Detailed Report: Network Performance Analysis Using Wireshark & Netmon
VerifiedAdded on 2023/06/11
|12
|2465
|331
Report
AI Summary
This report provides a comprehensive analysis of network performance using packet sniffers, specifically Wireshark and Network Monitor. It begins with an introduction to packet analysis and its importance in identifying network bottlenecks and unusual behaviors. The report details general statistics obtained from packet captures, including the time of capture, total number of packets, and IP addresses of the client and server. Key network performance metrics such as throughput, round trip time (RTT), and TCP retransmissions are examined, with comparative analysis between Wireshark and Network Monitor. The report highlights the advantages of Wireshark, including its ease of use, GUI facilities, and statistical information, and discusses how both tools can be used for troubleshooting, security analysis, and network planning. Ultimately, it emphasizes the importance of network monitoring and proactive identification of network issues to ensure smooth operation and prevent serious problems.

Table of Contents
1. Introduction.................................................................................................................................2
2. General Statistics.........................................................................................................................2
3. Network Performance.................................................................................................................3
4. Comparision-1..............................................................................................................................6
5. Comparision-2..............................................................................................................................8
6. Conclusion..................................................................................................................................11
7. References..................................................................................................................................12
1
1. Introduction.................................................................................................................................2
2. General Statistics.........................................................................................................................2
3. Network Performance.................................................................................................................3
4. Comparision-1..............................................................................................................................6
5. Comparision-2..............................................................................................................................8
6. Conclusion..................................................................................................................................11
7. References..................................................................................................................................12
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
The data packets are captured by the pocket sniffers [1]. In the final destination the pocket sniffers
are not shown. The unusual behaviors are easily is identified by using pocket sniffers. Mostly the
unusual behaviors are present in the network. The pocket sniffers are mostly used identified the
bottle necks of the network. Using wire shark we can record the data packets. For example the web
site will be browsed in 10 minutes continuously, and then using wire shark for identifies the data
packets of the web site. The pocket key features are based on the analyses. The data capture is
successfully completed then we need to check the total no of available packets, and IP address of
client and also the server. Types of network parameters are used such as TCP transmission,
throughput, etc. The pocket sniffers are participated in ease of access, ease of use, properties of
statistics operations, GUI facilities, and traffic virtualization.
In today's environment, company intranets are growing fastly.so that network administrators should
know different technologies related to networks. Traffic monitoring and analysis plays an significant
role in network.because these technologies used to ensure effctive troubleshoot and correct
behavior of the network activities without any traffic issues. From the network administrator's
perspective,Network monitoring is difficult task that should be handle with care.network
administrators put more effort to ensure smooth operation of networks continiously,they need to
monitor traffic movement in great extent.small problem in networks will leads to serious problem.
For example,public service departments provide services to customers.if any problem occured in
that department,then its ability to provide necessary services to customers should be affected and
also its productivity goes down. So its administrators responsibility to ensure proper behavior of the
network.if any problem occur in network,they have to ensure the causes of the problem do not
propagate into networks.
2
The data packets are captured by the pocket sniffers [1]. In the final destination the pocket sniffers
are not shown. The unusual behaviors are easily is identified by using pocket sniffers. Mostly the
unusual behaviors are present in the network. The pocket sniffers are mostly used identified the
bottle necks of the network. Using wire shark we can record the data packets. For example the web
site will be browsed in 10 minutes continuously, and then using wire shark for identifies the data
packets of the web site. The pocket key features are based on the analyses. The data capture is
successfully completed then we need to check the total no of available packets, and IP address of
client and also the server. Types of network parameters are used such as TCP transmission,
throughput, etc. The pocket sniffers are participated in ease of access, ease of use, properties of
statistics operations, GUI facilities, and traffic virtualization.
In today's environment, company intranets are growing fastly.so that network administrators should
know different technologies related to networks. Traffic monitoring and analysis plays an significant
role in network.because these technologies used to ensure effctive troubleshoot and correct
behavior of the network activities without any traffic issues. From the network administrator's
perspective,Network monitoring is difficult task that should be handle with care.network
administrators put more effort to ensure smooth operation of networks continiously,they need to
monitor traffic movement in great extent.small problem in networks will leads to serious problem.
For example,public service departments provide services to customers.if any problem occured in
that department,then its ability to provide necessary services to customers should be affected and
also its productivity goes down. So its administrators responsibility to ensure proper behavior of the
network.if any problem occur in network,they have to ensure the causes of the problem do not
propagate into networks.
2

2. Packet Analyser
Packet analyser is an analysing tool used to analyse the content of the packets in the network.its
look like computer program.packet analyser otherwise called packet sniffer,ethernet sniffer,wireless
sniffer.several data packets are transferred over the network.the sniffer captures every packet and
analyse its content,and also showing values of various fields that should be used in that packet. Here
are some examples showing why these packet analysers are used for:
For identifying troubleshoot network problems, network administrators prefer this packet analyser.
Network security engineers also using this analyser to identify security problems.
It also used in debug protocol implementation. For learning network protocol internal, people also
prefering this analyser.
Two network packet analyser softwares used here:
1. Wireshark
Wireshark[2] is well known packet analyser.it is also open source.
2.Network Monitor
Features of wireshark
Available for unix and windows operating systems.
It is used in capturing data packets in network interface.
It uses several capturing programs like windump to capture data in open files.
Used to import packets from text files.the text files may contain hex dumps of packet data.
It displays packets with protocal information in detail.
Captured data is saved.
It uses several file formats to export all packets.
Used to filtering packets based on some criteria.
Searching required packets based on given criteria.
Colorize packet display based on filters.
3. General Statistics
Time of Capture
3
Packet analyser is an analysing tool used to analyse the content of the packets in the network.its
look like computer program.packet analyser otherwise called packet sniffer,ethernet sniffer,wireless
sniffer.several data packets are transferred over the network.the sniffer captures every packet and
analyse its content,and also showing values of various fields that should be used in that packet. Here
are some examples showing why these packet analysers are used for:
For identifying troubleshoot network problems, network administrators prefer this packet analyser.
Network security engineers also using this analyser to identify security problems.
It also used in debug protocol implementation. For learning network protocol internal, people also
prefering this analyser.
Two network packet analyser softwares used here:
1. Wireshark
Wireshark[2] is well known packet analyser.it is also open source.
2.Network Monitor
Features of wireshark
Available for unix and windows operating systems.
It is used in capturing data packets in network interface.
It uses several capturing programs like windump to capture data in open files.
Used to import packets from text files.the text files may contain hex dumps of packet data.
It displays packets with protocal information in detail.
Captured data is saved.
It uses several file formats to export all packets.
Used to filtering packets based on some criteria.
Searching required packets based on given criteria.
Colorize packet display based on filters.
3. General Statistics
Time of Capture
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
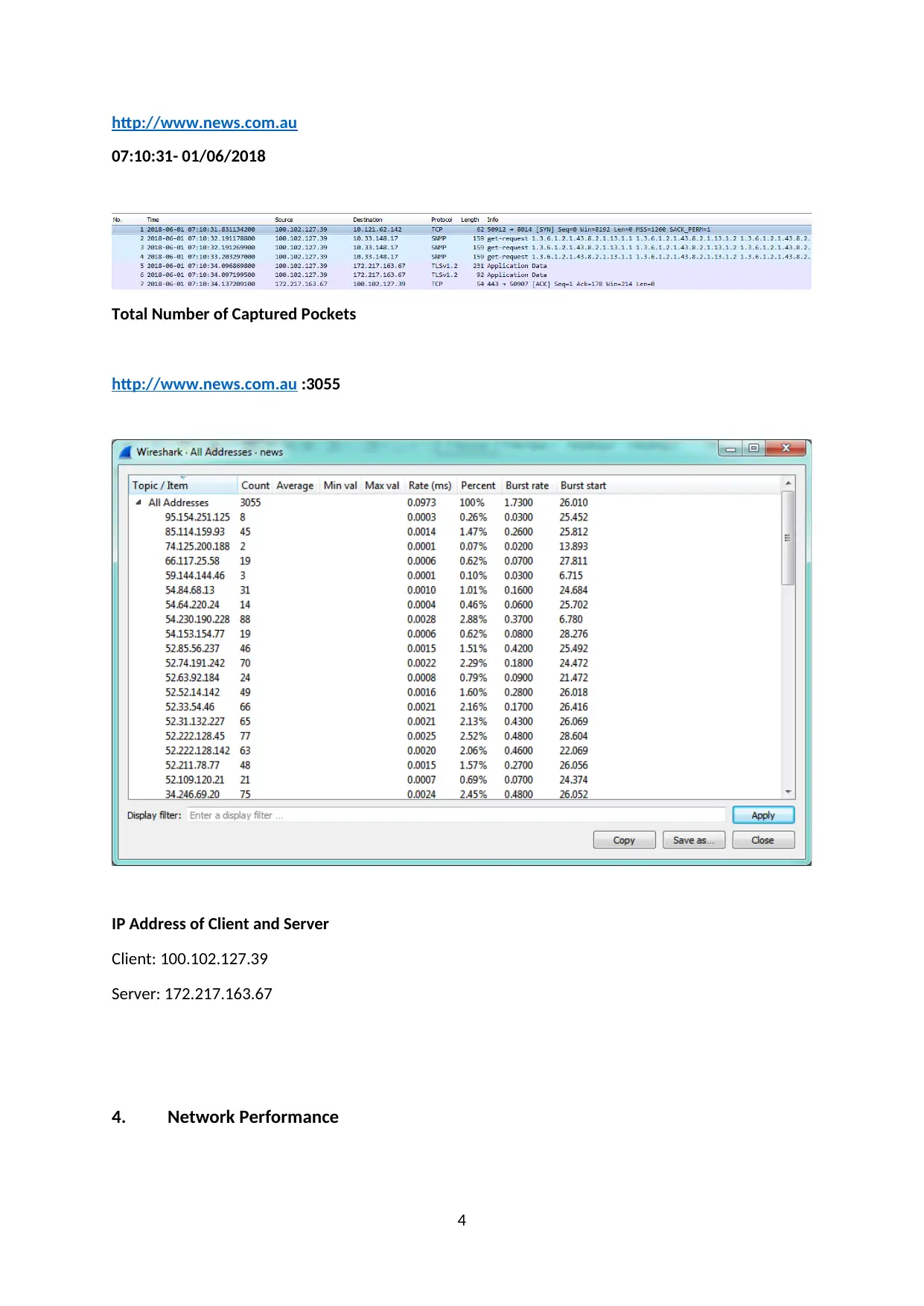
http://www.news.com.au
07:10:31- 01/06/2018
Total Number of Captured Pockets
http://www.news.com.au :3055
IP Address of Client and Server
Client: 100.102.127.39
Server: 172.217.163.67
4. Network Performance
4
07:10:31- 01/06/2018
Total Number of Captured Pockets
http://www.news.com.au :3055
IP Address of Client and Server
Client: 100.102.127.39
Server: 172.217.163.67
4. Network Performance
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Throughput
The average network throughput is measured in the scale of bits per second. And data packets per
second is also the another type of scale is used for measure the average throughput. The received
message have a high quality, it means the throughput is also high. Each bandwidth use different
types of throughput. Throughput is differing from every bandwidth. The internet pipe size is
indicated by the bandwidth. And also the capacity of the internet pipe, size of the internet pipe is
indicated by bandwidth. Throughput has an ability to note the practical value of data [3][4].
Round Trip Time
Using round trip time the travel time between the source and destination is calculated. The round trip
time is also known as round trip delay. Source is acts like a signal for initiate the computer. And the
server it acts like a target, the signal is received by server. Finally the signals are comes from the source
are gathered by the target [3][4].
TCP retransmissions
The packets are damaged or lose their quality in travelling time. So the computers cannot receive the
damaged packets, because the damaged packets lose their quantity. It informs the source computer,
send any other packet. Immediately the source computer send the another unaffected packets. This
process is known as ARQ. ARQ stands for automatic repeat request, used to perform retransmission
operation. No of acknowledgement is possible by the data transmission. The incorrect packets are
sending to the negative acknowledgement side [3][4].
Throughput
5
The average network throughput is measured in the scale of bits per second. And data packets per
second is also the another type of scale is used for measure the average throughput. The received
message have a high quality, it means the throughput is also high. Each bandwidth use different
types of throughput. Throughput is differing from every bandwidth. The internet pipe size is
indicated by the bandwidth. And also the capacity of the internet pipe, size of the internet pipe is
indicated by bandwidth. Throughput has an ability to note the practical value of data [3][4].
Round Trip Time
Using round trip time the travel time between the source and destination is calculated. The round trip
time is also known as round trip delay. Source is acts like a signal for initiate the computer. And the
server it acts like a target, the signal is received by server. Finally the signals are comes from the source
are gathered by the target [3][4].
TCP retransmissions
The packets are damaged or lose their quality in travelling time. So the computers cannot receive the
damaged packets, because the damaged packets lose their quantity. It informs the source computer,
send any other packet. Immediately the source computer send the another unaffected packets. This
process is known as ARQ. ARQ stands for automatic repeat request, used to perform retransmission
operation. No of acknowledgement is possible by the data transmission. The incorrect packets are
sending to the negative acknowledgement side [3][4].
Throughput
5
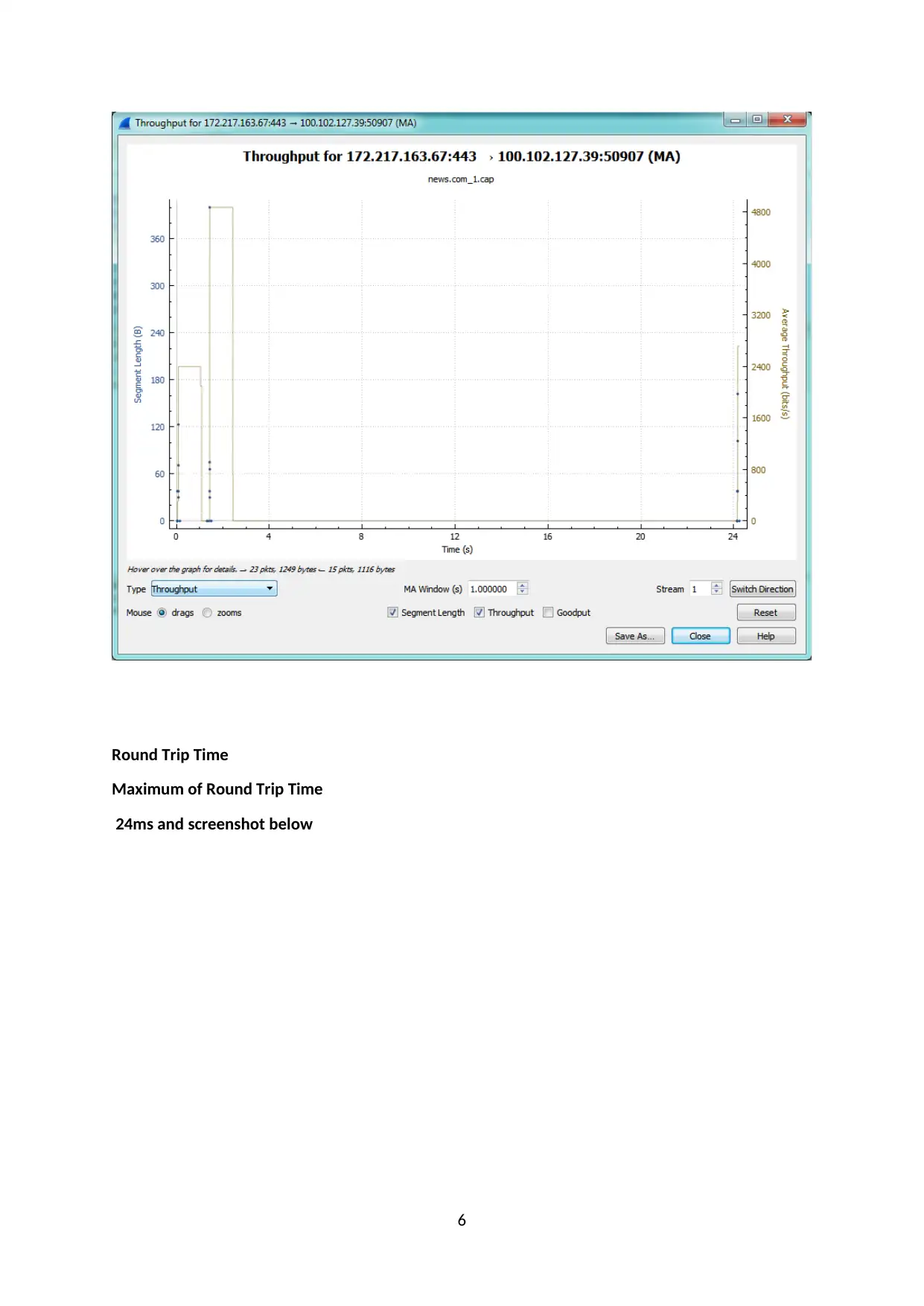
Round Trip Time
Maximum of Round Trip Time
24ms and screenshot below
6
Maximum of Round Trip Time
24ms and screenshot below
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
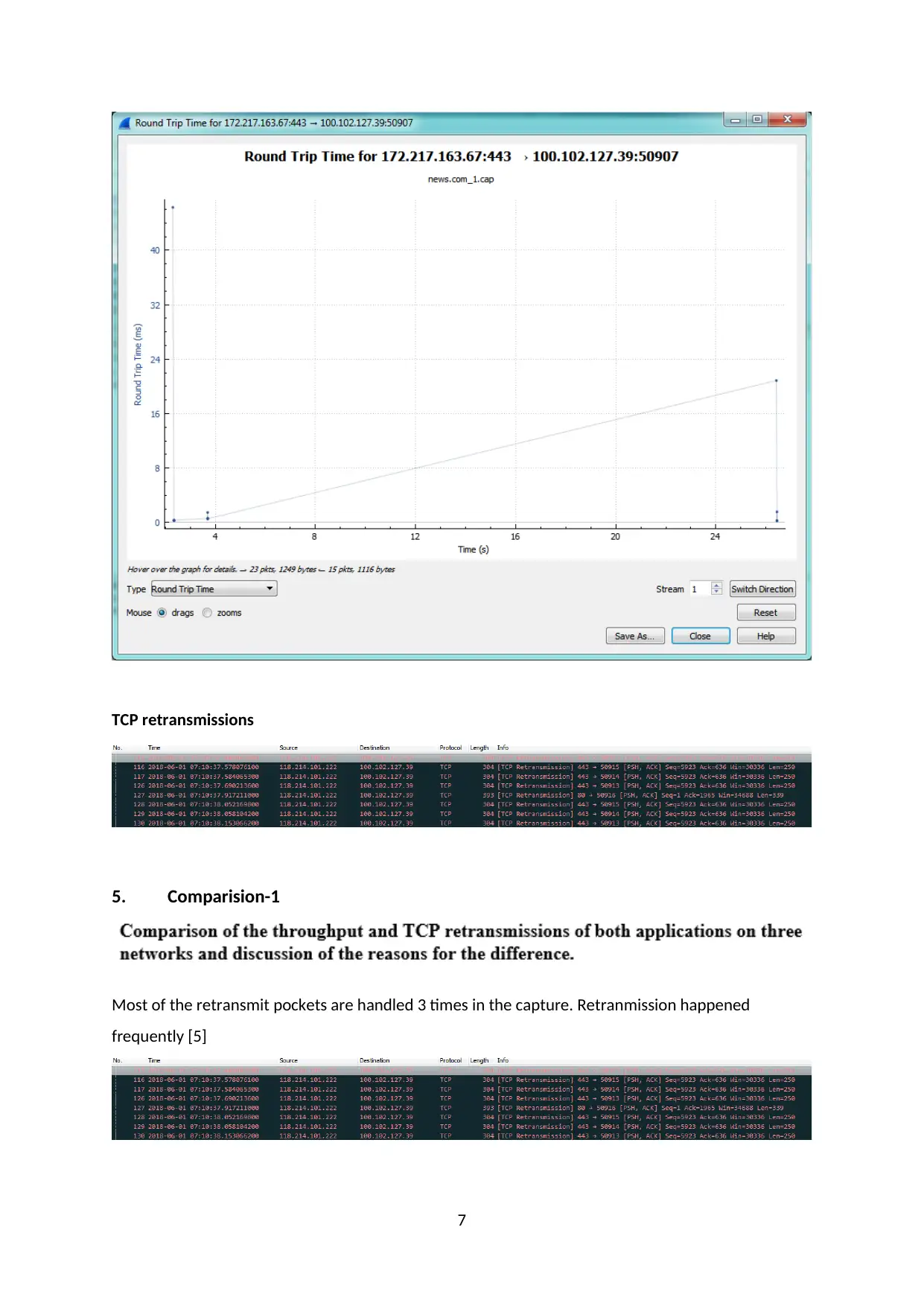
TCP retransmissions
5. Comparision-1
Most of the retransmit pockets are handled 3 times in the capture. Retranmission happened
frequently [5]
7
5. Comparision-1
Most of the retransmit pockets are handled 3 times in the capture. Retranmission happened
frequently [5]
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
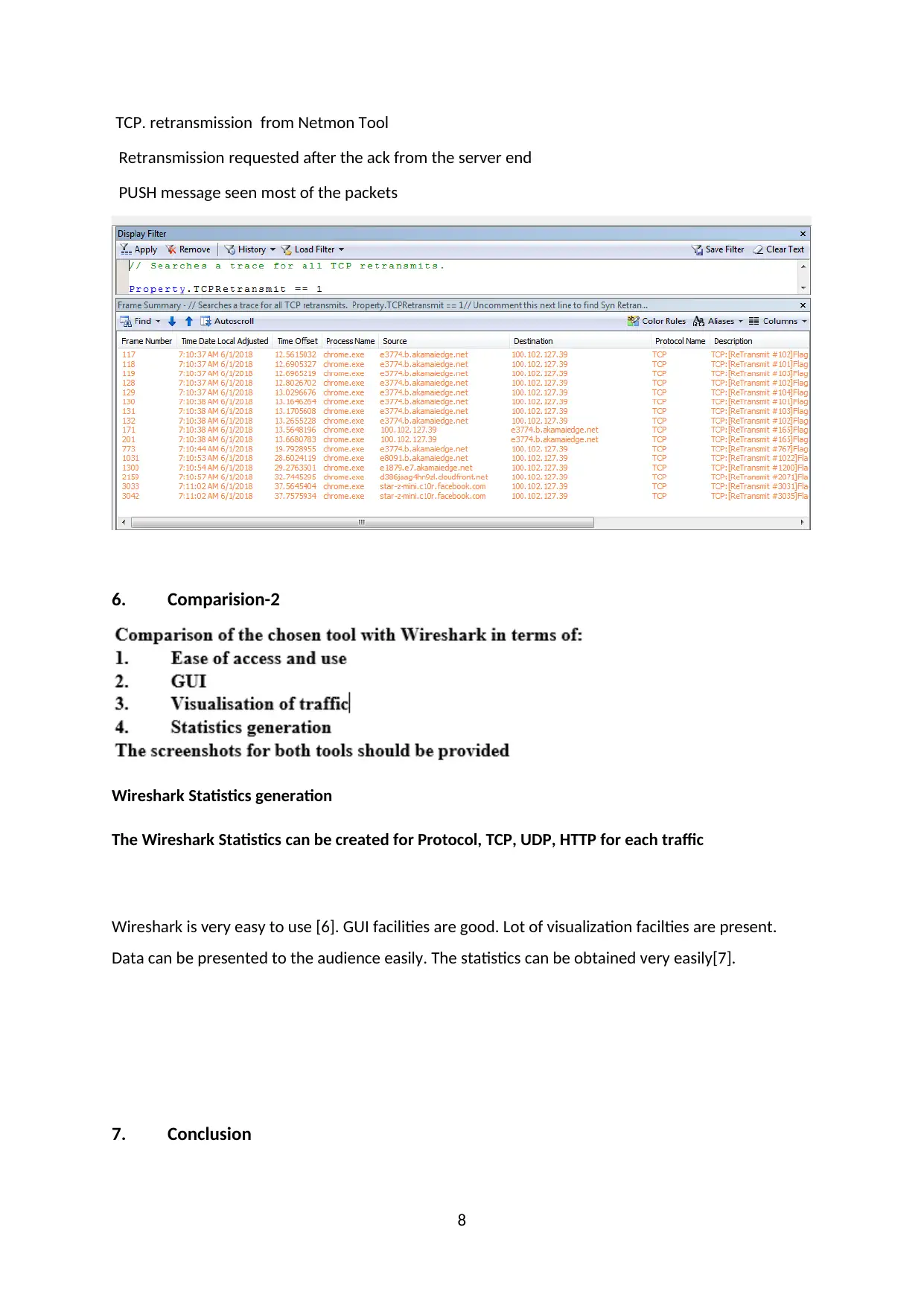
TCP. retransmission from Netmon Tool
Retransmission requested after the ack from the server end
PUSH message seen most of the packets
6. Comparision-2
Wireshark Statistics generation
The Wireshark Statistics can be created for Protocol, TCP, UDP, HTTP for each traffic
Wireshark is very easy to use [6]. GUI facilities are good. Lot of visualization facilties are present.
Data can be presented to the audience easily. The statistics can be obtained very easily[7].
7. Conclusion
8
Retransmission requested after the ack from the server end
PUSH message seen most of the packets
6. Comparision-2
Wireshark Statistics generation
The Wireshark Statistics can be created for Protocol, TCP, UDP, HTTP for each traffic
Wireshark is very easy to use [6]. GUI facilities are good. Lot of visualization facilties are present.
Data can be presented to the audience easily. The statistics can be obtained very easily[7].
7. Conclusion
8

Some of the advantages of wireshark are as follows.
Can be installed in both windows and linux.
It can collect the data from the live interface.
The details can be displayed with lot of information
This can save the data captured and the saved data can be opened anywhere
Data can be imported and exported among the programs
Lot of filters are used in wireshark and those filters are very useful.
Base don many conditions, pockets can be filtered.
Based on filters the data can be colourized.
The statistical information offered by the wireshark is very good
It supports lot of protocols
Wireshark supports bittorrent and apple protocols too
Wireshark gives best user interface
The gui of the wireshark is very clear
Open source community gives excellent support for the wireshark
Wireless community is very active community
Network monitor also one of the good network monitoring tools.
Main purpose of the netmon is troubleshooting
The collecte data will be having source IP details and destination IP details.
Capturing is the governing process in NetMon
Data capture can be customized
The duration of the data capture can be customized
The user interface can be customized
The output data that is captured can be customized
Wireshark runs on several platforms such as operating systems and for this project two operating
systems can be used and they are windows and Linux. And wireshark is used to do the same.
Wireshark comes with lot of functions using which the network problems can be resolved. Poor
configuration , Deice failures are some of the reasons for the network failure. Big and usefull analysis
can be done using filters. Graphical tools represents the data using graphics and hence it will reach
9
Can be installed in both windows and linux.
It can collect the data from the live interface.
The details can be displayed with lot of information
This can save the data captured and the saved data can be opened anywhere
Data can be imported and exported among the programs
Lot of filters are used in wireshark and those filters are very useful.
Base don many conditions, pockets can be filtered.
Based on filters the data can be colourized.
The statistical information offered by the wireshark is very good
It supports lot of protocols
Wireshark supports bittorrent and apple protocols too
Wireshark gives best user interface
The gui of the wireshark is very clear
Open source community gives excellent support for the wireshark
Wireless community is very active community
Network monitor also one of the good network monitoring tools.
Main purpose of the netmon is troubleshooting
The collecte data will be having source IP details and destination IP details.
Capturing is the governing process in NetMon
Data capture can be customized
The duration of the data capture can be customized
The user interface can be customized
The output data that is captured can be customized
Wireshark runs on several platforms such as operating systems and for this project two operating
systems can be used and they are windows and Linux. And wireshark is used to do the same.
Wireshark comes with lot of functions using which the network problems can be resolved. Poor
configuration , Deice failures are some of the reasons for the network failure. Big and usefull analysis
can be done using filters. Graphical tools represents the data using graphics and hence it will reach
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
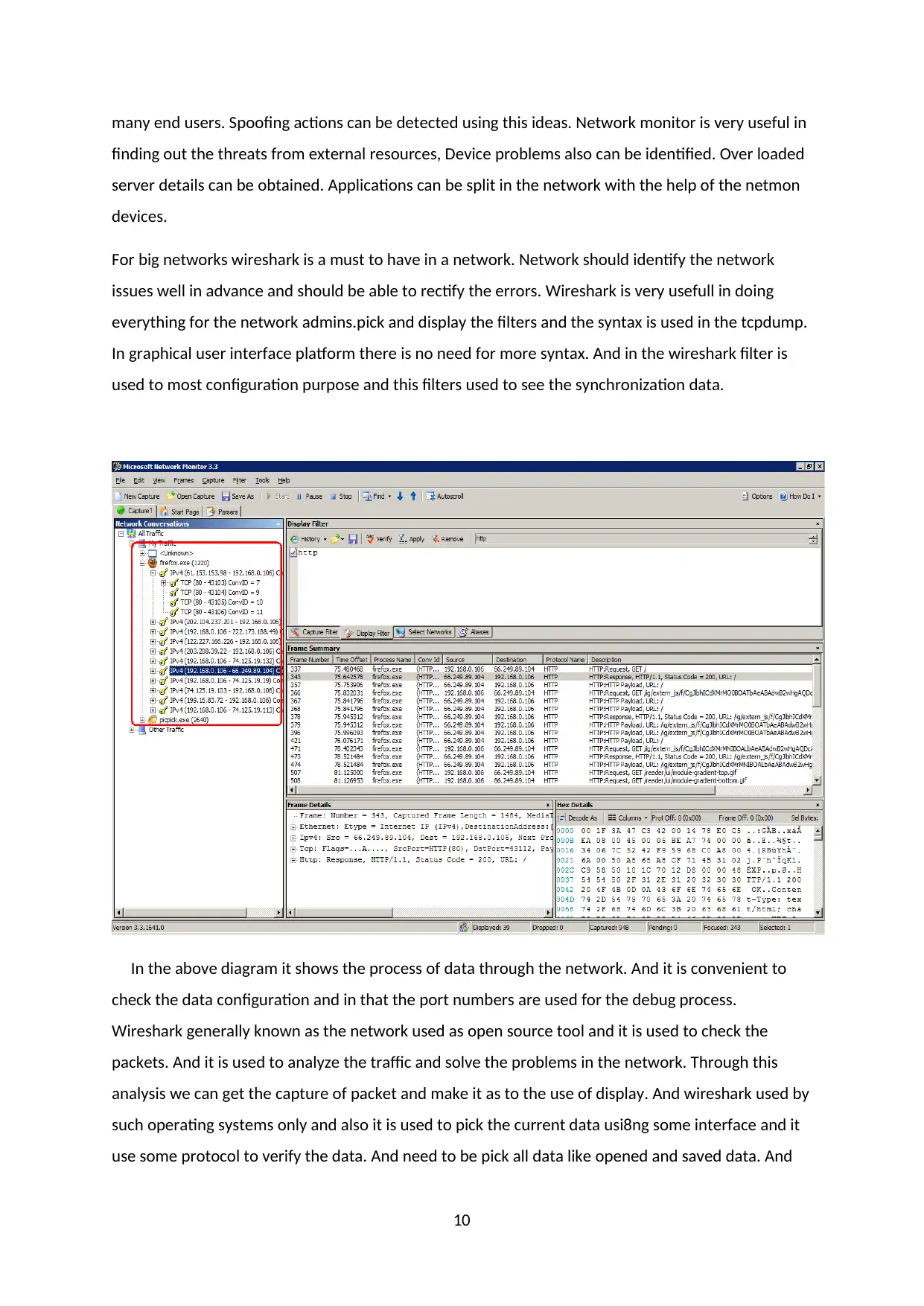
many end users. Spoofing actions can be detected using this ideas. Network monitor is very useful in
finding out the threats from external resources, Device problems also can be identified. Over loaded
server details can be obtained. Applications can be split in the network with the help of the netmon
devices.
For big networks wireshark is a must to have in a network. Network should identify the network
issues well in advance and should be able to rectify the errors. Wireshark is very usefull in doing
everything for the network admins.pick and display the filters and the syntax is used in the tcpdump.
In graphical user interface platform there is no need for more syntax. And in the wireshark filter is
used to most configuration purpose and this filters used to see the synchronization data.
In the above diagram it shows the process of data through the network. And it is convenient to
check the data configuration and in that the port numbers are used for the debug process.
Wireshark generally known as the network used as open source tool and it is used to check the
packets. And it is used to analyze the traffic and solve the problems in the network. Through this
analysis we can get the capture of packet and make it as to the use of display. And wireshark used by
such operating systems only and also it is used to pick the current data usi8ng some interface and it
use some protocol to verify the data. And need to be pick all data like opened and saved data. And
10
finding out the threats from external resources, Device problems also can be identified. Over loaded
server details can be obtained. Applications can be split in the network with the help of the netmon
devices.
For big networks wireshark is a must to have in a network. Network should identify the network
issues well in advance and should be able to rectify the errors. Wireshark is very usefull in doing
everything for the network admins.pick and display the filters and the syntax is used in the tcpdump.
In graphical user interface platform there is no need for more syntax. And in the wireshark filter is
used to most configuration purpose and this filters used to see the synchronization data.
In the above diagram it shows the process of data through the network. And it is convenient to
check the data configuration and in that the port numbers are used for the debug process.
Wireshark generally known as the network used as open source tool and it is used to check the
packets. And it is used to analyze the traffic and solve the problems in the network. Through this
analysis we can get the capture of packet and make it as to the use of display. And wireshark used by
such operating systems only and also it is used to pick the current data usi8ng some interface and it
use some protocol to verify the data. And need to be pick all data like opened and saved data. And
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the packets need to be found by some distinction. And it is used to make various condition and use
them as well [9][10][11]. And wiresahrk looks like popular and the people’s lot of them use this and
used to pick the data. And it is used many protocols for data configuration. And wiresahrk use some
interface and it belonging to graphical user interface. And for the packet recognizing the wireshark is
mostly one and it is known as an open source software and it is used to many purpose in the
industry and it has many rules for that it has many operating system. And for collecting the
information the monitor is needed and also for analyzing the data. And in this monitor it has
addresses like source and destination and for that some protocols are used data and it analyze how
to get the data and how to give the proper arrangement and analyze what are the data inside the
packets these are the things monitored through the network. And the wiresahrk has various function
to solve the problems through the network and used to analyze the configuration. And using this
tool we can analyze the data easily and some problems are discovered by the data form analyzing
and by usage the filters we can analyze the traffic and the functions and it use the kind of protocol
for the network communications.
It gives the feature to identify the sender’s address of the data packet sent through the
network system. That gives the feature to spoof the activities in network system. For this reason only
network admins checks the threads caused in outside of the network. They also can able to check
the reason for server crashing. It splits the data packets. That was monitored from the frame pane.
Due to the day to day increase of the no of network devices that also increase the no of monitor and
control tools. The network admins also have the responsibility to ensure the proper working of the
network. They also needs to perform the monitoring works also. They identify the root causes for
the problem and remove it before it occurs. For that purpose they use the traffic information about
the network. By this method the security flaws are identified. For network planning it was carried
out by this technique [8].
8. References
[1]J. Watson and J. Watson, "8 best packet sniffers and network analyzers for 2018 |
Comparitech", Comparitech, 2018. [Online]. Available: https://www.comparitech.com/net-
admin/packet-sniffer-network-analyzers/. [Accessed: 01- Jun- 2018].
[2]"Wireshark · Go Deep.", Wireshark.org, 2018. [Online]. Available: https://www.wireshark.org/.
[Accessed: 01- Jun- 2018].
11
them as well [9][10][11]. And wiresahrk looks like popular and the people’s lot of them use this and
used to pick the data. And it is used many protocols for data configuration. And wiresahrk use some
interface and it belonging to graphical user interface. And for the packet recognizing the wireshark is
mostly one and it is known as an open source software and it is used to many purpose in the
industry and it has many rules for that it has many operating system. And for collecting the
information the monitor is needed and also for analyzing the data. And in this monitor it has
addresses like source and destination and for that some protocols are used data and it analyze how
to get the data and how to give the proper arrangement and analyze what are the data inside the
packets these are the things monitored through the network. And the wiresahrk has various function
to solve the problems through the network and used to analyze the configuration. And using this
tool we can analyze the data easily and some problems are discovered by the data form analyzing
and by usage the filters we can analyze the traffic and the functions and it use the kind of protocol
for the network communications.
It gives the feature to identify the sender’s address of the data packet sent through the
network system. That gives the feature to spoof the activities in network system. For this reason only
network admins checks the threads caused in outside of the network. They also can able to check
the reason for server crashing. It splits the data packets. That was monitored from the frame pane.
Due to the day to day increase of the no of network devices that also increase the no of monitor and
control tools. The network admins also have the responsibility to ensure the proper working of the
network. They also needs to perform the monitoring works also. They identify the root causes for
the problem and remove it before it occurs. For that purpose they use the traffic information about
the network. By this method the security flaws are identified. For network planning it was carried
out by this technique [8].
8. References
[1]J. Watson and J. Watson, "8 best packet sniffers and network analyzers for 2018 |
Comparitech", Comparitech, 2018. [Online]. Available: https://www.comparitech.com/net-
admin/packet-sniffer-network-analyzers/. [Accessed: 01- Jun- 2018].
[2]"Wireshark · Go Deep.", Wireshark.org, 2018. [Online]. Available: https://www.wireshark.org/.
[Accessed: 01- Jun- 2018].
11

[3]R. Cole and R. Ramaswamy, Wide-area data network performance engineering. Boston: Artech
House, 2000.
[4]C. Chapman, Network performance and security. .
[5]"Comparison of packet sniffers - Colasoft", Colasoft.com, 2018. [Online]. Available:
https://www.colasoft.com/resources/vs_sniffer.php. [Accessed: 01- Jun- 2018].
[6]"Packet sniffers – SecTools Top Network Security Tools", Sectools.org, 2018. [Online]. Available:
http://sectools.org/tag/sniffers/. [Accessed: 01- Jun- 2018].
[7]R. Grimes, "6 Network Protocol Analyzers", IT Pro, 2018. [Online]. Available:
http://www.itprotoday.com/management-mobility/6-network-protocol-analyzers. [Accessed:
01- Jun- 2018].
[8]"Wireshark v.s NetMon", Social.technet.microsoft.com, 2018. [Online]. Available:
https://social.technet.microsoft.com/Forums/en-US/86c8614c-d0f1-42d0-814c-
e85529964861/wireshark-vs-netmon?forum=netmon. [Accessed: 01- Jun- 2018].
[9]R. Shimonski, The wireshark field guide. Amsterdam: Syngress, 2013.
[10]N. Kumar, Y. Ramdoss and Y. Orzach, Network Analysis Using Wireshark 2 Cookbook.
Birmingham: Packt Publishing, 2018.
[11]G. Eliot, The mill on the Floss. New York: Open Road Integrated Media, 2016.
12
House, 2000.
[4]C. Chapman, Network performance and security. .
[5]"Comparison of packet sniffers - Colasoft", Colasoft.com, 2018. [Online]. Available:
https://www.colasoft.com/resources/vs_sniffer.php. [Accessed: 01- Jun- 2018].
[6]"Packet sniffers – SecTools Top Network Security Tools", Sectools.org, 2018. [Online]. Available:
http://sectools.org/tag/sniffers/. [Accessed: 01- Jun- 2018].
[7]R. Grimes, "6 Network Protocol Analyzers", IT Pro, 2018. [Online]. Available:
http://www.itprotoday.com/management-mobility/6-network-protocol-analyzers. [Accessed:
01- Jun- 2018].
[8]"Wireshark v.s NetMon", Social.technet.microsoft.com, 2018. [Online]. Available:
https://social.technet.microsoft.com/Forums/en-US/86c8614c-d0f1-42d0-814c-
e85529964861/wireshark-vs-netmon?forum=netmon. [Accessed: 01- Jun- 2018].
[9]R. Shimonski, The wireshark field guide. Amsterdam: Syngress, 2013.
[10]N. Kumar, Y. Ramdoss and Y. Orzach, Network Analysis Using Wireshark 2 Cookbook.
Birmingham: Packt Publishing, 2018.
[11]G. Eliot, The mill on the Floss. New York: Open Road Integrated Media, 2016.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




