7COM1068: Penetration Testing Report - Vulnerability Analysis
VerifiedAdded on 2022/08/17
|12
|2834
|28
Report
AI Summary
This report delves into the realm of penetration testing, an essential practice for assessing system security by simulating attacks to uncover vulnerabilities. It begins by defining penetration testing and its objectives, followed by a discussion of various methodologies such as OSSTMM, ISSAF, and OWASP, which provide structured frameworks for conducting security tests. The report then explores the ethical and legal considerations that penetration testers must navigate, including the responsible use of tools, data privacy, and adherence to ethical guidelines. The core of the report details the key steps involved in penetration testing: intelligence gathering, vulnerability identification and analysis, and target exploitation. Each stage is explained with practical examples, emphasizing the importance of information collection, vulnerability scanning, and the ethical exploitation of identified weaknesses to improve system defenses. The report concludes by summarizing the significance of penetration testing in fortifying systems against real-world threats.

Running head: PENETRATION TESTING
PENETRATION TESTING
Name of student
Name of university
Author’s note:
PENETRATION TESTING
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PENETRATION TESTING
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Penetration testing methodologies.............................................................................2
Ethical and legal issues of penetration tester.............................................................4
Decision making tree..................................................................................................6
Step 1: Intelligence gathering.....................................................................................7
Step 2: Vulnerability identification and analysis.......................................................7
Step 3: Target exploitation.........................................................................................8
Conclusion......................................................................................................................9
References....................................................................................................................10
PENETRATION TESTING
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Penetration testing methodologies.............................................................................2
Ethical and legal issues of penetration tester.............................................................4
Decision making tree..................................................................................................6
Step 1: Intelligence gathering.....................................................................................7
Step 2: Vulnerability identification and analysis.......................................................7
Step 3: Target exploitation.........................................................................................8
Conclusion......................................................................................................................9
References....................................................................................................................10

2
PENETRATION TESTING
Introduction
Penetration testing or pen testing and ethical hacking could be described to be the
practices of effective testing any system, web application or the network for discovering
various security vulnerabilities that could be exploited by the attackers. The penetration
testing could be effectively automated with the various software applications or even
performed manually. In both the ways, the procedures mainly includes the information
collecting regarding the target prior testing, discovering the various entry points, intending to
break in, and then reporting back all the findings. This report intends to discuss the main
steps associated with the penetration testing for searching the various vulnerabilities.
Discussion
Penetration testing methodologies
Penetration testing methodology can be described as manuals that are used for
conducting any security test on any system in any specific method. In the manuals written by
the various organization, provides the complete guideline for conducting any test. Any typical
methodology mainly involves the vulnerability assessment, data collection, actual exploit,
result analysis as well as the report preparation. The penTest methodology is particularly
effective for determining the success of any test. The reporting aspect of the test becomes
significantly convenient and precise to clients (Pozzobon et al. 2018). The pentest could
become significantly easy in conducting, and it helps in initiating the procedure ethically as
well as legally. The methodologies which could be utilised for executing the penetration
testing are:
OSSTMM: Open Source Security Testing Methodology Manual can be referred as the
manual based on the security testing as well as the analysis created by Pete Herzog. It is latest
complete version of Open Source Security Testing Methodology Manual. The concept of
PENETRATION TESTING
Introduction
Penetration testing or pen testing and ethical hacking could be described to be the
practices of effective testing any system, web application or the network for discovering
various security vulnerabilities that could be exploited by the attackers. The penetration
testing could be effectively automated with the various software applications or even
performed manually. In both the ways, the procedures mainly includes the information
collecting regarding the target prior testing, discovering the various entry points, intending to
break in, and then reporting back all the findings. This report intends to discuss the main
steps associated with the penetration testing for searching the various vulnerabilities.
Discussion
Penetration testing methodologies
Penetration testing methodology can be described as manuals that are used for
conducting any security test on any system in any specific method. In the manuals written by
the various organization, provides the complete guideline for conducting any test. Any typical
methodology mainly involves the vulnerability assessment, data collection, actual exploit,
result analysis as well as the report preparation. The penTest methodology is particularly
effective for determining the success of any test. The reporting aspect of the test becomes
significantly convenient and precise to clients (Pozzobon et al. 2018). The pentest could
become significantly easy in conducting, and it helps in initiating the procedure ethically as
well as legally. The methodologies which could be utilised for executing the penetration
testing are:
OSSTMM: Open Source Security Testing Methodology Manual can be referred as the
manual based on the security testing as well as the analysis created by Pete Herzog. It is latest
complete version of Open Source Security Testing Methodology Manual. The concept of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PENETRATION TESTING
modules are used by OSSTMM by defining them as the set of particular phases or the
processes that are applicable for each of the channels. It involves the operational security
metrics, security testing, the security analysis, operation trust metrics, trust analysis as well as
the crucial tactics for testing of security (Denis, Zena and Hayajneh 2016). The OSSTMM is
the peer-reviewed methodology used for conducting security testing. The updating of the
manual is done every six months for remaining connected to the present states of the security
testing. It has been claimed by the ISECOM that the main objective with OSSTMM is
providing the scientific procedure for accurate characterisation of the operations security that
could be used for the penetration testing, ethical hacking, as well as other security testing.
ISSAF: Information System Security Assessment Framework or ISSAF could be
considered as peer reviewed structured framework that helps in the categorisation of the
security assessment of information system within the various domains, plus specifies the
particular assessment or the testing conditions for every domain (Singh et al. 2018). It intends
to offer the inputs in fields on the security evaluation that reflects the real situations of life.
The utilisation of the ISSAF should be done primarily for fulfilling the security assessment
requirements of the organisation and might furthermore be utilised as the reference for
fulfilling the other needs of information security. The ISSAF involves the critical facet of the
security procedures as well as the assessment for gaining the overall idea of the
vulnerabilities that may exist. The information within the ISSAF has been organised into the
well-defined criteria of evaluation and each of which is reviewed. The primary goal of ISSAF
is providing the sole point of reference for conducting the security assessment. It has been
considered as the reference that has been closely associated with the real life issues of
security evaluation and that provides significant value suggestion for the businesses.
OWASP: Open Web Application Security Project or the OWASP could be described
as the online community who provides the freely-available methodologies, articles,
PENETRATION TESTING
modules are used by OSSTMM by defining them as the set of particular phases or the
processes that are applicable for each of the channels. It involves the operational security
metrics, security testing, the security analysis, operation trust metrics, trust analysis as well as
the crucial tactics for testing of security (Denis, Zena and Hayajneh 2016). The OSSTMM is
the peer-reviewed methodology used for conducting security testing. The updating of the
manual is done every six months for remaining connected to the present states of the security
testing. It has been claimed by the ISECOM that the main objective with OSSTMM is
providing the scientific procedure for accurate characterisation of the operations security that
could be used for the penetration testing, ethical hacking, as well as other security testing.
ISSAF: Information System Security Assessment Framework or ISSAF could be
considered as peer reviewed structured framework that helps in the categorisation of the
security assessment of information system within the various domains, plus specifies the
particular assessment or the testing conditions for every domain (Singh et al. 2018). It intends
to offer the inputs in fields on the security evaluation that reflects the real situations of life.
The utilisation of the ISSAF should be done primarily for fulfilling the security assessment
requirements of the organisation and might furthermore be utilised as the reference for
fulfilling the other needs of information security. The ISSAF involves the critical facet of the
security procedures as well as the assessment for gaining the overall idea of the
vulnerabilities that may exist. The information within the ISSAF has been organised into the
well-defined criteria of evaluation and each of which is reviewed. The primary goal of ISSAF
is providing the sole point of reference for conducting the security assessment. It has been
considered as the reference that has been closely associated with the real life issues of
security evaluation and that provides significant value suggestion for the businesses.
OWASP: Open Web Application Security Project or the OWASP could be described
as the online community who provides the freely-available methodologies, articles,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PENETRATION TESTING
documentations, technologies as well as the tools within the sector of web application
security. It does not involve the complete penetration test rather it involves the core testing
stages of the web applications security testing (Chen et al. 2018). The guide offers the
comprehensive discussion on security assessment of the web application and the deployment
stack that involves the web server configuration. It effectively follows the black-box
pentesting approach. The major phases of OWASP Testing guide could be listed as the
configuration and the deployment management testing, information gathering, and the
security testing of web application.
Ethical and legal issues of penetration tester
The penetration testers mainly attacks the systems for evaluating the security in the
face of any genuine threats. These kinds of attacks mainly takes the shape of the authorised
penetration tests, which probes the defences of system, and then the defences are breached for
evaluating the major impact of any particular weakness, and consequences of tests are utilised
for improving the security of any system, allowing them to be increasingly resilient for
further attacks. The tests that are executed by the testers might be extensively legal if all the
exfiltrated data has not been used for any kind of personal work but this particular legality
might be significantly questionable relying on any legal jurisdiction regarding where test is
being conducted
There are significant questions regarding the morality related to the employment of
malware and involving with the markets from where the malware has been acquired from.
Ultimately the utilisation of deception as well as the de-anonymisation of the employees
acceptable, specifically where the policy is intentionally violated for achieving the critical
productivity goals (Baloch 2017). The ethics could be considered as the evaluation of
extensive morality. By offering the values as well as the theories regarding the various
perspectives regarding what is denoted to be authentic ethics assists in classifying the
PENETRATION TESTING
documentations, technologies as well as the tools within the sector of web application
security. It does not involve the complete penetration test rather it involves the core testing
stages of the web applications security testing (Chen et al. 2018). The guide offers the
comprehensive discussion on security assessment of the web application and the deployment
stack that involves the web server configuration. It effectively follows the black-box
pentesting approach. The major phases of OWASP Testing guide could be listed as the
configuration and the deployment management testing, information gathering, and the
security testing of web application.
Ethical and legal issues of penetration tester
The penetration testers mainly attacks the systems for evaluating the security in the
face of any genuine threats. These kinds of attacks mainly takes the shape of the authorised
penetration tests, which probes the defences of system, and then the defences are breached for
evaluating the major impact of any particular weakness, and consequences of tests are utilised
for improving the security of any system, allowing them to be increasingly resilient for
further attacks. The tests that are executed by the testers might be extensively legal if all the
exfiltrated data has not been used for any kind of personal work but this particular legality
might be significantly questionable relying on any legal jurisdiction regarding where test is
being conducted
There are significant questions regarding the morality related to the employment of
malware and involving with the markets from where the malware has been acquired from.
Ultimately the utilisation of deception as well as the de-anonymisation of the employees
acceptable, specifically where the policy is intentionally violated for achieving the critical
productivity goals (Baloch 2017). The ethics could be considered as the evaluation of
extensive morality. By offering the values as well as the theories regarding the various
perspectives regarding what is denoted to be authentic ethics assists in classifying the

5
PENETRATION TESTING
arguments, defend any position or gain improved understanding regarding the position others
takes and ultimately determining the suitable course of the action. The penetration testing
vivifies the ethics, compelling the experts in thinking regarding the concerns of variety of the
circumstances, stretching from the approving the main parameters of any test, for determining
the methods that should not or should be permitted during any test (Najera-Gutierrez and
Ansari 2018).
For instance, it has been stated by the Open Sources Security Testing Methodology
Manual that during evaluation of security position of any target, the business as well as the
industry ethics policies should be recognised that influences the privacy as well as the
security requirements. Even though some of ethical implications of the penetration testing has
been comprehended, the main implications of the ethical hacking are significantly ill-
explored. However, the primary role of the ethics is considered in the courses of computing
degrees, and there are various inconsistent options in what are required to be taught to the
students for preparing them for the professional courses. It has been considered that the
penetration testers would be making the informed decisions on the basis of the understanding
of the situation in consideration, supported by proper procedures, ethical as well as the
technical training that have been undertaken by them.
PENETRATION TESTING
arguments, defend any position or gain improved understanding regarding the position others
takes and ultimately determining the suitable course of the action. The penetration testing
vivifies the ethics, compelling the experts in thinking regarding the concerns of variety of the
circumstances, stretching from the approving the main parameters of any test, for determining
the methods that should not or should be permitted during any test (Najera-Gutierrez and
Ansari 2018).
For instance, it has been stated by the Open Sources Security Testing Methodology
Manual that during evaluation of security position of any target, the business as well as the
industry ethics policies should be recognised that influences the privacy as well as the
security requirements. Even though some of ethical implications of the penetration testing has
been comprehended, the main implications of the ethical hacking are significantly ill-
explored. However, the primary role of the ethics is considered in the courses of computing
degrees, and there are various inconsistent options in what are required to be taught to the
students for preparing them for the professional courses. It has been considered that the
penetration testers would be making the informed decisions on the basis of the understanding
of the situation in consideration, supported by proper procedures, ethical as well as the
technical training that have been undertaken by them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
PENETRATION TESTING
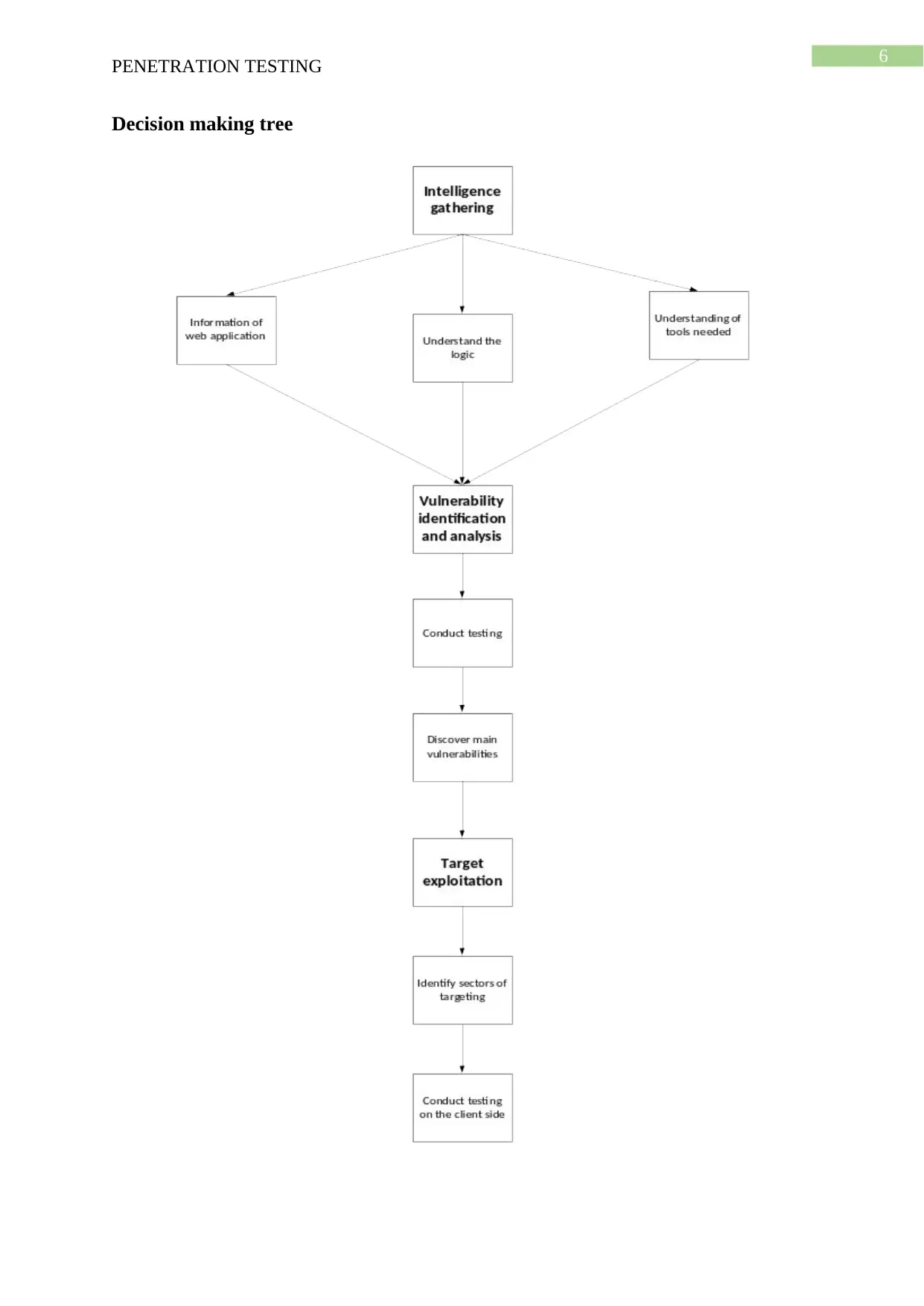
Decision making tree
PENETRATION TESTING
Decision making tree
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PENETRATION TESTING
Step 1: Intelligence gathering
Penetration testing could be described as the systematic penetrating of any system that
can be the mixture of the hosts, application or the networks (Miller et al. 2018). The most
common methodology of penetration testing is particular beneficial process for uncovering as
well as resolving the security weaknesses of the application, specifically the web
applications. It has been predicted that test preparation stage has to be completed before
initiating the test stage. There are mainly three phases involved within the testing stage,
namely, the intelligence gathering, vulnerability analysis as well as the vulnerability exploit.
These stages are commonly referred as the discovery stage, vulnerability stage as well as the
attach simulation stage. In the intelligence gathering stage, significant information is gathered
by the testers regarding the web application and then gain the proper knowledge of the logic.
The information collected would then be utilised for developing the appropriate knowledge
bases for acting upon in the later stages. The better the testers comprehends test target, the
more effective penetration testing would be (Taylor et al. 2018).The testers are required to
collect all the information even if it seems hugely useless as well as unrelated as there is no
accurate prediction of the outset of what information bits are required. In the penetration
testing that is being done, the open tools such as the scanners, search engines, transmitting the
simple HTTP requests is being done. The testers could recognise the intention of application
by accurately browsing them. The web server would be fingerprinted, the applications would
be spotted on the both server and client side and then the content would be determined. The
functionality would be determined manually or by the utilisation of automated tool.
Step 2: Vulnerability identification and analysis
With the utilisation of the knowledge gathered from intelligence gathering stage, the
testers then scans all the vulnerabilities that prevails within any web application. Testers
could then execute the testing on the business logic, configuration management, the
PENETRATION TESTING
Step 1: Intelligence gathering
Penetration testing could be described as the systematic penetrating of any system that
can be the mixture of the hosts, application or the networks (Miller et al. 2018). The most
common methodology of penetration testing is particular beneficial process for uncovering as
well as resolving the security weaknesses of the application, specifically the web
applications. It has been predicted that test preparation stage has to be completed before
initiating the test stage. There are mainly three phases involved within the testing stage,
namely, the intelligence gathering, vulnerability analysis as well as the vulnerability exploit.
These stages are commonly referred as the discovery stage, vulnerability stage as well as the
attach simulation stage. In the intelligence gathering stage, significant information is gathered
by the testers regarding the web application and then gain the proper knowledge of the logic.
The information collected would then be utilised for developing the appropriate knowledge
bases for acting upon in the later stages. The better the testers comprehends test target, the
more effective penetration testing would be (Taylor et al. 2018).The testers are required to
collect all the information even if it seems hugely useless as well as unrelated as there is no
accurate prediction of the outset of what information bits are required. In the penetration
testing that is being done, the open tools such as the scanners, search engines, transmitting the
simple HTTP requests is being done. The testers could recognise the intention of application
by accurately browsing them. The web server would be fingerprinted, the applications would
be spotted on the both server and client side and then the content would be determined. The
functionality would be determined manually or by the utilisation of automated tool.
Step 2: Vulnerability identification and analysis
With the utilisation of the knowledge gathered from intelligence gathering stage, the
testers then scans all the vulnerabilities that prevails within any web application. Testers
could then execute the testing on the business logic, configuration management, the

8
PENETRATION TESTING
authentication, data validation, the session management, authorisation, denial of service as
well as the web services (Sandhya et al. 2017). Within this stage, input-based vulnerabilities,
the vulnerabilities of web server, the vulnerabilities of authentication mechanism, as well as
the function-specific vulnerabilities are extensively examined. During the stage of examining
the web server vulnerabilities, any tester are required to properly evaluate the test for the
default authorisations, the default content, any risky HTTP methodologies, the proxy
functionalities, as well as the misconfiguration of virtual hosting. In this stage, it is
mandatory to properly test for all the flaws of the design as well as implementation in the
authentication mechanisms of the web application. The password quality, enumeration of
username, password guessing, and account recovery as well as the uniqueness of username
are required to be tested. Another kind of vulnerability that could be detected are the input
based vulnerabilities. The web applications that are data driven are significantly prone to the
input based vulnerabilities that could be easily exposed by properly testing from the Standard
Query Language injection as well as the Cross Site Scripting. The SQL injection attacks
would allow the attackers with injecting the SQL statements for reading as well as modifying
the data that is stored within database. XSS is the popular vulnerability of web application
that allows the attackers with injecting the client-side script within the web pages that are
observed by the other users (Dürrwang et al. 2018). The XSS could frequent occur in the web
applications that permits the users in submitting the comments.
Step 3: Target exploitation
After completing the vulnerability identification stage, the testers are required to have
the proper idea regarding the sectors that would be targeted for conducting the exploits. With
the proper knowledge of how the applications are susceptible to the SQL injection, the
various purposes of application has been explored with main intention of gaining increased
ideas for exploiting any system (Shinde and Ardhapurkar 2016). Commonly, during
PENETRATION TESTING
authentication, data validation, the session management, authorisation, denial of service as
well as the web services (Sandhya et al. 2017). Within this stage, input-based vulnerabilities,
the vulnerabilities of web server, the vulnerabilities of authentication mechanism, as well as
the function-specific vulnerabilities are extensively examined. During the stage of examining
the web server vulnerabilities, any tester are required to properly evaluate the test for the
default authorisations, the default content, any risky HTTP methodologies, the proxy
functionalities, as well as the misconfiguration of virtual hosting. In this stage, it is
mandatory to properly test for all the flaws of the design as well as implementation in the
authentication mechanisms of the web application. The password quality, enumeration of
username, password guessing, and account recovery as well as the uniqueness of username
are required to be tested. Another kind of vulnerability that could be detected are the input
based vulnerabilities. The web applications that are data driven are significantly prone to the
input based vulnerabilities that could be easily exposed by properly testing from the Standard
Query Language injection as well as the Cross Site Scripting. The SQL injection attacks
would allow the attackers with injecting the SQL statements for reading as well as modifying
the data that is stored within database. XSS is the popular vulnerability of web application
that allows the attackers with injecting the client-side script within the web pages that are
observed by the other users (Dürrwang et al. 2018). The XSS could frequent occur in the web
applications that permits the users in submitting the comments.
Step 3: Target exploitation
After completing the vulnerability identification stage, the testers are required to have
the proper idea regarding the sectors that would be targeted for conducting the exploits. With
the proper knowledge of how the applications are susceptible to the SQL injection, the
various purposes of application has been explored with main intention of gaining increased
ideas for exploiting any system (Shinde and Ardhapurkar 2016). Commonly, during
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PENETRATION TESTING
conducting the test for the XSS vulnerabilities, an application could be exploited by the
malicious messages that are posted on site before presenting the blog. This particular
vulnerability could be extensively misused further by the utilisation of link instead of alert
messages. One more popular exploit of the vulnerability is stealing the valuable data. It could
be done by the forging of website as well as embedding the content that effectively lures any
user in entering the sensitive information (Stefinko, Piskozub and Banakh 2016).
Conclusion
Therefore, it could be concluded that the penetration testing could be done in the
vulnerable web application for determining the main vulnerabilities of the system.
Penetration testing methodology could be described as the manuals that are used for
conducting any security test on any system in any specific method. In the manuals written by
the various organization, provides the complete guideline for conducting any test. The
penetration testing vivifies the ethics, compelling the experts in thinking regarding the
concerns of variety of the circumstances, stretching from the approving the main parameters
of any test, for determining the methods that should not or should be permitted during any
test. Penetration testing could be described as systematic examining of any system that can be
the mixture of the hosts, application or the networks.
PENETRATION TESTING
conducting the test for the XSS vulnerabilities, an application could be exploited by the
malicious messages that are posted on site before presenting the blog. This particular
vulnerability could be extensively misused further by the utilisation of link instead of alert
messages. One more popular exploit of the vulnerability is stealing the valuable data. It could
be done by the forging of website as well as embedding the content that effectively lures any
user in entering the sensitive information (Stefinko, Piskozub and Banakh 2016).
Conclusion
Therefore, it could be concluded that the penetration testing could be done in the
vulnerable web application for determining the main vulnerabilities of the system.
Penetration testing methodology could be described as the manuals that are used for
conducting any security test on any system in any specific method. In the manuals written by
the various organization, provides the complete guideline for conducting any test. The
penetration testing vivifies the ethics, compelling the experts in thinking regarding the
concerns of variety of the circumstances, stretching from the approving the main parameters
of any test, for determining the methods that should not or should be permitted during any
test. Penetration testing could be described as systematic examining of any system that can be
the mixture of the hosts, application or the networks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
PENETRATION TESTING
References
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Chen, C.K., Zhang, Z.K., Lee, S.H. and Shieh, S., 2018. Penetration testing in the iot
age. Computer, 51(4), pp.82-85.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Miller, G.A., Tan, N.K., Collins, R.W. and Muraleetharan, K.K., 2018. Cone penetration
testing in unsaturated soils. Transportation Geotechnics, 17, pp.85-99.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Pozzobon, E., Weiss, N., Renner, S. and Hackenberg, R., 2018. A Survey on Media Access
Solutions for CAN Penetration Testing.
PENETRATION TESTING
References
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Chen, C.K., Zhang, Z.K., Lee, S.H. and Shieh, S., 2018. Penetration testing in the iot
age. Computer, 51(4), pp.82-85.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Miller, G.A., Tan, N.K., Collins, R.W. and Muraleetharan, K.K., 2018. Cone penetration
testing in unsaturated soils. Transportation Geotechnics, 17, pp.85-99.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Pozzobon, E., Weiss, N., Renner, S. and Hackenberg, R., 2018. A Survey on Media Access
Solutions for CAN Penetration Testing.

11
PENETRATION TESTING
Sandhya, S., Purkayastha, S., Joshua, E. and Deep, A., 2017, January. Assessment of website
security by penetration testing using Wireshark. In 2017 4th International Conference on
Advanced Computing and Communication Systems (ICACCS) (pp. 1-4). IEEE.
Shinde, P.S. and Ardhapurkar, S.B., 2016, February. Cyber security analysis using
vulnerability assessment and penetration testing. In 2016 World Conference on Futuristic
Trends in Research and Innovation for Social Welfare (Startup Conclave) (pp. 1-5). IEEE.
Singh, A., Jaswal, N., Agarwal, M. and Teixeira, D., 2018. Metasploit Penetration Testing
Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments with the
most widely used penetration testing framework. Packt Publishing Ltd.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated
penetration testing. Benefits and drawbacks. Modern tendency. In 2016 13th International
Conference on Modern Problems of Radio Engineering, Telecommunications and Computer
Science (TCSET) (pp. 488-491). IEEE.
Taylor, L.M., Brown, M., Sadek, T. and Howe, J., 2018. Assessment of karst hazard using
cone penetration testing. In Engineering in Chalk: Proceedings of the Chalk 2018
Conference (pp. 315-321). ICE Publishing.
PENETRATION TESTING
Sandhya, S., Purkayastha, S., Joshua, E. and Deep, A., 2017, January. Assessment of website
security by penetration testing using Wireshark. In 2017 4th International Conference on
Advanced Computing and Communication Systems (ICACCS) (pp. 1-4). IEEE.
Shinde, P.S. and Ardhapurkar, S.B., 2016, February. Cyber security analysis using
vulnerability assessment and penetration testing. In 2016 World Conference on Futuristic
Trends in Research and Innovation for Social Welfare (Startup Conclave) (pp. 1-5). IEEE.
Singh, A., Jaswal, N., Agarwal, M. and Teixeira, D., 2018. Metasploit Penetration Testing
Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments with the
most widely used penetration testing framework. Packt Publishing Ltd.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated
penetration testing. Benefits and drawbacks. Modern tendency. In 2016 13th International
Conference on Modern Problems of Radio Engineering, Telecommunications and Computer
Science (TCSET) (pp. 488-491). IEEE.
Taylor, L.M., Brown, M., Sadek, T. and Howe, J., 2018. Assessment of karst hazard using
cone penetration testing. In Engineering in Chalk: Proceedings of the Chalk 2018
Conference (pp. 315-321). ICE Publishing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





