Comprehensive Report on Penetration Testing Methodologies and SOP
VerifiedAdded on 2022/08/20
|12
|2793
|15
Report
AI Summary
This report provides a comprehensive overview of penetration testing, a crucial practice for assessing the security of systems and networks. It delves into various penetration testing methodologies, including black box, white box, and gray box testing, outlining their characteristics, strengths, and weaknesses. The report emphasizes the importance of ethical and statutory considerations for penetration testers, highlighting the need for responsible conduct and adherence to legal frameworks. It also explores the standard operating procedures (SOP) involved in penetration testing, covering information gathering, threat modeling, vulnerability analysis, and exploitation phases. Furthermore, the report examines the application of decision-making trees in penetration testing, illustrating how this approach aids in analyzing data and identifying malicious activities. The report underscores the significance of penetration testing in uncovering vulnerabilities, enhancing overall security, and making systems resilient against potential attacks. It stresses the need for well-implemented security policies and methodologies to ensure the effectiveness of penetration testing efforts.

Running head: PENETRATION TESTING
PENETRATION TESTING
Name of the Student
Name of the University
Author Note:
PENETRATION TESTING
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PENETRATION TESTING
Table of Contents
Introduction..........................................................................................................................2
Different Penetration Testing Methodologies.....................................................................2
Statutory and ethical considerations of a penetration tester................................................4
Standard Operating Procedure.............................................................................................5
Decision-Making Tree.........................................................................................................6
Conclusion...........................................................................................................................8
References..........................................................................................................................10
Table of Contents
Introduction..........................................................................................................................2
Different Penetration Testing Methodologies.....................................................................2
Statutory and ethical considerations of a penetration tester................................................4
Standard Operating Procedure.............................................................................................5
Decision-Making Tree.........................................................................................................6
Conclusion...........................................................................................................................8
References..........................................................................................................................10

2PENETRATION TESTING
Introduction
Penetration testing methodologies stand out to be vital for the firm as they help in testing
operational security of the given physical location. In addition, this can be used for human
security testing, physical security testing, telecommunication security test and network data
testing. There is need for having pen testing methodologies in most of the firm as it helps in
identification of vulnerabilities and threat in the given environment (Baloch 2017). In other
words, penetration testing can be state as the kind of security testing which aim to uncover
various kind of vulnerabilities, risks and threats in various software application. All these can be
used by attacked in case of exploitation. The main purpose of pen test is all about analyzing the
security vulnerabilities found in the system (Shaukat et al. 2016). The ultimate goal of
penetration testing is all about enhancing the overall security of the network.
The report focus on pen testing methodologies and different steps which have asked to
complete in this assignment. In the report, an analysis has been done with respect to penetration
testing methodologies with the intention of carrying out penetration testing. The mere focus is all
about finding the vulnerabilities in SOP for pen testing and decision making tree.
Different Penetration Testing Methodologies
With respect to vulnerabilities of web application, there are mainly three kind of pen test
which can be used like
Black Box testing: The attacker does not have knowledge about the target, which is also
known as black-box penetration testing. It merely requires huge amount of time, and pen tester
can make use of different kind of automated tools in order to find out the vulnerabilities and
weak areas (Dawson and McDonald 2016). Black-box penetration testing helps in determining
Introduction
Penetration testing methodologies stand out to be vital for the firm as they help in testing
operational security of the given physical location. In addition, this can be used for human
security testing, physical security testing, telecommunication security test and network data
testing. There is need for having pen testing methodologies in most of the firm as it helps in
identification of vulnerabilities and threat in the given environment (Baloch 2017). In other
words, penetration testing can be state as the kind of security testing which aim to uncover
various kind of vulnerabilities, risks and threats in various software application. All these can be
used by attacked in case of exploitation. The main purpose of pen test is all about analyzing the
security vulnerabilities found in the system (Shaukat et al. 2016). The ultimate goal of
penetration testing is all about enhancing the overall security of the network.
The report focus on pen testing methodologies and different steps which have asked to
complete in this assignment. In the report, an analysis has been done with respect to penetration
testing methodologies with the intention of carrying out penetration testing. The mere focus is all
about finding the vulnerabilities in SOP for pen testing and decision making tree.
Different Penetration Testing Methodologies
With respect to vulnerabilities of web application, there are mainly three kind of pen test
which can be used like
Black Box testing: The attacker does not have knowledge about the target, which is also
known as black-box penetration testing. It merely requires huge amount of time, and pen tester
can make use of different kind of automated tools in order to find out the vulnerabilities and
weak areas (Dawson and McDonald 2016). Black-box penetration testing helps in determining
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PENETRATION TESTING
the vulnerabilities in the given system, which can be exploited just outside the network. Black-
box penetration testing completely depends on dynamic analysis of the present program within
the target networks. Black-box penetration tester needs to be familiar with the automated
scanning tools and methodologies needed for manual penetration testing. Black box penetration
tester also comes up with the capability of creating their own mind map for the target network.
This is completely based on observation as no kind of diagram is provided to them. As only
limited knowledge is allowed to penetration tester, which makes the black –box penetration test
as quickest to run (Casola et al. 2018). The duration of the assignment completely depends on
the ability of tester for locating and exploiting any kind of vulnerabilities. One of the biggest
drawback of this is that the tester cannot breach the given perimeter.
White Box: It comes up with series of names like clear-box, open-box and logic-driven
testing. It merely falls on the opposite side of the spectrum that is black-box testing where
penetration tester are provided with complete access to different source code. One of the biggest
challenges with white-box testing is the massive amount of data that helps in identifying the
weakness (Robertson 2016). This stand out to be as one of the time-consuming kind of
penetration testing. White-box tester comes up with the ability of doing the static code analysis.
This merely makes much familiar with the source code analyzer, debugger. Much similar kind of
tools are found to be vital for white box tester. As the static analysis can help in missing some of
the vulnerabilities which results due to system misconfiguration. This particular testing provides
a complete assessment with respect to internal and external vulnerabilities. It stand out to be the
best choice in case of carrying out calculation testing (Abu-Dabaseh and Alshammari 2018). As
a result of close relationship in between white box pen tester and developers, a high level of
system knowledge can be obtained.
the vulnerabilities in the given system, which can be exploited just outside the network. Black-
box penetration testing completely depends on dynamic analysis of the present program within
the target networks. Black-box penetration tester needs to be familiar with the automated
scanning tools and methodologies needed for manual penetration testing. Black box penetration
tester also comes up with the capability of creating their own mind map for the target network.
This is completely based on observation as no kind of diagram is provided to them. As only
limited knowledge is allowed to penetration tester, which makes the black –box penetration test
as quickest to run (Casola et al. 2018). The duration of the assignment completely depends on
the ability of tester for locating and exploiting any kind of vulnerabilities. One of the biggest
drawback of this is that the tester cannot breach the given perimeter.
White Box: It comes up with series of names like clear-box, open-box and logic-driven
testing. It merely falls on the opposite side of the spectrum that is black-box testing where
penetration tester are provided with complete access to different source code. One of the biggest
challenges with white-box testing is the massive amount of data that helps in identifying the
weakness (Robertson 2016). This stand out to be as one of the time-consuming kind of
penetration testing. White-box tester comes up with the ability of doing the static code analysis.
This merely makes much familiar with the source code analyzer, debugger. Much similar kind of
tools are found to be vital for white box tester. As the static analysis can help in missing some of
the vulnerabilities which results due to system misconfiguration. This particular testing provides
a complete assessment with respect to internal and external vulnerabilities. It stand out to be the
best choice in case of carrying out calculation testing (Abu-Dabaseh and Alshammari 2018). As
a result of close relationship in between white box pen tester and developers, a high level of
system knowledge can be obtained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PENETRATION TESTING
Gray-Box Testing: If a black tester is examining the system from outside, then a gray
box tester come up with ability of access and knowledge level of users. It merely elevate some
kind of privileges on the given system. This particular pen testers come up with some knowledge
of internal network. It is inclusive of both design and architecture documents and internal
account in the network (Stiawan et al. 2016). The main purpose of gray-box pen testing is all
about providing a much focused and efficient assessment of network in comparison to black-box
assessment. By making use of design documents for network, pen tester can easily emphasize on
the assessment efforts on system. It comes up with greatest risk and value from the beginning. It
does not need spending time for the given information on their own (Hatfield 2019). Internal
account of the system merely allow testing of security which lies in the harden perimeter. It
merely focus on stimulating an attacker by having long term access to network.
Statutory and ethical considerations of a penetration tester
The main target of penetration tester is all about evaluation of the security which stand
out to be face of realistic threats. All these kind of attacks come into picture as a result of
authorized penetration test which can probe the defense. The defense can be breached in order to
evaluate the effect of weakness. The output of the test ultimately helps in improving the security
of system, which makes resilient for any kind of further attacks. Hacking into the system requires
a complete technical prowess, creativity and ingenuity for finding the unexpected ways.
Penetration testing requires all of the given things (Aar and Sharma 2017). It merely adds up
constraints in finding and exploiting of vulnerabilities. It should neither harm the system nor
even encroach the dignity of those who are affected by this.
Commercial pressure focus on the point that penetration tester encounter pressure for
analyzing the insecurity without engaging themselves in unethical behavior. Penetration testing
Gray-Box Testing: If a black tester is examining the system from outside, then a gray
box tester come up with ability of access and knowledge level of users. It merely elevate some
kind of privileges on the given system. This particular pen testers come up with some knowledge
of internal network. It is inclusive of both design and architecture documents and internal
account in the network (Stiawan et al. 2016). The main purpose of gray-box pen testing is all
about providing a much focused and efficient assessment of network in comparison to black-box
assessment. By making use of design documents for network, pen tester can easily emphasize on
the assessment efforts on system. It comes up with greatest risk and value from the beginning. It
does not need spending time for the given information on their own (Hatfield 2019). Internal
account of the system merely allow testing of security which lies in the harden perimeter. It
merely focus on stimulating an attacker by having long term access to network.
Statutory and ethical considerations of a penetration tester
The main target of penetration tester is all about evaluation of the security which stand
out to be face of realistic threats. All these kind of attacks come into picture as a result of
authorized penetration test which can probe the defense. The defense can be breached in order to
evaluate the effect of weakness. The output of the test ultimately helps in improving the security
of system, which makes resilient for any kind of further attacks. Hacking into the system requires
a complete technical prowess, creativity and ingenuity for finding the unexpected ways.
Penetration testing requires all of the given things (Aar and Sharma 2017). It merely adds up
constraints in finding and exploiting of vulnerabilities. It should neither harm the system nor
even encroach the dignity of those who are affected by this.
Commercial pressure focus on the point that penetration tester encounter pressure for
analyzing the insecurity without engaging themselves in unethical behavior. Penetration testing

5PENETRATION TESTING
emphasizes the practitioners regarding the consequence of the range of situation (Gupta 2017).
Penetration tester is required to carry out the informed decision which is based on the decision of
understanding the situation.
There are large number of wealth for legal problem which are related to information
security. There is need for preventing the security breaches in order to maintain the security of
client details. It focus on the obligation considering the information security. As the technology
is an ever-changing domain, there are always some question related to legal protection which
should be taken into account with respect to the misuse of technology (Jat, Lamba and Rathore
2019). In order to indicate the exact needs of pen tester, there are range of subnets, networks,
computer or devices which are subjected to pen test. If the software is reviewed then there is
need for decompiling in it. The copy right of software needs to be analyzed for ensuring the
copyright does not completely permit the reverse engineering or even code review.
Standard Operating Procedure
Information gathering aims to cover the threat model phases where the tester are working
hard behind the scenes so that they can have a better understanding the testing organization.
Intelligence gathering: In this step, information or intelligence is gathered for assisting
some of the guideline of the assessment. The information collecting process is all about
conducting for collecting information about the employees in firm (Najera-Gutierrez and Ansari
2018). It can help in getting access to that. Both host and service discovery efforts ultimately
resulted in complied list of accessible system and respective services with the goal of having the
information.
emphasizes the practitioners regarding the consequence of the range of situation (Gupta 2017).
Penetration tester is required to carry out the informed decision which is based on the decision of
understanding the situation.
There are large number of wealth for legal problem which are related to information
security. There is need for preventing the security breaches in order to maintain the security of
client details. It focus on the obligation considering the information security. As the technology
is an ever-changing domain, there are always some question related to legal protection which
should be taken into account with respect to the misuse of technology (Jat, Lamba and Rathore
2019). In order to indicate the exact needs of pen tester, there are range of subnets, networks,
computer or devices which are subjected to pen test. If the software is reviewed then there is
need for decompiling in it. The copy right of software needs to be analyzed for ensuring the
copyright does not completely permit the reverse engineering or even code review.
Standard Operating Procedure
Information gathering aims to cover the threat model phases where the tester are working
hard behind the scenes so that they can have a better understanding the testing organization.
Intelligence gathering: In this step, information or intelligence is gathered for assisting
some of the guideline of the assessment. The information collecting process is all about
conducting for collecting information about the employees in firm (Najera-Gutierrez and Ansari
2018). It can help in getting access to that. Both host and service discovery efforts ultimately
resulted in complied list of accessible system and respective services with the goal of having the
information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PENETRATION TESTING
Threat Modelling: It can be stated as the method of optimizing the network security by
proper identification of any vulnerabilities. There is need for list of countermeasures in order to
prevent this. This can be done for preventing the effect of threats on the system (Klíma 2016).
Threat modelling is merely used for analyzing where the effort should be given for securing the
system. This can be defined as the factor which completely changes when application are added
to this.
Vulnerability analysis: Vulnerability analysis is generally used for identification and
evaluation of various kind of security risks which are identified by vulnerabilities. The whole
process of vulnerability can be divided into two major steps that are identification and validation
(van den Hout 2019). It is merely inclusive of analysis which is out for various kind of security
tools and techniques for manual testing. There are list of attractive vulnerabilities, suspicious
services and items available for researching.
Exploiting: After carrying out the vulnerability assessment, there is need for exploiting
the vulnerabilities related to system breach and security. In order to carry out exploiting, there
are various kind of framework and software which are recommended for exploitative issue and
completely available (Stefinko and Piskuzub 2017). In the post stage, an analysis is done
regarding the value of machine which has been compromised. It merely helps in maintaining a
complete control of the machine. The overall value of machine is analyzed by sensitive data
which is stored in it. The usefulness of machine result in further compromising of the network.
Decision-Making Tree
Penetration testing stand out to be important step need for the development of any secure
system or product. Penetration testing not only focus on the operation but it also address design
Threat Modelling: It can be stated as the method of optimizing the network security by
proper identification of any vulnerabilities. There is need for list of countermeasures in order to
prevent this. This can be done for preventing the effect of threats on the system (Klíma 2016).
Threat modelling is merely used for analyzing where the effort should be given for securing the
system. This can be defined as the factor which completely changes when application are added
to this.
Vulnerability analysis: Vulnerability analysis is generally used for identification and
evaluation of various kind of security risks which are identified by vulnerabilities. The whole
process of vulnerability can be divided into two major steps that are identification and validation
(van den Hout 2019). It is merely inclusive of analysis which is out for various kind of security
tools and techniques for manual testing. There are list of attractive vulnerabilities, suspicious
services and items available for researching.
Exploiting: After carrying out the vulnerability assessment, there is need for exploiting
the vulnerabilities related to system breach and security. In order to carry out exploiting, there
are various kind of framework and software which are recommended for exploitative issue and
completely available (Stefinko and Piskuzub 2017). In the post stage, an analysis is done
regarding the value of machine which has been compromised. It merely helps in maintaining a
complete control of the machine. The overall value of machine is analyzed by sensitive data
which is stored in it. The usefulness of machine result in further compromising of the network.
Decision-Making Tree
Penetration testing stand out to be important step need for the development of any secure
system or product. Penetration testing not only focus on the operation but it also address design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PENETRATION TESTING
and implementation of product or system. Penetration testing stand out to be a fundamental area
of information system in the domain of security engineering (Dürrwang et al. 2018). Decision
tree approach in penetration testing is the zone where less background of the information of
system is to be tested. One of the basic idea is all about combination of WBS from project
management. Model of penetration testing stand out to be bit useful. It merely have the benefits
of attack tree approach along with providing the key benefits. Penetration testing stand out to be
an important step with respect to development of secure system or product. The present business
completely defines the penetration testing like the application of automated network
vulnerability scanner for operational site. Decision tree provides a graphical approach
highlighting the collection of flaws. All these can be combined for achieving a significant kind of
system penetration (Baloch 2017). Attack net model stand out to be sophisticated attack which is
combination of different kind of flaws. It comes up with the ability of discovering the transition,
which helps in connecting subnets. This completely allow the penetration team to establish
communication about the effect of minor flaws.
The point can be concluded that decision making tree is the best tool needed for data
analysis and identification of any particular characteristics in network. This merely highlights the
malicious kind of activities (Shaukat et al. 2016). Decision logic can be used in conjunction
along with real-time tools for taking the corrective action against the threats. This become
ultimately possible as a result of highlighting malicious activities.
and implementation of product or system. Penetration testing stand out to be a fundamental area
of information system in the domain of security engineering (Dürrwang et al. 2018). Decision
tree approach in penetration testing is the zone where less background of the information of
system is to be tested. One of the basic idea is all about combination of WBS from project
management. Model of penetration testing stand out to be bit useful. It merely have the benefits
of attack tree approach along with providing the key benefits. Penetration testing stand out to be
an important step with respect to development of secure system or product. The present business
completely defines the penetration testing like the application of automated network
vulnerability scanner for operational site. Decision tree provides a graphical approach
highlighting the collection of flaws. All these can be combined for achieving a significant kind of
system penetration (Baloch 2017). Attack net model stand out to be sophisticated attack which is
combination of different kind of flaws. It comes up with the ability of discovering the transition,
which helps in connecting subnets. This completely allow the penetration team to establish
communication about the effect of minor flaws.
The point can be concluded that decision making tree is the best tool needed for data
analysis and identification of any particular characteristics in network. This merely highlights the
malicious kind of activities (Shaukat et al. 2016). Decision logic can be used in conjunction
along with real-time tools for taking the corrective action against the threats. This become
ultimately possible as a result of highlighting malicious activities.
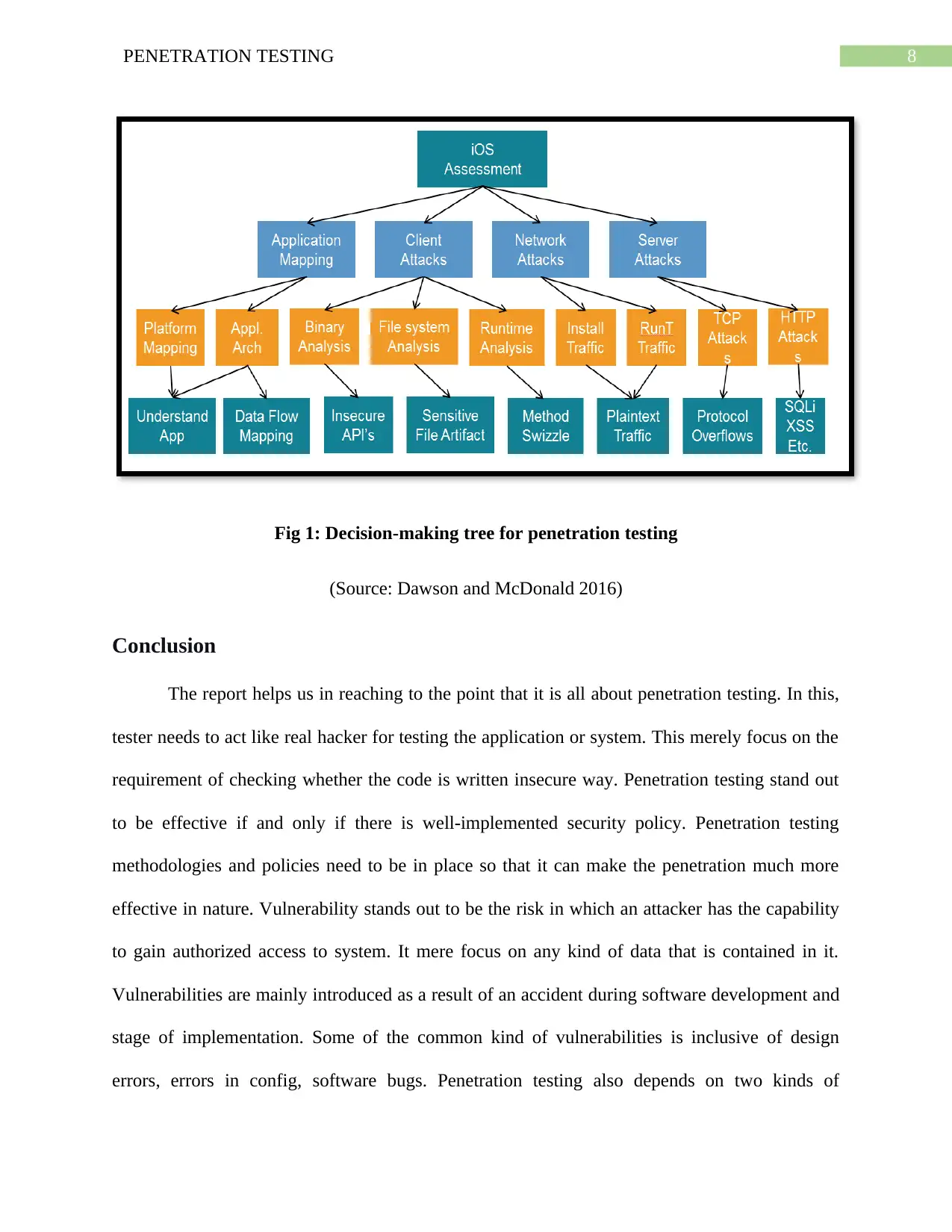
8PENETRATION TESTING
Fig 1: Decision-making tree for penetration testing
(Source: Dawson and McDonald 2016)
Conclusion
The report helps us in reaching to the point that it is all about penetration testing. In this,
tester needs to act like real hacker for testing the application or system. This merely focus on the
requirement of checking whether the code is written insecure way. Penetration testing stand out
to be effective if and only if there is well-implemented security policy. Penetration testing
methodologies and policies need to be in place so that it can make the penetration much more
effective in nature. Vulnerability stands out to be the risk in which an attacker has the capability
to gain authorized access to system. It mere focus on any kind of data that is contained in it.
Vulnerabilities are mainly introduced as a result of an accident during software development and
stage of implementation. Some of the common kind of vulnerabilities is inclusive of design
errors, errors in config, software bugs. Penetration testing also depends on two kinds of
Fig 1: Decision-making tree for penetration testing
(Source: Dawson and McDonald 2016)
Conclusion
The report helps us in reaching to the point that it is all about penetration testing. In this,
tester needs to act like real hacker for testing the application or system. This merely focus on the
requirement of checking whether the code is written insecure way. Penetration testing stand out
to be effective if and only if there is well-implemented security policy. Penetration testing
methodologies and policies need to be in place so that it can make the penetration much more
effective in nature. Vulnerability stands out to be the risk in which an attacker has the capability
to gain authorized access to system. It mere focus on any kind of data that is contained in it.
Vulnerabilities are mainly introduced as a result of an accident during software development and
stage of implementation. Some of the common kind of vulnerabilities is inclusive of design
errors, errors in config, software bugs. Penetration testing also depends on two kinds of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9PENETRATION TESTING
mechanism that is a vulnerability assessment and penetration testing. In the report, three kinds of
penetration testing that is black box, white box penetration testing and lastly grey box
penetration testing. The kind of penetration testing selected merely depends on scope and the
point whether the firm wants to be stimulated by the attack.
mechanism that is a vulnerability assessment and penetration testing. In the report, three kinds of
penetration testing that is black box, white box penetration testing and lastly grey box
penetration testing. The kind of penetration testing selected merely depends on scope and the
point whether the firm wants to be stimulated by the attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10PENETRATION TESTING
References
Aar, P. and Sharma, A.K., 2017. Analysis of Penetration Testing Tools. International Journal of
Advanced Research in Computer Science and Software Engineering (IJARCSSE), 7(9), p.36.
Abu-Dabaseh, F. and Alshammari, E., 2018. Automated Penetration Testing: An
Overview. Computer Science & Information Technology.
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies for
Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp. 51-58).
IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Gupta, B.B., 2017. Requirements Based Web Application Security Testing–A Preemptive
Approach!.
Hatfield, J.M., 2019. Virtuous human hacking: The ethics of social engineering in penetration-
testing. computers & security, 83, pp.354-366.
References
Aar, P. and Sharma, A.K., 2017. Analysis of Penetration Testing Tools. International Journal of
Advanced Research in Computer Science and Software Engineering (IJARCSSE), 7(9), p.36.
Abu-Dabaseh, F. and Alshammari, E., 2018. Automated Penetration Testing: An
Overview. Computer Science & Information Technology.
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies for
Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp. 51-58).
IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Gupta, B.B., 2017. Requirements Based Web Application Security Testing–A Preemptive
Approach!.
Hatfield, J.M., 2019. Virtuous human hacking: The ethics of social engineering in penetration-
testing. computers & security, 83, pp.354-366.

11PENETRATION TESTING
Jat, S.C., Lamba, C.S. and Rathore, V.S., 2019. Software Quality Improvement Through
Penetration Testing. In Emerging Trends in Expert Applications and Security (pp. 239-244).
Springer, Singapore.
Klíma, T., 2016. PETA: Methodology of information systems security penetration testing. Acta
Informatica Pragensia, 5(2), pp.98-117.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux: Explore
the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Robertson, P.K., 2016. Cone penetration test (CPT)-based soil behaviour type (SBT)
classification system—an update. Canadian Geotechnical Journal, 53(12), pp.1910-1927.
Shaukat, K., Faisal, A., Masood, R., Usman, A. and Shaukat, U., 2016, December. Security
quality assurance through penetration testing. In 2016 19th International Multi-Topic
Conference (INMIC) (pp. 1-6). IEEE.
Stefinko, Y.Y. and Piskuzub, A.Z., 2017. Theory of modern penetration testing expert
system. Системи обробки інформації, (2), pp.129-133.
Stiawan, D., Idris, M.Y.B., Abdullah, A.H., AlQurashi, M. and Budiarto, R., 2016. Penetration
Testing and Mitigation of Vulnerabilities Windows Server. IJ Network Security, 18(3), pp.501-
513.
van den Hout, N.J., 2019. Standardised penetration testing? Examining the usefulness of current
penetration testing methodologies.
Jat, S.C., Lamba, C.S. and Rathore, V.S., 2019. Software Quality Improvement Through
Penetration Testing. In Emerging Trends in Expert Applications and Security (pp. 239-244).
Springer, Singapore.
Klíma, T., 2016. PETA: Methodology of information systems security penetration testing. Acta
Informatica Pragensia, 5(2), pp.98-117.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux: Explore
the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Robertson, P.K., 2016. Cone penetration test (CPT)-based soil behaviour type (SBT)
classification system—an update. Canadian Geotechnical Journal, 53(12), pp.1910-1927.
Shaukat, K., Faisal, A., Masood, R., Usman, A. and Shaukat, U., 2016, December. Security
quality assurance through penetration testing. In 2016 19th International Multi-Topic
Conference (INMIC) (pp. 1-6). IEEE.
Stefinko, Y.Y. and Piskuzub, A.Z., 2017. Theory of modern penetration testing expert
system. Системи обробки інформації, (2), pp.129-133.
Stiawan, D., Idris, M.Y.B., Abdullah, A.H., AlQurashi, M. and Budiarto, R., 2016. Penetration
Testing and Mitigation of Vulnerabilities Windows Server. IJ Network Security, 18(3), pp.501-
513.
van den Hout, N.J., 2019. Standardised penetration testing? Examining the usefulness of current
penetration testing methodologies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





