Olive-Oyl Retail: Analyzing Network Security & Breach Prevention
VerifiedAdded on 2023/06/18
|10
|2714
|469
Report
AI Summary
This report investigates the network security of 'Olive-Oyl' retail store, focusing on potential security breaches that led to a ransomware attack encrypting files with the ".meds" extension. It identifies possible breaches such as internal actors with excessive access, disgruntled employees, phishing attacks via the customer Wi-Fi network, and malicious insiders. The report details various cybersecurity threats like denial of service, SQL injection, and ransomware, alongside vulnerabilities including a shared network for employees and customers, and unrestricted access to business applications. It also discusses attacks like malware and man-in-the-middle attacks. The document proposes security implementations, such as firewalls, and provides guidelines for staff and customers to ensure responsible digital space usage. The goal is to enhance the overall network security and protect business applications and sensitive data within the Olive-Oyl retail environment. Desklib provides access to past papers and solved assignments for students.

NETWORKS AND CYBER
SECURITY ESSENTIALS
SECURITY ESSENTIALS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
TASK 1- Possible security breaches that clod have led to network................................................1
TASK 2- different types of threats, vulnerabilities and attacks to understand importance
of Cybersecurity 2
TASK 3- Ways in which security could be implemented in given case study network
infrastructure....................................................................................................................................5
TASK 4- Guideline for Olive-Oyl staff members, and customers to responsibly use their digital
space................................................................................................................................................6
Conclusion.......................................................................................................................................7
REFERENCES................................................................................................................................8
Introduction......................................................................................................................................1
TASK 1- Possible security breaches that clod have led to network................................................1
TASK 2- different types of threats, vulnerabilities and attacks to understand importance
of Cybersecurity 2
TASK 3- Ways in which security could be implemented in given case study network
infrastructure....................................................................................................................................5
TASK 4- Guideline for Olive-Oyl staff members, and customers to responsibly use their digital
space................................................................................................................................................6
Conclusion.......................................................................................................................................7
REFERENCES................................................................................................................................8

Introduction
Network security is one of the most important part of an organization that can result in success or
failure of business. Comptonization with network security can result in increasing threat for
busiess. This report will lay emphasis upon case study of ‘Olive-Oyl’ retail store whose
documents/ services encrypted with “.meds” file format due to lack of network security.
TASK 1- Possible security breaches that clod have led to network
Possible Security Breach 1: Due to internal actors
Reason: In the given scenario it was stated that when Wimpy diversified his job responsibilities
to sales Executives and gave complete access of business application to all Sales Executives till a
point that all the users of business had complete access to business application. This increased
possibility of security breach due to internal actors. In fact, internal actors are one of the main
threats and increases possibility of security breach as they have complete access to the
organizational system. This can result in privilege abuse because it can result in granting
unauthorized access to network and database. Such type of breach is a bit difficult to be detected
(Plachkinova and Maurer, 2018). It is one of the main possible security breaches that could have
led to this situation because as per the scenario all Sales Executive, and marketing head, had
access to the application.
Possible Security Breach 2: Due to Disgruntled Employees
Reason: In the given scenario it was stated that Popeye owner of ‘Olive-Oyl’ withdrawn Sales
Head positions within organization because of which they were either demoted or were force to
leave the organization. This could have directly resulted in increasing dissatisfaction of
employees whether they were junior positioned employees (Sales Executives) or demoted
employees. In the case study it was also explained that one of the competitor ‘Bluto’ hired an Ex-
Sales Head of retail showroom of “Olive-Oyl” and a hacker. It is possible that, that hired Ex-
Sales Head could have contacted an existing dissatisfied employee of “Olive-Oyl” who had
complete access of business application of “Olive-Oyl” retail showroom so that important
required information to the hacker hired by Brutus could have been one of the main possible
security breaches. Disgruntled Employees are one of the main threats in terms of security breach
because they have lower satisfaction level and purposefully harm the company in any way they
can (Goode and et. al., 2017).
1
Network security is one of the most important part of an organization that can result in success or
failure of business. Comptonization with network security can result in increasing threat for
busiess. This report will lay emphasis upon case study of ‘Olive-Oyl’ retail store whose
documents/ services encrypted with “.meds” file format due to lack of network security.
TASK 1- Possible security breaches that clod have led to network
Possible Security Breach 1: Due to internal actors
Reason: In the given scenario it was stated that when Wimpy diversified his job responsibilities
to sales Executives and gave complete access of business application to all Sales Executives till a
point that all the users of business had complete access to business application. This increased
possibility of security breach due to internal actors. In fact, internal actors are one of the main
threats and increases possibility of security breach as they have complete access to the
organizational system. This can result in privilege abuse because it can result in granting
unauthorized access to network and database. Such type of breach is a bit difficult to be detected
(Plachkinova and Maurer, 2018). It is one of the main possible security breaches that could have
led to this situation because as per the scenario all Sales Executive, and marketing head, had
access to the application.
Possible Security Breach 2: Due to Disgruntled Employees
Reason: In the given scenario it was stated that Popeye owner of ‘Olive-Oyl’ withdrawn Sales
Head positions within organization because of which they were either demoted or were force to
leave the organization. This could have directly resulted in increasing dissatisfaction of
employees whether they were junior positioned employees (Sales Executives) or demoted
employees. In the case study it was also explained that one of the competitor ‘Bluto’ hired an Ex-
Sales Head of retail showroom of “Olive-Oyl” and a hacker. It is possible that, that hired Ex-
Sales Head could have contacted an existing dissatisfied employee of “Olive-Oyl” who had
complete access of business application of “Olive-Oyl” retail showroom so that important
required information to the hacker hired by Brutus could have been one of the main possible
security breaches. Disgruntled Employees are one of the main threats in terms of security breach
because they have lower satisfaction level and purposefully harm the company in any way they
can (Goode and et. al., 2017).
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Possible Security Breach 3: Due to Phishing attack
Reason: In the above scenario, it was stated that same network which is used to urn business was
used to offer “Complimentary” Wi-Fi with high- speed internet to all the customers. This means
that same network was being used by employees for business and same network was used by
customers for personal work. It is one of the main type of possible security breach that could
have led to this situation because there was a possibility hacker hired by Brutus could have used
network of “Olive-Oyl” retail showroom only as a customers as it would have made hacking
much easier and access to the network was easily granted to customers. Using the network of
business hacker could have sent a phishing email to employees for logging to a fake website
through email (Bhushan and Sahoo, 2018). This could have led to comptonization of username
and password of business application.
Possible Security Breach 4: Due to malicious insiders that could have led to ransomware attack
Reason: In the above scenario, it was stated that competitor of “Olive-Oyl” retail showroom was
not happy with its success and as a result they hired an Ex- employee and a hacker. Hacker could
have used all the information provided by Ex- sales Head and hacked business application and
converted all the fines into .meds file format and only on demand ransomware only those files
could have been encrypted. It is possible because of open Wi-Fi facility for all employees and
customers as hacker could have used their own network and could have encrypted all of their
main data using ransomware virus (Balakrishnan and et. al., 2019).
TASK 2- different types of threats, vulnerabilities and attacks to understand
importance of Cybersecurity
Threats
Threat can be defined as a kind of malicious act that can damage, steal, disrupt data.
Many times, threats in network can increase if unauthorised person is given access to the
network. These threats can include viruses, data breeches, denial od service, hacking network
etc.
There are various type of threats in cyber security of network, some of them have been
explained below:
2
Reason: In the above scenario, it was stated that same network which is used to urn business was
used to offer “Complimentary” Wi-Fi with high- speed internet to all the customers. This means
that same network was being used by employees for business and same network was used by
customers for personal work. It is one of the main type of possible security breach that could
have led to this situation because there was a possibility hacker hired by Brutus could have used
network of “Olive-Oyl” retail showroom only as a customers as it would have made hacking
much easier and access to the network was easily granted to customers. Using the network of
business hacker could have sent a phishing email to employees for logging to a fake website
through email (Bhushan and Sahoo, 2018). This could have led to comptonization of username
and password of business application.
Possible Security Breach 4: Due to malicious insiders that could have led to ransomware attack
Reason: In the above scenario, it was stated that competitor of “Olive-Oyl” retail showroom was
not happy with its success and as a result they hired an Ex- employee and a hacker. Hacker could
have used all the information provided by Ex- sales Head and hacked business application and
converted all the fines into .meds file format and only on demand ransomware only those files
could have been encrypted. It is possible because of open Wi-Fi facility for all employees and
customers as hacker could have used their own network and could have encrypted all of their
main data using ransomware virus (Balakrishnan and et. al., 2019).
TASK 2- different types of threats, vulnerabilities and attacks to understand
importance of Cybersecurity
Threats
Threat can be defined as a kind of malicious act that can damage, steal, disrupt data.
Many times, threats in network can increase if unauthorised person is given access to the
network. These threats can include viruses, data breeches, denial od service, hacking network
etc.
There are various type of threats in cyber security of network, some of them have been
explained below:
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Denial of service threat: using DOS attack an application can be flooded with packets that
can further make it impossible for users to access the application (Bhushan and Sahoo, 2018).
Whereas distributed denial of service is even more of a threat as it is done from several
computers and entire network of owner is compromised.
SQL injection attack threat is not only a threat for business application and network but it is a
threat for all the data or information which is stored within network (Thing, 2017). This
attack focuses upon identifying security vulnerabilities within a network, application of
website.
Ransomware is another threat that can publish or block data to a computer system by
encrypting data or files stores within it until and unless victim pays demanded ransom (Sinha
and et. al., 2017).
It is important for organizations to focus upon identifying different types of threats
associated with network because these threats can directly impact business organizations in many
different ways. For example, denial of service can make it impossible for employees to access
the system. Ransomware attack can encrypt whole system and every file or data stored within it.
Due to this not only business can suffer loss but threat to loss or theft of confidential data can
increase.
Vulnerabilities
There are various kinds of vulnerabilities identified within case study, some of them are:
Common network for employees and customers it one of the main vulnerabilities because
same network upon which main business application runs and sensitive and confidential data
of organization is stored is used by customers as well (Sinha and et. al., 2017). This makes
network and business application vulnerable because outsiders have easy access to
organizational network which increased risk of accessing confidential information more.
Complete access to business application to all the employees which full permission and no
limitation is another vulnerability. This is because all the employees whether they are at
lower level or at higher level will be able to access all kinds of sensitive data or files stored
within application (Sinha and et. al., 2017). It is a vulnerability because if any dissatisfied
employees leaves the organization then complete access to business application can make it
possible for them to delete, modify, theft, encrypt data or even copy some important
3
can further make it impossible for users to access the application (Bhushan and Sahoo, 2018).
Whereas distributed denial of service is even more of a threat as it is done from several
computers and entire network of owner is compromised.
SQL injection attack threat is not only a threat for business application and network but it is a
threat for all the data or information which is stored within network (Thing, 2017). This
attack focuses upon identifying security vulnerabilities within a network, application of
website.
Ransomware is another threat that can publish or block data to a computer system by
encrypting data or files stores within it until and unless victim pays demanded ransom (Sinha
and et. al., 2017).
It is important for organizations to focus upon identifying different types of threats
associated with network because these threats can directly impact business organizations in many
different ways. For example, denial of service can make it impossible for employees to access
the system. Ransomware attack can encrypt whole system and every file or data stored within it.
Due to this not only business can suffer loss but threat to loss or theft of confidential data can
increase.
Vulnerabilities
There are various kinds of vulnerabilities identified within case study, some of them are:
Common network for employees and customers it one of the main vulnerabilities because
same network upon which main business application runs and sensitive and confidential data
of organization is stored is used by customers as well (Sinha and et. al., 2017). This makes
network and business application vulnerable because outsiders have easy access to
organizational network which increased risk of accessing confidential information more.
Complete access to business application to all the employees which full permission and no
limitation is another vulnerability. This is because all the employees whether they are at
lower level or at higher level will be able to access all kinds of sensitive data or files stored
within application (Sinha and et. al., 2017). It is a vulnerability because if any dissatisfied
employees leaves the organization then complete access to business application can make it
possible for them to delete, modify, theft, encrypt data or even copy some important
3

confidential or sensitive data or file with them that can result that can be used by their
competitors and this vulnerability can convert into threat.
Attacks
There are various kinds of attacks that can result in threat to business application and can
impact business and profitability in many ways, some f them are:
Malwares such as ransomware can result in network breach and encryption of files or other
sensitive data. It is an attack that can affect busies because if victim does not pay ransom
demanded by attacker then it can result in loss or theft of data or damage to other fines stored
within network.
Man in the middle attack is another type of attack that can affect business of “Olive-Oyl”
retail showroom as they have same network which is used for business and by customers and
due to this it becomes easy for attacker to interrupt a traffic, filter or steal any kind of data.
“.meds” file format attack
.Meds file format attack is based on the virus which is directly affecting the sensitive or
confidential information. Usually, it get rid of malicious files so that it is important to secure PC
and potentially restore .meds files and alternative option to data discovery approaches.
.Meds attacks are directly associated with ransomware infection which is known as
STOP. This type of meds virus is helping to lock data and directly affecting the computer
operational tasks. Once, med virus establishes the files, afterwards it starts executing a task and
also pre-defined certain order (Ma and Wei, 2021). As a result, it will be affecting some kind of
system setting. On the other hand, it could be attached with registry key stored by editor,
legitimate processes. All files are renamed with proper extension and also encrypted by
ransomware. Unfortunately, it could be stored valuable data or information in proper format.
The operational aspect of attack is to encrypt personal files and focused on the demand a
ransom fee for their file recovery. Since, it uses as strong cipher based algorithm to directly
corrupt target files. .Meds files are consider as an inaccessible (Ma and Wei, 2021).when it is
completely end the attack. Any kind of file recovery cannot possible with infected system but it
can be identified the restored files and encrypt themselves. For proper ransomware elimination, it
would be selected the anti-malware tool as recovery option to identify any defects, threat or risk
in file systems.
4
competitors and this vulnerability can convert into threat.
Attacks
There are various kinds of attacks that can result in threat to business application and can
impact business and profitability in many ways, some f them are:
Malwares such as ransomware can result in network breach and encryption of files or other
sensitive data. It is an attack that can affect busies because if victim does not pay ransom
demanded by attacker then it can result in loss or theft of data or damage to other fines stored
within network.
Man in the middle attack is another type of attack that can affect business of “Olive-Oyl”
retail showroom as they have same network which is used for business and by customers and
due to this it becomes easy for attacker to interrupt a traffic, filter or steal any kind of data.
“.meds” file format attack
.Meds file format attack is based on the virus which is directly affecting the sensitive or
confidential information. Usually, it get rid of malicious files so that it is important to secure PC
and potentially restore .meds files and alternative option to data discovery approaches.
.Meds attacks are directly associated with ransomware infection which is known as
STOP. This type of meds virus is helping to lock data and directly affecting the computer
operational tasks. Once, med virus establishes the files, afterwards it starts executing a task and
also pre-defined certain order (Ma and Wei, 2021). As a result, it will be affecting some kind of
system setting. On the other hand, it could be attached with registry key stored by editor,
legitimate processes. All files are renamed with proper extension and also encrypted by
ransomware. Unfortunately, it could be stored valuable data or information in proper format.
The operational aspect of attack is to encrypt personal files and focused on the demand a
ransom fee for their file recovery. Since, it uses as strong cipher based algorithm to directly
corrupt target files. .Meds files are consider as an inaccessible (Ma and Wei, 2021).when it is
completely end the attack. Any kind of file recovery cannot possible with infected system but it
can be identified the restored files and encrypt themselves. For proper ransomware elimination, it
would be selected the anti-malware tool as recovery option to identify any defects, threat or risk
in file systems.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Sometimes, Meds ransomware virus will be dropped a ransom message which is known as
ReadMe. Text. This kind of file will be loading in the system which means that directly attached
the folder but it is consists in the encoded format. For sake of security or privacy, many
authorities are recommended that avoid any kind of negotiations with cyber-criminals.
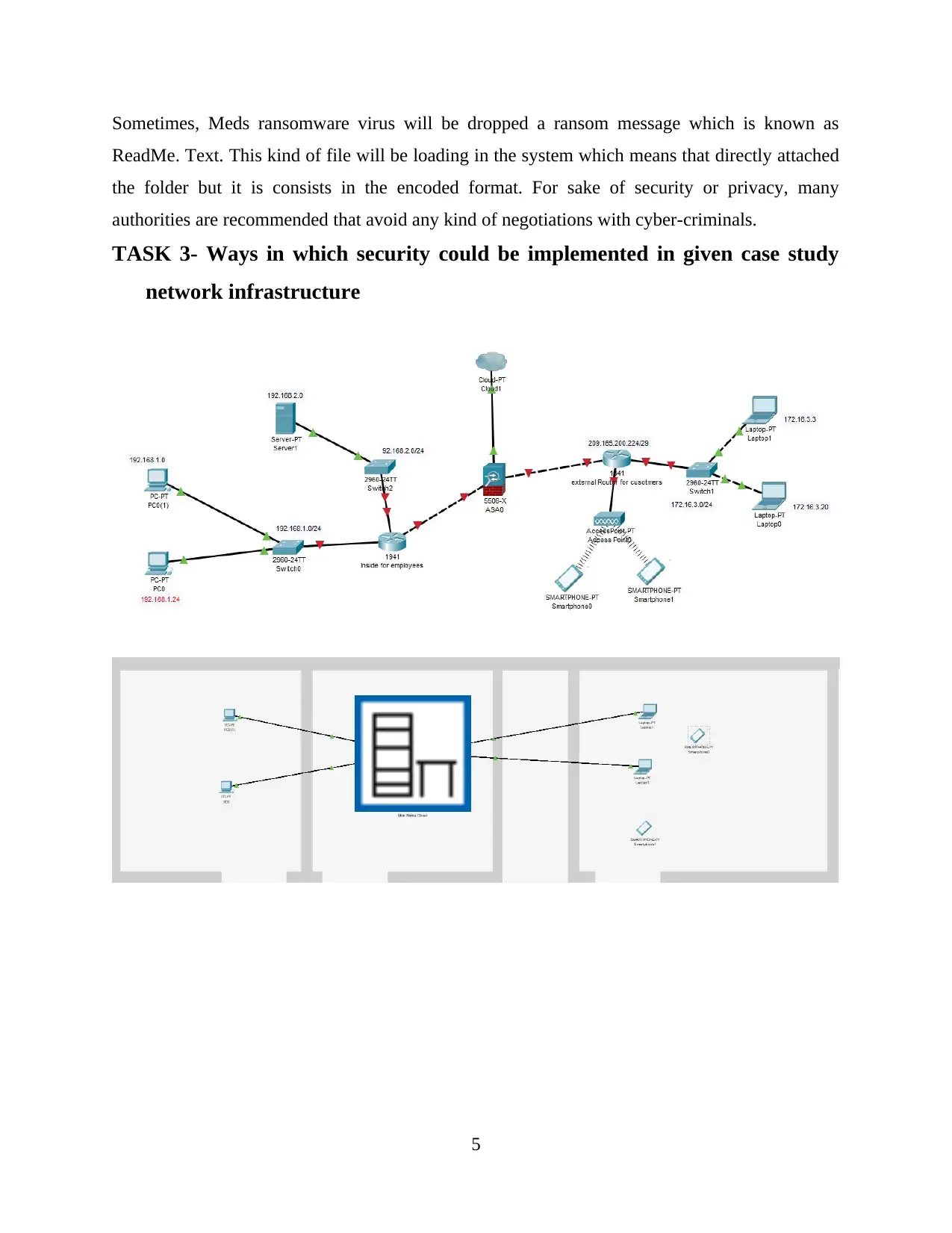
TASK 3- Ways in which security could be implemented in given case study
network infrastructure
5
ReadMe. Text. This kind of file will be loading in the system which means that directly attached
the folder but it is consists in the encoded format. For sake of security or privacy, many
authorities are recommended that avoid any kind of negotiations with cyber-criminals.
TASK 3- Ways in which security could be implemented in given case study
network infrastructure
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As per the aove proposed netowkr main securty devices that are required to be installed
within netowok for enhacing overall security of netowkr and busiess application of “Olive-Oyl”
retail showroom firewall. Firewall is one of the most important security devices which is
required to be installed within a network as it directly helps in filtering out traffic within network
(Bhushan and Sahoo, 2018). Not only this it further helps in blocking any unauthorised user or
outsider to gain unauthorised access to business application. It will help in blocking cusotmers of
“Olive-Oyl” retail showroom to access business application of store even if they are logged in to
same network it will filter customers and employees and will enhance overall security of
application and data stored within it.
TASK 4- Guideline for Olive-Oyl staff members, and customers to responsibly
use their digital space
Guideline for Olive-Oyl staff members
All the staff members are expected to use network of organization responsibly. Access to
internet will be limited to job related activities only. It is important for all the employees to first
of all log in themselves on network be specifying their user type only then they will be allowed
to access the internet. All the data is stored within business application of Olive-Oyl So therefore
none of the employees will be allowed to copy, sent or receive data using online connection. If
6
within netowok for enhacing overall security of netowkr and busiess application of “Olive-Oyl”
retail showroom firewall. Firewall is one of the most important security devices which is
required to be installed within a network as it directly helps in filtering out traffic within network
(Bhushan and Sahoo, 2018). Not only this it further helps in blocking any unauthorised user or
outsider to gain unauthorised access to business application. It will help in blocking cusotmers of
“Olive-Oyl” retail showroom to access business application of store even if they are logged in to
same network it will filter customers and employees and will enhance overall security of
application and data stored within it.
TASK 4- Guideline for Olive-Oyl staff members, and customers to responsibly
use their digital space
Guideline for Olive-Oyl staff members
All the staff members are expected to use network of organization responsibly. Access to
internet will be limited to job related activities only. It is important for all the employees to first
of all log in themselves on network be specifying their user type only then they will be allowed
to access the internet. All the data is stored within business application of Olive-Oyl So therefore
none of the employees will be allowed to copy, sent or receive data using online connection. If
6

found copying, receiving or transmitting any data including confidential and sensitive data then
strict actions will be taken against those staff members. Sharing any kind of confidential or
sensitive data or information outside organization is strictly prohibited. If a staff member is
required to access any kind of information which is outside their job related activity then for this
permission from head or marketing head is required to be taken only after that they will be
allowed to access data or information required by them. Usage of unauthorised or malicious
devices or software into organizational network or business application will not be tolerated and
strict actions will be taken for the same.
Guideline for Olive-Oyl customers
All the customers of Olive-Oyl will be allowed to access internet and public website that
are certified and secure will be allowed to be accessed by cusotmers. None of the customers will
be allowed to access internal network of organization or try to gain access of staff members of
Olive-Oyl for logging in to network. None of the customers will try to access unauthorised
applications or websites. Not only this, customers will not be allowed to upload or download to
network without permission if found, that IP address of customers will be blocked and they will
not be able to access internet.
Conclusion
Form the above report it has been summarized that it is important for organizations to focus upon
their network security and limit access to network and business application as per user type
because complete access to business application to all the employees which full permission and
no limitation is another vulnerability. This is because all the employees whether they are at lower
level or at higher level will be able to access all kinds of sensitive data or files stored within
application.
7
strict actions will be taken against those staff members. Sharing any kind of confidential or
sensitive data or information outside organization is strictly prohibited. If a staff member is
required to access any kind of information which is outside their job related activity then for this
permission from head or marketing head is required to be taken only after that they will be
allowed to access data or information required by them. Usage of unauthorised or malicious
devices or software into organizational network or business application will not be tolerated and
strict actions will be taken for the same.
Guideline for Olive-Oyl customers
All the customers of Olive-Oyl will be allowed to access internet and public website that
are certified and secure will be allowed to be accessed by cusotmers. None of the customers will
be allowed to access internal network of organization or try to gain access of staff members of
Olive-Oyl for logging in to network. None of the customers will try to access unauthorised
applications or websites. Not only this, customers will not be allowed to upload or download to
network without permission if found, that IP address of customers will be blocked and they will
not be able to access internet.
Conclusion
Form the above report it has been summarized that it is important for organizations to focus upon
their network security and limit access to network and business application as per user type
because complete access to business application to all the employees which full permission and
no limitation is another vulnerability. This is because all the employees whether they are at lower
level or at higher level will be able to access all kinds of sensitive data or files stored within
application.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books and Journals
Balakrishnan, N., and et. al., 2019. Deep Belief Network enhanced intrusion detection system to
prevent security breach in the Internet of Things. Internet of things, p.100112.
Bhushan, B. and Sahoo, G., 2018. Recent advances in attacks, technical challenges,
vulnerabilities and their countermeasures in wireless sensor networks. Wireless
Personal Communications, 98(2), pp.2037-2077.
Goode, S., and et. al., 2017. User compensation as a data breach recovery action: An
investigation of the Sony PlayStation network breach. MIS Quarterly, 41(3), pp.703-
727.
Ma, T.T. and Wei, L., 2021. Impact of multiple cardiovascular medications on mortality after an
incidence of ischemic stroke or transient ischemic attack. BMC medicine, 19(1), pp.1-
11.
Plachkinova, M. and Maurer, C., 2018. Security breach at target. Journal of Information Systems
Education, 29(1), pp.11-20.
Sinha, P., and et. al., 2017, July. Security vulnerabilities, attacks and countermeasures in wireless
sensor networks at various layers of OSI reference model: A survey. In 2017
International Conference on Signal Processing and Communication (ICSPC) (pp. 288-
293). IEEE.
Thing, V.L., 2017, March. IEEE 802.11 network anomaly detection and attack classification: A
deep learning approach. In 2017 IEEE Wireless Communications and Networking
Conference (WCNC) (pp. 1-6). IEEE.
8
Books and Journals
Balakrishnan, N., and et. al., 2019. Deep Belief Network enhanced intrusion detection system to
prevent security breach in the Internet of Things. Internet of things, p.100112.
Bhushan, B. and Sahoo, G., 2018. Recent advances in attacks, technical challenges,
vulnerabilities and their countermeasures in wireless sensor networks. Wireless
Personal Communications, 98(2), pp.2037-2077.
Goode, S., and et. al., 2017. User compensation as a data breach recovery action: An
investigation of the Sony PlayStation network breach. MIS Quarterly, 41(3), pp.703-
727.
Ma, T.T. and Wei, L., 2021. Impact of multiple cardiovascular medications on mortality after an
incidence of ischemic stroke or transient ischemic attack. BMC medicine, 19(1), pp.1-
11.
Plachkinova, M. and Maurer, C., 2018. Security breach at target. Journal of Information Systems
Education, 29(1), pp.11-20.
Sinha, P., and et. al., 2017, July. Security vulnerabilities, attacks and countermeasures in wireless
sensor networks at various layers of OSI reference model: A survey. In 2017
International Conference on Signal Processing and Communication (ICSPC) (pp. 288-
293). IEEE.
Thing, V.L., 2017, March. IEEE 802.11 network anomaly detection and attack classification: A
deep learning approach. In 2017 IEEE Wireless Communications and Networking
Conference (WCNC) (pp. 1-6). IEEE.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





