Standard Operating Procedure for Penetration Testing
VerifiedAdded on 2023/06/03
|11
|1708
|256
AI Summary
This report discusses different methodologies for penetration testing and provides a standard operating procedure for the process. It also includes a decision tree analysis for penetration testing.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: STANDARD OPERATING PROCEDURE FOR PEN TESTING
Standard Operating Procedure for Pen Testing
Name of the Student
Name of the University
Authors note
Standard Operating Procedure for Pen Testing
Name of the Student
Name of the University
Authors note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1STANDARD OPERATING PROCEDURE FOR PEN TESTING
Table of Contents
1. Introduction..........................................................................................................2
2. Pen Testing Methodologies..................................................................................2
3. Best SOP..............................................................................................................5
4. Decision Tree Analysis for Penetration Testing..................................................6
5. Conclusions..........................................................................................................7
References......................................................................................................................8
Appendix......................................................................................................................10
Table of Contents
1. Introduction..........................................................................................................2
2. Pen Testing Methodologies..................................................................................2
3. Best SOP..............................................................................................................5
4. Decision Tree Analysis for Penetration Testing..................................................6
5. Conclusions..........................................................................................................7
References......................................................................................................................8
Appendix......................................................................................................................10

2STANDARD OPERATING PROCEDURE FOR PEN TESTING
1. Introduction
The Penetration testing process includes different automated as well as manual
techniques in order to simulate security exploiting attack on an organisation’s network and
information systems (Stefinko, Piskozub and Banakh 2016). This type of attack is used to
look out for the different known as well as unknown vulnerabilities that needs to be addresses
in order to secure the network. Carrying out pen testing is important to exploit vulnerabilities
in order to patch them so that in future it becomes hard to have unauthorized access by the
hackers or intruders. In order to carry out the pen test on some organizations network and
information system there are multiple techniques that can be used some of them are listed as;
Mobile application penetration testing
legacy application or the Client server architecture based application
penetration testing
Device based pen testing through workstations, laptops and other devices
(smartphones and tablets) penetration testing.
Wireless access point penetration testing.
This report focuses on the discussion about different methodologies that can be used
with the target of detecting the flaws of the existing architecture and application
configuration. In addition to that, the report also consists of discussion about the standard
operating procedure for penetration testing process to find out the vulnerabilities.
2. Pen Testing Methodologies
There are mainly following types of the methodologies are available and used by the
professionals which are listed below;
1. Introduction
The Penetration testing process includes different automated as well as manual
techniques in order to simulate security exploiting attack on an organisation’s network and
information systems (Stefinko, Piskozub and Banakh 2016). This type of attack is used to
look out for the different known as well as unknown vulnerabilities that needs to be addresses
in order to secure the network. Carrying out pen testing is important to exploit vulnerabilities
in order to patch them so that in future it becomes hard to have unauthorized access by the
hackers or intruders. In order to carry out the pen test on some organizations network and
information system there are multiple techniques that can be used some of them are listed as;
Mobile application penetration testing
legacy application or the Client server architecture based application
penetration testing
Device based pen testing through workstations, laptops and other devices
(smartphones and tablets) penetration testing.
Wireless access point penetration testing.
This report focuses on the discussion about different methodologies that can be used
with the target of detecting the flaws of the existing architecture and application
configuration. In addition to that, the report also consists of discussion about the standard
operating procedure for penetration testing process to find out the vulnerabilities.
2. Pen Testing Methodologies
There are mainly following types of the methodologies are available and used by the
professionals which are listed below;

3STANDARD OPERATING PROCEDURE FOR PEN TESTING
NIST 800-115
ISSAF (Information Systems Security Assessment Framework)
OWASP penetration testing guide
PCI Penetration testing guide
Penetration Testing Framework
Penetration Testing Execution Standard
OSSTMM (Open Source Security Testing Methodology Manual)
The NIST 800-115 is one of the methodologies that are considered as standard which
provides clearly defined security assessment in order determine the way an entity effectively
being assessed that needs to meets specific security requirements to make a robust
organizational network and information system (Lunne, Powell and Robertson 2014). This
methodology reviews the logs of the different services and Systems for authentication server
logs which may comprise successful / failed authentication attempts.
The PTES methodology includes the following stages;
Pre-engagement Interactions
Intelligence Gathering
Threat Modeling
Vulnerability Analysis
Exploitation
Post Exploitation
Reporting
NIST 800-115
ISSAF (Information Systems Security Assessment Framework)
OWASP penetration testing guide
PCI Penetration testing guide
Penetration Testing Framework
Penetration Testing Execution Standard
OSSTMM (Open Source Security Testing Methodology Manual)
The NIST 800-115 is one of the methodologies that are considered as standard which
provides clearly defined security assessment in order determine the way an entity effectively
being assessed that needs to meets specific security requirements to make a robust
organizational network and information system (Lunne, Powell and Robertson 2014). This
methodology reviews the logs of the different services and Systems for authentication server
logs which may comprise successful / failed authentication attempts.
The PTES methodology includes the following stages;
Pre-engagement Interactions
Intelligence Gathering
Threat Modeling
Vulnerability Analysis
Exploitation
Post Exploitation
Reporting
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4STANDARD OPERATING PROCEDURE FOR PEN TESTING
The PCI Penetration testing guide is related to the Payment Card Industry Data
Security and is a Standard for maintain security for the different card based data transactions.
The Penetration testing Framework is that provides a comprehensive and detailed
guide for penetration testing process. Such as use of tools and different consecutive stages;
Network Footprinting
Discovery & Probing
Enumeration
Password cracking
Vulnerability Assessment
AS/400 Auditing
Bluetooth Specific Testing
Network Backbone testing
Server Specific Tests
VoIP Security tests
Wireless Penetration testing
Physical Security testing
Final Report presentation
Another methodology is OSSTMM. This methodology is important in order to test the
operational security of workflow, wireless security testing, telecommunication security
The PCI Penetration testing guide is related to the Payment Card Industry Data
Security and is a Standard for maintain security for the different card based data transactions.
The Penetration testing Framework is that provides a comprehensive and detailed
guide for penetration testing process. Such as use of tools and different consecutive stages;
Network Footprinting
Discovery & Probing
Enumeration
Password cracking
Vulnerability Assessment
AS/400 Auditing
Bluetooth Specific Testing
Network Backbone testing
Server Specific Tests
VoIP Security tests
Wireless Penetration testing
Physical Security testing
Final Report presentation
Another methodology is OSSTMM. This methodology is important in order to test the
operational security of workflow, wireless security testing, telecommunication security

5STANDARD OPERATING PROCEDURE FOR PEN TESTING
testing, human security testing physical locations, physical security testing, data networks
security testing as well as compliance with different standards.
3. Best SOP
The PTES can be considered as the best SOP for carrying out a penetration
technique for a penetration test of a network or application. Vulnerability or the penetration
testing includes stages from initial communication for social engineering in order to
information gathering to the threat modelling phase (Stefinko, Piskozub and Banakh 2016).
All this stages involves the pen testers to understand the organization. According to the
PTES framework a penetration testing model consists of following seven phases.
Pre-engagement Interactions
Intelligence Gathering (for gathering information of the network or application)
Threat Modelling (identification of the potential threats for the targeted system. Then
they are enumerated as well as prioritized for use in the exploitation stage.)
Vulnerability Analysis (Validation of the identified vulnerabilities)
Exploitation (Exploitation of the prioritized and validated Vulnerabilities)
Post Exploitation.
Reporting (presenting the loopholes of the system in a report format to the
management of the organization. ( Lunne, Powell and Robertson 2014))
The exploitation method starts with search of the publicly available information
sources of targeted network such as utilization of the automated dialling tools, accessibility of
poorly configured modems inside the targeted networks, committed host computers in the
targeted infrastructure and so on (Knowles, Baron and McGarr 2015). Moreover, it is also
testing, human security testing physical locations, physical security testing, data networks
security testing as well as compliance with different standards.
3. Best SOP
The PTES can be considered as the best SOP for carrying out a penetration
technique for a penetration test of a network or application. Vulnerability or the penetration
testing includes stages from initial communication for social engineering in order to
information gathering to the threat modelling phase (Stefinko, Piskozub and Banakh 2016).
All this stages involves the pen testers to understand the organization. According to the
PTES framework a penetration testing model consists of following seven phases.
Pre-engagement Interactions
Intelligence Gathering (for gathering information of the network or application)
Threat Modelling (identification of the potential threats for the targeted system. Then
they are enumerated as well as prioritized for use in the exploitation stage.)
Vulnerability Analysis (Validation of the identified vulnerabilities)
Exploitation (Exploitation of the prioritized and validated Vulnerabilities)
Post Exploitation.
Reporting (presenting the loopholes of the system in a report format to the
management of the organization. ( Lunne, Powell and Robertson 2014))
The exploitation method starts with search of the publicly available information
sources of targeted network such as utilization of the automated dialling tools, accessibility of
poorly configured modems inside the targeted networks, committed host computers in the
targeted infrastructure and so on (Knowles, Baron and McGarr 2015). Moreover, it is also

6STANDARD OPERATING PROCEDURE FOR PEN TESTING
possible to use external testing tools for finding and assessing the vulnerabilities through the
defined subset of the points of access to the network.
In the post exploitation phase the breached (compromised) system or applications
value is determined by the sensitivity of the data in it.
Although there are a large number of Penetration Testing Tools that are accessible for
utilize, the decision to empower one should in a perfect world leave the straightforwardness
to send, design and utilize the equivalent. It is to be remembered that the instruments should
philosophies that encourages vulnerabilities to be sorted dependent on seriousness that
necessities prompt fix. It ought to likewise be noticed that Penetration Testing instruments
ought to enable mechanized confirmation of vulnerabilities to spare time and lessen human
mistakes.
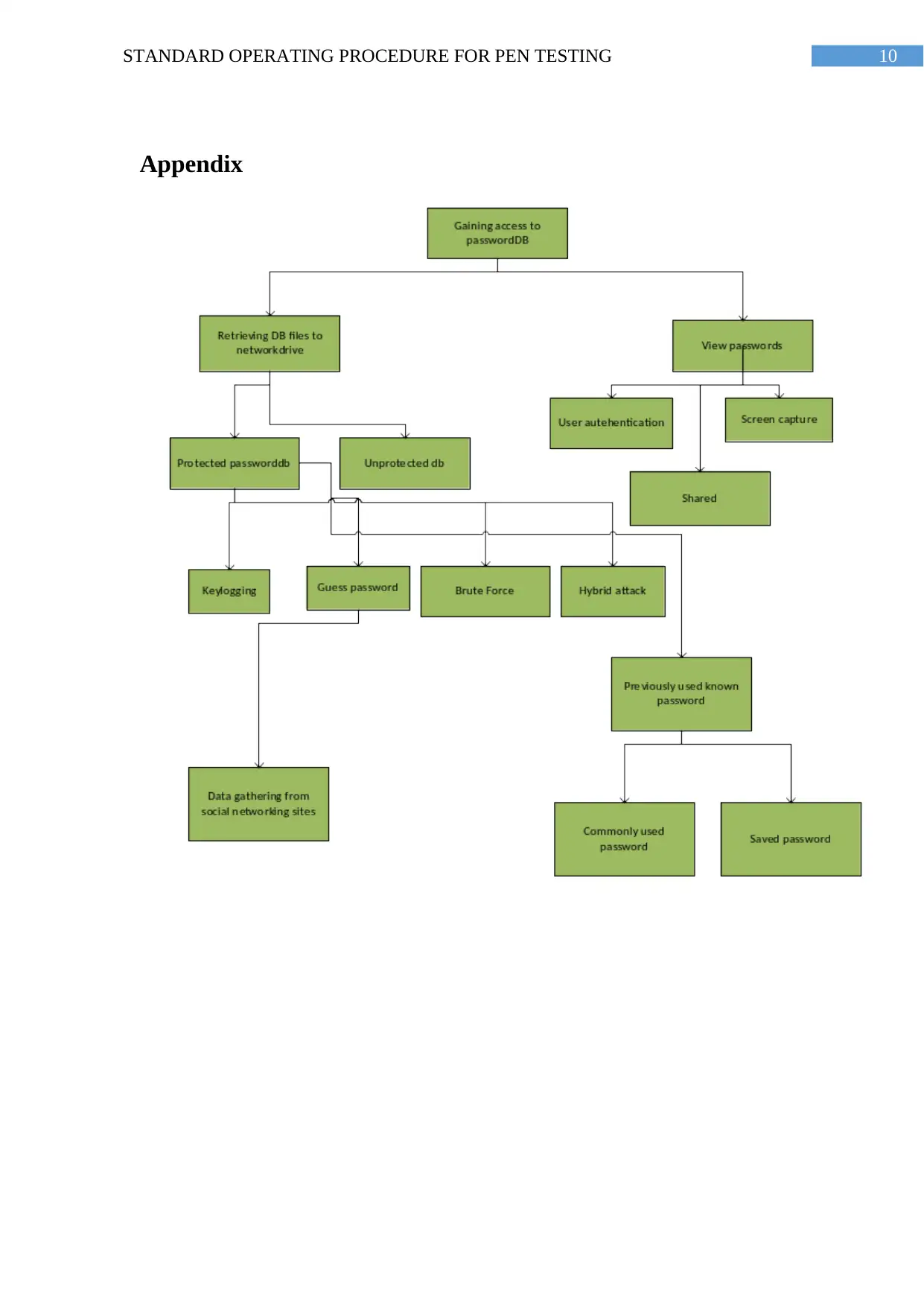
4. Decision Tree Analysis for Penetration Testing
The different stages of the Penetration testing are an imperative subject that IT
administrators or attackers ought to know about. With the increased accessibility to the
internet each day, the security of the networks d has turned into an extremely difficult subject
not just for the organizations yet in addition for consistent clients. Open source testing tools
can be concurring individual needs (Stefinko, Piskozub and Banakh 2016). Following is the
Decision tree format for the selected Standard operating procedure for the penetration testing
process.
For any pen testing attack the decision tree gives a perception of various aspects
which can be utilized to pick up access to a safe (Lunne, Powell and Robertson 2014). The
tree is additionally separated with numerous varieties appearing conceivable and
possible to use external testing tools for finding and assessing the vulnerabilities through the
defined subset of the points of access to the network.
In the post exploitation phase the breached (compromised) system or applications
value is determined by the sensitivity of the data in it.
Although there are a large number of Penetration Testing Tools that are accessible for
utilize, the decision to empower one should in a perfect world leave the straightforwardness
to send, design and utilize the equivalent. It is to be remembered that the instruments should
philosophies that encourages vulnerabilities to be sorted dependent on seriousness that
necessities prompt fix. It ought to likewise be noticed that Penetration Testing instruments
ought to enable mechanized confirmation of vulnerabilities to spare time and lessen human
mistakes.
4. Decision Tree Analysis for Penetration Testing
The different stages of the Penetration testing are an imperative subject that IT
administrators or attackers ought to know about. With the increased accessibility to the
internet each day, the security of the networks d has turned into an extremely difficult subject
not just for the organizations yet in addition for consistent clients. Open source testing tools
can be concurring individual needs (Stefinko, Piskozub and Banakh 2016). Following is the
Decision tree format for the selected Standard operating procedure for the penetration testing
process.
For any pen testing attack the decision tree gives a perception of various aspects
which can be utilized to pick up access to a safe (Lunne, Powell and Robertson 2014). The
tree is additionally separated with numerous varieties appearing conceivable and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7STANDARD OPERATING PROCEDURE FOR PEN TESTING
inconceivable vulnerabilities, cost of playing out an attack inside an organizational network
and different minor departure from the same subject.
Each attack tree exhibits a point of view of the intruder’s target or root hub. The
intruder is typically centred around a nearby issue when characterizing the decision tree for
an attack (Knowles, Baron and McGarr 2015). The models inn appendix gives a decent
delegate review to a nonexclusive safe. In any case, more points of interest must be known,
before the tree can be utilized to plan security for a particular safe.
5. Conclusions
Penetration testing is considered as the oldest as well as effective methods that helps
in assessment of the security of the systems used by the organizations. This helps the
organizations to measure the extent until which the data needs to be secure in the network so
that the organization can improve the performance in order to prevent the infiltration to the
data because of the possible breach. Pentest can be an important tool for the organizations
and agencies in monitoring potential threats.
inconceivable vulnerabilities, cost of playing out an attack inside an organizational network
and different minor departure from the same subject.
Each attack tree exhibits a point of view of the intruder’s target or root hub. The
intruder is typically centred around a nearby issue when characterizing the decision tree for
an attack (Knowles, Baron and McGarr 2015). The models inn appendix gives a decent
delegate review to a nonexclusive safe. In any case, more points of interest must be known,
before the tree can be utilized to plan security for a particular safe.
5. Conclusions
Penetration testing is considered as the oldest as well as effective methods that helps
in assessment of the security of the systems used by the organizations. This helps the
organizations to measure the extent until which the data needs to be secure in the network so
that the organization can improve the performance in order to prevent the infiltration to the
data because of the possible breach. Pentest can be an important tool for the organizations
and agencies in monitoring potential threats.

8STANDARD OPERATING PROCEDURE FOR PEN TESTING
References
Brandt, D.D., Hall, K., Anderson, M.B., Anderson, C.D. and Collins, G.B., Rockwell
Automation Technologies Inc, 2014. System and methodology providing automation security
analysis, validation, and learning in an industrial controller environment. U.S. Patent
8,909,926.
Khaitan, S.K. and McCalley, J.D., 2015. Design techniques and applications of cyberphysical
systems: A survey. IEEE Systems Journal, 9(2), pp.350-365.
Knowles, W., Baron, A. and McGarr, T., 2015. Analysis and recommendations for
standardisation in penetration testing and vulnerability assessment: penetration testing market
survey.
Lunne, T., Powell, J.J. and Robertson, P.K., 2014. Cone penetration testing in geotechnical
practice. CRC Press.
Milenkoski, A., Vieira, M., Kounev, S., Avritzer, A. and Payne, B.D., 2015. Evaluating
computer intrusion detection systems: A survey of common practices. ACM Computing
Surveys (CSUR), 48(1), p.12.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated
penetration testing. Benefits and drawbacks. Modern tendency. In Modern Problems of Radio
Engineering. Telecommunications and Computer Science (TCSET), 2016 13th International
Conference on (pp. 488-491). IEEE.
Uner, E.R., Kobrinetz, A., Singer, M.H., Matthews, J.S. and Leslie, B.J., Redwall
Technologies, LLC, 2016. Systems and methods for enhanced security in wireless
communication. U.S. Patent 9,514,300.
References
Brandt, D.D., Hall, K., Anderson, M.B., Anderson, C.D. and Collins, G.B., Rockwell
Automation Technologies Inc, 2014. System and methodology providing automation security
analysis, validation, and learning in an industrial controller environment. U.S. Patent
8,909,926.
Khaitan, S.K. and McCalley, J.D., 2015. Design techniques and applications of cyberphysical
systems: A survey. IEEE Systems Journal, 9(2), pp.350-365.
Knowles, W., Baron, A. and McGarr, T., 2015. Analysis and recommendations for
standardisation in penetration testing and vulnerability assessment: penetration testing market
survey.
Lunne, T., Powell, J.J. and Robertson, P.K., 2014. Cone penetration testing in geotechnical
practice. CRC Press.
Milenkoski, A., Vieira, M., Kounev, S., Avritzer, A. and Payne, B.D., 2015. Evaluating
computer intrusion detection systems: A survey of common practices. ACM Computing
Surveys (CSUR), 48(1), p.12.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated
penetration testing. Benefits and drawbacks. Modern tendency. In Modern Problems of Radio
Engineering. Telecommunications and Computer Science (TCSET), 2016 13th International
Conference on (pp. 488-491). IEEE.
Uner, E.R., Kobrinetz, A., Singer, M.H., Matthews, J.S. and Leslie, B.J., Redwall
Technologies, LLC, 2016. Systems and methods for enhanced security in wireless
communication. U.S. Patent 9,514,300.

9STANDARD OPERATING PROCEDURE FOR PEN TESTING
Amalfitano, D., Amatucci, N., Memon, A.M., Tramontana, P. and Fasolino, A.R., 2017. A
general framework for comparing automatic testing techniques of Android mobile
apps. Journal of Systems and Software, 125, pp.322-343.
Amalfitano, D., Amatucci, N., Memon, A.M., Tramontana, P. and Fasolino, A.R., 2017. A
general framework for comparing automatic testing techniques of Android mobile
apps. Journal of Systems and Software, 125, pp.322-343.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10STANDARD OPERATING PROCEDURE FOR PEN TESTING
Appendix
Appendix
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





