Detailed Comparison of Operating Systems: Windows, iOS, Android, OS X
VerifiedAdded on 2023/05/30
|7
|1695
|237
Report
AI Summary
This report provides a comprehensive comparison of six major operating systems: Windows, iOS, Android, OS X, Linux, and Unix. The comparison is based on criteria such as supported computer architectures, default graphical user interface (GUI), target systems, supported file systems, user-friendliness, firewall integration, encrypted file systems, security threats, shell terminal, and kernel type. Each operating system's strengths and weaknesses are analyzed, with in-text citations supporting the information presented. The report also discusses the best use cases for each OS, justifying the recommendations based on the facts presented in the comparison table. For instance, Windows is highlighted for its user-friendliness and gaming support, while Linux is recommended for desktop tasks and Unix for its stability and cryptography capabilities. The report concludes with a list of references in APA format, providing a well-researched overview of the operating systems landscape.

Running head: COMPARISON OF OPERATING SYSTEMS
Comparison of Operating Systems
Name of the Student
Name of the University
Author’s note
Comparison of Operating Systems
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPARISON OF OPERATING SYSTEMS
Table of Contents
1. Comparison of Operating Systems..............................................................................................2
2. Best use of Operating Systems....................................................................................................3
3. References....................................................................................................................................5
Table of Contents
1. Comparison of Operating Systems..............................................................................................2
2. Best use of Operating Systems....................................................................................................3
3. References....................................................................................................................................5
2COMPARISON OF OPERATING SYSTEMS
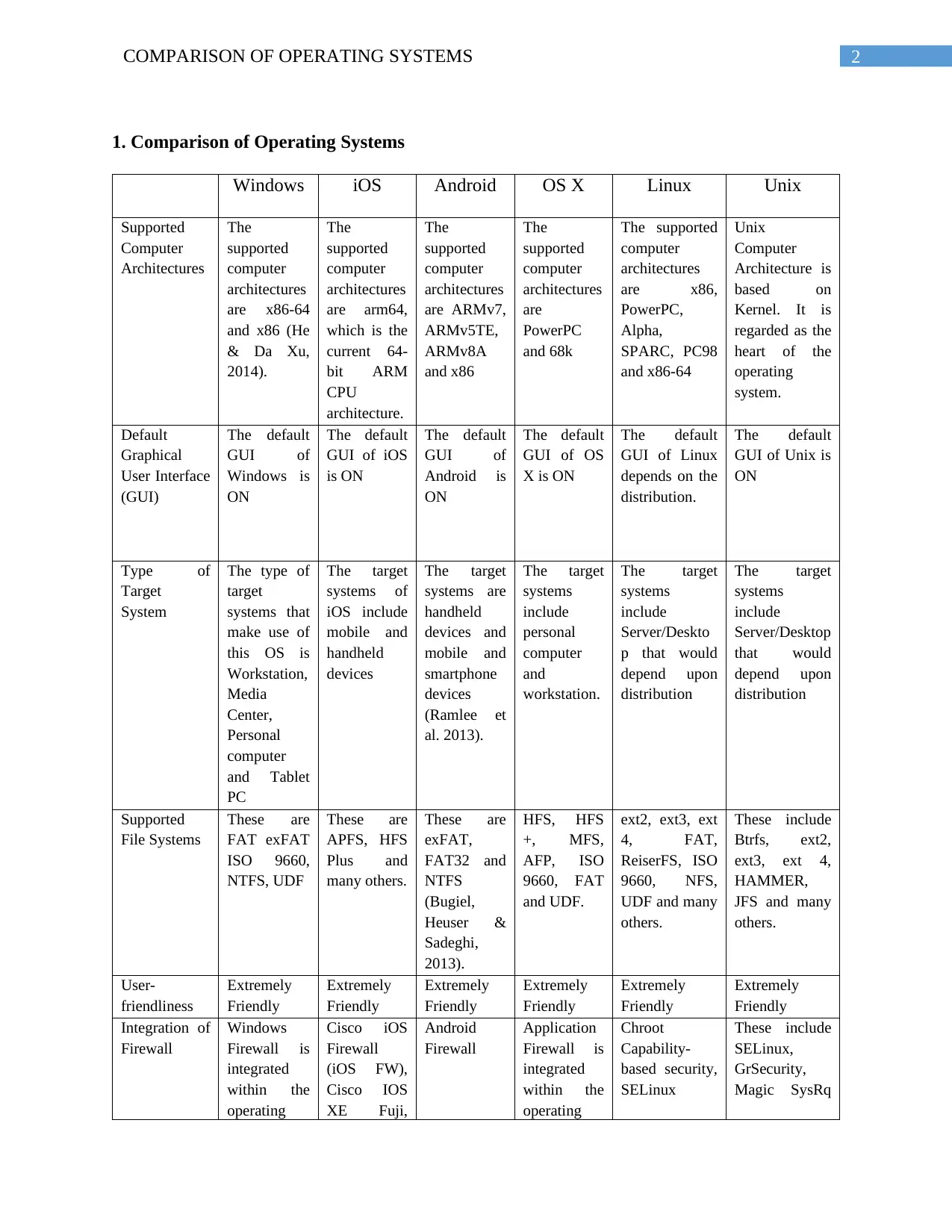
1. Comparison of Operating Systems
Windows iOS Android OS X Linux Unix
Supported
Computer
Architectures
The
supported
computer
architectures
are x86-64
and x86 (He
& Da Xu,
2014).
The
supported
computer
architectures
are arm64,
which is the
current 64-
bit ARM
CPU
architecture.
The
supported
computer
architectures
are ARMv7,
ARMv5TE,
ARMv8A
and x86
The
supported
computer
architectures
are
PowerPC
and 68k
The supported
computer
architectures
are x86,
PowerPC,
Alpha,
SPARC, PC98
and x86-64
Unix
Computer
Architecture is
based on
Kernel. It is
regarded as the
heart of the
operating
system.
Default
Graphical
User Interface
(GUI)
The default
GUI of
Windows is
ON
The default
GUI of iOS
is ON
The default
GUI of
Android is
ON
The default
GUI of OS
X is ON
The default
GUI of Linux
depends on the
distribution.
The default
GUI of Unix is
ON
Type of
Target
System
The type of
target
systems that
make use of
this OS is
Workstation,
Media
Center,
Personal
computer
and Tablet
PC
The target
systems of
iOS include
mobile and
handheld
devices
The target
systems are
handheld
devices and
mobile and
smartphone
devices
(Ramlee et
al. 2013).
The target
systems
include
personal
computer
and
workstation.
The target
systems
include
Server/Deskto
p that would
depend upon
distribution
The target
systems
include
Server/Desktop
that would
depend upon
distribution
Supported
File Systems
These are
FAT exFAT
ISO 9660,
NTFS, UDF
These are
APFS, HFS
Plus and
many others.
These are
exFAT,
FAT32 and
NTFS
(Bugiel,
Heuser &
Sadeghi,
2013).
HFS, HFS
+, MFS,
AFP, ISO
9660, FAT
and UDF.
ext2, ext3, ext
4, FAT,
ReiserFS, ISO
9660, NFS,
UDF and many
others.
These include
Btrfs, ext2,
ext3, ext 4,
HAMMER,
JFS and many
others.
User-
friendliness
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Integration of
Firewall
Windows
Firewall is
integrated
within the
operating
Cisco iOS
Firewall
(iOS FW),
Cisco IOS
XE Fuji,
Android
Firewall
Application
Firewall is
integrated
within the
operating
Chroot
Capability-
based security,
SELinux
These include
SELinux,
GrSecurity,
Magic SysRq
1. Comparison of Operating Systems
Windows iOS Android OS X Linux Unix
Supported
Computer
Architectures
The
supported
computer
architectures
are x86-64
and x86 (He
& Da Xu,
2014).
The
supported
computer
architectures
are arm64,
which is the
current 64-
bit ARM
CPU
architecture.
The
supported
computer
architectures
are ARMv7,
ARMv5TE,
ARMv8A
and x86
The
supported
computer
architectures
are
PowerPC
and 68k
The supported
computer
architectures
are x86,
PowerPC,
Alpha,
SPARC, PC98
and x86-64
Unix
Computer
Architecture is
based on
Kernel. It is
regarded as the
heart of the
operating
system.
Default
Graphical
User Interface
(GUI)
The default
GUI of
Windows is
ON
The default
GUI of iOS
is ON
The default
GUI of
Android is
ON
The default
GUI of OS
X is ON
The default
GUI of Linux
depends on the
distribution.
The default
GUI of Unix is
ON
Type of
Target
System
The type of
target
systems that
make use of
this OS is
Workstation,
Media
Center,
Personal
computer
and Tablet
PC
The target
systems of
iOS include
mobile and
handheld
devices
The target
systems are
handheld
devices and
mobile and
smartphone
devices
(Ramlee et
al. 2013).
The target
systems
include
personal
computer
and
workstation.
The target
systems
include
Server/Deskto
p that would
depend upon
distribution
The target
systems
include
Server/Desktop
that would
depend upon
distribution
Supported
File Systems
These are
FAT exFAT
ISO 9660,
NTFS, UDF
These are
APFS, HFS
Plus and
many others.
These are
exFAT,
FAT32 and
NTFS
(Bugiel,
Heuser &
Sadeghi,
2013).
HFS, HFS
+, MFS,
AFP, ISO
9660, FAT
and UDF.
ext2, ext3, ext
4, FAT,
ReiserFS, ISO
9660, NFS,
UDF and many
others.
These include
Btrfs, ext2,
ext3, ext 4,
HAMMER,
JFS and many
others.
User-
friendliness
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Extremely
Friendly
Integration of
Firewall
Windows
Firewall is
integrated
within the
operating
Cisco iOS
Firewall
(iOS FW),
Cisco IOS
XE Fuji,
Android
Firewall
Application
Firewall is
integrated
within the
operating
Chroot
Capability-
based security,
SELinux
These include
SELinux,
GrSecurity,
Magic SysRq
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3COMPARISON OF OPERATING SYSTEMS
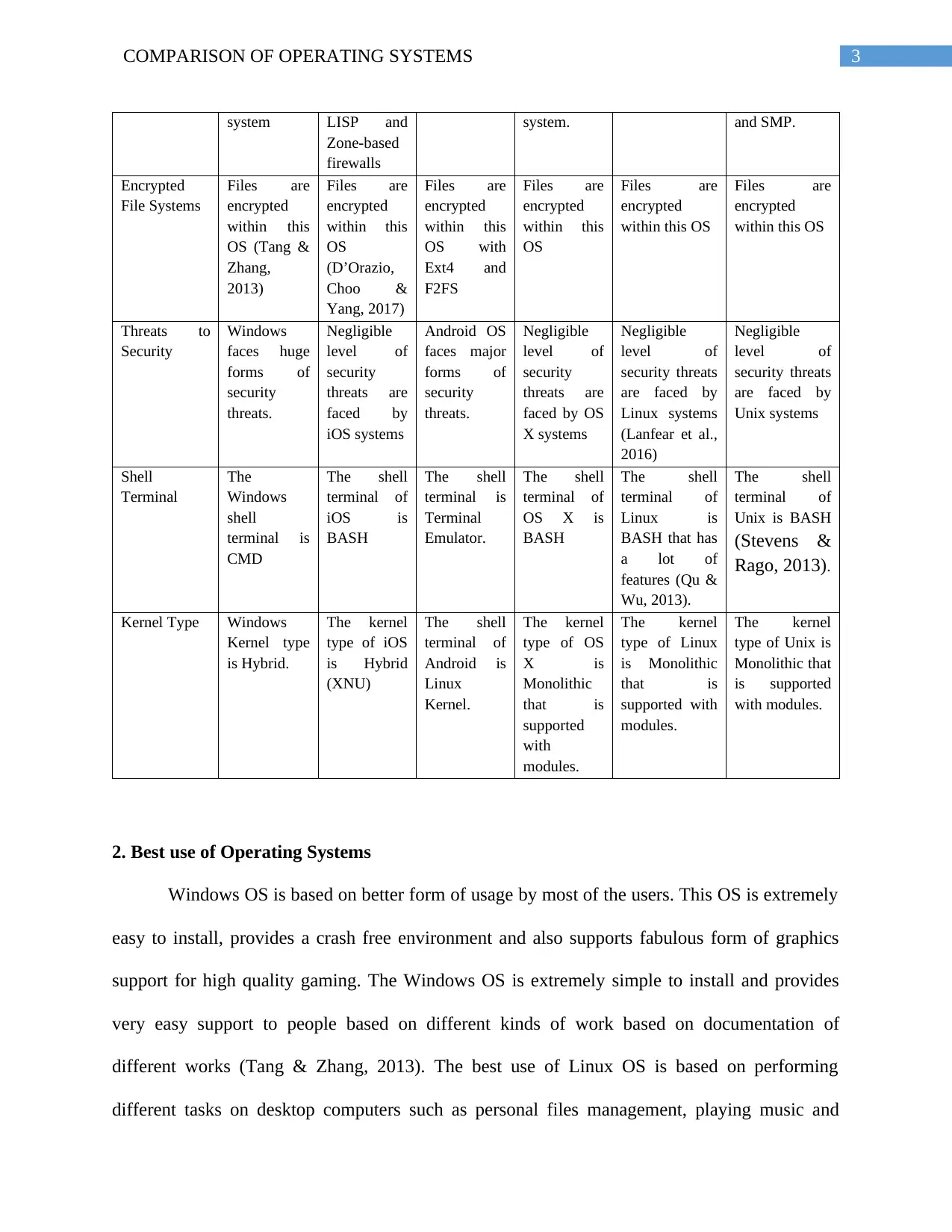
system LISP and
Zone-based
firewalls
system. and SMP.
Encrypted
File Systems
Files are
encrypted
within this
OS (Tang &
Zhang,
2013)
Files are
encrypted
within this
OS
(D’Orazio,
Choo &
Yang, 2017)
Files are
encrypted
within this
OS with
Ext4 and
F2FS
Files are
encrypted
within this
OS
Files are
encrypted
within this OS
Files are
encrypted
within this OS
Threats to
Security
Windows
faces huge
forms of
security
threats.
Negligible
level of
security
threats are
faced by
iOS systems
Android OS
faces major
forms of
security
threats.
Negligible
level of
security
threats are
faced by OS
X systems
Negligible
level of
security threats
are faced by
Linux systems
(Lanfear et al.,
2016)
Negligible
level of
security threats
are faced by
Unix systems
Shell
Terminal
The
Windows
shell
terminal is
CMD
The shell
terminal of
iOS is
BASH
The shell
terminal is
Terminal
Emulator.
The shell
terminal of
OS X is
BASH
The shell
terminal of
Linux is
BASH that has
a lot of
features (Qu &
Wu, 2013).
The shell
terminal of
Unix is BASH
(Stevens &
Rago, 2013).
Kernel Type Windows
Kernel type
is Hybrid.
The kernel
type of iOS
is Hybrid
(XNU)
The shell
terminal of
Android is
Linux
Kernel.
The kernel
type of OS
X is
Monolithic
that is
supported
with
modules.
The kernel
type of Linux
is Monolithic
that is
supported with
modules.
The kernel
type of Unix is
Monolithic that
is supported
with modules.
2. Best use of Operating Systems
Windows OS is based on better form of usage by most of the users. This OS is extremely
easy to install, provides a crash free environment and also supports fabulous form of graphics
support for high quality gaming. The Windows OS is extremely simple to install and provides
very easy support to people based on different kinds of work based on documentation of
different works (Tang & Zhang, 2013). The best use of Linux OS is based on performing
different tasks on desktop computers such as personal files management, playing music and
system LISP and
Zone-based
firewalls
system. and SMP.
Encrypted
File Systems
Files are
encrypted
within this
OS (Tang &
Zhang,
2013)
Files are
encrypted
within this
OS
(D’Orazio,
Choo &
Yang, 2017)
Files are
encrypted
within this
OS with
Ext4 and
F2FS
Files are
encrypted
within this
OS
Files are
encrypted
within this OS
Files are
encrypted
within this OS
Threats to
Security
Windows
faces huge
forms of
security
threats.
Negligible
level of
security
threats are
faced by
iOS systems
Android OS
faces major
forms of
security
threats.
Negligible
level of
security
threats are
faced by OS
X systems
Negligible
level of
security threats
are faced by
Linux systems
(Lanfear et al.,
2016)
Negligible
level of
security threats
are faced by
Unix systems
Shell
Terminal
The
Windows
shell
terminal is
CMD
The shell
terminal of
iOS is
BASH
The shell
terminal is
Terminal
Emulator.
The shell
terminal of
OS X is
BASH
The shell
terminal of
Linux is
BASH that has
a lot of
features (Qu &
Wu, 2013).
The shell
terminal of
Unix is BASH
(Stevens &
Rago, 2013).
Kernel Type Windows
Kernel type
is Hybrid.
The kernel
type of iOS
is Hybrid
(XNU)
The shell
terminal of
Android is
Linux
Kernel.
The kernel
type of OS
X is
Monolithic
that is
supported
with
modules.
The kernel
type of Linux
is Monolithic
that is
supported with
modules.
The kernel
type of Unix is
Monolithic that
is supported
with modules.
2. Best use of Operating Systems
Windows OS is based on better form of usage by most of the users. This OS is extremely
easy to install, provides a crash free environment and also supports fabulous form of graphics
support for high quality gaming. The Windows OS is extremely simple to install and provides
very easy support to people based on different kinds of work based on documentation of
different works (Tang & Zhang, 2013). The best use of Linux OS is based on performing
different tasks on desktop computers such as personal files management, playing music and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPARISON OF OPERATING SYSTEMS
videos and also performing gaming (Lanfear et al., 2016). The Unix based OS is under constant
development. The Unix OS is stable, supports multi-user support, multi-tasking systems for
desktops, laptops and servers. The Unix OS is also best in terms of cryptography (Stevens &
Rago, 2013). The Macintosh OS is one of the best operating systems based on Apple Computer
Macintosh line of workstations and personal computers. The most popular feature of the latest
version of Mac OS X is a type of desktop interface that would have some form of characteristics
of 3D appearance. The OS X has a different form of modular design. This is mainly intended for
most of the user in order to make it easy for them for adding new kind of features to the OS in
the future. The OS X is highly useful for programming development (Campigotto, McEwen &
Epp, 2013). The OS X is highly secure and helps in providing a different form of secure
operating platform.
The Android OS is one of the operating systems that was created by Google. This OS is
based on mobile devices that includes tablets and smartphones. The Android OS has been
developed for multi-users and hence supports a large number of devices. This kind of OS
provides easy form of customization (Peiravian & Zhu, 2013). They offer huge number of
applications and also offers security features. The iOS provides a high level of feature for the
users. The operating system is highly accessible. It supports multi-tasking and different modes of
switching applications (Campigotto, McEwen & Epp, 2013). iOS also provides better and a high
level of security feature for their users. This form of high-level security would be able to break
by most of the hackers and thus performing different tasks is highly easy and secure. This form
of secure platform would be helpful for the users as they would be helpful for making different
kinds of functionalities and payments, which demand high level of security.
videos and also performing gaming (Lanfear et al., 2016). The Unix based OS is under constant
development. The Unix OS is stable, supports multi-user support, multi-tasking systems for
desktops, laptops and servers. The Unix OS is also best in terms of cryptography (Stevens &
Rago, 2013). The Macintosh OS is one of the best operating systems based on Apple Computer
Macintosh line of workstations and personal computers. The most popular feature of the latest
version of Mac OS X is a type of desktop interface that would have some form of characteristics
of 3D appearance. The OS X has a different form of modular design. This is mainly intended for
most of the user in order to make it easy for them for adding new kind of features to the OS in
the future. The OS X is highly useful for programming development (Campigotto, McEwen &
Epp, 2013). The OS X is highly secure and helps in providing a different form of secure
operating platform.
The Android OS is one of the operating systems that was created by Google. This OS is
based on mobile devices that includes tablets and smartphones. The Android OS has been
developed for multi-users and hence supports a large number of devices. This kind of OS
provides easy form of customization (Peiravian & Zhu, 2013). They offer huge number of
applications and also offers security features. The iOS provides a high level of feature for the
users. The operating system is highly accessible. It supports multi-tasking and different modes of
switching applications (Campigotto, McEwen & Epp, 2013). iOS also provides better and a high
level of security feature for their users. This form of high-level security would be able to break
by most of the hackers and thus performing different tasks is highly easy and secure. This form
of secure platform would be helpful for the users as they would be helpful for making different
kinds of functionalities and payments, which demand high level of security.

5COMPARISON OF OPERATING SYSTEMS
3. References
Bugiel, S., Heuser, S., & Sadeghi, A. R. (2013). Flexible and fine-grained mandatory access
control on android for diverse security and privacy policies. In Presented as part of the
22nd {USENIX} Security Symposium ({USENIX} Security 13) (pp. 131-146).
Campigotto, R., McEwen, R., & Epp, C. D. (2013). Especially social: Exploring the use of an
iOS application in special needs classrooms. Computers & Education, 60(1), 74-86.
D’Orazio, C. J., Choo, K. K. R., & Yang, L. T. (2017). Data exfiltration from internet of things
devices: iOS devices as case studies. IEEE Internet of Things Journal, 4(2), 524-535.
He, W., & Da Xu, L. (2014). Integration of distributed enterprise applications: A survey. IEEE
Transactions on Industrial Informatics, 10(1), 35-42.
Lanfear, R., Frandsen, P. B., Wright, A. M., Senfeld, T., & Calcott, B. (2016). PartitionFinder 2:
new methods for selecting partitioned models of evolution for molecular and
morphological phylogenetic analyses. Molecular Biology and Evolution, 34(3), 772-773.
Peiravian, N., & Zhu, X. (2013, November). Machine learning for android malware detection
using permission and api calls. In Tools with Artificial Intelligence (ICTAI), 2013 IEEE
25th International Conference on (pp. 300-305). IEEE.
Qu, B., & Wu, Z. Z. (2013). Design of Mini Multi-Process Micro-Kernel Embedded OS on
ARM. In Applied Mechanics and Materials (Vol. 347, pp. 1780-1785). Trans Tech
Publications.
3. References
Bugiel, S., Heuser, S., & Sadeghi, A. R. (2013). Flexible and fine-grained mandatory access
control on android for diverse security and privacy policies. In Presented as part of the
22nd {USENIX} Security Symposium ({USENIX} Security 13) (pp. 131-146).
Campigotto, R., McEwen, R., & Epp, C. D. (2013). Especially social: Exploring the use of an
iOS application in special needs classrooms. Computers & Education, 60(1), 74-86.
D’Orazio, C. J., Choo, K. K. R., & Yang, L. T. (2017). Data exfiltration from internet of things
devices: iOS devices as case studies. IEEE Internet of Things Journal, 4(2), 524-535.
He, W., & Da Xu, L. (2014). Integration of distributed enterprise applications: A survey. IEEE
Transactions on Industrial Informatics, 10(1), 35-42.
Lanfear, R., Frandsen, P. B., Wright, A. M., Senfeld, T., & Calcott, B. (2016). PartitionFinder 2:
new methods for selecting partitioned models of evolution for molecular and
morphological phylogenetic analyses. Molecular Biology and Evolution, 34(3), 772-773.
Peiravian, N., & Zhu, X. (2013, November). Machine learning for android malware detection
using permission and api calls. In Tools with Artificial Intelligence (ICTAI), 2013 IEEE
25th International Conference on (pp. 300-305). IEEE.
Qu, B., & Wu, Z. Z. (2013). Design of Mini Multi-Process Micro-Kernel Embedded OS on
ARM. In Applied Mechanics and Materials (Vol. 347, pp. 1780-1785). Trans Tech
Publications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPARISON OF OPERATING SYSTEMS
Ramlee, R. A., Othman, M. A., Leong, M. H., Ismail, M. M., & Ranjit, S. S. S. (2013, March).
Smart home system using android application. In Information and Communication
Technology (ICoICT), 2013 International Conference of (pp. 277-280). IEEE.
Stevens, W. R., & Rago, S. A. (2013). Advanced programming in the UNIX environment.
Addison-Wesley.
Tang, Q. Y., & Zhang, C. X. (2013). Data Processing System (DPS) software with experimental
design, statistical analysis and data mining developed for use in entomological
research. Insect Science, 20(2), 254-260.
Ramlee, R. A., Othman, M. A., Leong, M. H., Ismail, M. M., & Ranjit, S. S. S. (2013, March).
Smart home system using android application. In Information and Communication
Technology (ICoICT), 2013 International Conference of (pp. 277-280). IEEE.
Stevens, W. R., & Rago, S. A. (2013). Advanced programming in the UNIX environment.
Addison-Wesley.
Tang, Q. Y., & Zhang, C. X. (2013). Data Processing System (DPS) software with experimental
design, statistical analysis and data mining developed for use in entomological
research. Insect Science, 20(2), 254-260.
1 out of 7
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.