BN104 - Operating Systems: Deadlock, Livelock, and System Integration
VerifiedAdded on 2023/03/30
|14
|1780
|390
Report
AI Summary
This assignment delves into various aspects of operating systems, starting with a detailed analysis of deadlock and livelock scenarios, using the Mount George Tunnel example. It explores conditions for deadlock, its detection using deadlock graphs, and differentiates livelock from deadlock. The assignment further investigates the integration of hardware, operating systems, and application software, explaining their interaction steps. It also rationalizes RAM memory capacities being powers of 2. The report discusses the purpose and applications of user interfaces, followed by an analysis of disk scheduling algorithms (FCFS, SSTF, SCAN, LOOK) with arm movement diagrams and track calculations. Key UNIX commands (chmod, ls, cp) are documented, and common operating system problems are identified along with troubleshooting tools and solutions. The document concludes with a bibliography of cited sources, with the complete solution available on Desklib, a platform offering AI-powered study tools and a wealth of academic resources.

Running head: OPERATING SYSTEM
Operating System
Name of the Student
Name of the University
Author Note
Operating System
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
OPERATING SYSTEM
Summary
OPERATING SYSTEM
Summary
2
OPERATING SYSTEM
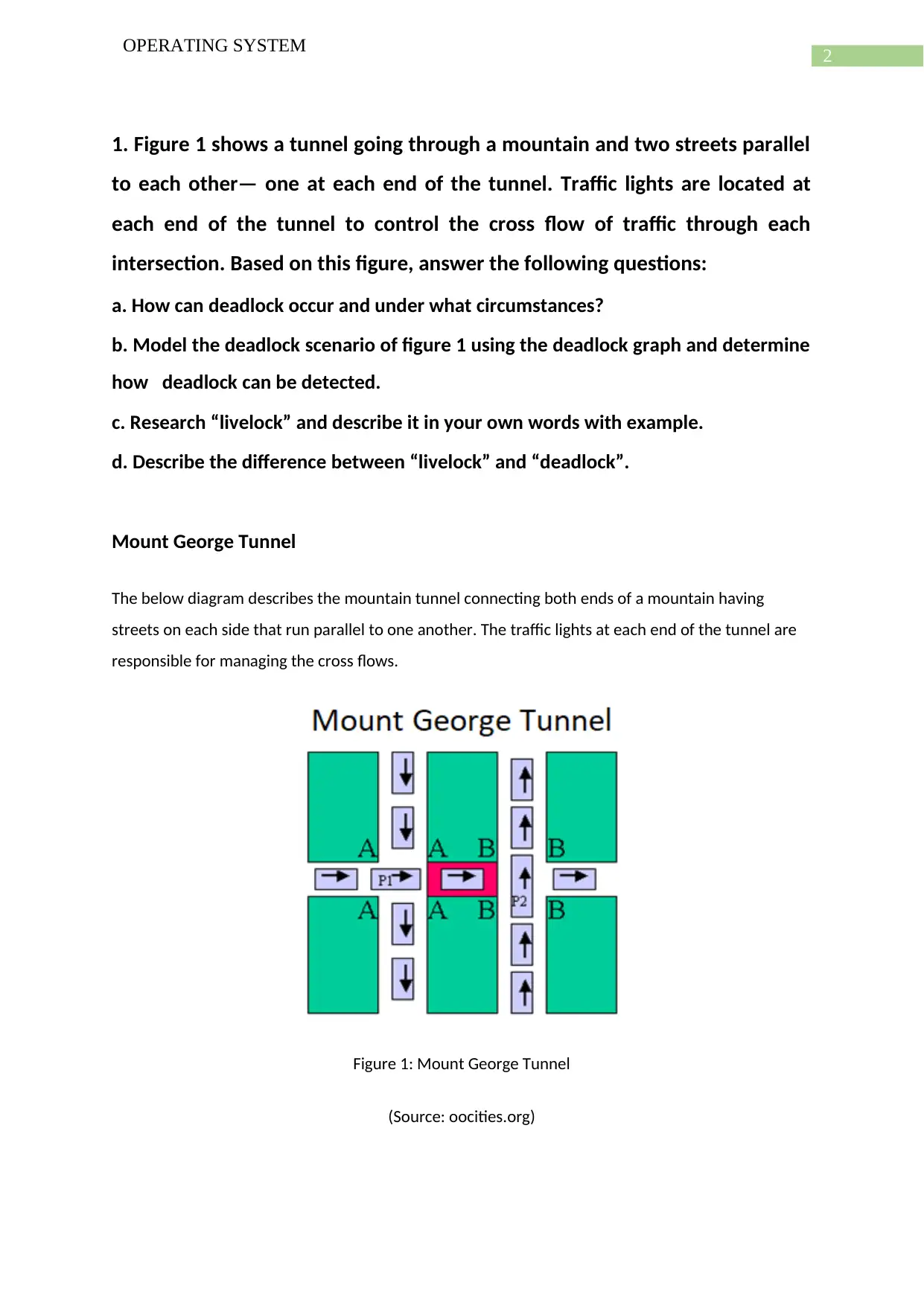
1. Figure 1 shows a tunnel going through a mountain and two streets parallel
to each other— one at each end of the tunnel. Traffic lights are located at
each end of the tunnel to control the cross flow of traffic through each
intersection. Based on this figure, answer the following questions:
a. How can deadlock occur and under what circumstances?
b. Model the deadlock scenario of figure 1 using the deadlock graph and determine
how deadlock can be detected.
c. Research “livelock” and describe it in your own words with example.
d. Describe the difference between “livelock” and “deadlock”.
Mount George Tunnel
The below diagram describes the mountain tunnel connecting both ends of a mountain having
streets on each side that run parallel to one another. The traffic lights at each end of the tunnel are
responsible for managing the cross flows.
Figure 1: Mount George Tunnel
(Source: oocities.org)
OPERATING SYSTEM
1. Figure 1 shows a tunnel going through a mountain and two streets parallel
to each other— one at each end of the tunnel. Traffic lights are located at
each end of the tunnel to control the cross flow of traffic through each
intersection. Based on this figure, answer the following questions:
a. How can deadlock occur and under what circumstances?
b. Model the deadlock scenario of figure 1 using the deadlock graph and determine
how deadlock can be detected.
c. Research “livelock” and describe it in your own words with example.
d. Describe the difference between “livelock” and “deadlock”.
Mount George Tunnel
The below diagram describes the mountain tunnel connecting both ends of a mountain having
streets on each side that run parallel to one another. The traffic lights at each end of the tunnel are
responsible for managing the cross flows.
Figure 1: Mount George Tunnel
(Source: oocities.org)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
OPERATING SYSTEM
Deadlock Occurrence and Circumstances
Here resources can be the streets in the A and B intersections, these streets are controlled
by the traffic lights. The tests to find out deadlock are given below.
Mutual Exclusion: Every resource in the intersections are assigned one process or vehicle at any
given time when available. Both A and B intersections are assigned to one process. The condition
gets satisfied.
Resource Holding: Processes or vehicles currently utilizing resources or intersections which were
granted previously are able to request newer resource. Vehicles that are moving down the tunnel
from intersection A, are able to request intersection B. The condition gets satisfied.
No Preemption: Any resource granted earlier is not revocable forcibly by another process. These
need to be released explicitly with the particular process acquiring it unless if vehicles get airlifted
out from intersections. The condition gets satisfied.
Circular Wait: There needs to be circular chains comprising several processes that are waiting for
resources held by other members present in this chain. However, here no circular chain is present.
As a result, the circular wait property is missing from this process. Therefore no deadlock can occur
in this scenario.
Traffic lights can control intersections to make them go vacant. In this way, vehicles from the tunnel
can be allowed to exit.
Incorrect operation of traffic lights can lead to starvation but that is not same as deadlocks.
Detection of Deadlocks
Consider the deadlock graph below for Mount George Tunnel. Deadlock can be detected by
applying respective rules.
OPERATING SYSTEM
Deadlock Occurrence and Circumstances
Here resources can be the streets in the A and B intersections, these streets are controlled
by the traffic lights. The tests to find out deadlock are given below.
Mutual Exclusion: Every resource in the intersections are assigned one process or vehicle at any
given time when available. Both A and B intersections are assigned to one process. The condition
gets satisfied.
Resource Holding: Processes or vehicles currently utilizing resources or intersections which were
granted previously are able to request newer resource. Vehicles that are moving down the tunnel
from intersection A, are able to request intersection B. The condition gets satisfied.
No Preemption: Any resource granted earlier is not revocable forcibly by another process. These
need to be released explicitly with the particular process acquiring it unless if vehicles get airlifted
out from intersections. The condition gets satisfied.
Circular Wait: There needs to be circular chains comprising several processes that are waiting for
resources held by other members present in this chain. However, here no circular chain is present.
As a result, the circular wait property is missing from this process. Therefore no deadlock can occur
in this scenario.
Traffic lights can control intersections to make them go vacant. In this way, vehicles from the tunnel
can be allowed to exit.
Incorrect operation of traffic lights can lead to starvation but that is not same as deadlocks.
Detection of Deadlocks
Consider the deadlock graph below for Mount George Tunnel. Deadlock can be detected by
applying respective rules.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
OPERATING SYSTEM
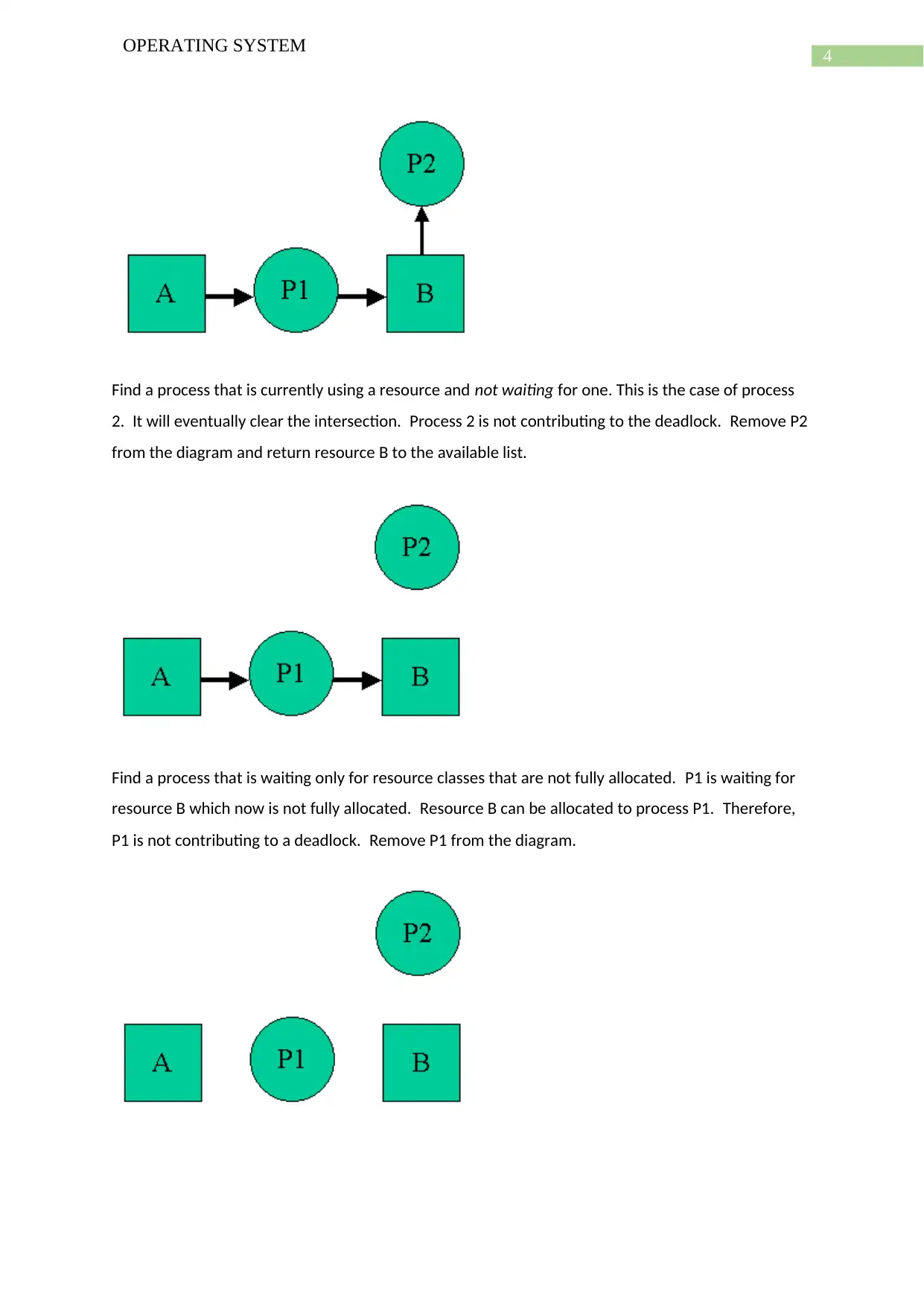
Find a process that is currently using a resource and not waiting for one. This is the case of process
2. It will eventually clear the intersection. Process 2 is not contributing to the deadlock. Remove P2
from the diagram and return resource B to the available list.
Find a process that is waiting only for resource classes that are not fully allocated. P1 is waiting for
resource B which now is not fully allocated. Resource B can be allocated to process P1. Therefore,
P1 is not contributing to a deadlock. Remove P1 from the diagram.
OPERATING SYSTEM
Find a process that is currently using a resource and not waiting for one. This is the case of process
2. It will eventually clear the intersection. Process 2 is not contributing to the deadlock. Remove P2
from the diagram and return resource B to the available list.
Find a process that is waiting only for resource classes that are not fully allocated. P1 is waiting for
resource B which now is not fully allocated. Resource B can be allocated to process P1. Therefore,
P1 is not contributing to a deadlock. Remove P1 from the diagram.

5
OPERATING SYSTEM
There are no processes in the system remaining that can be contributing to a deadlock. The system
both irreducible and has been completely reduced. There is no deadlock.
A livelock is quite similar to deadlocks, only the states of these processes involved in livelocks keep
changing with respect to each otherwith no forward progression. Livelock in other words is a special
kind of starvation which shows that a particular process is unable to progress.
Figure 2: Livelock Example
(Source: courses.cs.cmu.edu)
2. Research on integration of hardware, operating systems and application
software and answer the following:
How do computer hardware, OS and application programs work together? Discuss
the steps involved with their interactions.
The application informs the OS what the program wants to be done like - show window,
display activity, save data.
In return the OS takes these orders and tells the specific hardware what needs to be done.
The role of the OS can thus be described as housekeeping.
OPERATING SYSTEM
There are no processes in the system remaining that can be contributing to a deadlock. The system
both irreducible and has been completely reduced. There is no deadlock.
A livelock is quite similar to deadlocks, only the states of these processes involved in livelocks keep
changing with respect to each otherwith no forward progression. Livelock in other words is a special
kind of starvation which shows that a particular process is unable to progress.
Figure 2: Livelock Example
(Source: courses.cs.cmu.edu)
2. Research on integration of hardware, operating systems and application
software and answer the following:
How do computer hardware, OS and application programs work together? Discuss
the steps involved with their interactions.
The application informs the OS what the program wants to be done like - show window,
display activity, save data.
In return the OS takes these orders and tells the specific hardware what needs to be done.
The role of the OS can thus be described as housekeeping.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
OPERATING SYSTEM
The hardware devices are doing the actual physical work. These can be generating the
display, read and write of files, transferring of data, receive incoming data detecting I/O activities
and sending them to the OS among other tasks.
3. Reason out why are RAM memory capacities in powers of 2 and why don’t
hard disk and DVD discs follow the same norm?
For instance, 512 KB, 512 MB, 1 MB, 2, 4, 8 MB.
RAM or main memory is closely associated with CPU. Making memory size a power of two
helps multiple modules to get packed with minimum logic for switching between them such that
only two or more bits from the very end of the number needs to be checked where the binary
representation of size can be 1000...0000 and so would require several bits if it was not a power of
two.
4. Describe in your own words the purpose and applications of all user
interfaces? Which one you would prefer and why?
In computer applications, the user interface refers to all the designing and
framework for being displayed in information devices through which the users interact.
Companies are increasingly becoming more and more dependent on web and mobile based
applications As a result there has been a recent upsurge in priority on user interface in order
to improve user experience.
OPERATING SYSTEM
The hardware devices are doing the actual physical work. These can be generating the
display, read and write of files, transferring of data, receive incoming data detecting I/O activities
and sending them to the OS among other tasks.
3. Reason out why are RAM memory capacities in powers of 2 and why don’t
hard disk and DVD discs follow the same norm?
For instance, 512 KB, 512 MB, 1 MB, 2, 4, 8 MB.
RAM or main memory is closely associated with CPU. Making memory size a power of two
helps multiple modules to get packed with minimum logic for switching between them such that
only two or more bits from the very end of the number needs to be checked where the binary
representation of size can be 1000...0000 and so would require several bits if it was not a power of
two.
4. Describe in your own words the purpose and applications of all user
interfaces? Which one you would prefer and why?
In computer applications, the user interface refers to all the designing and
framework for being displayed in information devices through which the users interact.
Companies are increasingly becoming more and more dependent on web and mobile based
applications As a result there has been a recent upsurge in priority on user interface in order
to improve user experience.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
OPERATING SYSTEM
5. Answer the below questions for the following disk scheduling algorithms:
FCFS, SSTF, SCAN and LOOK.
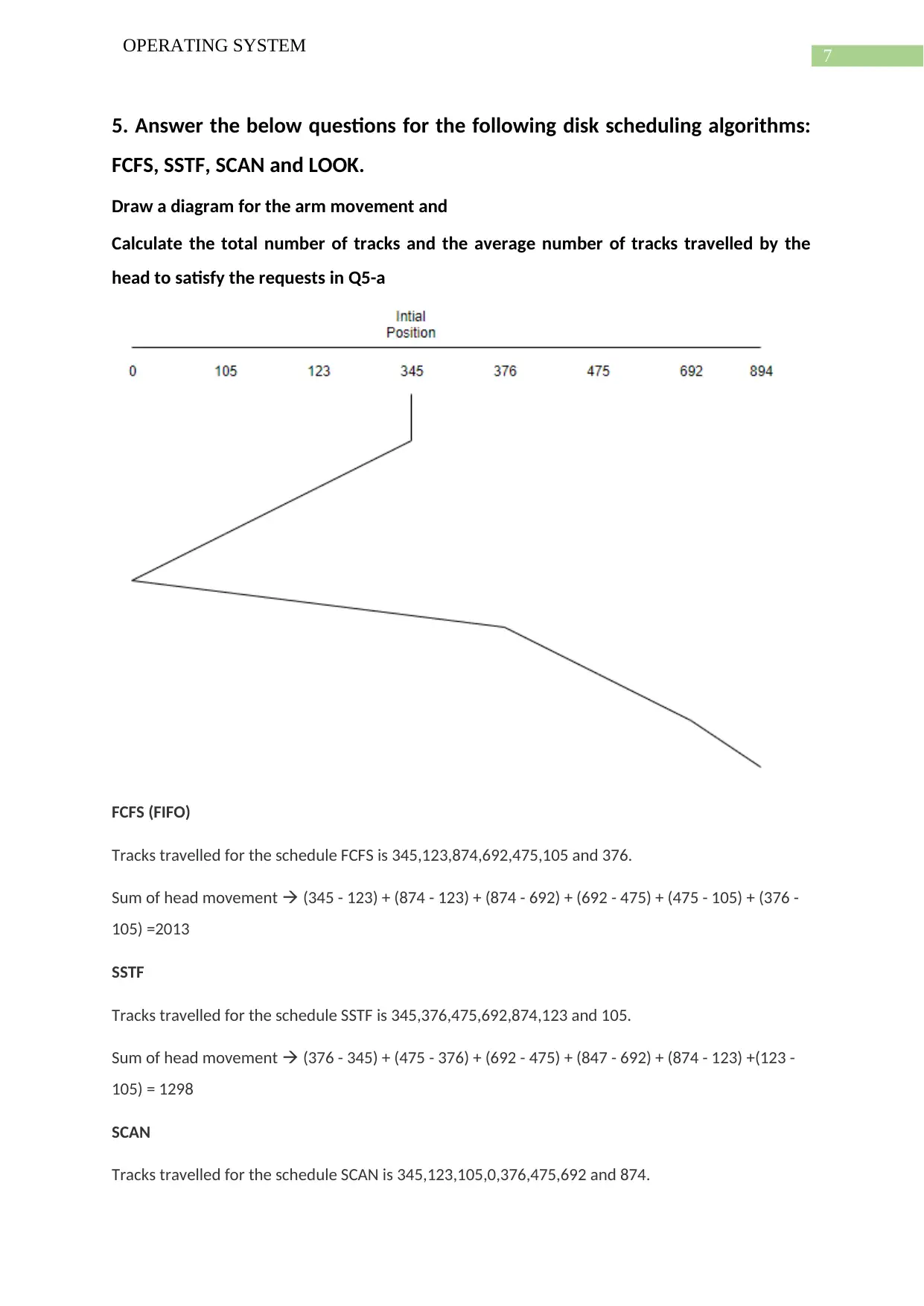
Draw a diagram for the arm movement and
Calculate the total number of tracks and the average number of tracks travelled by the
head to satisfy the requests in Q5-a
FCFS (FIFO)
Tracks travelled for the schedule FCFS is 345,123,874,692,475,105 and 376.
Sum of head movement (345 - 123) + (874 - 123) + (874 - 692) + (692 - 475) + (475 - 105) + (376 -
105) =2013
SSTF
Tracks travelled for the schedule SSTF is 345,376,475,692,874,123 and 105.
Sum of head movement (376 - 345) + (475 - 376) + (692 - 475) + (847 - 692) + (874 - 123) +(123 -
105) = 1298
SCAN
Tracks travelled for the schedule SCAN is 345,123,105,0,376,475,692 and 874.
OPERATING SYSTEM
5. Answer the below questions for the following disk scheduling algorithms:
FCFS, SSTF, SCAN and LOOK.
Draw a diagram for the arm movement and
Calculate the total number of tracks and the average number of tracks travelled by the
head to satisfy the requests in Q5-a
FCFS (FIFO)
Tracks travelled for the schedule FCFS is 345,123,874,692,475,105 and 376.
Sum of head movement (345 - 123) + (874 - 123) + (874 - 692) + (692 - 475) + (475 - 105) + (376 -
105) =2013
SSTF
Tracks travelled for the schedule SSTF is 345,376,475,692,874,123 and 105.
Sum of head movement (376 - 345) + (475 - 376) + (692 - 475) + (847 - 692) + (874 - 123) +(123 -
105) = 1298
SCAN
Tracks travelled for the schedule SCAN is 345,123,105,0,376,475,692 and 874.
8
OPERATING SYSTEM
Sum of head movement (345 - 123) + (123 - 105) + (105 - 0) + (0 - 376) + (376 - 475) +(475 - 692) +
(692 - 874) = 1219
6. Document the following UNIX commands (in clear and concise form):
chmod
ls
cp
chmod: The command ‘chmod’ stands for change mode. This command changes the
permissions of every file according to the mode. Here the mode describes permissions to be
modified.
OPERATING SYSTEM
Sum of head movement (345 - 123) + (123 - 105) + (105 - 0) + (0 - 376) + (376 - 475) +(475 - 692) +
(692 - 874) = 1219
6. Document the following UNIX commands (in clear and concise form):
chmod
ls
cp
chmod: The command ‘chmod’ stands for change mode. This command changes the
permissions of every file according to the mode. Here the mode describes permissions to be
modified.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
OPERATING SYSTEM
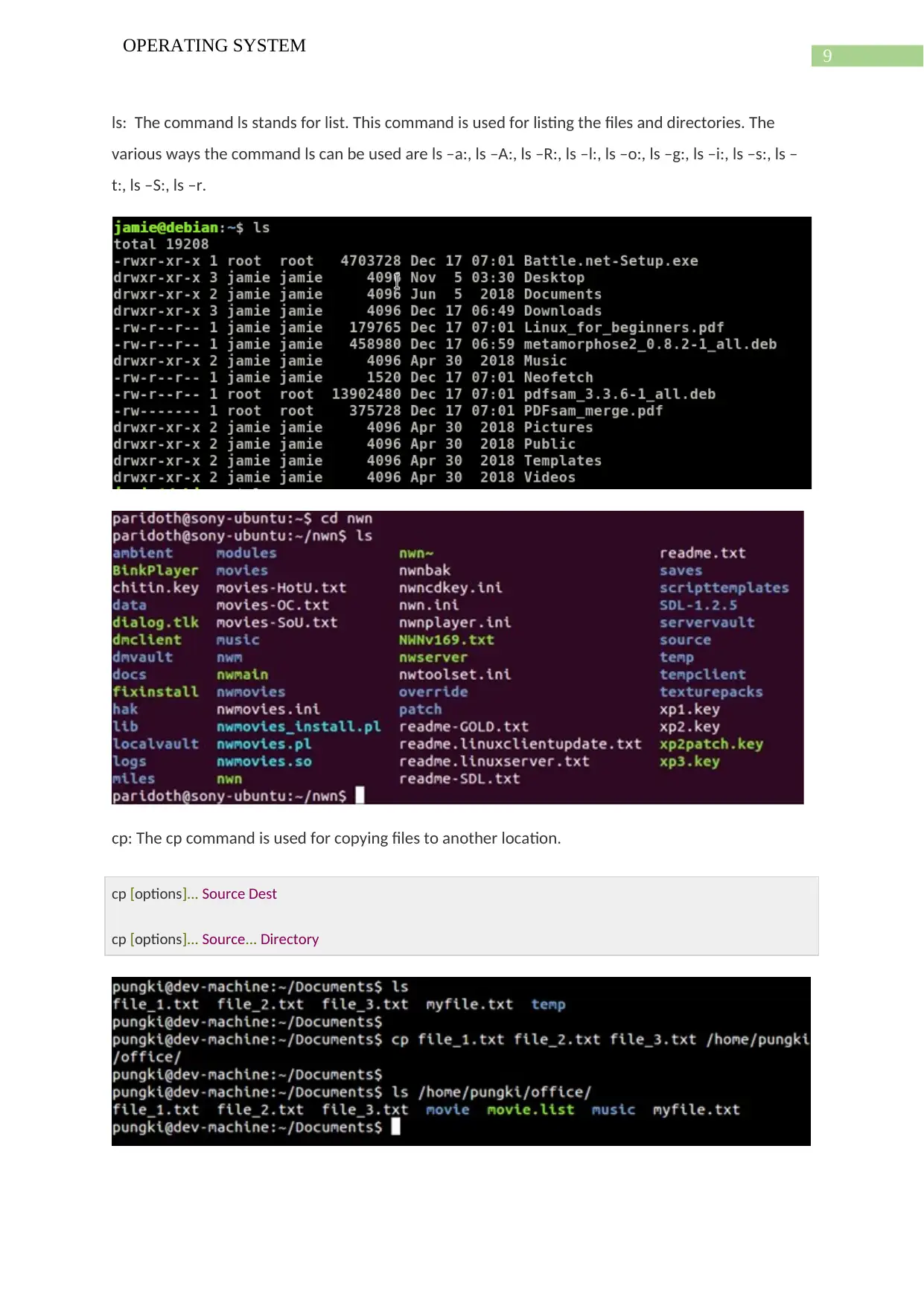
ls: The command ls stands for list. This command is used for listing the files and directories. The
various ways the command ls can be used are ls –a:, ls –A:, ls –R:, ls –l:, ls –o:, ls –g:, ls –i:, ls –s:, ls –
t:, ls –S:, ls –r.
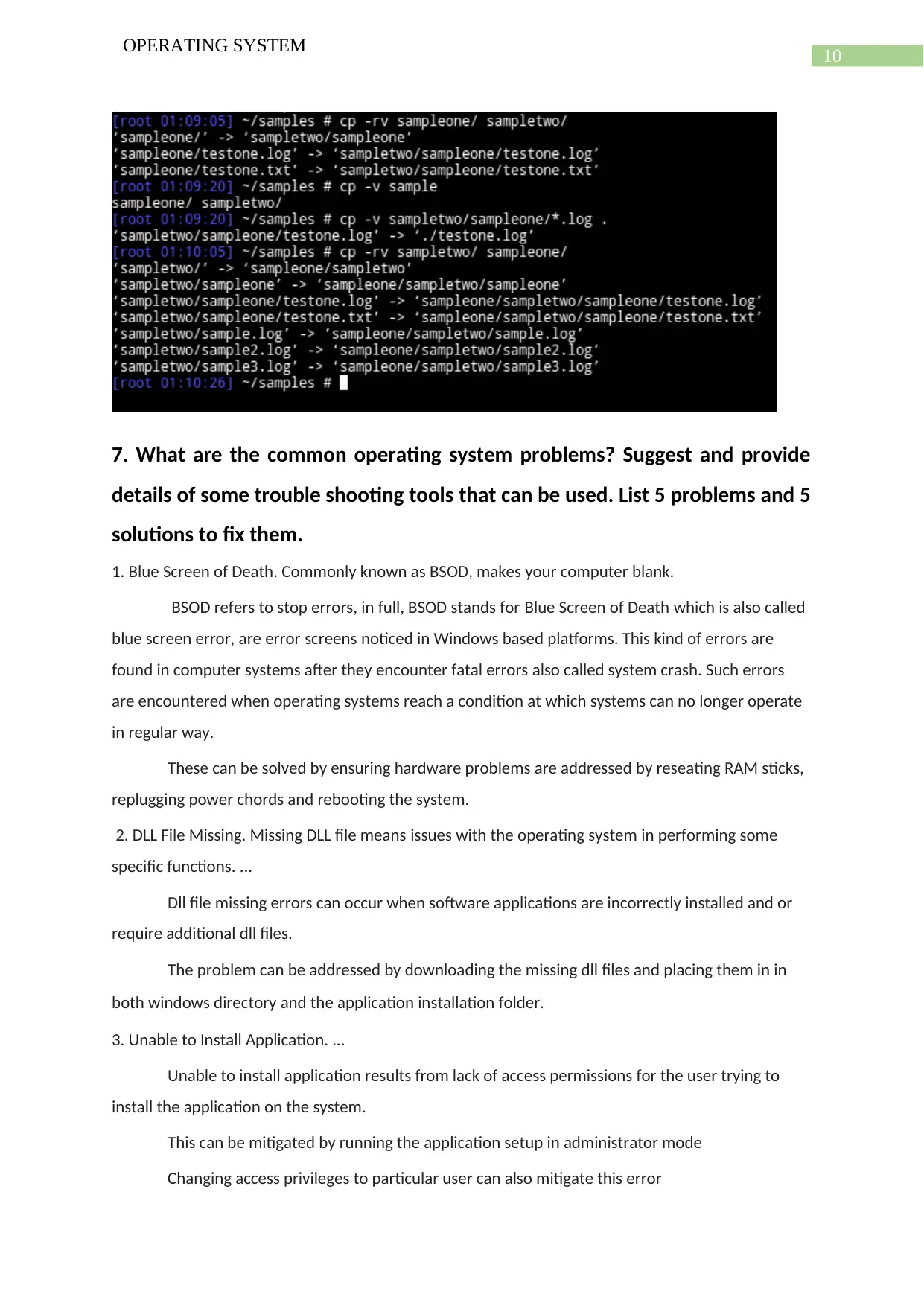
cp: The cp command is used for copying files to another location.
cp [options]... Source Dest
cp [options]... Source... Directory
OPERATING SYSTEM
ls: The command ls stands for list. This command is used for listing the files and directories. The
various ways the command ls can be used are ls –a:, ls –A:, ls –R:, ls –l:, ls –o:, ls –g:, ls –i:, ls –s:, ls –
t:, ls –S:, ls –r.
cp: The cp command is used for copying files to another location.
cp [options]... Source Dest
cp [options]... Source... Directory
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
OPERATING SYSTEM
7. What are the common operating system problems? Suggest and provide
details of some trouble shooting tools that can be used. List 5 problems and 5
solutions to fix them.
1. Blue Screen of Death. Commonly known as BSOD, makes your computer blank.
BSOD refers to stop errors, in full, BSOD stands for Blue Screen of Death which is also called
blue screen error, are error screens noticed in Windows based platforms. This kind of errors are
found in computer systems after they encounter fatal errors also called system crash. Such errors
are encountered when operating systems reach a condition at which systems can no longer operate
in regular way.
These can be solved by ensuring hardware problems are addressed by reseating RAM sticks,
replugging power chords and rebooting the system.
2. DLL File Missing. Missing DLL file means issues with the operating system in performing some
specific functions. ...
Dll file missing errors can occur when software applications are incorrectly installed and or
require additional dll files.
The problem can be addressed by downloading the missing dll files and placing them in in
both windows directory and the application installation folder.
3. Unable to Install Application. ...
Unable to install application results from lack of access permissions for the user trying to
install the application on the system.
This can be mitigated by running the application setup in administrator mode
Changing access privileges to particular user can also mitigate this error
OPERATING SYSTEM
7. What are the common operating system problems? Suggest and provide
details of some trouble shooting tools that can be used. List 5 problems and 5
solutions to fix them.
1. Blue Screen of Death. Commonly known as BSOD, makes your computer blank.
BSOD refers to stop errors, in full, BSOD stands for Blue Screen of Death which is also called
blue screen error, are error screens noticed in Windows based platforms. This kind of errors are
found in computer systems after they encounter fatal errors also called system crash. Such errors
are encountered when operating systems reach a condition at which systems can no longer operate
in regular way.
These can be solved by ensuring hardware problems are addressed by reseating RAM sticks,
replugging power chords and rebooting the system.
2. DLL File Missing. Missing DLL file means issues with the operating system in performing some
specific functions. ...
Dll file missing errors can occur when software applications are incorrectly installed and or
require additional dll files.
The problem can be addressed by downloading the missing dll files and placing them in in
both windows directory and the application installation folder.
3. Unable to Install Application. ...
Unable to install application results from lack of access permissions for the user trying to
install the application on the system.
This can be mitigated by running the application setup in administrator mode
Changing access privileges to particular user can also mitigate this error

11
OPERATING SYSTEM
4. Applications are Running Slow. ...
Slow running of system applications can result from shortage of installed main memory as
well as hard disk space getting filled up.
This problem can get addressed by acquiring additional RAM and hard disks and integrating
the same to the system.
5. Abnormal Behaviour.
Abnormal Behaviour of operating systems usually occur for a short period of time and the
scope of this error is generally local and sudden.
These kind of errors can be mitigated by ensuring enough headroom of resources for all the
tasks in queue.
OPERATING SYSTEM
4. Applications are Running Slow. ...
Slow running of system applications can result from shortage of installed main memory as
well as hard disk space getting filled up.
This problem can get addressed by acquiring additional RAM and hard disks and integrating
the same to the system.
5. Abnormal Behaviour.
Abnormal Behaviour of operating systems usually occur for a short period of time and the
scope of this error is generally local and sudden.
These kind of errors can be mitigated by ensuring enough headroom of resources for all the
tasks in queue.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.