Master of IT Project: Next-Generation Firewalls in Maldivian Business
VerifiedAdded on 2022/09/18
|13
|3766
|25
Project
AI Summary
This project proposal outlines a Master of Information Technology (MIT) project focusing on the implementation and impact of Next-Generation Firewalls (NGFWs) within the business sector of the Maldives. The proposal begins with an introduction to the importance of NGFWs in the context of evolving cyber threats and the limitations of conventional firewalls. The project background highlights the benefits of NGFWs, including application awareness, streamlined infrastructure, enhanced threat protection, and increased network speed. A literature review explores the background of NGFWs, their features, and their application in securing data centers and controlling application layers. The project aims to identify the application of NGFWs and their effects on Maldivian enterprises. The methodology will involve primary research. The proposal includes a project plan and references to support the research. The project aims to find the benefits of new generation firewalls and understand the application of new generation firewalls at the various business in the Maldives.

SCHOOL OF INFORMATION TECHNOLOGY
MASTER OF INFORMATION TECHNOLOGY
PROJECT PROPOSAL
Student Name:
Student Number:
Batch Number
Module Name:
Module Code:
Title of Project:
Lecturer/ Supervisor:
Date:
Student Name / Index Number Page | 1
MASTER OF INFORMATION TECHNOLOGY
PROJECT PROPOSAL
Student Name:
Student Number:
Batch Number
Module Name:
Module Code:
Title of Project:
Lecturer/ Supervisor:
Date:
Student Name / Index Number Page | 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MIT Final Project Proposal Assessment Form
Student Name:
Student Number:
Course: Masters of Information Technology
Batch Number:
Project Title:
Due Date:
Lecturer/ Supervisor: Aishath Shimaz
Student Name / Index Number Page | 2
Student Name:
Student Number:
Course: Masters of Information Technology
Batch Number:
Project Title:
Due Date:
Lecturer/ Supervisor: Aishath Shimaz
Student Name / Index Number Page | 2

Table of Contents
1 Introduction...................................................................................................................................4
2 Project Background.......................................................................................................................4
3 Literature Review..........................................................................................................................6
3.1 Background of Next Generation Firewalls and business at Maldives:...................................6
3.2 Implementing the firewall for the peak performance:............................................................7
3.3 Understanding multiple protections of security:....................................................................7
4 Project Aim and Objectives...........................................................................................................8
5 Methodology..................................................................................................................................8
6 Commercial/ Industrial Collaboration............................................................................................9
7 Project Plan....................................................................................................................................9
8 References...................................................................................................................................11
Student Name / Index Number Page | 3
1 Introduction...................................................................................................................................4
2 Project Background.......................................................................................................................4
3 Literature Review..........................................................................................................................6
3.1 Background of Next Generation Firewalls and business at Maldives:...................................6
3.2 Implementing the firewall for the peak performance:............................................................7
3.3 Understanding multiple protections of security:....................................................................7
4 Project Aim and Objectives...........................................................................................................8
5 Methodology..................................................................................................................................8
6 Commercial/ Industrial Collaboration............................................................................................9
7 Project Plan....................................................................................................................................9
8 References...................................................................................................................................11
Student Name / Index Number Page | 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table of Figures
Figure 1: “The Gantt chart for the current project”..............................................................................10
Student Name / Index Number Page | 4
Figure 1: “The Gantt chart for the current project”..............................................................................10
Student Name / Index Number Page | 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 INTRODUCTION
The infrastructure development at the Maldives is dependent primarily in the tourism
industry along with the commentary government, construction, real estate distribution,
transport and other tertiary sectors. The taxes on their tourism is ploughed to infrastructure
and is utilized for developing technology in agricultural areas. On the other hand, the
firewalls have remained as the standard security tools for most of the enterprises at Maldives
(Azzam 2019). Nevertheless, in current changing landscape of threat, the “next-generation
firewalls” have remained as the only ones providing suitable protection. The NGFW or
“next-generation firewall” is the deep packet inspection firewall moving beyond the protocol
or port inspection. It has been blocking to include the inspection at application level along
with bringing intelligence and intrusion prevention from external to the firewall (Kolios et
al. 2016). Moreover, they are able to replace the present security technologies around the
enterprises both small and large. Nevertheless, they are not all that new. Further, the
technology underpinning the devices has been across for few time. Here, the new thing is the
thoroughness and integration of security provided. This is due to the processing of high
performance and awareness of applications. Besides, the next generation is never the most
effective moniker for the firewalls. This has been never doing more than only blocking ports
along with filter traffic. Besides, the term is stuck. Here a brand new set of security
appliances has emerged in market. Here, everyone is found to be sporting the categorization
of the next-generation firewall. The following proposal demonstrates the next-generation
firewalls. This is done from the usage perspectives for Maldivian Enterprises.
2 PROJECT BACKGROUND
Here, the importance and the effective effect of the present project for the business
sector at the Maldives is demonstrated. First of all, innovation is multifunctional. The
conventional firewalls have been found to be providing the primary packet filtering along
with translations of port address, stateful inspections. They can also support VPNs or virtual
private networks. Nevertheless, they are restricted to Transport layer and Data Link layer of
OSI Model (Perlman, Kaufman & Speciner, 2016). Apart from this, the NGFWs also been
also involving IDS or Integrated Intrusion Detection Systems and IPS or Intrusion Protection
Systems. It detects the attacks on the basis of threat signatures, traffic behavioral assessment
Student Name / Index Number Page | 5
The infrastructure development at the Maldives is dependent primarily in the tourism
industry along with the commentary government, construction, real estate distribution,
transport and other tertiary sectors. The taxes on their tourism is ploughed to infrastructure
and is utilized for developing technology in agricultural areas. On the other hand, the
firewalls have remained as the standard security tools for most of the enterprises at Maldives
(Azzam 2019). Nevertheless, in current changing landscape of threat, the “next-generation
firewalls” have remained as the only ones providing suitable protection. The NGFW or
“next-generation firewall” is the deep packet inspection firewall moving beyond the protocol
or port inspection. It has been blocking to include the inspection at application level along
with bringing intelligence and intrusion prevention from external to the firewall (Kolios et
al. 2016). Moreover, they are able to replace the present security technologies around the
enterprises both small and large. Nevertheless, they are not all that new. Further, the
technology underpinning the devices has been across for few time. Here, the new thing is the
thoroughness and integration of security provided. This is due to the processing of high
performance and awareness of applications. Besides, the next generation is never the most
effective moniker for the firewalls. This has been never doing more than only blocking ports
along with filter traffic. Besides, the term is stuck. Here a brand new set of security
appliances has emerged in market. Here, everyone is found to be sporting the categorization
of the next-generation firewall. The following proposal demonstrates the next-generation
firewalls. This is done from the usage perspectives for Maldivian Enterprises.
2 PROJECT BACKGROUND
Here, the importance and the effective effect of the present project for the business
sector at the Maldives is demonstrated. First of all, innovation is multifunctional. The
conventional firewalls have been found to be providing the primary packet filtering along
with translations of port address, stateful inspections. They can also support VPNs or virtual
private networks. Nevertheless, they are restricted to Transport layer and Data Link layer of
OSI Model (Perlman, Kaufman & Speciner, 2016). Apart from this, the NGFWs also been
also involving IDS or Integrated Intrusion Detection Systems and IPS or Intrusion Protection
Systems. It detects the attacks on the basis of threat signatures, traffic behavioral assessment
Student Name / Index Number Page | 5

and anomalous activities. The functionalities have been useful to perform the in-depth
investigation and develop the filtering of packet content of the network traffic to the
application layer. Next, there is application awareness. The convention firewalls have been
typically blocking the common application ports and services over the network for
controlling the access of location and monitoring the particular threats (Chimento Jr, 2019).
Besides, the network connectivity has been turning to be complicated and various
applications have been using ports. This has been making that highly complicated for
conventional firewalls for determining the port targeted. Again, the ports are used in
different other manners like tunnelling. Here, the network protocol is been enclosed under
the packers that are carried by second network and is been de-encapsulated at destinations.
For countering that, the devices of next-generation firewall devices have been monitoring the
traffic for the second layer across the seventh layer. They are sufficiently intelligent for
determining what is been sent or gained exactly. As the content is under policy it is been sent
further and otherwise it can be blocked (Malmgren & Persson, 2016). Besides, the
application awareness has been also enabling the business in setting policies depending on
user and applications. Here, for example this has been permitting the users in accessing
Facebook and not blocking the chats over Facebook.
Next, the project is useful for streamlined infrastructures at Maldives’s organziations.
The conventional firewalls have needed distinct security appliances for all the new threats.
This leads to extra costs and efforts to maintain and update all the devices. Having the
dynamic IP address, this turns to be a complex mess to configure various rules required to
determine and control traffic (Zapechnikov, Miloslavskaya & Tolstoy, 2015). Besides, the
devices have been never prodding the needed controls and security to those contents with
applications and users. Besides, NGFW has been providing the integrated type of antivirus,
deep-packet inspection, spam filtering and control of applications through just one console
and device. Here the infrastructural complexities get reduced as no additional devices are
needed. Again, the project is useful to identify the threat protections (Neupane, Haddad &
Chen, 2018). The NGFWs, unlike the conventional firewalls has been involving the malware
protections and antivirus that has been upgraded automatically in a continuous way as new
threats are found out. The devices further decrease the attack avenues with restricting the
applications running on that (Antonov, Filippov & Mamoutova, 2016). Apart from this, it has
been scanning every approved application for the confidential data and hidden
vulnerabilities along with mitigating the risks from an unknown type of applications. It is
Student Name / Index Number Page | 6
investigation and develop the filtering of packet content of the network traffic to the
application layer. Next, there is application awareness. The convention firewalls have been
typically blocking the common application ports and services over the network for
controlling the access of location and monitoring the particular threats (Chimento Jr, 2019).
Besides, the network connectivity has been turning to be complicated and various
applications have been using ports. This has been making that highly complicated for
conventional firewalls for determining the port targeted. Again, the ports are used in
different other manners like tunnelling. Here, the network protocol is been enclosed under
the packers that are carried by second network and is been de-encapsulated at destinations.
For countering that, the devices of next-generation firewall devices have been monitoring the
traffic for the second layer across the seventh layer. They are sufficiently intelligent for
determining what is been sent or gained exactly. As the content is under policy it is been sent
further and otherwise it can be blocked (Malmgren & Persson, 2016). Besides, the
application awareness has been also enabling the business in setting policies depending on
user and applications. Here, for example this has been permitting the users in accessing
Facebook and not blocking the chats over Facebook.
Next, the project is useful for streamlined infrastructures at Maldives’s organziations.
The conventional firewalls have needed distinct security appliances for all the new threats.
This leads to extra costs and efforts to maintain and update all the devices. Having the
dynamic IP address, this turns to be a complex mess to configure various rules required to
determine and control traffic (Zapechnikov, Miloslavskaya & Tolstoy, 2015). Besides, the
devices have been never prodding the needed controls and security to those contents with
applications and users. Besides, NGFW has been providing the integrated type of antivirus,
deep-packet inspection, spam filtering and control of applications through just one console
and device. Here the infrastructural complexities get reduced as no additional devices are
needed. Again, the project is useful to identify the threat protections (Neupane, Haddad &
Chen, 2018). The NGFWs, unlike the conventional firewalls has been involving the malware
protections and antivirus that has been upgraded automatically in a continuous way as new
threats are found out. The devices further decrease the attack avenues with restricting the
applications running on that (Antonov, Filippov & Mamoutova, 2016). Apart from this, it has
been scanning every approved application for the confidential data and hidden
vulnerabilities along with mitigating the risks from an unknown type of applications. It is
Student Name / Index Number Page | 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

also helpful to decrease the usage of bandwidth from useless traffic that has never been
possible with the conventional firewalls.
Again, the project is useful for increasing the network speed at the various business of
Maldives. Having various vendors of the conventional claims of firewalls for offering
particular throughput from all the ports, the reality is totally different. This is commonly a
gigabyte in nature (Russo, Costa & Armando, 2018). Here, the rise in the number of
protection services and devices, as turned on, they tend to choke the speed of the network.
Within this time, the traffic has been reaching the end-users. Here, the speed gets chopped by
about one-third of the real speed as promised. The throughput of the next-gen firewall, in
contrast, has been staying exactly the similar irrespective of the number of security services.
3 LITERATURE REVIEW
3.1 BACKGROUND OF NEXT GENERATION FIREWALLS AND
BUSINESS AT MALDIVES:
Kokko (2017) identifies that the next generation firewalling business at the Maldives
has been using to secure the data centres or perimeter of a network offering other vital
features. Here, the main one is Ethernet-layer tagging where the IT security professionals
are able to tag and then assign the related security policies for the data. Further, IT security
professionals are able to tag the information and then assign important security policies to
the data. These security policies have been travelling with that irrespective of the fact where
it can finish up over the network. The administrators are able to streamline the operations
through that they trusted for bypassing inspection of the checkpoints.
Hachana, Cuppens and Cuppens-Boulahia (2016) mention another feature of it is the
control of the application layer. It has been safeguarding to regulate the groups or
individuals of the software titles that are deemed by the security managers deeming highly
risky to run over the network. Here, the web pages have been a common mechanism of
delivery of mechanism for the firewalls, malware to control and understand with
technologies as the content filtering. This is as the content filtering. Here, the web URL
malware and filtering detection.
Student Name / Index Number Page | 7
possible with the conventional firewalls.
Again, the project is useful for increasing the network speed at the various business of
Maldives. Having various vendors of the conventional claims of firewalls for offering
particular throughput from all the ports, the reality is totally different. This is commonly a
gigabyte in nature (Russo, Costa & Armando, 2018). Here, the rise in the number of
protection services and devices, as turned on, they tend to choke the speed of the network.
Within this time, the traffic has been reaching the end-users. Here, the speed gets chopped by
about one-third of the real speed as promised. The throughput of the next-gen firewall, in
contrast, has been staying exactly the similar irrespective of the number of security services.
3 LITERATURE REVIEW
3.1 BACKGROUND OF NEXT GENERATION FIREWALLS AND
BUSINESS AT MALDIVES:
Kokko (2017) identifies that the next generation firewalling business at the Maldives
has been using to secure the data centres or perimeter of a network offering other vital
features. Here, the main one is Ethernet-layer tagging where the IT security professionals
are able to tag and then assign the related security policies for the data. Further, IT security
professionals are able to tag the information and then assign important security policies to
the data. These security policies have been travelling with that irrespective of the fact where
it can finish up over the network. The administrators are able to streamline the operations
through that they trusted for bypassing inspection of the checkpoints.
Hachana, Cuppens and Cuppens-Boulahia (2016) mention another feature of it is the
control of the application layer. It has been safeguarding to regulate the groups or
individuals of the software titles that are deemed by the security managers deeming highly
risky to run over the network. Here, the web pages have been a common mechanism of
delivery of mechanism for the firewalls, malware to control and understand with
technologies as the content filtering. This is as the content filtering. Here, the web URL
malware and filtering detection.
Student Name / Index Number Page | 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Again, Miranda, Mtz and Mata (2017) firewalls have been delivering the prevention
technology or intrusion detection. This has been provided as the stand-alone anomalies for
determining the common attacks and the helping to protect unpatched systems. Otherwise
this has been including misconfigured applications. Jingyao et al. (2019) show that NGFW
has been providing intrusion prevention abilities for protecting against SQL injections. This
is the exploit where the attackers have been inserting the malware to the statements of the
database. This takes the load off the staff of security due to the fact that is never been
reviewing o logs of network for determining attacks.
3.2 IMPLEMENTING FIREWALL FOR PEAK PERFORMANCE:
The security experts like Xuan et al. (2016) has stated that the success of firewall
needing the assimilation of picking the proper feature set and implementing the technology
having in mind the optimum performances. The network performance has been involving
keeping the included latency for the least is the primary implementing considerations. For
instance, the rates of throughputs for NGFWs where the layer on the advanced features of
security has been alarmingly slow as compared to the conventional firewalls. This mainly
monitors the port numbers and IP addresses. Next, NGFW has been running virtual
machines apart from dedicated appliances. This has been comprised of ASICs or
Application-Specific Integrated Circuits. Apart from this, asynchronous and multithreading
real processing is able to put contribution to the extra boost of speed. Apart from this, there
have been some solutions devoting any processor for the applications and the prevention of
intrusion. Here, there has been separating screens for the viruses and performing the duties.
Besides, Rebahi et al. (2015) explain that the ongoing tuning of performance has been vital
to assure that the enterprises were getting the complete benefit of the NGFW. Here, the
application level controls have been keeping the risky of the software away from Maldives’
enterprise networks. This comprises of the landscape changing constantly. As one is unable
to make the rule to manage the application that has been recently been resealed. Hence, one
is unable to gain the benefits of the controls of application-levels.
3.3 UNDERSTANDING MULTIPLE PROTECTIONS OF SECURITY:
Though the best of firewalls has been doing much to secure the enterprise. This indicates
the means the business at the Maldives has been requiring other parts for creating wider
ecosystem. It needs IT managers for orchestrating the different parts as running system
smoothly. In order to meet their ultimate objectives, few vendors have been providing tools
Student Name / Index Number Page | 8
technology or intrusion detection. This has been provided as the stand-alone anomalies for
determining the common attacks and the helping to protect unpatched systems. Otherwise
this has been including misconfigured applications. Jingyao et al. (2019) show that NGFW
has been providing intrusion prevention abilities for protecting against SQL injections. This
is the exploit where the attackers have been inserting the malware to the statements of the
database. This takes the load off the staff of security due to the fact that is never been
reviewing o logs of network for determining attacks.
3.2 IMPLEMENTING FIREWALL FOR PEAK PERFORMANCE:
The security experts like Xuan et al. (2016) has stated that the success of firewall
needing the assimilation of picking the proper feature set and implementing the technology
having in mind the optimum performances. The network performance has been involving
keeping the included latency for the least is the primary implementing considerations. For
instance, the rates of throughputs for NGFWs where the layer on the advanced features of
security has been alarmingly slow as compared to the conventional firewalls. This mainly
monitors the port numbers and IP addresses. Next, NGFW has been running virtual
machines apart from dedicated appliances. This has been comprised of ASICs or
Application-Specific Integrated Circuits. Apart from this, asynchronous and multithreading
real processing is able to put contribution to the extra boost of speed. Apart from this, there
have been some solutions devoting any processor for the applications and the prevention of
intrusion. Here, there has been separating screens for the viruses and performing the duties.
Besides, Rebahi et al. (2015) explain that the ongoing tuning of performance has been vital
to assure that the enterprises were getting the complete benefit of the NGFW. Here, the
application level controls have been keeping the risky of the software away from Maldives’
enterprise networks. This comprises of the landscape changing constantly. As one is unable
to make the rule to manage the application that has been recently been resealed. Hence, one
is unable to gain the benefits of the controls of application-levels.
3.3 UNDERSTANDING MULTIPLE PROTECTIONS OF SECURITY:
Though the best of firewalls has been doing much to secure the enterprise. This indicates
the means the business at the Maldives has been requiring other parts for creating wider
ecosystem. It needs IT managers for orchestrating the different parts as running system
smoothly. In order to meet their ultimate objectives, few vendors have been providing tools
Student Name / Index Number Page | 8

for all sort of unified management. It has been enabling the managers in deploying the
constant polices around the overall continuum of the attack. This is done through the
invoking of intrusion detection, access controls and other rules across the core interface.
Here, the actual value has been actually knowing the identity as per Huh et al. (2016). As the
system has known specific person of using specific device to connect the networks. Here, one
can send the data to NGFW such that granular policies could be applied for particular
situation. Rather than setting the rules for huge groups of people. This s to set as per the
according to the individual tasks for requiring to be performed.
Talpur, Abdalla & Kechadi (2015) assures that while the solutions have been there
currently, it is able to integrate the security products successfully under distinct vendor
profiles. This has been orchestrating the solutions under the multivendor scenarios staying
challenging. The interfaces of the application programming interfaces as the integration
method which is common in nature. However, this has been dependably among various
vendors having near partnerships. Apart from this, the enterprises have been writing the
scripts for cobbling the components together. Again, the crisis has been turning to be brittle.
This has meant the architecture of security has not been adaptable for change the business
requirements. Here, the initiatives and applications like moving to the cloud.
4 PROJECT AIM AND OBJECTIVES
The aims of the project include the following:
What is the application of new generation firewalls? How new generation firewalls have been affecting the Maldivian Enterprises?
The objectives are mentioned hereafter:
To find the benefits of new generation firewalls To understand the application of new generation firewalls at the various business in
the Maldives.
5 METHODOLOGY
Here, primary research would be conducted. This involves going directly to the origin of
the business of Maldives and prospective managers working there. Here questions would be
asked and information would be collected. The qualitative data would be analyzed. This is
through deriving the explanation of implementation of NGFW at various organizations at
Student Name / Index Number Page | 9
constant polices around the overall continuum of the attack. This is done through the
invoking of intrusion detection, access controls and other rules across the core interface.
Here, the actual value has been actually knowing the identity as per Huh et al. (2016). As the
system has known specific person of using specific device to connect the networks. Here, one
can send the data to NGFW such that granular policies could be applied for particular
situation. Rather than setting the rules for huge groups of people. This s to set as per the
according to the individual tasks for requiring to be performed.
Talpur, Abdalla & Kechadi (2015) assures that while the solutions have been there
currently, it is able to integrate the security products successfully under distinct vendor
profiles. This has been orchestrating the solutions under the multivendor scenarios staying
challenging. The interfaces of the application programming interfaces as the integration
method which is common in nature. However, this has been dependably among various
vendors having near partnerships. Apart from this, the enterprises have been writing the
scripts for cobbling the components together. Again, the crisis has been turning to be brittle.
This has meant the architecture of security has not been adaptable for change the business
requirements. Here, the initiatives and applications like moving to the cloud.
4 PROJECT AIM AND OBJECTIVES
The aims of the project include the following:
What is the application of new generation firewalls? How new generation firewalls have been affecting the Maldivian Enterprises?
The objectives are mentioned hereafter:
To find the benefits of new generation firewalls To understand the application of new generation firewalls at the various business in
the Maldives.
5 METHODOLOGY
Here, primary research would be conducted. This involves going directly to the origin of
the business of Maldives and prospective managers working there. Here questions would be
asked and information would be collected. The qualitative data would be analyzed. This is
through deriving the explanation of implementation of NGFW at various organizations at
Student Name / Index Number Page | 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Maldives. It would be useful to understand the aforementioned research objective by
revealing the themes and patterns in the results (Shah & Parvez, 2015). For this a survey
would be conducted over the Internet, where questionnaires are to be sent the managers
employed in various sectors of Maldives. Besides, the researchers must be asking the
participants to directly report the behaviors, feelings and thoughts. Next, considerable
attention must be paid to the sampling issues. Here, a strong preference must be provided for
the huge random samples as they deliver the most accurate estimations of the aspects that
are true for the populations. Performing this over the internet is the most vital characteristic
of this online survey. This established has been leading to appealing outcomes. Further, the
researchers must be decision the aim towards conducting the survey over the Internet such
that the results gauged are used for developing the service and products along with customer
services and another objective that is pre-decided (Mimidis-Kentis et al. 2019). Further, it
must be following an accurate research design. In order to bear effective outcomes, it is
essential to design a thorough framework of the current research. The deployment of the
research design is useful to find out how to conduct market analysis and research through
this online survey. Here, precisely structured survey questions are to be constructed. This
must involve the carefully curated balance of the open and close-ended survey questions.
Here, different question types are there sufficing various reasons for the survey across the
Internet (Qazi et al. 2017).
It is proposed that for the current research the evaluation must be done through big data
and the data analytics. It is driven through specialized analytics software and systems. This
involves the computer systems that are of high-power. Moreover, it provides different
benefits of a business that involves the competitive befits over the various rivals. Next it
delivers improved operational affectivity, smarter customer serve, efficient marketing along
with new opportunities of revenue.
6 COMMERCIAL/ INDUSTRIAL COLLABORATION
Here, various universities that run information technology and management programs at
the Maldives are to be brought in collaboration. Besides, the research activities are to be
taken up by various industries of Maldives and then turned into services and products.
Student Name / Index Number Page | 10
revealing the themes and patterns in the results (Shah & Parvez, 2015). For this a survey
would be conducted over the Internet, where questionnaires are to be sent the managers
employed in various sectors of Maldives. Besides, the researchers must be asking the
participants to directly report the behaviors, feelings and thoughts. Next, considerable
attention must be paid to the sampling issues. Here, a strong preference must be provided for
the huge random samples as they deliver the most accurate estimations of the aspects that
are true for the populations. Performing this over the internet is the most vital characteristic
of this online survey. This established has been leading to appealing outcomes. Further, the
researchers must be decision the aim towards conducting the survey over the Internet such
that the results gauged are used for developing the service and products along with customer
services and another objective that is pre-decided (Mimidis-Kentis et al. 2019). Further, it
must be following an accurate research design. In order to bear effective outcomes, it is
essential to design a thorough framework of the current research. The deployment of the
research design is useful to find out how to conduct market analysis and research through
this online survey. Here, precisely structured survey questions are to be constructed. This
must involve the carefully curated balance of the open and close-ended survey questions.
Here, different question types are there sufficing various reasons for the survey across the
Internet (Qazi et al. 2017).
It is proposed that for the current research the evaluation must be done through big data
and the data analytics. It is driven through specialized analytics software and systems. This
involves the computer systems that are of high-power. Moreover, it provides different
benefits of a business that involves the competitive befits over the various rivals. Next it
delivers improved operational affectivity, smarter customer serve, efficient marketing along
with new opportunities of revenue.
6 COMMERCIAL/ INDUSTRIAL COLLABORATION
Here, various universities that run information technology and management programs at
the Maldives are to be brought in collaboration. Besides, the research activities are to be
taken up by various industries of Maldives and then turned into services and products.
Student Name / Index Number Page | 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
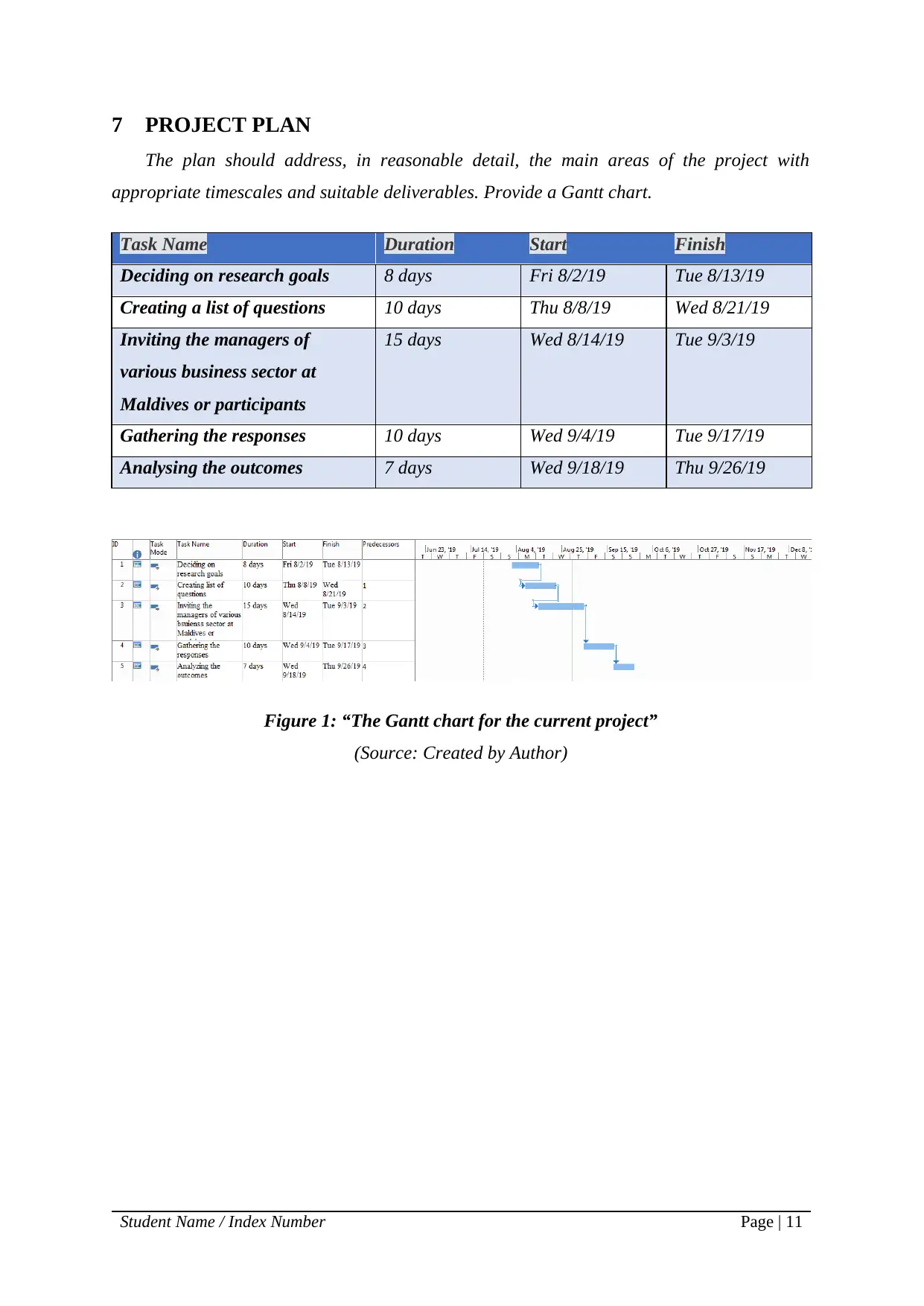
7 PROJECT PLAN
The plan should address, in reasonable detail, the main areas of the project with
appropriate timescales and suitable deliverables. Provide a Gantt chart.
Task Name Duration Start Finish
Deciding on research goals 8 days Fri 8/2/19 Tue 8/13/19
Creating a list of questions 10 days Thu 8/8/19 Wed 8/21/19
Inviting the managers of
various business sector at
Maldives or participants
15 days Wed 8/14/19 Tue 9/3/19
Gathering the responses 10 days Wed 9/4/19 Tue 9/17/19
Analysing the outcomes 7 days Wed 9/18/19 Thu 9/26/19
Figure 1: “The Gantt chart for the current project”
(Source: Created by Author)
Student Name / Index Number Page | 11
The plan should address, in reasonable detail, the main areas of the project with
appropriate timescales and suitable deliverables. Provide a Gantt chart.
Task Name Duration Start Finish
Deciding on research goals 8 days Fri 8/2/19 Tue 8/13/19
Creating a list of questions 10 days Thu 8/8/19 Wed 8/21/19
Inviting the managers of
various business sector at
Maldives or participants
15 days Wed 8/14/19 Tue 9/3/19
Gathering the responses 10 days Wed 9/4/19 Tue 9/17/19
Analysing the outcomes 7 days Wed 9/18/19 Thu 9/26/19
Figure 1: “The Gantt chart for the current project”
(Source: Created by Author)
Student Name / Index Number Page | 11

8 REFERENCES
Antonov, A. P., Filippov, A. S., & Mamoutova, O. V. (2016, April). Next generation FPGA-
based platform for network security. In 2016 18th Conference of Open Innovations
Association and Seminar on Information Security and Protection of Information
Technology (FRUCT-ISPIT) (pp. 9-14). IEEE.
Azzam, H., 2019. Corporates in the Digital Age. In Technology Optimization and Change
Management for Successful Digital Supply Chains (pp. 39-52). IGI Global.
Chimento Jr, J. J. (2019). Toward an Understanding of Using High Entropic Digital
Communication Techniques in Cybersecurity Decision Making (Doctoral
dissertation, New Jersey City University).
Hachana, S., Cuppens, F., & Cuppens-Boulahia, N. (2016, December). Towards a new
generation of industrial firewalls: Operational-process aware filtering. In 2016 14th
Annual Conference on Privacy, Security and Trust (PST) (pp. 615-622). IEEE.
Huh, J. H., Bobba, R. B., Markham, T., Nicol, D. M., Hull, J., Chernoguzov, A., ... & Huang,
J. (2016). Next-generation access control for distributed control systems. IEEE
Internet Computing, 20(5), 28-37.
Jingyao, S., Chandel, S., Yunnan, Y., Jingji, Z., & Zhipeng, Z. (2019, March). Securing a
Network: How Effective Using Firewalls and VPNs Are?. In Future of Information
and Communication Conference (pp. 1050-1068). Springer, Cham.
Kokko, K. (2017). Next-generation firewall case study.
Kolios, P., Pitsillides, A., Mokryn, O., & Papdaki, K. (2016). Data dissemination in public
safety networks. In Wireless Public Safety Networks 2 (pp. 199-225). Elsevier.
Malmgren, A., & Persson, S. (2016). A comparative study of Palo Alto Networks and Juniper
Networks next-generation firewalls for a small enterprise network.
Mimidis-Kentis, A., Soler, J., Veitch, P., Broadbent, A., Mobilio, M., Riganelli, O., ... &
Sayadi, B. (2019). The Next Generation Platform as A Service: Composition and
Deployment of Platforms and Services. Future Internet, 11(5), 119.
Miranda, J. M., Mtz, F. A. P., & Mata, M. A. M. (2017, June). Next generation systems—
Scope and application of intrusion detection and prevention systems (IDPS) a
systematic literature review. In 2017 12th Iberian Conference on Information Systems
and Technologies (CISTI) (pp. 1-7). IEEE.
Neupane, K., Haddad, R., & Chen, L. (2018, April). Next Generation Firewall for Network
Security: A Survey. In SoutheastCon 2018 (pp. 1-6). IEEE.
Student Name / Index Number Page | 12
Antonov, A. P., Filippov, A. S., & Mamoutova, O. V. (2016, April). Next generation FPGA-
based platform for network security. In 2016 18th Conference of Open Innovations
Association and Seminar on Information Security and Protection of Information
Technology (FRUCT-ISPIT) (pp. 9-14). IEEE.
Azzam, H., 2019. Corporates in the Digital Age. In Technology Optimization and Change
Management for Successful Digital Supply Chains (pp. 39-52). IGI Global.
Chimento Jr, J. J. (2019). Toward an Understanding of Using High Entropic Digital
Communication Techniques in Cybersecurity Decision Making (Doctoral
dissertation, New Jersey City University).
Hachana, S., Cuppens, F., & Cuppens-Boulahia, N. (2016, December). Towards a new
generation of industrial firewalls: Operational-process aware filtering. In 2016 14th
Annual Conference on Privacy, Security and Trust (PST) (pp. 615-622). IEEE.
Huh, J. H., Bobba, R. B., Markham, T., Nicol, D. M., Hull, J., Chernoguzov, A., ... & Huang,
J. (2016). Next-generation access control for distributed control systems. IEEE
Internet Computing, 20(5), 28-37.
Jingyao, S., Chandel, S., Yunnan, Y., Jingji, Z., & Zhipeng, Z. (2019, March). Securing a
Network: How Effective Using Firewalls and VPNs Are?. In Future of Information
and Communication Conference (pp. 1050-1068). Springer, Cham.
Kokko, K. (2017). Next-generation firewall case study.
Kolios, P., Pitsillides, A., Mokryn, O., & Papdaki, K. (2016). Data dissemination in public
safety networks. In Wireless Public Safety Networks 2 (pp. 199-225). Elsevier.
Malmgren, A., & Persson, S. (2016). A comparative study of Palo Alto Networks and Juniper
Networks next-generation firewalls for a small enterprise network.
Mimidis-Kentis, A., Soler, J., Veitch, P., Broadbent, A., Mobilio, M., Riganelli, O., ... &
Sayadi, B. (2019). The Next Generation Platform as A Service: Composition and
Deployment of Platforms and Services. Future Internet, 11(5), 119.
Miranda, J. M., Mtz, F. A. P., & Mata, M. A. M. (2017, June). Next generation systems—
Scope and application of intrusion detection and prevention systems (IDPS) a
systematic literature review. In 2017 12th Iberian Conference on Information Systems
and Technologies (CISTI) (pp. 1-7). IEEE.
Neupane, K., Haddad, R., & Chen, L. (2018, April). Next Generation Firewall for Network
Security: A Survey. In SoutheastCon 2018 (pp. 1-6). IEEE.
Student Name / Index Number Page | 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

