Operation Contingencies Report: Threats, Risks and Mitigation
VerifiedAdded on 2020/05/04
|9
|1570
|33
Report
AI Summary
This report examines operation contingencies, focusing on the increasing importance of securing organizational data in the face of modern technology and the rise of internet threats. It explores various security challenges, including eavesdropping, penetration, viruses, denial-of-service attacks, human error, and natural disasters. The report delves into redundancy measures, such as fault-tolerant systems and data backups, and discusses the significance of company policies, user group privilege management, and utility backups. It includes a risk-minimization plan with associated costs and specifications, assesses business-critical elements, and analyzes vulnerabilities and threats. The report proposes establishing alternate sites for data storage and emphasizes the need for employee security training and access control measures. References to relevant research are included. This report provides a comprehensive overview of operation contingencies, security measures, and risk management strategies in the current technological landscape.

Operation contingencies 1
OPERATION CONTINGENCIES
Course:
Tutor:
University:
University location
Date:
OPERATION CONTINGENCIES
Course:
Tutor:
University:
University location
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATION CONTINGENCIES 2
Assessment One.
Introduction
Organizations currently are rapidly immersing themselves into the modern technology to
maximize operation. This has brought on board increased internet threats that are even more
devastating than just deploying manual operations. The trend has shifted to securing the
organization data more meanly than service delivery. Organizations have put in place resources
to curb impending risks and unnecessary attacks into the systems. As a result innovations in the
networking field have been able to come up with concepts like SDN and NFV. This technology
has enhanced security and minimized cost. Threats range from natural disasters to man-made
disasters.
Eavesdropping
Computer attacks have been the major security challenges facing organizations in the recent
times. Eavesdropping computer attack is an unauthorized interception of secret communications
such as phone calls and messages transmission in real time (Thurner 2017). This is achieved
through development of encryption software that is capable of intercepting messages before
getting into the destination; they decrypt the data and direct it to a different destination. It is also
referred to as wiretapping.
Penetration
Penetration is a computer attack technique that that involves malicious entry into private systems
with the aim of getting vital information about the organization (Chen 2016). Penetration is
achieved after a thorough reconnaissance of the target system to detect faults.
Assessment One.
Introduction
Organizations currently are rapidly immersing themselves into the modern technology to
maximize operation. This has brought on board increased internet threats that are even more
devastating than just deploying manual operations. The trend has shifted to securing the
organization data more meanly than service delivery. Organizations have put in place resources
to curb impending risks and unnecessary attacks into the systems. As a result innovations in the
networking field have been able to come up with concepts like SDN and NFV. This technology
has enhanced security and minimized cost. Threats range from natural disasters to man-made
disasters.
Eavesdropping
Computer attacks have been the major security challenges facing organizations in the recent
times. Eavesdropping computer attack is an unauthorized interception of secret communications
such as phone calls and messages transmission in real time (Thurner 2017). This is achieved
through development of encryption software that is capable of intercepting messages before
getting into the destination; they decrypt the data and direct it to a different destination. It is also
referred to as wiretapping.
Penetration
Penetration is a computer attack technique that that involves malicious entry into private systems
with the aim of getting vital information about the organization (Chen 2016). Penetration is
achieved after a thorough reconnaissance of the target system to detect faults.

OPERATION CONTINGENCIES 3
Viruses
Viruses are known to offer protection from suspicious software. When a machine is actively
protected by a legit antivirus, it is not easy for an attacker to gain entry into your computer.
Viruses have the ability to prevent, detect and stop installation of suspicious software or opening
of malicious websites.
Denial of service attack
Denial of service attack is mostly evident in the banking system. Hardly do banks come out to
reveal that they have been attacked. Denying an attack is not a good practice.
Human error
Human error in the computer attack industry is mostly forgetting to log out from the system after
a day’s work. Forgetting to log out, grants an attacker an easier access into the system. Another
error is opening of counterfeit links. The links may be software that can automatically get
installed unknowingly.
Bomb threat
Bombs may destroy the networking system or damage the computers completely. Bombs can
smash servers hence exposing data to potential attackers
Storms or earthquake
As discussed in the journal (Lam 2017). Natural disasters such as floods, storms and earthquakes
are some the rare but fatal threats to data loss. They cannot be prevented and hardly are they
detected. Storms can lead to permanent loss of data.
Viruses
Viruses are known to offer protection from suspicious software. When a machine is actively
protected by a legit antivirus, it is not easy for an attacker to gain entry into your computer.
Viruses have the ability to prevent, detect and stop installation of suspicious software or opening
of malicious websites.
Denial of service attack
Denial of service attack is mostly evident in the banking system. Hardly do banks come out to
reveal that they have been attacked. Denying an attack is not a good practice.
Human error
Human error in the computer attack industry is mostly forgetting to log out from the system after
a day’s work. Forgetting to log out, grants an attacker an easier access into the system. Another
error is opening of counterfeit links. The links may be software that can automatically get
installed unknowingly.
Bomb threat
Bombs may destroy the networking system or damage the computers completely. Bombs can
smash servers hence exposing data to potential attackers
Storms or earthquake
As discussed in the journal (Lam 2017). Natural disasters such as floods, storms and earthquakes
are some the rare but fatal threats to data loss. They cannot be prevented and hardly are they
detected. Storms can lead to permanent loss of data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPERATION CONTINGENCIES 4
2
Redundancies
Redundancies in the business environment refer to duplicating data so that incase of failure or
loss, then the data can be retrieved from back-up. It is advisable for organizations to practice data
duplication to safeguard data loss.
Fault tolerant systems
Modern innovations in the technology industry have brought on course attack resistant systems.
The systems are equipped with both risk proof hardware and software. The systems are meant to
withstand attacks to certain extents then replaced. Fault tolerant systems have gained popularity
nowadays thus recommended to organizations.
Computer backups
Data backup one of the mechanisms used by organizations today to safeguard data. Data is stored
in a storage server and updated periodically so that information in the backup server is up to date.
It is technically advisable to have the backup server located at a secure environment, to be
precise, far away from the organization premises.
Alternative site
Organizations are of late contemplating storing their data at a secure, private place.
Company policy planning
It is advisable that company stakeholders and staff should hold outstanding morals and ethics for
proper coordination towards service delivery (Kock 2016). Company expenditures on their
2
Redundancies
Redundancies in the business environment refer to duplicating data so that incase of failure or
loss, then the data can be retrieved from back-up. It is advisable for organizations to practice data
duplication to safeguard data loss.
Fault tolerant systems
Modern innovations in the technology industry have brought on course attack resistant systems.
The systems are equipped with both risk proof hardware and software. The systems are meant to
withstand attacks to certain extents then replaced. Fault tolerant systems have gained popularity
nowadays thus recommended to organizations.
Computer backups
Data backup one of the mechanisms used by organizations today to safeguard data. Data is stored
in a storage server and updated periodically so that information in the backup server is up to date.
It is technically advisable to have the backup server located at a secure environment, to be
precise, far away from the organization premises.
Alternative site
Organizations are of late contemplating storing their data at a secure, private place.
Company policy planning
It is advisable that company stakeholders and staff should hold outstanding morals and ethics for
proper coordination towards service delivery (Kock 2016). Company expenditures on their
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATION CONTINGENCIES 5
employees should be proportional to the resource outsourced from the company. The human
resource managers have the responsibility to ensure all employees are paid in time to avoid
worker stunts and strikes that may lead to information leakage.
User group privilege management
Companies that have created teamwork and groups between their employees have been
advancing greatly. When employees are grouped then assigned responsibilities, workers feel
encouraged and performance shoots.
Utility backups
Ensuring standby electricity and water supply maximizes service delivery; therefore, companies
should take into consideration of backing up utility services in order to increase profits.
3.
Risk minimizing plan is costly since companies have to incur double costs on purchasing storage
devices. It is important to prevent possible data loss rather than recovering lost data. Having
remote servers in the system is less secure than having manual backups. Remote servers are
prone to attacks than manual servers. On utility backups, if for instance, a company does not
have standby generators or water storage tanks, then whenever a breakdown of any of those
utilities happens, losses are incurred.
employees should be proportional to the resource outsourced from the company. The human
resource managers have the responsibility to ensure all employees are paid in time to avoid
worker stunts and strikes that may lead to information leakage.
User group privilege management
Companies that have created teamwork and groups between their employees have been
advancing greatly. When employees are grouped then assigned responsibilities, workers feel
encouraged and performance shoots.
Utility backups
Ensuring standby electricity and water supply maximizes service delivery; therefore, companies
should take into consideration of backing up utility services in order to increase profits.
3.
Risk minimizing plan is costly since companies have to incur double costs on purchasing storage
devices. It is important to prevent possible data loss rather than recovering lost data. Having
remote servers in the system is less secure than having manual backups. Remote servers are
prone to attacks than manual servers. On utility backups, if for instance, a company does not
have standby generators or water storage tanks, then whenever a breakdown of any of those
utilities happens, losses are incurred.
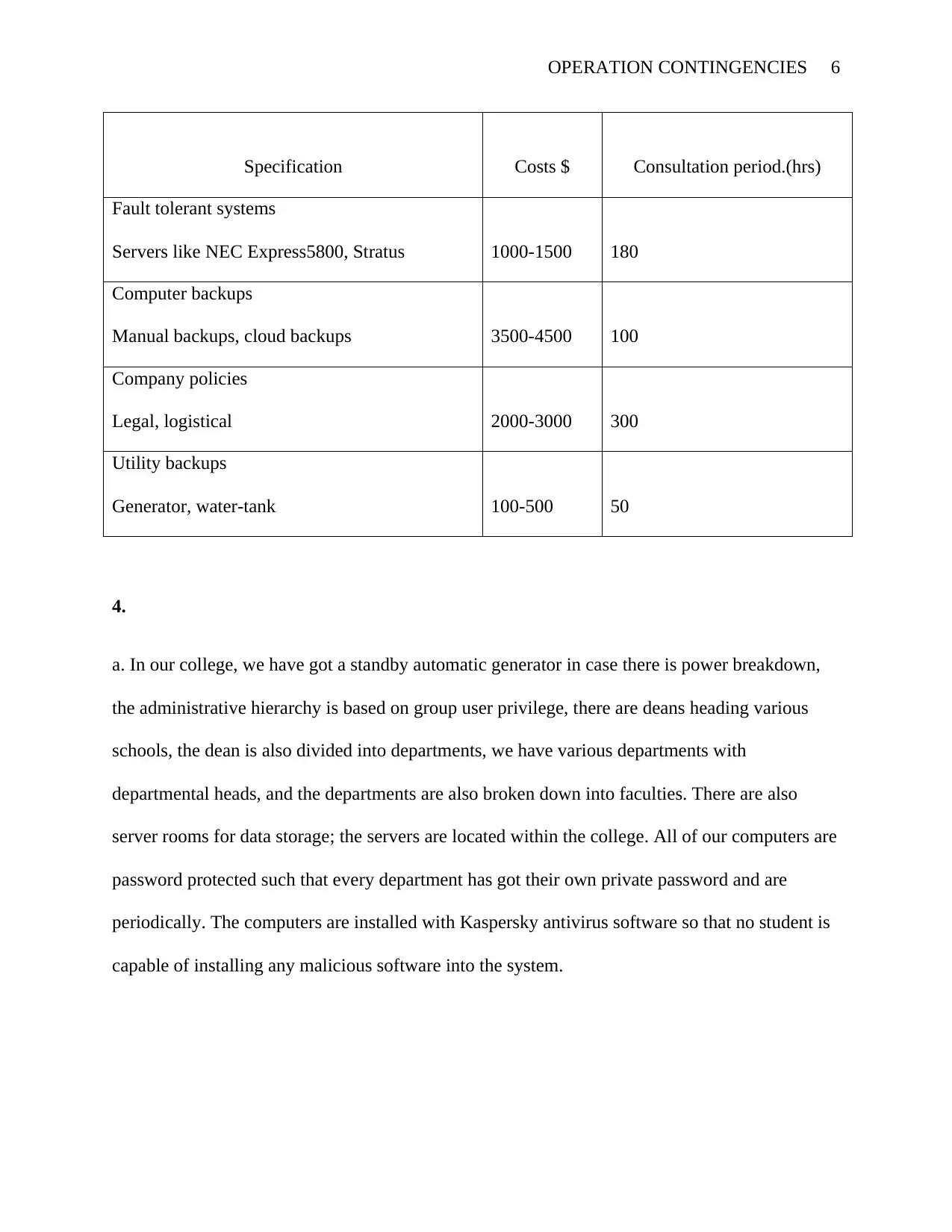
OPERATION CONTINGENCIES 6
Specification Costs $ Consultation period.(hrs)
Fault tolerant systems
Servers like NEC Express5800, Stratus 1000-1500 180
Computer backups
Manual backups, cloud backups 3500-4500 100
Company policies
Legal, logistical 2000-3000 300
Utility backups
Generator, water-tank 100-500 50
4.
a. In our college, we have got a standby automatic generator in case there is power breakdown,
the administrative hierarchy is based on group user privilege, there are deans heading various
schools, the dean is also divided into departments, we have various departments with
departmental heads, and the departments are also broken down into faculties. There are also
server rooms for data storage; the servers are located within the college. All of our computers are
password protected such that every department has got their own private password and are
periodically. The computers are installed with Kaspersky antivirus software so that no student is
capable of installing any malicious software into the system.
Specification Costs $ Consultation period.(hrs)
Fault tolerant systems
Servers like NEC Express5800, Stratus 1000-1500 180
Computer backups
Manual backups, cloud backups 3500-4500 100
Company policies
Legal, logistical 2000-3000 300
Utility backups
Generator, water-tank 100-500 50
4.
a. In our college, we have got a standby automatic generator in case there is power breakdown,
the administrative hierarchy is based on group user privilege, there are deans heading various
schools, the dean is also divided into departments, we have various departments with
departmental heads, and the departments are also broken down into faculties. There are also
server rooms for data storage; the servers are located within the college. All of our computers are
password protected such that every department has got their own private password and are
periodically. The computers are installed with Kaspersky antivirus software so that no student is
capable of installing any malicious software into the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPERATION CONTINGENCIES 7
5.
Business critical elements
Business critical elements include; team building, continuous growth, marketing the business
products and strategy, financial management, business planning and customer care techniques.
APD Company seems to have good business planning owing to the fact of having 140
employees; the company also has got a favorable financial management strategy that has enabled
it maintain such a high number of employees.
Vulnerabilities and threats
Risks are anywhere and when they come calling, everything shifts to unfortunates. Any company
is vulnerable to attacks and thus a need to ensure proper security mechanism. Whenever there is
a threat to data security, it is important to first ensure security of crucial data like passwords. A
website that is vulnerable should be pulled down for maintenance.
Budget requirements
The budget for redundant and fault tolerant systems cannot be reduced or ignored, purchasing
storage equipment and the fault proof servers is essential to keeping data safe. Budget for
alternate sites can be ignored and set the funds to acquiring state of the art remote backup
servers. Policy updates only requires experts on legal and logistical consultants. Hiring the
services of both experts is costly but advantageous. Access control only requires authentication
and verification mechanisms, this can be achieved through passwords.
I propose to my college to establish alternate sites since all the backup servers are distributed
within the college, this could be risky.
5.
Business critical elements
Business critical elements include; team building, continuous growth, marketing the business
products and strategy, financial management, business planning and customer care techniques.
APD Company seems to have good business planning owing to the fact of having 140
employees; the company also has got a favorable financial management strategy that has enabled
it maintain such a high number of employees.
Vulnerabilities and threats
Risks are anywhere and when they come calling, everything shifts to unfortunates. Any company
is vulnerable to attacks and thus a need to ensure proper security mechanism. Whenever there is
a threat to data security, it is important to first ensure security of crucial data like passwords. A
website that is vulnerable should be pulled down for maintenance.
Budget requirements
The budget for redundant and fault tolerant systems cannot be reduced or ignored, purchasing
storage equipment and the fault proof servers is essential to keeping data safe. Budget for
alternate sites can be ignored and set the funds to acquiring state of the art remote backup
servers. Policy updates only requires experts on legal and logistical consultants. Hiring the
services of both experts is costly but advantageous. Access control only requires authentication
and verification mechanisms, this can be achieved through passwords.
I propose to my college to establish alternate sites since all the backup servers are distributed
within the college, this could be risky.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATION CONTINGENCIES 8
6.
Companies have resolved to periodical security trainings for employees in order to keep them up
to date on current security mechanisms in service. Computer attack is evolving occasionally thus
a need to also be up to date. Keeping backup sites secure should be taken into consideration since
if an attacker gains access into the backup server, then it is like all is gone. Equipping your senior
employees with access privileges into the system should done carefully in such a way that only
trusted employees get credentials to access the system.
6.
Companies have resolved to periodical security trainings for employees in order to keep them up
to date on current security mechanisms in service. Computer attack is evolving occasionally thus
a need to also be up to date. Keeping backup sites secure should be taken into consideration since
if an attacker gains access into the backup server, then it is like all is gone. Equipping your senior
employees with access privileges into the system should done carefully in such a way that only
trusted employees get credentials to access the system.

OPERATION CONTINGENCIES 9
References
Chen, C.J., Lin, B.W., Lin, Y.H. and Hsiao, Y.C., 2016, 'ownership structure, independent board
members and innovation performance: A contingency perspective', Journal of business
Research, pp. pp. 3371-3379.
Kock, A,HWAGHG, 2016, 'A Contingency Approach on the Impact of Front-End Success on
Project Portfolio success', Project managament Journal , pp. pp. 115-129.
Lam, TASN,N, 2017, 'A risk Management Approach for Prediction of Contigency Sum for
Public-Sector Construction Projects', In the proceedings of the 20th International Synposium on
Advancement of Construction Management and Real Estate, no. Springer , pp. pp. 367-378.
Thurner, L,SA,PAABM, 2017, 'Heuristic optimisation for network restoration and expansion in
compliance with the single-contingency policy', IET Generation, Transmission & Distributions.
References
Chen, C.J., Lin, B.W., Lin, Y.H. and Hsiao, Y.C., 2016, 'ownership structure, independent board
members and innovation performance: A contingency perspective', Journal of business
Research, pp. pp. 3371-3379.
Kock, A,HWAGHG, 2016, 'A Contingency Approach on the Impact of Front-End Success on
Project Portfolio success', Project managament Journal , pp. pp. 115-129.
Lam, TASN,N, 2017, 'A risk Management Approach for Prediction of Contigency Sum for
Public-Sector Construction Projects', In the proceedings of the 20th International Synposium on
Advancement of Construction Management and Real Estate, no. Springer , pp. pp. 367-378.
Thurner, L,SA,PAABM, 2017, 'Heuristic optimisation for network restoration and expansion in
compliance with the single-contingency policy', IET Generation, Transmission & Distributions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


