Introduction to Research Assignment 4 - Experimental Design & ReSULT AnalySIS by Rachid Hamadi Student ID: 30099999
VerifiedAdded on 2020/05/01
|13
|2999
|404
AI Summary
Data Source Name Source Organization Data Description Data File Format URL Charge fee Target data source Data 1 Gartner Inc Privacy attacks Pdf http://www.iaeng.org/publication/WCE2013/WCE2013_pp1287-1291.pdf Free No Data 2 RazorFish Inc Social Engineering attacks Pdf https://www.lume.ufrgs.br/bitstream/handle/10183/99410/000921541.pdf;sequence=1 Free Yes Data 3 AWS Account Hijacking Pdf
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NIT6130 INTRODUCTION TO RESEARCH
ASSIGNMENT 4 – EXPERIMENT DESIGN & RESULT ANALYSIS
by
Rachid Hamadi
Student ID: 30099999
ASSIGNMENT 4 – EXPERIMENT DESIGN & RESULT ANALYSIS
by
Rachid Hamadi
Student ID: 30099999
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Objective........................................................................................................................................................3
1. Data Collection......................................................................................................................................3
1.1 Data Sources..................................................................................................................................3
1.2 Collection of data...........................................................................................................................3
1.3 Data Storage...................................................................................................................................5
2. Design and Implementation...................................................................................................................5
2.1 Data pre-computing.......................................................................................................................5
2.2 Feature selection or dimension reduction......................................................................................6
2.3 Experiment designing....................................................................................................................6
2.3.1 Detailed design steps..................................................................................................................6
2.4 Implementation..................................................................................................................................7
3. Analysis..................................................................................................................................................7
3.1 Results Estimation...............................................................................................................................7
3.2 Results Summary.................................................................................................................................9
4. Outline of the research...........................................................................................................................9
References....................................................................................................................................................11
Objective........................................................................................................................................................3
1. Data Collection......................................................................................................................................3
1.1 Data Sources..................................................................................................................................3
1.2 Collection of data...........................................................................................................................3
1.3 Data Storage...................................................................................................................................5
2. Design and Implementation...................................................................................................................5
2.1 Data pre-computing.......................................................................................................................5
2.2 Feature selection or dimension reduction......................................................................................6
2.3 Experiment designing....................................................................................................................6
2.3.1 Detailed design steps..................................................................................................................6
2.4 Implementation..................................................................................................................................7
3. Analysis..................................................................................................................................................7
3.1 Results Estimation...............................................................................................................................7
3.2 Results Summary.................................................................................................................................9
4. Outline of the research...........................................................................................................................9
References....................................................................................................................................................11

Objective
The objective of the assignment is to analyze data and information with proper design
process. This assignment have reviewed various journals, articles as data is collected with the
help of secondary method data collection. Data and information related to cloud security is
collected from various online journals, books and articles from various sources. All the journals
are published after 2012.
1. Data Collection
Before initiating experimental analysis and results, data collection is an important step to
follow in the research. Therefore, data is collected from various secondary sources including
journals, books, articles and government databases. Following sections will help in identifying
various sources pf data collection related to cloud security. We have used various organization as
case studies to collect data and information regarding cloud attacks and security challenges. All
data and information are put into a table for creating records in a proper manner.
1.1 Data Sources
Before initiating experiment analysis, problems and challenges regarding cloud security need
to be identified by data collection. Therefore, data sources are important part of the research.
Following are the data sources from where data is collected related to the cloud security:
Online Journals
Articles
Books
Private Companies
The objective of the assignment is to analyze data and information with proper design
process. This assignment have reviewed various journals, articles as data is collected with the
help of secondary method data collection. Data and information related to cloud security is
collected from various online journals, books and articles from various sources. All the journals
are published after 2012.
1. Data Collection
Before initiating experimental analysis and results, data collection is an important step to
follow in the research. Therefore, data is collected from various secondary sources including
journals, books, articles and government databases. Following sections will help in identifying
various sources pf data collection related to cloud security. We have used various organization as
case studies to collect data and information regarding cloud attacks and security challenges. All
data and information are put into a table for creating records in a proper manner.
1.1 Data Sources
Before initiating experiment analysis, problems and challenges regarding cloud security need
to be identified by data collection. Therefore, data sources are important part of the research.
Following are the data sources from where data is collected related to the cloud security:
Online Journals
Articles
Books
Private Companies
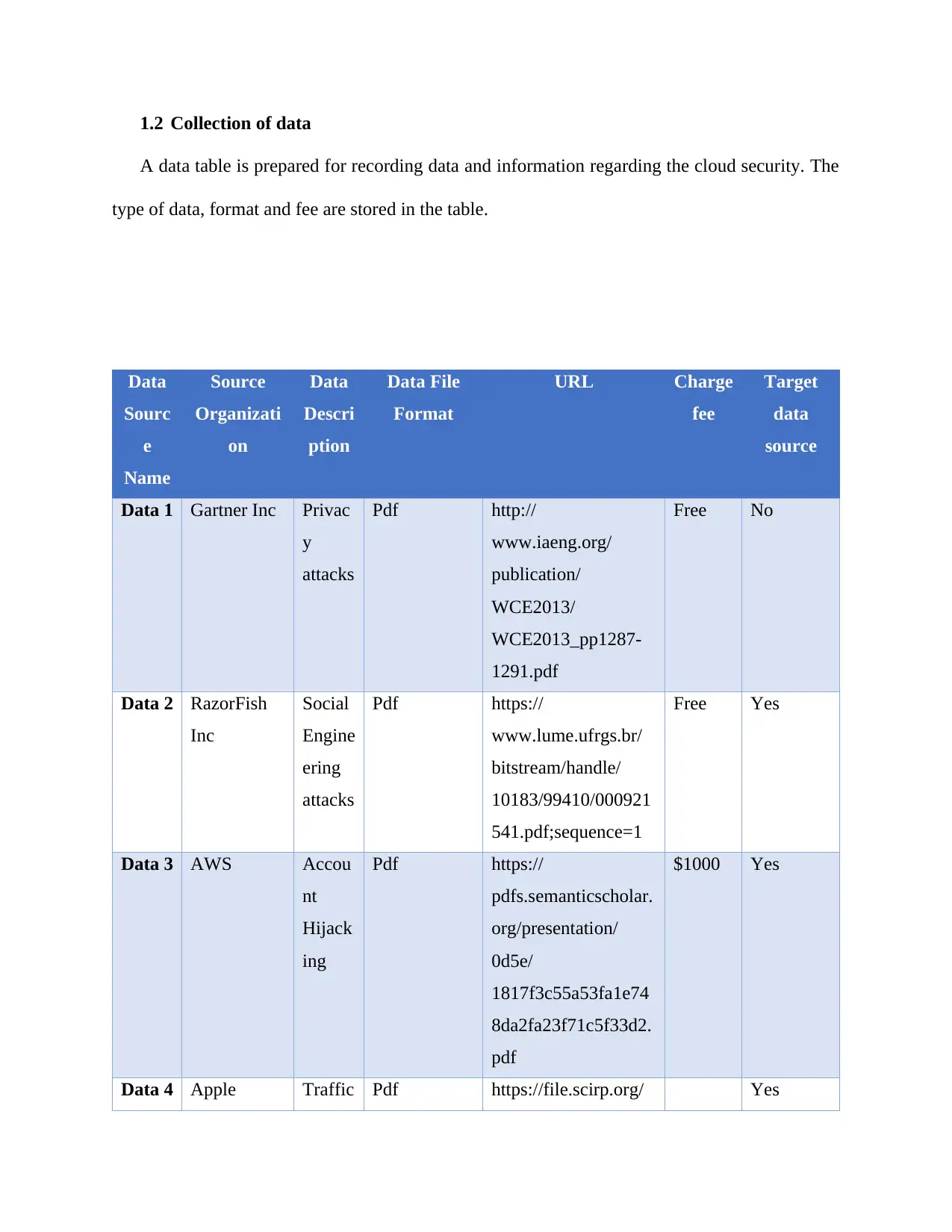
1.2 Collection of data
A data table is prepared for recording data and information regarding the cloud security. The
type of data, format and fee are stored in the table.
Data
Sourc
e
Name
Source
Organizati
on
Data
Descri
ption
Data File
Format
URL Charge
fee
Target
data
source
Data 1 Gartner Inc Privac
y
attacks
Pdf http://
www.iaeng.org/
publication/
WCE2013/
WCE2013_pp1287-
1291.pdf
Free No
Data 2 RazorFish
Inc
Social
Engine
ering
attacks
Pdf https://
www.lume.ufrgs.br/
bitstream/handle/
10183/99410/000921
541.pdf;sequence=1
Free Yes
Data 3 AWS Accou
nt
Hijack
ing
Pdf https://
pdfs.semanticscholar.
org/presentation/
0d5e/
1817f3c55a53fa1e74
8da2fa23f71c5f33d2.
pdf
$1000 Yes
Data 4 Apple Traffic Pdf https://file.scirp.org/ Yes
A data table is prepared for recording data and information regarding the cloud security. The
type of data, format and fee are stored in the table.
Data
Sourc
e
Name
Source
Organizati
on
Data
Descri
ption
Data File
Format
URL Charge
fee
Target
data
source
Data 1 Gartner Inc Privac
y
attacks
Pdf http://
www.iaeng.org/
publication/
WCE2013/
WCE2013_pp1287-
1291.pdf
Free No
Data 2 RazorFish
Inc
Social
Engine
ering
attacks
Pdf https://
www.lume.ufrgs.br/
bitstream/handle/
10183/99410/000921
541.pdf;sequence=1
Free Yes
Data 3 AWS Accou
nt
Hijack
ing
Pdf https://
pdfs.semanticscholar.
org/presentation/
0d5e/
1817f3c55a53fa1e74
8da2fa23f71c5f33d2.
$1000 Yes
Data 4 Apple Traffic Pdf https://file.scirp.org/ Yes
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
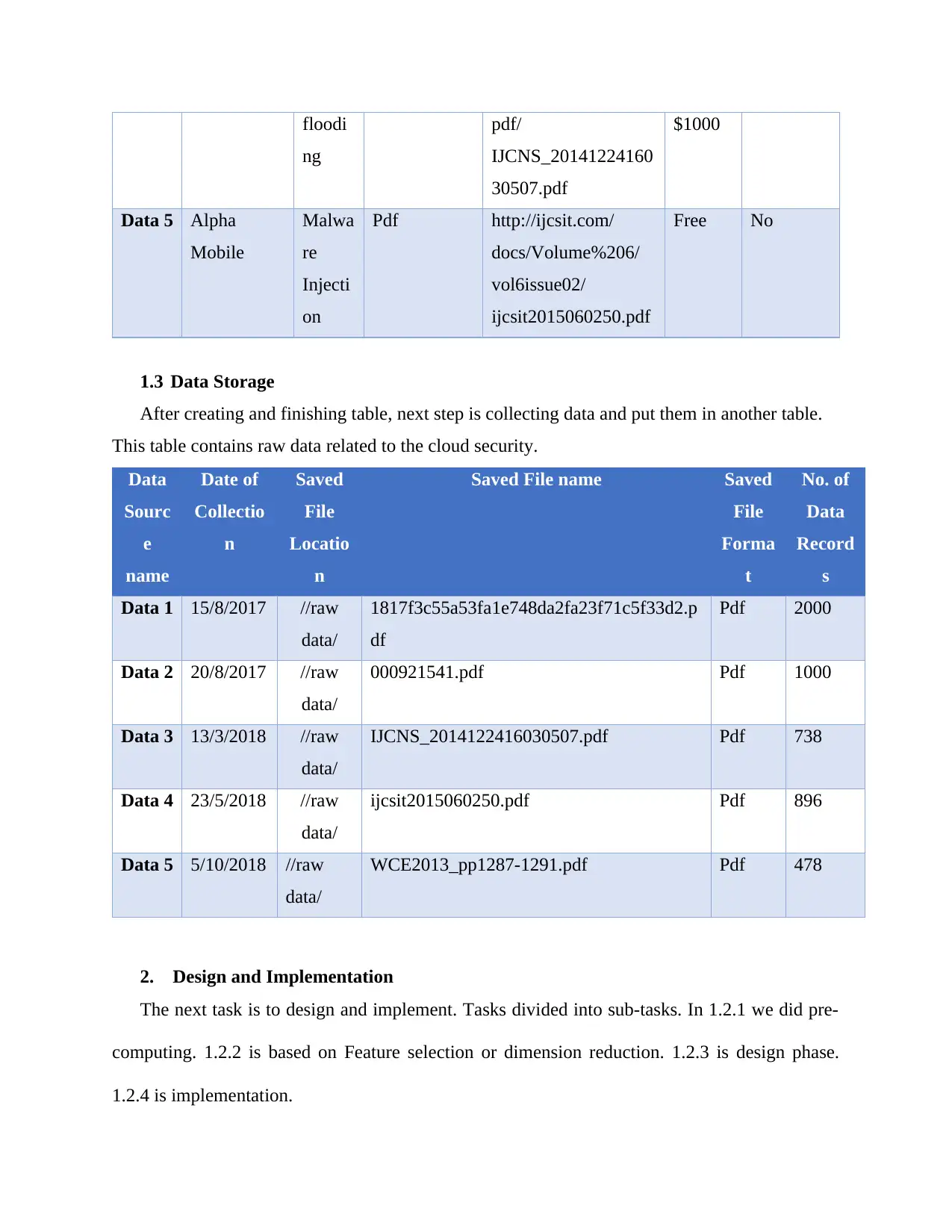
floodi
ng
pdf/
IJCNS_20141224160
30507.pdf
$1000
Data 5 Alpha
Mobile
Malwa
re
Injecti
on
Pdf http://ijcsit.com/
docs/Volume%206/
vol6issue02/
ijcsit2015060250.pdf
Free No
1.3 Data Storage
After creating and finishing table, next step is collecting data and put them in another table.
This table contains raw data related to the cloud security.
Data
Sourc
e
name
Date of
Collectio
n
Saved
File
Locatio
n
Saved File name Saved
File
Forma
t
No. of
Data
Record
s
Data 1 15/8/2017 //raw
data/
1817f3c55a53fa1e748da2fa23f71c5f33d2.p
df
Pdf 2000
Data 2 20/8/2017 //raw
data/
000921541.pdf Pdf 1000
Data 3 13/3/2018 //raw
data/
IJCNS_2014122416030507.pdf Pdf 738
Data 4 23/5/2018 //raw
data/
ijcsit2015060250.pdf Pdf 896
Data 5 5/10/2018 //raw
data/
WCE2013_pp1287-1291.pdf Pdf 478
2. Design and Implementation
The next task is to design and implement. Tasks divided into sub-tasks. In 1.2.1 we did pre-
computing. 1.2.2 is based on Feature selection or dimension reduction. 1.2.3 is design phase.
1.2.4 is implementation.
ng
pdf/
IJCNS_20141224160
30507.pdf
$1000
Data 5 Alpha
Mobile
Malwa
re
Injecti
on
Pdf http://ijcsit.com/
docs/Volume%206/
vol6issue02/
ijcsit2015060250.pdf
Free No
1.3 Data Storage
After creating and finishing table, next step is collecting data and put them in another table.
This table contains raw data related to the cloud security.
Data
Sourc
e
name
Date of
Collectio
n
Saved
File
Locatio
n
Saved File name Saved
File
Forma
t
No. of
Data
Record
s
Data 1 15/8/2017 //raw
data/
1817f3c55a53fa1e748da2fa23f71c5f33d2.p
df
Pdf 2000
Data 2 20/8/2017 //raw
data/
000921541.pdf Pdf 1000
Data 3 13/3/2018 //raw
data/
IJCNS_2014122416030507.pdf Pdf 738
Data 4 23/5/2018 //raw
data/
ijcsit2015060250.pdf Pdf 896
Data 5 5/10/2018 //raw
data/
WCE2013_pp1287-1291.pdf Pdf 478
2. Design and Implementation
The next task is to design and implement. Tasks divided into sub-tasks. In 1.2.1 we did pre-
computing. 1.2.2 is based on Feature selection or dimension reduction. 1.2.3 is design phase.
1.2.4 is implementation.
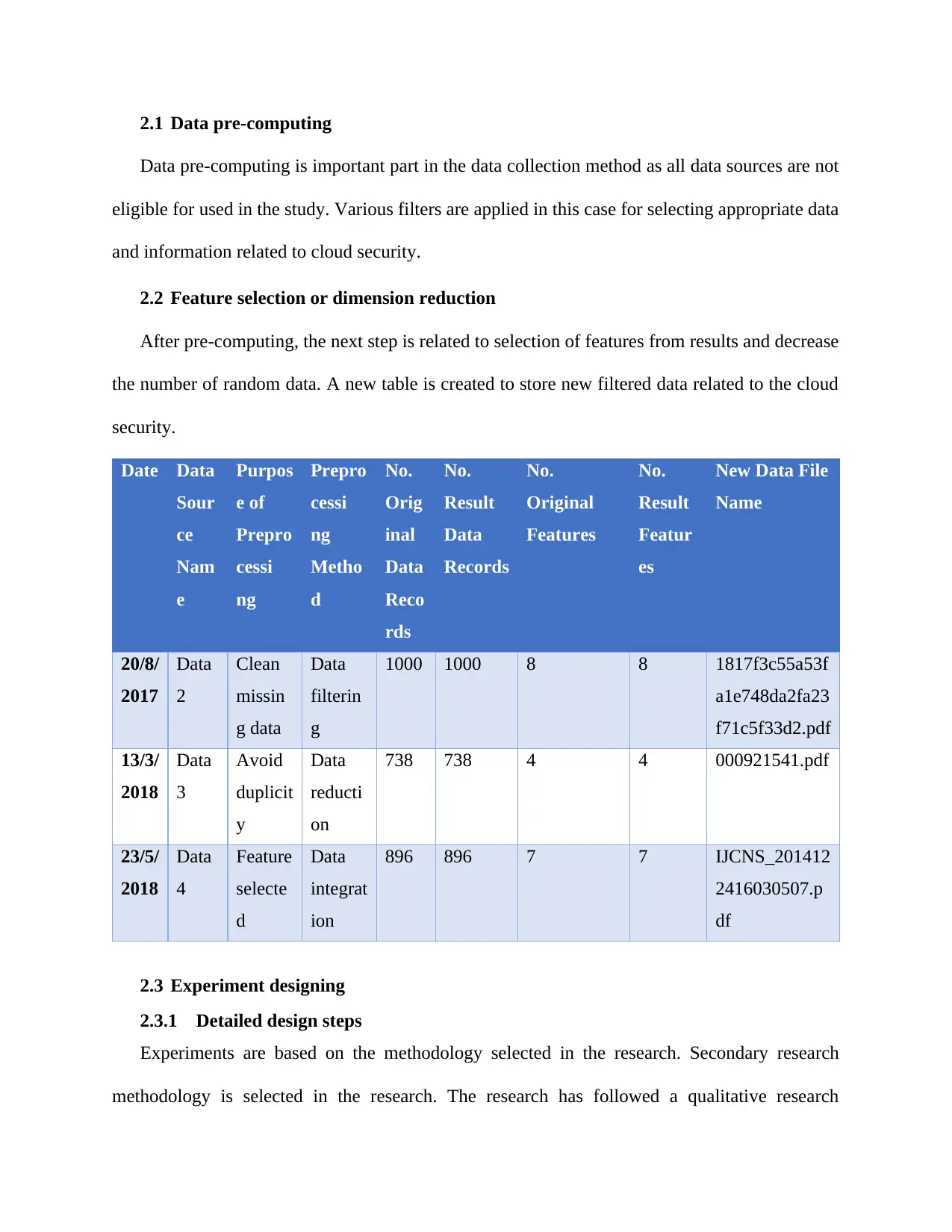
2.1 Data pre-computing
Data pre-computing is important part in the data collection method as all data sources are not
eligible for used in the study. Various filters are applied in this case for selecting appropriate data
and information related to cloud security.
2.2 Feature selection or dimension reduction
After pre-computing, the next step is related to selection of features from results and decrease
the number of random data. A new table is created to store new filtered data related to the cloud
security.
Date Data
Sour
ce
Nam
e
Purpos
e of
Prepro
cessi
ng
Prepro
cessi
ng
Metho
d
No.
Orig
inal
Data
Reco
rds
No.
Result
Data
Records
No.
Original
Features
No.
Result
Featur
es
New Data File
Name
20/8/
2017
Data
2
Clean
missin
g data
Data
filterin
g
1000 1000 8 8 1817f3c55a53f
a1e748da2fa23
f71c5f33d2.pdf
13/3/
2018
Data
3
Avoid
duplicit
y
Data
reducti
on
738 738 4 4 000921541.pdf
23/5/
2018
Data
4
Feature
selecte
d
Data
integrat
ion
896 896 7 7 IJCNS_201412
2416030507.p
df
2.3 Experiment designing
2.3.1 Detailed design steps
Experiments are based on the methodology selected in the research. Secondary research
methodology is selected in the research. The research has followed a qualitative research
Data pre-computing is important part in the data collection method as all data sources are not
eligible for used in the study. Various filters are applied in this case for selecting appropriate data
and information related to cloud security.
2.2 Feature selection or dimension reduction
After pre-computing, the next step is related to selection of features from results and decrease
the number of random data. A new table is created to store new filtered data related to the cloud
security.
Date Data
Sour
ce
Nam
e
Purpos
e of
Prepro
cessi
ng
Prepro
cessi
ng
Metho
d
No.
Orig
inal
Data
Reco
rds
No.
Result
Data
Records
No.
Original
Features
No.
Result
Featur
es
New Data File
Name
20/8/
2017
Data
2
Clean
missin
g data
Data
filterin
g
1000 1000 8 8 1817f3c55a53f
a1e748da2fa23
f71c5f33d2.pdf
13/3/
2018
Data
3
Avoid
duplicit
y
Data
reducti
on
738 738 4 4 000921541.pdf
23/5/
2018
Data
4
Feature
selecte
d
Data
integrat
ion
896 896 7 7 IJCNS_201412
2416030507.p
df
2.3 Experiment designing
2.3.1 Detailed design steps
Experiments are based on the methodology selected in the research. Secondary research
methodology is selected in the research. The research has followed a qualitative research

method. Thematic analysis is selected for analyzing data and information collected for the
research. Themes are created for analyzing data and information.
2.4 Implementation
The further step is implementation. After designing, the next part is to implement themes
related to the cloud security. Themes are created based on cloud security.
3. Analysis
3.1 Results Estimation
Cloud computing are useful for SMEs in market. Autonomous endeavors are monetarily
weak and cannot adopt expense of over the top applications and software. In this way, Cloud
computing are maintaining budgetary arrangement. Cloud computing provides securing huge
proportion of data over the web. This are a phenomenal methodology given by Cloud computing.
Giant proportion of data sources are accessible over internet. Subsequently, organization and
limit of data are a great issue for associations in the market (Taha et al. 2014). Subsequently,
Cloud computing helps in keeping up data and information over internet. Of course, there are a
couple of security challenges in the Cloud computing. Data security is critical security challenges
in Cloud computing. Different data and information is secured in the cloud. Several challenges in
security are recognized in the Cloud computing (Kaur and Kaur 2015).
The usage of cloud computing are helping in securing data an information of customers.
In any case, there are a couple of advanced ambushes over the web. Diverse models are going up
against unmistakable kind of security challenges in the cloud (Kulkarni and Khanai 2015). SaaS
indicate is defying challenges in data and framework. Basic data of the affiliations are secured
completed the Cloud computing databases. In this way, there is tremendous threats and risks of
losing data over cloud. Advanced ambushes are undeniable over these progressing years (Casola,
research. Themes are created for analyzing data and information.
2.4 Implementation
The further step is implementation. After designing, the next part is to implement themes
related to the cloud security. Themes are created based on cloud security.
3. Analysis
3.1 Results Estimation
Cloud computing are useful for SMEs in market. Autonomous endeavors are monetarily
weak and cannot adopt expense of over the top applications and software. In this way, Cloud
computing are maintaining budgetary arrangement. Cloud computing provides securing huge
proportion of data over the web. This are a phenomenal methodology given by Cloud computing.
Giant proportion of data sources are accessible over internet. Subsequently, organization and
limit of data are a great issue for associations in the market (Taha et al. 2014). Subsequently,
Cloud computing helps in keeping up data and information over internet. Of course, there are a
couple of security challenges in the Cloud computing. Data security is critical security challenges
in Cloud computing. Different data and information is secured in the cloud. Several challenges in
security are recognized in the Cloud computing (Kaur and Kaur 2015).
The usage of cloud computing are helping in securing data an information of customers.
In any case, there are a couple of advanced ambushes over the web. Diverse models are going up
against unmistakable kind of security challenges in the cloud (Kulkarni and Khanai 2015). SaaS
indicate is defying challenges in data and framework. Basic data of the affiliations are secured
completed the Cloud computing databases. In this way, there is tremendous threats and risks of
losing data over cloud. Advanced ambushes are undeniable over these progressing years (Casola,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

De Benedictis and Rak 2015). This can be an exceptional hazard for the Cloud computing. Cloud
expert centers are helping in tying down data and information of associations over their servers.
Software engineers and programmers are concentrating on this databases over the web (Sharma
et al. 2017). Control and organization of data is a sharp perils for affiliations.
SMEs are benefited by use of cloud services in market. Private companies are small and
are not able to bear costly software. Along these lines, cloud computing helps in maintaining
business plan of companies. This are an awesome methodology given by cloud computing.
Tremendous measure of information sources are available over the web (Jyothi and Bhavani
2017). Along these lines, storage and management of data is an incredible risk for companies in
the market. Accordingly, cloud storage are helping in storing information and data over the web.
The utilization of cloud computing are helping in putting away information and data of
clients. However, there are a few digital attacks over the web. Different models are confronting
diverse sort of security challenges in cloud. SaaS demonstrate is confronting challenges in
information and system (Khan and Al-Yasiri 2016). Critical information of associations are put
away over cloud computing databases. In this manner, there are immense dangers and risk of
losing information and data over cloud. Cloud-attacks are unmistakable over ongoing years (Tari
2014). Cloud specialist organizations are helping in anchoring information and data of
organizations over their servers. However, programmers and interlopers are focusing on this
databases over the web. Control and administration of information is a sharp dangers for
associations. Cloud security is an important aspect for companies in the market.
The utilization of a few approaches and standards are documented in ceasing these cloud
attacks. Subsequently, data innovation are assuming an incredible job in keeping up hazard over
the cloud computing. In cloud computing, information should be exchanged starting with one
expert centers are helping in tying down data and information of associations over their servers.
Software engineers and programmers are concentrating on this databases over the web (Sharma
et al. 2017). Control and organization of data is a sharp perils for affiliations.
SMEs are benefited by use of cloud services in market. Private companies are small and
are not able to bear costly software. Along these lines, cloud computing helps in maintaining
business plan of companies. This are an awesome methodology given by cloud computing.
Tremendous measure of information sources are available over the web (Jyothi and Bhavani
2017). Along these lines, storage and management of data is an incredible risk for companies in
the market. Accordingly, cloud storage are helping in storing information and data over the web.
The utilization of cloud computing are helping in putting away information and data of
clients. However, there are a few digital attacks over the web. Different models are confronting
diverse sort of security challenges in cloud. SaaS demonstrate is confronting challenges in
information and system (Khan and Al-Yasiri 2016). Critical information of associations are put
away over cloud computing databases. In this manner, there are immense dangers and risk of
losing information and data over cloud. Cloud-attacks are unmistakable over ongoing years (Tari
2014). Cloud specialist organizations are helping in anchoring information and data of
organizations over their servers. However, programmers and interlopers are focusing on this
databases over the web. Control and administration of information is a sharp dangers for
associations. Cloud security is an important aspect for companies in the market.
The utilization of a few approaches and standards are documented in ceasing these cloud
attacks. Subsequently, data innovation are assuming an incredible job in keeping up hazard over
the cloud computing. In cloud computing, information should be exchanged starting with one

system then onto the next system much of the time (Kaiya et al. 2016). Consequently, Data flow
issues are occurring in cloud computing. The utilization of methodology are helping in
recognizing digital attacks in system. A few system attacks including DOS, DDOS and SQL
infusion are major attacks in cloud computing system (Modic et al. 2016). Information protection
and privacy challenges are happening in classified information and data amid sharing. The
verification issue are occurring in the cloud computing related to the information security. The
respectability of information is an issue that is making protection need in the cloud computing. A
large portion of the occasions because of need in confirmation and protection, unapproved clients
are going into the system of the cloud computing.
3.2 Results Summary
The IT field are profited by utilization of the cloud computing. The challenges and
difficulties in the cloud computing are discussed about in these reports. The past researches in
cloud security are discussed about in area. An engaged methodology are utilized so as to
examinations writing. The sum total of what online are actually identified with cloud computing
security. Distinctive specialized parts of the cloud computing are discussed about in online
(Chouhan and Singh 2016). These online have possessed the capacity to distinguish security
issues in the cloud computing. Cloud computing is an ongoing idea in the IT field (De Carvalho
et al. 2017). The utilization of cloud services in the business association are an extraordinary
advantageous for advancement of organization in the market. These examination online contains
different contextual investigations of the distinctive associations that are profited because of the
cloud computing. Alongside these, the principle focal point of these online are challenges and
difficulties in cloud computing identified with security approach.
issues are occurring in cloud computing. The utilization of methodology are helping in
recognizing digital attacks in system. A few system attacks including DOS, DDOS and SQL
infusion are major attacks in cloud computing system (Modic et al. 2016). Information protection
and privacy challenges are happening in classified information and data amid sharing. The
verification issue are occurring in the cloud computing related to the information security. The
respectability of information is an issue that is making protection need in the cloud computing. A
large portion of the occasions because of need in confirmation and protection, unapproved clients
are going into the system of the cloud computing.
3.2 Results Summary
The IT field are profited by utilization of the cloud computing. The challenges and
difficulties in the cloud computing are discussed about in these reports. The past researches in
cloud security are discussed about in area. An engaged methodology are utilized so as to
examinations writing. The sum total of what online are actually identified with cloud computing
security. Distinctive specialized parts of the cloud computing are discussed about in online
(Chouhan and Singh 2016). These online have possessed the capacity to distinguish security
issues in the cloud computing. Cloud computing is an ongoing idea in the IT field (De Carvalho
et al. 2017). The utilization of cloud services in the business association are an extraordinary
advantageous for advancement of organization in the market. These examination online contains
different contextual investigations of the distinctive associations that are profited because of the
cloud computing. Alongside these, the principle focal point of these online are challenges and
difficulties in cloud computing identified with security approach.

4. Outline of the research
Objective
1. Data Collection
1.1 Data Sources
1.2 Collection of data
1.3 Data Storage
2. Design and Implementation
2.1 Data pre-computing
2.2 Feature selection or dimension reduction
2.3 Experiment designing
2.3.1 Detailed design steps
2.4 Implementation
3. Analysis
3.1 Results Estimation
3.2 Results Summary
Objective
1. Data Collection
1.1 Data Sources
1.2 Collection of data
1.3 Data Storage
2. Design and Implementation
2.1 Data pre-computing
2.2 Feature selection or dimension reduction
2.3 Experiment designing
2.3.1 Detailed design steps
2.4 Implementation
3. Analysis
3.1 Results Estimation
3.2 Results Summary
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Chauhan, P. and Bansal, P., 2017. Emphasizing on Various Security Challenges in Cloud
Forensic Framework. Indian Journal of Science and Technology, 10(18).
Chen, X., Chen, C., Tao, Y. and Hu, J., 2015. A cloud security assessment system based on
classifying and grading. IEEE Cloud Computing, 2(2), pp.58-67.
Chouhan, P. and Singh, R., 2016. Security attacks on cloud computing with possible
solution. International Journal of Advanced Research in Computer Science and Software
Engineering, 6(1).
Cook, A., Robinson, M., Ferrag, M.A., Maglaras, L.A., He, Y., Jones, K. and Janicke, H., 2018.
Internet of Cloud: Security and Privacy Challenges. In Cloud Computing for Optimization:
Foundations, Applications, and Challenges (pp. 271-301). Springer, Cham.
De Carvalho, C.A.B., de Castro Andrade, R.M., de Castro, M.F., Coutinho, E.F. and Agoulmine,
N., 2017. State of the art and challenges of security SLA for cloud computing. Computers &
Electrical Engineering, 59, pp.141-152.
Guo, C. and Zheng, X., 2015. The Research of Data Security Mechanism Based on Cloud
Computing. International Journal of Security and Its Applications, 9(3), pp.363-370.
Joseph, A.O., Kathrine, J.W. and Vijayan, R., 2014. Cloud security mechanisms for data
protection: a survey. International Journal of Multimedia and Ubiquitous Engineering, 9(9),
pp.81-90.
Jyothi, C. and Bhavani, P., 2017. Study on Security Controversies and Techniques in Cloud
Computing. International Journal of Research, 4(14), pp.5568-5572.
Kaur, M. and Singh, H., 2015. A review of cloud computing security challenges. International
Journal of Advances in Engineering & Technology, 8(3), p.397.
Chauhan, P. and Bansal, P., 2017. Emphasizing on Various Security Challenges in Cloud
Forensic Framework. Indian Journal of Science and Technology, 10(18).
Chen, X., Chen, C., Tao, Y. and Hu, J., 2015. A cloud security assessment system based on
classifying and grading. IEEE Cloud Computing, 2(2), pp.58-67.
Chouhan, P. and Singh, R., 2016. Security attacks on cloud computing with possible
solution. International Journal of Advanced Research in Computer Science and Software
Engineering, 6(1).
Cook, A., Robinson, M., Ferrag, M.A., Maglaras, L.A., He, Y., Jones, K. and Janicke, H., 2018.
Internet of Cloud: Security and Privacy Challenges. In Cloud Computing for Optimization:
Foundations, Applications, and Challenges (pp. 271-301). Springer, Cham.
De Carvalho, C.A.B., de Castro Andrade, R.M., de Castro, M.F., Coutinho, E.F. and Agoulmine,
N., 2017. State of the art and challenges of security SLA for cloud computing. Computers &
Electrical Engineering, 59, pp.141-152.
Guo, C. and Zheng, X., 2015. The Research of Data Security Mechanism Based on Cloud
Computing. International Journal of Security and Its Applications, 9(3), pp.363-370.
Joseph, A.O., Kathrine, J.W. and Vijayan, R., 2014. Cloud security mechanisms for data
protection: a survey. International Journal of Multimedia and Ubiquitous Engineering, 9(9),
pp.81-90.
Jyothi, C. and Bhavani, P., 2017. Study on Security Controversies and Techniques in Cloud
Computing. International Journal of Research, 4(14), pp.5568-5572.
Kaur, M. and Singh, H., 2015. A review of cloud computing security challenges. International
Journal of Advances in Engineering & Technology, 8(3), p.397.

Khan, N. and Al-Yasiri, A., 2016. Identifying cloud security threats to strengthen cloud
computing adoption framework. Procedia Computer Science, 94, pp.485-490.
Khattak, H.A.K., Abbass, H., Naeem, A., Saleem, K. and Iqbal, W., 2015, October. Security
concerns of cloud-based healthcare systems: A perspective of moving from single-cloud to a
multi-cloud infrastructure. In E-health Networking, Application & Services (HealthCom), 2015
17th International Conference on (pp. 61-67). IEEE.
Tari, Z., 2014. Security and Privacy in Cloud Computing. IEEE Cloud Computing, 1(1), pp.54-
57.
Tirthani, N. and Ganesan, R., 2014. Data Security in Cloud Architecture Based on Diffie
Hellman and Elliptical Curve Cryptography. IACR Cryptology ePrint Archive, 2014, p.49.
Washizaki, H., Fukumoto, S., Yamamoto, M., Yoshizawa, M., Fukazawa, Y., Kato, T., Ogata,
S., Kaiya, H., Fernandez, E.B., Kanuka, H. and Kondo, Y., 2016, June. A metamodel for security
and privacy knowledge in cloud services. In 2016 IEEE World Congress on Services
(SERVICES) (pp. 142-143). IEEE.
Yu, W., Yu, P., Wang, J., Wei, C., Gong, L., Li, W., Cui, B., Tadepalli, H.K. and Will, B., 2018,
May. Protecting Your Own Private Key in Cloud: Security, Scalability and Performance.
In 2018 IEEE Conference on Communications and Network Security (CNS) (pp. 1-2). IEEE.
Massonet, P., Luna, J., Pannetrat, A. and Trapero, R., 2015, March. Idea: Optimising multi-cloud
deployments with security controls as constraints. In International Symposium on Engineering
Secure Software and Systems (pp. 102-110). Springer, Cham.
Modic, J., Trapero, R., Taha, A., Luna, J., Stopar, M. and Suri, N., 2016. Novel efficient
techniques for real-time cloud security assessment. Computers & Security, 62, pp.1-18.
computing adoption framework. Procedia Computer Science, 94, pp.485-490.
Khattak, H.A.K., Abbass, H., Naeem, A., Saleem, K. and Iqbal, W., 2015, October. Security
concerns of cloud-based healthcare systems: A perspective of moving from single-cloud to a
multi-cloud infrastructure. In E-health Networking, Application & Services (HealthCom), 2015
17th International Conference on (pp. 61-67). IEEE.
Tari, Z., 2014. Security and Privacy in Cloud Computing. IEEE Cloud Computing, 1(1), pp.54-
57.
Tirthani, N. and Ganesan, R., 2014. Data Security in Cloud Architecture Based on Diffie
Hellman and Elliptical Curve Cryptography. IACR Cryptology ePrint Archive, 2014, p.49.
Washizaki, H., Fukumoto, S., Yamamoto, M., Yoshizawa, M., Fukazawa, Y., Kato, T., Ogata,
S., Kaiya, H., Fernandez, E.B., Kanuka, H. and Kondo, Y., 2016, June. A metamodel for security
and privacy knowledge in cloud services. In 2016 IEEE World Congress on Services
(SERVICES) (pp. 142-143). IEEE.
Yu, W., Yu, P., Wang, J., Wei, C., Gong, L., Li, W., Cui, B., Tadepalli, H.K. and Will, B., 2018,
May. Protecting Your Own Private Key in Cloud: Security, Scalability and Performance.
In 2018 IEEE Conference on Communications and Network Security (CNS) (pp. 1-2). IEEE.
Massonet, P., Luna, J., Pannetrat, A. and Trapero, R., 2015, March. Idea: Optimising multi-cloud
deployments with security controls as constraints. In International Symposium on Engineering
Secure Software and Systems (pp. 102-110). Springer, Cham.
Modic, J., Trapero, R., Taha, A., Luna, J., Stopar, M. and Suri, N., 2016. Novel efficient
techniques for real-time cloud security assessment. Computers & Security, 62, pp.1-18.

Raza, N., Rashid, I. and Awan, F.A., 2017. Security and management framework for an
organization operating in cloud environment. Annals of Telecommunications, 72(5-6), pp.325-
333.
Rittinghouse, J.W. and Ransome, J.F., 2016. Cloud computing: implementation, management,
and security. CRC press.
Ryoo, J., Rizvi, S., Aiken, W. and Kissell, J., 2014. Cloud security auditing: challenges and
emerging approaches. IEEE Security & Privacy, (1), pp.1-1.
Taha, A., Trapero, R., Luna, J. and Suri, N., 2014, September. AHP-based quantitative approach
for assessing and comparing cloud security. In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th International Conference on (pp. 284-291). IEEE.
Kaur, R. and Kaur, J., 2015, March. Cloud computing security challenges and its solution: A
review. In Computing for Sustainable Global Development (INDIACom), 2015 2nd International
Conference on (pp. 1198-1200). IEEE.
Kulkarni, P. and Khanai, R., 2015, April. Addressing mobile Cloud Computing security
challenges: A survey. In Communications and Signal Computing (ICCSP), 2015 International
Conference on (pp. 1463-1467). IEEE.
Casola, V., De Benedictis, A. and Rak, M., 2015, August. Security monitoring in the cloud: an
SLA-based approach. In Availability, Reliability and Security (ARES), 2015 10th International
Conference on (pp. 749-755). IEEE.
Chandra, J.V., Challa, N. and Pasupuleti, S.K., 2016, March. Advanced persistent threat defense
system using self-destructive mechanism for cloud security. In Engineering and Technology
(ICETECH), 2016 IEEE International Conference on (pp. 7-11). IEEE.
organization operating in cloud environment. Annals of Telecommunications, 72(5-6), pp.325-
333.
Rittinghouse, J.W. and Ransome, J.F., 2016. Cloud computing: implementation, management,
and security. CRC press.
Ryoo, J., Rizvi, S., Aiken, W. and Kissell, J., 2014. Cloud security auditing: challenges and
emerging approaches. IEEE Security & Privacy, (1), pp.1-1.
Taha, A., Trapero, R., Luna, J. and Suri, N., 2014, September. AHP-based quantitative approach
for assessing and comparing cloud security. In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th International Conference on (pp. 284-291). IEEE.
Kaur, R. and Kaur, J., 2015, March. Cloud computing security challenges and its solution: A
review. In Computing for Sustainable Global Development (INDIACom), 2015 2nd International
Conference on (pp. 1198-1200). IEEE.
Kulkarni, P. and Khanai, R., 2015, April. Addressing mobile Cloud Computing security
challenges: A survey. In Communications and Signal Computing (ICCSP), 2015 International
Conference on (pp. 1463-1467). IEEE.
Casola, V., De Benedictis, A. and Rak, M., 2015, August. Security monitoring in the cloud: an
SLA-based approach. In Availability, Reliability and Security (ARES), 2015 10th International
Conference on (pp. 749-755). IEEE.
Chandra, J.V., Challa, N. and Pasupuleti, S.K., 2016, March. Advanced persistent threat defense
system using self-destructive mechanism for cloud security. In Engineering and Technology
(ICETECH), 2016 IEEE International Conference on (pp. 7-11). IEEE.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





