MN404 - Role of Operating Systems and Command Line Interface (CLI)
VerifiedAdded on 2023/04/20
|12
|1611
|294
Homework Assignment
AI Summary
This assignment solution covers the fundamentals of operating systems, focusing on the role of operating systems and the command-line interface (CLI). It includes a comparison of Unix and Windows operating systems in terms of stability, performance, compatibility, and reliability. The solution also provides answers to short answer questions related to open-source operating systems, multiprogramming, time-sharing, kernel functionality, and system calls. Furthermore, it demonstrates OS administration using CLI, including security-related commands for file and directory management, permission changes, and password resets. The assignment also covers UNIX networking commands such as ping, ifconfig, netstat, nslookup, hostname, and arp, along with explanations and examples. Desklib provides this assignment as a resource for students.
OPERATING SYSTEM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Section 1: Operating Systems(OS).......................................................................................................2
Comparison and contrast the Unix OS with Window OS in terms of :................................................2
Short Answer Questions...................................................................................................................3
Section 2: OS Administration using Command Line Interface (CLI)....................................................4
Security related commands..............................................................................................................4
UNIX networking Commands...........................................................................................................6
References............................................................................................................................................9
Section 1: Operating Systems(OS).......................................................................................................2
Comparison and contrast the Unix OS with Window OS in terms of :................................................2
Short Answer Questions...................................................................................................................3
Section 2: OS Administration using Command Line Interface (CLI)....................................................4
Security related commands..............................................................................................................4
UNIX networking Commands...........................................................................................................6
References............................................................................................................................................9
Section 1: Operating Systems(OS)
Comparison and contrast the Unix OS with Window OS in terms of :
Stability
Unix OS is more stable compared to windows OS. Unix OS is the most scalable and reliable
OS because it usually is tightly integrated with the hardware. The massive UNIX vendors
have the advantage of coming up with their various OS versions around their hardware
that permits them to possess hardware with less incompatibilities and problems than
Windows OS. [1]
Performance
Unix OS run faster in desktop than Windows OS. This feature of Linux makes it more
suitable software development environment. Developer find it easier to use Linux than
windows since most of development tools are provided by default. [2] Also Unix OS are
known to have better hosting environment compared to windows OS.
Compatibility
Almost all application tends to be designed to run in windows OS. Although there are
alternatives Unix applications in the market for windows, some don’t have alternatives.
This makes it important to ask yourself if there exist an alternative to the application you
are using in windows before you migrate to Unix OS.
If there doesn’t exist an alternative for Unix, one can use some software such as WINE or
VM to run windows applications in Unix OS. [3]
Installing applications in Unix is usually done by typing the correct commands in the
terminal. One can install the application from the repository while other need to be
downloaded and installed directly the source. Windows OS users aren’t affected by these
incompatible issues since installing applications in windows is much simply compared to
Unix. [3]
Reliability
Unix OS is additional reliable in comparison to Windows. Unix OS has a reliable in build
security measures. Developers of Unix versions are much active and unleash major and
Comparison and contrast the Unix OS with Window OS in terms of :
Stability
Unix OS is more stable compared to windows OS. Unix OS is the most scalable and reliable
OS because it usually is tightly integrated with the hardware. The massive UNIX vendors
have the advantage of coming up with their various OS versions around their hardware
that permits them to possess hardware with less incompatibilities and problems than
Windows OS. [1]
Performance
Unix OS run faster in desktop than Windows OS. This feature of Linux makes it more
suitable software development environment. Developer find it easier to use Linux than
windows since most of development tools are provided by default. [2] Also Unix OS are
known to have better hosting environment compared to windows OS.
Compatibility
Almost all application tends to be designed to run in windows OS. Although there are
alternatives Unix applications in the market for windows, some don’t have alternatives.
This makes it important to ask yourself if there exist an alternative to the application you
are using in windows before you migrate to Unix OS.
If there doesn’t exist an alternative for Unix, one can use some software such as WINE or
VM to run windows applications in Unix OS. [3]
Installing applications in Unix is usually done by typing the correct commands in the
terminal. One can install the application from the repository while other need to be
downloaded and installed directly the source. Windows OS users aren’t affected by these
incompatible issues since installing applications in windows is much simply compared to
Unix. [3]
Reliability
Unix OS is additional reliable in comparison to Windows. Unix OS has a reliable in build
security measures. Developers of Unix versions are much active and unleash major and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

minor updates time to time. Historically systems that run in Unix OS are well-known for
running for many years without failures or need to restart. UNIX operating system OS is
additional reliable in terms of security than window OS. Hackers or virus developers realize
it harder to penetrate through Linux as compared to window OS that is more prone to
viruses and malware without ant-virus program. Once a programme hang in windows,
typically it’s troublesome to kill the programme even through task manager. In Linux, any
application can be terminated with the XKill command. [4]
Short Answer Questions
a. Open source code OS is a software system whose source code is freely out there for users.
Open source OS is taken into account safer compared with closed source OS. OS like UNIX
is an open source OS. Since everybody has access to the codes, bugs and week points of OS
are found faster and so they are fixed faster, closing up security holes quicker. In addition,
anyone and everybody are free to produce a higher, safer version of the package. [4]
b. In multiprogramming and Time sharing there are problems such as:
i. There is stealing of personal files or other data.
ii. Resources e.g. main memory and other hardware devices are used without
proper management.
c. It is impossible to make sure the identical degree of security in time-shared machine as
we've got in dedicated machine since any security scheme designed by humans can be
broken by a human, and therefore the more complicated the scheme, the harder it's to feel
assured of its correct implementation.
d. Kernel is a software that provides save multiplexing to underlying hardware. Kernel has to
provide at least the following three functionality;
i. Scheduling.
ii. Protection.
iii. Message passing.
e. They reside in libraries and applications (user space). User space interacts through system
calls with kernel. System call is an entry point to kernel [4][.
running for many years without failures or need to restart. UNIX operating system OS is
additional reliable in terms of security than window OS. Hackers or virus developers realize
it harder to penetrate through Linux as compared to window OS that is more prone to
viruses and malware without ant-virus program. Once a programme hang in windows,
typically it’s troublesome to kill the programme even through task manager. In Linux, any
application can be terminated with the XKill command. [4]
Short Answer Questions
a. Open source code OS is a software system whose source code is freely out there for users.
Open source OS is taken into account safer compared with closed source OS. OS like UNIX
is an open source OS. Since everybody has access to the codes, bugs and week points of OS
are found faster and so they are fixed faster, closing up security holes quicker. In addition,
anyone and everybody are free to produce a higher, safer version of the package. [4]
b. In multiprogramming and Time sharing there are problems such as:
i. There is stealing of personal files or other data.
ii. Resources e.g. main memory and other hardware devices are used without
proper management.
c. It is impossible to make sure the identical degree of security in time-shared machine as
we've got in dedicated machine since any security scheme designed by humans can be
broken by a human, and therefore the more complicated the scheme, the harder it's to feel
assured of its correct implementation.
d. Kernel is a software that provides save multiplexing to underlying hardware. Kernel has to
provide at least the following three functionality;
i. Scheduling.
ii. Protection.
iii. Message passing.
e. They reside in libraries and applications (user space). User space interacts through system
calls with kernel. System call is an entry point to kernel [4][.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Section 2: OS Administration using Command Line Interface (CLI)
Security related commands
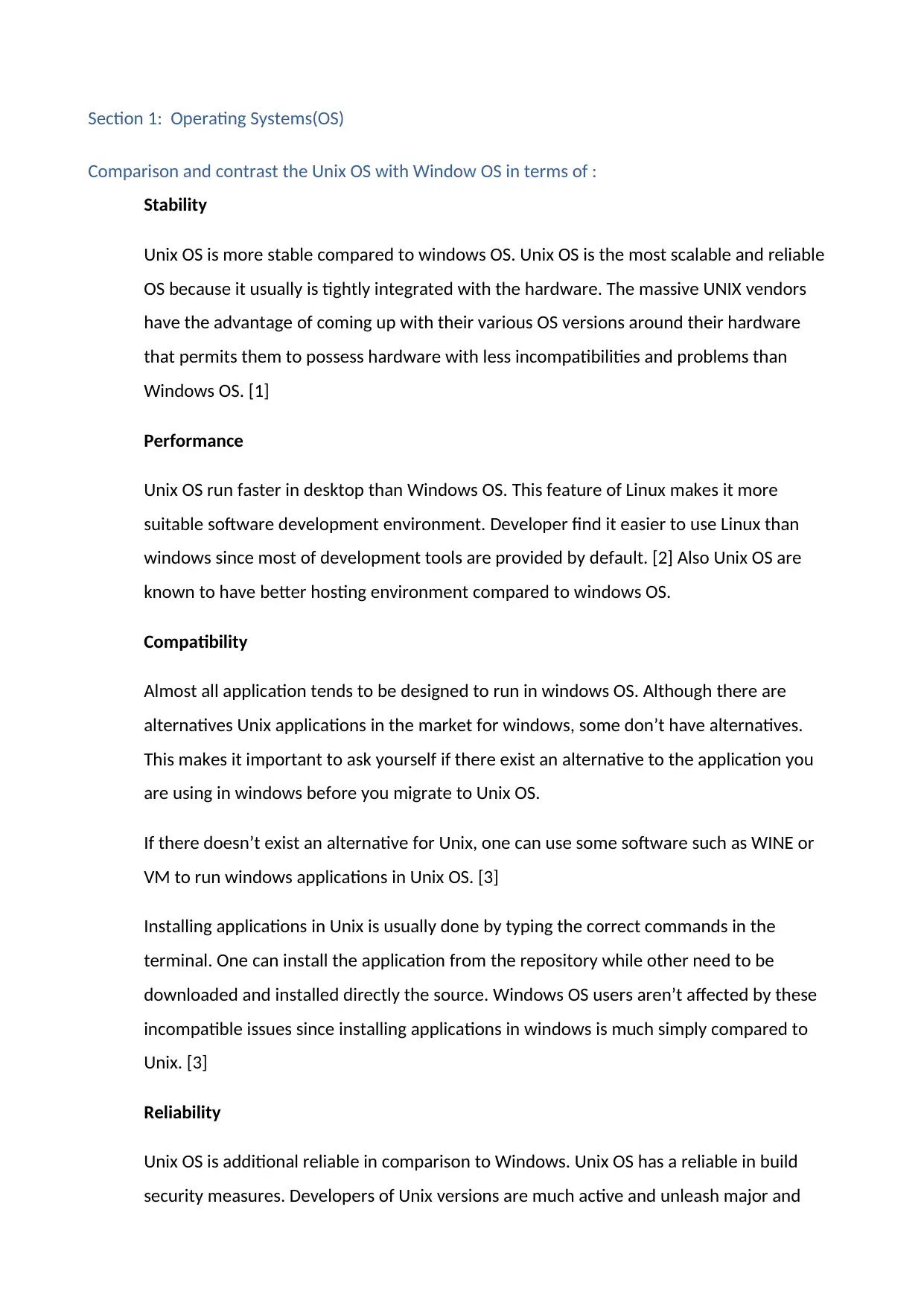
1) Create a file in your home directory; name it with your MITID?
We use the ‘touch’ command to create a file. The syntax is touch <filename>.
2) What is the default file permissions assigned to the newly created file?
The default permissions as seen below for the file, MIT182523, is read-write (rw)
for owner (user), read(r) for group, and r for other users.
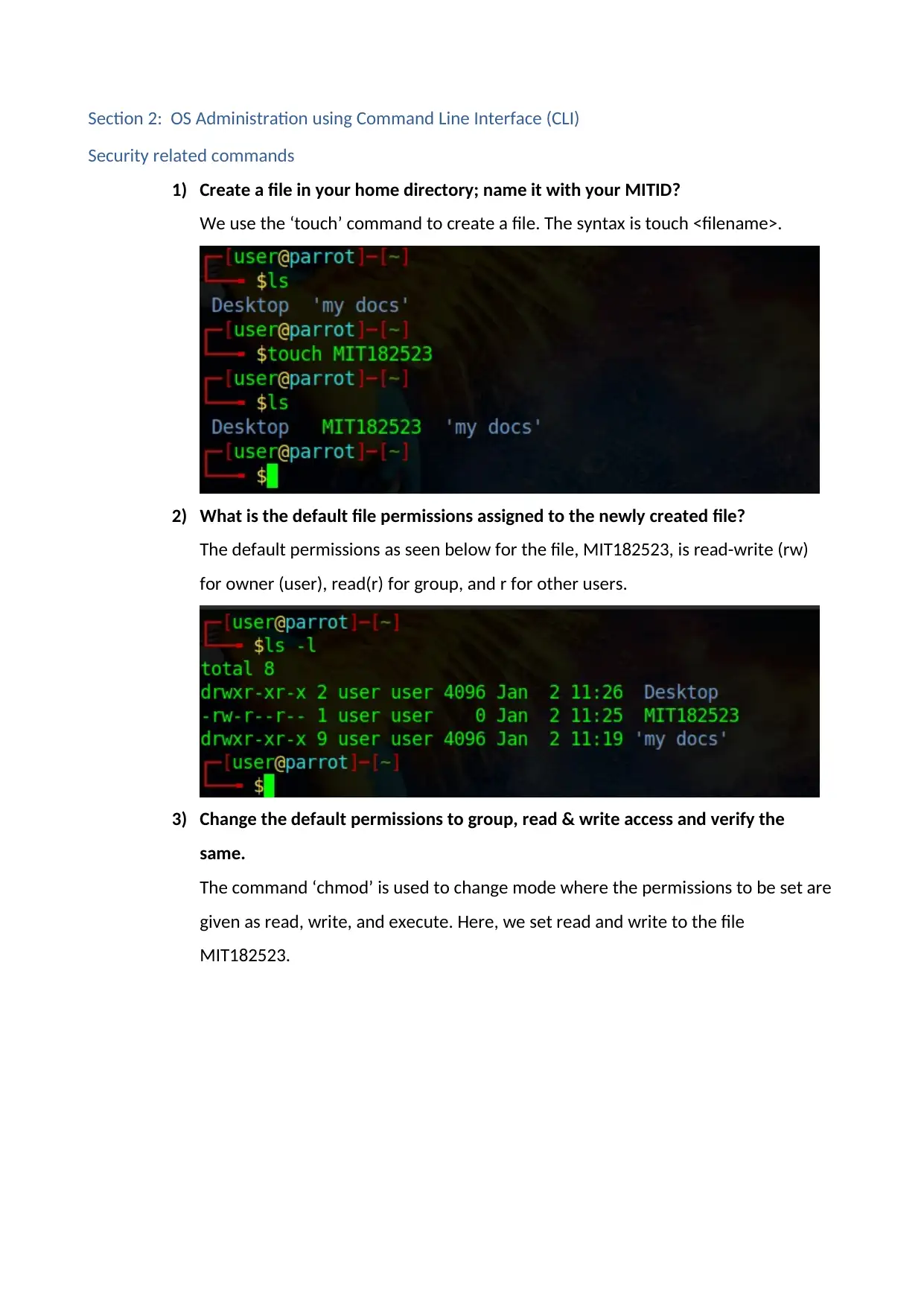
3) Change the default permissions to group, read & write access and verify the
same.
The command ‘chmod’ is used to change mode where the permissions to be set are
given as read, write, and execute. Here, we set read and write to the file
MIT182523.
Security related commands
1) Create a file in your home directory; name it with your MITID?
We use the ‘touch’ command to create a file. The syntax is touch <filename>.
2) What is the default file permissions assigned to the newly created file?
The default permissions as seen below for the file, MIT182523, is read-write (rw)
for owner (user), read(r) for group, and r for other users.
3) Change the default permissions to group, read & write access and verify the
same.
The command ‘chmod’ is used to change mode where the permissions to be set are
given as read, write, and execute. Here, we set read and write to the file
MIT182523.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
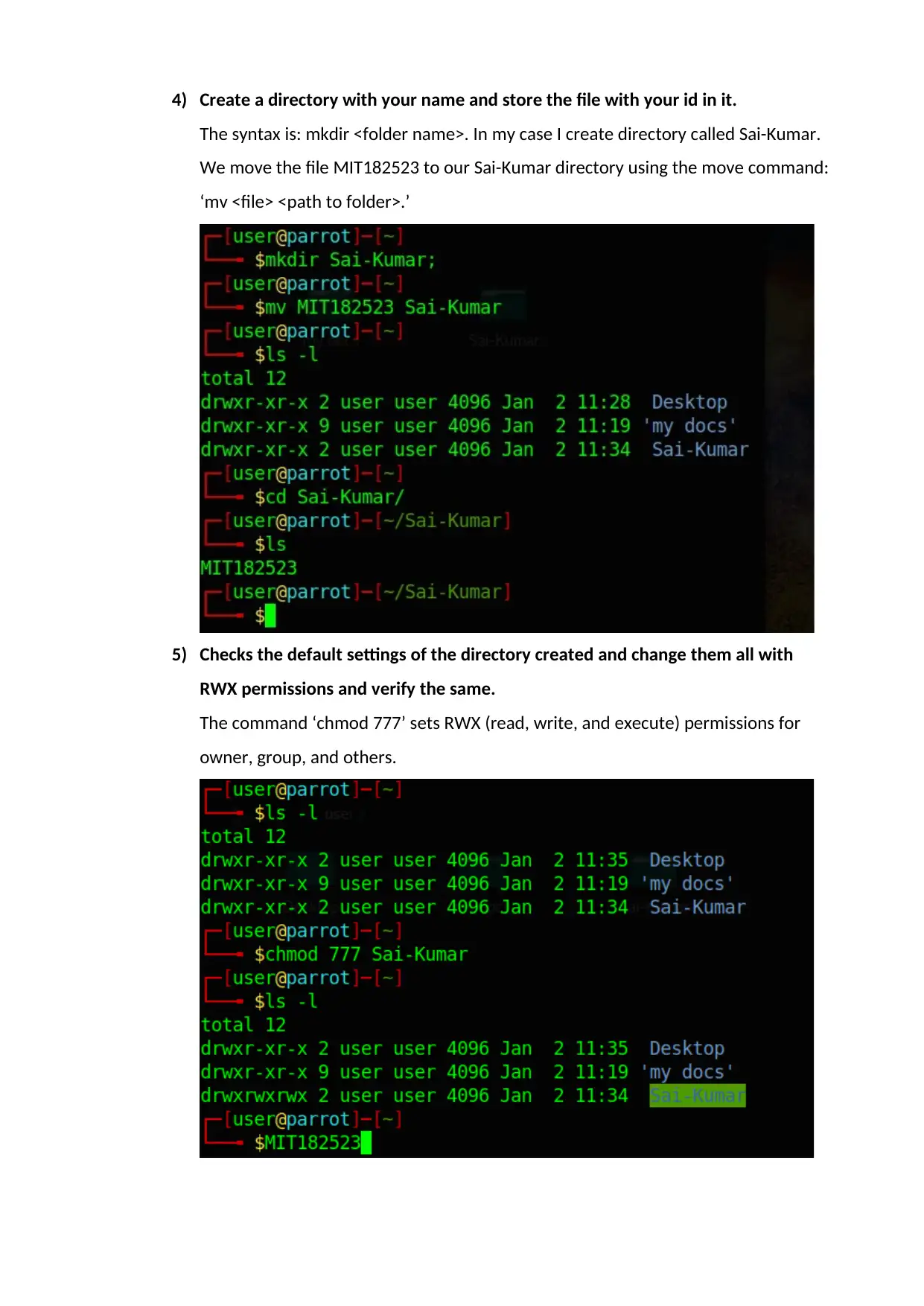
4) Create a directory with your name and store the file with your id in it.
The syntax is: mkdir <folder name>. In my case I create directory called Sai-Kumar.
We move the file MIT182523 to our Sai-Kumar directory using the move command:
‘mv <file> <path to folder>.’
5) Checks the default settings of the directory created and change them all with
RWX permissions and verify the same.
The command ‘chmod 777’ sets RWX (read, write, and execute) permissions for
owner, group, and others.
The syntax is: mkdir <folder name>. In my case I create directory called Sai-Kumar.
We move the file MIT182523 to our Sai-Kumar directory using the move command:
‘mv <file> <path to folder>.’
5) Checks the default settings of the directory created and change them all with
RWX permissions and verify the same.
The command ‘chmod 777’ sets RWX (read, write, and execute) permissions for
owner, group, and others.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
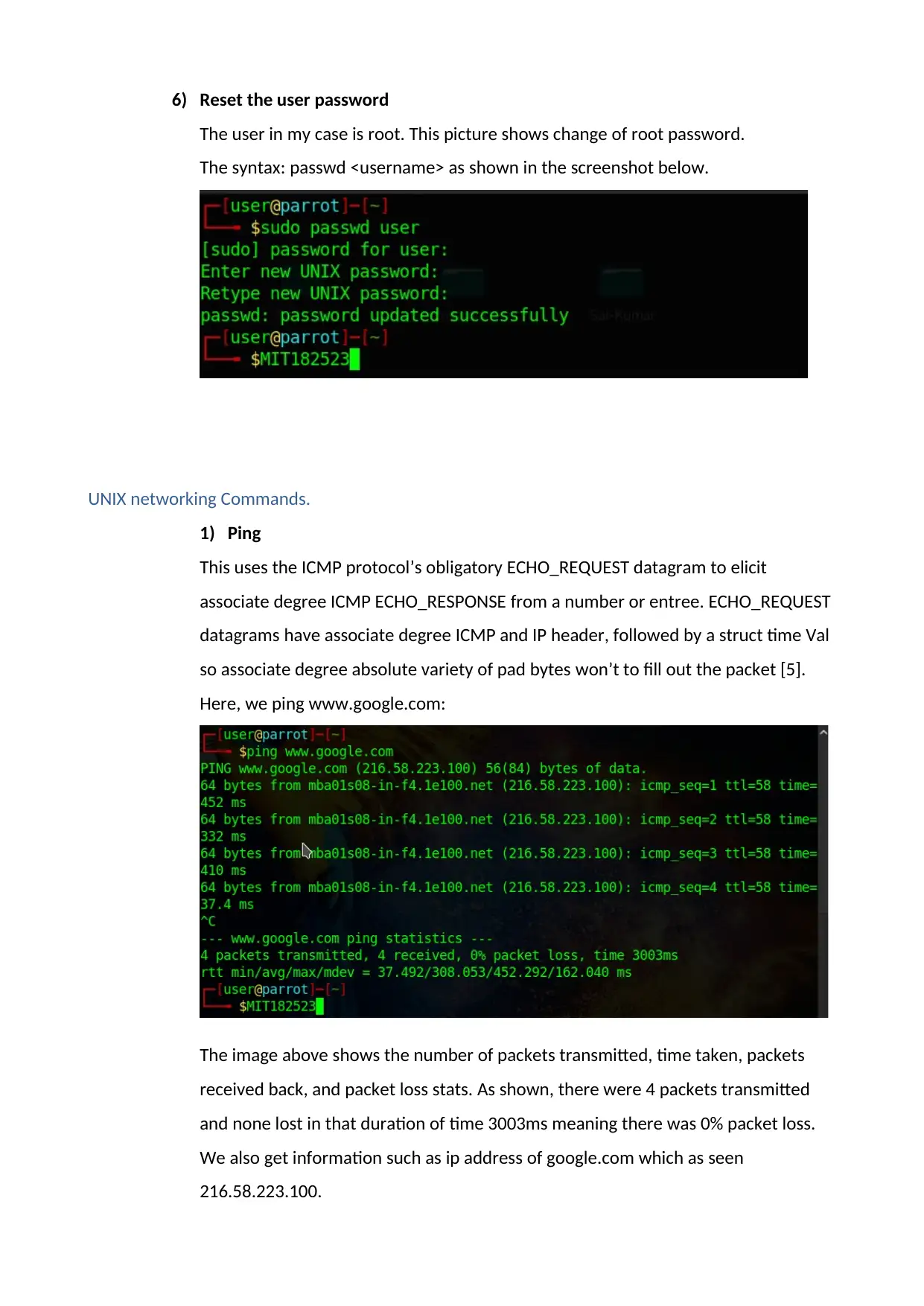
6) Reset the user password
The user in my case is root. This picture shows change of root password.
The syntax: passwd <username> as shown in the screenshot below.
UNIX networking Commands.
1) Ping
This uses the ICMP protocol’s obligatory ECHO_REQUEST datagram to elicit
associate degree ICMP ECHO_RESPONSE from a number or entree. ECHO_REQUEST
datagrams have associate degree ICMP and IP header, followed by a struct time Val
so associate degree absolute variety of pad bytes won’t to fill out the packet [5].
Here, we ping www.google.com:
The image above shows the number of packets transmitted, time taken, packets
received back, and packet loss stats. As shown, there were 4 packets transmitted
and none lost in that duration of time 3003ms meaning there was 0% packet loss.
We also get information such as ip address of google.com which as seen
216.58.223.100.
The user in my case is root. This picture shows change of root password.
The syntax: passwd <username> as shown in the screenshot below.
UNIX networking Commands.
1) Ping
This uses the ICMP protocol’s obligatory ECHO_REQUEST datagram to elicit
associate degree ICMP ECHO_RESPONSE from a number or entree. ECHO_REQUEST
datagrams have associate degree ICMP and IP header, followed by a struct time Val
so associate degree absolute variety of pad bytes won’t to fill out the packet [5].
Here, we ping www.google.com:
The image above shows the number of packets transmitted, time taken, packets
received back, and packet loss stats. As shown, there were 4 packets transmitted
and none lost in that duration of time 3003ms meaning there was 0% packet loss.
We also get information such as ip address of google.com which as seen
216.58.223.100.
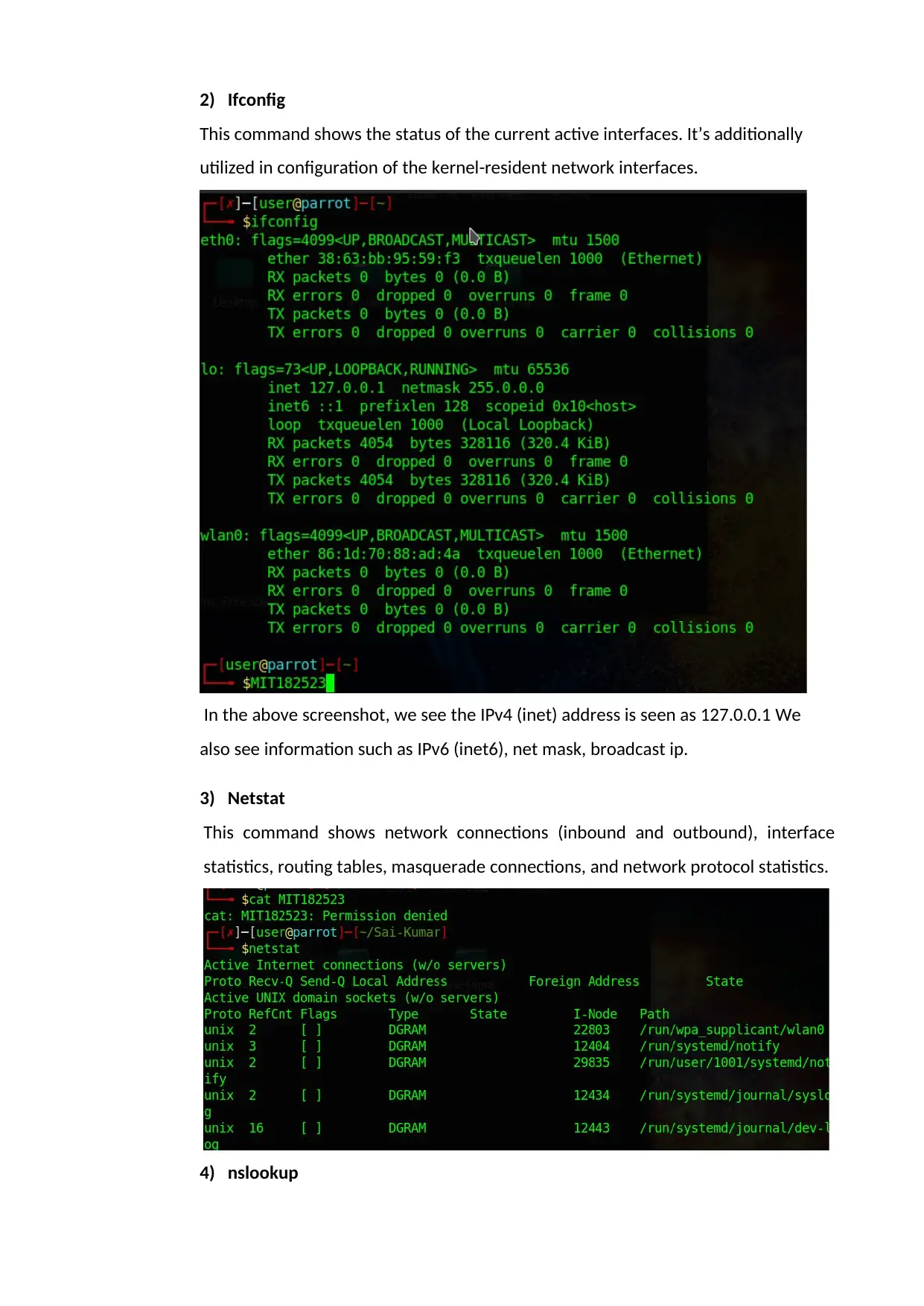
2) Ifconfig
This command shows the status of the current active interfaces. It’s additionally
utilized in configuration of the kernel-resident network interfaces.
In the above screenshot, we see the IPv4 (inet) address is seen as 127.0.0.1 We
also see information such as IPv6 (inet6), net mask, broadcast ip.
3) Netstat
This command shows network connections (inbound and outbound), interface
statistics, routing tables, masquerade connections, and network protocol statistics.
4) nslookup
This command shows the status of the current active interfaces. It’s additionally
utilized in configuration of the kernel-resident network interfaces.
In the above screenshot, we see the IPv4 (inet) address is seen as 127.0.0.1 We
also see information such as IPv6 (inet6), net mask, broadcast ip.
3) Netstat
This command shows network connections (inbound and outbound), interface
statistics, routing tables, masquerade connections, and network protocol statistics.
4) nslookup
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
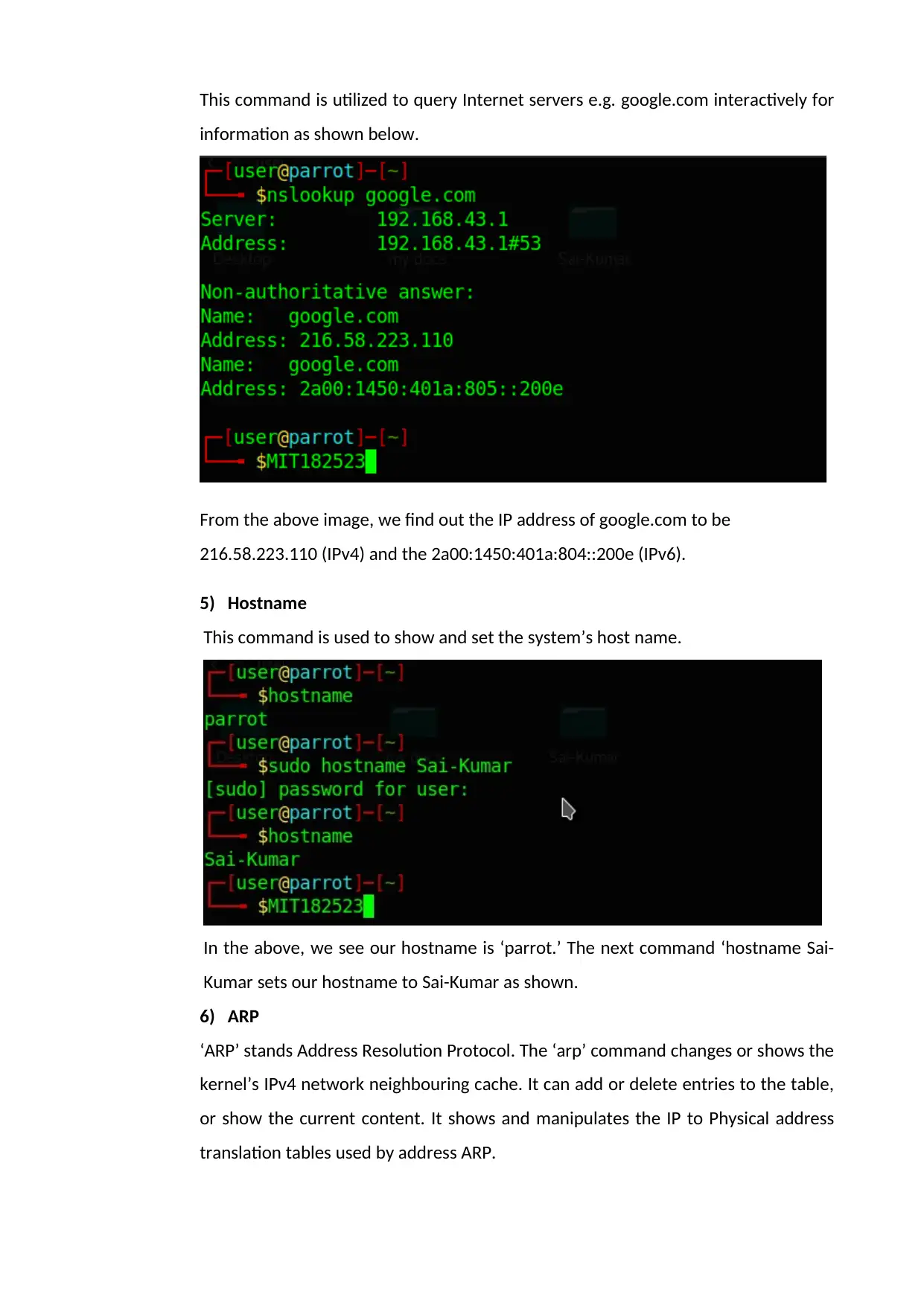
This command is utilized to query Internet servers e.g. google.com interactively for
information as shown below.
From the above image, we find out the IP address of google.com to be
216.58.223.110 (IPv4) and the 2a00:1450:401a:804::200e (IPv6).
5) Hostname
This command is used to show and set the system’s host name.
In the above, we see our hostname is ‘parrot.’ The next command ‘hostname Sai-
Kumar sets our hostname to Sai-Kumar as shown.
6) ARP
‘ARP’ stands Address Resolution Protocol. The ‘arp’ command changes or shows the
kernel’s IPv4 network neighbouring cache. It can add or delete entries to the table,
or show the current content. It shows and manipulates the IP to Physical address
translation tables used by address ARP.
information as shown below.
From the above image, we find out the IP address of google.com to be
216.58.223.110 (IPv4) and the 2a00:1450:401a:804::200e (IPv6).
5) Hostname
This command is used to show and set the system’s host name.
In the above, we see our hostname is ‘parrot.’ The next command ‘hostname Sai-
Kumar sets our hostname to Sai-Kumar as shown.
6) ARP
‘ARP’ stands Address Resolution Protocol. The ‘arp’ command changes or shows the
kernel’s IPv4 network neighbouring cache. It can add or delete entries to the table,
or show the current content. It shows and manipulates the IP to Physical address
translation tables used by address ARP.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


References
[1]. Boulanger, Alan. "Open-source versus proprietary software: Is one more reliable
and secure than the other?" IBM Systems Journal 44, no. 2 (2015): 239-248
[2]. Bovet, Daniel P., and Marco Cesati. Understanding the Linux Kernel: from I/O ports
to process management. " O'Reilly Media, Inc.", 2015.
[3]. Morris, James, Stephen Smalley, and Greg Kroah-Hartman. "Linux security modules:
General security support for the linux kernel." In USENIX Security Symposium. 2012.
[4]. Ritchie, Dennis M., and Ken Thompson. "The UNIX time sharing system." Bell‐
System Technical Journal 57, no. 6 1905-1929, 2009.
[5]. Silberschatz, Abraham, Greg Gagne, and Peter B. Galvin. Operating system
concepts. Wiley, 2018
[1]. Boulanger, Alan. "Open-source versus proprietary software: Is one more reliable
and secure than the other?" IBM Systems Journal 44, no. 2 (2015): 239-248
[2]. Bovet, Daniel P., and Marco Cesati. Understanding the Linux Kernel: from I/O ports
to process management. " O'Reilly Media, Inc.", 2015.
[3]. Morris, James, Stephen Smalley, and Greg Kroah-Hartman. "Linux security modules:
General security support for the linux kernel." In USENIX Security Symposium. 2012.
[4]. Ritchie, Dennis M., and Ken Thompson. "The UNIX time sharing system." Bell‐
System Technical Journal 57, no. 6 1905-1929, 2009.
[5]. Silberschatz, Abraham, Greg Gagne, and Peter B. Galvin. Operating system
concepts. Wiley, 2018
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


![Server Installation and Management Project - [Course Name] [Semester]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fkl%2F1a2c109da7e14c78a6b2e8ca6dd132c5.jpg&w=256&q=75)


