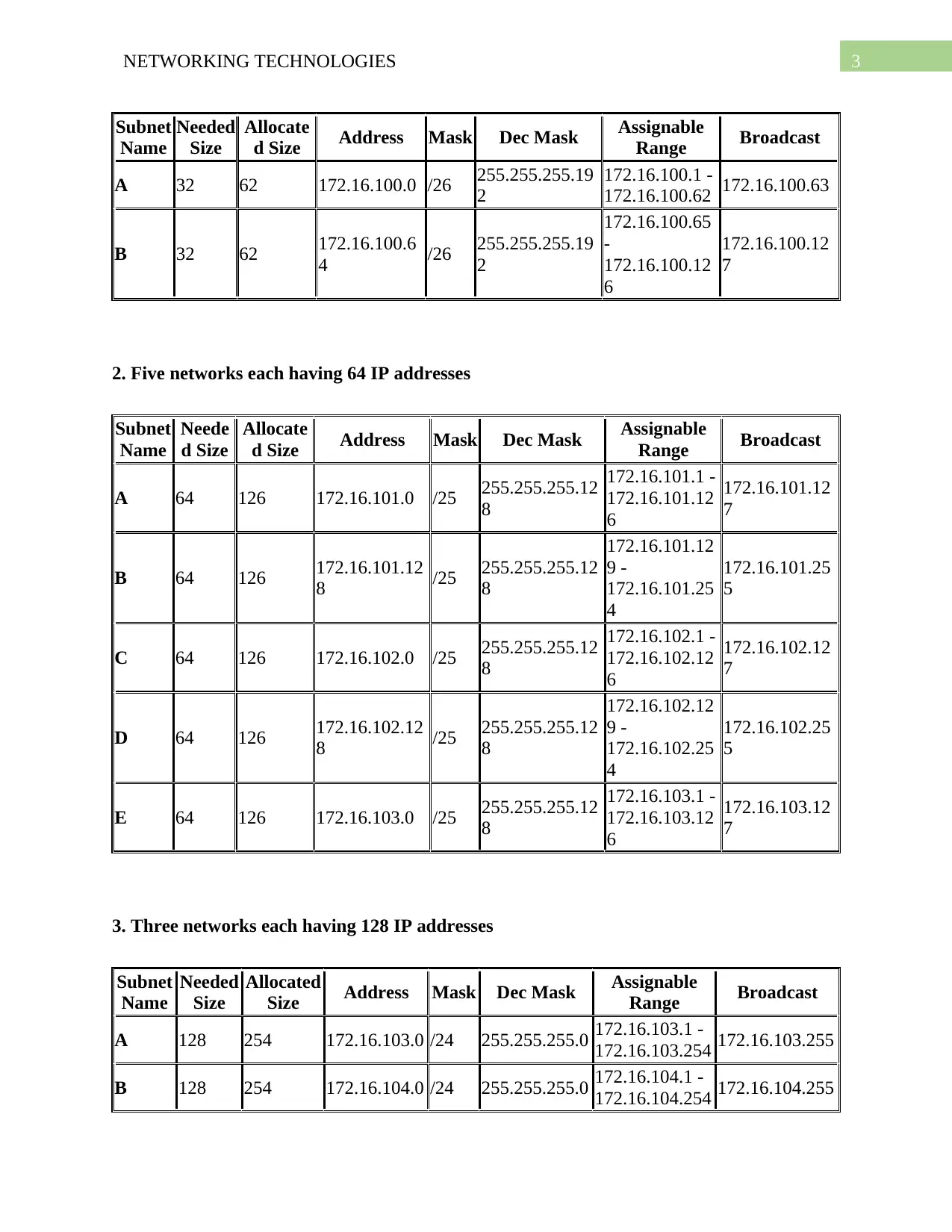
3NETWORKING TECHNOLOGIES
Subnet
Name
Needed
Size
Allocate
d Size Address Mask Dec Mask Assignable
Range Broadcast
A 32 62 172.16.100.0 /26 255.255.255.19
2
172.16.100.1 -
172.16.100.62 172.16.100.63
B 32 62 172.16.100.6
4 /26 255.255.255.19
2
172.16.100.65
-
172.16.100.12
6
172.16.100.12
7
2. Five networks each having 64 IP addresses
Subnet
Name
Neede
d Size
Allocate
d Size Address Mask Dec Mask Assignable
Range Broadcast
A 64 126 172.16.101.0 /25 255.255.255.12
8
172.16.101.1 -
172.16.101.12
6
172.16.101.12
7
B 64 126 172.16.101.12
8 /25 255.255.255.12
8
172.16.101.12
9 -
172.16.101.25
4
172.16.101.25
5
C 64 126 172.16.102.0 /25 255.255.255.12
8
172.16.102.1 -
172.16.102.12
6
172.16.102.12
7
D 64 126 172.16.102.12
8 /25 255.255.255.12
8
172.16.102.12
9 -
172.16.102.25
4
172.16.102.25
5
E 64 126 172.16.103.0 /25 255.255.255.12
8
172.16.103.1 -
172.16.103.12
6
172.16.103.12
7
3. Three networks each having 128 IP addresses
Subnet
Name
Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
A 128 254 172.16.103.0 /24 255.255.255.0 172.16.103.1 -
172.16.103.254 172.16.103.255
B 128 254 172.16.104.0 /24 255.255.255.0 172.16.104.1 -
172.16.104.254 172.16.104.255
Subnet
Name
Needed
Size
Allocate
d Size Address Mask Dec Mask Assignable
Range Broadcast
A 32 62 172.16.100.0 /26 255.255.255.19
2
172.16.100.1 -
172.16.100.62 172.16.100.63
B 32 62 172.16.100.6
4 /26 255.255.255.19
2
172.16.100.65
-
172.16.100.12
6
172.16.100.12
7
2. Five networks each having 64 IP addresses
Subnet
Name
Neede
d Size
Allocate
d Size Address Mask Dec Mask Assignable
Range Broadcast
A 64 126 172.16.101.0 /25 255.255.255.12
8
172.16.101.1 -
172.16.101.12
6
172.16.101.12
7
B 64 126 172.16.101.12
8 /25 255.255.255.12
8
172.16.101.12
9 -
172.16.101.25
4
172.16.101.25
5
C 64 126 172.16.102.0 /25 255.255.255.12
8
172.16.102.1 -
172.16.102.12
6
172.16.102.12
7
D 64 126 172.16.102.12
8 /25 255.255.255.12
8
172.16.102.12
9 -
172.16.102.25
4
172.16.102.25
5
E 64 126 172.16.103.0 /25 255.255.255.12
8
172.16.103.1 -
172.16.103.12
6
172.16.103.12
7
3. Three networks each having 128 IP addresses
Subnet
Name
Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
A 128 254 172.16.103.0 /24 255.255.255.0 172.16.103.1 -
172.16.103.254 172.16.103.255
B 128 254 172.16.104.0 /24 255.255.255.0 172.16.104.1 -
172.16.104.254 172.16.104.255
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
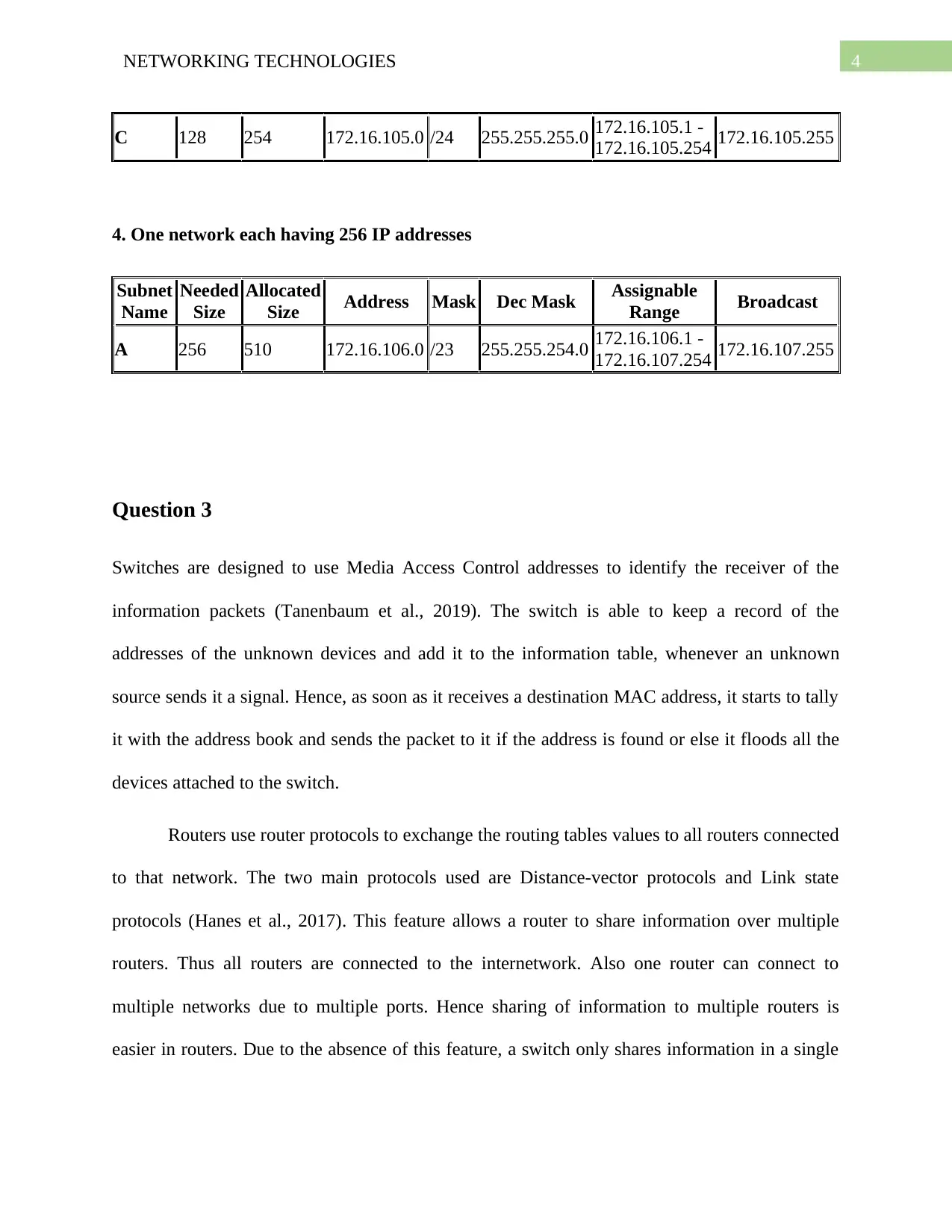
4NETWORKING TECHNOLOGIES
C 128 254 172.16.105.0 /24 255.255.255.0 172.16.105.1 -
172.16.105.254 172.16.105.255
4. One network each having 256 IP addresses
Subnet
Name
Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
A 256 510 172.16.106.0 /23 255.255.254.0 172.16.106.1 -
172.16.107.254 172.16.107.255
Question 3
Switches are designed to use Media Access Control addresses to identify the receiver of the
information packets (Tanenbaum et al., 2019). The switch is able to keep a record of the
addresses of the unknown devices and add it to the information table, whenever an unknown
source sends it a signal. Hence, as soon as it receives a destination MAC address, it starts to tally
it with the address book and sends the packet to it if the address is found or else it floods all the
devices attached to the switch.
Routers use router protocols to exchange the routing tables values to all routers connected
to that network. The two main protocols used are Distance-vector protocols and Link state
protocols (Hanes et al., 2017). This feature allows a router to share information over multiple
routers. Thus all routers are connected to the internetwork. Also one router can connect to
multiple networks due to multiple ports. Hence sharing of information to multiple routers is
easier in routers. Due to the absence of this feature, a switch only shares information in a single
C 128 254 172.16.105.0 /24 255.255.255.0 172.16.105.1 -
172.16.105.254 172.16.105.255
4. One network each having 256 IP addresses
Subnet
Name
Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
A 256 510 172.16.106.0 /23 255.255.254.0 172.16.106.1 -
172.16.107.254 172.16.107.255
Question 3
Switches are designed to use Media Access Control addresses to identify the receiver of the
information packets (Tanenbaum et al., 2019). The switch is able to keep a record of the
addresses of the unknown devices and add it to the information table, whenever an unknown
source sends it a signal. Hence, as soon as it receives a destination MAC address, it starts to tally
it with the address book and sends the packet to it if the address is found or else it floods all the
devices attached to the switch.
Routers use router protocols to exchange the routing tables values to all routers connected
to that network. The two main protocols used are Distance-vector protocols and Link state
protocols (Hanes et al., 2017). This feature allows a router to share information over multiple
routers. Thus all routers are connected to the internetwork. Also one router can connect to
multiple networks due to multiple ports. Hence sharing of information to multiple routers is
easier in routers. Due to the absence of this feature, a switch only shares information in a single

5NETWORKING TECHNOLOGIES
network and has only one switching table and cannot share information like routers to populate
switching tables in other switches.
Question 4
Every Virtual LAN or VLAN have their own broadcast domain. They also use their own MAC
address table to refer to when sending information packets. The VLANS also have their
individual ports that only they have access to. Due to this a problem arises for the switch during
sending a information packet from one device to another. This problem happens because the
VLAN of both the different devices have different MAC addresses. This problem can be solved
by configuring the route of the VLANs by routing them to the concerned devices using a router
(Vidal et al., 2019). A router can connect to multiple VLANs and act as a medium of
communication between them which is not possible over a single network. Therefore, it becomes
essential to use a router for communicating between two VLANS of two different devices.
Reflection Exercise
a) The last two modules have taught me about the concept of MAC address, Routers, Switches
and VLANS. Switches are mainly used to transfer information to separate devices whose MAC
addresses are kept recorded in the switch’s data storage table. MAC address is the physical
address of a device which is separate for each and every device. These networking technologies
are very useful as they form the core of this subject.
b) The switches and its different configuration is also very hard for me to understand. The setup
formation of switch along with the details of the switching tables and information exchanges is
quite a complex mechanism. The function of switches in VLAN is also quite complex for me to
comprehend. In VLANs, each individual VLAN has its own set of addresses and rules to
network and has only one switching table and cannot share information like routers to populate
switching tables in other switches.
Question 4
Every Virtual LAN or VLAN have their own broadcast domain. They also use their own MAC
address table to refer to when sending information packets. The VLANS also have their
individual ports that only they have access to. Due to this a problem arises for the switch during
sending a information packet from one device to another. This problem happens because the
VLAN of both the different devices have different MAC addresses. This problem can be solved
by configuring the route of the VLANs by routing them to the concerned devices using a router
(Vidal et al., 2019). A router can connect to multiple VLANs and act as a medium of
communication between them which is not possible over a single network. Therefore, it becomes
essential to use a router for communicating between two VLANS of two different devices.
Reflection Exercise
a) The last two modules have taught me about the concept of MAC address, Routers, Switches
and VLANS. Switches are mainly used to transfer information to separate devices whose MAC
addresses are kept recorded in the switch’s data storage table. MAC address is the physical
address of a device which is separate for each and every device. These networking technologies
are very useful as they form the core of this subject.
b) The switches and its different configuration is also very hard for me to understand. The setup
formation of switch along with the details of the switching tables and information exchanges is
quite a complex mechanism. The function of switches in VLAN is also quite complex for me to
comprehend. In VLANs, each individual VLAN has its own set of addresses and rules to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORKING TECHNOLOGIES
communicate. This results in the more complex situations when connecting multiple VLANs
together. This makes the matter more confusing.
communicate. This results in the more complex situations when connecting multiple VLANs
together. This makes the matter more confusing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKING TECHNOLOGIES
References
Comer, D. E. (2018). The Internet book: everything you need to know about computer
networking and how the Internet works. Chapman and Hall/CRC.
Hanes, D., Salgueiro, G., Grossetete, P., Barton, R., & Henry, J. (2017). IoT fundamentals:
Networking technologies, protocols, and use cases for the internet of things. Cisco Press.
Tanenbaum, A., Wetherall, D., Kurose, J., & Ross, K. (2019). Computer Networks Title:
Computer Networking: A Top-Down Approach. Instructor, 201901.
Vidal, I., Soto, I., Banchs, A., Garcia-Reinoso, J., Lozano, I., & Camarillo, G. (2019).
Multimedia Networking Technologies, Protocols, and Architectures. Artech House.
References
Comer, D. E. (2018). The Internet book: everything you need to know about computer
networking and how the Internet works. Chapman and Hall/CRC.
Hanes, D., Salgueiro, G., Grossetete, P., Barton, R., & Henry, J. (2017). IoT fundamentals:
Networking technologies, protocols, and use cases for the internet of things. Cisco Press.
Tanenbaum, A., Wetherall, D., Kurose, J., & Ross, K. (2019). Computer Networks Title:
Computer Networking: A Top-Down Approach. Instructor, 201901.
Vidal, I., Soto, I., Banchs, A., Garcia-Reinoso, J., Lozano, I., & Camarillo, G. (2019).
Multimedia Networking Technologies, Protocols, and Architectures. Artech House.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




