Network Addressing: Implementation, Testing, and IPv6 Configuration
VerifiedAdded on 2023/01/09
|9
|2594
|97
Report
AI Summary
This report provides a comprehensive overview of computer network addressing, focusing on the application of layered reference models and IPv6 configuration. The introduction establishes the fundamental concepts of computer networks and the importance of communication protocols. Part 1 delves into a literature review concerning the role of layered network models, specifically the OSI and TCP/IP models, in the implementation of switches, routers, and end devices. The report explores the benefits of these models for network engineers. It presents an approach for documenting, implementing, and testing network addressing, including the justification for the chosen methods, such as the utilization of NAT (Network Address Translation). Part 2 focuses on IPv6 addressing, including the computation and assignment of IPv6 subnets, and the documentation of global unicast and link-local IPv6 addresses for router and end devices. The report concludes by summarizing the key findings and emphasizing the significance of reference models and IPv6 in ensuring efficient and secure network operations. References to relevant literature are included to support the analysis and findings.

Networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................1
Part 1................................................................................................................................................1
1.1 Conduct literature search associated with research question (RQ1: In case layered network
reference models are used for implementation of switches, routers and end devices will this
aid the network engineer) and document the outcome...........................................................1
1.2 Review on essential literature identified within literature search....................................1
1.3 Develop approach for documentation, implementation and testing of network addressing
of computer network within figure and illustrate it appropriately.........................................3
1.4 Justify the usage of approach for implementation as well as testing network addressing of
computer network...................................................................................................................4
Part 2................................................................................................................................................4
Compute and assign 4 IPv6 subnets via appending subnet ID to global routing prefix given
and document IPv6 subnets within the table..........................................................................4
Document global unicast IPv6 addresses to network interface of router devices within
Interface Address table by making use of MAC address. Along with this, document IPv6Link
Local addresses of LAN network of router devices...............................................................5
Complete device address table with device IPv6 address & prefix length along with Link
Local address of end devices by utilisation of MAC addresses.............................................5
Conclusion.......................................................................................................................................5
References........................................................................................................................................7
Introduction......................................................................................................................................1
Part 1................................................................................................................................................1
1.1 Conduct literature search associated with research question (RQ1: In case layered network
reference models are used for implementation of switches, routers and end devices will this
aid the network engineer) and document the outcome...........................................................1
1.2 Review on essential literature identified within literature search....................................1
1.3 Develop approach for documentation, implementation and testing of network addressing
of computer network within figure and illustrate it appropriately.........................................3
1.4 Justify the usage of approach for implementation as well as testing network addressing of
computer network...................................................................................................................4
Part 2................................................................................................................................................4
Compute and assign 4 IPv6 subnets via appending subnet ID to global routing prefix given
and document IPv6 subnets within the table..........................................................................4
Document global unicast IPv6 addresses to network interface of router devices within
Interface Address table by making use of MAC address. Along with this, document IPv6Link
Local addresses of LAN network of router devices...............................................................5
Complete device address table with device IPv6 address & prefix length along with Link
Local address of end devices by utilisation of MAC addresses.............................................5
Conclusion.......................................................................................................................................5
References........................................................................................................................................7

Introduction
Computer network refers to set of interconnected computers where information can be
shared among them. The connection among two systems can be done through cabling mostly
fibre optical cable or Ethernet cable. It is liable for connecting parts of distributed architecture.
While transmission of data different protocols, frameworks and methods are used (Kuznetsov
and et. al, 2019). Computer network implies group of computers which utilise set of common
communication protocols on digital interconnections for the rationale of sharing resources
provided or located by network nodes. This report will furnish literature review related with
layered reference model and approach for network addressing. Furthermore, it will also provide
IPv6 addressing for computer networks.
Part 1
1.1 Conduct literature search associated with research question (RQ1: In case layered network
reference models are used for implementation of switches, routers and end devices will
this aid the network engineer) and document the outcome.
Reference models renders conceptual framework that is liable for standardisation of
communication heterogeneous networks. It has been identified by carrying out literature search
that OSI and TCP/IP protocol are layered network models which are utilised to ensure that
network works as per desired standards. The literature review has been conducted and it has
been found that reference models are utilised within execution of networking devices to ensure
that effectual communication can be carried out (Khattak and et. al, 2019). The next section
illustrates literature review in terms of work carried out by researchers with reference to the
topic.
1.2 Review on essential literature identified within literature search
As per Jean-Yuves Colin (2016), the research illustrates NOLI (New open logistics
interconnection) reference model is used for physical internet that is inspired by OSI (Open
systems interconnections) reference model to deal with data networks. In this paper comparison
of NOLI with OSI model and TCP/IP (Transmission Control Protocol/Internet Protocol) model
of internet (Colin, Mathieu and Nakechbandi, 2016). It illustrates that the major difference is that
the other models are in appearance of definitions related with physical objects in distinct layers
and not only lowest one. NOLI locates containerization as well as de-containerization operations
1
Computer network refers to set of interconnected computers where information can be
shared among them. The connection among two systems can be done through cabling mostly
fibre optical cable or Ethernet cable. It is liable for connecting parts of distributed architecture.
While transmission of data different protocols, frameworks and methods are used (Kuznetsov
and et. al, 2019). Computer network implies group of computers which utilise set of common
communication protocols on digital interconnections for the rationale of sharing resources
provided or located by network nodes. This report will furnish literature review related with
layered reference model and approach for network addressing. Furthermore, it will also provide
IPv6 addressing for computer networks.
Part 1
1.1 Conduct literature search associated with research question (RQ1: In case layered network
reference models are used for implementation of switches, routers and end devices will
this aid the network engineer) and document the outcome.
Reference models renders conceptual framework that is liable for standardisation of
communication heterogeneous networks. It has been identified by carrying out literature search
that OSI and TCP/IP protocol are layered network models which are utilised to ensure that
network works as per desired standards. The literature review has been conducted and it has
been found that reference models are utilised within execution of networking devices to ensure
that effectual communication can be carried out (Khattak and et. al, 2019). The next section
illustrates literature review in terms of work carried out by researchers with reference to the
topic.
1.2 Review on essential literature identified within literature search
As per Jean-Yuves Colin (2016), the research illustrates NOLI (New open logistics
interconnection) reference model is used for physical internet that is inspired by OSI (Open
systems interconnections) reference model to deal with data networks. In this paper comparison
of NOLI with OSI model and TCP/IP (Transmission Control Protocol/Internet Protocol) model
of internet (Colin, Mathieu and Nakechbandi, 2016). It illustrates that the major difference is that
the other models are in appearance of definitions related with physical objects in distinct layers
and not only lowest one. NOLI locates containerization as well as de-containerization operations
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

within topmost layer and in lower below. It unites two layers i.e. transport and session layers in
one.
As per Pranaab Bandhu Nath (2015), here functionality is organised within four
abstraction layers that are utilised for sorting related protocols as per scope of network that is
involved. Operations of TCP/IP suite within data communication networking have been
illustrated (Nath and Uddin, 2015).
P.suresh (2016), emphasis is laid on OSI reference model that involves seven different
layers and each comprises of their responsibilities (Suresh, 2016). Networking has evolved from
basic principle that comprises of moving data from one system to other.
Nitish Aggarwal (2014), provides a comparative analysis of OSI and TCP/IP Reference
Model (Aggarwal, Gupta and Saxena, 2019). The reference model is defined like a virtual model
that defines way in which communication must occur.
Preeti Sinha (2017), the focus is laid on security vulnerabilities within wireless networks
as well as classification of different within WSNs as per distinct OSI protocol layers (Sinha and
et. al,, 2017). There are some technical challenges that need to be solved.
Hamound M. Aldosari (2017), depending on IoT communication reference model, the
substantial amendment to layers will be made by adding up extra layer named security layer
(Aldosari, 2015). It will aim at confirming identity of receiver or sender and will aid within
blocking connections to vulnerable services.
Sergio Duque Castilho (2017), this paper surveys IoT based security in which
technologies are used in devices. The risks associated with these devices are exposed for staying
connected with global network, the TCP/IP model is utilised within this connection (Castilho and
et. al, 2017). The rationale behind this is execution of models of security depending on ISO
7498-2.
Pakawat Pupawibul (2015), OpenFlow is key enabler within SDN which enables direct
manipulation on forwarding plane related with network devices. These methods are dependent
on flows, via protocol such as OpenFlow, that operates within contrast for networking device
methods like TCP/IP routing and MAC table (Banjar, Pupatwibul and Braun, 2015). This paper
emphasise on relationship among processes related with forwarding packets within IP routing
table in comparison to OpenFlow-table.
2
one.
As per Pranaab Bandhu Nath (2015), here functionality is organised within four
abstraction layers that are utilised for sorting related protocols as per scope of network that is
involved. Operations of TCP/IP suite within data communication networking have been
illustrated (Nath and Uddin, 2015).
P.suresh (2016), emphasis is laid on OSI reference model that involves seven different
layers and each comprises of their responsibilities (Suresh, 2016). Networking has evolved from
basic principle that comprises of moving data from one system to other.
Nitish Aggarwal (2014), provides a comparative analysis of OSI and TCP/IP Reference
Model (Aggarwal, Gupta and Saxena, 2019). The reference model is defined like a virtual model
that defines way in which communication must occur.
Preeti Sinha (2017), the focus is laid on security vulnerabilities within wireless networks
as well as classification of different within WSNs as per distinct OSI protocol layers (Sinha and
et. al,, 2017). There are some technical challenges that need to be solved.
Hamound M. Aldosari (2017), depending on IoT communication reference model, the
substantial amendment to layers will be made by adding up extra layer named security layer
(Aldosari, 2015). It will aim at confirming identity of receiver or sender and will aid within
blocking connections to vulnerable services.
Sergio Duque Castilho (2017), this paper surveys IoT based security in which
technologies are used in devices. The risks associated with these devices are exposed for staying
connected with global network, the TCP/IP model is utilised within this connection (Castilho and
et. al, 2017). The rationale behind this is execution of models of security depending on ISO
7498-2.
Pakawat Pupawibul (2015), OpenFlow is key enabler within SDN which enables direct
manipulation on forwarding plane related with network devices. These methods are dependent
on flows, via protocol such as OpenFlow, that operates within contrast for networking device
methods like TCP/IP routing and MAC table (Banjar, Pupatwibul and Braun, 2015). This paper
emphasise on relationship among processes related with forwarding packets within IP routing
table in comparison to OpenFlow-table.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ammar Rayes (2016), the paper states that it is difficult for having large scale networks.
The OSI standard is used mostly for carrying networking there tasks like addressing composite
problem (Rayes, and Salam, 2017).
Md M. Alani (2014), this provides adequate introduction for reference layer model i.e.
TTCP/IP along with protocols that are used within the layer. The internetwork is also illustrated
within the operating networking layers like RARP, ARP, IP, ICMP and InARP (Alani, 2014). In
addition to this the protocols which are used for transmission of message are also illustrated.
Various papers have been reviewed but these are main paper as each have provided an
insight into reference models. They will aid within carrying out successful communication with
one other through networking devices like switch, hub, router and many others (Zhang, Bengio
and Singer, 2019). For ensuring that adequate messages are received the extra security protocols
can be implemented like in IoT reference model a security layer is added for identification of
vulnerabilities.
1.3 Develop approach for documentation, implementation and testing of network addressing of
computer network within figure and illustrate it appropriately
While opting for any networking project, it is important to carry out documentation so that
each aspect can be covered while implementing this. With respect to this, certain aspects are
stated beneath:
Identification of assets
Analysis of security risks
Assess security requirements along with tradeoff
Formulation of security plan
Defining security policies
Development of procedures to apply security policies
Formulating technical implementation strategy
Attain buy-in from managers, users and technical employees
Train employees and users
Implementation of technical strategy along with security procedures
Test security as well as update in case any problem is there
Maintain security
3
The OSI standard is used mostly for carrying networking there tasks like addressing composite
problem (Rayes, and Salam, 2017).
Md M. Alani (2014), this provides adequate introduction for reference layer model i.e.
TTCP/IP along with protocols that are used within the layer. The internetwork is also illustrated
within the operating networking layers like RARP, ARP, IP, ICMP and InARP (Alani, 2014). In
addition to this the protocols which are used for transmission of message are also illustrated.
Various papers have been reviewed but these are main paper as each have provided an
insight into reference models. They will aid within carrying out successful communication with
one other through networking devices like switch, hub, router and many others (Zhang, Bengio
and Singer, 2019). For ensuring that adequate messages are received the extra security protocols
can be implemented like in IoT reference model a security layer is added for identification of
vulnerabilities.
1.3 Develop approach for documentation, implementation and testing of network addressing of
computer network within figure and illustrate it appropriately
While opting for any networking project, it is important to carry out documentation so that
each aspect can be covered while implementing this. With respect to this, certain aspects are
stated beneath:
Identification of assets
Analysis of security risks
Assess security requirements along with tradeoff
Formulation of security plan
Defining security policies
Development of procedures to apply security policies
Formulating technical implementation strategy
Attain buy-in from managers, users and technical employees
Train employees and users
Implementation of technical strategy along with security procedures
Test security as well as update in case any problem is there
Maintain security
3
Apart from this, NAT (network address translation) can be utilised. This is process for
reassigning single IP address space within further by changing network address data within IP
header of data packet when they travel via network to destination node (Saranya and
Thangadurai, 2019).
1.4 Justify the usage of approach for implementation as well as testing network addressing of
computer network.
Suppose the inside host 172.16.0.0/18 want to interact with 192.168.0.4/30 then the data
packet will be sent to NAT-enabled gateway router for having further interaction. The gateway
router will learn source IP address of packet and then will find in table whether packet
acknowledge the conditions for translation. Gateway router is liable for maintaining access
control list which will locate authenticated host for internal network translation purpose.
Thereby, inside local IP address will be translated into global IP address. This will be saved
within NAT table along with gateway router for routing the destination (Rahouma, Abdul-Karim,
and Nasr, 2020). In this way, NAT will be implemented and for testing message will be sent to
destination to ensure that it reach the destination as well as any kind of modifications in data
have not occurred. The security layer of reference layered model will aid within doing so.
Part 2
Compute and assign 4 IPv6 subnets via appending subnet ID to global routing prefix given and
document IPv6 subnets within the table
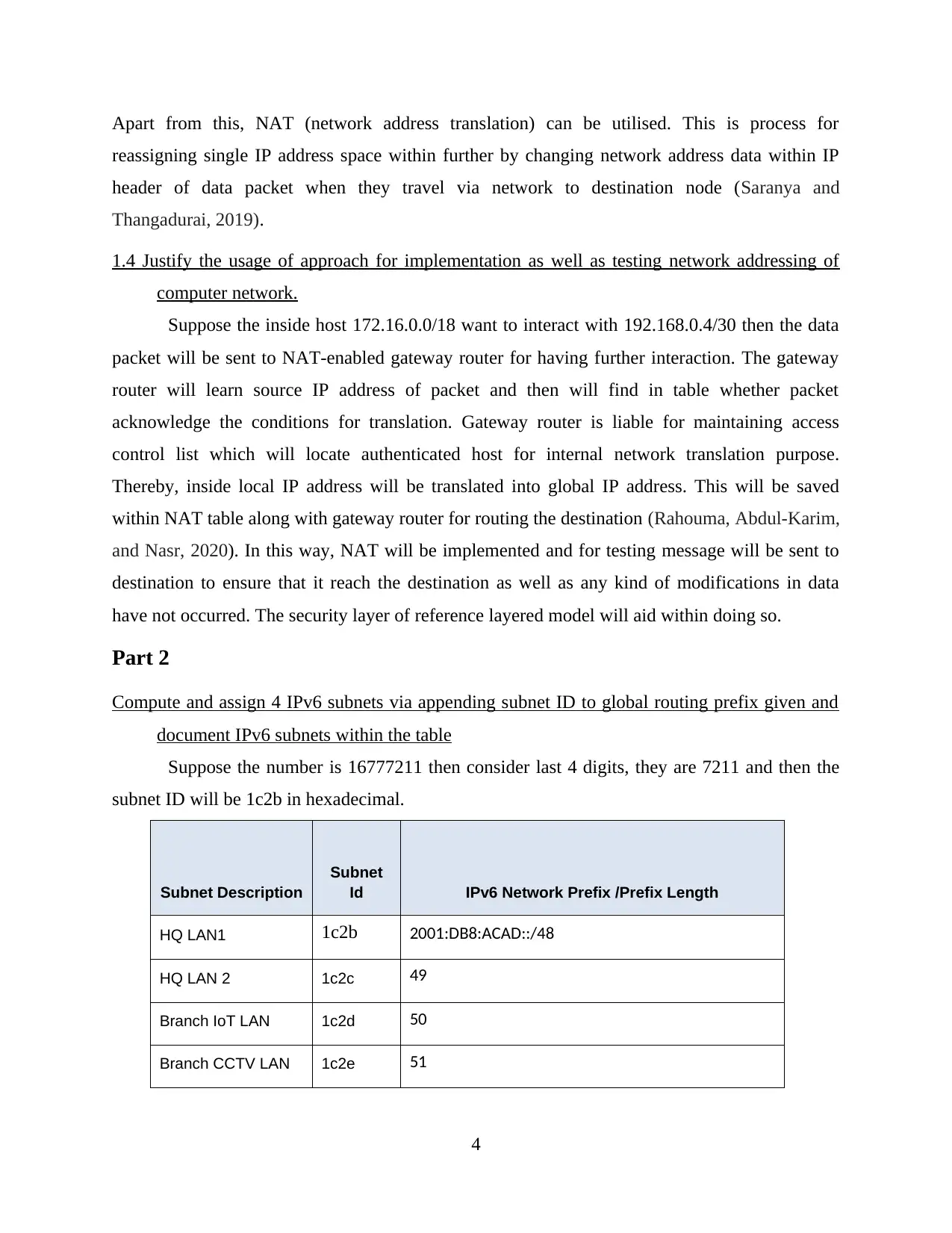
Suppose the number is 16777211 then consider last 4 digits, they are 7211 and then the
subnet ID will be 1c2b in hexadecimal.
Subnet Description
Subnet
Id IPv6 Network Prefix /Prefix Length
HQ LAN1 1c2b 2001:DB8:ACAD::/48
HQ LAN 2 1c2c 49
Branch IoT LAN 1c2d 50
Branch CCTV LAN 1c2e 51
4
reassigning single IP address space within further by changing network address data within IP
header of data packet when they travel via network to destination node (Saranya and
Thangadurai, 2019).
1.4 Justify the usage of approach for implementation as well as testing network addressing of
computer network.
Suppose the inside host 172.16.0.0/18 want to interact with 192.168.0.4/30 then the data
packet will be sent to NAT-enabled gateway router for having further interaction. The gateway
router will learn source IP address of packet and then will find in table whether packet
acknowledge the conditions for translation. Gateway router is liable for maintaining access
control list which will locate authenticated host for internal network translation purpose.
Thereby, inside local IP address will be translated into global IP address. This will be saved
within NAT table along with gateway router for routing the destination (Rahouma, Abdul-Karim,
and Nasr, 2020). In this way, NAT will be implemented and for testing message will be sent to
destination to ensure that it reach the destination as well as any kind of modifications in data
have not occurred. The security layer of reference layered model will aid within doing so.
Part 2
Compute and assign 4 IPv6 subnets via appending subnet ID to global routing prefix given and
document IPv6 subnets within the table
Suppose the number is 16777211 then consider last 4 digits, they are 7211 and then the
subnet ID will be 1c2b in hexadecimal.
Subnet Description
Subnet
Id IPv6 Network Prefix /Prefix Length
HQ LAN1 1c2b 2001:DB8:ACAD::/48
HQ LAN 2 1c2c 49
Branch IoT LAN 1c2d 50
Branch CCTV LAN 1c2e 51
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
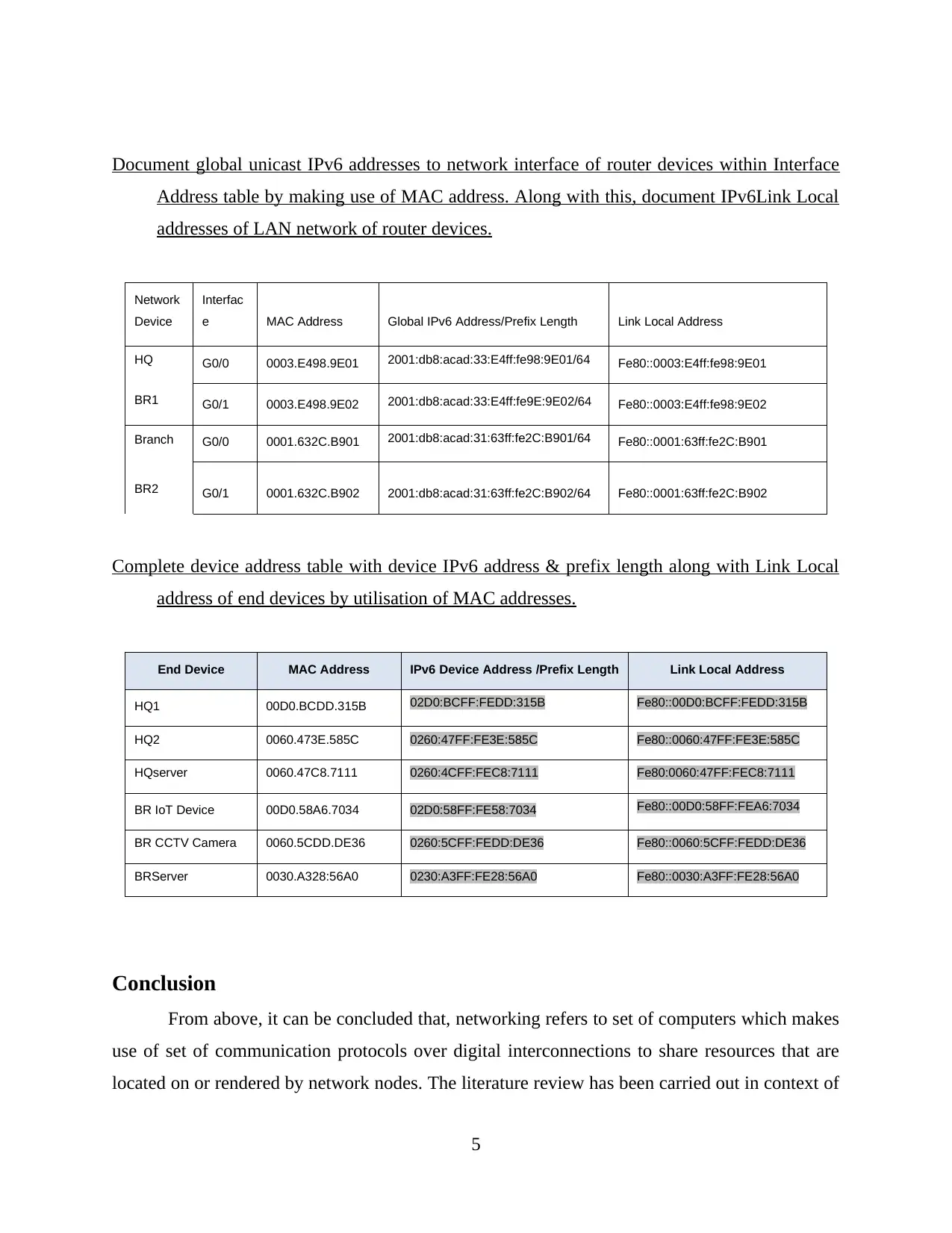
Document global unicast IPv6 addresses to network interface of router devices within Interface
Address table by making use of MAC address. Along with this, document IPv6Link Local
addresses of LAN network of router devices.
Network
Device
Interfac
e MAC Address Global IPv6 Address/Prefix Length Link Local Address
HQ
BR1
G0/0 0003.E498.9E01 2001:db8:acad:33:E4ff:fe98:9E01/64 Fe80::0003:E4ff:fe98:9E01
G0/1 0003.E498.9E02 2001:db8:acad:33:E4ff:fe9E:9E02/64 Fe80::0003:E4ff:fe98:9E02
Branch G0/0 0001.632C.B901 2001:db8:acad:31:63ff:fe2C:B901/64 Fe80::0001:63ff:fe2C:B901
BR2 G0/1 0001.632C.B902 2001:db8:acad:31:63ff:fe2C:B902/64 Fe80::0001:63ff:fe2C:B902
Complete device address table with device IPv6 address & prefix length along with Link Local
address of end devices by utilisation of MAC addresses.
End Device MAC Address IPv6 Device Address /Prefix Length Link Local Address
HQ1 00D0.BCDD.315B 02D0:BCFF:FEDD:315B Fe80::00D0:BCFF:FEDD:315B
HQ2 0060.473E.585C 0260:47FF:FE3E:585C Fe80::0060:47FF:FE3E:585C
HQserver 0060.47C8.7111 0260:4CFF:FEC8:7111 Fe80:0060:47FF:FEC8:7111
BR IoT Device 00D0.58A6.7034 02D0:58FF:FE58:7034 Fe80::00D0:58FF:FEA6:7034
BR CCTV Camera 0060.5CDD.DE36 0260:5CFF:FEDD:DE36 Fe80::0060:5CFF:FEDD:DE36
BRServer 0030.A328:56A0 0230:A3FF:FE28:56A0 Fe80::0030:A3FF:FE28:56A0
Conclusion
From above, it can be concluded that, networking refers to set of computers which makes
use of set of communication protocols over digital interconnections to share resources that are
located on or rendered by network nodes. The literature review has been carried out in context of
5
Address table by making use of MAC address. Along with this, document IPv6Link Local
addresses of LAN network of router devices.
Network
Device
Interfac
e MAC Address Global IPv6 Address/Prefix Length Link Local Address
HQ
BR1
G0/0 0003.E498.9E01 2001:db8:acad:33:E4ff:fe98:9E01/64 Fe80::0003:E4ff:fe98:9E01
G0/1 0003.E498.9E02 2001:db8:acad:33:E4ff:fe9E:9E02/64 Fe80::0003:E4ff:fe98:9E02
Branch G0/0 0001.632C.B901 2001:db8:acad:31:63ff:fe2C:B901/64 Fe80::0001:63ff:fe2C:B901
BR2 G0/1 0001.632C.B902 2001:db8:acad:31:63ff:fe2C:B902/64 Fe80::0001:63ff:fe2C:B902
Complete device address table with device IPv6 address & prefix length along with Link Local
address of end devices by utilisation of MAC addresses.
End Device MAC Address IPv6 Device Address /Prefix Length Link Local Address
HQ1 00D0.BCDD.315B 02D0:BCFF:FEDD:315B Fe80::00D0:BCFF:FEDD:315B
HQ2 0060.473E.585C 0260:47FF:FE3E:585C Fe80::0060:47FF:FE3E:585C
HQserver 0060.47C8.7111 0260:4CFF:FEC8:7111 Fe80:0060:47FF:FEC8:7111
BR IoT Device 00D0.58A6.7034 02D0:58FF:FE58:7034 Fe80::00D0:58FF:FEA6:7034
BR CCTV Camera 0060.5CDD.DE36 0260:5CFF:FEDD:DE36 Fe80::0060:5CFF:FEDD:DE36
BRServer 0030.A328:56A0 0230:A3FF:FE28:56A0 Fe80::0030:A3FF:FE28:56A0
Conclusion
From above, it can be concluded that, networking refers to set of computers which makes
use of set of communication protocols over digital interconnections to share resources that are
located on or rendered by network nodes. The literature review has been carried out in context of
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

whether reference models aids within implementation of networking devices for a network
engineer. It has been identified that reference models like TCP/IP aids within having knowledge
related with IP addresses and ways in which message are transmitted. In addition to this, OSI
reference model has different layers each with distinct rationale so by implementation of
networking devices, it assists the network engineer. Apart from this, IPv6 addresses has been
illustrated for given diagram.
6
engineer. It has been identified that reference models like TCP/IP aids within having knowledge
related with IP addresses and ways in which message are transmitted. In addition to this, OSI
reference model has different layers each with distinct rationale so by implementation of
networking devices, it assists the network engineer. Apart from this, IPv6 addresses has been
illustrated for given diagram.
6

References
Books & Journals
Aggarwal, N., Gupta, R. and Saxena, P., 2019. Comparative Study of OSI & TCP/IP Reference
Model. International Journal for Research in Applied Science & Engineering Technology
(IJRASET).
Alani, M.M., 2014. Guide to OSI and TCP/IP models.
Aldosari, H.M., 2015. A proposed security layer for the Internet of things communication
reference model. Procedia Computer Science, 65, pp.95-98.
Banjar, A., Pupatwibul, P. and Braun, R., 2015. Comparison of TCP/IP routing versus OpenFlow
table and implementation of intelligent computational model to provide autonomous
behavior. In Computational Intelligence and Efficiency in Engineering Systems (pp. 121-
142). Springer, Cham.
Castilho, S.D. and et. al, 2017, May. Proposed model to implement high-level information
security in internet of things. In 2017 Second International Conference on Fog and
Mobile Edge Computing (FMEC) (pp. 165-170). Ieee.
Colin, J.Y., Mathieu, H. and Nakechbandi, M., 2016, May. A proposal for an open logistics
interconnection reference model for a Physical Internet. In 2016 3rd International
Conference on Logistics Operations Management (GOL) (pp. 1-6). IEEE.
Khattak, H.A. and et. al, 2019. Cross-layer design and optimization techniques in wireless
multimedia sensor networks for smart cities. Computer Science and Information
Systems, 16(1), pp.1-17.
Kuznetsov, A. and et. al, 2019, April. Malware Correlation Monitoring in Computer Networks of
Promising Smart Grids. In 2019 IEEE 6th International Conference on Energy Smart
Systems (ESS) (pp. 347-352). IEEE.
Nath, P.B. and Uddin, M., 2015. TCP-IP Model in Data Communication and
Networking. American Journal of Engineering Research, 4(10), pp.102-107.
Rahouma, K.H., Abdul-Karim, M.S. and Nasr, K.S., 2020. TCP/IP Network Layers and Their
Protocols (A Survey). In Internet of Things—Applications and Future (pp. 287-323).
Springer, Singapore.
Rayes, A. and Salam, S., 2017. The Internet in IoT—OSI, TCP/IP, IPv4, IPv6 and Internet
Routing. In Internet of Things From Hype to Reality (pp. 35-56). Springer, Cham.
Saranya, M.S. and Thangadurai, K., 2019. An Analysis and Study on Computer Networks
Mechanisms and Network Elements.
Sinha, P. and et. al,, 2017, July. Security vulnerabilities, attacks and countermeasures in wireless
sensor networks at various layers of OSI reference model: A survey. In 2017
International Conference on Signal Processing and Communication (ICSPC) (pp. 288-
293). IEEE.
Suresh, P., 2016. Survey on seven layered architecture of OSI model. International Journal of
research in computer applications and robotics, 4(8), pp.1-10.
Zhang, C., Bengio, S. and Singer, Y., 2019. Are all layers created equal?. arXiv preprint
arXiv:1902.01996.
7
Books & Journals
Aggarwal, N., Gupta, R. and Saxena, P., 2019. Comparative Study of OSI & TCP/IP Reference
Model. International Journal for Research in Applied Science & Engineering Technology
(IJRASET).
Alani, M.M., 2014. Guide to OSI and TCP/IP models.
Aldosari, H.M., 2015. A proposed security layer for the Internet of things communication
reference model. Procedia Computer Science, 65, pp.95-98.
Banjar, A., Pupatwibul, P. and Braun, R., 2015. Comparison of TCP/IP routing versus OpenFlow
table and implementation of intelligent computational model to provide autonomous
behavior. In Computational Intelligence and Efficiency in Engineering Systems (pp. 121-
142). Springer, Cham.
Castilho, S.D. and et. al, 2017, May. Proposed model to implement high-level information
security in internet of things. In 2017 Second International Conference on Fog and
Mobile Edge Computing (FMEC) (pp. 165-170). Ieee.
Colin, J.Y., Mathieu, H. and Nakechbandi, M., 2016, May. A proposal for an open logistics
interconnection reference model for a Physical Internet. In 2016 3rd International
Conference on Logistics Operations Management (GOL) (pp. 1-6). IEEE.
Khattak, H.A. and et. al, 2019. Cross-layer design and optimization techniques in wireless
multimedia sensor networks for smart cities. Computer Science and Information
Systems, 16(1), pp.1-17.
Kuznetsov, A. and et. al, 2019, April. Malware Correlation Monitoring in Computer Networks of
Promising Smart Grids. In 2019 IEEE 6th International Conference on Energy Smart
Systems (ESS) (pp. 347-352). IEEE.
Nath, P.B. and Uddin, M., 2015. TCP-IP Model in Data Communication and
Networking. American Journal of Engineering Research, 4(10), pp.102-107.
Rahouma, K.H., Abdul-Karim, M.S. and Nasr, K.S., 2020. TCP/IP Network Layers and Their
Protocols (A Survey). In Internet of Things—Applications and Future (pp. 287-323).
Springer, Singapore.
Rayes, A. and Salam, S., 2017. The Internet in IoT—OSI, TCP/IP, IPv4, IPv6 and Internet
Routing. In Internet of Things From Hype to Reality (pp. 35-56). Springer, Cham.
Saranya, M.S. and Thangadurai, K., 2019. An Analysis and Study on Computer Networks
Mechanisms and Network Elements.
Sinha, P. and et. al,, 2017, July. Security vulnerabilities, attacks and countermeasures in wireless
sensor networks at various layers of OSI reference model: A survey. In 2017
International Conference on Signal Processing and Communication (ICSPC) (pp. 288-
293). IEEE.
Suresh, P., 2016. Survey on seven layered architecture of OSI model. International Journal of
research in computer applications and robotics, 4(8), pp.1-10.
Zhang, C., Bengio, S. and Singer, Y., 2019. Are all layers created equal?. arXiv preprint
arXiv:1902.01996.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





