NIT6130: Literature Review on Cost Optimization in Cloud Computing
VerifiedAdded on 2024/04/25
|19
|3929
|165
Literature Review
AI Summary
This document presents a literature review focused on cloud computing, starting with a broad scan of research papers and culminating in a focused analysis of key articles. The review covers topics such as cloud computing vulnerabilities, forensic investigation approaches using VM snapshots, and the application of inventory theory for cost optimization. It details the process of selecting and analyzing relevant papers, updating bibliographic files, and developing a final outline for the literature review chapter. The review explores the background of cloud computing, its service models, and the challenges associated with its adoption, including data security, privacy, and cost structure. The document also discusses the potential of inventory theory to optimize costs in cloud computing environments, highlighting its value deliverables and expected outcomes. This assignment examines the role of cloud computing in IT, emphasizing its importance for both individuals and organizations seeking efficient information access, storage, and sharing solutions.

NIT6130 INTRODUCTION TO RESEARCH
ASSIGNMENT 2 – LITERATURE REVIEW
ASSIGNMENT 2 – LITERATURE REVIEW
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Table of Contents...............................................................................................................................ii
List of Figures...................................................................................................................................iii
List of Tables....................................................................................................................................iv
1.1 Broad Scan...............................................................................................................................1
1.1.1 Research Journal................................................................................................................1
1.1.2 Filing System.....................................................................................................................3
1.1.3 Bibliographic file from broad scan....................................................................................4
1.2 Focused Review.......................................................................................................................6
1.2.1 Updated filing system........................................................................................................6
1.2.2 Updated bibliographic file from focused review................................................................7
1.3 Cloud Computing.....................................................................................................................8
1.3.1 Background.......................................................................................................................9
1.3.2 Framework and Method.....................................................................................................9
1.3.3 Overview of the Proposed System.....................................................................................9
1.3.4 Discussion.......................................................................................................................10
1.4 Theory based on inventory applied to cost optimization in Cloud Computing.......................11
1.4.1 What is theory related to inventory and should be applied in organisation to Cost
Optimization in Cloud Computing?..........................................................................................11
1.4.2 Functioning of Inventory Theory Model.........................................................................11
1.4.3 Value Deliverables..........................................................................................................12
1.4.4 Outcome..........................................................................................................................12
1.4.5 Conclusion.......................................................................................................................13
1.5 Final Outline of the Literature review Chapter.......................................................................13
1.6 Introduction............................................................................................................................14
List of References............................................................................................................................15
ii
Table of Contents...............................................................................................................................ii
List of Figures...................................................................................................................................iii
List of Tables....................................................................................................................................iv
1.1 Broad Scan...............................................................................................................................1
1.1.1 Research Journal................................................................................................................1
1.1.2 Filing System.....................................................................................................................3
1.1.3 Bibliographic file from broad scan....................................................................................4
1.2 Focused Review.......................................................................................................................6
1.2.1 Updated filing system........................................................................................................6
1.2.2 Updated bibliographic file from focused review................................................................7
1.3 Cloud Computing.....................................................................................................................8
1.3.1 Background.......................................................................................................................9
1.3.2 Framework and Method.....................................................................................................9
1.3.3 Overview of the Proposed System.....................................................................................9
1.3.4 Discussion.......................................................................................................................10
1.4 Theory based on inventory applied to cost optimization in Cloud Computing.......................11
1.4.1 What is theory related to inventory and should be applied in organisation to Cost
Optimization in Cloud Computing?..........................................................................................11
1.4.2 Functioning of Inventory Theory Model.........................................................................11
1.4.3 Value Deliverables..........................................................................................................12
1.4.4 Outcome..........................................................................................................................12
1.4.5 Conclusion.......................................................................................................................13
1.5 Final Outline of the Literature review Chapter.......................................................................13
1.6 Introduction............................................................................................................................14
List of References............................................................................................................................15
ii

List of Figures
Figure 1: Global Spending Forecast....................................................................................10
iii
Figure 1: Global Spending Forecast....................................................................................10
iii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

List of Tables
Table 1: Research Journal Tasks...........................................................................................1
Table 2: Table of Filling System.............................................................................................3
Table 3: Updated Filling System............................................................................................7
iv
Table 1: Research Journal Tasks...........................................................................................1
Table 2: Table of Filling System.............................................................................................3
Table 3: Updated Filling System............................................................................................7
iv
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CHAPTER 1
LITERATURE REVIEW
In the present assignment, literature review is to be written on the topic “Cloud
Computing”. I am analysing and investigating the two papers which depends on cloud
computing. I am selecting two diversified papers, first one is demonstrating the
vulnerabilities which are related to Cloud Computing. In the second paper, I am
evaluating the efficient approach which is related to the forensic investigation in Cloud
Computing by adopting VM snapshots and this is more reliable. This literature review is
starting from the beginning and it includes some steps which they have to follow:
Segment 1.1 is identified with expansive sweep and in this, I talk about my exploration
papers, a gathering of research articles and in addition a list of sources of all papers. Area
1.2 is relying upon the engaged output and in this, I channel my exploration and discover
more papers which are significant with the subject. At that point, after this, I again
refreshed the book index. Area 1.3 and 1.4 depend on writing Review where I chose and
broke down the two papers. Area 1.5 gives the layout of the section which is identified
with Literature Review. Last, Section 1.6 is the Introduction of my point.
1.1 Broad Scan
In Broad Scan I have chosen my theme by doing research on the Internet by utilizing
enhanced catchphrases. I sought point on the distinctive stage, for example, VU library,
IEEE and also Google Scholar. I discovered such a large number of papers and select
twenty-five from them for the following level.
1.1.1 Research Journal
Table 1: Research Journal Tasks
Date Task Action Comment
15/01/2018 Topic search Choose appropriate Selected one topic
1
LITERATURE REVIEW
In the present assignment, literature review is to be written on the topic “Cloud
Computing”. I am analysing and investigating the two papers which depends on cloud
computing. I am selecting two diversified papers, first one is demonstrating the
vulnerabilities which are related to Cloud Computing. In the second paper, I am
evaluating the efficient approach which is related to the forensic investigation in Cloud
Computing by adopting VM snapshots and this is more reliable. This literature review is
starting from the beginning and it includes some steps which they have to follow:
Segment 1.1 is identified with expansive sweep and in this, I talk about my exploration
papers, a gathering of research articles and in addition a list of sources of all papers. Area
1.2 is relying upon the engaged output and in this, I channel my exploration and discover
more papers which are significant with the subject. At that point, after this, I again
refreshed the book index. Area 1.3 and 1.4 depend on writing Review where I chose and
broke down the two papers. Area 1.5 gives the layout of the section which is identified
with Literature Review. Last, Section 1.6 is the Introduction of my point.
1.1 Broad Scan
In Broad Scan I have chosen my theme by doing research on the Internet by utilizing
enhanced catchphrases. I sought point on the distinctive stage, for example, VU library,
IEEE and also Google Scholar. I discovered such a large number of papers and select
twenty-five from them for the following level.
1.1.1 Research Journal
Table 1: Research Journal Tasks
Date Task Action Comment
15/01/2018 Topic search Choose appropriate Selected one topic
1
topic
16/01/2018 Identify papers on
the different
sources which
include IEEE, VU
Library and etc.
Read those papers
and save some of
them.
Make a folder and
save the work
which is related to
that topic.
18/01/2018 Literature Review After collection of
paper, read them.
Found best topic to
do research.
20/01/2018 Literature Review Read another two
more papers
Not properly
relevant to the
research. Discard
them.
23/01/2018 4 final documents
should select
All papers should
read in a proper
manner.
Select two for the
final examination.
24/01/2018 Start Assignment Started citations
related to topic
Insert the citations.
25/01/2018 Start assignment
from reviewing first
paper.
Read all the papers. Put some comments
in LR section.
27/01/2018 Reading of paper Prepare notes
related to the topic.
Put them into our
own words.
28/01/2018 Analyse and
examine of second
paper
Read all the papers. Picked some
important work and
analyse them.
1/02/2018 Analysing and
written down some
articles
Some data written
down from the two
articles.
Fill all fields and
prepare assignment.
2
16/01/2018 Identify papers on
the different
sources which
include IEEE, VU
Library and etc.
Read those papers
and save some of
them.
Make a folder and
save the work
which is related to
that topic.
18/01/2018 Literature Review After collection of
paper, read them.
Found best topic to
do research.
20/01/2018 Literature Review Read another two
more papers
Not properly
relevant to the
research. Discard
them.
23/01/2018 4 final documents
should select
All papers should
read in a proper
manner.
Select two for the
final examination.
24/01/2018 Start Assignment Started citations
related to topic
Insert the citations.
25/01/2018 Start assignment
from reviewing first
paper.
Read all the papers. Put some comments
in LR section.
27/01/2018 Reading of paper Prepare notes
related to the topic.
Put them into our
own words.
28/01/2018 Analyse and
examine of second
paper
Read all the papers. Picked some
important work and
analyse them.
1/02/2018 Analysing and
written down some
articles
Some data written
down from the two
articles.
Fill all fields and
prepare assignment.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1.1.2 Filing System
Table 2: Table of Filling System
Source Keyword use No. of returned
Literature
No. of Collected
Literature
Scholar Cloud Computing
Use of Cloud
Computing
1000
2000
5
6
VU Library Cloud Computing
Appropriate
strategies and
theories
6000
500
4
5
IEEE Theories based on
inventory and that
should be applied
on cost optimization
in the cloud
computing
3000 5
1.1.3 Bibliographic file from broad scan
Jiang, Q., Feng, W., Peng, J., Han, F., Li, Q., Zhang, W and Su, H. (2012). Inventory -
Based Resource Management in Cloud Computing. IEEE Xplore.
Gupta, K., Beri, R and Behal, V. (2016). Cloud Computing: A survey on Cloud
Simulation Tools. International Journal for Innovative Research in Science and
Technology. Vol. 2, Issue 11.
3
Table 2: Table of Filling System
Source Keyword use No. of returned
Literature
No. of Collected
Literature
Scholar Cloud Computing
Use of Cloud
Computing
1000
2000
5
6
VU Library Cloud Computing
Appropriate
strategies and
theories
6000
500
4
5
IEEE Theories based on
inventory and that
should be applied
on cost optimization
in the cloud
computing
3000 5
1.1.3 Bibliographic file from broad scan
Jiang, Q., Feng, W., Peng, J., Han, F., Li, Q., Zhang, W and Su, H. (2012). Inventory -
Based Resource Management in Cloud Computing. IEEE Xplore.
Gupta, K., Beri, R and Behal, V. (2016). Cloud Computing: A survey on Cloud
Simulation Tools. International Journal for Innovative Research in Science and
Technology. Vol. 2, Issue 11.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Rani, D. R., Geethakumari, G. (2015). An Efficient Approach to Forensic investigation in
Cloud using VM Snapshots. International Conference on Pervasive Computing.
Subramanian, S and Munuswamy, D. (2015). Features. ISACA Journal. Volume 3.
Nodari, A., Nurminen, J.K and Fruhwirth, C. (2016). Inventory Theory Applied to Cost
optimization in Cloud Computing. IEEE Xplore.
Dustdar, S. (2016). Cloud Computing. IEEE.
Sanaei, Z., Abolfazli, S., Gani, A. and Buyya, R. (2014). Heterogeneity in mobile cloud
computing: taxonomy and open challenges. IEEE Communications Surveys &
Tutorials, 16(1), pp.369-392.
Botta, A., De Donato, W., Persico, V. and Pescapé, A. (2016). Integration of cloud
computing and internet of things: a survey. Future Generation Computer Systems, 56,
pp.684-700.
Oliveira, T., Thomas, M. and Espadanal, M. (2014). Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services sectors. Information
& Management, 51(5), pp.497-510.
Garrison, G., Wakefield, R.L. and Kim, S. (2015). The effects of IT capabilities and
delivery model on cloud computing success and firm performance for cloud supported
processes and operations. International Journal of Information Management, 35(4),
pp.377-393.
Ratten, V. (2016). Continuance use intention of cloud computing: innovativeness and
creativity perspectives. Journal of Business Research, 69(5), pp.1737-1740.
Zhang, H., Jiang, H., Li, B., Liu, F., Vasilakos, A.V. and Liu, J., (2016). A framework for
truthful online auctions in cloud computing with heterogeneous user demands. IEEE
Transactions on Computers, 65(3), pp.805-818.
4
Cloud using VM Snapshots. International Conference on Pervasive Computing.
Subramanian, S and Munuswamy, D. (2015). Features. ISACA Journal. Volume 3.
Nodari, A., Nurminen, J.K and Fruhwirth, C. (2016). Inventory Theory Applied to Cost
optimization in Cloud Computing. IEEE Xplore.
Dustdar, S. (2016). Cloud Computing. IEEE.
Sanaei, Z., Abolfazli, S., Gani, A. and Buyya, R. (2014). Heterogeneity in mobile cloud
computing: taxonomy and open challenges. IEEE Communications Surveys &
Tutorials, 16(1), pp.369-392.
Botta, A., De Donato, W., Persico, V. and Pescapé, A. (2016). Integration of cloud
computing and internet of things: a survey. Future Generation Computer Systems, 56,
pp.684-700.
Oliveira, T., Thomas, M. and Espadanal, M. (2014). Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services sectors. Information
& Management, 51(5), pp.497-510.
Garrison, G., Wakefield, R.L. and Kim, S. (2015). The effects of IT capabilities and
delivery model on cloud computing success and firm performance for cloud supported
processes and operations. International Journal of Information Management, 35(4),
pp.377-393.
Ratten, V. (2016). Continuance use intention of cloud computing: innovativeness and
creativity perspectives. Journal of Business Research, 69(5), pp.1737-1740.
Zhang, H., Jiang, H., Li, B., Liu, F., Vasilakos, A.V. and Liu, J., (2016). A framework for
truthful online auctions in cloud computing with heterogeneous user demands. IEEE
Transactions on Computers, 65(3), pp.805-818.
4

Zhan, Z.H., Liu, X.F., Gong, Y.J., Zhang, J., Chung, H.S.H. and Li, Y. (2015). Cloud
computing resource scheduling and a survey of its evolutionary approaches. ACM
Computing Surveys (CSUR), 47(4), p.63.
Li, J., Li, J., Chen, X., Jia, C. and Lou, W. (2015). Identity-based encryption with
outsourced revocation in cloud computing. Ieee Transactions on computers, 64(2),
pp.425-437.
Bera, S., Misra, S. and Rodrigues, J.J. (2015). Cloud computing applications for smart
grid: A survey. IEEE Transactions on Parallel and Distributed Systems, 26(5), pp.1477-
1494.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, 308-319.
Manvi, S. S., & Shyam, G. K. (2014). Resource management for Infrastructure as a
Service (IaaS) in cloud computing: A survey. Journal of Network and Computer
Applications, 41, 424-440.
Aazam, M., Khan, I., Alsaffar, A. A., & Huh, E. N. (2014, January). Cloud of Things:
Integrating Internet of Things and cloud computing and the issues involved. In Applied
Sciences and Technology (IBCAST), 2014 11th International Bhurban Conference
on (pp. 414-419). IEEE.
Ahmed, E., Gani, A., Khan, M. K., Buyya, R., & Khan, S. U. (2015). Seamless
application execution in mobile cloud computing: Motivation, taxonomy, and open
challenges. Journal of Network and Computer Applications, 52, 154-172.
Sharma, A. K., & Jha, R. K. (2015). Cloud Computing. Expansion, Impact and
Challenges of IT & CS, 103.
Chang, V., Kuo, Y.H. and Ramachandran, M., 2016. Cloud computing adoption
framework: A security framework for business clouds. Future Generation Computer
Systems, 57, pp.24-41.
5
computing resource scheduling and a survey of its evolutionary approaches. ACM
Computing Surveys (CSUR), 47(4), p.63.
Li, J., Li, J., Chen, X., Jia, C. and Lou, W. (2015). Identity-based encryption with
outsourced revocation in cloud computing. Ieee Transactions on computers, 64(2),
pp.425-437.
Bera, S., Misra, S. and Rodrigues, J.J. (2015). Cloud computing applications for smart
grid: A survey. IEEE Transactions on Parallel and Distributed Systems, 26(5), pp.1477-
1494.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, 308-319.
Manvi, S. S., & Shyam, G. K. (2014). Resource management for Infrastructure as a
Service (IaaS) in cloud computing: A survey. Journal of Network and Computer
Applications, 41, 424-440.
Aazam, M., Khan, I., Alsaffar, A. A., & Huh, E. N. (2014, January). Cloud of Things:
Integrating Internet of Things and cloud computing and the issues involved. In Applied
Sciences and Technology (IBCAST), 2014 11th International Bhurban Conference
on (pp. 414-419). IEEE.
Ahmed, E., Gani, A., Khan, M. K., Buyya, R., & Khan, S. U. (2015). Seamless
application execution in mobile cloud computing: Motivation, taxonomy, and open
challenges. Journal of Network and Computer Applications, 52, 154-172.
Sharma, A. K., & Jha, R. K. (2015). Cloud Computing. Expansion, Impact and
Challenges of IT & CS, 103.
Chang, V., Kuo, Y.H. and Ramachandran, M., 2016. Cloud computing adoption
framework: A security framework for business clouds. Future Generation Computer
Systems, 57, pp.24-41.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Tao, F., Cheng, Y., Da Xu, L., Zhang, L., & Li, B. H. (2014). CCIoT-CMfg: cloud
computing and internet of things-based cloud manufacturing service system. IEEE
Transactions on Industrial Informatics, 10(2), 1435-1442.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015).
The rise of “big data” on cloud computing: Review and open research issues. Information
Systems, 47, 98-115.
Wang, W., Li, B., & Liang, B. (2014, April). Dominant resource fairness in cloud
computing systems with heterogeneous servers. In INFOCOM, 2014 Proceedings
IEEE (pp. 583-591). IEEE.
Bruneo, D. (2014). A stochastic model to investigate data center performance and QoS in
IaaS cloud computing systems. IEEE Transactions on Parallel and Distributed
Systems, 25(3), 560-569.
1.2 Focused Review
I have selected two main articles on the topic “Cloud Computing” from the 10 articles
and these are helpful for me in doing proper and effective research.
1.2.1 Updated filing system
The below table contains the efficient as well as updated filling system:
Table 3: Updated Filling System
Source Keyword use No. of returned
Literature
No. of Collected
Literature
Scholar Cloud Computing
Use of Cloud
Computing
1000
2000
3
3
VU Library Cloud Computing 6000 2
6
computing and internet of things-based cloud manufacturing service system. IEEE
Transactions on Industrial Informatics, 10(2), 1435-1442.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015).
The rise of “big data” on cloud computing: Review and open research issues. Information
Systems, 47, 98-115.
Wang, W., Li, B., & Liang, B. (2014, April). Dominant resource fairness in cloud
computing systems with heterogeneous servers. In INFOCOM, 2014 Proceedings
IEEE (pp. 583-591). IEEE.
Bruneo, D. (2014). A stochastic model to investigate data center performance and QoS in
IaaS cloud computing systems. IEEE Transactions on Parallel and Distributed
Systems, 25(3), 560-569.
1.2 Focused Review
I have selected two main articles on the topic “Cloud Computing” from the 10 articles
and these are helpful for me in doing proper and effective research.
1.2.1 Updated filing system
The below table contains the efficient as well as updated filling system:
Table 3: Updated Filling System
Source Keyword use No. of returned
Literature
No. of Collected
Literature
Scholar Cloud Computing
Use of Cloud
Computing
1000
2000
3
3
VU Library Cloud Computing 6000 2
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
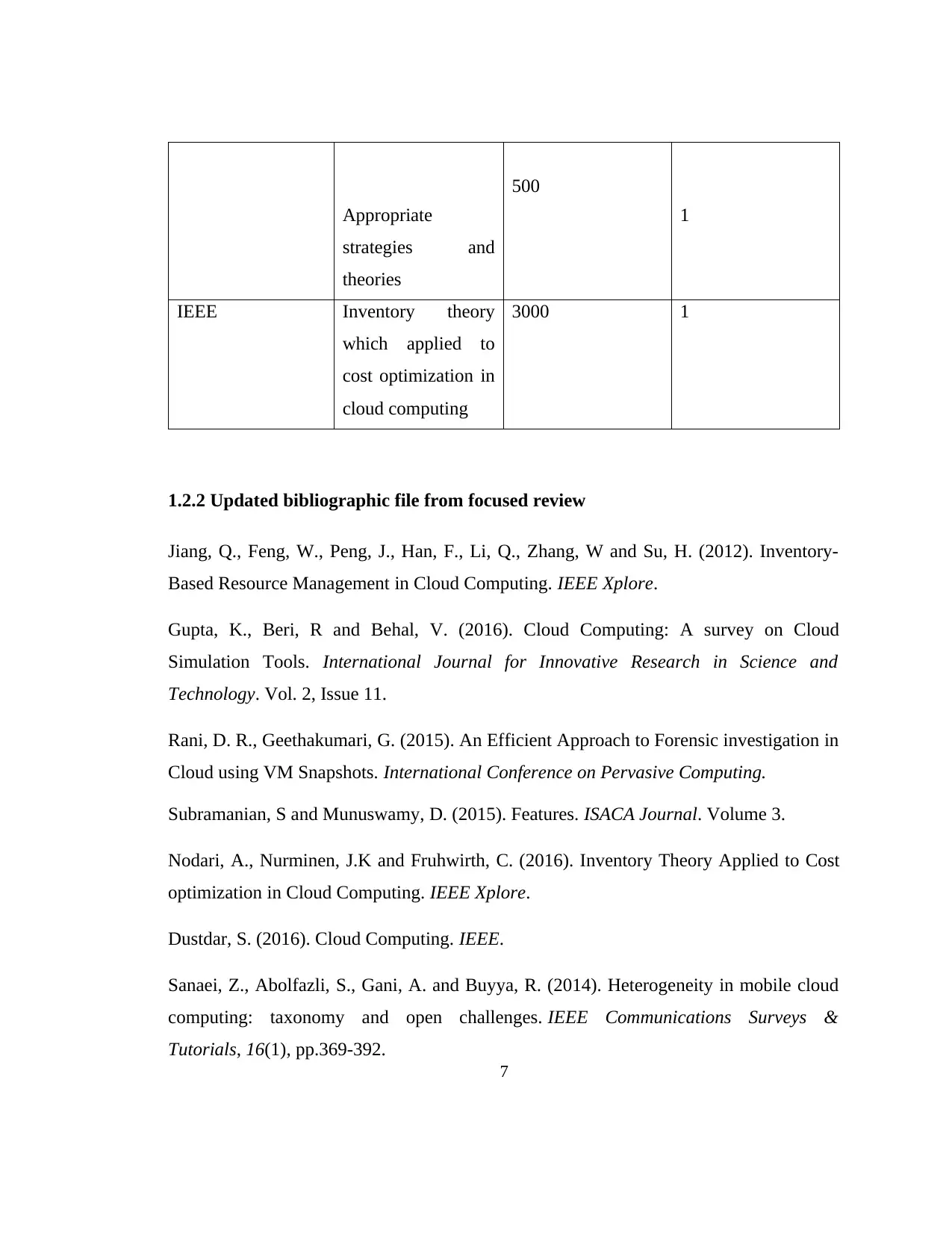
Appropriate
strategies and
theories
500
1
IEEE Inventory theory
which applied to
cost optimization in
cloud computing
3000 1
1.2.2 Updated bibliographic file from focused review
Jiang, Q., Feng, W., Peng, J., Han, F., Li, Q., Zhang, W and Su, H. (2012). Inventory-
Based Resource Management in Cloud Computing. IEEE Xplore.
Gupta, K., Beri, R and Behal, V. (2016). Cloud Computing: A survey on Cloud
Simulation Tools. International Journal for Innovative Research in Science and
Technology. Vol. 2, Issue 11.
Rani, D. R., Geethakumari, G. (2015). An Efficient Approach to Forensic investigation in
Cloud using VM Snapshots. International Conference on Pervasive Computing.
Subramanian, S and Munuswamy, D. (2015). Features. ISACA Journal. Volume 3.
Nodari, A., Nurminen, J.K and Fruhwirth, C. (2016). Inventory Theory Applied to Cost
optimization in Cloud Computing. IEEE Xplore.
Dustdar, S. (2016). Cloud Computing. IEEE.
Sanaei, Z., Abolfazli, S., Gani, A. and Buyya, R. (2014). Heterogeneity in mobile cloud
computing: taxonomy and open challenges. IEEE Communications Surveys &
Tutorials, 16(1), pp.369-392.
7
strategies and
theories
500
1
IEEE Inventory theory
which applied to
cost optimization in
cloud computing
3000 1
1.2.2 Updated bibliographic file from focused review
Jiang, Q., Feng, W., Peng, J., Han, F., Li, Q., Zhang, W and Su, H. (2012). Inventory-
Based Resource Management in Cloud Computing. IEEE Xplore.
Gupta, K., Beri, R and Behal, V. (2016). Cloud Computing: A survey on Cloud
Simulation Tools. International Journal for Innovative Research in Science and
Technology. Vol. 2, Issue 11.
Rani, D. R., Geethakumari, G. (2015). An Efficient Approach to Forensic investigation in
Cloud using VM Snapshots. International Conference on Pervasive Computing.
Subramanian, S and Munuswamy, D. (2015). Features. ISACA Journal. Volume 3.
Nodari, A., Nurminen, J.K and Fruhwirth, C. (2016). Inventory Theory Applied to Cost
optimization in Cloud Computing. IEEE Xplore.
Dustdar, S. (2016). Cloud Computing. IEEE.
Sanaei, Z., Abolfazli, S., Gani, A. and Buyya, R. (2014). Heterogeneity in mobile cloud
computing: taxonomy and open challenges. IEEE Communications Surveys &
Tutorials, 16(1), pp.369-392.
7

Botta, A., De Donato, W., Persico, V. and Pescapé, A. (2016). Integration of cloud
computing and internet of things: a survey. Future Generation Computer Systems, 56,
pp.684-700.
Oliveira, T., Thomas, M. and Espadanal, M. (2014). Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services sectors. Information
& Management, 51(5), pp.497-510.
Garrison, G., Wakefield, R.L. and Kim, S. (2015). The effects of IT capabilities and
delivery model on cloud computing success and firm performance for cloud supported
processes and operations. International Journal of Information Management, 35(4),
pp.377-393.
1.3 Cloud Computing
According to Grobauer, et. al (2016), it has been analysed that cloud computing
demonstrate the essential role in IT sector for the both individual and organisations from
the appropriate way so that they can properly access, store along with the sharing
information. For the experiment, they have to above some vulnerabilities which are
related to cloud computing. Along with this, they have to adopt appropriate service model
which are related to cloud computing. Section 1.3.1 provides the lights on the background
of the topic. This includes the vulnerabilities and service model which are related to
cloud computing. Section 1.3.2 shows the appropriate outline by which they investigated.
Section 1.3.3 provides the indication of service model which is related to cloud
computing. Section 1.3.4 is the discussion part and in this pros and cons related to the
topic.
8
computing and internet of things: a survey. Future Generation Computer Systems, 56,
pp.684-700.
Oliveira, T., Thomas, M. and Espadanal, M. (2014). Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services sectors. Information
& Management, 51(5), pp.497-510.
Garrison, G., Wakefield, R.L. and Kim, S. (2015). The effects of IT capabilities and
delivery model on cloud computing success and firm performance for cloud supported
processes and operations. International Journal of Information Management, 35(4),
pp.377-393.
1.3 Cloud Computing
According to Grobauer, et. al (2016), it has been analysed that cloud computing
demonstrate the essential role in IT sector for the both individual and organisations from
the appropriate way so that they can properly access, store along with the sharing
information. For the experiment, they have to above some vulnerabilities which are
related to cloud computing. Along with this, they have to adopt appropriate service model
which are related to cloud computing. Section 1.3.1 provides the lights on the background
of the topic. This includes the vulnerabilities and service model which are related to
cloud computing. Section 1.3.2 shows the appropriate outline by which they investigated.
Section 1.3.3 provides the indication of service model which is related to cloud
computing. Section 1.3.4 is the discussion part and in this pros and cons related to the
topic.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





