Pen Testing Methodology: SOP, Decision Tree, and Analysis
VerifiedAdded on 2022/08/11
|11
|2477
|29
Report
AI Summary
This report provides a comprehensive overview of penetration testing methodologies, including black box, white box, and grey box testing, comparing their operational processes, advantages, and disadvantages. It delves into the statutory and legal considerations that penetration testers must be aware of, such as legal authority, scope of work, licensing, and data privacy, as well as ethical considerations. The report also outlines a Standard Operating Procedure (SOP) for conducting penetration tests, detailing the purpose, scope, roles, responsibilities, and the steps involved, from introductory briefings to exploitation and reporting. Additionally, the report includes a decision tree to aid in the planning and execution of penetration testing engagements, ensuring a structured and legally compliant approach to security assessments. This report is a valuable resource for students and professionals seeking to understand and implement effective penetration testing strategies, offering insights into both the technical and legal aspects of the field.

Running head: PEN TEST METHODOLOGY
PEN TEST METHODOLOGY
Name of the Student
Name of the University
Author note
PEN TEST METHODOLOGY
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PEN TEST METHODOLOGY
Table of Contents
PEN TESTING METHODOLOGY COMPARISON.....................................................................2
Statutory and legal consideration of a penetration tester.................................................................4
Standard Operating Procedure.........................................................................................................6
Decision tree diagram......................................................................................................................9
References......................................................................................................................................10
PEN TEST METHODOLOGY
Table of Contents
PEN TESTING METHODOLOGY COMPARISON.....................................................................2
Statutory and legal consideration of a penetration tester.................................................................4
Standard Operating Procedure.........................................................................................................6
Decision tree diagram......................................................................................................................9
References......................................................................................................................................10

2
PEN TEST METHODOLOGY
PEN TESTING METHODOLOGY COMPARISON
There are three methodologies that are considered for performing pen testing
methodology. They are namely Black Box Penetration Testing, White Box Penetration Testing
and Gray Box Testing.
These methodologies vary in their operational processes. It have been seen that in case of
Black Box penetration testing, the consultant does not have any kind of access to the internal
information and hence wise they do not have any kind of access to the client’s application
network (Mehta, Raj and Singh 2018). The job role of the consultant have been acting important
in the process as well. The entire process of reconnaissance have been obtaining sensitive
knowledge that is needed to be proceeded. This type of Black Box penetration testing is the most
realistic testing method. IT have been seen that the time that is take for detecting an attack have
been high. The chances of detecting the vulnerabilities are also lesser than the other two testing
methodology. There are several security tools that are present in the networking services as this
might be providing a robustness and security to the network (Stefinko, Piskozub and Banakh
2016). This prevents the network form getting its vulnerabilities exploited. However, there is an
issue in this method. The issue is that the sole thing that is required for exploiting the
vulnerability is that with the help of variation in the setting or connecting from a different
browser version will ensure that the vulnerabilities can be exploited.
Whereas in case of Grey Box Testing, the access point on the internal section of the
network is higher. Internal knowledge of the application falls under the category of the grey box
testing methodology. It can be stated that in case of black box testing, the testing process begins
with the engagement from an external view point. Whereas in case of grey box penetration
PEN TEST METHODOLOGY
PEN TESTING METHODOLOGY COMPARISON
There are three methodologies that are considered for performing pen testing
methodology. They are namely Black Box Penetration Testing, White Box Penetration Testing
and Gray Box Testing.
These methodologies vary in their operational processes. It have been seen that in case of
Black Box penetration testing, the consultant does not have any kind of access to the internal
information and hence wise they do not have any kind of access to the client’s application
network (Mehta, Raj and Singh 2018). The job role of the consultant have been acting important
in the process as well. The entire process of reconnaissance have been obtaining sensitive
knowledge that is needed to be proceeded. This type of Black Box penetration testing is the most
realistic testing method. IT have been seen that the time that is take for detecting an attack have
been high. The chances of detecting the vulnerabilities are also lesser than the other two testing
methodology. There are several security tools that are present in the networking services as this
might be providing a robustness and security to the network (Stefinko, Piskozub and Banakh
2016). This prevents the network form getting its vulnerabilities exploited. However, there is an
issue in this method. The issue is that the sole thing that is required for exploiting the
vulnerability is that with the help of variation in the setting or connecting from a different
browser version will ensure that the vulnerabilities can be exploited.
Whereas in case of Grey Box Testing, the access point on the internal section of the
network is higher. Internal knowledge of the application falls under the category of the grey box
testing methodology. It can be stated that in case of black box testing, the testing process begins
with the engagement from an external view point. Whereas in case of grey box penetration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PEN TEST METHODOLOGY
testing, some internal access is already granted. Access to the logic flow charts are already
provided to the Grey Box penetration testing process. As a proper outlook to the background is
provide the consultant a better scenario understanding ability. The vulnerabilities that are present
in the operational process are also well stated. This helps the consultants to perform better
analysis of the vulnerabilities that are present in the network system. The major difference in
between Grey box penetration testing and Black Box penetration testing is that the consultants
are allowed to create a more streamlined testing process in the in grey box penetration testing
process. Hence the time that is required in performing the testing process is case of grey box
testing is much lower than that of the black box testing.
Again it is seen that white box testing is mainly focused on providing proper security to
the application as it has complete access to the application and system. The white box testing
process ensures that there is a complete access to the code of the application. Thus it is seen that
the consultant has the open access to the source code of the application. Hence wise granting of
high level privilege have been one of the major advantage that is received during the usage of the
white box testing process. The main reason of using the methodology of white box testing is that
there will be proper identification of potential weaknesses that are present in the areas, namely
logical vulnerabilities. Understanding the vulnerabilities that are present in the processing of the
potential security exposures along with the poorly developed code is also performed. Lack of
defensive areas in case if present in also well understood. These are the major aspect that is
considered. Hence it can be stated that white box testing method have been the most efficient
testing method. However there have been issues with practicality in this testing method.
PEN TEST METHODOLOGY
testing, some internal access is already granted. Access to the logic flow charts are already
provided to the Grey Box penetration testing process. As a proper outlook to the background is
provide the consultant a better scenario understanding ability. The vulnerabilities that are present
in the operational process are also well stated. This helps the consultants to perform better
analysis of the vulnerabilities that are present in the network system. The major difference in
between Grey box penetration testing and Black Box penetration testing is that the consultants
are allowed to create a more streamlined testing process in the in grey box penetration testing
process. Hence the time that is required in performing the testing process is case of grey box
testing is much lower than that of the black box testing.
Again it is seen that white box testing is mainly focused on providing proper security to
the application as it has complete access to the application and system. The white box testing
process ensures that there is a complete access to the code of the application. Thus it is seen that
the consultant has the open access to the source code of the application. Hence wise granting of
high level privilege have been one of the major advantage that is received during the usage of the
white box testing process. The main reason of using the methodology of white box testing is that
there will be proper identification of potential weaknesses that are present in the areas, namely
logical vulnerabilities. Understanding the vulnerabilities that are present in the processing of the
potential security exposures along with the poorly developed code is also performed. Lack of
defensive areas in case if present in also well understood. These are the major aspect that is
considered. Hence it can be stated that white box testing method have been the most efficient
testing method. However there have been issues with practicality in this testing method.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PEN TEST METHODOLOGY
Statutory and legal consideration of a penetration tester
There are a few statutory and legal issues that can be considered for a penetration tester.
They are namely legal authority, get out of jail free, damage control, Indemnification, Hack
back, Scope of Work, Professionalism, Licensing and Certification, Venue and Jurisdiction,
Privacy issues, Data Ownership and Duty to Warn.
It have been seen that in case of pen testing the main aspect that is to be considered is that
breaking into a computing device acts important. This have been one of the major aspect that is
to be considered. It is stated that ethical hackers will only be trying to penetrate the system
behesting the owner as well as the operator. Another aspect that is seen in this section is that the
process is that there is a certain limit till which the tester needs to penetrate. Even if the tester
crosses their limit during performing their duties might lead to face them severe issues legally by
the company.
Another aspect that is to be considered in this case is that when the penetrating test is
performed in the production or live system the impact of the test directly affect the users. Hence
then the user might be facing severe issues in the operating process (Cardwell 2016). Disrupting
a brittle system have been another aspect that might be affecting the entire section.
Indemnification is another issue that is to be considered. This section ensures that the
authorization process have been affecting the entire operational process. It have been seen that in
time of performing the pen testing the entire data sets that are present and are important in
completion of the working process might get disrupted or get corrupted. Security system might
be getting affected and the tester is held responsible for this section. Hence legal issues arise in
this section.
PEN TEST METHODOLOGY
Statutory and legal consideration of a penetration tester
There are a few statutory and legal issues that can be considered for a penetration tester.
They are namely legal authority, get out of jail free, damage control, Indemnification, Hack
back, Scope of Work, Professionalism, Licensing and Certification, Venue and Jurisdiction,
Privacy issues, Data Ownership and Duty to Warn.
It have been seen that in case of pen testing the main aspect that is to be considered is that
breaking into a computing device acts important. This have been one of the major aspect that is
to be considered. It is stated that ethical hackers will only be trying to penetrate the system
behesting the owner as well as the operator. Another aspect that is seen in this section is that the
process is that there is a certain limit till which the tester needs to penetrate. Even if the tester
crosses their limit during performing their duties might lead to face them severe issues legally by
the company.
Another aspect that is to be considered in this case is that when the penetrating test is
performed in the production or live system the impact of the test directly affect the users. Hence
then the user might be facing severe issues in the operating process (Cardwell 2016). Disrupting
a brittle system have been another aspect that might be affecting the entire section.
Indemnification is another issue that is to be considered. This section ensures that the
authorization process have been affecting the entire operational process. It have been seen that in
time of performing the pen testing the entire data sets that are present and are important in
completion of the working process might get disrupted or get corrupted. Security system might
be getting affected and the tester is held responsible for this section. Hence legal issues arise in
this section.

5
PEN TEST METHODOLOGY
Another legal and statutory issue that is faced in the system is that the customers try to
hack back when they find that pen testing is being performed. In this case the legal attributes are
not well defined. It is seen that the hacking back is also considered as an offense and falls under
the heading of hacking. This act as a legal issue that might be troubling the tester.
Developing a proper scope of work have been a statutory issue that is to be considered. It
have been seen that the wireless set up as well as the cables were not considered to be a
vulnerability. However it have been seen that attacks have been imposed from these set up as
well. This have been also acting as a legal aspect that is to be considered (de Jiménez 2016).
During conduction of pen testing the main issue that have been seen is that these issues are to be
considered as well. With proper defining of the testing process, the main issue that is to be
considered is that the security process is to be maintained.
Licensing and certification have been another aspect that is to be considered. This
consideration includes the fact that a pen tester needs to perform their duty in a proper manner
and this will be ensuring that proper licensing of the process and the testing method is to be
performed. Again if the testing process is not performed in a proper manner the entire process
gets effected (Vega, Orozco and Villalba 2017). The type of investigation that will be made is
needed to be properly licensed in order to eliminate the issues that are present in operational
process.
The foremost issue that is present in the process is that there might be presence of privacy
issues in the functional process. This section ensures that this might happen that during the
testing process, the level of processing might be getting affected. In case the limit of penetration
is crossed, the main issue that will be faced by the tester is that they might be accused of
PEN TEST METHODOLOGY
Another legal and statutory issue that is faced in the system is that the customers try to
hack back when they find that pen testing is being performed. In this case the legal attributes are
not well defined. It is seen that the hacking back is also considered as an offense and falls under
the heading of hacking. This act as a legal issue that might be troubling the tester.
Developing a proper scope of work have been a statutory issue that is to be considered. It
have been seen that the wireless set up as well as the cables were not considered to be a
vulnerability. However it have been seen that attacks have been imposed from these set up as
well. This have been also acting as a legal aspect that is to be considered (de Jiménez 2016).
During conduction of pen testing the main issue that have been seen is that these issues are to be
considered as well. With proper defining of the testing process, the main issue that is to be
considered is that the security process is to be maintained.
Licensing and certification have been another aspect that is to be considered. This
consideration includes the fact that a pen tester needs to perform their duty in a proper manner
and this will be ensuring that proper licensing of the process and the testing method is to be
performed. Again if the testing process is not performed in a proper manner the entire process
gets effected (Vega, Orozco and Villalba 2017). The type of investigation that will be made is
needed to be properly licensed in order to eliminate the issues that are present in operational
process.
The foremost issue that is present in the process is that there might be presence of privacy
issues in the functional process. This section ensures that this might happen that during the
testing process, the level of processing might be getting affected. In case the limit of penetration
is crossed, the main issue that will be faced by the tester is that they might be accused of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PEN TEST METHODOLOGY
deliberate violation of the privacy policies. As in case of occurring of this security violation the
data sets of the clients might be getting breached.
Standard Operating Procedure
Introduction
A security penetration test acts as an activity that will be ensuring that the test team will
be attempting to circumvent the entire security process. This section ensures that internal and
external unauthorized intruders are considered in this process. Due to the sensitive nature of the
entire process, there are several measures that are to be taken for performing the penetration
testing.
Purpose
The major purpose of the SOP is to provide a layout of the procedures and hence wise
establish the rules that are important in the proposing of security penetration process.
Scope
The main scope of the SOP is to analyze the processes that are considered for performing
the penetration test.
Roles and Responsibilities
Be responsible for proper performing of the penetration test.
Perform coordination in the penetration process
Be recipient to all the data sets that are available for the ITS Security Penetration test.
Be responsible for the security issues that are present in the penetration process.
PEN TEST METHODOLOGY
deliberate violation of the privacy policies. As in case of occurring of this security violation the
data sets of the clients might be getting breached.
Standard Operating Procedure
Introduction
A security penetration test acts as an activity that will be ensuring that the test team will
be attempting to circumvent the entire security process. This section ensures that internal and
external unauthorized intruders are considered in this process. Due to the sensitive nature of the
entire process, there are several measures that are to be taken for performing the penetration
testing.
Purpose
The major purpose of the SOP is to provide a layout of the procedures and hence wise
establish the rules that are important in the proposing of security penetration process.
Scope
The main scope of the SOP is to analyze the processes that are considered for performing
the penetration test.
Roles and Responsibilities
Be responsible for proper performing of the penetration test.
Perform coordination in the penetration process
Be recipient to all the data sets that are available for the ITS Security Penetration test.
Be responsible for the security issues that are present in the penetration process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PEN TEST METHODOLOGY
Penetration test Point of Contact
Being responsible for the penetration test and have the primary interface with the help of
Site POC for all the testing activities that are to be performed. After this process proper
documentation of the data is to be performed. With the help of the documentation, proper
penetration can be made. After this process, proper assigning of roles will take place. This is
considered as an important prospect. Proper identification of the estimated dates of the
performing of pen testing. After this process the steps that will be required for protecting the test
plan is also stated. Hence wise final deliverables are also stated in the section (Casola et al
2018). Proper coordination of the IT Security Pen test is also considered as a major aspect that is
to be considered. After this process, maintenance of the data that are collected in the process will
be performed in a better manner.
Process
It have been estimated that the Point of Contact as well as the Pen Test plan is separately
performed. Thus it can be stated that individual responsible for the penetration coordination.
Notifying managers have been a prime aspect that id to be considered in a process. This section
also ensures test activities and schedules will be providing better planned activities and primary
interface is also considered as management notification process. It can be stated that allocating
task to the tester acts as one of the major aspect that is to be considered.
Steps for performing the penetration test
The major steps that are to be taken for performing the penetration tests are as follows: -
PEN TEST METHODOLOGY
Penetration test Point of Contact
Being responsible for the penetration test and have the primary interface with the help of
Site POC for all the testing activities that are to be performed. After this process proper
documentation of the data is to be performed. With the help of the documentation, proper
penetration can be made. After this process, proper assigning of roles will take place. This is
considered as an important prospect. Proper identification of the estimated dates of the
performing of pen testing. After this process the steps that will be required for protecting the test
plan is also stated. Hence wise final deliverables are also stated in the section (Casola et al
2018). Proper coordination of the IT Security Pen test is also considered as a major aspect that is
to be considered. After this process, maintenance of the data that are collected in the process will
be performed in a better manner.
Process
It have been estimated that the Point of Contact as well as the Pen Test plan is separately
performed. Thus it can be stated that individual responsible for the penetration coordination.
Notifying managers have been a prime aspect that id to be considered in a process. This section
also ensures test activities and schedules will be providing better planned activities and primary
interface is also considered as management notification process. It can be stated that allocating
task to the tester acts as one of the major aspect that is to be considered.
Steps for performing the penetration test
The major steps that are to be taken for performing the penetration tests are as follows: -

8
PEN TEST METHODOLOGY
Introductory briefing: In this stage, there will be key players will be getting introduced. This
section ensures that there will be consideration regarding the tester capabilities. Reviewing
resources are also performed in this stage.
Technical and Administrative Face to face meeting: This includes the likes of conducting the
introductions and perform specification of meeting the objectives. Proper discussion of the
selection criteria have been one of the major attribute that is to be considered. Specifying the
tools that are required for performing this process is also considered in the process. Finalizing the
resources and logistics have been another aspect that is to be considered in the process.
Executive In Briefing: In this process introduction of the pen testing method is also considered.
Reviewing selected have been one of the major aspect that is considered. Addressing issues and
concerns have been one of the major aspect that is performed in this section.
Reviewing of the IT Policies: Planning and scheduling of the test is also performed in this
process. Proper exploitation of the vulnerabilities are also considered in the process.
Performing outsider penetration test: Planning and scheduling the entire process. Conducting
the examination process. Reporting of the data that have been gathered is also performed in the
section.
Perform insider penetration test: Perform planning and scheduling and perform the scheduling
with side staff.
Analysis of the collected data: In this process the data that have been collected are analyzed.
Exit briefing: In this process, summarizing the finding is performed.
PEN TEST METHODOLOGY
Introductory briefing: In this stage, there will be key players will be getting introduced. This
section ensures that there will be consideration regarding the tester capabilities. Reviewing
resources are also performed in this stage.
Technical and Administrative Face to face meeting: This includes the likes of conducting the
introductions and perform specification of meeting the objectives. Proper discussion of the
selection criteria have been one of the major attribute that is to be considered. Specifying the
tools that are required for performing this process is also considered in the process. Finalizing the
resources and logistics have been another aspect that is to be considered in the process.
Executive In Briefing: In this process introduction of the pen testing method is also considered.
Reviewing selected have been one of the major aspect that is considered. Addressing issues and
concerns have been one of the major aspect that is performed in this section.
Reviewing of the IT Policies: Planning and scheduling of the test is also performed in this
process. Proper exploitation of the vulnerabilities are also considered in the process.
Performing outsider penetration test: Planning and scheduling the entire process. Conducting
the examination process. Reporting of the data that have been gathered is also performed in the
section.
Perform insider penetration test: Perform planning and scheduling and perform the scheduling
with side staff.
Analysis of the collected data: In this process the data that have been collected are analyzed.
Exit briefing: In this process, summarizing the finding is performed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
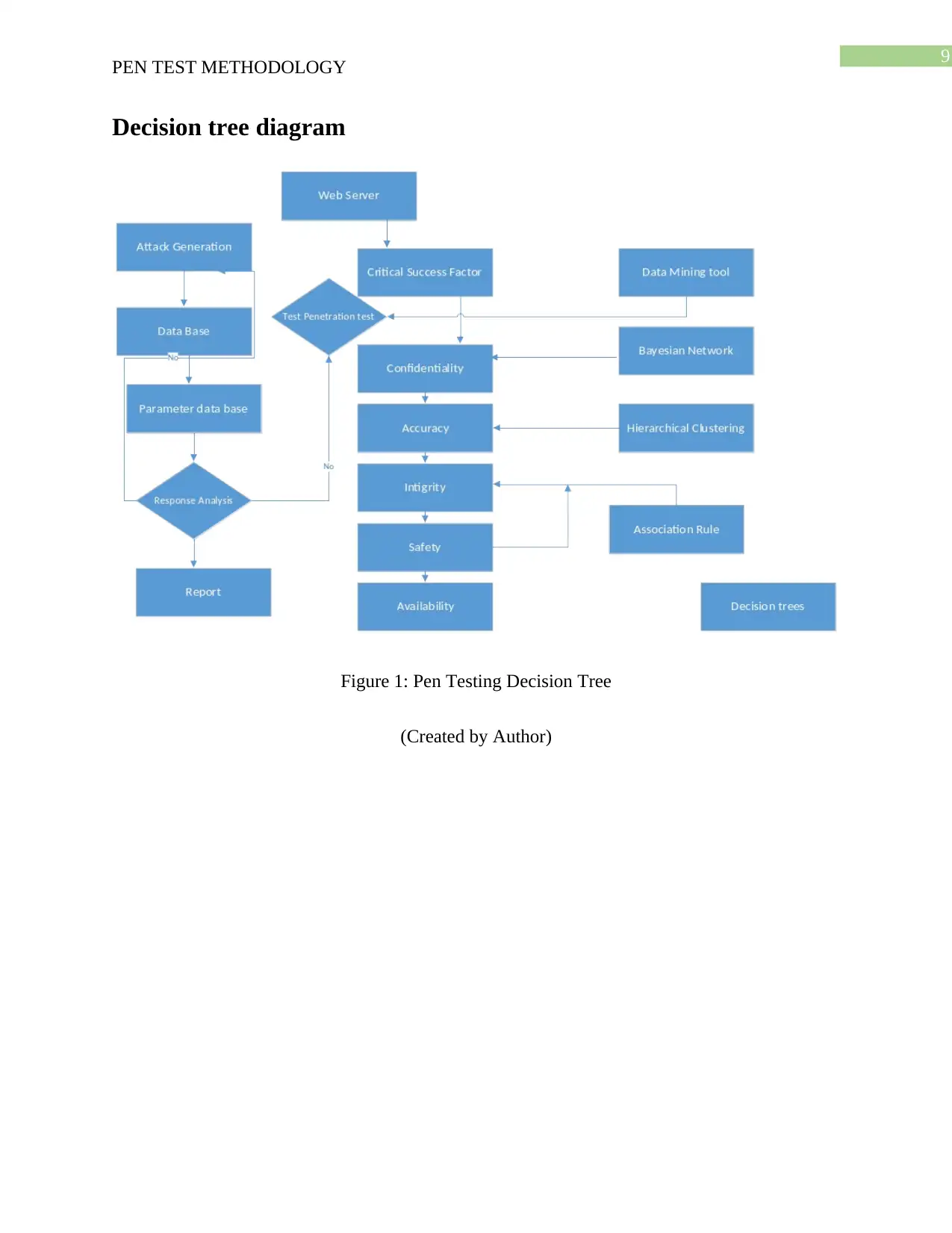
9
PEN TEST METHODOLOGY
Decision tree diagram
Figure 1: Pen Testing Decision Tree
(Created by Author)
PEN TEST METHODOLOGY
Decision tree diagram
Figure 1: Pen Testing Decision Tree
(Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
0PEN TEST METHODOLOGY
References
Mehta, S., Raj, G. and Singh, D., 2018. Penetration Testing as a Test Phase in Web Service
Testing a Black Box Pen Testing Approach. In Smart Computing and Informatics (pp. 623-635).
Springer, Singapore.
Cardwell, K., 2016. Building Virtual Pentesting Labs for Advanced Penetration Testing. Packt
Publishing Ltd.
Vega, E.A.A., Orozco, A.L.S. and Villalba, L.J.G., 2017. Benchmarking of pentesting
tools. International Journal of Computer, Electrical, Automation, Control and Information
Engineering, 11(5), pp.602-605.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
de Jiménez, R.E.L., 2016, November. Pentesting on web applications using ethical-hacking.
In 2016 IEEE 36th Central American and Panama Convention (CONCAPAN XXXVI) (pp. 1-6).
IEEE.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
0PEN TEST METHODOLOGY
References
Mehta, S., Raj, G. and Singh, D., 2018. Penetration Testing as a Test Phase in Web Service
Testing a Black Box Pen Testing Approach. In Smart Computing and Informatics (pp. 623-635).
Springer, Singapore.
Cardwell, K., 2016. Building Virtual Pentesting Labs for Advanced Penetration Testing. Packt
Publishing Ltd.
Vega, E.A.A., Orozco, A.L.S. and Villalba, L.J.G., 2017. Benchmarking of pentesting
tools. International Journal of Computer, Electrical, Automation, Control and Information
Engineering, 11(5), pp.602-605.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
de Jiménez, R.E.L., 2016, November. Pentesting on web applications using ethical-hacking.
In 2016 IEEE 36th Central American and Panama Convention (CONCAPAN XXXVI) (pp. 1-6).
IEEE.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





