A Comparative Analysis: Penetration Testing Methodologies and Ethics
VerifiedAdded on 2022/08/22
|10
|2053
|53
Report
AI Summary
This report provides a comprehensive overview of penetration testing, exploring various methodologies such as OSSTMM, OWASP, NIST, PTES, and ISSAF, and their respective strengths and weaknesses in identifying network vulnerabilities. It delves into the ethical considerations surrounding penetration testing, emphasizing the crucial role of ethical hackers and the importance of legal compliance to protect both clients and testers. The report highlights the potential legal and ethical issues that can arise during penetration testing, such as data security and privacy concerns. It also examines the balance between the legality and ethicality of penetration testing activities, concluding that adhering to legal procedures is essential for ethical practice. The report underscores the significance of ethical considerations in cybersecurity and the need for careful selection and management of penetration testers. This report, along with other solved assignments and past papers, is available on Desklib, a platform dedicated to providing AI-based study tools for students.

Running head: PENETRATION TESTING AND ITS ETHICAL CONSIDERATION
PENETRATION TESTING
AND
ITS ETHICAL CONSIDERATION
Name of the Student
Name of the University
Author Note:
PENETRATION TESTING
AND
ITS ETHICAL CONSIDERATION
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PENETRATION TESTING
Penetration testing methodology-
Penetration testing is such practice that is also known as pen test which is applied with
the purpose to check the vulnerabilities as well as to determine the presence of cyber-attacks. Pen
testing operations takes place by breaching any system. While analyzing the operations and
results of the pen testing it is observed that the findings of the pen testing can vary according to
the standards and methodologies as there are several methodologies present for penetration
testing that includes OSSTMM, OWASP, NIST, PTES and ISSAF (Mehta, Raj and Singh 2018).
Thus, a detailed comparison of these identified pen test methodologies and their standards are
mentioned below:-
OSSTMM-
OSSTMM is one of the popular pen testing standard present in the cyber security industry
that is highly effective for analyzing the vulnerabilities. While analyzing this concern it is
observed that this method is highly effective for determining the network security vulnerabilities
by utilizing the experience and the knowledge of the tester. Along with the above mentioned
capabilities the human intelligence is also very essential in this method for determining the
network vulnerabilities. OSSTMM stands for open source security testing methodology manual
that permits the tester to modify the testing the procedure according to the requirement as well as
according to the technical specification of the network (Giuseppi et al., 2019).
Compared to the other penetration testing methods OSSTMM is one of the most effective
pen testing standard as during the testing process it is followed by a set of rules in order to
determine the gap between the security of the organizational network. Along with this method
has targeted to enhance the computing environment for virtualization, cloud computing as well
Penetration testing methodology-
Penetration testing is such practice that is also known as pen test which is applied with
the purpose to check the vulnerabilities as well as to determine the presence of cyber-attacks. Pen
testing operations takes place by breaching any system. While analyzing the operations and
results of the pen testing it is observed that the findings of the pen testing can vary according to
the standards and methodologies as there are several methodologies present for penetration
testing that includes OSSTMM, OWASP, NIST, PTES and ISSAF (Mehta, Raj and Singh 2018).
Thus, a detailed comparison of these identified pen test methodologies and their standards are
mentioned below:-
OSSTMM-
OSSTMM is one of the popular pen testing standard present in the cyber security industry
that is highly effective for analyzing the vulnerabilities. While analyzing this concern it is
observed that this method is highly effective for determining the network security vulnerabilities
by utilizing the experience and the knowledge of the tester. Along with the above mentioned
capabilities the human intelligence is also very essential in this method for determining the
network vulnerabilities. OSSTMM stands for open source security testing methodology manual
that permits the tester to modify the testing the procedure according to the requirement as well as
according to the technical specification of the network (Giuseppi et al., 2019).
Compared to the other penetration testing methods OSSTMM is one of the most effective
pen testing standard as during the testing process it is followed by a set of rules in order to
determine the gap between the security of the organizational network. Along with this method
has targeted to enhance the computing environment for virtualization, cloud computing as well

2PENETRATION TESTING
as for remote operations. During the analysis it primarily include human channels, wireless
channels, telecom as well as network channel.
OWASP-
OWASP stands for an Open Web Application Security Project which is also one of the
most effective pen testing methodology. This method is highly effective for its investigation
capabilities of security vulnerabilities that is present in the mobile and web applications (de
Jiménez 2016). Along with these features of OWASP it is identified that the utilization of this
method will help the tester to effectively investigate the critical impact of the cyber threats that
will ensure that the organization become more equipped and improve their security. During this
pen testing procedure the organization will get an effective recommendation for securing the
system and the network server of the organization (Gil, Baquero and Hernández 2018).
NIST-
Apart from the other methodologies it is identified that The National Institute of Standard
and Technology (NIST) will majorly impact the procedure of the penetration testing with the
purpose to enhance the cyber security for the specific organization. While analyzing the
effectiveness of this framework it is identified that the adoption of NIST will effectively improve
the security for small as well as large industries. In order to establish the NIST framework into
the organizational network it is very essential to perform penetration testing followed by a pre-
recognized guidelines.
PTES-
PTES stands for Penetration Testing Methodologies and Standards that is also one of the
most effective pen testing structure. Following this structure the tester will be able to get a detail
as for remote operations. During the analysis it primarily include human channels, wireless
channels, telecom as well as network channel.
OWASP-
OWASP stands for an Open Web Application Security Project which is also one of the
most effective pen testing methodology. This method is highly effective for its investigation
capabilities of security vulnerabilities that is present in the mobile and web applications (de
Jiménez 2016). Along with these features of OWASP it is identified that the utilization of this
method will help the tester to effectively investigate the critical impact of the cyber threats that
will ensure that the organization become more equipped and improve their security. During this
pen testing procedure the organization will get an effective recommendation for securing the
system and the network server of the organization (Gil, Baquero and Hernández 2018).
NIST-
Apart from the other methodologies it is identified that The National Institute of Standard
and Technology (NIST) will majorly impact the procedure of the penetration testing with the
purpose to enhance the cyber security for the specific organization. While analyzing the
effectiveness of this framework it is identified that the adoption of NIST will effectively improve
the security for small as well as large industries. In order to establish the NIST framework into
the organizational network it is very essential to perform penetration testing followed by a pre-
recognized guidelines.
PTES-
PTES stands for Penetration Testing Methodologies and Standards that is also one of the
most effective pen testing structure. Following this structure the tester will be able to get a detail
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PENETRATION TESTING
information about the steps of penetration testing as well as the procedure of communication,
data gathering and about other phases.
While analyzing this aspect it is identified that in this methodology the tester will get a
detailed guideline for effectively analyzing the technical context of the organizational network as
well as to analyze the vulnerabilities of the network server.
ISSAF-
ISSAF stands for the information system security assessment framework which is one of
the well-structured procedure of testing. Considering this aspect it is identified that there are
several organization present which required customized solution for their organization, here
ISSAF will be very effective as this guides the tester based on the personalized findings.
Followed by a detail analysis on the operations of this standard it is identified that it provides
most effective investigation feature as well as effective recommendation that will help to reduce
the impact of the cyber-attacks (Al Shebli and Beheshti 2018).
information about the steps of penetration testing as well as the procedure of communication,
data gathering and about other phases.
While analyzing this aspect it is identified that in this methodology the tester will get a
detailed guideline for effectively analyzing the technical context of the organizational network as
well as to analyze the vulnerabilities of the network server.
ISSAF-
ISSAF stands for the information system security assessment framework which is one of
the well-structured procedure of testing. Considering this aspect it is identified that there are
several organization present which required customized solution for their organization, here
ISSAF will be very effective as this guides the tester based on the personalized findings.
Followed by a detail analysis on the operations of this standard it is identified that it provides
most effective investigation feature as well as effective recommendation that will help to reduce
the impact of the cyber-attacks (Al Shebli and Beheshti 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4PENETRATION TESTING
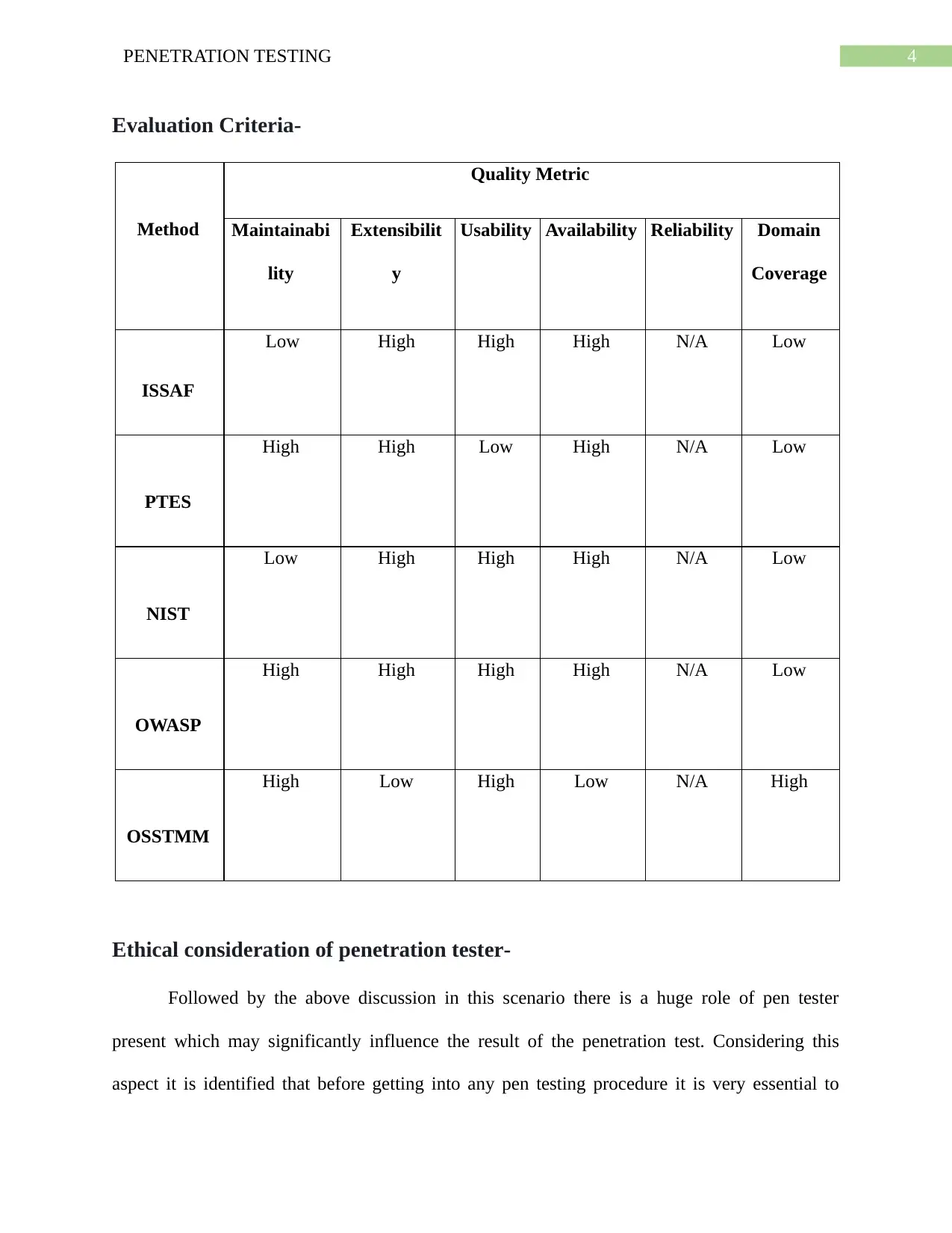
Evaluation Criteria-
Method
Quality Metric
Maintainabi
lity
Extensibilit
y
Usability Availability Reliability Domain
Coverage
ISSAF
Low High High High N/A Low
PTES
High High Low High N/A Low
NIST
Low High High High N/A Low
OWASP
High High High High N/A Low
OSSTMM
High Low High Low N/A High
Ethical consideration of penetration tester-
Followed by the above discussion in this scenario there is a huge role of pen tester
present which may significantly influence the result of the penetration test. Considering this
aspect it is identified that before getting into any pen testing procedure it is very essential to
Evaluation Criteria-
Method
Quality Metric
Maintainabi
lity
Extensibilit
y
Usability Availability Reliability Domain
Coverage
ISSAF
Low High High High N/A Low
PTES
High High Low High N/A Low
NIST
Low High High High N/A Low
OWASP
High High High High N/A Low
OSSTMM
High Low High Low N/A High
Ethical consideration of penetration tester-
Followed by the above discussion in this scenario there is a huge role of pen tester
present which may significantly influence the result of the penetration test. Considering this
aspect it is identified that before getting into any pen testing procedure it is very essential to

5PENETRATION TESTING
carefully appoint a pen tester for the testing activity. As the role of the pen tester includes the
identification of effective methodology, analyzing the systems of the organization, provide
security to the organizational data as well as to enhance the security of the organization based on
the findings of the vulnerabilities present in the organization (Kellezi, Boegelund and Meng
2019).
During these identification it is observed that in the field of pen testing there are several
factors present that influences the performance effectiveness of the pen tester. Those factors
includes the legal and ethical consideration of the pen tester. While analyzing the aspect of legal
consideration it is identified that pen testing always stands for the analysis of sensitive data of
organization or any individual. Thus, it is very essential to effectively verify the tester before
allowing them to analyze the sensitive data. Hence, in order to incorporate this for the pen tester
it is very essential to include legal compliance to regulate the activities of a pen tester. Making
allowance to this concern it is identified that there are few significant issues present that might
raise during the procedure of pen testing. Those issues includes that the fact that if the tester and
the client is not known to each other it is very difficult to give access of his personal data to an
unknown person.
Along with this it is also very prominent that during the pen testing activity there is not
guarantee of data security provided by the tester to its client which is also one of the most
harmful issue in pen testing. Considering these aspects it can be assumed that the tester might get
accused for stealing any client’s data as well. Hence, it is very essential to comply legal actions
before initiating any pen testing process as the legal benefit will show profits for both clients and
tester by supporting the activity of the tester as well as by protecting the data of the client
(Stefinko, Piskozub and Banakh 2016).
carefully appoint a pen tester for the testing activity. As the role of the pen tester includes the
identification of effective methodology, analyzing the systems of the organization, provide
security to the organizational data as well as to enhance the security of the organization based on
the findings of the vulnerabilities present in the organization (Kellezi, Boegelund and Meng
2019).
During these identification it is observed that in the field of pen testing there are several
factors present that influences the performance effectiveness of the pen tester. Those factors
includes the legal and ethical consideration of the pen tester. While analyzing the aspect of legal
consideration it is identified that pen testing always stands for the analysis of sensitive data of
organization or any individual. Thus, it is very essential to effectively verify the tester before
allowing them to analyze the sensitive data. Hence, in order to incorporate this for the pen tester
it is very essential to include legal compliance to regulate the activities of a pen tester. Making
allowance to this concern it is identified that there are few significant issues present that might
raise during the procedure of pen testing. Those issues includes that the fact that if the tester and
the client is not known to each other it is very difficult to give access of his personal data to an
unknown person.
Along with this it is also very prominent that during the pen testing activity there is not
guarantee of data security provided by the tester to its client which is also one of the most
harmful issue in pen testing. Considering these aspects it can be assumed that the tester might get
accused for stealing any client’s data as well. Hence, it is very essential to comply legal actions
before initiating any pen testing process as the legal benefit will show profits for both clients and
tester by supporting the activity of the tester as well as by protecting the data of the client
(Stefinko, Piskozub and Banakh 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PENETRATION TESTING
Apart from the above findings it is also very prominent that in order to conduct a pen
testing the pen tester primarily attacks the system of the client with the purpose to evaluate
threats and vulnerabilities. While analyzing this aspect based on the ethical consideration it is
identified that by considering the purpose of the pen testing it is legal however, while
considering the other aspects potentially it is very unethical. As it is mentioned earlier that pen
testing is popularly known as ethical hacking thus, it is identified that in the pen testing process it
legally breaks the computers privacy to get into privacy data of the client with the purpose to
determine vulnerabilities and threat that might significantly impact the data security of the client
(Satria et al., 2018).
While analyzing this concern from the view point of the tester it is identified that in the
field of pen testing the tester are getting a legal authority to get the access of their clients data
and investigate if there is any vulnerabilities are present or not. This process will help to identify
the threat present in any organizational structure before an attack takes place. Thus, it can be
stated that the activity of a pen tester will considered as ethical if the tester follows legal
procedure for pen testing.
Apart from the above findings it is also very prominent that in order to conduct a pen
testing the pen tester primarily attacks the system of the client with the purpose to evaluate
threats and vulnerabilities. While analyzing this aspect based on the ethical consideration it is
identified that by considering the purpose of the pen testing it is legal however, while
considering the other aspects potentially it is very unethical. As it is mentioned earlier that pen
testing is popularly known as ethical hacking thus, it is identified that in the pen testing process it
legally breaks the computers privacy to get into privacy data of the client with the purpose to
determine vulnerabilities and threat that might significantly impact the data security of the client
(Satria et al., 2018).
While analyzing this concern from the view point of the tester it is identified that in the
field of pen testing the tester are getting a legal authority to get the access of their clients data
and investigate if there is any vulnerabilities are present or not. This process will help to identify
the threat present in any organizational structure before an attack takes place. Thus, it can be
stated that the activity of a pen tester will considered as ethical if the tester follows legal
procedure for pen testing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PENETRATION TESTING
Reference:
Mehta, S., Raj, G. and Singh, D., 2018. Penetration Testing as a Test Phase in Web Service
Testing a Black Box Pen Testing Approach. In Smart Computing and Informatics (pp. 623-635).
Springer, Singapore.
Giuseppi, A., Tortorelli, A., Germanà, R., Liberati, F. and Fiaschetti, A., 2019, July. Securing
Cyber-Physical Systems: An Optimization Framework based on OSSTMM and Genetic
Algorithms. In 2019 27th Mediterranean Conference on Control and Automation (MED) (pp. 50-
56). IEEE.
Gil, C., Baquero, L. and Hernández, M., 2018. A Conceptual Exploration for the Safe
Development of Mobile Devices Software Based on OWASP. International Journal of Applied
Engineering Research, 13(18), pp.13603-13609.
Satria, D., Alanda, A., Erianda, A. and Prayama, D., 2018. Network Security Assessment Using
Internal Network Penetration Testing Methodology. JOIV: International Journal on Informatics
Visualization, 2(4-2), pp.360-365.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Reference:
Mehta, S., Raj, G. and Singh, D., 2018. Penetration Testing as a Test Phase in Web Service
Testing a Black Box Pen Testing Approach. In Smart Computing and Informatics (pp. 623-635).
Springer, Singapore.
Giuseppi, A., Tortorelli, A., Germanà, R., Liberati, F. and Fiaschetti, A., 2019, July. Securing
Cyber-Physical Systems: An Optimization Framework based on OSSTMM and Genetic
Algorithms. In 2019 27th Mediterranean Conference on Control and Automation (MED) (pp. 50-
56). IEEE.
Gil, C., Baquero, L. and Hernández, M., 2018. A Conceptual Exploration for the Safe
Development of Mobile Devices Software Based on OWASP. International Journal of Applied
Engineering Research, 13(18), pp.13603-13609.
Satria, D., Alanda, A., Erianda, A. and Prayama, D., 2018. Network Security Assessment Using
Internal Network Penetration Testing Methodology. JOIV: International Journal on Informatics
Visualization, 2(4-2), pp.360-365.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on

8PENETRATION TESTING
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
de Jiménez, R.E.L., 2016, November. Pentesting on web applications using ethical-hacking.
In 2016 IEEE 36th Central American and Panama Convention (CONCAPAN XXXVI) (pp. 1-6).
IEEE.
Al Shebli, H.M.Z. and Beheshti, B.D., 2018, May. A study on penetration testing process and
tools. In 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT) (pp.
1-7). IEEE.
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated penetration
testing. Benefits and drawbacks. Modern tendency. In 2016 13th International Conference on
Modern Problems of Radio Engineering, Telecommunications and Computer Science
(TCSET) (pp. 488-491). IEEE.
de Jiménez, R.E.L., 2016, November. Pentesting on web applications using ethical-hacking.
In 2016 IEEE 36th Central American and Panama Convention (CONCAPAN XXXVI) (pp. 1-6).
IEEE.
Al Shebli, H.M.Z. and Beheshti, B.D., 2018, May. A study on penetration testing process and
tools. In 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT) (pp.
1-7). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9PENETRATION TESTING
Kellezi, D., Boegelund, C. and Meng, W., 2019, December. Towards Secure Open Banking
Architecture: An Evaluation with OWASP. In International Conference on Network and System
Security (pp. 185-198). Springer, Cham.
Nguyen, T.D., Austin, S.C. and Irvine, C.E., 2019, December. A Strategy for Security Testing
Industrial Firewalls. In Proceedings of the Fifth Annual Industrial Control System Security
(ICSS) Workshop (pp. 38-47).
Kellezi, D., Boegelund, C. and Meng, W., 2019, December. Towards Secure Open Banking
Architecture: An Evaluation with OWASP. In International Conference on Network and System
Security (pp. 185-198). Springer, Cham.
Nguyen, T.D., Austin, S.C. and Irvine, C.E., 2019, December. A Strategy for Security Testing
Industrial Firewalls. In Proceedings of the Fifth Annual Industrial Control System Security
(ICSS) Workshop (pp. 38-47).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





