Information System Contingency Plan (ISCP) for Payroll System
VerifiedAdded on 2022/11/30
|16
|5167
|347
Report
AI Summary
This document presents a comprehensive Information System Contingency Plan (ISCP) for a Payroll System, designed to ensure business continuity and rapid recovery from service disruptions. It outlines a three-phased approach: Activation and Notification, Recovery, and Reconstitution. The Activation and Notification phase details the criteria for activating the plan and the subsequent notification procedures for relevant personnel. The Recovery phase outlines the activities and procedures for restoring the affected system, including escalation notices and awareness protocols. Finally, the Reconstitution phase focuses on testing and validating the system's functionality, declaring recovery, notifying users, and documenting the entire process. The plan also includes sections on system description, roles and responsibilities, activation criteria, notification procedures, recovery activities, offsite data storage, data backup, and event documentation. The ISCP is designed to recover the Payroll System within a specified Recovery Time Objective (RTO), ensuring minimal disruption to critical business processes. It also includes appendices for plan approval and other relevant information.

NOTE: This sample template is provided to address NIST SP 800-53 security controls from the Contingency
Planning family for a moderate impact information system. The template provided is a guide and may be
customized and adapted as necessary to best fit the system or organizational requirements for contingency
planning.
[Payroll System]
Security Categorization: Very High
[Department for Wildlife]
Information System Contingency Plan (ISCP)
Version [#]
[Date]
Prepared by
[Organization Name]
[Street Address]
[City, State, and Zip Code]
Planning family for a moderate impact information system. The template provided is a guide and may be
customized and adapted as necessary to best fit the system or organizational requirements for contingency
planning.
[Payroll System]
Security Categorization: Very High
[Department for Wildlife]
Information System Contingency Plan (ISCP)
Version [#]
[Date]
Prepared by
[Organization Name]
[Street Address]
[City, State, and Zip Code]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Plan Approval…………………………………………………….………..….……….……A.2-3
1. Introduction ………………………………………………….……..……….…….……..A.2-4
1.1 Background………..………………………………………….………………..A.2-4
1.2 Scope……..………..…………………………..…….……….……….………..A.2-4
1.3 Assumptions..…….………………………..….……………….……….……...A.2-4
2. Concept of Operations ………………………….……..…………………………..…..A.2-5
2.1 System Description………………....……………………………………..…..A.2-5
2.2 Overview of Three Phases..………………………………………………….A.2-5
2.3 Roles and Responsibilities…….…......……………………………………....A.2-6
3. Activation and Notification………………....………………………..………….……..A.2-6
3.1 Activation Criteria and Procedure ...………………………..………………..A.2-6
3.2 Notification…………………...………………………………..………………..A.2-7
3.3 Outage Assessment…………....…......……………………..………………..A.2-7
4. Recovery……………………….……………....…………………………………………..A.2-7
4.1 Sequence of Recovery Activities ....……………………………..…………..A.2-7
4.2 Recovery Procedures ……...………………………………………..………..A.2-8
4.3 Recovery Escalation Notices/Awareness..…………………………..……...A.2-8
5. Reconstitution..……………….……………....………………….………………..……..A.2-8
5.1 Validation Data Testing………….…………………….………………….…..A.2-8
5.2 Validation Functionality Testing…......……………….………………….…...A.2-8
5.3 Recovery Declaration…………........………………….………………….…..A.2-9
5.4 Notification (users)…. ……...………………………….………………….…..A.2-9
5.5 Cleanup ...……………………...…......……………….………………….…....A.2-9
5.6 Offsite Data Storage……………. ....………………….………………….…..A.2-9
5.7 Data Backup………………...………………………….…………………..…..A.2-9
5.8 Event Documentation…………..…......……………….………………….…..A.2-9
5.9 Deactivation……………………..…......……………….………………….…..A.2-10
APPENDICES
Plan Approval…………………………………………………….………..….……….……A.2-3
1. Introduction ………………………………………………….……..……….…….……..A.2-4
1.1 Background………..………………………………………….………………..A.2-4
1.2 Scope……..………..…………………………..…….……….……….………..A.2-4
1.3 Assumptions..…….………………………..….……………….……….……...A.2-4
2. Concept of Operations ………………………….……..…………………………..…..A.2-5
2.1 System Description………………....……………………………………..…..A.2-5
2.2 Overview of Three Phases..………………………………………………….A.2-5
2.3 Roles and Responsibilities…….…......……………………………………....A.2-6
3. Activation and Notification………………....………………………..………….……..A.2-6
3.1 Activation Criteria and Procedure ...………………………..………………..A.2-6
3.2 Notification…………………...………………………………..………………..A.2-7
3.3 Outage Assessment…………....…......……………………..………………..A.2-7
4. Recovery……………………….……………....…………………………………………..A.2-7
4.1 Sequence of Recovery Activities ....……………………………..…………..A.2-7
4.2 Recovery Procedures ……...………………………………………..………..A.2-8
4.3 Recovery Escalation Notices/Awareness..…………………………..……...A.2-8
5. Reconstitution..……………….……………....………………….………………..……..A.2-8
5.1 Validation Data Testing………….…………………….………………….…..A.2-8
5.2 Validation Functionality Testing…......……………….………………….…...A.2-8
5.3 Recovery Declaration…………........………………….………………….…..A.2-9
5.4 Notification (users)…. ……...………………………….………………….…..A.2-9
5.5 Cleanup ...……………………...…......……………….………………….…....A.2-9
5.6 Offsite Data Storage……………. ....………………….………………….…..A.2-9
5.7 Data Backup………………...………………………….…………………..…..A.2-9
5.8 Event Documentation…………..…......……………….………………….…..A.2-9
5.9 Deactivation……………………..…......……………….………………….…..A.2-10
APPENDICES

Plan Approval
Provide a statement in accordance with the agency’s contingency planning policy to affirm that the ISCP
is complete and has been tested sufficiently. The statement should also affirm that the designated
authority is responsible for continued maintenance and testing of the ISCP. This statement should be
approved and signed by the system designated authority. Space should be provided for the designated
authority to sign, along with any other applicable approving signatures. Sample language is provided
below:
As the designated authority for the Payroll System, I hereby certify that the information system
contingency plan (ISCP) is complete, and that the information contained in this ISCP provides an
accurate representation of the application, its hardware, software, and telecommunication components. I
further certify that this document identifies the criticality of the system as it relates to the mission of the
Department for Wildlife, and that the recovery strategies identified will provide the ability to recover the
system functionality in the most expedient and cost-beneficial method in keeping with its level of
criticality.
I further attest that this ISCP for Payroll System will be tested at least annually. This plan was last tested
on September 5th 2019; the test, training, and exercise (TT&E) material associated with this test can be
found {TT&E results appendix or location}. This document will be modified as changes occur and will
remain under version control, in accordance with Department for Wildlife’s contingency planning policy.
________________________________________ ________________________
{System Owner Name} Date
{System Owner Title}
Provide a statement in accordance with the agency’s contingency planning policy to affirm that the ISCP
is complete and has been tested sufficiently. The statement should also affirm that the designated
authority is responsible for continued maintenance and testing of the ISCP. This statement should be
approved and signed by the system designated authority. Space should be provided for the designated
authority to sign, along with any other applicable approving signatures. Sample language is provided
below:
As the designated authority for the Payroll System, I hereby certify that the information system
contingency plan (ISCP) is complete, and that the information contained in this ISCP provides an
accurate representation of the application, its hardware, software, and telecommunication components. I
further certify that this document identifies the criticality of the system as it relates to the mission of the
Department for Wildlife, and that the recovery strategies identified will provide the ability to recover the
system functionality in the most expedient and cost-beneficial method in keeping with its level of
criticality.
I further attest that this ISCP for Payroll System will be tested at least annually. This plan was last tested
on September 5th 2019; the test, training, and exercise (TT&E) material associated with this test can be
found {TT&E results appendix or location}. This document will be modified as changes occur and will
remain under version control, in accordance with Department for Wildlife’s contingency planning policy.
________________________________________ ________________________
{System Owner Name} Date
{System Owner Title}
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction
Information systems are vital to Department for Wildlife mission/business processes; therefore, it is
critical that services provided by the Payroll System are able to operate effectively without excessive
interruption. This Information System Contingency Plan (ISCP) establishes comprehensive procedures to
recover Department for Wildlife quickly and effectively following a service disruption.
1.1 Background
This Payroll System ISCP- establishes procedures to recover the Payroll System following a disruption.
The following recovery plan objectives have been established:
Maximize the effectiveness of contingency operations through an established plan that
consists of the following phases:
o Activation and Notification phase to activate the plan and determine the extent of damage;
o Recovery phase to restore the Payroll System operations; and
o Reconstitution phase to ensure that the Payroll System is validated through testing and that
normal operations are resumed.
Identify the activities, resources, and procedures to carry out the Payroll System processing
requirements during prolonged interruptions to normal operations.
Assign responsibilities to designated Department for Wildlife personnel and provide guidance
for recovering The Payroll System during prolonged periods of interruption to normal
operations.
Ensure coordination with other personnel responsible for Department for Wildlife
contingency planning strategies. Ensure coordination with external points of contact and
vendors associated with The Payroll System and execution of this plan.
1.2 Scope
This ISCP has been developed for The Payroll System, which is classified as a moderate-impact system,
in accordance with Federal Information Processing Standards (FIPS) 199 – Standards for Security
Categorization of Federal Information and Information Systems. Procedures in this ISCP are for
moderate-impact systems and designed to recover The Payroll System within between 2 and 36 RTO
hours. This plan does not address replacement or purchase of new equipment, short-term disruptions
lasting less than 6 hours, or loss of data at the onsite facility or at the user-desktop levels.
1.3 Assumptions
The following assumptions were used when developing this ISCP:
The Payroll System has been established as a moderate-impact system, in accordance with
FIPS 199.
Alternate processing sites and offsite storage are required and have been established for this
system.
Current backups of the system software and data are intact and available at the offsite storage
facility in Boston, MA.
Alternate facilities have been established at New York, WA and are available if needed for
relocation of The Payroll System.
Information systems are vital to Department for Wildlife mission/business processes; therefore, it is
critical that services provided by the Payroll System are able to operate effectively without excessive
interruption. This Information System Contingency Plan (ISCP) establishes comprehensive procedures to
recover Department for Wildlife quickly and effectively following a service disruption.
1.1 Background
This Payroll System ISCP- establishes procedures to recover the Payroll System following a disruption.
The following recovery plan objectives have been established:
Maximize the effectiveness of contingency operations through an established plan that
consists of the following phases:
o Activation and Notification phase to activate the plan and determine the extent of damage;
o Recovery phase to restore the Payroll System operations; and
o Reconstitution phase to ensure that the Payroll System is validated through testing and that
normal operations are resumed.
Identify the activities, resources, and procedures to carry out the Payroll System processing
requirements during prolonged interruptions to normal operations.
Assign responsibilities to designated Department for Wildlife personnel and provide guidance
for recovering The Payroll System during prolonged periods of interruption to normal
operations.
Ensure coordination with other personnel responsible for Department for Wildlife
contingency planning strategies. Ensure coordination with external points of contact and
vendors associated with The Payroll System and execution of this plan.
1.2 Scope
This ISCP has been developed for The Payroll System, which is classified as a moderate-impact system,
in accordance with Federal Information Processing Standards (FIPS) 199 – Standards for Security
Categorization of Federal Information and Information Systems. Procedures in this ISCP are for
moderate-impact systems and designed to recover The Payroll System within between 2 and 36 RTO
hours. This plan does not address replacement or purchase of new equipment, short-term disruptions
lasting less than 6 hours, or loss of data at the onsite facility or at the user-desktop levels.
1.3 Assumptions
The following assumptions were used when developing this ISCP:
The Payroll System has been established as a moderate-impact system, in accordance with
FIPS 199.
Alternate processing sites and offsite storage are required and have been established for this
system.
Current backups of the system software and data are intact and available at the offsite storage
facility in Boston, MA.
Alternate facilities have been established at New York, WA and are available if needed for
relocation of The Payroll System.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The The Payroll System is inoperable at the Department for Wildlife and cannot be recovered
within between 2 and 36 RTO hours.
Key the Payroll System personnel have been identified and trained in their emergency
response and recovery roles; they are available to activate the The Payroll System Contingency
Plan.
Additional assumptions as appropriate.
The Payroll System Contingency Plan does not apply to the following situations:
Overall recovery and continuity of mission/business operations. The Business Continuity
Plan (BCP) and Continuity of Operations Plan (COOP) address continuity of business operations.
Emergency evacuation of personnel. The Occupant Emergency Plan (OEP) addresses
employee evacuation.
Any additional constraints and associated plans should be added to this list.
2. Concept of Operations
The Concept of Operations section provides details about The Payroll System , an overview of the three
phases of the ISCP (Activation and Notification, Recovery, and Reconstitution), and a description of roles
and responsibilities of Department for Wildlife personnel during a contingency activation.
2.1 System Description
The overall architecture of the PS is a client- sever Architecture; the company has several divisions and
different branches distributed within one city and also in other cities. The PS is based on a cloud
architecture in which the application is installed within a hybrid cloud system to enable access to
information from any department/ branch from the central Human Resource office located at the head
office of the company. The application is thus implemented as a SaaS (software as a service) and also has
a physical server located in the company’s data center with a bridge to the public cloud. It is implemented
in a WAN (wide area network) and linked to the LANs (local area networks) found at each branch and
department. The PS gathers employee data from the attendance management system as well as from the
CRM/ sales management system (for sales staff) and updates these to the central database which contains
detailed employee information and data, including role, remuneration rate, benefits, leave days,
performance bonuses, qualifications, trainings attended, as well as personal details. When a new
employee is hired, all their information is entered into the main database and are assigned a unique
employee number as well as their pay rates, bonuses, and leave days. Each time an employee checks in to
work, they must swipe or touch a finger print employee attendance system that clocks in the time they
started work, and they swipe or touch it when they leave or at the end of the work day. This information
is then automatically uploaded and updated to the hybrid cloud worked employee and HR database over a
WAN. At the end of a given period or week; the payroll system automatically computes the employee
pay; the HR officer can add parameters for additional bonuses, commissions, or leave days and these
compute the employee payment. The system then automatically makes statutory deductions including
taxes, membership fees, or loans advanced to the employee and computes the final pay, which can be
printed.
2.2 Overview of Three Phases
within between 2 and 36 RTO hours.
Key the Payroll System personnel have been identified and trained in their emergency
response and recovery roles; they are available to activate the The Payroll System Contingency
Plan.
Additional assumptions as appropriate.
The Payroll System Contingency Plan does not apply to the following situations:
Overall recovery and continuity of mission/business operations. The Business Continuity
Plan (BCP) and Continuity of Operations Plan (COOP) address continuity of business operations.
Emergency evacuation of personnel. The Occupant Emergency Plan (OEP) addresses
employee evacuation.
Any additional constraints and associated plans should be added to this list.
2. Concept of Operations
The Concept of Operations section provides details about The Payroll System , an overview of the three
phases of the ISCP (Activation and Notification, Recovery, and Reconstitution), and a description of roles
and responsibilities of Department for Wildlife personnel during a contingency activation.
2.1 System Description
The overall architecture of the PS is a client- sever Architecture; the company has several divisions and
different branches distributed within one city and also in other cities. The PS is based on a cloud
architecture in which the application is installed within a hybrid cloud system to enable access to
information from any department/ branch from the central Human Resource office located at the head
office of the company. The application is thus implemented as a SaaS (software as a service) and also has
a physical server located in the company’s data center with a bridge to the public cloud. It is implemented
in a WAN (wide area network) and linked to the LANs (local area networks) found at each branch and
department. The PS gathers employee data from the attendance management system as well as from the
CRM/ sales management system (for sales staff) and updates these to the central database which contains
detailed employee information and data, including role, remuneration rate, benefits, leave days,
performance bonuses, qualifications, trainings attended, as well as personal details. When a new
employee is hired, all their information is entered into the main database and are assigned a unique
employee number as well as their pay rates, bonuses, and leave days. Each time an employee checks in to
work, they must swipe or touch a finger print employee attendance system that clocks in the time they
started work, and they swipe or touch it when they leave or at the end of the work day. This information
is then automatically uploaded and updated to the hybrid cloud worked employee and HR database over a
WAN. At the end of a given period or week; the payroll system automatically computes the employee
pay; the HR officer can add parameters for additional bonuses, commissions, or leave days and these
compute the employee payment. The system then automatically makes statutory deductions including
taxes, membership fees, or loans advanced to the employee and computes the final pay, which can be
printed.
2.2 Overview of Three Phases

This ISCP has been developed to recover and reconstitute the Payroll Systemusing a three-phased
approach. This approach ensures that system recovery and reconstitution efforts are performed in a
methodical sequence to maximize the effectiveness of the recovery and reconstitution efforts and
minimize system outage time due to errors and omissions.
The three system recovery phases are:
Activation and Notification Phase – Activation of the ISCP occurs after a disruption or outage that may
reasonably extend beyond the RTO established for a system. The outage event may result in severe
damage to the facility that houses the system, severe damage or loss of equipment, or other damage that
typically results in long-term loss.
Once the ISCP is activated, system owners and users are notified of a possible long-term outage, and a
thorough outage assessment is performed for the system. Information from the outage assessment is
presented to system owners and may be used to modify recovery procedures specific to the cause of the
outage.
Recovery Phase – The Recovery phase details the activities and procedures for recovery of the affected
system. Activities and procedures are written at a level that an appropriately skilled technician can
recover the system without intimate system knowledge. This phase includes notification and awareness
escalation procedures for communication of recovery status to system owners and users.
Reconstitution – The Reconstitution phase defines the actions taken to test and validate system capability
and functionality at the original or new permanent location. This phase consists of two major activities:
validating successful reconstitution and deactivation of the plan.
During validation, the system is tested and validated as operational prior to returning operation to its
normal state. Validation procedures may include functionality or regression testing, concurrent
processing, and/or data validation. The system is declared recovered and operational by system owners
upon successful completion of validation testing.
Deactivation includes activities to notify users of system operational status. This phase also addresses
recovery effort documentation, activity log finalization, incorporation of lessons learned into plan
updates, and readying resources for any future events.
2.3 Roles and Responsibilities
The ISCP Director, the IT manager, working with the IT team (managers and their support staff) will be
responsible for developing contingency policies and plans for Payroll System recovery.
Each IT manager will ensure their physical hardware are running efficiently while the System Analyst
will ensure the system is backed up and business processes restored in the event of crashes/ Payroll
System unavailability
The network engineer will provide an alternate network access system during design and ensure this
system automatically becomes operational should be primary network system fail. The network will also
have a cloud component of Infrastructure as a Service (IaaS) to ensure the network continues to run even
when the physical network is disrupted
3. Activation and Notification
approach. This approach ensures that system recovery and reconstitution efforts are performed in a
methodical sequence to maximize the effectiveness of the recovery and reconstitution efforts and
minimize system outage time due to errors and omissions.
The three system recovery phases are:
Activation and Notification Phase – Activation of the ISCP occurs after a disruption or outage that may
reasonably extend beyond the RTO established for a system. The outage event may result in severe
damage to the facility that houses the system, severe damage or loss of equipment, or other damage that
typically results in long-term loss.
Once the ISCP is activated, system owners and users are notified of a possible long-term outage, and a
thorough outage assessment is performed for the system. Information from the outage assessment is
presented to system owners and may be used to modify recovery procedures specific to the cause of the
outage.
Recovery Phase – The Recovery phase details the activities and procedures for recovery of the affected
system. Activities and procedures are written at a level that an appropriately skilled technician can
recover the system without intimate system knowledge. This phase includes notification and awareness
escalation procedures for communication of recovery status to system owners and users.
Reconstitution – The Reconstitution phase defines the actions taken to test and validate system capability
and functionality at the original or new permanent location. This phase consists of two major activities:
validating successful reconstitution and deactivation of the plan.
During validation, the system is tested and validated as operational prior to returning operation to its
normal state. Validation procedures may include functionality or regression testing, concurrent
processing, and/or data validation. The system is declared recovered and operational by system owners
upon successful completion of validation testing.
Deactivation includes activities to notify users of system operational status. This phase also addresses
recovery effort documentation, activity log finalization, incorporation of lessons learned into plan
updates, and readying resources for any future events.
2.3 Roles and Responsibilities
The ISCP Director, the IT manager, working with the IT team (managers and their support staff) will be
responsible for developing contingency policies and plans for Payroll System recovery.
Each IT manager will ensure their physical hardware are running efficiently while the System Analyst
will ensure the system is backed up and business processes restored in the event of crashes/ Payroll
System unavailability
The network engineer will provide an alternate network access system during design and ensure this
system automatically becomes operational should be primary network system fail. The network will also
have a cloud component of Infrastructure as a Service (IaaS) to ensure the network continues to run even
when the physical network is disrupted
3. Activation and Notification
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The Activation and Notification Phase defines initial actions taken once a Payroll System disruption has
been detected or appears to be imminent. This phase includes activities to notify recovery personnel,
conduct an outage assessment, and activate the ISCP. At the completion of the Activation and
Notification Phase, Payroll SystemISCP staff will be prepared to perform recovery measures to restore
system functions.
3.1 Activation Criteria and Procedure
The Payroll System ISCP may be activated if one or more of the following criteria are met:
1. The type of outage indicates Payroll System application will be down for more than Two RTO
hours;
2. The facility housing the Payroll System is damaged and may not be available within 24 RTO
hours; and
3. The Payroll System network access is down for more than 15 minutes.
The following persons or roles may activate the ISCP if one or more of these criteria are met:
The IT support staff at each division/ branch/ department
IT manager at every respective branch
3.2 Notification
The first step upon activation of the Payroll System ISCP is notification of appropriate business and
system support personnel. Contact information for appropriate POCs is included in ISCP contact list.
For Payroll System, the following method and procedure for notifications are used:
The users notify their relevant IT support staff/ managers of a problem through a phone call; the notified
IT support staff then checks the problem and esclataes the issue to their respective line/ IT managers who
will then inform the ICSP Director and Overall IT Manager of the problem and appropriate actions
initiated
3.3 Outage Assessment
Following notification, a thorough outage assessment is necessary to determine the extent of the
disruption, any damage, and expected recovery time. This outage assessment is conducted by the ICSP
IT Support Staff. Assessment results are provided to the ISCP Coordinator to assist in the coordination of
the recovery of the Payroll System. The system will be evaluated through a detailed network analysis,
evaluation of its performance, logs, and user logs to determine cause of outage, include network
monitoring and activity; these will help determine the next course of action.
been detected or appears to be imminent. This phase includes activities to notify recovery personnel,
conduct an outage assessment, and activate the ISCP. At the completion of the Activation and
Notification Phase, Payroll SystemISCP staff will be prepared to perform recovery measures to restore
system functions.
3.1 Activation Criteria and Procedure
The Payroll System ISCP may be activated if one or more of the following criteria are met:
1. The type of outage indicates Payroll System application will be down for more than Two RTO
hours;
2. The facility housing the Payroll System is damaged and may not be available within 24 RTO
hours; and
3. The Payroll System network access is down for more than 15 minutes.
The following persons or roles may activate the ISCP if one or more of these criteria are met:
The IT support staff at each division/ branch/ department
IT manager at every respective branch
3.2 Notification
The first step upon activation of the Payroll System ISCP is notification of appropriate business and
system support personnel. Contact information for appropriate POCs is included in ISCP contact list.
For Payroll System, the following method and procedure for notifications are used:
The users notify their relevant IT support staff/ managers of a problem through a phone call; the notified
IT support staff then checks the problem and esclataes the issue to their respective line/ IT managers who
will then inform the ICSP Director and Overall IT Manager of the problem and appropriate actions
initiated
3.3 Outage Assessment
Following notification, a thorough outage assessment is necessary to determine the extent of the
disruption, any damage, and expected recovery time. This outage assessment is conducted by the ICSP
IT Support Staff. Assessment results are provided to the ISCP Coordinator to assist in the coordination of
the recovery of the Payroll System. The system will be evaluated through a detailed network analysis,
evaluation of its performance, logs, and user logs to determine cause of outage, include network
monitoring and activity; these will help determine the next course of action.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4. Recovery
The Recovery Phase provides formal recovery operations that begin after the ISCP has been activated,
outage assessments have been completed (if possible), personnel have been notified, and appropriate
teams have been mobilized. Recovery Phase activities focus on implementing recovery strategies to
restore system capabilities, repair damage, and resume operational capabilities at the original or an
alternate location. At the completion of the Recovery Phase, Payroll System will be functional and
capable of performing the functions identified in Section 2.1 of this plan.
4.1 Sequence of Recovery Activities
The following activities occur during recovery of Payroll System:
1. Identify the recovery location ;
2. Identify the necessary resources to undertake recovery procedures;
3. Retrieve the cloud based or private cloud backup and system installation media;
4. Recover the server hardware and operating system (if necessary);
5. Restore operations as soon as possible, and
6. Recover the system from backup and system installation media.
4.2 Recovery Procedures
The following procedures are provided for recovery of Payroll System at the original or established
alternate location. Recovery procedures are outlined per team and should be executed in the sequence
presented to maintain an efficient recovery effort.
The mirrored application system data will be restored and cloud backup restored to ensure business
process continuity while the physical recovery takes place
4.3 Recovery Escalation Notices/Awareness
The users notify their relevant IT support staff/ managers of a problem through a phone call; the notified
IT support staff then checks the problem and esclataes the issue to their respective line/ IT managers who
will then inform the ICSP Director and Overall IT Manager of the problem and appropriate actions
initiated
5. Reconstitution
Reconstitution is the process by which recovery activities are completed and normal system operations
are resumed. If the original facility is unrecoverable, the activities in this phase can also be applied to
preparing a new permanent location to support system processing requirements. A determination must be
made on whether the system has undergone significant change and will require reassessment and
reauthorization. The phase consists of two major activities: validating successful reconstitution and
deactivation of the plan.
5.1 Validation Data Testing
The Recovery Phase provides formal recovery operations that begin after the ISCP has been activated,
outage assessments have been completed (if possible), personnel have been notified, and appropriate
teams have been mobilized. Recovery Phase activities focus on implementing recovery strategies to
restore system capabilities, repair damage, and resume operational capabilities at the original or an
alternate location. At the completion of the Recovery Phase, Payroll System will be functional and
capable of performing the functions identified in Section 2.1 of this plan.
4.1 Sequence of Recovery Activities
The following activities occur during recovery of Payroll System:
1. Identify the recovery location ;
2. Identify the necessary resources to undertake recovery procedures;
3. Retrieve the cloud based or private cloud backup and system installation media;
4. Recover the server hardware and operating system (if necessary);
5. Restore operations as soon as possible, and
6. Recover the system from backup and system installation media.
4.2 Recovery Procedures
The following procedures are provided for recovery of Payroll System at the original or established
alternate location. Recovery procedures are outlined per team and should be executed in the sequence
presented to maintain an efficient recovery effort.
The mirrored application system data will be restored and cloud backup restored to ensure business
process continuity while the physical recovery takes place
4.3 Recovery Escalation Notices/Awareness
The users notify their relevant IT support staff/ managers of a problem through a phone call; the notified
IT support staff then checks the problem and esclataes the issue to their respective line/ IT managers who
will then inform the ICSP Director and Overall IT Manager of the problem and appropriate actions
initiated
5. Reconstitution
Reconstitution is the process by which recovery activities are completed and normal system operations
are resumed. If the original facility is unrecoverable, the activities in this phase can also be applied to
preparing a new permanent location to support system processing requirements. A determination must be
made on whether the system has undergone significant change and will require reassessment and
reauthorization. The phase consists of two major activities: validating successful reconstitution and
deactivation of the plan.
5.1 Validation Data Testing

Validation data testing is the process of testing and validating data to ensure that data files or databases
have been recovered completely at the permanent location. The following procedures will be used to
determine that the data is complete and current to the last available backup:
The recovered data will be checked for their digital signatures, size, and functionality to be equivalent to
the mirrored backup of the application.
5.2 Validation Functionality Testing
Validation functionality testing is the process of verifying that recovered Payroll System functionality has
been tested, and the system is ready to return to normal operations.
Manual system testing will be done by testing the employee attendance capture system, database
functionality, and ability of system to calculate payments and make deductions as well as generate
requisite reports. Automated testing will also be done for the functionality of the entire Payroll System
5.3 Recovery Declaration
Upon successfully completing testing and validation, the IT/ ISCP Director will formally declare
recovery efforts complete, and that Payroll System is in normal operations. Payroll System business and
technical POCs will be notified of the declaration by the ISCP Coordinator.
5.4 Notifications (users)
Upon return to normal system operations, Payroll System users will be notified by the IT manager using
phone calls, e-mail and broadcast messages.
5.5 Cleanup
The cloud services and mirrored servers used while the system was being restored/ recovered will be
disengaged and old recovery points used deleted. The system, after being tested, will be restored to its
initial architecture and connected to the cloud where real time backup will continue
5.6 Offsite Data Storage
The system data will be backed up in physical mirrored servers, disks set up in RAID 6 architecture, and
virtual servers implemented and backed up in the cloud.
5.7 Data Backup
A full system backup will be implemented to the cloud where data is stored in four different geographic
locations and backup done off site using mirroring as well as at the main data center
have been recovered completely at the permanent location. The following procedures will be used to
determine that the data is complete and current to the last available backup:
The recovered data will be checked for their digital signatures, size, and functionality to be equivalent to
the mirrored backup of the application.
5.2 Validation Functionality Testing
Validation functionality testing is the process of verifying that recovered Payroll System functionality has
been tested, and the system is ready to return to normal operations.
Manual system testing will be done by testing the employee attendance capture system, database
functionality, and ability of system to calculate payments and make deductions as well as generate
requisite reports. Automated testing will also be done for the functionality of the entire Payroll System
5.3 Recovery Declaration
Upon successfully completing testing and validation, the IT/ ISCP Director will formally declare
recovery efforts complete, and that Payroll System is in normal operations. Payroll System business and
technical POCs will be notified of the declaration by the ISCP Coordinator.
5.4 Notifications (users)
Upon return to normal system operations, Payroll System users will be notified by the IT manager using
phone calls, e-mail and broadcast messages.
5.5 Cleanup
The cloud services and mirrored servers used while the system was being restored/ recovered will be
disengaged and old recovery points used deleted. The system, after being tested, will be restored to its
initial architecture and connected to the cloud where real time backup will continue
5.6 Offsite Data Storage
The system data will be backed up in physical mirrored servers, disks set up in RAID 6 architecture, and
virtual servers implemented and backed up in the cloud.
5.7 Data Backup
A full system backup will be implemented to the cloud where data is stored in four different geographic
locations and backup done off site using mirroring as well as at the main data center
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5.8 Event Documentation
The time the event began, the initial reporting person, the actions taken, the escalation procedures used,
the identified problems, and the solutions implemented are recorded. The persons involved are also
documented, and the time when normal functionality was restored also reported. Any mitigation measures
to ensure the same is not experienced in future are also documented and stored according to the
organization documentation policy. The functionality testing procedures along with test results after
restoration are also documented
5.9 Deactivation
Once all activities have been completed and documentation has been updated, the ISCP Director will
formally deactivate the ISCP recovery and reconstitution effort. Notification of this declaration will be
provided to all business and technical POCs.
The time the event began, the initial reporting person, the actions taken, the escalation procedures used,
the identified problems, and the solutions implemented are recorded. The persons involved are also
documented, and the time when normal functionality was restored also reported. Any mitigation measures
to ensure the same is not experienced in future are also documented and stored according to the
organization documentation policy. The functionality testing procedures along with test results after
restoration are also documented
5.9 Deactivation
Once all activities have been completed and documentation has been updated, the ISCP Director will
formally deactivate the ISCP recovery and reconstitution effort. Notification of this declaration will be
provided to all business and technical POCs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SUGGESTED APPENDICES
ISCP appendices included should be based on system and plan requirements. The following appendices
are recommended:
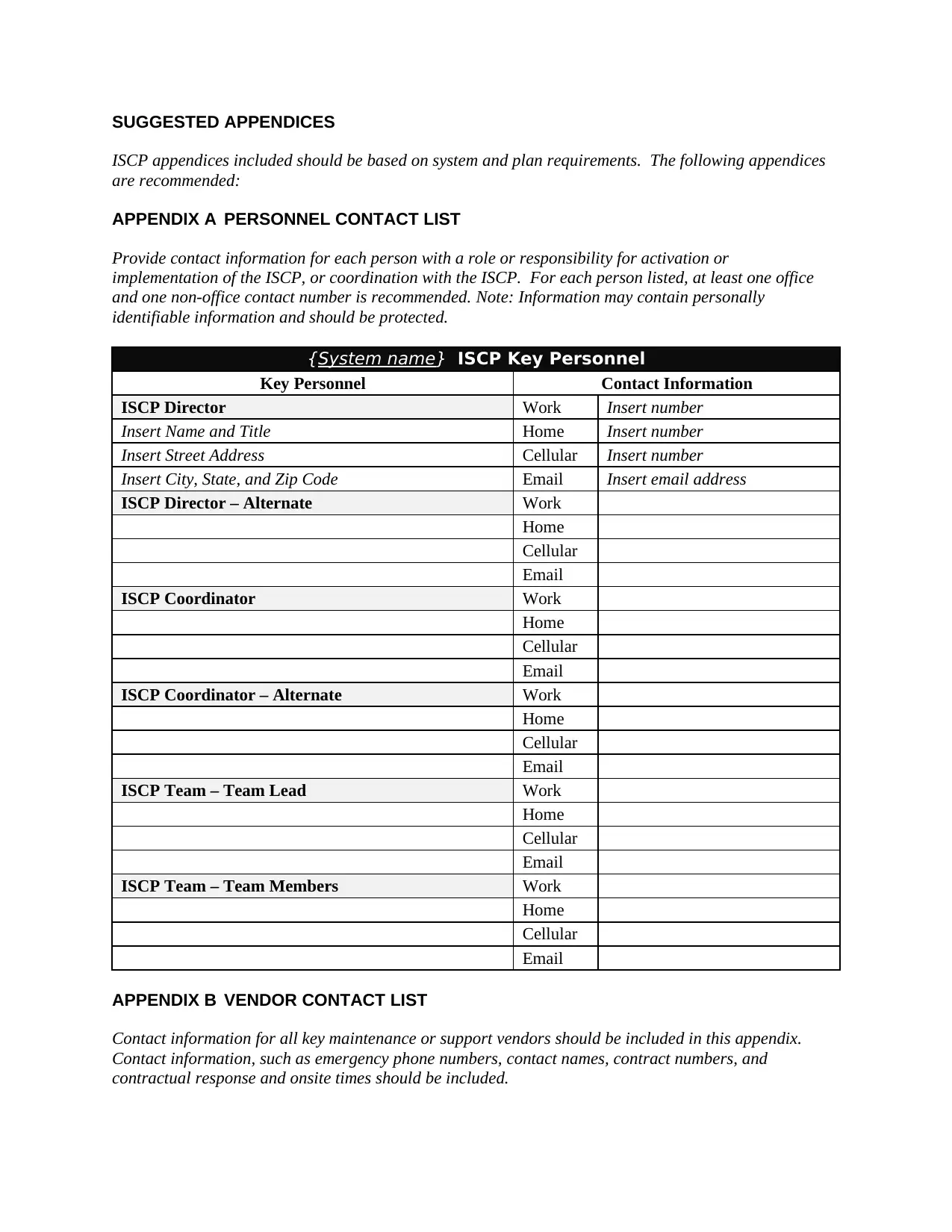
APPENDIX A PERSONNEL CONTACT LIST
Provide contact information for each person with a role or responsibility for activation or
implementation of the ISCP, or coordination with the ISCP. For each person listed, at least one office
and one non-office contact number is recommended. Note: Information may contain personally
identifiable information and should be protected.
{System name} ISCP Key Personnel
Key Personnel Contact Information
ISCP Director Work Insert number
Insert Name and Title Home Insert number
Insert Street Address Cellular Insert number
Insert City, State, and Zip Code Email Insert email address
ISCP Director – Alternate Work
Home
Cellular
Email
ISCP Coordinator Work
Home
Cellular
Email
ISCP Coordinator – Alternate Work
Home
Cellular
Email
ISCP Team – Team Lead Work
Home
Cellular
Email
ISCP Team – Team Members Work
Home
Cellular
Email
APPENDIX B VENDOR CONTACT LIST
Contact information for all key maintenance or support vendors should be included in this appendix.
Contact information, such as emergency phone numbers, contact names, contract numbers, and
contractual response and onsite times should be included.
ISCP appendices included should be based on system and plan requirements. The following appendices
are recommended:
APPENDIX A PERSONNEL CONTACT LIST
Provide contact information for each person with a role or responsibility for activation or
implementation of the ISCP, or coordination with the ISCP. For each person listed, at least one office
and one non-office contact number is recommended. Note: Information may contain personally
identifiable information and should be protected.
{System name} ISCP Key Personnel
Key Personnel Contact Information
ISCP Director Work Insert number
Insert Name and Title Home Insert number
Insert Street Address Cellular Insert number
Insert City, State, and Zip Code Email Insert email address
ISCP Director – Alternate Work
Home
Cellular
ISCP Coordinator Work
Home
Cellular
ISCP Coordinator – Alternate Work
Home
Cellular
ISCP Team – Team Lead Work
Home
Cellular
ISCP Team – Team Members Work
Home
Cellular
APPENDIX B VENDOR CONTACT LIST
Contact information for all key maintenance or support vendors should be included in this appendix.
Contact information, such as emergency phone numbers, contact names, contract numbers, and
contractual response and onsite times should be included.
APPENDIX C DETAILED RECOVERY PROCEDURES
This appendix includes the detailed recovery procedures for the system, which may include items such as:
Keystroke-level recovery steps;
System installation instructions from tape, CD, or other media;
Required configuration settings or changes;
Recovery of data from tape and audit logs; and
Other system recovery procedures, as appropriate.
If the system relies totally on another group or system for its recovery and reconstitution (such as a
mainframe system), information provided should include contact information and locations of detailed
recovery and reconstitution procedures for that supporting system.
APPENDIX D ALTERNATE PROCESSING PROCEDURES
This section should identify any alternate manual or technical processing procedures available that allow
the business unit to continue some processing of information that would normally be done by the affected
system. Examples of alternate processes include manual forms processing, input into workstations to
store data until it can be uploaded and processed, or queuing of data input.
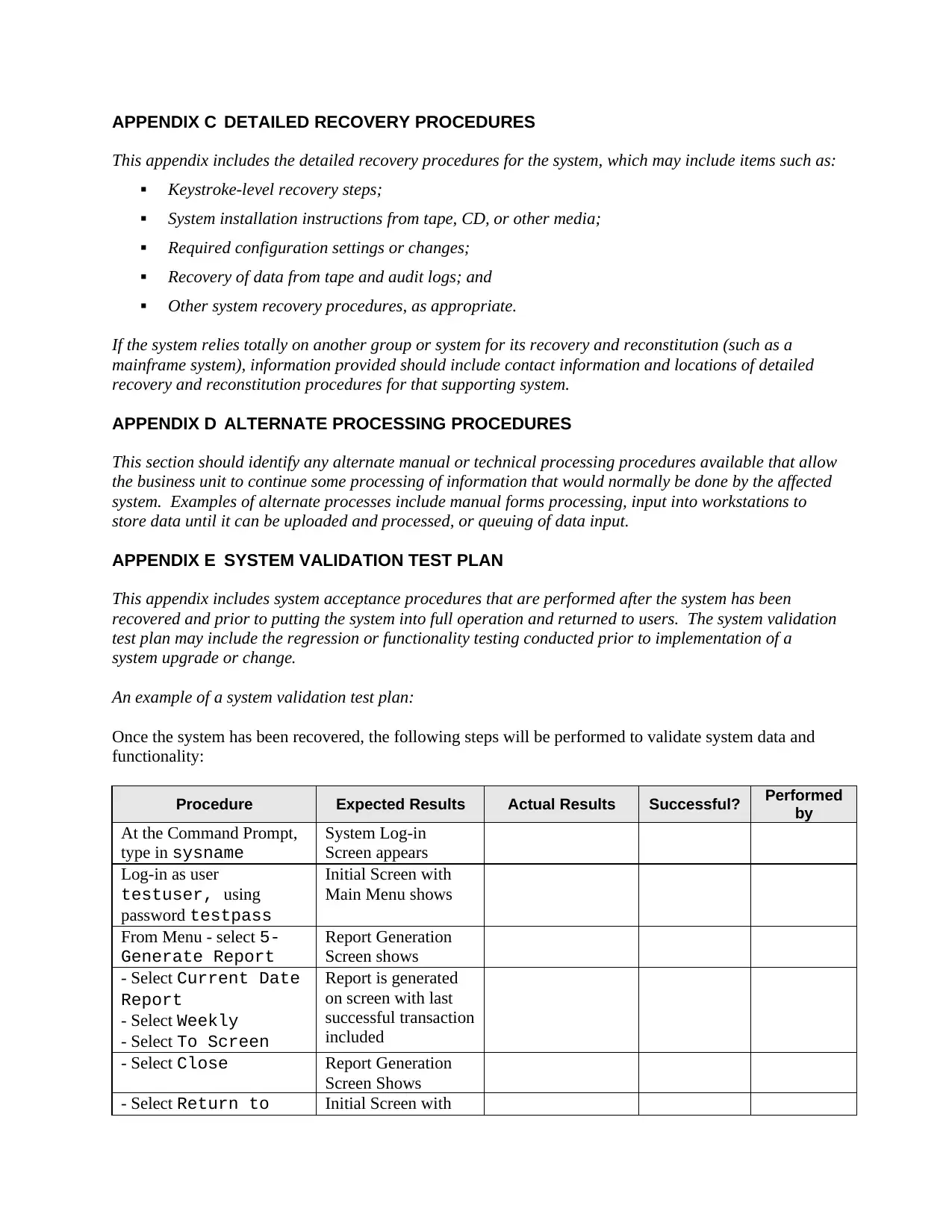
APPENDIX E SYSTEM VALIDATION TEST PLAN
This appendix includes system acceptance procedures that are performed after the system has been
recovered and prior to putting the system into full operation and returned to users. The system validation
test plan may include the regression or functionality testing conducted prior to implementation of a
system upgrade or change.
An example of a system validation test plan:
Once the system has been recovered, the following steps will be performed to validate system data and
functionality:
Procedure Expected Results Actual Results Successful? Performed
by
At the Command Prompt,
type in sysname
System Log-in
Screen appears
Log-in as user
testuser, using
password testpass
Initial Screen with
Main Menu shows
From Menu - select 5-
Generate Report
Report Generation
Screen shows
- Select Current Date
Report
- Select Weekly
- Select To Screen
Report is generated
on screen with last
successful transaction
included
- Select Close Report Generation
Screen Shows
- Select Return to Initial Screen with
This appendix includes the detailed recovery procedures for the system, which may include items such as:
Keystroke-level recovery steps;
System installation instructions from tape, CD, or other media;
Required configuration settings or changes;
Recovery of data from tape and audit logs; and
Other system recovery procedures, as appropriate.
If the system relies totally on another group or system for its recovery and reconstitution (such as a
mainframe system), information provided should include contact information and locations of detailed
recovery and reconstitution procedures for that supporting system.
APPENDIX D ALTERNATE PROCESSING PROCEDURES
This section should identify any alternate manual or technical processing procedures available that allow
the business unit to continue some processing of information that would normally be done by the affected
system. Examples of alternate processes include manual forms processing, input into workstations to
store data until it can be uploaded and processed, or queuing of data input.
APPENDIX E SYSTEM VALIDATION TEST PLAN
This appendix includes system acceptance procedures that are performed after the system has been
recovered and prior to putting the system into full operation and returned to users. The system validation
test plan may include the regression or functionality testing conducted prior to implementation of a
system upgrade or change.
An example of a system validation test plan:
Once the system has been recovered, the following steps will be performed to validate system data and
functionality:
Procedure Expected Results Actual Results Successful? Performed
by
At the Command Prompt,
type in sysname
System Log-in
Screen appears
Log-in as user
testuser, using
password testpass
Initial Screen with
Main Menu shows
From Menu - select 5-
Generate Report
Report Generation
Screen shows
- Select Current Date
Report
- Select Weekly
- Select To Screen
Report is generated
on screen with last
successful transaction
included
- Select Close Report Generation
Screen Shows
- Select Return to Initial Screen with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




