Evaluating Penetration Testing Methods and Standard SOP
VerifiedAdded on 2023/03/31
|8
|1625
|478
Report
AI Summary
This report provides an overview of penetration testing, a crucial security measure for governments and businesses, especially given the rise in cyber-attacks. It discusses various penetration testing methodologies, including OSSTMM, ISSAF, OWASP, and PTES, highlighting their unique applications and strengths. The report emphasizes the importance of a well-designed and executed penetration testing strategy to detect flaws and improve system security. Furthermore, it delves into the concept of a Standard Operating Procedure (SOP) for penetration testing, detailing its key steps such as intelligence gathering, target selection, vulnerability analysis, and exploitation, primarily using the PTES framework. The conclusion underscores penetration testing's validity in assessing security levels and advocates for a well-planned SOP to ensure efficient system security testing.

Running head: PENETRATION TESTING
PENETRATION TESTING
Name of the Student:
Name of the University:
Author Note:
PENETRATION TESTING
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PENETRATION TESTING
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Penetration testing methodologies.........................................................................................2
Standard Operating Procedure or SOP...................................................................................3
Conclusion..................................................................................................................................4
References..................................................................................................................................5
Appendix....................................................................................................................................7
Decision tree...........................................................................................................................7
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Penetration testing methodologies.........................................................................................2
Standard Operating Procedure or SOP...................................................................................3
Conclusion..................................................................................................................................4
References..................................................................................................................................5
Appendix....................................................................................................................................7
Decision tree...........................................................................................................................7

2PENETRATION TESTING
Introduction
The number of cyber-attacks have increased in the last few years and it has adversely
affected both governments and businesses. This has increased the need for developing
security technologies such as improved web security measures, improved security protocols
and antiviruses. The number of cybersecurity agencies and companies have also increased
around the world with an increased focus on cyber security. Penetration testing is one of the
most commonly used security measure. This method is mainly used to test the defence
quality of security measures or software installed in organisation and perform vulnerability
analysis on them.
This approach is used so that the vulnerabilities in the systems can be detected earlier
so that they can be rectified before an actual attack takes place. The most important part of
penetration testing is to analyse the situation and establish a high quality solid method or
framework according to the type of the organisation and its needs. The assessment of the
infrastructure plays a vital role in this testing. A well designed and properly executed
penetration testing can be used to effectively detect flaws and improve the system.
Discussion
Penetration testing methodologies
The most widely used penetration testing methodologies are discussed below:
1. OSSTMM: This is an open source methodology that was first used in 2000 to test system
securities. It was developed by the Institute of Security and Open Methodologies. This
framework includes many different channels and modules. OSSTMM is a type of auditing
method and is not a complete one. This method is used in corporate offices and industries to
satisfy the requirements of regulation.
2. ISSAF: This method is an open source, peer reviewed penetration testing framework that
was developed by the Open Information Security Group. The framework is a complete
framework which includes multiple different methodologies and can be used for all types of
possible penetration testing tests.
3. OWASP: This methodology is non-profit which is designed for increasing the security of
software. This includes many types of different testing methods, testing tools and guides that
are designed for cyber security software. It comes with an open license and is mainly used for
Introduction
The number of cyber-attacks have increased in the last few years and it has adversely
affected both governments and businesses. This has increased the need for developing
security technologies such as improved web security measures, improved security protocols
and antiviruses. The number of cybersecurity agencies and companies have also increased
around the world with an increased focus on cyber security. Penetration testing is one of the
most commonly used security measure. This method is mainly used to test the defence
quality of security measures or software installed in organisation and perform vulnerability
analysis on them.
This approach is used so that the vulnerabilities in the systems can be detected earlier
so that they can be rectified before an actual attack takes place. The most important part of
penetration testing is to analyse the situation and establish a high quality solid method or
framework according to the type of the organisation and its needs. The assessment of the
infrastructure plays a vital role in this testing. A well designed and properly executed
penetration testing can be used to effectively detect flaws and improve the system.
Discussion
Penetration testing methodologies
The most widely used penetration testing methodologies are discussed below:
1. OSSTMM: This is an open source methodology that was first used in 2000 to test system
securities. It was developed by the Institute of Security and Open Methodologies. This
framework includes many different channels and modules. OSSTMM is a type of auditing
method and is not a complete one. This method is used in corporate offices and industries to
satisfy the requirements of regulation.
2. ISSAF: This method is an open source, peer reviewed penetration testing framework that
was developed by the Open Information Security Group. The framework is a complete
framework which includes multiple different methodologies and can be used for all types of
possible penetration testing tests.
3. OWASP: This methodology is non-profit which is designed for increasing the security of
software. This includes many types of different testing methods, testing tools and guides that
are designed for cyber security software. It comes with an open license and is mainly used for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PENETRATION TESTING
conducting penetration testing on web applications and websites. Therefore unlike the above
two methodologies mentioned, OWASP is mainly involved for development of web
applications.
4. PTES: Penetration testing execution standard or PTES is a testing methodology that can
be used to do a multiple types of activities like vulnerability analysis, post exploitation, threat
detection, gathering intelligence and reporting. PTES is the only standard that can make use
of other frameworks to analyse and conduct penetration testing depending on the attack type.
For example, web based attacks can be tested using a combination of PTES and OWASP.
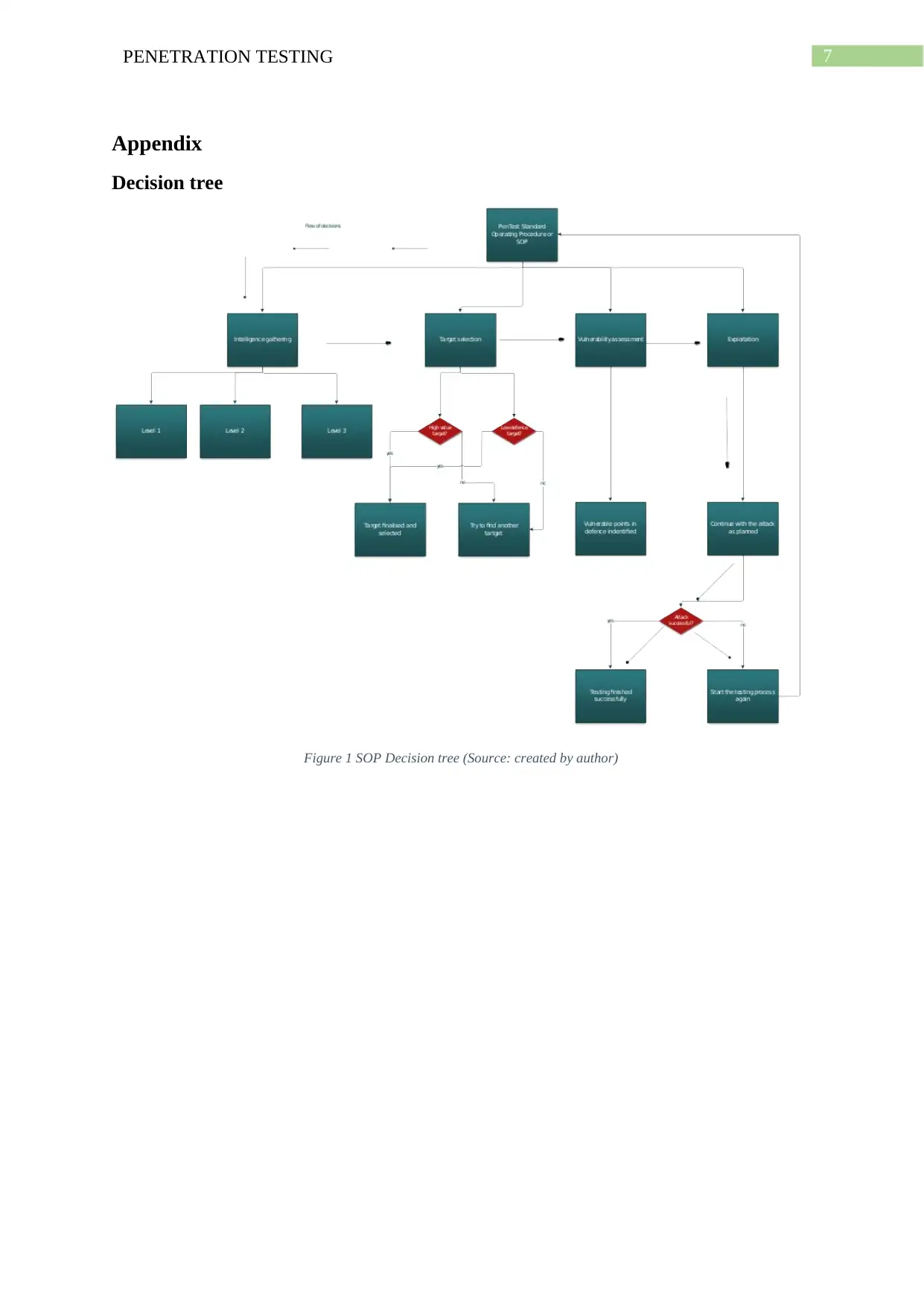
Standard Operating Procedure or SOP
The standard operating procedure is a protocol or a set of steps that workers in
organisations need to follow in their daily routine operations to conduct penetration testing.
PTES or penetration testing execution standard can be effectively used to create a standard
operating procedure and then help in implementing it. The PTES includes all the steps needed
for a penetration testing SOP like vulnerability detection, post exploitation, target
exploitation and intelligence gathering. The following are the steps that are needed for the
SOP.
1. Gathering intelligence: This is the first step of the Pentest and can be divided into three
main parts. These parts are level 1, level 2 and level 3. The first stage or level 1 is mainly
related to gathering of data using automated tools. In the level 2 stage, the data is gathered
using both manual analysis and automated tools. In stage or level 3, the amount of manual
work and analysis needed is much more along with the use of automated tools are also used
to gather intelligence.
2. Target selection: In this stage, the data or intelligence collected is analysed and a
matching target is selected. This target’s selection is based on many factors like the length of
time required for conducting the attack, the risks attached with the attack and the final result
of the attack including the amount of information that can be gained from it.
3. Vulnerability analysis: In this stage, the main target company’s systems are analysed and
their main flaws or vulnerabilities are noted. Based on the type of the vulnerabilities detected
in the system, different sets of tools that will be used for the attack are determined. The flaws
are generally detected in the service configuration of the systems or in its design. The
vulnerability analysis may take varied about of time in detecting the flaws depending upon
the complexity of the system chosen. The testing must be done in such a way such that it
conducting penetration testing on web applications and websites. Therefore unlike the above
two methodologies mentioned, OWASP is mainly involved for development of web
applications.
4. PTES: Penetration testing execution standard or PTES is a testing methodology that can
be used to do a multiple types of activities like vulnerability analysis, post exploitation, threat
detection, gathering intelligence and reporting. PTES is the only standard that can make use
of other frameworks to analyse and conduct penetration testing depending on the attack type.
For example, web based attacks can be tested using a combination of PTES and OWASP.
Standard Operating Procedure or SOP
The standard operating procedure is a protocol or a set of steps that workers in
organisations need to follow in their daily routine operations to conduct penetration testing.
PTES or penetration testing execution standard can be effectively used to create a standard
operating procedure and then help in implementing it. The PTES includes all the steps needed
for a penetration testing SOP like vulnerability detection, post exploitation, target
exploitation and intelligence gathering. The following are the steps that are needed for the
SOP.
1. Gathering intelligence: This is the first step of the Pentest and can be divided into three
main parts. These parts are level 1, level 2 and level 3. The first stage or level 1 is mainly
related to gathering of data using automated tools. In the level 2 stage, the data is gathered
using both manual analysis and automated tools. In stage or level 3, the amount of manual
work and analysis needed is much more along with the use of automated tools are also used
to gather intelligence.
2. Target selection: In this stage, the data or intelligence collected is analysed and a
matching target is selected. This target’s selection is based on many factors like the length of
time required for conducting the attack, the risks attached with the attack and the final result
of the attack including the amount of information that can be gained from it.
3. Vulnerability analysis: In this stage, the main target company’s systems are analysed and
their main flaws or vulnerabilities are noted. Based on the type of the vulnerabilities detected
in the system, different sets of tools that will be used for the attack are determined. The flaws
are generally detected in the service configuration of the systems or in its design. The
vulnerability analysis may take varied about of time in detecting the flaws depending upon
the complexity of the system chosen. The testing must be done in such a way such that it
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PENETRATION TESTING
matches with the requirements in depth. The testing scope can be met by validating the
breadth of the testing.
4. Exploitation: The primary aim of this part is to establish a complete and safe connection
to the target system for completion of the exploit. The security protocols and measures can be
host based intrusion prevention system, security guard, web applications firewall and other
such security measures. The degree of success of this exploitation part totally depends on the
correct and focussed execution of the vulnerability analysis. A well thought out and planned
phase for vulnerability analysis will lead to a highly successful exploit attack. The primary
objective of this process is to segregate the high value assets and identify the primary entry
points.
Conclusion
To conclude it can be said that penetration testing is a valid method to test the security
level of governments and other organisations. The main four penetration testing methods as
discussed above are OWASP, ISSAF, PTES and OSSTMM. Among this only OWASP is
used for web based companies and applications and ISSAF is the only fully complete and
versatile framework. This report also highlights the definition of the standard operating
procedure or SOP and also describes its four main steps in detail. The report demonstrates
this by using the PTES method which is a unique method that can be combined with other
frameworks and methodologies to create SOPs for penetration testing. Overall, the security of
the system can be tested efficiently with the help of penetration testing using a well-planned
SOP.
matches with the requirements in depth. The testing scope can be met by validating the
breadth of the testing.
4. Exploitation: The primary aim of this part is to establish a complete and safe connection
to the target system for completion of the exploit. The security protocols and measures can be
host based intrusion prevention system, security guard, web applications firewall and other
such security measures. The degree of success of this exploitation part totally depends on the
correct and focussed execution of the vulnerability analysis. A well thought out and planned
phase for vulnerability analysis will lead to a highly successful exploit attack. The primary
objective of this process is to segregate the high value assets and identify the primary entry
points.
Conclusion
To conclude it can be said that penetration testing is a valid method to test the security
level of governments and other organisations. The main four penetration testing methods as
discussed above are OWASP, ISSAF, PTES and OSSTMM. Among this only OWASP is
used for web based companies and applications and ISSAF is the only fully complete and
versatile framework. This report also highlights the definition of the standard operating
procedure or SOP and also describes its four main steps in detail. The report demonstrates
this by using the PTES method which is a unique method that can be combined with other
frameworks and methodologies to create SOPs for penetration testing. Overall, the security of
the system can be tested efficiently with the help of penetration testing using a well-planned
SOP.

5PENETRATION TESTING
References
Bertoglio, D.D. and Zorzo, A.F., 2017. Overview and open issues on penetration
test. Journal of the Brazilian Computer Society, 23(1), p.2.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies
for Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC)(pp.
51-58). IEEE.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Farah, T., Alam, D., Kabir, M.A. and Bhuiyan, T., 2015, October. SQLi penetration testing of
financial Web applications: Investigation of Bangladesh region. In 2015 World Congress on
Internet Security (WorldCIS) (pp. 146-151). IEEE.
Hoffmann, J., 2015, April. Simulated Penetration Testing: From" Dijkstra" to" Turing Test+
+". In Twenty-Fifth International Conference on Automated Planning and Scheduling.
Jajodia, S., Noel, S. and O’berry, B., 2005. Topological analysis of network attack
vulnerability. In Managing Cyber Threats (pp. 247-266). Springer, Boston, MA.
Jat, S.C., Lamba, C.S. and Rathore, V.S., 2019. Software Quality Improvement Through
Penetration Testing. In Emerging Trends in Expert Applications and Security (pp. 239-244).
Springer, Singapore.
Johansen, G., Allen, L., Heriyanto, T. and Ali, S., 2016. Kali Linux 2–Assuring Security by
Penetration Testing. Packt Publishing Ltd.
Kim, P., 2018. The Hacker Playbook 3: Practical Guide To Penetration Testing.
Independently published.
Knowles, W., Baron, A. and McGarr, T., 2016. The simulated security assessment
ecosystem: Does penetration testing need standardisation?. Computers & Security, 62,
pp.296-316.
Micskei, Z., Madeira, H., Avritzer, A., Majzik, I., Vieira, M. and Antunes, N., 2012.
Robustness testing techniques and tools. In Resilience Assessment and Evaluation of
Computing Systems (pp. 323-339). Springer, Berlin, Heidelberg.
References
Bertoglio, D.D. and Zorzo, A.F., 2017. Overview and open issues on penetration
test. Journal of the Brazilian Computer Society, 23(1), p.2.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies
for Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC)(pp.
51-58). IEEE.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Farah, T., Alam, D., Kabir, M.A. and Bhuiyan, T., 2015, October. SQLi penetration testing of
financial Web applications: Investigation of Bangladesh region. In 2015 World Congress on
Internet Security (WorldCIS) (pp. 146-151). IEEE.
Hoffmann, J., 2015, April. Simulated Penetration Testing: From" Dijkstra" to" Turing Test+
+". In Twenty-Fifth International Conference on Automated Planning and Scheduling.
Jajodia, S., Noel, S. and O’berry, B., 2005. Topological analysis of network attack
vulnerability. In Managing Cyber Threats (pp. 247-266). Springer, Boston, MA.
Jat, S.C., Lamba, C.S. and Rathore, V.S., 2019. Software Quality Improvement Through
Penetration Testing. In Emerging Trends in Expert Applications and Security (pp. 239-244).
Springer, Singapore.
Johansen, G., Allen, L., Heriyanto, T. and Ali, S., 2016. Kali Linux 2–Assuring Security by
Penetration Testing. Packt Publishing Ltd.
Kim, P., 2018. The Hacker Playbook 3: Practical Guide To Penetration Testing.
Independently published.
Knowles, W., Baron, A. and McGarr, T., 2016. The simulated security assessment
ecosystem: Does penetration testing need standardisation?. Computers & Security, 62,
pp.296-316.
Micskei, Z., Madeira, H., Avritzer, A., Majzik, I., Vieira, M. and Antunes, N., 2012.
Robustness testing techniques and tools. In Resilience Assessment and Evaluation of
Computing Systems (pp. 323-339). Springer, Berlin, Heidelberg.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PENETRATION TESTING
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Reddy, M.R. and Yalla, P., 2016, March. Mathematical analysis of Penetration Testing and
vulnerability countermeasures. In 2016 IEEE International Conference on Engineering and
Technology (ICETECH) (pp. 26-30). IEEE.
Shah, S. and Mehtre, B.M., 2015. An overview of vulnerability assessment and penetration
testing techniques. Journal of Computer Virology and Hacking Techniques, 11(1), pp.27-49.
Singh, A., Jaswal, N., Agarwal, M. and Teixeira, D., 2018. Metasploit Penetration Testing
Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments with the
most widely used penetration testing framework. Packt Publishing Ltd.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated
penetration testing. Benefits and drawbacks. Modern tendency. In 2016 13th International
Conference on Modern Problems of Radio Engineering, Telecommunications and Computer
Science (TCSET) (pp. 488-491). IEEE.
Tian, W., Yang, J.F., Xu, J. and Si, G.N., 2012, July. Attack model based penetration test for
SQL injection vulnerability. In 2012 IEEE 36th Annual Computer Software and Applications
Conference Workshops (pp. 589-594). IEEE.
Türpe, S. and Eichler, J., 2009, September. Testing production systems safely: Common
precautions in penetration testing. In 2009 Testing: Academic and Industrial Conference-
Practice and Research Techniques (pp. 205-209). IEEE.
Williams, P.A. and Woodward, A.J., 2015. Cybersecurity vulnerabilities in medical devices:
a complex environment and multifaceted problem. Medical Devices (Auckland, NZ), 8, p.305.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Reddy, M.R. and Yalla, P., 2016, March. Mathematical analysis of Penetration Testing and
vulnerability countermeasures. In 2016 IEEE International Conference on Engineering and
Technology (ICETECH) (pp. 26-30). IEEE.
Shah, S. and Mehtre, B.M., 2015. An overview of vulnerability assessment and penetration
testing techniques. Journal of Computer Virology and Hacking Techniques, 11(1), pp.27-49.
Singh, A., Jaswal, N., Agarwal, M. and Teixeira, D., 2018. Metasploit Penetration Testing
Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments with the
most widely used penetration testing framework. Packt Publishing Ltd.
Stefinko, Y., Piskozub, A. and Banakh, R., 2016, February. Manual and automated
penetration testing. Benefits and drawbacks. Modern tendency. In 2016 13th International
Conference on Modern Problems of Radio Engineering, Telecommunications and Computer
Science (TCSET) (pp. 488-491). IEEE.
Tian, W., Yang, J.F., Xu, J. and Si, G.N., 2012, July. Attack model based penetration test for
SQL injection vulnerability. In 2012 IEEE 36th Annual Computer Software and Applications
Conference Workshops (pp. 589-594). IEEE.
Türpe, S. and Eichler, J., 2009, September. Testing production systems safely: Common
precautions in penetration testing. In 2009 Testing: Academic and Industrial Conference-
Practice and Research Techniques (pp. 205-209). IEEE.
Williams, P.A. and Woodward, A.J., 2015. Cybersecurity vulnerabilities in medical devices:
a complex environment and multifaceted problem. Medical Devices (Auckland, NZ), 8, p.305.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7PENETRATION TESTING
Appendix
Decision tree
Figure 1 SOP Decision tree (Source: created by author)
Appendix
Decision tree
Figure 1 SOP Decision tree (Source: created by author)
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





