Comprehensive Risk Assessment and Analysis for Aztek IT Outsourcing
VerifiedAdded on 2020/04/07
|21
|6235
|58
Report
AI Summary
This report provides a comprehensive risk assessment for Aztek, a financial institution, considering the potential of outsourcing its IT services. It examines the main functions of IT, the reasons for outsourcing, and the regulations involved. The report identifies various cyber risks, including cybercrimes, espionage, fraud, and terrorism, and proposes mitigation strategies. It also addresses data security concerns, including theft, loss, and improper deletion. Effective data risk management techniques such as encryption, authorization, digital signatures, and biometrics are discussed. The report concludes with a recommendation for Aztek to outsource key IT roles while implementing stringent security measures and regular inspections to ensure the safety of its data and operations. The financial advantages, such as cost reduction, tax advantages, and increased cash flow, are also highlighted, emphasizing the importance of a well-managed outsourcing process.

NAME
STUDENT ID
INSTRUCTOR
AFFILIATE INSTITUTION
SUBJECT
TOPIC
DATE
1
STUDENT ID
INSTRUCTOR
AFFILIATE INSTITUTION
SUBJECT
TOPIC
DATE
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT FOR OUTSOURCING IT SERVICES
EXECUTIVE SUMMARY
Key Information Technology (IT) functionality comprises a set of the major tasks performed by
the latter in the organization. These functions include planning, communication, application and
network development and technology support (Galliers et al, 2014). Outsourcing is the act of
procuring these IT functionalities from an outside vendor especially if the organization’s IT team
can carry them out. Aztek is a financial institution that is responsible for accepting deposits from
the general public and issuing out loans. It has a strong IT team that carries out all the roles of IT.
Lately, however, Aztek’s management has been considering outsourcing IT services to give the
IT team enough time to concentrate on other more demanding issues. This has been as a result of
the organization’s fast growth.
Outsourcing IT functionality is a very beneficial step to Aztek as it leads to risk sharing between
the institution and the outsourcer. It is also a cost-effective way for the organizationto have a
functioning computer system and allow sufficient time for its IT team to concentrate on other
functions such as planning. Also, it has a tax advantage since the expenses of outsourcing are
deducted from that period’s earning. It also increases the cash flow from thetransfer of software
passes and staff to the service provider. This means that the institution is not liable to that group
and the expenses they incur. These expenses become the organization’s gains. Increase in cash
flow may also stem from the lease of the equipment that is no longer in use.
IT functions that Aztek is considering outsourcing include application development and
management, desktop management, data or managed security roles and network
development.This IT functionality can expose the organization in extreme cases of IT risks such
as cyberterrorism, cybercrimes, computer fraud and cyber espionage if the outsourcer is a greedy
untrustworthy individual (Wang et al, 2015).
These risks are however avoidable if the organization carries out its outsourcing activities
diligently and cautiously by ensuring that the agreement is in written form and signed by the
outsourcer. Based on the various advantages of outsourcing IT functionality and the results of the
risk assessment, it would be prudent for Aztek to take up the decision to outsource key IT roles
(Clark, G. L., & Monk, A. H., 2013).
2
EXECUTIVE SUMMARY
Key Information Technology (IT) functionality comprises a set of the major tasks performed by
the latter in the organization. These functions include planning, communication, application and
network development and technology support (Galliers et al, 2014). Outsourcing is the act of
procuring these IT functionalities from an outside vendor especially if the organization’s IT team
can carry them out. Aztek is a financial institution that is responsible for accepting deposits from
the general public and issuing out loans. It has a strong IT team that carries out all the roles of IT.
Lately, however, Aztek’s management has been considering outsourcing IT services to give the
IT team enough time to concentrate on other more demanding issues. This has been as a result of
the organization’s fast growth.
Outsourcing IT functionality is a very beneficial step to Aztek as it leads to risk sharing between
the institution and the outsourcer. It is also a cost-effective way for the organizationto have a
functioning computer system and allow sufficient time for its IT team to concentrate on other
functions such as planning. Also, it has a tax advantage since the expenses of outsourcing are
deducted from that period’s earning. It also increases the cash flow from thetransfer of software
passes and staff to the service provider. This means that the institution is not liable to that group
and the expenses they incur. These expenses become the organization’s gains. Increase in cash
flow may also stem from the lease of the equipment that is no longer in use.
IT functions that Aztek is considering outsourcing include application development and
management, desktop management, data or managed security roles and network
development.This IT functionality can expose the organization in extreme cases of IT risks such
as cyberterrorism, cybercrimes, computer fraud and cyber espionage if the outsourcer is a greedy
untrustworthy individual (Wang et al, 2015).
These risks are however avoidable if the organization carries out its outsourcing activities
diligently and cautiously by ensuring that the agreement is in written form and signed by the
outsourcer. Based on the various advantages of outsourcing IT functionality and the results of the
risk assessment, it would be prudent for Aztek to take up the decision to outsource key IT roles
(Clark, G. L., & Monk, A. H., 2013).
2

The main goal of Aztek at the moment is expansion, growth and development and outsourcing
some resources to focus on this objective will be worthwhile in the long run.The institution
should conduct regular inspection of the outsourcing process to avoid any misconduct from the
outsourcer and to tackle any problems that may arise without delay.Additionally, after
outsourcing the organization should take measures to ensure that the outsourcer did not tamper
with its crucial information or delete it. It should carry out a thorough analysis of the computer
system and networks to clarify that the components are in order and the system is still
functioning the right way (Lacity et al, 2017).
Aztek should take serious data security measures to avoid any leakage of information to the
public and competitors. The financial sector is a very competitive industry and a single wrong
move can set the institution off its game. Employees should be alert and cautious all the time to
avoid forgetting their devices in communal places. The organization can use encryptions, digital
signatures as well as biometric identifiers in securing their data, especially that which is exposed
to the public could pose serious risks to the institution.
Table of Contents
3
some resources to focus on this objective will be worthwhile in the long run.The institution
should conduct regular inspection of the outsourcing process to avoid any misconduct from the
outsourcer and to tackle any problems that may arise without delay.Additionally, after
outsourcing the organization should take measures to ensure that the outsourcer did not tamper
with its crucial information or delete it. It should carry out a thorough analysis of the computer
system and networks to clarify that the components are in order and the system is still
functioning the right way (Lacity et al, 2017).
Aztek should take serious data security measures to avoid any leakage of information to the
public and competitors. The financial sector is a very competitive industry and a single wrong
move can set the institution off its game. Employees should be alert and cautious all the time to
avoid forgetting their devices in communal places. The organization can use encryptions, digital
signatures as well as biometric identifiers in securing their data, especially that which is exposed
to the public could pose serious risks to the institution.
Table of Contents
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION.......................................................................................................................................5
Main functions of IT................................................................................................................................5
OUTSOURCING IT SERVICES................................................................................................................6
Introduction.............................................................................................................................................6
Outsourcing Regulations.........................................................................................................................7
Reasons for outsourcing..........................................................................................................................7
IMPACTS OF OUTSOURCING ON AZTEK’S SECURITY....................................................................8
CYBER RISKS.......................................................................................................................................8
Cybercrimes.........................................................................................................................................9
Cyber Espionage or Cyber Spying.......................................................................................................9
Computer Fraud...................................................................................................................................9
Financial Crimes................................................................................................................................10
Cyberterrorism...................................................................................................................................10
Cyberextortion...................................................................................................................................10
Cyber Risks Mitigation......................................................................................................................11
Counterparty Risks................................................................................................................................11
Exit Strategy Risk..................................................................................................................................11
Country Risks........................................................................................................................................12
Contractual Risk....................................................................................................................................12
Access Risk...........................................................................................................................................12
Lack of Ownership................................................................................................................................12
DATA SECURITY...................................................................................................................................12
Data classification.................................................................................................................................12
RISKS TO DATA.................................................................................................................................13
Theft..................................................................................................................................................13
Data loss or Accidental loss...............................................................................................................14
Imperfect or Improper data deletion..................................................................................................14
EFFECTIVE DATA RISK MANAGEMENT.......................................................................................14
Encryption.........................................................................................................................................14
Authorization.....................................................................................................................................14
Use of Digital Signature....................................................................................................................15
Biometrics.........................................................................................................................................15
CONCLUSION.........................................................................................................................................15
4
Main functions of IT................................................................................................................................5
OUTSOURCING IT SERVICES................................................................................................................6
Introduction.............................................................................................................................................6
Outsourcing Regulations.........................................................................................................................7
Reasons for outsourcing..........................................................................................................................7
IMPACTS OF OUTSOURCING ON AZTEK’S SECURITY....................................................................8
CYBER RISKS.......................................................................................................................................8
Cybercrimes.........................................................................................................................................9
Cyber Espionage or Cyber Spying.......................................................................................................9
Computer Fraud...................................................................................................................................9
Financial Crimes................................................................................................................................10
Cyberterrorism...................................................................................................................................10
Cyberextortion...................................................................................................................................10
Cyber Risks Mitigation......................................................................................................................11
Counterparty Risks................................................................................................................................11
Exit Strategy Risk..................................................................................................................................11
Country Risks........................................................................................................................................12
Contractual Risk....................................................................................................................................12
Access Risk...........................................................................................................................................12
Lack of Ownership................................................................................................................................12
DATA SECURITY...................................................................................................................................12
Data classification.................................................................................................................................12
RISKS TO DATA.................................................................................................................................13
Theft..................................................................................................................................................13
Data loss or Accidental loss...............................................................................................................14
Imperfect or Improper data deletion..................................................................................................14
EFFECTIVE DATA RISK MANAGEMENT.......................................................................................14
Encryption.........................................................................................................................................14
Authorization.....................................................................................................................................14
Use of Digital Signature....................................................................................................................15
Biometrics.........................................................................................................................................15
CONCLUSION.........................................................................................................................................15
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Main functions of IT
IT is an essential component of success in the financial sector. Financial institutions all over the
world are trying to come up with new and improved ways of making their services more
desirable and efficiently available to their customers. Their efforts have led to theavailability of
internet services in the banking sector such as telebanking, internet banking, self-inquiry
facilities and anywhere banking-everywhere banking (ATMs). Aztek company has not been left
behind in these developments. The organization has incorporated IT in most of its operations
with the aim of achieving a competitive advantage (Terlizzi et al, 2017). The major IT functions in
Aztek include planning, communication, technology support, network development and data
management and security.
Planning is mostly encompassed by Enterprise Resource Planning (ERP), which is a cross-
functional technologicalapproach that takes care of all the roles undertaken in an organization.
Aztek’s IT team works with the executive management to come up with an IT strategy that
supports all the organizational departments as well as its objectives. The team is also responsible
for ensuring that there are enough IT resources in the organization (Peppard, J., & Ward, J., 2016).
IT enables efficient and instant communication within and without the organization hence
increasing collaboration among the employees and between the management and the workers.
This enhances the efficiency and effectiveness of the work done.
Technology support is provided by the IT team whereby they attach manuals for user support on
every part of a new or improved technology to enable all employees to make effective use of the
new resource. This service is also extended by theprovision of ongoing support to users through
a helpdesk in the organization’s intranet.
It is essential for Aztek’s IT team to provide Data Management and Security measures. They
should protect the company’s data from viruses and cyber-attacks such as hacking which could
result to altering or destroying of crucial information permanently. Critical information should
also be encrypted to avoid leaks. Data management is achieved via the use of databases that
store, manage and control access to the organization’s data (Chi et al, 2017).
5
Main functions of IT
IT is an essential component of success in the financial sector. Financial institutions all over the
world are trying to come up with new and improved ways of making their services more
desirable and efficiently available to their customers. Their efforts have led to theavailability of
internet services in the banking sector such as telebanking, internet banking, self-inquiry
facilities and anywhere banking-everywhere banking (ATMs). Aztek company has not been left
behind in these developments. The organization has incorporated IT in most of its operations
with the aim of achieving a competitive advantage (Terlizzi et al, 2017). The major IT functions in
Aztek include planning, communication, technology support, network development and data
management and security.
Planning is mostly encompassed by Enterprise Resource Planning (ERP), which is a cross-
functional technologicalapproach that takes care of all the roles undertaken in an organization.
Aztek’s IT team works with the executive management to come up with an IT strategy that
supports all the organizational departments as well as its objectives. The team is also responsible
for ensuring that there are enough IT resources in the organization (Peppard, J., & Ward, J., 2016).
IT enables efficient and instant communication within and without the organization hence
increasing collaboration among the employees and between the management and the workers.
This enhances the efficiency and effectiveness of the work done.
Technology support is provided by the IT team whereby they attach manuals for user support on
every part of a new or improved technology to enable all employees to make effective use of the
new resource. This service is also extended by theprovision of ongoing support to users through
a helpdesk in the organization’s intranet.
It is essential for Aztek’s IT team to provide Data Management and Security measures. They
should protect the company’s data from viruses and cyber-attacks such as hacking which could
result to altering or destroying of crucial information permanently. Critical information should
also be encrypted to avoid leaks. Data management is achieved via the use of databases that
store, manage and control access to the organization’s data (Chi et al, 2017).
5

Network Development entails coming up with a new network that supports communication and
teamwork within the organization as well as enabling the outside stakeholders such as customers
to have easy access to its services. For example, Aztek’s IT team deploy Internet Protocol (IP)
networks that can carry data, voice and video messages in a single network.
OUTSOURCING IT SERVICES
Introduction
There has been an increase in the rate at which financial service providers all over the world
have been obtaining IT services from outside sources even when their IT team can undertake the
obligation (Verwaal, E., 2017).Surveys carried out in the Financial industry in the past have shown
that financial institutions outsource substantial portions of their regulated and even unregulated
functions, sometimes across a country’s boundaries (offshore outsourcing).Some organizations
move their operations to other countries or have foreign subsidiaries in a foreign country carry
out their functions for them (offshoring).
The IT services that Aztek is considering to outsource are; desktop management, application
development and maintenance, Managed Security Services(MSS)and network development.
Application development and maintenance: this includes coding which should follow a laborious
Software Development Life Cycle (SDLC) created as part of the service provider’s standard
quality process. The suppliers should therefore strictly follow the specifications given to them by
their clients. The organization’s management should monitor the procedures to compare the
actual performance with the expected levels of service provider parameters.
Desktop management: this entails physical hosting of servers and other IT assets, continuous
monitoring and capacity management of the latter,server builds and application software
installation and upgrading, backup and restoration and recovery of server systems in case of a
tragedy. Local Area Network (LAN) establishment and maintenance is also includedinthis
category.
Managed Security: this takes care of the safety of the entire IT infrastructure and all data assets
in the organization.
6
teamwork within the organization as well as enabling the outside stakeholders such as customers
to have easy access to its services. For example, Aztek’s IT team deploy Internet Protocol (IP)
networks that can carry data, voice and video messages in a single network.
OUTSOURCING IT SERVICES
Introduction
There has been an increase in the rate at which financial service providers all over the world
have been obtaining IT services from outside sources even when their IT team can undertake the
obligation (Verwaal, E., 2017).Surveys carried out in the Financial industry in the past have shown
that financial institutions outsource substantial portions of their regulated and even unregulated
functions, sometimes across a country’s boundaries (offshore outsourcing).Some organizations
move their operations to other countries or have foreign subsidiaries in a foreign country carry
out their functions for them (offshoring).
The IT services that Aztek is considering to outsource are; desktop management, application
development and maintenance, Managed Security Services(MSS)and network development.
Application development and maintenance: this includes coding which should follow a laborious
Software Development Life Cycle (SDLC) created as part of the service provider’s standard
quality process. The suppliers should therefore strictly follow the specifications given to them by
their clients. The organization’s management should monitor the procedures to compare the
actual performance with the expected levels of service provider parameters.
Desktop management: this entails physical hosting of servers and other IT assets, continuous
monitoring and capacity management of the latter,server builds and application software
installation and upgrading, backup and restoration and recovery of server systems in case of a
tragedy. Local Area Network (LAN) establishment and maintenance is also includedinthis
category.
Managed Security: this takes care of the safety of the entire IT infrastructure and all data assets
in the organization.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Outsourcing Regulations
Regulation of outsourcing is majorly important for theprotection of consumer interests. It also
protects stakeholders such as shareholders and policy-holders. Outsourcing is also regulated to
protect the rights of the suppliers. Such regulations include:
o Outsourcing agreement should be signed with the service provider
o The outsourcer should be named in the contract
o As a regulated entity, Aztek should have in place a comprehensive policy to guide on
whether and how the IT functionality can be appropriately outsourced. The management
should retain responsibility for the outsourcing policy and all other activities carried out
under this policy
o It should also ensure that the outsourcing activity does not diminish its ability to serve
customers or impede operativeregulation
o The entity should exercise due diligence in picking third-party service providers.
o Written documents that clearly describe all the important features of the outsourcing
arrangement should dictate the latter
o Backup facilities should be provided for by both the outsourcers and the institution to
take care of any disaster that may arise
o The organizationshould take appropriate steps requiring that the vendors protect its
confidential information and that of its clients
o Aztek should take into account outsourcing activities as an integral partof their ongoing
assessment of the regulated entity.
Reasons for outsourcing
An organization’s decision to outsource depends on various on a combination of logistical,
organizational and financial considerations. In Aztek’s case, the principal reason for outsourcing
would be, cost reduction. This stems from the fact that long-term outsourcing contracts convert
the variable costs involved in fixed costs thus making IT usage in the organization more
predictable. Cost reduction is achieved by Return on Investment (ROI) by the project over a long
period of time. This method is used because Aztek is planning on outsourcing the resources for a
while to enhance its growth and expansion.
ROI= (total benefits- total costs)/ total costs
7
Regulation of outsourcing is majorly important for theprotection of consumer interests. It also
protects stakeholders such as shareholders and policy-holders. Outsourcing is also regulated to
protect the rights of the suppliers. Such regulations include:
o Outsourcing agreement should be signed with the service provider
o The outsourcer should be named in the contract
o As a regulated entity, Aztek should have in place a comprehensive policy to guide on
whether and how the IT functionality can be appropriately outsourced. The management
should retain responsibility for the outsourcing policy and all other activities carried out
under this policy
o It should also ensure that the outsourcing activity does not diminish its ability to serve
customers or impede operativeregulation
o The entity should exercise due diligence in picking third-party service providers.
o Written documents that clearly describe all the important features of the outsourcing
arrangement should dictate the latter
o Backup facilities should be provided for by both the outsourcers and the institution to
take care of any disaster that may arise
o The organizationshould take appropriate steps requiring that the vendors protect its
confidential information and that of its clients
o Aztek should take into account outsourcing activities as an integral partof their ongoing
assessment of the regulated entity.
Reasons for outsourcing
An organization’s decision to outsource depends on various on a combination of logistical,
organizational and financial considerations. In Aztek’s case, the principal reason for outsourcing
would be, cost reduction. This stems from the fact that long-term outsourcing contracts convert
the variable costs involved in fixed costs thus making IT usage in the organization more
predictable. Cost reduction is achieved by Return on Investment (ROI) by the project over a long
period of time. This method is used because Aztek is planning on outsourcing the resources for a
while to enhance its growth and expansion.
ROI= (total benefits- total costs)/ total costs
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
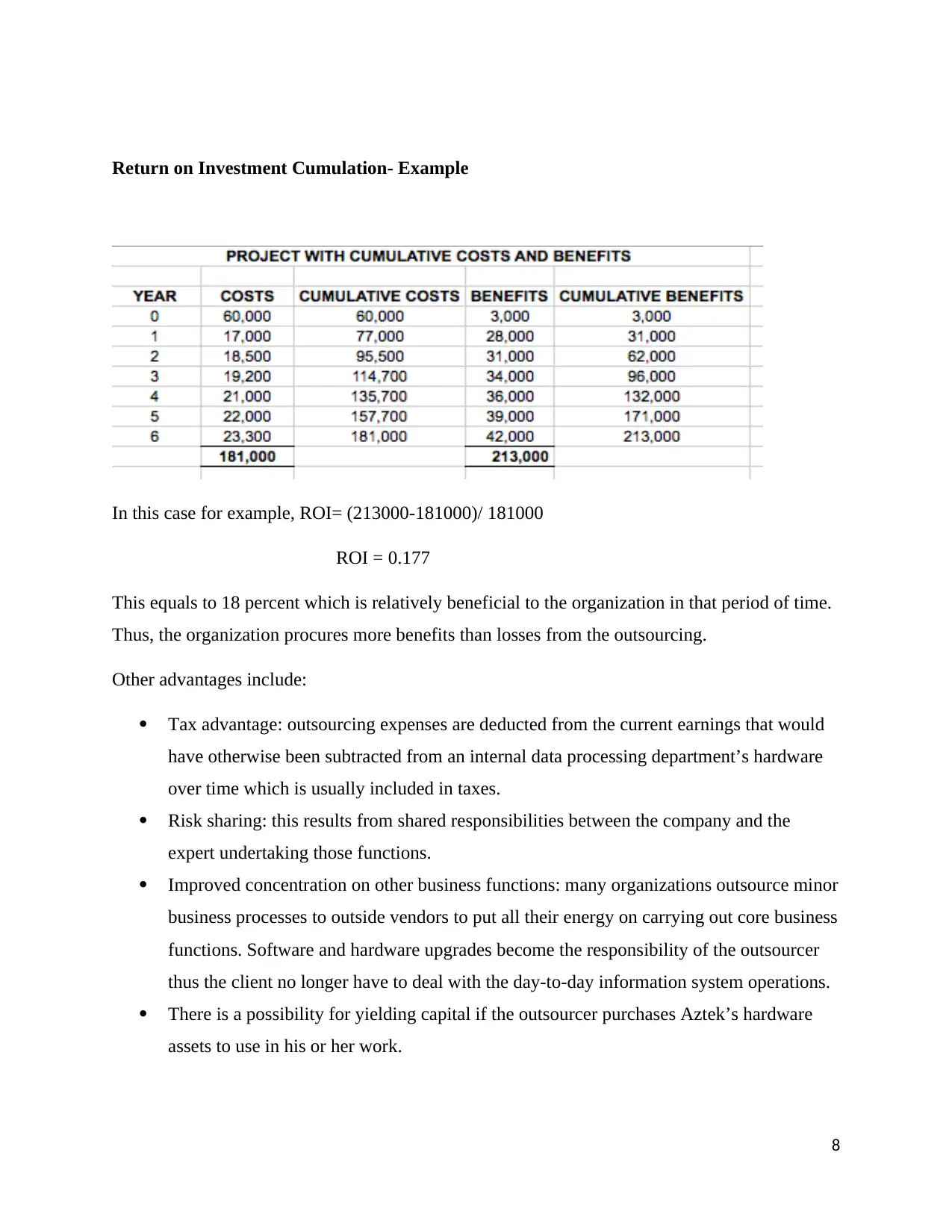
Return on Investment Cumulation- Example
In this case for example, ROI= (213000-181000)/ 181000
ROI = 0.177
This equals to 18 percent which is relatively beneficial to the organization in that period of time.
Thus, the organization procures more benefits than losses from the outsourcing.
Other advantages include:
Tax advantage: outsourcing expenses are deducted from the current earnings that would
have otherwise been subtracted from an internal data processing department’s hardware
over time which is usually included in taxes.
Risk sharing: this results from shared responsibilities between the company and the
expert undertaking those functions.
Improved concentration on other business functions: many organizations outsource minor
business processes to outside vendors to put all their energy on carrying out core business
functions. Software and hardware upgrades become the responsibility of the outsourcer
thus the client no longer have to deal with the day-to-day information system operations.
There is a possibility for yielding capital if the outsourcer purchases Aztek’s hardware
assets to use in his or her work.
8
In this case for example, ROI= (213000-181000)/ 181000
ROI = 0.177
This equals to 18 percent which is relatively beneficial to the organization in that period of time.
Thus, the organization procures more benefits than losses from the outsourcing.
Other advantages include:
Tax advantage: outsourcing expenses are deducted from the current earnings that would
have otherwise been subtracted from an internal data processing department’s hardware
over time which is usually included in taxes.
Risk sharing: this results from shared responsibilities between the company and the
expert undertaking those functions.
Improved concentration on other business functions: many organizations outsource minor
business processes to outside vendors to put all their energy on carrying out core business
functions. Software and hardware upgrades become the responsibility of the outsourcer
thus the client no longer have to deal with the day-to-day information system operations.
There is a possibility for yielding capital if the outsourcer purchases Aztek’s hardware
assets to use in his or her work.
8

Cash flow improvements: this results from the transfer of software licenses andpersonnel
to the supplier. This also includes maintenance costs for the data center and release of the
organization from the obligation of a previously leased a plant or equipment.
Expertise: organizations also outsource to ensure that those functions are performed
excellently especially in cases where there are no experts in that area within the
organization.Their facilities are equipped with excessively designed systems to avert
power and cooling failures and to detect leakage of water, smoke or extreme heat and
anything else that would adversely affect system action. The vendors’ operation
procedures might include advanced system and communication monitoring tools that are
designed to ensure uninterrupted processing and network availability.
IMPACTS OF OUTSOURCING ON AZTEK’S SECURITY
Aztek’s infrastructural and data security measures do a very good job in ensuring the
organization’s data safety and smooth running of the computer system. The IT team has however
been quite occupied lately with trying to fulfill major requirements of the organization such as
planning. The current security system has therefore been running for a while and needs an
update. Due to the insufficient time by Aztek’s IT team, it is more efficient to outsource these
security services. Unfortunately, there are various risks associated with this process, both to the
organization as a whole and to the stakeholders (Riggins, F., & Weber, D., 2016).
CYBERRISKS
Cyber risks describe the possibility of loss, disruptionin daily business operation, or damage to
an organization’s reputation caused by dysfunction in its Information Communication
Technology (ICT), computer networks and systems.
Cyberattacksrefer to any offensive action undertaken by nations, organizations, groups of people
or individuals targeting computer information systems, networks or other infrastructure (Page et
al, 2017). They include cybercrimes and cyber espionage.
Cybercrimes
This is any crime involving a computer or a network whereby the latter may have been used in
committing the misconduct or where it is the target. These offenses are committed with a
criminal motive of intentionally ruining the reputation of the individual or the organization or
causing physical or psychological harm or costing the victim otherwise. Cybercrime therefore
9
to the supplier. This also includes maintenance costs for the data center and release of the
organization from the obligation of a previously leased a plant or equipment.
Expertise: organizations also outsource to ensure that those functions are performed
excellently especially in cases where there are no experts in that area within the
organization.Their facilities are equipped with excessively designed systems to avert
power and cooling failures and to detect leakage of water, smoke or extreme heat and
anything else that would adversely affect system action. The vendors’ operation
procedures might include advanced system and communication monitoring tools that are
designed to ensure uninterrupted processing and network availability.
IMPACTS OF OUTSOURCING ON AZTEK’S SECURITY
Aztek’s infrastructural and data security measures do a very good job in ensuring the
organization’s data safety and smooth running of the computer system. The IT team has however
been quite occupied lately with trying to fulfill major requirements of the organization such as
planning. The current security system has therefore been running for a while and needs an
update. Due to the insufficient time by Aztek’s IT team, it is more efficient to outsource these
security services. Unfortunately, there are various risks associated with this process, both to the
organization as a whole and to the stakeholders (Riggins, F., & Weber, D., 2016).
CYBERRISKS
Cyber risks describe the possibility of loss, disruptionin daily business operation, or damage to
an organization’s reputation caused by dysfunction in its Information Communication
Technology (ICT), computer networks and systems.
Cyberattacksrefer to any offensive action undertaken by nations, organizations, groups of people
or individuals targeting computer information systems, networks or other infrastructure (Page et
al, 2017). They include cybercrimes and cyber espionage.
Cybercrimes
This is any crime involving a computer or a network whereby the latter may have been used in
committing the misconduct or where it is the target. These offenses are committed with a
criminal motive of intentionally ruining the reputation of the individual or the organization or
causing physical or psychological harm or costing the victim otherwise. Cybercrime therefore
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

may threaten an individual’s or organization’s security and financial position (Johnson, A. L.,
2016).
Cyber Espionage or Cyber Spying
It refers to the use of computer networks to gain unauthorized access to an organization’s
confidential information (Bang et al, 2017). Acquiring those services from outside the
organization would expose its important data to the third party. Activities such as desktop
management, application and network development enable the developer to come into contact
with their client’s crucial data. The vendors could use that information against Aztek later on in
case of an argument or a misunderstanding or for their selfish gains. In other words, the
outsourcer may not be an individual of great character and may use that opportunity to get into
the organization’s system, get confidential information and probably share it with the company’s
competitors.
Additionally, this information can be obtained by use of malicious software, hacking or proxy
servers to hinder Aztek from ever trying the leak to their outsourcers. They may also have the
motive to continue control over the organization’s computer system even long after their contract
has been depleted, for strategic advantages or sabotaging reasons.
Computer Fraud
Computer fraud refers to an act of misinterpreting data to make an organization or individual do
or refrain from doing something that will eventually lead to losses (Cumming et al, 2017).
Procuring IT personnel from outside the organization would make Aztek vulnerable to computer
fraud since the outsourcer may alter the data in the company’s system and consequently mislead
all the other operators.This can be achieved through, changingof deleting stored data, altering
data before entry, entering false data, destroying, stealing or altering theoutput. Thisis easily
achievable by the individuals at the desktop management and is usually hard to detect.
Financial Crimes
Bank fraud
This refers to the use of illegal means to obtain money, property or other assets held or owned by
a financial institution or the act of fraudulently posing as a bank in order to receive currency
from depositors. Not directly affiliated to Aztek, it is possible for the outsourcers to acquire these
10
2016).
Cyber Espionage or Cyber Spying
It refers to the use of computer networks to gain unauthorized access to an organization’s
confidential information (Bang et al, 2017). Acquiring those services from outside the
organization would expose its important data to the third party. Activities such as desktop
management, application and network development enable the developer to come into contact
with their client’s crucial data. The vendors could use that information against Aztek later on in
case of an argument or a misunderstanding or for their selfish gains. In other words, the
outsourcer may not be an individual of great character and may use that opportunity to get into
the organization’s system, get confidential information and probably share it with the company’s
competitors.
Additionally, this information can be obtained by use of malicious software, hacking or proxy
servers to hinder Aztek from ever trying the leak to their outsourcers. They may also have the
motive to continue control over the organization’s computer system even long after their contract
has been depleted, for strategic advantages or sabotaging reasons.
Computer Fraud
Computer fraud refers to an act of misinterpreting data to make an organization or individual do
or refrain from doing something that will eventually lead to losses (Cumming et al, 2017).
Procuring IT personnel from outside the organization would make Aztek vulnerable to computer
fraud since the outsourcer may alter the data in the company’s system and consequently mislead
all the other operators.This can be achieved through, changingof deleting stored data, altering
data before entry, entering false data, destroying, stealing or altering theoutput. Thisis easily
achievable by the individuals at the desktop management and is usually hard to detect.
Financial Crimes
Bank fraud
This refers to the use of illegal means to obtain money, property or other assets held or owned by
a financial institution or the act of fraudulently posing as a bank in order to receive currency
from depositors. Not directly affiliated to Aztek, it is possible for the outsourcers to acquire these
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

resources for their benefit or someone else’s. (Kshetri, N., & Voas, J., 2017).There are various types
of bank fraud such as stolen cheques and payment cards, forgery in checks and documents,
fraudulent wire transfer, bill discounting, skimming or duplication of card information,
impersonation or identity theft and money laundering. All these actions can be easily carried out
via the internet of by a group of people working together. A fraudulent outsourcer who apart
from knowing his or her way around the bank, its operations and its worth also has computer
intellect will find it incredibly simple to obtain these resources with limited help or even with no
help at all.
Cyberterrorism
A cyber terrorist is someone who threatens or coerces an organization to advance their wishes by
launching a computer-related attack against their systems,networks or information contained in
them. The outsourcer may take the opportunity of working for Aztek to advance his or her
objectives. For example, he or she may create a virus that would attack Aztek’s computer
systems long after the work is done and make demands to the organizationwith the aim of
achieving his or her goals.
Cyberextortion
Outsourcing of key IT functionality exposes Aztek to malicious hackers who subjects their
computer system to repeated denial of service or other attacks. These hackers may be affiliated
with the outsourcers and end up asking for money or other resources in return for ending the
attacks.
Cyber Risks Mitigation
Aztek should take proper steps to ensure that connected devices around the institution are well
connected to have a chance at beating the cyber criminals at their own game. These steps include
regular change of pass codes, creation of complex passwords and disabling unnecessary remote
connections and features. The organization’s technology team should have a thorough
understanding of the continuously evolving cyber risks and the knowledge on how to mitigate
them. This is, however, not a problem just for the IT team but for the organization as a whole.
The institution’s management should ensure that it has enough resources to take care of the
11
of bank fraud such as stolen cheques and payment cards, forgery in checks and documents,
fraudulent wire transfer, bill discounting, skimming or duplication of card information,
impersonation or identity theft and money laundering. All these actions can be easily carried out
via the internet of by a group of people working together. A fraudulent outsourcer who apart
from knowing his or her way around the bank, its operations and its worth also has computer
intellect will find it incredibly simple to obtain these resources with limited help or even with no
help at all.
Cyberterrorism
A cyber terrorist is someone who threatens or coerces an organization to advance their wishes by
launching a computer-related attack against their systems,networks or information contained in
them. The outsourcer may take the opportunity of working for Aztek to advance his or her
objectives. For example, he or she may create a virus that would attack Aztek’s computer
systems long after the work is done and make demands to the organizationwith the aim of
achieving his or her goals.
Cyberextortion
Outsourcing of key IT functionality exposes Aztek to malicious hackers who subjects their
computer system to repeated denial of service or other attacks. These hackers may be affiliated
with the outsourcers and end up asking for money or other resources in return for ending the
attacks.
Cyber Risks Mitigation
Aztek should take proper steps to ensure that connected devices around the institution are well
connected to have a chance at beating the cyber criminals at their own game. These steps include
regular change of pass codes, creation of complex passwords and disabling unnecessary remote
connections and features. The organization’s technology team should have a thorough
understanding of the continuously evolving cyber risks and the knowledge on how to mitigate
them. This is, however, not a problem just for the IT team but for the organization as a whole.
The institution’s management should ensure that it has enough resources to take care of the
11

arising cyber-attacks. In addition, it should constantly educate its employees especially the IT
personnel on how to avoid the arousal of those risks or manage them where they are inevitable.
It is evident that outsourcing key IT functionality to the third party is a risky decision for an
organization to work. Those risks can however be managed to minimize them, especially since
most of them are brought to the company by untrustworthy vendors. An organization should
therefore make sure that the outsourcer they are about to work with is trustworthy. It should also
make their agreement legal by ensuring that it is a written document and signed by the supplier.
The organization should involve its lawyer in this process no matter how well the outsourcer is
known to them (Johnson, K. N., 2015).Categorically, the risks involved are:
Counterparty Risks
In the case where the supplier is not an expert there would arise inconsistencies in the workflow
such as untimely delivery, inappropriate categorization of responsibilities and low-quality output.
The supplier may also not have full focus on Aztek’s requirements which would lead to
incompletion of the task designated to him or her. Outsourcing key IT functionalities would also
be an expensive exercise due to the nature of those functions. This is important work to the
organization and the vendor may take advantage of that fact to make his or her services even
costlier.
Exit Strategy Risk
Over-reliance on one firm to work on Aztek’s IT department may put it in jeopardy whereby
appropriate exit strategiesare not put in place.This also -arises from theloss of the required
crucial skills within the organization preventing it from undertaking its own IT tasks.
Country Risks
If Aztek decides on offshore outsourcing, the other nation’s political, economic and legal climate
may create added risks. This would increase the complexity of the outsourcing process in
addition tothat of business continuity, growth and expansion.
Contractual Risk
This is the possibility of loss arising from failure in contract performance. This happens when
one or all the parties fail to honor the terms of their agreement.
12
personnel on how to avoid the arousal of those risks or manage them where they are inevitable.
It is evident that outsourcing key IT functionality to the third party is a risky decision for an
organization to work. Those risks can however be managed to minimize them, especially since
most of them are brought to the company by untrustworthy vendors. An organization should
therefore make sure that the outsourcer they are about to work with is trustworthy. It should also
make their agreement legal by ensuring that it is a written document and signed by the supplier.
The organization should involve its lawyer in this process no matter how well the outsourcer is
known to them (Johnson, K. N., 2015).Categorically, the risks involved are:
Counterparty Risks
In the case where the supplier is not an expert there would arise inconsistencies in the workflow
such as untimely delivery, inappropriate categorization of responsibilities and low-quality output.
The supplier may also not have full focus on Aztek’s requirements which would lead to
incompletion of the task designated to him or her. Outsourcing key IT functionalities would also
be an expensive exercise due to the nature of those functions. This is important work to the
organization and the vendor may take advantage of that fact to make his or her services even
costlier.
Exit Strategy Risk
Over-reliance on one firm to work on Aztek’s IT department may put it in jeopardy whereby
appropriate exit strategiesare not put in place.This also -arises from theloss of the required
crucial skills within the organization preventing it from undertaking its own IT tasks.
Country Risks
If Aztek decides on offshore outsourcing, the other nation’s political, economic and legal climate
may create added risks. This would increase the complexity of the outsourcing process in
addition tothat of business continuity, growth and expansion.
Contractual Risk
This is the possibility of loss arising from failure in contract performance. This happens when
one or all the parties fail to honor the terms of their agreement.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





