Pen Test Methodology Comparisons
VerifiedAdded on 2023/01/12
|11
|2755
|43
AI Summary
This document compares different penetration testing methodologies and discusses the statutory and ethical considerations of penetration testers. It also explores standard operating procedures, intelligence gathering, vulnerability identification, and target exploitation.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Pen Test Methodology Comparisons
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Contents
INTRODUCTION...........................................................................................................................3
TASK 1............................................................................................................................................3
Critically Compare the Penetration Testing Methodologies.......................................................3
Describe about Statutory and Ethical considerations of penetration tester.................................5
Standard Operating procedures....................................................................................................5
Intelligence Gathering.................................................................................................................7
Vulnerability identification and analysis.....................................................................................7
Target exploitation.......................................................................................................................8
CONCLUSION................................................................................................................................8
REFERENCES..............................................................................................................................10
2
INTRODUCTION...........................................................................................................................3
TASK 1............................................................................................................................................3
Critically Compare the Penetration Testing Methodologies.......................................................3
Describe about Statutory and Ethical considerations of penetration tester.................................5
Standard Operating procedures....................................................................................................5
Intelligence Gathering.................................................................................................................7
Vulnerability identification and analysis.....................................................................................7
Target exploitation.......................................................................................................................8
CONCLUSION................................................................................................................................8
REFERENCES..............................................................................................................................10
2

INTRODUCTION
Penetrating testing is a process that help for identifying security vulnerabilities in different
computing applications. It is mainly useful for evaluating the system and network with various
malicious methodologies that applied within task. It is also giving prioritizing the risk and fix
them by improving overall security response time. With increasing cyber-attack, many
companies will start on performing various security testing on their software application.
Penetration is one of most common that will identify the vulnerable area of system. it including
wilful attacks on the application system to identify weak area which might provide the passage to
malicious and another unauthorised user. Moreover, Penetration testing will help for evaluating
the capacity of system and defence unexpected malicious attacks. The report will discuss about
the different type of penetration testing methodologies that will support for identifying threats. It
will describe about statutory and ethical considerations for improving moral values. There are
different techniques which help for analysing and gathering vulnerabilities such as decision-
making tree, it will consider the target exploitation.
TASK 1
Critically Compare the Penetration Testing Methodologies.
Penetration testing plays important role of identifying, rectifying and understanding the
vulnerabilities in the business computing application. By using Pen test, it can utilise opportunity
to identify potential attackers, who will target the application system. Sometimes, it can be
evaluating the system for gathering large amount of information relates malicious (Bian and
et.al., 2020). Main purpose is to apply penetrating testing methodologies as per requirement. it
will try to gain unauthorised access within system.
Penetration testing methodologies are evolved the function of IT infrastructure of many
business. It wings expanding to different inter-departmental concern such as web application
security. Penetration testing methodologies are classified into different groups: black box, grey
box and white box testing.
3
Penetrating testing is a process that help for identifying security vulnerabilities in different
computing applications. It is mainly useful for evaluating the system and network with various
malicious methodologies that applied within task. It is also giving prioritizing the risk and fix
them by improving overall security response time. With increasing cyber-attack, many
companies will start on performing various security testing on their software application.
Penetration is one of most common that will identify the vulnerable area of system. it including
wilful attacks on the application system to identify weak area which might provide the passage to
malicious and another unauthorised user. Moreover, Penetration testing will help for evaluating
the capacity of system and defence unexpected malicious attacks. The report will discuss about
the different type of penetration testing methodologies that will support for identifying threats. It
will describe about statutory and ethical considerations for improving moral values. There are
different techniques which help for analysing and gathering vulnerabilities such as decision-
making tree, it will consider the target exploitation.
TASK 1
Critically Compare the Penetration Testing Methodologies.
Penetration testing plays important role of identifying, rectifying and understanding the
vulnerabilities in the business computing application. By using Pen test, it can utilise opportunity
to identify potential attackers, who will target the application system. Sometimes, it can be
evaluating the system for gathering large amount of information relates malicious (Bian and
et.al., 2020). Main purpose is to apply penetrating testing methodologies as per requirement. it
will try to gain unauthorised access within system.
Penetration testing methodologies are evolved the function of IT infrastructure of many
business. It wings expanding to different inter-departmental concern such as web application
security. Penetration testing methodologies are classified into different groups: black box, grey
box and white box testing.
3
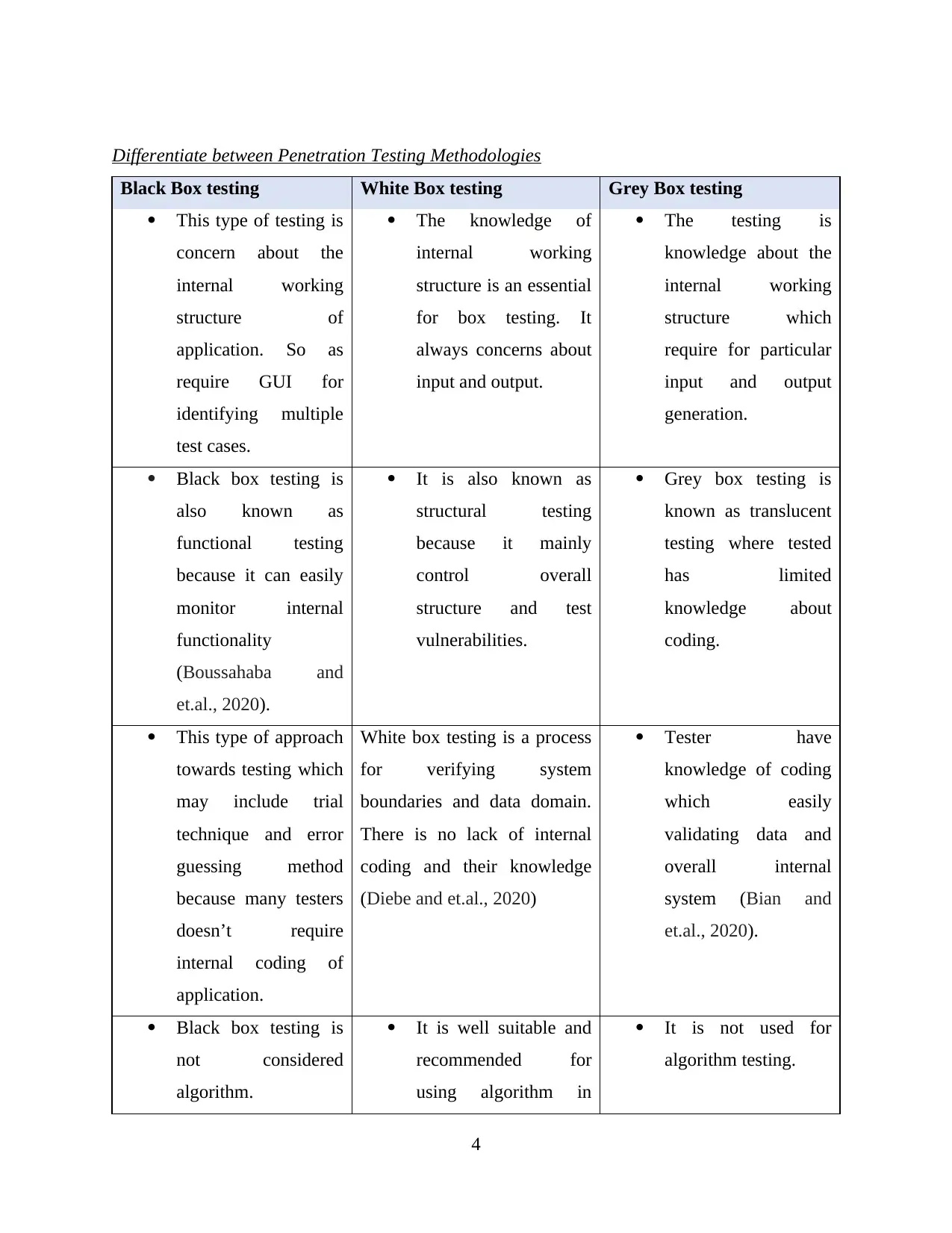
Differentiate between Penetration Testing Methodologies
Black Box testing White Box testing Grey Box testing
This type of testing is
concern about the
internal working
structure of
application. So as
require GUI for
identifying multiple
test cases.
The knowledge of
internal working
structure is an essential
for box testing. It
always concerns about
input and output.
The testing is
knowledge about the
internal working
structure which
require for particular
input and output
generation.
Black box testing is
also known as
functional testing
because it can easily
monitor internal
functionality
(Boussahaba and
et.al., 2020).
It is also known as
structural testing
because it mainly
control overall
structure and test
vulnerabilities.
Grey box testing is
known as translucent
testing where tested
has limited
knowledge about
coding.
This type of approach
towards testing which
may include trial
technique and error
guessing method
because many testers
doesn’t require
internal coding of
application.
White box testing is a process
for verifying system
boundaries and data domain.
There is no lack of internal
coding and their knowledge
(Diebe and et.al., 2020)
Tester have
knowledge of coding
which easily
validating data and
overall internal
system (Bian and
et.al., 2020).
Black box testing is
not considered
algorithm.
It is well suitable and
recommended for
using algorithm in
It is not used for
algorithm testing.
4
Black Box testing White Box testing Grey Box testing
This type of testing is
concern about the
internal working
structure of
application. So as
require GUI for
identifying multiple
test cases.
The knowledge of
internal working
structure is an essential
for box testing. It
always concerns about
input and output.
The testing is
knowledge about the
internal working
structure which
require for particular
input and output
generation.
Black box testing is
also known as
functional testing
because it can easily
monitor internal
functionality
(Boussahaba and
et.al., 2020).
It is also known as
structural testing
because it mainly
control overall
structure and test
vulnerabilities.
Grey box testing is
known as translucent
testing where tested
has limited
knowledge about
coding.
This type of approach
towards testing which
may include trial
technique and error
guessing method
because many testers
doesn’t require
internal coding of
application.
White box testing is a process
for verifying system
boundaries and data domain.
There is no lack of internal
coding and their knowledge
(Diebe and et.al., 2020)
Tester have
knowledge of coding
which easily
validating data and
overall internal
system (Bian and
et.al., 2020).
Black box testing is
not considered
algorithm.
It is well suitable and
recommended for
using algorithm in
It is not used for
algorithm testing.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

testing purpose.
Table:1
Describe about Statutory and Ethical considerations of penetration tester.
Ethics within penetrating testing is becoming potentially confusing aspects which often
used interchangeably with hacking. Although, it is clearly validating the label and referring to
ethical hacking. Which are sems that uncomfortable in system application. It is helping for
expose security weakness, implemented defend action by claiming (Lin, Wang and Li, 2020). In
this way, it might be clearly intended professional interpretation that will not easy to justify the
Vulnerabilities, threats within system. In regardless, Penetration testing is clearly making
valuable contribution to the system in both network as well as physical security.
Penetration testers are mainly expected to make inform decision on the basis of
understanding, situation by ethical. The tester attack system is to evaluate their security aspects
in face of realistic threats. it also added constraints that exploiting and finding vulnerabilities. It
should be either harm overall system which affects on the dignity. In consideration, it is more
specific value of ethics which are undertaken by each position (Shiva, kumar, 2020). It is noted
that ethics as learned, interpersonal skills, it can easily tackle ethical hazards to client. While
penetration tester has more contextual knowledge which are necessarily know who can easily
handle the best deals. Sometimes, Tester may subscribe the perspective of ethical which
ambiguous because it helps for measured the legal norms during testing.
As per Statutory, Organization should be hired the Licensed penetration tester which are
successfully handle the challenges, threats in term of application security. It is the most effective
to test threats, malicious attacks. Furthermore, it is also demonstrating the skill which require to
conduct black box penetration testing (Trejos Zelaya, 2020). As per council, it mainly follows
the entire process which are performing different process such as scanning, gaining access,
enumeration, exploiting vulnerabilities that will seek out in the network. legal norm will provide
the entire cyber range which automatically secure or protect large amount of data within cloud
application.
5
Table:1
Describe about Statutory and Ethical considerations of penetration tester.
Ethics within penetrating testing is becoming potentially confusing aspects which often
used interchangeably with hacking. Although, it is clearly validating the label and referring to
ethical hacking. Which are sems that uncomfortable in system application. It is helping for
expose security weakness, implemented defend action by claiming (Lin, Wang and Li, 2020). In
this way, it might be clearly intended professional interpretation that will not easy to justify the
Vulnerabilities, threats within system. In regardless, Penetration testing is clearly making
valuable contribution to the system in both network as well as physical security.
Penetration testers are mainly expected to make inform decision on the basis of
understanding, situation by ethical. The tester attack system is to evaluate their security aspects
in face of realistic threats. it also added constraints that exploiting and finding vulnerabilities. It
should be either harm overall system which affects on the dignity. In consideration, it is more
specific value of ethics which are undertaken by each position (Shiva, kumar, 2020). It is noted
that ethics as learned, interpersonal skills, it can easily tackle ethical hazards to client. While
penetration tester has more contextual knowledge which are necessarily know who can easily
handle the best deals. Sometimes, Tester may subscribe the perspective of ethical which
ambiguous because it helps for measured the legal norms during testing.
As per Statutory, Organization should be hired the Licensed penetration tester which are
successfully handle the challenges, threats in term of application security. It is the most effective
to test threats, malicious attacks. Furthermore, it is also demonstrating the skill which require to
conduct black box penetration testing (Trejos Zelaya, 2020). As per council, it mainly follows
the entire process which are performing different process such as scanning, gaining access,
enumeration, exploiting vulnerabilities that will seek out in the network. legal norm will provide
the entire cyber range which automatically secure or protect large amount of data within cloud
application.
5
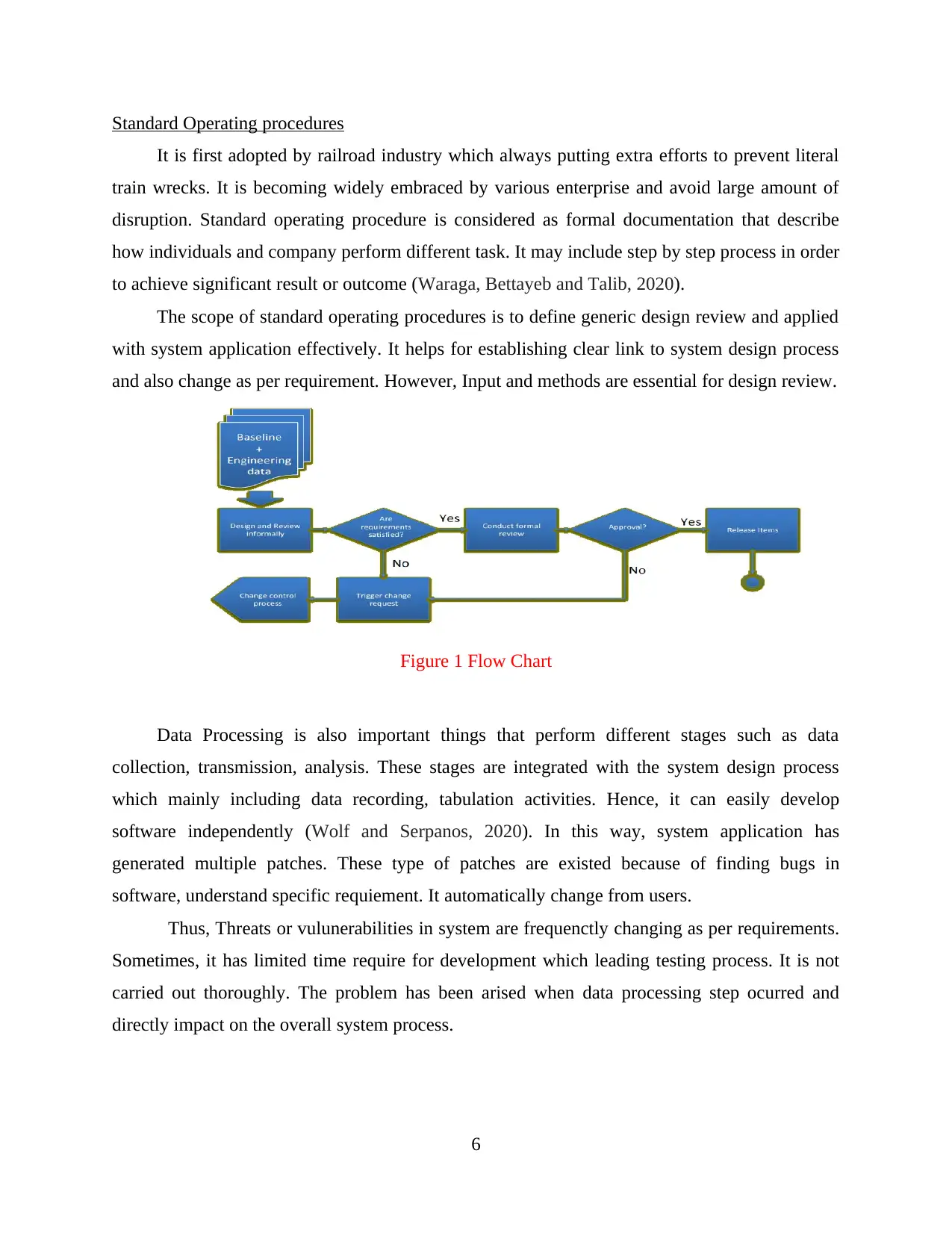
Standard Operating procedures
It is first adopted by railroad industry which always putting extra efforts to prevent literal
train wrecks. It is becoming widely embraced by various enterprise and avoid large amount of
disruption. Standard operating procedure is considered as formal documentation that describe
how individuals and company perform different task. It may include step by step process in order
to achieve significant result or outcome (Waraga, Bettayeb and Talib, 2020).
The scope of standard operating procedures is to define generic design review and applied
with system application effectively. It helps for establishing clear link to system design process
and also change as per requirement. However, Input and methods are essential for design review.
Figure 1 Flow Chart
Data Processing is also important things that perform different stages such as data
collection, transmission, analysis. These stages are integrated with the system design process
which mainly including data recording, tabulation activities. Hence, it can easily develop
software independently (Wolf and Serpanos, 2020). In this way, system application has
generated multiple patches. These type of patches are existed because of finding bugs in
software, understand specific requiement. It automatically change from users.
Thus, Threats or vulunerabilities in system are frequenctly changing as per requirements.
Sometimes, it has limited time require for development which leading testing process. It is not
carried out thoroughly. The problem has been arised when data processing step ocurred and
directly impact on the overall system process.
6
It is first adopted by railroad industry which always putting extra efforts to prevent literal
train wrecks. It is becoming widely embraced by various enterprise and avoid large amount of
disruption. Standard operating procedure is considered as formal documentation that describe
how individuals and company perform different task. It may include step by step process in order
to achieve significant result or outcome (Waraga, Bettayeb and Talib, 2020).
The scope of standard operating procedures is to define generic design review and applied
with system application effectively. It helps for establishing clear link to system design process
and also change as per requirement. However, Input and methods are essential for design review.
Figure 1 Flow Chart
Data Processing is also important things that perform different stages such as data
collection, transmission, analysis. These stages are integrated with the system design process
which mainly including data recording, tabulation activities. Hence, it can easily develop
software independently (Wolf and Serpanos, 2020). In this way, system application has
generated multiple patches. These type of patches are existed because of finding bugs in
software, understand specific requiement. It automatically change from users.
Thus, Threats or vulunerabilities in system are frequenctly changing as per requirements.
Sometimes, it has limited time require for development which leading testing process. It is not
carried out thoroughly. The problem has been arised when data processing step ocurred and
directly impact on the overall system process.
6

Figure 2 SOP
Standard operating procedure consits of secure document repository that allow for user to easily
retrive, search information. It is to considered the automatic routing and electronic distribution in
the overall system management. It can be identified the different features in the Standaard
operating procedures such as
Permissions for sharing
Control overall workflow process
Centrailised procedures
Decision-Making Tree
It is based on the tool which support for purpose of decision-making in system design. It
is possible consequence, including resource cost, event outcome and other utility (Bian and et.al.,
2020). It is one of most common algorithms that mainly contain conditional control statements.
This type of decision tree allows for operational research which specifying decision analysis,
help for identifying strategy. it is likely to reach on significant goals and objectives, but it is
popular in term of machine learning that’s why, many companies are used decision making tree
for design efficient system application which help for improving business performance and
efficiency.
Furthermore, Decision tree is becoming choice of management that analyse tree and
contain probabilities. In order to generate result or outcome (Waraga, Bettayeb and Talib, 2020).
This type of decision tree is identifying and organising condition or suitable action in the overall
7
Standard operating procedure consits of secure document repository that allow for user to easily
retrive, search information. It is to considered the automatic routing and electronic distribution in
the overall system management. It can be identified the different features in the Standaard
operating procedures such as
Permissions for sharing
Control overall workflow process
Centrailised procedures
Decision-Making Tree
It is based on the tool which support for purpose of decision-making in system design. It
is possible consequence, including resource cost, event outcome and other utility (Bian and et.al.,
2020). It is one of most common algorithms that mainly contain conditional control statements.
This type of decision tree allows for operational research which specifying decision analysis,
help for identifying strategy. it is likely to reach on significant goals and objectives, but it is
popular in term of machine learning that’s why, many companies are used decision making tree
for design efficient system application which help for improving business performance and
efficiency.
Furthermore, Decision tree is becoming choice of management that analyse tree and
contain probabilities. In order to generate result or outcome (Waraga, Bettayeb and Talib, 2020).
This type of decision tree is identifying and organising condition or suitable action in the overall
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

structure process. In this way, it easily distinguishes between certain actions and condition
during decision tree. Especially, it relevant when condition as well as action take place over
period of time. For instances, it is primarily use square node which mainly indicate an action.
Sometimes, it helps for decision making through symmetrical structure that contain multiple
branches.
Intelligence Gathering
It is a type of network that gathered and collected large amount data through different
entities. It is the most suitable approach that can be related to source. Many industries are used
intelligence gathering network such as military, commercial and government intelligence. It
employs with analysis to refine, filter information. So, as it become easier to keep table on news
channel of different host nations. Sometimes, it cannot be divided into useful intelligence but
also indeed to increasing quality in term of digital media (Waraga, Bettayeb and Talib, 2020).
For Example- Many intelligence agencies are used different network system that usually follow
the linear rather than other type of distributed structure. The person within agencies are
coordinated and collecting large amount of facts, figures. In this way, it can easily target the
operations that performed outside.
The information is to be gathered and processed by multiple testers which directly turned
into intelligence item. The information may convey between one node to another in network
system. there are various types of secure physical and electronic devices which always support to
hold large amount of data in proper manner (Bian and et.al., 2020). Although The publicly
available information that helping for identifying background purpose, generally the better way
to find out some threats within organization. If a person gathered information that will be used
the interest of firm, intention, plans, infrastructure and other type of capabilities.
Vulnerability identification and analysis
A vulnerability is a type of threat that occurs within system, often include penetrating
testing for identifying threat in the organization. it might not be detectable with system but
sometimes, it mainly refers the vulnerability approach through penetration testing. When
penetration testers exploit within project which is not enough. Client can understand the impact
of vulnerabilities in the existing business network environment (Bian and et.al., 2020). However,
risk is not enough to measure during penetrating testing project but it also evaluates inherent risk
to successful completion. In the organization, tester has made plan for analysis potential risk that
8
during decision tree. Especially, it relevant when condition as well as action take place over
period of time. For instances, it is primarily use square node which mainly indicate an action.
Sometimes, it helps for decision making through symmetrical structure that contain multiple
branches.
Intelligence Gathering
It is a type of network that gathered and collected large amount data through different
entities. It is the most suitable approach that can be related to source. Many industries are used
intelligence gathering network such as military, commercial and government intelligence. It
employs with analysis to refine, filter information. So, as it become easier to keep table on news
channel of different host nations. Sometimes, it cannot be divided into useful intelligence but
also indeed to increasing quality in term of digital media (Waraga, Bettayeb and Talib, 2020).
For Example- Many intelligence agencies are used different network system that usually follow
the linear rather than other type of distributed structure. The person within agencies are
coordinated and collecting large amount of facts, figures. In this way, it can easily target the
operations that performed outside.
The information is to be gathered and processed by multiple testers which directly turned
into intelligence item. The information may convey between one node to another in network
system. there are various types of secure physical and electronic devices which always support to
hold large amount of data in proper manner (Bian and et.al., 2020). Although The publicly
available information that helping for identifying background purpose, generally the better way
to find out some threats within organization. If a person gathered information that will be used
the interest of firm, intention, plans, infrastructure and other type of capabilities.
Vulnerability identification and analysis
A vulnerability is a type of threat that occurs within system, often include penetrating
testing for identifying threat in the organization. it might not be detectable with system but
sometimes, it mainly refers the vulnerability approach through penetration testing. When
penetration testers exploit within project which is not enough. Client can understand the impact
of vulnerabilities in the existing business network environment (Bian and et.al., 2020). However,
risk is not enough to measure during penetrating testing project but it also evaluates inherent risk
to successful completion. In the organization, tester has made plan for analysis potential risk that
8

affects overall functionality of system. although it should gather large amount of data through
plan and analyse information technology threats, what are different professional risk which
directly manage overall system. in this way, it can easily identify the risk metrics by using
penetrating testing.
In this way, it can be determined the activity to identify the potential vulnerabilities
which assets to be leveraged by source of threat. Afterwards, it will be recorded the output of
activities in the form of listing. Sometimes, it has analysed that two possible approach take place
either for listing vulnerabilities. Penetration testing is properly analysing all security aspects and
adopting them (Waraga, Bettayeb and Talib, 2020). On the other hand, Penetration testing is a
type of ethical hacking which is known as pen testing. It provides facility of tester to include
network, web application to discover threats, vulnerabilities. In most of cases, it could be
conducted through penetration testing which easily recognise the different areas. It might not be
detected in application system
Target exploitation
It is important phase within penetration testing which mainly focused on the establishing
access to system, resources. It useful for maintaining and controlling different security aspects.
In this phase, it can perform the significant plan which help for decision making. Another way, it
is also understanding main entry point into business and target the high assets (Waraga, Bettayeb
and Talib, 2020). If in case vulnerability phase has been completed in properly then it moves
towards high value target, exploit to compiled with attackers.
Unlikely it should take consideration of success parameter which increasing productivity
and profitability of organization in marketplace. The exploit in the system typically carried out
the pay load and deliver to system target. It is commonly control buffer overflow (Bian and et.al.,
2020).
CONCLUSION
From above discussion, it concluded that Penetration is a type of process which mainly used
for vulnerabilities identification. It has summarised about the different type of penetration testing
methodologies that will support for identifying threats. It is also considered the statutory and
ethical considerations for improving moral values. Penetration techniques methodologies, which
help for analysing and gathering vulnerabilities such as decision-making tree. Furthermore, it is
increasing cyber-attack, many companies that start on performing various security testing on
9
plan and analyse information technology threats, what are different professional risk which
directly manage overall system. in this way, it can easily identify the risk metrics by using
penetrating testing.
In this way, it can be determined the activity to identify the potential vulnerabilities
which assets to be leveraged by source of threat. Afterwards, it will be recorded the output of
activities in the form of listing. Sometimes, it has analysed that two possible approach take place
either for listing vulnerabilities. Penetration testing is properly analysing all security aspects and
adopting them (Waraga, Bettayeb and Talib, 2020). On the other hand, Penetration testing is a
type of ethical hacking which is known as pen testing. It provides facility of tester to include
network, web application to discover threats, vulnerabilities. In most of cases, it could be
conducted through penetration testing which easily recognise the different areas. It might not be
detected in application system
Target exploitation
It is important phase within penetration testing which mainly focused on the establishing
access to system, resources. It useful for maintaining and controlling different security aspects.
In this phase, it can perform the significant plan which help for decision making. Another way, it
is also understanding main entry point into business and target the high assets (Waraga, Bettayeb
and Talib, 2020). If in case vulnerability phase has been completed in properly then it moves
towards high value target, exploit to compiled with attackers.
Unlikely it should take consideration of success parameter which increasing productivity
and profitability of organization in marketplace. The exploit in the system typically carried out
the pay load and deliver to system target. It is commonly control buffer overflow (Bian and et.al.,
2020).
CONCLUSION
From above discussion, it concluded that Penetration is a type of process which mainly used
for vulnerabilities identification. It has summarised about the different type of penetration testing
methodologies that will support for identifying threats. It is also considered the statutory and
ethical considerations for improving moral values. Penetration techniques methodologies, which
help for analysing and gathering vulnerabilities such as decision-making tree. Furthermore, it is
increasing cyber-attack, many companies that start on performing various security testing on
9

their software application. Penetration testing is the most common for identifying the vulnerable
area of system. Sometimes, it may include wilful attacks on the application system for
eliminating threats within system. it also protects or secure through malicious attack and
unauthorised user access.
10
area of system. Sometimes, it may include wilful attacks on the application system for
eliminating threats within system. it also protects or secure through malicious attack and
unauthorised user access.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

REFERENCES
Book and Journals
Bian, Y. and et.al., 2020. Design, Fabrication and Measurement of Heat Sink with Microchannel
Cold Frame for Electronics Cooling. In Proceedings of the Seventh Asia International
Symposium on Mechatronics (pp. 436-444). Springer, Singapore.
Boussahaba, H. and et.al., 2020, January. New and Advanced PDC Bit Design with Innovative
Backup Layout Cutters Helps Extend Bit Life without Sacrificing Rate of Penetration
During a Heterogeneous Application, Northwest Kuwait. In International Petroleum
Technology Conference. International Petroleum Technology Conference.
Dieber, B. and et.al., 2020. Penetration testing ROS. In Robot Operating System (ROS) (pp. 183-
225). Springer, Cham.
Lin, L., Wang, L. and Li, H., 2020, January. Design of Quality Management and Inspection
Platform for Industrial Control Integration Based on AI. In Journal of Physics:
Conference Series (Vol. 1437, No. 1, p. 012097). IOP Publishing.
Shivakumar, S.K., 2020. Digital Workplace Testing. In Build a Next-Generation Digital
Workplace (pp. 143-171). Apress, Berkeley, CA.
Trejos-Zelaya, I., 2020. Developing Software Quality and Testing Capabilities in Hispanic
America: Challenges and Prospects. In The Future of Software Quality Assurance (pp.
175-196). Springer, Cham.
Waraga, O.A., Bettayeb, M. and Talib, M.A., 2020. Design and implementation of automated
IoT security testbed. Computers & Security, 88, p.101648.
Wolf, M. and Serpanos, D., 2020. Threats and Threat Analysis. In Safe and Secure Cyber-
Physical Systems and Internet-of-Things Systems (pp. 35-45). Springer, Cham.
11
Book and Journals
Bian, Y. and et.al., 2020. Design, Fabrication and Measurement of Heat Sink with Microchannel
Cold Frame for Electronics Cooling. In Proceedings of the Seventh Asia International
Symposium on Mechatronics (pp. 436-444). Springer, Singapore.
Boussahaba, H. and et.al., 2020, January. New and Advanced PDC Bit Design with Innovative
Backup Layout Cutters Helps Extend Bit Life without Sacrificing Rate of Penetration
During a Heterogeneous Application, Northwest Kuwait. In International Petroleum
Technology Conference. International Petroleum Technology Conference.
Dieber, B. and et.al., 2020. Penetration testing ROS. In Robot Operating System (ROS) (pp. 183-
225). Springer, Cham.
Lin, L., Wang, L. and Li, H., 2020, January. Design of Quality Management and Inspection
Platform for Industrial Control Integration Based on AI. In Journal of Physics:
Conference Series (Vol. 1437, No. 1, p. 012097). IOP Publishing.
Shivakumar, S.K., 2020. Digital Workplace Testing. In Build a Next-Generation Digital
Workplace (pp. 143-171). Apress, Berkeley, CA.
Trejos-Zelaya, I., 2020. Developing Software Quality and Testing Capabilities in Hispanic
America: Challenges and Prospects. In The Future of Software Quality Assurance (pp.
175-196). Springer, Cham.
Waraga, O.A., Bettayeb, M. and Talib, M.A., 2020. Design and implementation of automated
IoT security testbed. Computers & Security, 88, p.101648.
Wolf, M. and Serpanos, D., 2020. Threats and Threat Analysis. In Safe and Secure Cyber-
Physical Systems and Internet-of-Things Systems (pp. 35-45). Springer, Cham.
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





