National University Enrollment System: Object and Data Modeling Report
VerifiedAdded on 2023/01/03
|14
|3010
|50
Report
AI Summary
This report presents a comprehensive analysis of the object and data modeling for a university enrollment system. It begins by identifying and describing the functional and non-functional requirements, crucial for the system's operation and security. The report then details the use cases, illustrating the interactions between students, administrators, and the system, and includes use case diagrams to visualize these interactions. A fully developed Use Case description is provided for a key process within the system. Furthermore, the report includes a UML domain model class diagram, offering a detailed representation of the system's data structure and relationships. Finally, event-partitioned system models are developed to illustrate the system's behavior in response to various events. The report concludes with a bibliography of the sources used.

Running head: OBJECT AND DATA MODELLING
Object and Data Modelling
Name of the Student
Name of the University
Author’s note:
Object and Data Modelling
Name of the Student
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OBJECT AND DATA MODELLING
Table of Contents
1. Functional and Non-Functional Requirements:...........................................................................2
2. Use Cases:....................................................................................................................................5
3. UML Domain Model Class Diagram:.........................................................................................9
4. Event Partitioned System Model:..............................................................................................10
Bibliography:.................................................................................................................................11
Table of Contents
1. Functional and Non-Functional Requirements:...........................................................................2
2. Use Cases:....................................................................................................................................5
3. UML Domain Model Class Diagram:.........................................................................................9
4. Event Partitioned System Model:..............................................................................................10
Bibliography:.................................................................................................................................11
2OBJECT AND DATA MODELLING
1. Functional and Non-Functional Requirements:
Functional requirements Non-functional requirements
The selection of the major is one of the functional
requirements. When a student gets an enrollment
in a National university the first thing that is
needed to be done is selecting the major. The
university offers an interactive interface that
allows the student to select from the available list
of majors. The student s not allowed selecting
more than one major. Although the list of the
majors other than the majors offered by the
university cannot be available to the student in the
interface. The student is thus applicable of
selecting from a certain list that is offered to them
(Kurtanović & Maalej, 2017).
The security of such system is very important.
This is one of the major requirement in the non-
functionality areas. The details of the cards are
stored in the system in secure manner and it
should ensure that the information is not visible to
a third person. The data that are related t the
transaction need to be stored in a safe way that
will not not b assessed by anyone. The
methodology of the encryption and decryption
process need to be strong that cannot be hacked.
The encrypted data need to be decrypted by the
management and no one in the middle of such
process can hamper the process.
The next step after the selection of the major is
the selection of the course. After that the user is
redirected to the next page where they have to
select the course. These courses are the
subcategories of the majors that is selected by the
student. The number of courses s also limited as
the University offered only certain courses. The
student can redo or undo different course that is
selected.
The flow o the data within the system need to be
real time. The real time term means that when an
user enter a data it need to be visible before it is
entered in the database. The flow of th data within
the system need to be fast and accessible by the
users. The refreshing option in the system will
allow the user to see the updated information
every-time they access the database.
1. Functional and Non-Functional Requirements:
Functional requirements Non-functional requirements
The selection of the major is one of the functional
requirements. When a student gets an enrollment
in a National university the first thing that is
needed to be done is selecting the major. The
university offers an interactive interface that
allows the student to select from the available list
of majors. The student s not allowed selecting
more than one major. Although the list of the
majors other than the majors offered by the
university cannot be available to the student in the
interface. The student is thus applicable of
selecting from a certain list that is offered to them
(Kurtanović & Maalej, 2017).
The security of such system is very important.
This is one of the major requirement in the non-
functionality areas. The details of the cards are
stored in the system in secure manner and it
should ensure that the information is not visible to
a third person. The data that are related t the
transaction need to be stored in a safe way that
will not not b assessed by anyone. The
methodology of the encryption and decryption
process need to be strong that cannot be hacked.
The encrypted data need to be decrypted by the
management and no one in the middle of such
process can hamper the process.
The next step after the selection of the major is
the selection of the course. After that the user is
redirected to the next page where they have to
select the course. These courses are the
subcategories of the majors that is selected by the
student. The number of courses s also limited as
the University offered only certain courses. The
student can redo or undo different course that is
selected.
The flow o the data within the system need to be
real time. The real time term means that when an
user enter a data it need to be visible before it is
entered in the database. The flow of th data within
the system need to be fast and accessible by the
users. The refreshing option in the system will
allow the user to see the updated information
every-time they access the database.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3OBJECT AND DATA MODELLING
One of the important step of the process is the
login step. The important function that the
interactive system need to offer is the login. The
user will need to enter certain credential
information to login to their account. The user
have the right of accessing there account from
anywhere and by using any system. These also
make the process of detecting the user little
critical. The different activities that is performed
by the user in their particular account to remain
secure. They can keep a track on their activities
and can also save the same. The facility of
accessing one account by only one user make it
possible to save the activities.
The availability of the system need to be there for
twenty four hours and throughout the seven data
in the week. The restriction on the time for which
the user can access the data need to be restricted
so that they will not suffer any problem related to
the time.
The process of gathering the data that belongs to
the user is known as registration process. The
details of the user in a personal level need to be
provided to ensure the process of registration.
The admin of the university demands for data
from the student in order to complete the process
of the registration. A password that is provided by
the student is confidential and it ensures that only
the student can access the account. Password
verification s also provided by the system as it
asks the student to type the password for two
One of the important step of the process is the
login step. The important function that the
interactive system need to offer is the login. The
user will need to enter certain credential
information to login to their account. The user
have the right of accessing there account from
anywhere and by using any system. These also
make the process of detecting the user little
critical. The different activities that is performed
by the user in their particular account to remain
secure. They can keep a track on their activities
and can also save the same. The facility of
accessing one account by only one user make it
possible to save the activities.
The availability of the system need to be there for
twenty four hours and throughout the seven data
in the week. The restriction on the time for which
the user can access the data need to be restricted
so that they will not suffer any problem related to
the time.
The process of gathering the data that belongs to
the user is known as registration process. The
details of the user in a personal level need to be
provided to ensure the process of registration.
The admin of the university demands for data
from the student in order to complete the process
of the registration. A password that is provided by
the student is confidential and it ensures that only
the student can access the account. Password
verification s also provided by the system as it
asks the student to type the password for two
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4OBJECT AND DATA MODELLING
times
These system ensures that a report for the
management of the University is generated. These
contains the data that is provided by the student
and also a analysis of the data that is provided.
The report is for the management and the other
faculty and the teaching staff cannot access the
same data.
The usability requirement contains the
information about how the system is effective and
efficient to the users. These also offer the users a
set of instructions that contains the information
about how the system is efficient to them. These
also allow the user to prevent errors in the process
of using the system. A error message in a simple
language that can be understandable by the user is
provided. The complex steps that are included in
using the interactive system is break down into
simple steps or they are removed permanently.
The creation of the course and the major is also
provided by the system. The system show the
major and the courses that are available under the
course in a systematic manner. The authority of
arranging the courses under the major is with the
administrator. To complete the task an interface
is provided that contains the list and the student
can select from the same.
The system need to be trusted by the users. The
information about the usage of the system need to
be there. The user need to be satisfied and the
system need to meet the requirements of the users.
If the system fails to become reliable thn it will
not provide the information of the course
available to the students.
The end step for these purpose is paying the
amount that is offered by the University. A variety
of options is offered b the student so that they can
select the mode of the payment. However the
system also promote the card payment which is a
The task of the system need to be done within a
proper time so that the utility can be enjoyed by
the users. It should n give slow responses to the
user which can frustrate them.
times
These system ensures that a report for the
management of the University is generated. These
contains the data that is provided by the student
and also a analysis of the data that is provided.
The report is for the management and the other
faculty and the teaching staff cannot access the
same data.
The usability requirement contains the
information about how the system is effective and
efficient to the users. These also offer the users a
set of instructions that contains the information
about how the system is efficient to them. These
also allow the user to prevent errors in the process
of using the system. A error message in a simple
language that can be understandable by the user is
provided. The complex steps that are included in
using the interactive system is break down into
simple steps or they are removed permanently.
The creation of the course and the major is also
provided by the system. The system show the
major and the courses that are available under the
course in a systematic manner. The authority of
arranging the courses under the major is with the
administrator. To complete the task an interface
is provided that contains the list and the student
can select from the same.
The system need to be trusted by the users. The
information about the usage of the system need to
be there. The user need to be satisfied and the
system need to meet the requirements of the users.
If the system fails to become reliable thn it will
not provide the information of the course
available to the students.
The end step for these purpose is paying the
amount that is offered by the University. A variety
of options is offered b the student so that they can
select the mode of the payment. However the
system also promote the card payment which is a
The task of the system need to be done within a
proper time so that the utility can be enjoyed by
the users. It should n give slow responses to the
user which can frustrate them.

5OBJECT AND DATA MODELLING
environment friendly option. The information
system administrator are the persons who are
responsible for ensuring that student do not get
confused with a lot of information and only
selected information is visible to them.
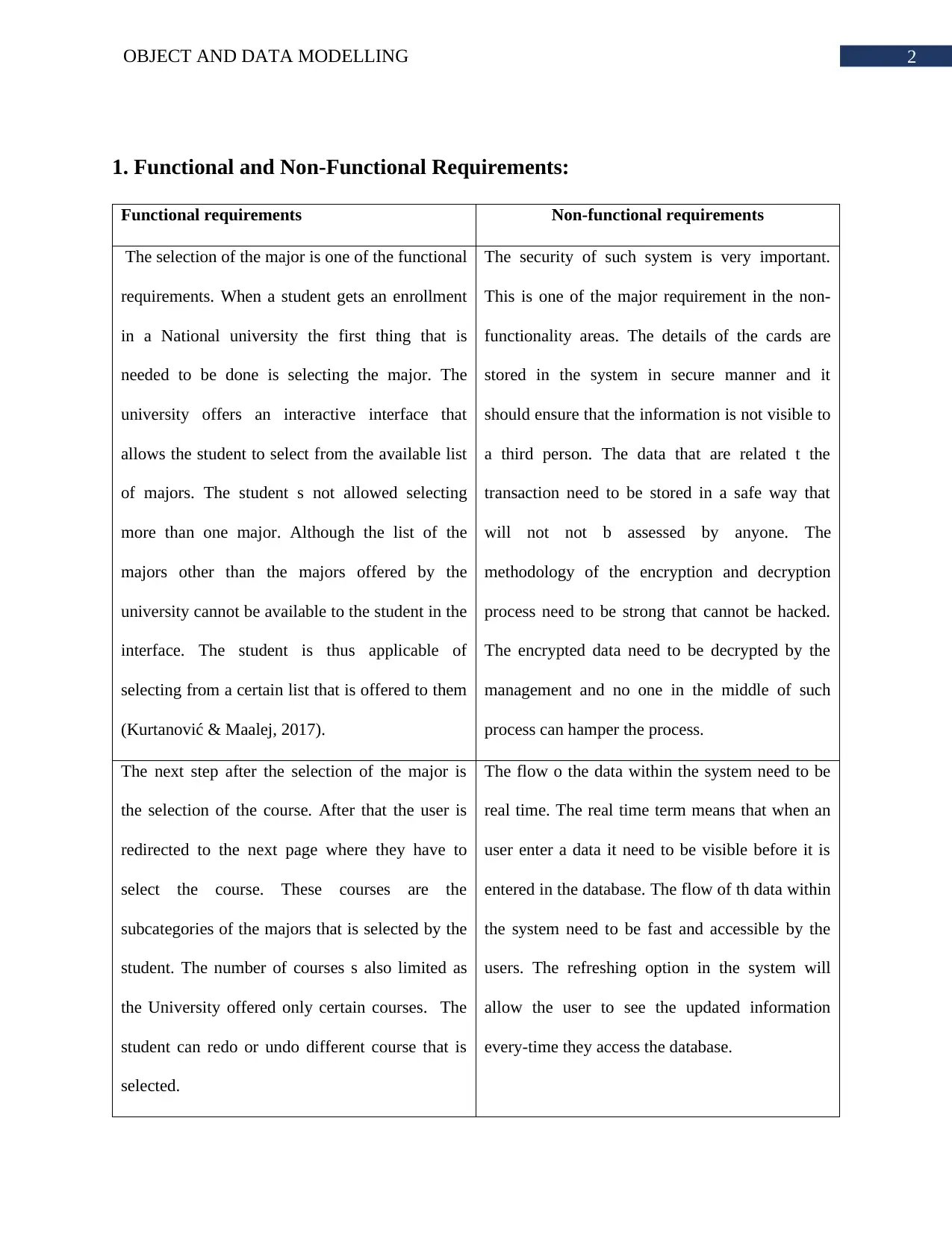
2. Use Cases:
Choose Major: The name of the user use case is Choose Major. The use case id of the
use case is ‘UC EXTERNAL USER 03’. The description is that student selects the major after
the system asks. Along with the major, the student has to choose the term of the enrolment such
as 20XX30, 20xx60 and 20xx90. The use case is accessed by the actor name student. This use
case has include association with ‘enter course’ use case. The precondition of this use case is
student needs to be logged in to the system. The trigger of the use case is student send request to
the user for enrolment. The actions to complete this use case is presented in sequential manner.
First, the student click on enrolment. The system shows the available majors. The student will
select one of the available majors as per desire. The use case has the post condition system
checks if right selection is made. The exception of the use case is no desired major is available in
the system.
Enter Course: The name of the user use case is Enter Course. The use case id of the use
case is ‘UC EXTERNAL USER 04’. The description is that student have to select the course
available under the chosen major. The use case is accessed by the actor named student. This use
case has include association with ‘choose major’ use case. The precondition of this use case is
that user have to select a major first. The trigger of the use case is system verifies the student
major selection as successful. The actions to complete this use case is presented in sequential
environment friendly option. The information
system administrator are the persons who are
responsible for ensuring that student do not get
confused with a lot of information and only
selected information is visible to them.
2. Use Cases:
Choose Major: The name of the user use case is Choose Major. The use case id of the
use case is ‘UC EXTERNAL USER 03’. The description is that student selects the major after
the system asks. Along with the major, the student has to choose the term of the enrolment such
as 20XX30, 20xx60 and 20xx90. The use case is accessed by the actor name student. This use
case has include association with ‘enter course’ use case. The precondition of this use case is
student needs to be logged in to the system. The trigger of the use case is student send request to
the user for enrolment. The actions to complete this use case is presented in sequential manner.
First, the student click on enrolment. The system shows the available majors. The student will
select one of the available majors as per desire. The use case has the post condition system
checks if right selection is made. The exception of the use case is no desired major is available in
the system.
Enter Course: The name of the user use case is Enter Course. The use case id of the use
case is ‘UC EXTERNAL USER 04’. The description is that student have to select the course
available under the chosen major. The use case is accessed by the actor named student. This use
case has include association with ‘choose major’ use case. The precondition of this use case is
that user have to select a major first. The trigger of the use case is system verifies the student
major selection as successful. The actions to complete this use case is presented in sequential
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OBJECT AND DATA MODELLING
manner. First, the student is shown the list of courses that are available under the major. Then the
student will select one of the available. The use case has the post condition system checks if class
limit is reached. The exception of the use case is administrator has blocked the enrolment in the
course even after seats are available.
Sign Up: The name of the user use case is sign up. The use case id of the use case is ‘UC
EXTERNAL USER 01’. The description is that student has to be registered into the system in
order access it. The use case is accessed by the actor name student. This use case has no
association with any use case. The precondition of this use case is user must not have any active
account. The trigger of the use case is system identify a new user.
Sign In: The name of the user use case is sign in. The use case id of the use case is ‘UC
EXTERNAL USER 02’. The description is that the student logs into the system using the login
credentials. The use case is accessed by the actor name student, teaching staff and management.
This use case has no association with any use case. The precondition of this use case is student
must be registered and have entered accurate login credentials. The trigger of the use case is
system has found a user wants to access the system.
Process Payment: The name of the user use case is process payment. The use case id of
the use case is ‘UC EXTERNAL USER 05’. The description is that student is asked to make
payment for getting enrolment through different ways. The use case is accessed by the actor
name student. This use case has no association with any use case. The precondition of this use
case is that student has successfully selected the course and class timings. The trigger of the use
case is system reaches the final process of enrolment.
manner. First, the student is shown the list of courses that are available under the major. Then the
student will select one of the available. The use case has the post condition system checks if class
limit is reached. The exception of the use case is administrator has blocked the enrolment in the
course even after seats are available.
Sign Up: The name of the user use case is sign up. The use case id of the use case is ‘UC
EXTERNAL USER 01’. The description is that student has to be registered into the system in
order access it. The use case is accessed by the actor name student. This use case has no
association with any use case. The precondition of this use case is user must not have any active
account. The trigger of the use case is system identify a new user.
Sign In: The name of the user use case is sign in. The use case id of the use case is ‘UC
EXTERNAL USER 02’. The description is that the student logs into the system using the login
credentials. The use case is accessed by the actor name student, teaching staff and management.
This use case has no association with any use case. The precondition of this use case is student
must be registered and have entered accurate login credentials. The trigger of the use case is
system has found a user wants to access the system.
Process Payment: The name of the user use case is process payment. The use case id of
the use case is ‘UC EXTERNAL USER 05’. The description is that student is asked to make
payment for getting enrolment through different ways. The use case is accessed by the actor
name student. This use case has no association with any use case. The precondition of this use
case is that student has successfully selected the course and class timings. The trigger of the use
case is system reaches the final process of enrolment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7OBJECT AND DATA MODELLING
Generate Report: The name of the user use case is generate report. The use case id of the
use case is ‘UC INTERNAL USER 02’. The description is that managers use the system to get
information about the students, courses, majors and available classes. The use case is accessed
by the actor name manager. This use case has no association with any use case. The precondition
of this use case is manger has to be logged into the management account. The trigger of the use
case is highest authority user wants to see report based on specific data for certain period of time.
Figure 1: Use Case of Enrollment System
(Source: Created by Author)
Use Case ID UC EXTERNAL USER 04
Use Case Name Enter Course
Description Student have to select the course available under the chosen
Generate Report: The name of the user use case is generate report. The use case id of the
use case is ‘UC INTERNAL USER 02’. The description is that managers use the system to get
information about the students, courses, majors and available classes. The use case is accessed
by the actor name manager. This use case has no association with any use case. The precondition
of this use case is manger has to be logged into the management account. The trigger of the use
case is highest authority user wants to see report based on specific data for certain period of time.
Figure 1: Use Case of Enrollment System
(Source: Created by Author)
Use Case ID UC EXTERNAL USER 04
Use Case Name Enter Course
Description Student have to select the course available under the chosen
8OBJECT AND DATA MODELLING
major. The student can select three to four courses based on the
class timings. One class can have maximum of forty students
Precondition The user have to select a major first
Trigger System verifies the student major selection as successful
Actors Student
Stakeholder Student, Teacher, National University
Associated Use Case Choose Major
Action The system enables the course selection option
The student select the course and corresponding class timing
Post-condition System checks if class limit is reached
Exception Administrator has blocked the enrolment in the course even after
seats are available
major. The student can select three to four courses based on the
class timings. One class can have maximum of forty students
Precondition The user have to select a major first
Trigger System verifies the student major selection as successful
Actors Student
Stakeholder Student, Teacher, National University
Associated Use Case Choose Major
Action The system enables the course selection option
The student select the course and corresponding class timing
Post-condition System checks if class limit is reached
Exception Administrator has blocked the enrolment in the course even after
seats are available
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OBJECT AND DATA MODELLING
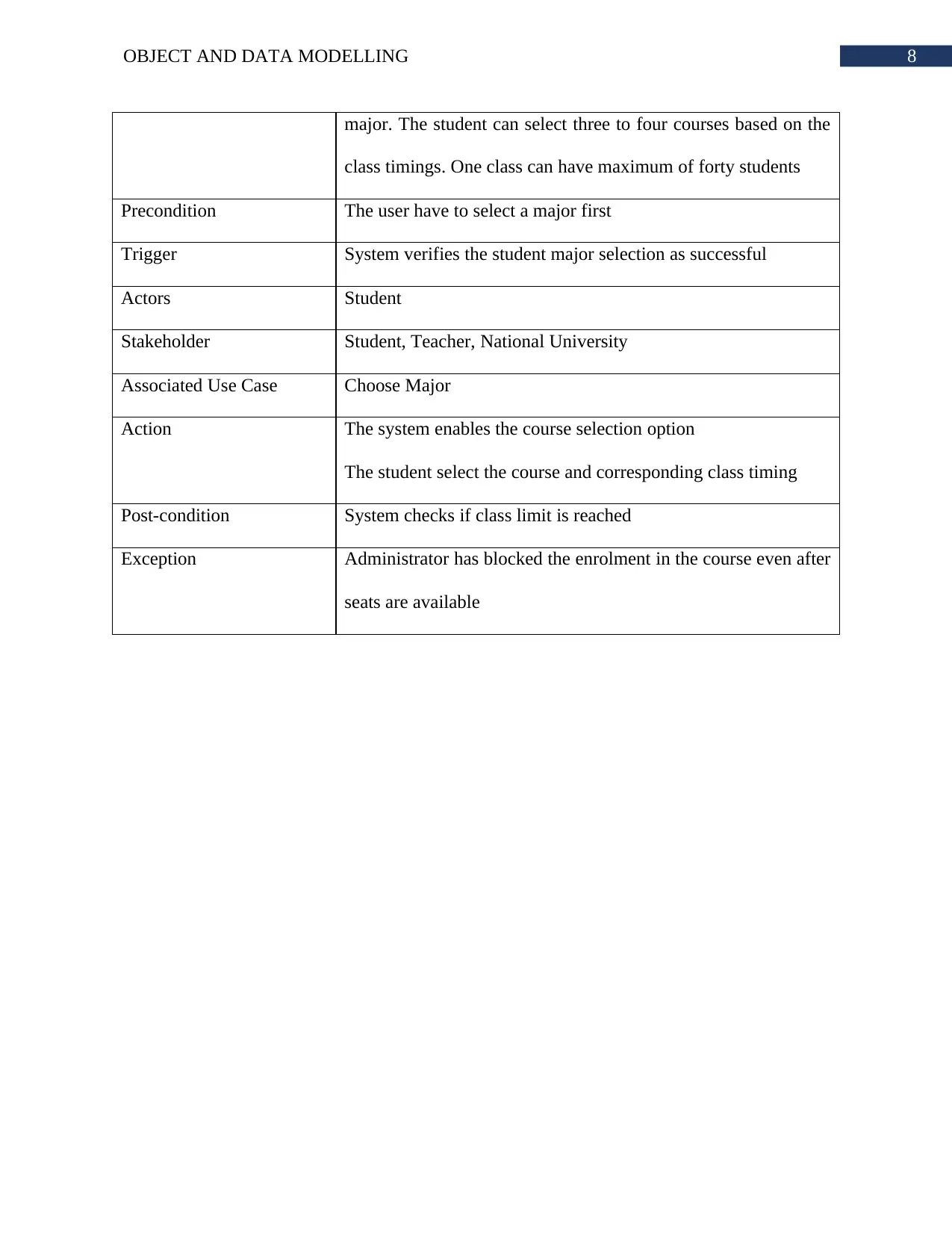
3. UML Domain Model Class Diagram:
Figure 2: UML Domain Model Class Diagram of Enrollment System
(Source: Created by Author)
3. UML Domain Model Class Diagram:
Figure 2: UML Domain Model Class Diagram of Enrollment System
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10OBJECT AND DATA MODELLING
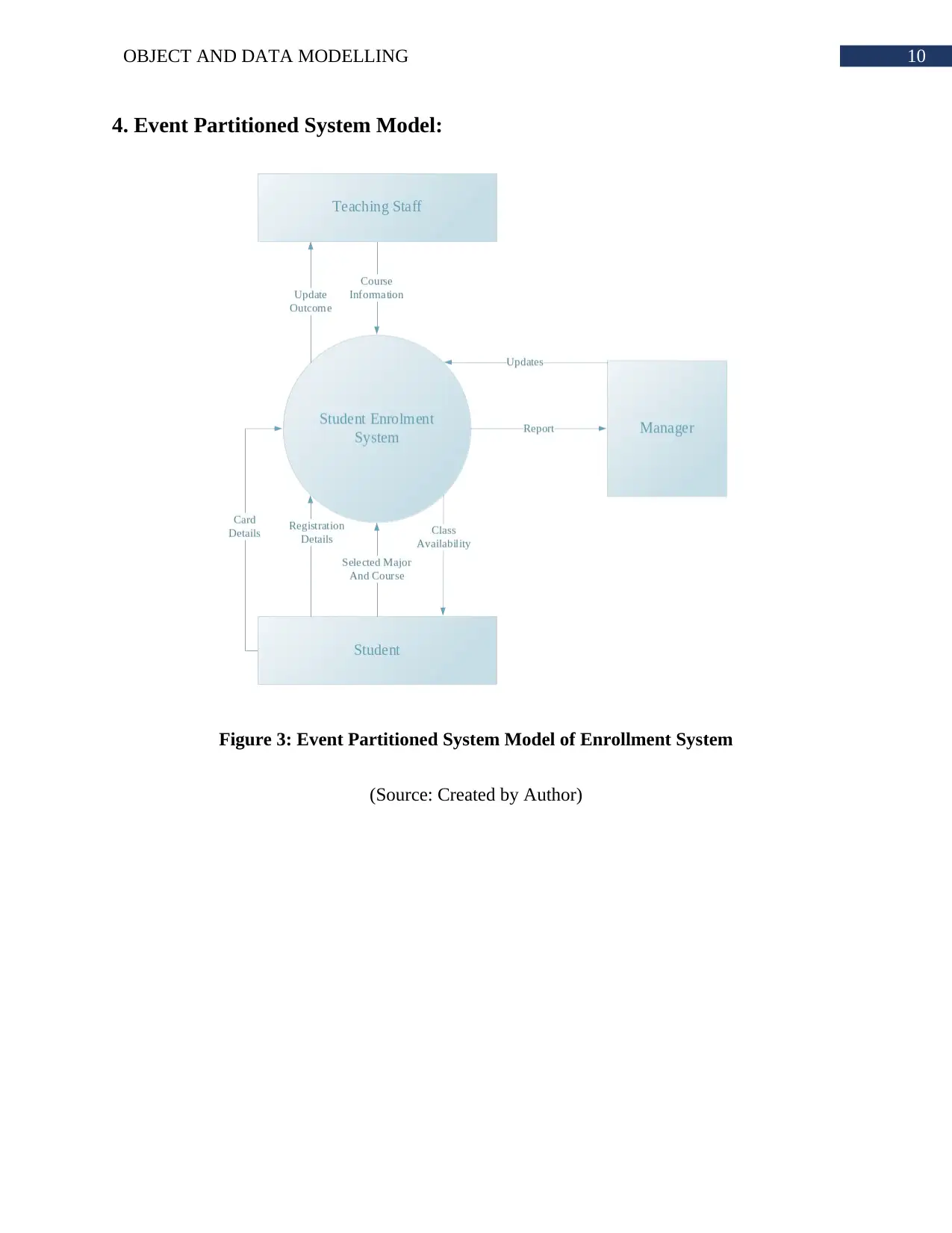
4. Event Partitioned System Model:
Figure 3: Event Partitioned System Model of Enrollment System
(Source: Created by Author)
4. Event Partitioned System Model:
Figure 3: Event Partitioned System Model of Enrollment System
(Source: Created by Author)

11OBJECT AND DATA MODELLING
Bibliography:
Afreen, N., Khatoon, A., & Sadiq, M. (2016). A taxonomy of software’s non-functional
requirements. In Proceedings of the second international conference on computer and
communication technologies (pp. 47-53). Springer, New Delhi.
Bakaev, M., Gaedke, M., Khvorostov, V., & Heil, S. (2016, June). Extending Kansei
Engineering for Requirements Consideration in Web Interaction Design. In International
Conference on Web Engineering (pp. 513-518). Springer, Cham.
Eckhardt, J., Vogelsang, A., & Fernández, D. M. (2016, May). Are" non-functional"
requirements really non-functional? an investigation of non-functional requirements in
practice. In 2016 IEEE/ACM 38th International Conference on Software Engineering
(ICSE) (pp. 832-842). IEEE.
Elallaoui, M., Nafil, K., & Touahni, R. (2018). Automatic transformation of user stories into
UML use case diagrams using NLP techniques. Procedia computer science, 130, 42-49.
Faitelson, D., & Tyszberowicz, S. (2017, May). UML diagram refinement (focusing on class-and
use case diagrams). In Proceedings of the 39th International Conference on Software
Engineering (pp. 735-745). IEEE Press.
Ferreira, J. M., & Acuña, S. T. (2017). A Software Application for Collecting Usability
Empirical Data about User Efficiency, Effectiveness and Satisfaction. XII Jornadas
Iberoamericanas de Ingeniería de Software e Ingeniería del Conocimiento JIISIC’2017,
11.
Bibliography:
Afreen, N., Khatoon, A., & Sadiq, M. (2016). A taxonomy of software’s non-functional
requirements. In Proceedings of the second international conference on computer and
communication technologies (pp. 47-53). Springer, New Delhi.
Bakaev, M., Gaedke, M., Khvorostov, V., & Heil, S. (2016, June). Extending Kansei
Engineering for Requirements Consideration in Web Interaction Design. In International
Conference on Web Engineering (pp. 513-518). Springer, Cham.
Eckhardt, J., Vogelsang, A., & Fernández, D. M. (2016, May). Are" non-functional"
requirements really non-functional? an investigation of non-functional requirements in
practice. In 2016 IEEE/ACM 38th International Conference on Software Engineering
(ICSE) (pp. 832-842). IEEE.
Elallaoui, M., Nafil, K., & Touahni, R. (2018). Automatic transformation of user stories into
UML use case diagrams using NLP techniques. Procedia computer science, 130, 42-49.
Faitelson, D., & Tyszberowicz, S. (2017, May). UML diagram refinement (focusing on class-and
use case diagrams). In Proceedings of the 39th International Conference on Software
Engineering (pp. 735-745). IEEE Press.
Ferreira, J. M., & Acuña, S. T. (2017). A Software Application for Collecting Usability
Empirical Data about User Efficiency, Effectiveness and Satisfaction. XII Jornadas
Iberoamericanas de Ingeniería de Software e Ingeniería del Conocimiento JIISIC’2017,
11.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




