Analysis of Sensor Network Security: A Review of Recent Studies
VerifiedAdded on 2019/11/25
|16
|2156
|353
Report
AI Summary
The assignment content is about an updated filing system for network security, wireless networks, and sensor networks. It includes a focus on persuasive networking technology, business processes, and technological advancements. The content also discusses the approach of Hamadi et al. (2008) in specifying exceptional behavior in business processes using Self-Adapting Recovery Nets (SARN). Additionally, it touches upon the use of Google Scholar as a source, bibliographic files, and selected papers.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NIT6130 INTRODUCTION TO RESEARCH
ASSIGNMENT 2 – LITERATURE REVIEW
by
RachidHamadi
Student ID: 30099999
ASSIGNMENT 2 – LITERATURE REVIEW
by
RachidHamadi
Student ID: 30099999
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Table of Contents.................................................................................................................................ii
List of Figures.....................................................................................................................................iii
List of Tables.......................................................................................................................................iv
1.1 Broad Scan.................................................................................................................................1
1.1.1 Research Journal..................................................................................................................1
1.1.2 Filing System.......................................................................................................................1
1.1.3 Bibliographic file from broad scan......................................................................................1
1.2 Focused Review.........................................................................................................................2
1.2.1 Updated filing system..........................................................................................................2
1.2.2 Updated bibliographic file from focused review.................................................................2
1.3 Selected Paper1..........................................................................................................................2
1.3.1 Problem Definition..............................................................................................................3
1.3.2 Running Example................................................................................................................3
1.3.3 Overview of the Proposed System......................................................................................3
1.3.4 System Architecture............................................................................................................3
1.3.4.1 Module1........................................................................................................................3
1.3.4.2 Module2........................................................................................................................3
1.3.4.3 Module3........................................................................................................................3
1.4 Selected Paper2..........................................................................................................................3
1.4.1 Architecture of the solution.................................................................................................4
1.4.2 Experiments.........................................................................................................................4
1.4.3 Results.................................................................................................................................4
1.4.4 Discussion...........................................................................................................................4
1.5 Final Outline of the Literature review Chapter..........................................................................4
1.6 Introduction................................................................................................................................5
List of References.................................................................................................................................6
ii
Table of Contents.................................................................................................................................ii
List of Figures.....................................................................................................................................iii
List of Tables.......................................................................................................................................iv
1.1 Broad Scan.................................................................................................................................1
1.1.1 Research Journal..................................................................................................................1
1.1.2 Filing System.......................................................................................................................1
1.1.3 Bibliographic file from broad scan......................................................................................1
1.2 Focused Review.........................................................................................................................2
1.2.1 Updated filing system..........................................................................................................2
1.2.2 Updated bibliographic file from focused review.................................................................2
1.3 Selected Paper1..........................................................................................................................2
1.3.1 Problem Definition..............................................................................................................3
1.3.2 Running Example................................................................................................................3
1.3.3 Overview of the Proposed System......................................................................................3
1.3.4 System Architecture............................................................................................................3
1.3.4.1 Module1........................................................................................................................3
1.3.4.2 Module2........................................................................................................................3
1.3.4.3 Module3........................................................................................................................3
1.4 Selected Paper2..........................................................................................................................3
1.4.1 Architecture of the solution.................................................................................................4
1.4.2 Experiments.........................................................................................................................4
1.4.3 Results.................................................................................................................................4
1.4.4 Discussion...........................................................................................................................4
1.5 Final Outline of the Literature review Chapter..........................................................................4
1.6 Introduction................................................................................................................................5
List of References.................................................................................................................................6
ii

List of Figures
ARCHITECTURE OF THE SOLUTION
iii
ARCHITECTURE OF THE SOLUTION
iii

List of Tables
1.1.1 Research Journal
1.1.2 Filing System
1.1.3 Bibliographic file from broad scan
1.1.4 Research Journal
1.1.5 Filing System
1.1.6 Updated filing system
iv
1.1.1 Research Journal
1.1.2 Filing System
1.1.3 Bibliographic file from broad scan
1.1.4 Research Journal
1.1.5 Filing System
1.1.6 Updated filing system
iv
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

The following chapter is going to illustrate the concept of persuasive technology and
communication for human well-being. The literature review is going to discuss effective
understanding of the cases that has been taken into certain consideration pertaining to the
effective case so as to find out how this would become one of the most impactful nature with
the entire understanding of the case. In fact, this has been taken into certain understanding
pertaining to the effective case to find out how effective this is going to be to find out the basic
knowledge system within the research work. The following paper is going to discuss different
procedures of writing a literature review through extensive research methods. In fact, this has
been taken into certain consideration pertaining to different steps to conduct an effective
literature review in the process. There are different bibliographical considerations that would
finally focus on the expressive self of the actual case.
1.1 Broad Scan
I have elected my topic of interest in broad scan. In order to do so, I have searched in the
internet for the key words. different platforms have been used to search on the topics. These
are:
i) Google Scholar
ii) IEEE
iii) VU Library
There were numbers of papers- mostly scholarly works. Those journals have been read
through touch stoner method. From the scholarly works, I have selected more than twenty-
five works. This has to be taken into certain consideration pertaining to the effective
understanding of the process. In fact, this has been taken into certain understanding of the
exact case pertaining to the effective understanding of the process. After finding the
papers, I shortlisted twenty-five contextual and relevant works.
1
communication for human well-being. The literature review is going to discuss effective
understanding of the cases that has been taken into certain consideration pertaining to the
effective case so as to find out how this would become one of the most impactful nature with
the entire understanding of the case. In fact, this has been taken into certain understanding
pertaining to the effective case to find out how effective this is going to be to find out the basic
knowledge system within the research work. The following paper is going to discuss different
procedures of writing a literature review through extensive research methods. In fact, this has
been taken into certain consideration pertaining to different steps to conduct an effective
literature review in the process. There are different bibliographical considerations that would
finally focus on the expressive self of the actual case.
1.1 Broad Scan
I have elected my topic of interest in broad scan. In order to do so, I have searched in the
internet for the key words. different platforms have been used to search on the topics. These
are:
i) Google Scholar
ii) IEEE
iii) VU Library
There were numbers of papers- mostly scholarly works. Those journals have been read
through touch stoner method. From the scholarly works, I have selected more than twenty-
five works. This has to be taken into certain consideration pertaining to the effective
understanding of the process. In fact, this has been taken into certain understanding of the
exact case pertaining to the effective understanding of the process. After finding the
papers, I shortlisted twenty-five contextual and relevant works.
1
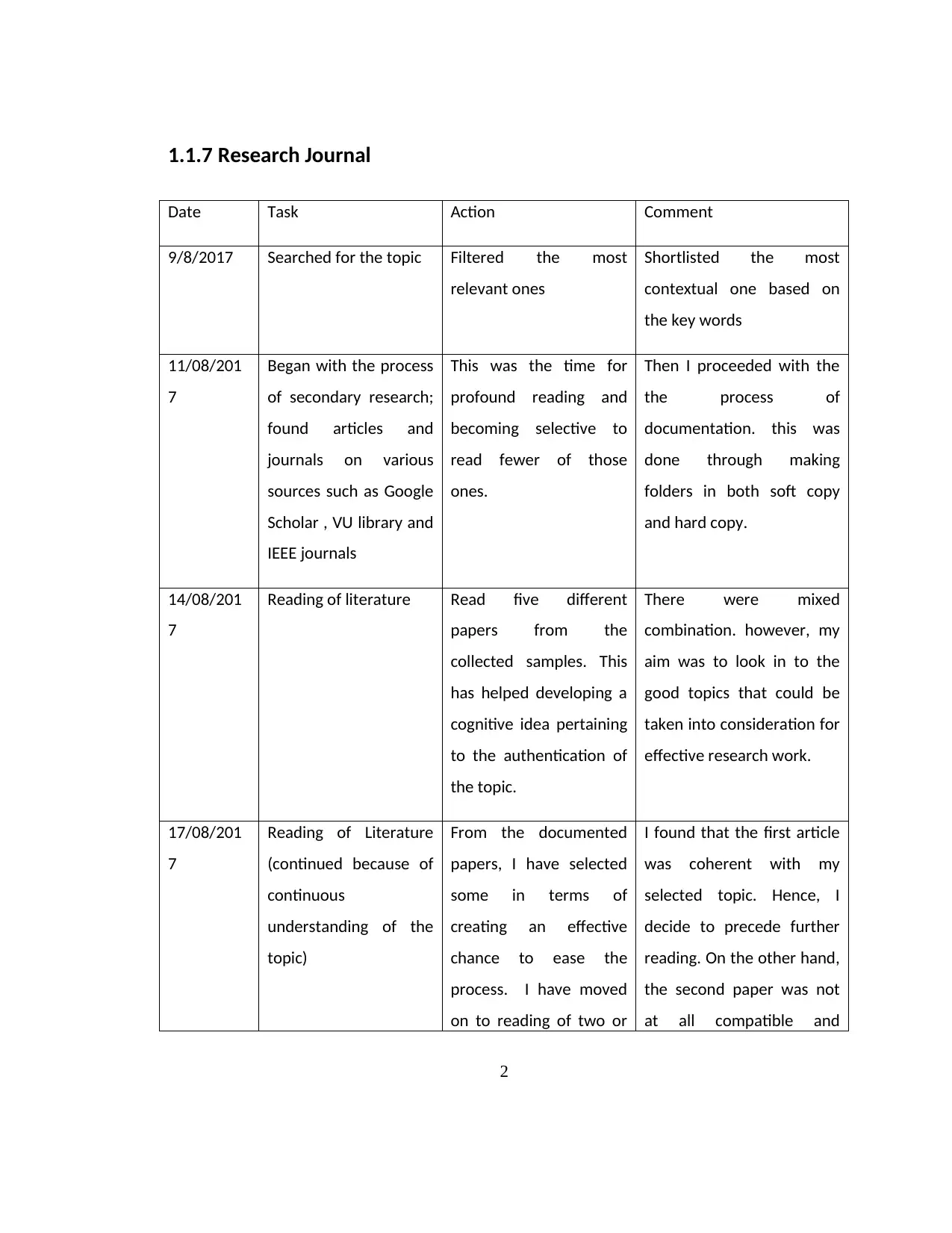
1.1.7 Research Journal
Date Task Action Comment
9/8/2017 Searched for the topic Filtered the most
relevant ones
Shortlisted the most
contextual one based on
the key words
11/08/201
7
Began with the process
of secondary research;
found articles and
journals on various
sources such as Google
Scholar , VU library and
IEEE journals
This was the time for
profound reading and
becoming selective to
read fewer of those
ones.
Then I proceeded with the
the process of
documentation. this was
done through making
folders in both soft copy
and hard copy.
14/08/201
7
Reading of literature Read five different
papers from the
collected samples. This
has helped developing a
cognitive idea pertaining
to the authentication of
the topic.
There were mixed
combination. however, my
aim was to look in to the
good topics that could be
taken into consideration for
effective research work.
17/08/201
7
Reading of Literature
(continued because of
continuous
understanding of the
topic)
From the documented
papers, I have selected
some in terms of
creating an effective
chance to ease the
process. I have moved
on to reading of two or
I found that the first article
was coherent with my
selected topic. Hence, I
decide to precede further
reading. On the other hand,
the second paper was not
at all compatible and
2
Date Task Action Comment
9/8/2017 Searched for the topic Filtered the most
relevant ones
Shortlisted the most
contextual one based on
the key words
11/08/201
7
Began with the process
of secondary research;
found articles and
journals on various
sources such as Google
Scholar , VU library and
IEEE journals
This was the time for
profound reading and
becoming selective to
read fewer of those
ones.
Then I proceeded with the
the process of
documentation. this was
done through making
folders in both soft copy
and hard copy.
14/08/201
7
Reading of literature Read five different
papers from the
collected samples. This
has helped developing a
cognitive idea pertaining
to the authentication of
the topic.
There were mixed
combination. however, my
aim was to look in to the
good topics that could be
taken into consideration for
effective research work.
17/08/201
7
Reading of Literature
(continued because of
continuous
understanding of the
topic)
From the documented
papers, I have selected
some in terms of
creating an effective
chance to ease the
process. I have moved
on to reading of two or
I found that the first article
was coherent with my
selected topic. Hence, I
decide to precede further
reading. On the other hand,
the second paper was not
at all compatible and
2
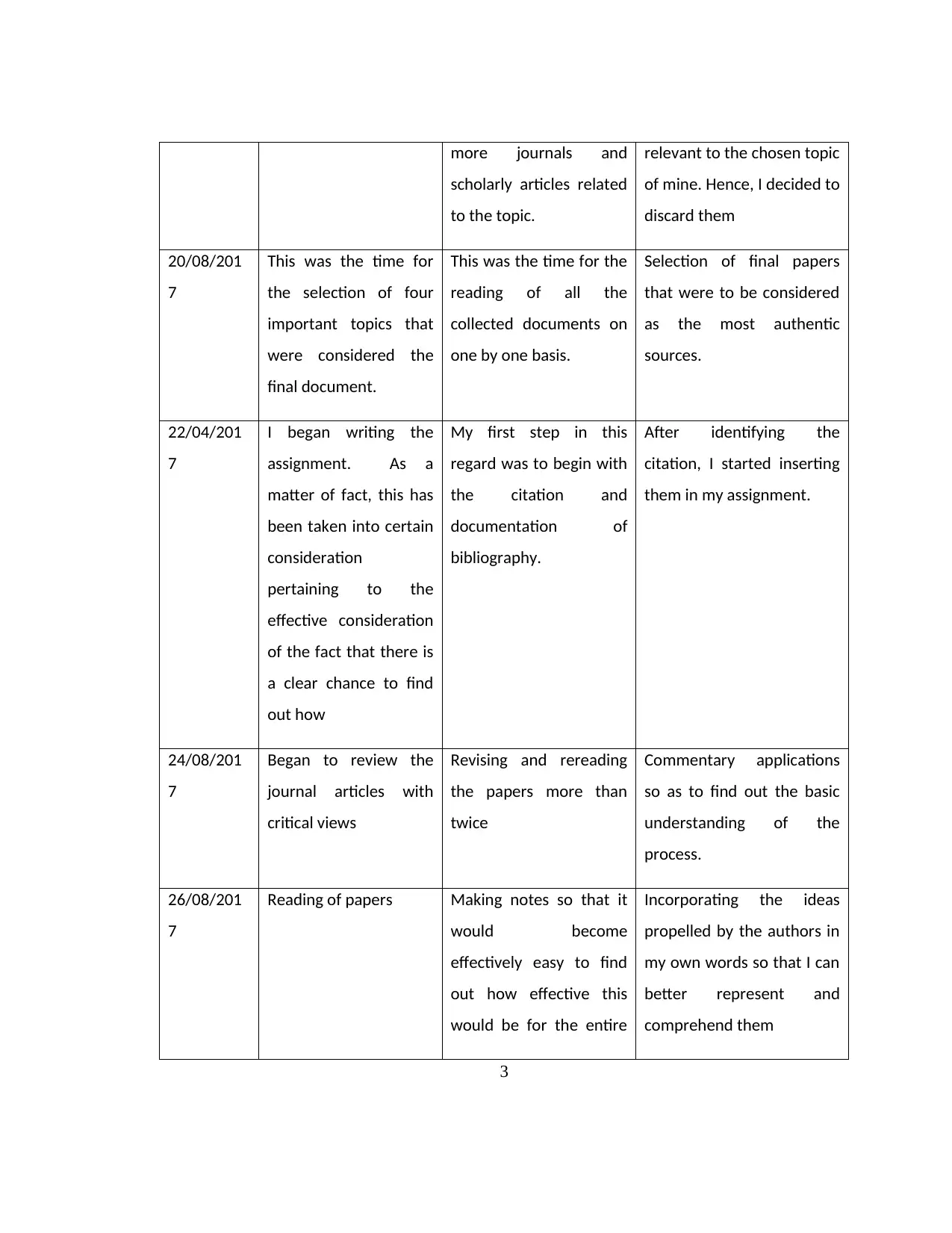
more journals and
scholarly articles related
to the topic.
relevant to the chosen topic
of mine. Hence, I decided to
discard them
20/08/201
7
This was the time for
the selection of four
important topics that
were considered the
final document.
This was the time for the
reading of all the
collected documents on
one by one basis.
Selection of final papers
that were to be considered
as the most authentic
sources.
22/04/201
7
I began writing the
assignment. As a
matter of fact, this has
been taken into certain
consideration
pertaining to the
effective consideration
of the fact that there is
a clear chance to find
out how
My first step in this
regard was to begin with
the citation and
documentation of
bibliography.
After identifying the
citation, I started inserting
them in my assignment.
24/08/201
7
Began to review the
journal articles with
critical views
Revising and rereading
the papers more than
twice
Commentary applications
so as to find out the basic
understanding of the
process.
26/08/201
7
Reading of papers Making notes so that it
would become
effectively easy to find
out how effective this
would be for the entire
Incorporating the ideas
propelled by the authors in
my own words so that I can
better represent and
comprehend them
3
scholarly articles related
to the topic.
relevant to the chosen topic
of mine. Hence, I decided to
discard them
20/08/201
7
This was the time for
the selection of four
important topics that
were considered the
final document.
This was the time for the
reading of all the
collected documents on
one by one basis.
Selection of final papers
that were to be considered
as the most authentic
sources.
22/04/201
7
I began writing the
assignment. As a
matter of fact, this has
been taken into certain
consideration
pertaining to the
effective consideration
of the fact that there is
a clear chance to find
out how
My first step in this
regard was to begin with
the citation and
documentation of
bibliography.
After identifying the
citation, I started inserting
them in my assignment.
24/08/201
7
Began to review the
journal articles with
critical views
Revising and rereading
the papers more than
twice
Commentary applications
so as to find out the basic
understanding of the
process.
26/08/201
7
Reading of papers Making notes so that it
would become
effectively easy to find
out how effective this
would be for the entire
Incorporating the ideas
propelled by the authors in
my own words so that I can
better represent and
comprehend them
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
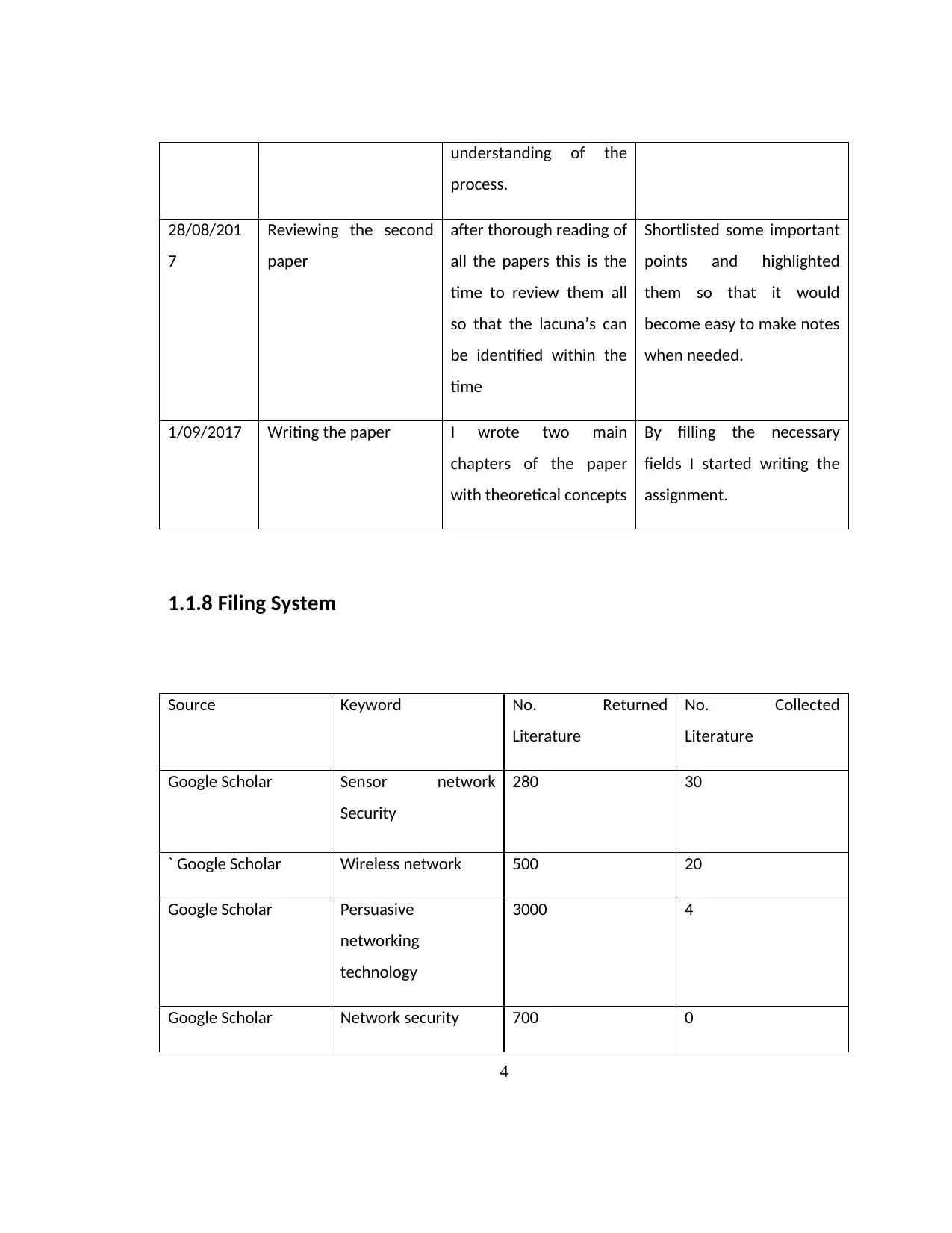
understanding of the
process.
28/08/201
7
Reviewing the second
paper
after thorough reading of
all the papers this is the
time to review them all
so that the lacuna’s can
be identified within the
time
Shortlisted some important
points and highlighted
them so that it would
become easy to make notes
when needed.
1/09/2017 Writing the paper I wrote two main
chapters of the paper
with theoretical concepts
By filling the necessary
fields I started writing the
assignment.
1.1.8 Filing System
Source Keyword No. Returned
Literature
No. Collected
Literature
Google Scholar Sensor network
Security
280 30
` Google Scholar Wireless network 500 20
Google Scholar Persuasive
networking
technology
3000 4
Google Scholar Network security 700 0
4
process.
28/08/201
7
Reviewing the second
paper
after thorough reading of
all the papers this is the
time to review them all
so that the lacuna’s can
be identified within the
time
Shortlisted some important
points and highlighted
them so that it would
become easy to make notes
when needed.
1/09/2017 Writing the paper I wrote two main
chapters of the paper
with theoretical concepts
By filling the necessary
fields I started writing the
assignment.
1.1.8 Filing System
Source Keyword No. Returned
Literature
No. Collected
Literature
Google Scholar Sensor network
Security
280 30
` Google Scholar Wireless network 500 20
Google Scholar Persuasive
networking
technology
3000 4
Google Scholar Network security 700 0
4
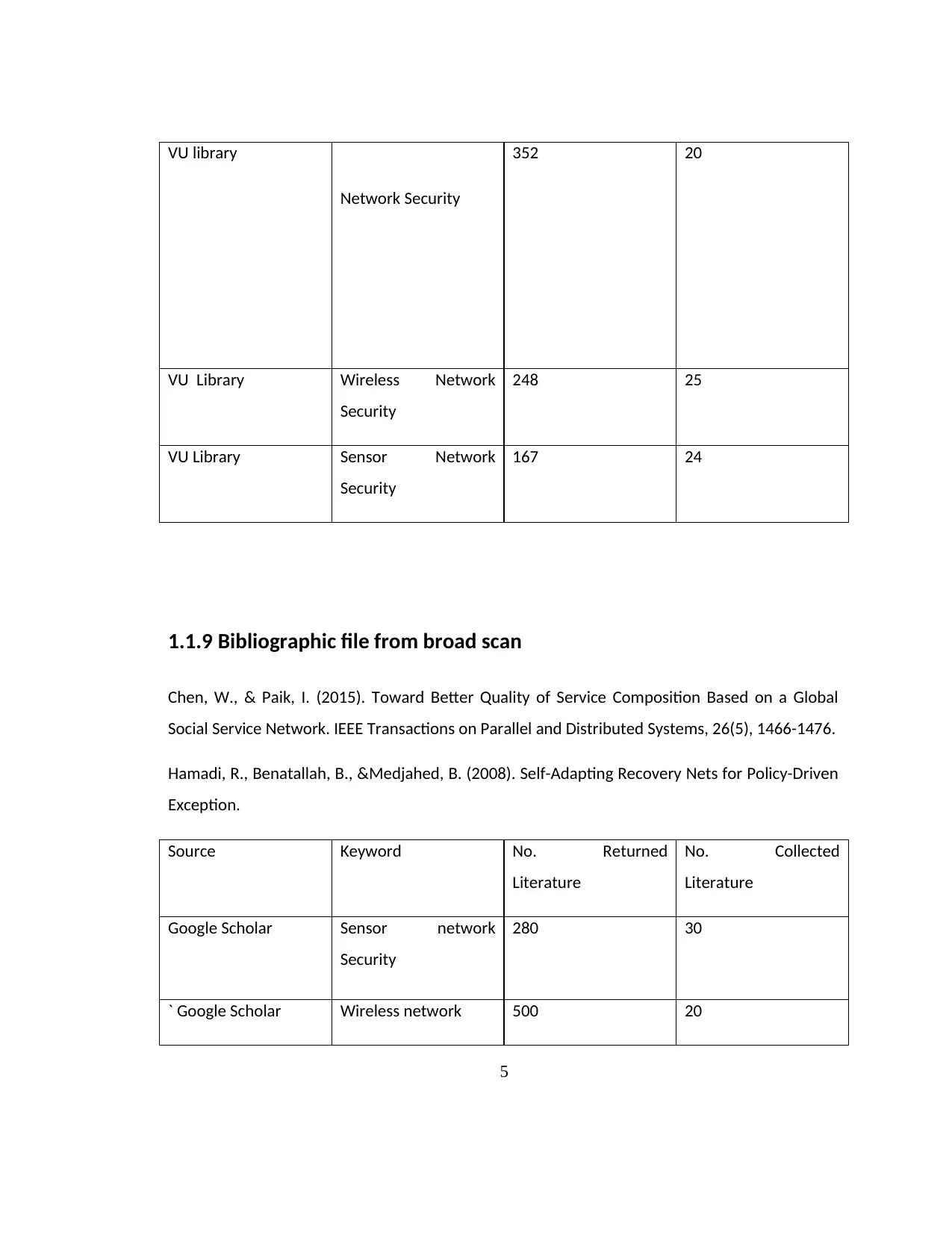
VU library
Network Security
352 20
VU Library Wireless Network
Security
248 25
VU Library Sensor Network
Security
167 24
1.1.9 Bibliographic file from broad scan
Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a Global
Social Service Network. IEEE Transactions on Parallel and Distributed Systems, 26(5), 1466-1476.
Hamadi, R., Benatallah, B., &Medjahed, B. (2008). Self-Adapting Recovery Nets for Policy-Driven
Exception.
Source Keyword No. Returned
Literature
No. Collected
Literature
Google Scholar Sensor network
Security
280 30
` Google Scholar Wireless network 500 20
5
Network Security
352 20
VU Library Wireless Network
Security
248 25
VU Library Sensor Network
Security
167 24
1.1.9 Bibliographic file from broad scan
Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a Global
Social Service Network. IEEE Transactions on Parallel and Distributed Systems, 26(5), 1466-1476.
Hamadi, R., Benatallah, B., &Medjahed, B. (2008). Self-Adapting Recovery Nets for Policy-Driven
Exception.
Source Keyword No. Returned
Literature
No. Collected
Literature
Google Scholar Sensor network
Security
280 30
` Google Scholar Wireless network 500 20
5
Google Scholar Persuasive
networking
technology
3000 4
Google Scholar Network security 700 0
VU library
Network Security
352 20
VU Library Wireless Network
Security
248 25
VU Library Sensor Network
Security
167 24
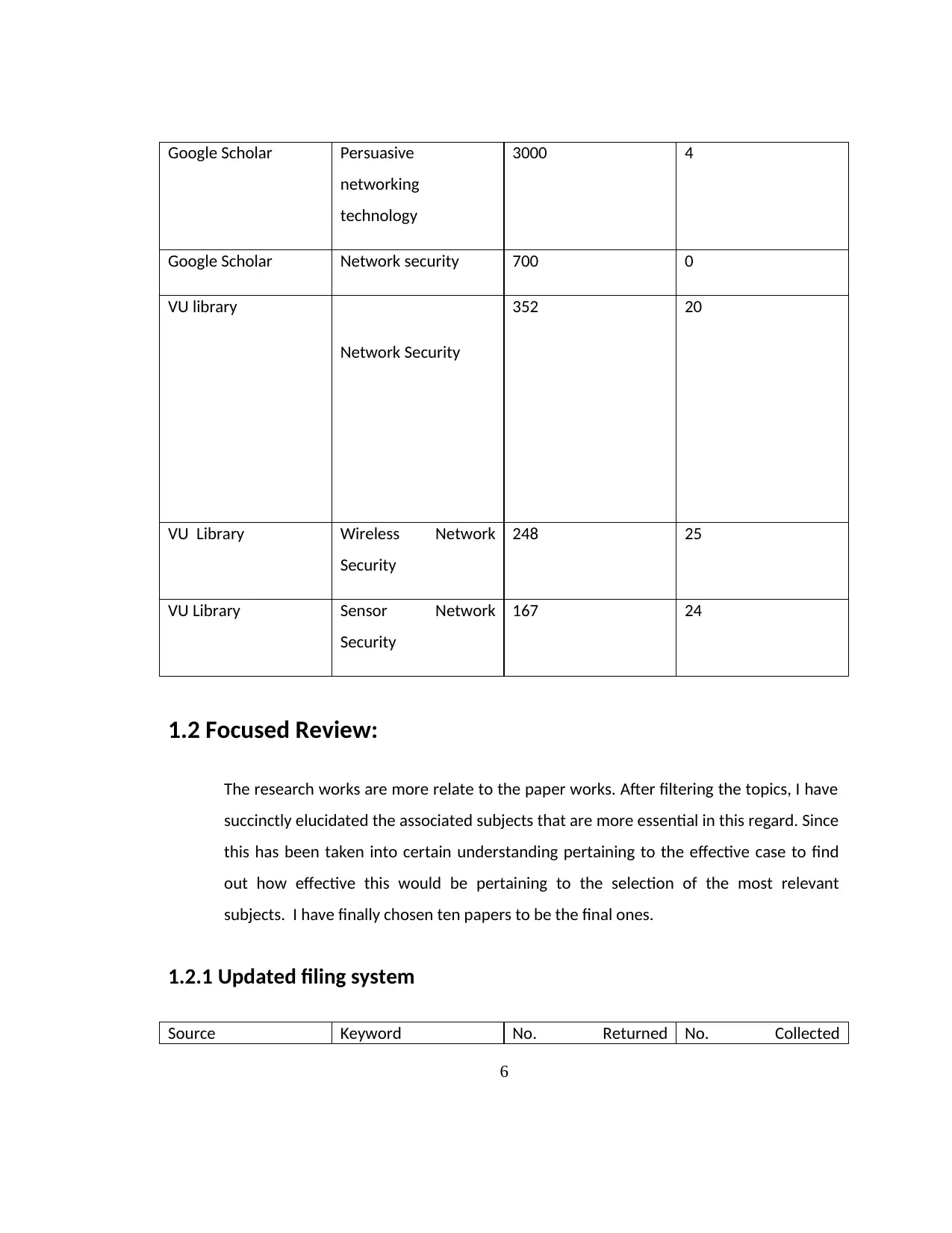
1.2 Focused Review:
The research works are more relate to the paper works. After filtering the topics, I have
succinctly elucidated the associated subjects that are more essential in this regard. Since
this has been taken into certain understanding pertaining to the effective case to find
out how effective this would be pertaining to the selection of the most relevant
subjects. I have finally chosen ten papers to be the final ones.
1.2.1 Updated filing system
Source Keyword No. Returned No. Collected
6
networking
technology
3000 4
Google Scholar Network security 700 0
VU library
Network Security
352 20
VU Library Wireless Network
Security
248 25
VU Library Sensor Network
Security
167 24
1.2 Focused Review:
The research works are more relate to the paper works. After filtering the topics, I have
succinctly elucidated the associated subjects that are more essential in this regard. Since
this has been taken into certain understanding pertaining to the effective case to find
out how effective this would be pertaining to the selection of the most relevant
subjects. I have finally chosen ten papers to be the final ones.
1.2.1 Updated filing system
Source Keyword No. Returned No. Collected
6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Literature Literature
Google Scholar Sensor network
Security
280 30
` Google Scholar Wireless network 500 20
Google Scholar Persuasive
networking
technology
3000 4
Google Scholar Network security 700 0
VU library
Network Security
352 20
VU Library Wireless Network
Security
248 25
VU Library Sensor Network
Security
167 24
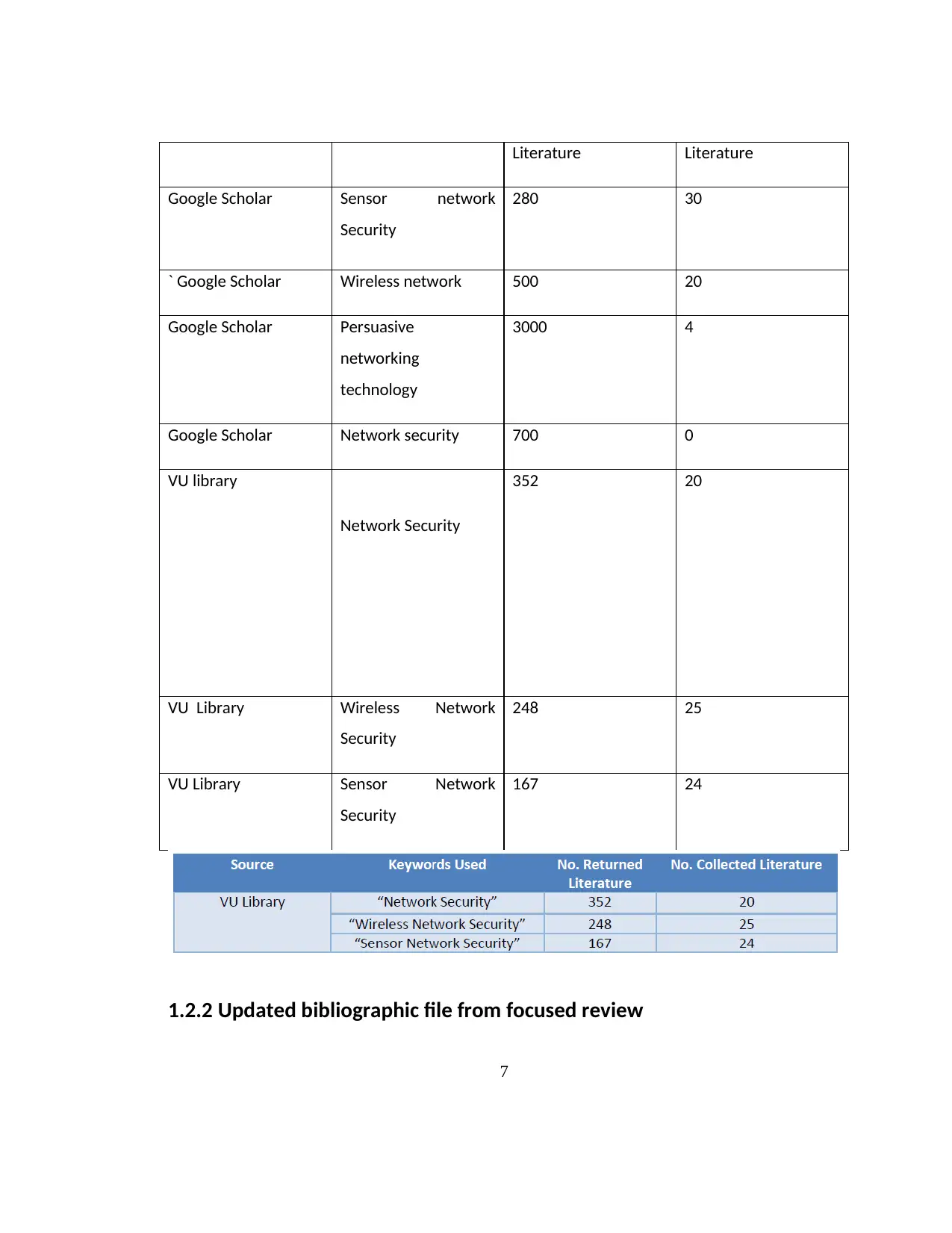
1.2.2 Updated bibliographic file from focused review
7
Google Scholar Sensor network
Security
280 30
` Google Scholar Wireless network 500 20
Google Scholar Persuasive
networking
technology
3000 4
Google Scholar Network security 700 0
VU library
Network Security
352 20
VU Library Wireless Network
Security
248 25
VU Library Sensor Network
Security
167 24
1.2.2 Updated bibliographic file from focused review
7

Chen, W., & Paik, I. (2015). Toward Better Quality of Service Composition Based on a Global
Social Service Network. IEEE Transactions on Parallel and Distributed Systems, 26(5),
1466-1476.
Hamadi, R., Benatallah, B., & Medjahed, B. (2008). Self-Adapting Recovery Nets for Policy-
Driven Exception Handling in Business Processes. Distributed and Parallel Databases,
1-44.
Holzinger, A., Schantl, J., Schroettner, M., Seifert, C., & Verspoor, K. (2014). Biomedical text
mining: state-of-the-art, open problems and future challenges. Interactive Knowledge
Discovery and Data Mining in Biomedical Informatics (pp. 271-300). Springer Berlin
Heidelberg.
1.3 Selected Paper1
In this section, the approch of Hamadi et al. (2008). is that SARN is one of the most
significant and extended PETRI net model that is used to specify exceptional behavior in the
external and internal business process. The authors have also proposed the framework of SARN
(Self-adapting recovery net) with the effective understanding of the business process. It does
not only encompass the “Recovery Region” regarding particular implementation and adherence
to the policy frameworks, but also focuses on the effective understanding of the process. They
have also talked about the recovery processes of lost data.
1.3.1 Problem Definition
The actual problem statement pertains to the business process with the effective
understanding of the actual case. This is universally granted that technology plays quite
significant role in the overall business development of an organization. Technological
understanding by the business personae and the eligibility to implement those are highly
important for the acceleration of the business pace. In this context, it can be stated that there is
a clear usage of technology and its intervention in terms of creating a proper and constructive
8
Social Service Network. IEEE Transactions on Parallel and Distributed Systems, 26(5),
1466-1476.
Hamadi, R., Benatallah, B., & Medjahed, B. (2008). Self-Adapting Recovery Nets for Policy-
Driven Exception Handling in Business Processes. Distributed and Parallel Databases,
1-44.
Holzinger, A., Schantl, J., Schroettner, M., Seifert, C., & Verspoor, K. (2014). Biomedical text
mining: state-of-the-art, open problems and future challenges. Interactive Knowledge
Discovery and Data Mining in Biomedical Informatics (pp. 271-300). Springer Berlin
Heidelberg.
1.3 Selected Paper1
In this section, the approch of Hamadi et al. (2008). is that SARN is one of the most
significant and extended PETRI net model that is used to specify exceptional behavior in the
external and internal business process. The authors have also proposed the framework of SARN
(Self-adapting recovery net) with the effective understanding of the business process. It does
not only encompass the “Recovery Region” regarding particular implementation and adherence
to the policy frameworks, but also focuses on the effective understanding of the process. They
have also talked about the recovery processes of lost data.
1.3.1 Problem Definition
The actual problem statement pertains to the business process with the effective
understanding of the actual case. This is universally granted that technology plays quite
significant role in the overall business development of an organization. Technological
understanding by the business personae and the eligibility to implement those are highly
important for the acceleration of the business pace. In this context, it can be stated that there is
a clear usage of technology and its intervention in terms of creating a proper and constructive
8

environment has been taken into certain considerate so that this would finally uphold the basic
needs of the business.
1.3.2 Running Example
The paper has been developed through exemplary usage of technological interpretation
with its business association. Since this has been taken into certain consideration pertaining to
the effective understanding of the process that looks into overall business development process.
1.3.3 Overview of the Proposed System
The proposed literature links to the effective understanding of the technological
advancement. Since this has been taken into certain understanding of the process, there is a
clear chance to find out how effective this is pertaining to the basic understanding of the case.
This is how there is a clear chance to find out how effective this would for the entire
understanding of the process.
1.3.4 System Architecture
1.3.4.1 Module1: Problem Statement
1.3.4.2 Module2: Business and Technology- relational aspect
1.3.4.3 Module3: Technological intervention in Business Process
9
needs of the business.
1.3.2 Running Example
The paper has been developed through exemplary usage of technological interpretation
with its business association. Since this has been taken into certain consideration pertaining to
the effective understanding of the process that looks into overall business development process.
1.3.3 Overview of the Proposed System
The proposed literature links to the effective understanding of the technological
advancement. Since this has been taken into certain understanding of the process, there is a
clear chance to find out how effective this is pertaining to the basic understanding of the case.
This is how there is a clear chance to find out how effective this would for the entire
understanding of the process.
1.3.4 System Architecture
1.3.4.1 Module1: Problem Statement
1.3.4.2 Module2: Business and Technology- relational aspect
1.3.4.3 Module3: Technological intervention in Business Process
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.4 Selected Paper 2
Another interesting solution for the investigated problem is the QWERTY framework (Holzinger,
Schantl, Schroettner, Seifert, & Verspoor, 2014).
1.4.1 Architecture of the solution:
1.4.2 Experiments
All the experiments have been done on the basis of the research conducted from
different scholarly literatures. Eventually this has been taken into certain consideration
pertaining to the fact that this would focus on the effective consideration o the cases.
10
Conclusion
Another interesting solution for the investigated problem is the QWERTY framework (Holzinger,
Schantl, Schroettner, Seifert, & Verspoor, 2014).
1.4.1 Architecture of the solution:
1.4.2 Experiments
All the experiments have been done on the basis of the research conducted from
different scholarly literatures. Eventually this has been taken into certain consideration
pertaining to the fact that this would focus on the effective consideration o the cases.
10
Conclusion

1.4.3 Results
The outcome of the secondary research has been the development of cognitive ideas
pertaining to the core topic discussed above.
1.4.4 Discussion
The introduction was written on a broad to narrow technique. This would somehow
focus on the actual understanding of the process pertaining to the effective nature of
such interest. Since this has been taken into certain consideration of the issues
pertaining to constant development of the research method. it further moves on to
discussing how effective this would be for the actual understanding of the process in
terms of creating broader scope.
1.5 Final Outline of the Literature review Chapter
1. Introduction
2. Selected Paper1
2.1
2.2
3. Selected Paper2
3.1
3.2
4. Put other papers to be reviewed here even though they have not been reviewed above
(optional)
5. Discussion
11
The outcome of the secondary research has been the development of cognitive ideas
pertaining to the core topic discussed above.
1.4.4 Discussion
The introduction was written on a broad to narrow technique. This would somehow
focus on the actual understanding of the process pertaining to the effective nature of
such interest. Since this has been taken into certain consideration of the issues
pertaining to constant development of the research method. it further moves on to
discussing how effective this would be for the actual understanding of the process in
terms of creating broader scope.
1.5 Final Outline of the Literature review Chapter
1. Introduction
2. Selected Paper1
2.1
2.2
3. Selected Paper2
3.1
3.2
4. Put other papers to be reviewed here even though they have not been reviewed above
(optional)
5. Discussion
11

6. Conclusion
12
12
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





